EternalBlue Exploitation: CVE-2017-0144 Vulnerability and Risk Matrix
VerifiedAdded on 2023/06/12
|10
|2009
|354
AI Summary
This report discusses the exploitation of EternalBlue for the file servers of Files’R’Us. The report focuses on the CVE-2017-0144 vulnerability and the procedure of this exploit. Moreover, a risk matrix will be provided with risk rating and proper justification. The domain impact, various remediation actions and probable prevention measures will also be discussed in this report.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: ETERNALBLUE EXPLOITATION
EternalBlue Exploitation
Name of the Student
Name of the University
Author’s Note:
EternalBlue Exploitation
Name of the Student
Name of the University
Author’s Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
ETERNALBLUE EXPLOITATION
Table of Contents
Introduction/ Abstract......................................................................................................................2
CVE-2017-0144 Issues....................................................................................................................2
EternalBlue Leverage CVE-2017-0144 Vulnerability for Performing Exploitation.......................4
Risk Matrix and Risk Rating...........................................................................................................5
Brief Justification.........................................................................................................................5
Domain Impact................................................................................................................................6
Immediate Remediation Actions.....................................................................................................6
Future Prevention Policies...............................................................................................................7
References........................................................................................................................................8
ETERNALBLUE EXPLOITATION
Table of Contents
Introduction/ Abstract......................................................................................................................2
CVE-2017-0144 Issues....................................................................................................................2
EternalBlue Leverage CVE-2017-0144 Vulnerability for Performing Exploitation.......................4
Risk Matrix and Risk Rating...........................................................................................................5
Brief Justification.........................................................................................................................5
Domain Impact................................................................................................................................6
Immediate Remediation Actions.....................................................................................................6
Future Prevention Policies...............................................................................................................7
References........................................................................................................................................8

2
ETERNALBLUE EXPLOITATION
Introduction/ Abstract
A small organization, namely, Files’R’Us mainly hosts file for its clients. Various
protocols like HTTP, SFTP, SMB and many others are being utilized by them for file
transferring. One of the employees of this organization has the responsibility of customer
services and file server management (Caulfield, Ioannidis and Pym 2017). The file servers are
being divided in a demilitarized zone, which could be accessible through RDP by utilizing the
domain account. Normal protocols for file transferring like SMB are not allowed in this
organization and hence RDP is utilized. This is resulting to the speeding up of DMZ. SMB has
the vulnerability of EternalBlue exploits and thus the file servers could be in danger.
The following report outlines a brief discussion on the exploitation of EternalBlue for the
file servers of Files’R’Us. The report focuses on the CVE-2017-0144 vulnerability and the
procedure of this exploit. Moreover, a risk matrix will be provided with risk rating and proper
justification. The domain impact, various remediation actions and probable prevention measures
will also be discussed in this report.
CVE-2017-0144 Issues
In one of the research, it was found that the Monero miner Smominru use EternalBlue
exploit to spread CVE-2017-0144 vulnerability. In May 2017 Smominruinfection was not
changed that it use Windows exploit. Malicious actor with another bad guy has mined 8900
Moneroand US$ 3.6 millionand 24 Monero, US$ 8,500 per week (Adamov and Carlsson 2017).
An operation begins regarding the EternalBlue CVE-2017-0144 vulnerability. There were 25
host trying to attack new nodes and infect via EternalBlue (CVE-2017-0144 SMB). This
increase the size of the botnet. All the hosts appear behind the autonomous system AS63199
ETERNALBLUE EXPLOITATION
Introduction/ Abstract
A small organization, namely, Files’R’Us mainly hosts file for its clients. Various
protocols like HTTP, SFTP, SMB and many others are being utilized by them for file
transferring. One of the employees of this organization has the responsibility of customer
services and file server management (Caulfield, Ioannidis and Pym 2017). The file servers are
being divided in a demilitarized zone, which could be accessible through RDP by utilizing the
domain account. Normal protocols for file transferring like SMB are not allowed in this
organization and hence RDP is utilized. This is resulting to the speeding up of DMZ. SMB has
the vulnerability of EternalBlue exploits and thus the file servers could be in danger.
The following report outlines a brief discussion on the exploitation of EternalBlue for the
file servers of Files’R’Us. The report focuses on the CVE-2017-0144 vulnerability and the
procedure of this exploit. Moreover, a risk matrix will be provided with risk rating and proper
justification. The domain impact, various remediation actions and probable prevention measures
will also be discussed in this report.
CVE-2017-0144 Issues
In one of the research, it was found that the Monero miner Smominru use EternalBlue
exploit to spread CVE-2017-0144 vulnerability. In May 2017 Smominruinfection was not
changed that it use Windows exploit. Malicious actor with another bad guy has mined 8900
Moneroand US$ 3.6 millionand 24 Monero, US$ 8,500 per week (Adamov and Carlsson 2017).
An operation begins regarding the EternalBlue CVE-2017-0144 vulnerability. There were 25
host trying to attack new nodes and infect via EternalBlue (CVE-2017-0144 SMB). This
increase the size of the botnet. All the hosts appear behind the autonomous system AS63199

3
ETERNALBLUE EXPLOITATION
network. The Monero Mining Pool, MineXMR and Proofpoint manage to locate the attack that
were conducted by 526,000 infected Windows hosts. The majority of the attack were located in
India, Russia and Taiwan.MinXMR had requested to ban the Smominru which is associated with
the current address of Monero (Dwyer 2018). At the same time, after the operation being,
Monero Mining Pool, MineXMR reacted for several days. It was observed that botnet operators
were registering new mining and domains in the new address of the same pool. One third of the
botnet had lost control in the process. Later, researchers noted that the capacity of the CPU’s was
often dominated by the cryptominer’s (Mazuran, Payne and Abegaz 2017). They have even
noted that cryptominer’s use Windows business tool and then the corporation is spread to mine
Monero which leads to performance issues.
During the first half of 2017, the researcher was not clear about the sensitive hacking
tools and exploits that were stolen from the hacking team of NSA’s elite. In the mid-August
2016, a cache of NSA tools was stolen and had auctioned off by the ShadowBrokers (Morris and
Gao 2013). This stolen tool was the EternalBlue exploit that leverage the SMB vulnerability or
CVE-2017-0144. Several supply chain hacks demonstrated interconnect cybercrime and other
cybersecurity issues that are well known. This cybersecurity issue coalesced and create massive
botnets. The May outbreak of WannaCryand June outbreak of NotPetya leveraged NSA exploits
and disrupts the organization globally (Rid and Buchanan 2015). In the mid-year report at
SurfWatch Labs, the cyber analysts described the most dangerous data breaches involve the tools
and exploits theft who leaked information.
In the research it was speculated that TheVerge.com cyber-attack was against the
Ukaraine. The attacker screwed up their decryption systems and the payments due to some
carelessness (Kwon, Liu and Hwang 2013). At the same time Petya collected important data and
ETERNALBLUE EXPLOITATION
network. The Monero Mining Pool, MineXMR and Proofpoint manage to locate the attack that
were conducted by 526,000 infected Windows hosts. The majority of the attack were located in
India, Russia and Taiwan.MinXMR had requested to ban the Smominru which is associated with
the current address of Monero (Dwyer 2018). At the same time, after the operation being,
Monero Mining Pool, MineXMR reacted for several days. It was observed that botnet operators
were registering new mining and domains in the new address of the same pool. One third of the
botnet had lost control in the process. Later, researchers noted that the capacity of the CPU’s was
often dominated by the cryptominer’s (Mazuran, Payne and Abegaz 2017). They have even
noted that cryptominer’s use Windows business tool and then the corporation is spread to mine
Monero which leads to performance issues.
During the first half of 2017, the researcher was not clear about the sensitive hacking
tools and exploits that were stolen from the hacking team of NSA’s elite. In the mid-August
2016, a cache of NSA tools was stolen and had auctioned off by the ShadowBrokers (Morris and
Gao 2013). This stolen tool was the EternalBlue exploit that leverage the SMB vulnerability or
CVE-2017-0144. Several supply chain hacks demonstrated interconnect cybercrime and other
cybersecurity issues that are well known. This cybersecurity issue coalesced and create massive
botnets. The May outbreak of WannaCryand June outbreak of NotPetya leveraged NSA exploits
and disrupts the organization globally (Rid and Buchanan 2015). In the mid-year report at
SurfWatch Labs, the cyber analysts described the most dangerous data breaches involve the tools
and exploits theft who leaked information.
In the research it was speculated that TheVerge.com cyber-attack was against the
Ukaraine. The attacker screwed up their decryption systems and the payments due to some
carelessness (Kwon, Liu and Hwang 2013). At the same time Petya collected important data and
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
ETERNALBLUE EXPLOITATION
credentials from the infected machine. This data and credentials will be valuable for the attacker
to attack in the future. The attackers are working in many ways to make money.
EternalBlue Leverage CVE-2017-0144 Vulnerability for Performing Exploitation
EladErez is the security researcher who has created EternalBlue tool for system
administrators (Uma and Padmavathi 2013). The system administrator use this tool to test the
computer connected to the network that are vulnerable via NSA’s EternalBule exploit. In the
cyber-security and hacking circles, the most potent exploit that has ever seen is the EternalBlue.
The EternalBlue has leverages the CVE-2017-0144 vulnerability in the file transfer protocol
namely SMB. As SMB was used by the company for the Windows file servers and EternalBlue
exploit has targeted SMB. In Windows computer SMB has enabled by default. There are some
special crafted SMB packets that are mishandled (Hartmann and Steup 2013). This allows
attacker to execute arbitrary code on the user’s computer and slowly attacks nearby computer.
ETERNALBLUE EXPLOITATION
credentials from the infected machine. This data and credentials will be valuable for the attacker
to attack in the future. The attackers are working in many ways to make money.
EternalBlue Leverage CVE-2017-0144 Vulnerability for Performing Exploitation
EladErez is the security researcher who has created EternalBlue tool for system
administrators (Uma and Padmavathi 2013). The system administrator use this tool to test the
computer connected to the network that are vulnerable via NSA’s EternalBule exploit. In the
cyber-security and hacking circles, the most potent exploit that has ever seen is the EternalBlue.
The EternalBlue has leverages the CVE-2017-0144 vulnerability in the file transfer protocol
namely SMB. As SMB was used by the company for the Windows file servers and EternalBlue
exploit has targeted SMB. In Windows computer SMB has enabled by default. There are some
special crafted SMB packets that are mishandled (Hartmann and Steup 2013). This allows
attacker to execute arbitrary code on the user’s computer and slowly attacks nearby computer.
5
ETERNALBLUE EXPLOITATION
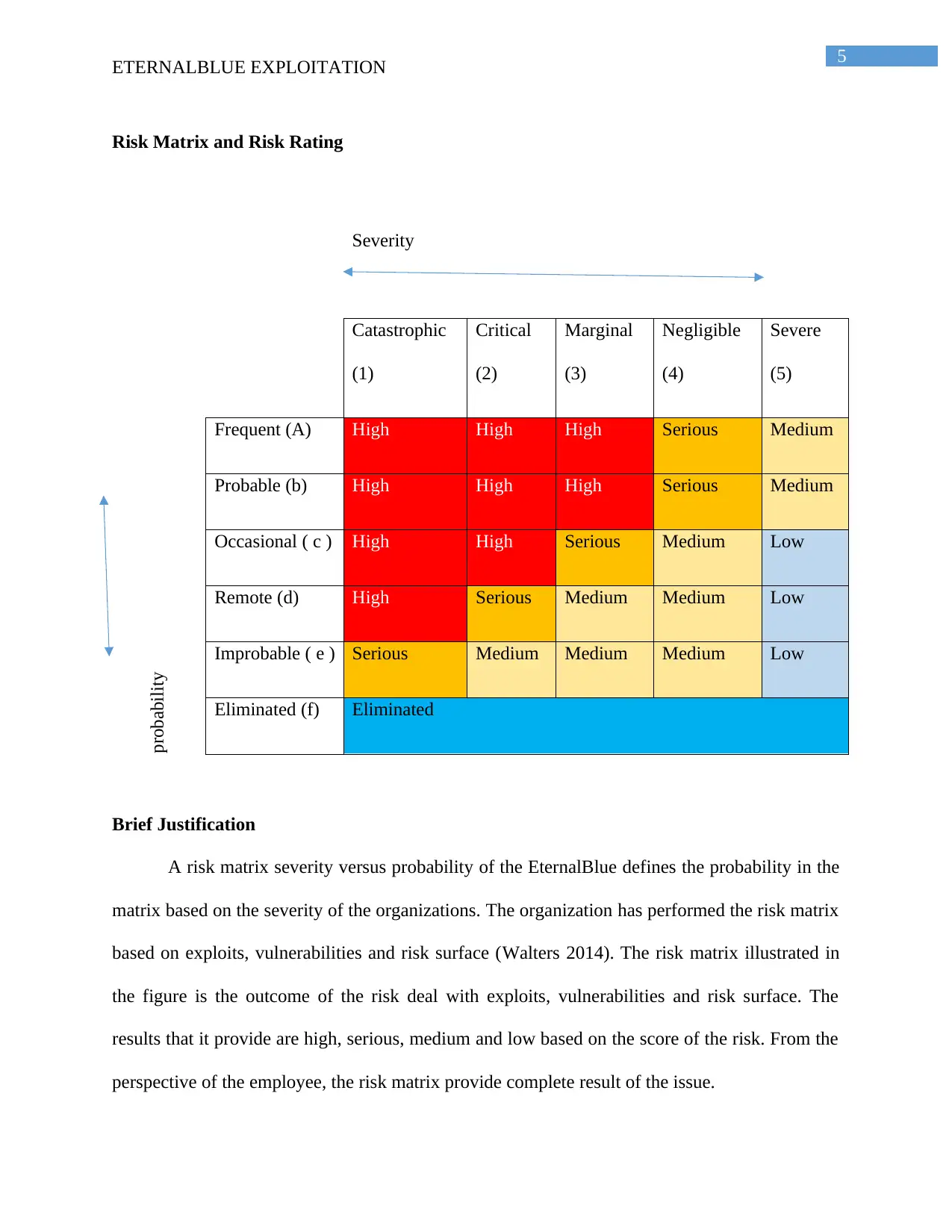
Risk Matrix and Risk Rating
Severity
Catastrophic
(1)
Critical
(2)
Marginal
(3)
Negligible
(4)
Severe
(5)
probability
Frequent (A) High High High Serious Medium
Probable (b) High High High Serious Medium
Occasional ( c ) High High Serious Medium Low
Remote (d) High Serious Medium Medium Low
Improbable ( e ) Serious Medium Medium Medium Low
Eliminated (f) Eliminated
Brief Justification
A risk matrix severity versus probability of the EternalBlue defines the probability in the
matrix based on the severity of the organizations. The organization has performed the risk matrix
based on exploits, vulnerabilities and risk surface (Walters 2014). The risk matrix illustrated in
the figure is the outcome of the risk deal with exploits, vulnerabilities and risk surface. The
results that it provide are high, serious, medium and low based on the score of the risk. From the
perspective of the employee, the risk matrix provide complete result of the issue.
ETERNALBLUE EXPLOITATION
Risk Matrix and Risk Rating
Severity
Catastrophic
(1)
Critical
(2)
Marginal
(3)
Negligible
(4)
Severe
(5)
probability
Frequent (A) High High High Serious Medium
Probable (b) High High High Serious Medium
Occasional ( c ) High High Serious Medium Low
Remote (d) High Serious Medium Medium Low
Improbable ( e ) Serious Medium Medium Medium Low
Eliminated (f) Eliminated
Brief Justification
A risk matrix severity versus probability of the EternalBlue defines the probability in the
matrix based on the severity of the organizations. The organization has performed the risk matrix
based on exploits, vulnerabilities and risk surface (Walters 2014). The risk matrix illustrated in
the figure is the outcome of the risk deal with exploits, vulnerabilities and risk surface. The
results that it provide are high, serious, medium and low based on the score of the risk. From the
perspective of the employee, the risk matrix provide complete result of the issue.

6
ETERNALBLUE EXPLOITATION
Domain Impact
The CVE-2015-5143 impact was found in the Windows version which has redirected to
the SMB vulnerability of the malicious SMB-based server that was connected to the core library
of Window API (Dwyer 2018). The Windows SMB Remote Code Execution Vulnerability –
CVE-2017-0144 affected the software version and editions namely Windows Vista, Windows
Server 2008, Windows 7, Windows Server 2008 R2, Windows 8.1, Windows Server 2012 and
Windows Server 2012 R2, Windows RT 8.1, Windows 10, and Windows Server 2016. Each of
the affected software has maximum impact of vulnerability which has been indicated by the
severity rating (Morris and Gao 2013). The vulnerabilities of remote code execution handles the
SMB server request in certain ways. Vulnerabilities when exploited by the attacker start to target
the server and could gain the ability to execute the code. The attacker sends some special crafted
packet to the targeted SMB server for the purpose of phishing. As soon as the SMB server is
being accessed y the user, the codes are being stolen by the attacker and hence the authenticity is
being lost (Uma and Padmavathi 2013). RDP is the only port that is allowed between the DMZ
and the Corporate environment and hence the employees of Files’R’Us are utilizing this
particular port for accessing the DMZ.
Immediate Remediation Actions
Although, the organization of Files’R’Us is vulnerable to EternalBlue exploitation, there
are some of the remediation actions that could be useful for them. The various remediation
actions for the organization of Files’R’Us are given below:
i) Awareness amongst Employees: This is the most significant remedy for this type of
exploitation (Caulfield, Ioannidis and Pym 2017). The employees should not click on any
ETERNALBLUE EXPLOITATION
Domain Impact
The CVE-2015-5143 impact was found in the Windows version which has redirected to
the SMB vulnerability of the malicious SMB-based server that was connected to the core library
of Window API (Dwyer 2018). The Windows SMB Remote Code Execution Vulnerability –
CVE-2017-0144 affected the software version and editions namely Windows Vista, Windows
Server 2008, Windows 7, Windows Server 2008 R2, Windows 8.1, Windows Server 2012 and
Windows Server 2012 R2, Windows RT 8.1, Windows 10, and Windows Server 2016. Each of
the affected software has maximum impact of vulnerability which has been indicated by the
severity rating (Morris and Gao 2013). The vulnerabilities of remote code execution handles the
SMB server request in certain ways. Vulnerabilities when exploited by the attacker start to target
the server and could gain the ability to execute the code. The attacker sends some special crafted
packet to the targeted SMB server for the purpose of phishing. As soon as the SMB server is
being accessed y the user, the codes are being stolen by the attacker and hence the authenticity is
being lost (Uma and Padmavathi 2013). RDP is the only port that is allowed between the DMZ
and the Corporate environment and hence the employees of Files’R’Us are utilizing this
particular port for accessing the DMZ.
Immediate Remediation Actions
Although, the organization of Files’R’Us is vulnerable to EternalBlue exploitation, there
are some of the remediation actions that could be useful for them. The various remediation
actions for the organization of Files’R’Us are given below:
i) Awareness amongst Employees: This is the most significant remedy for this type of
exploitation (Caulfield, Ioannidis and Pym 2017). The employees should not click on any
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
ETERNALBLUE EXPLOITATION
suspicious mails or activities and if any such activity is noticed, the IT personnel should be
reported.
ii) Obtaining and Patching Systems: This particular phenomenon of obtaining and
patching systems to the updated versions helps to notify such exploitations.
iii) Isolation of UDP and TCP ports: This type of isolation within the networks would
help to avoid exploitation (Walters 2014).
iv) Antivirus: Implementation and updating antivirus software helps to protect the file
servers.
Future Prevention Policies
For the future prevention from these types of exploitations, various policies could be
undertaken by the organization.
i) Vulnerability patch management process should be implemented within the business.
ii) There is a special security patch for this type of exploitations for windows (Rid and
Buchanan 2015). This was launched by Microsoft and it is extremely effective.
iii) The utilization of threat intelligence data feeds is another important procedure for
mitigating these exploitations.
iv) All the systems should be allowed to be accessed by the employees and there should
be a strict restriction in this.
ETERNALBLUE EXPLOITATION
suspicious mails or activities and if any such activity is noticed, the IT personnel should be
reported.
ii) Obtaining and Patching Systems: This particular phenomenon of obtaining and
patching systems to the updated versions helps to notify such exploitations.
iii) Isolation of UDP and TCP ports: This type of isolation within the networks would
help to avoid exploitation (Walters 2014).
iv) Antivirus: Implementation and updating antivirus software helps to protect the file
servers.
Future Prevention Policies
For the future prevention from these types of exploitations, various policies could be
undertaken by the organization.
i) Vulnerability patch management process should be implemented within the business.
ii) There is a special security patch for this type of exploitations for windows (Rid and
Buchanan 2015). This was launched by Microsoft and it is extremely effective.
iii) The utilization of threat intelligence data feeds is another important procedure for
mitigating these exploitations.
iv) All the systems should be allowed to be accessed by the employees and there should
be a strict restriction in this.

8
ETERNALBLUE EXPLOITATION
References
Adamov, A. and Carlsson, A., 2017, September. The state of ransomware. Trends and mitigation
techniques. In East-West Design & Test Symposium (EWDTS), 2017 IEEE (pp. 1-8). IEEE.
Caulfield, T., Ioannidis, C. and Pym, D., 2017, October. The US Vulnerabilities Equities
Process: An Economic Perspective. In International Conference on Decision and Game Theory
for Security (pp. 131-150). Springer, Cham.
Dwyer, A.C., 2018. The NHS cyber-attack: A look at the complex environmental conditions of
WannaCry. RAD Magazine, 44, pp.25-26.
Hartmann, K. and Steup, C., 2013, June. The vulnerability of UAVs to cyber attacks-An
approach to the risk assessment. In Cyber Conflict (CyCon), 2013 5th International Conference
on(pp. 1-23). IEEE.
Kwon, C., Liu, W. and Hwang, I., 2013, June. Security analysis for cyber-physical systems
against stealthy deception attacks. In American Control Conference (ACC), 2013 (pp. 3344-
3349). IEEE.
Mazuran, L.I., Payne, B.R. and Abegaz, T.T., 2017. Voice Hacking Proof of Concept: Using
Smartphones to Spread Ransomware to Traditional PCs.
Morris, T.H. and Gao, W., 2013, September. Industrial control system cyber attacks.
In Proceedings of the 1st International Symposium on ICS & SCADA Cyber Security
Research (pp. 22-29).
ETERNALBLUE EXPLOITATION
References
Adamov, A. and Carlsson, A., 2017, September. The state of ransomware. Trends and mitigation
techniques. In East-West Design & Test Symposium (EWDTS), 2017 IEEE (pp. 1-8). IEEE.
Caulfield, T., Ioannidis, C. and Pym, D., 2017, October. The US Vulnerabilities Equities
Process: An Economic Perspective. In International Conference on Decision and Game Theory
for Security (pp. 131-150). Springer, Cham.
Dwyer, A.C., 2018. The NHS cyber-attack: A look at the complex environmental conditions of
WannaCry. RAD Magazine, 44, pp.25-26.
Hartmann, K. and Steup, C., 2013, June. The vulnerability of UAVs to cyber attacks-An
approach to the risk assessment. In Cyber Conflict (CyCon), 2013 5th International Conference
on(pp. 1-23). IEEE.
Kwon, C., Liu, W. and Hwang, I., 2013, June. Security analysis for cyber-physical systems
against stealthy deception attacks. In American Control Conference (ACC), 2013 (pp. 3344-
3349). IEEE.
Mazuran, L.I., Payne, B.R. and Abegaz, T.T., 2017. Voice Hacking Proof of Concept: Using
Smartphones to Spread Ransomware to Traditional PCs.
Morris, T.H. and Gao, W., 2013, September. Industrial control system cyber attacks.
In Proceedings of the 1st International Symposium on ICS & SCADA Cyber Security
Research (pp. 22-29).

9
ETERNALBLUE EXPLOITATION
Rid, T. and Buchanan, B., 2015. Attributing cyber attacks. Journal of Strategic Studies, 38(1-2),
pp.4-37.
Uma, M. and Padmavathi, G., 2013. A Survey on Various Cyber Attacks and their
Classification. IJ Network Security, 15(5), pp.390-396.
Walters, R., 2014. Cyber attacks on us companies in 2014. The Heritage Foundation, 4289, pp.1-
5.
ETERNALBLUE EXPLOITATION
Rid, T. and Buchanan, B., 2015. Attributing cyber attacks. Journal of Strategic Studies, 38(1-2),
pp.4-37.
Uma, M. and Padmavathi, G., 2013. A Survey on Various Cyber Attacks and their
Classification. IJ Network Security, 15(5), pp.390-396.
Walters, R., 2014. Cyber attacks on us companies in 2014. The Heritage Foundation, 4289, pp.1-
5.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





