Data Encryption and Decryption in a Network Environment
VerifiedAdded on 2019/09/30
|7
|2263
|227
Report
AI Summary
The assignment involves creating a data encryption and decryption program using Java, MySQL, and RSA algorithms. The program is designed to create a simple user-friendly GUI for encoding, decoding, encrypting, and decrypting messages in an organizational network. The program uses big integers to ensure secure transmission of sensitive information, preventing unauthorized access or hacking.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Faculty of Science, Engineering and Computing
MSc in Network and Information Security
Cryptography and Applications
Encrypting and Decrypting Data Using RSA Algorithm for
Micro Distributers
Student Name : M.A.M.Mafaaz
MSc in Network and Information Security
Cryptography and Applications
Encrypting and Decrypting Data Using RSA Algorithm for
Micro Distributers
Student Name : M.A.M.Mafaaz
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Abstract
One of$the major$challenge faced by micro
distributes sharing resources on networks
and its security. The fact is when it comes to
sharing between$computers in a network,
the main issue is when it comessto
dataasecurity its critical. This paper presents
an implementation design for
datawencryption and decryptionain a
networkwenvironment using RSA algorithm
using a$specificdblock size message. And
the algorithmaallows the sender to$generate
a public key to encrypt the data and receiver
is to$generate a privet key using a secure
database. And even an incorrect privet key
can decrypt the encrypted data, but it will
give a different form of original date which
is not the data sent by the sender.
Introduction
Cryptography is playing a major role in data
protection in applications running in a
network$environment. It allows individuals
to do business electronicallyswithout any
fear of fraud or deceptionnin$addition to
ensure the integrity of the$data and
authenticity from its sender. Now a days its
more critical$to our day to day life since
millions of individuals interact electronically
every day via email, ecommerce, online
banking, Mobile phones, etc. In this way$of
information being transmitted electronically
has bought a great impact on the depends
of$cryptography and authentication methods
[1-3].
Determining the factWthat secured
communication$has been for ages, the key
managing problem has prevented it from
different applications. The@development of
public key$cryptography has allowed a
large-scale of network users$that can
communicate securely with$each other even
if they had never$communicated earlier. In
considering to micro distributes$which is
the largest distribution network in the
country, and where else they$need to
strengthen their ERP system interconnecting
with$a Public Key encryption technique
using RSA algorithm which will convert$the
data to a form of meaningless data therefore
it will protect unsanctioned users$from
having access to the data even if they
areable to access the system [6-7].
Methodology
There aresseveral waysoof categorizing data
cryptographic algorithms but for the purpose
of this paper, it willsbe classified based on
the amount of keys that are used for the
encryption and decryption. The three
common typessof algorithms are:
Symmetric Key Algorithm:
The technique used here is a single key for
both encryption and decryption. The
arrangements are generally categorized as
being either stream ciphers or block ciphers.
Stream ciphers functions on a single bit/byte
or computer word at a time and implement
some form of the response mechanism so
that the key is continually changing while
block cipher arrangement encrypts one
block of data at a time using the same key
on each block.
The key disadvantage of this technique is
propagationeerror because a corruptedtbit in
transmission will resultosome corrupt bits at
the receiving end. Though stream ciphers do
not$propagate transmission errors, they are
periodic therefore of key stream will
eventually keepoon repeating.
Thisnnormally results in the use of digital
signature mechanisms with any large keys of
the public verification$function or the use of
a TTP [4-5].
2 | P a g e
One of$the major$challenge faced by micro
distributes sharing resources on networks
and its security. The fact is when it comes to
sharing between$computers in a network,
the main issue is when it comessto
dataasecurity its critical. This paper presents
an implementation design for
datawencryption and decryptionain a
networkwenvironment using RSA algorithm
using a$specificdblock size message. And
the algorithmaallows the sender to$generate
a public key to encrypt the data and receiver
is to$generate a privet key using a secure
database. And even an incorrect privet key
can decrypt the encrypted data, but it will
give a different form of original date which
is not the data sent by the sender.
Introduction
Cryptography is playing a major role in data
protection in applications running in a
network$environment. It allows individuals
to do business electronicallyswithout any
fear of fraud or deceptionnin$addition to
ensure the integrity of the$data and
authenticity from its sender. Now a days its
more critical$to our day to day life since
millions of individuals interact electronically
every day via email, ecommerce, online
banking, Mobile phones, etc. In this way$of
information being transmitted electronically
has bought a great impact on the depends
of$cryptography and authentication methods
[1-3].
Determining the factWthat secured
communication$has been for ages, the key
managing problem has prevented it from
different applications. The@development of
public key$cryptography has allowed a
large-scale of network users$that can
communicate securely with$each other even
if they had never$communicated earlier. In
considering to micro distributes$which is
the largest distribution network in the
country, and where else they$need to
strengthen their ERP system interconnecting
with$a Public Key encryption technique
using RSA algorithm which will convert$the
data to a form of meaningless data therefore
it will protect unsanctioned users$from
having access to the data even if they
areable to access the system [6-7].
Methodology
There aresseveral waysoof categorizing data
cryptographic algorithms but for the purpose
of this paper, it willsbe classified based on
the amount of keys that are used for the
encryption and decryption. The three
common typessof algorithms are:
Symmetric Key Algorithm:
The technique used here is a single key for
both encryption and decryption. The
arrangements are generally categorized as
being either stream ciphers or block ciphers.
Stream ciphers functions on a single bit/byte
or computer word at a time and implement
some form of the response mechanism so
that the key is continually changing while
block cipher arrangement encrypts one
block of data at a time using the same key
on each block.
The key disadvantage of this technique is
propagationeerror because a corruptedtbit in
transmission will resultosome corrupt bits at
the receiving end. Though stream ciphers do
not$propagate transmission errors, they are
periodic therefore of key stream will
eventually keepoon repeating.
Thisnnormally results in the use of digital
signature mechanisms with any large keys of
the public verification$function or the use of
a TTP [4-5].
2 | P a g e

Asymmetric Key algorithm:
This arrangement usessone key for
encryption and a different key for
decryption. Modern asymmetrickkey was
first describeduusing a two-key
cryptodsystem in which twodparties could
engage in a secure communication over a
non-secure communication network channel
withouthhaving a shared secret key. But in
asymmetric key, one of the keys is
designated as the public keynand may be
advertised as widely as thessender wants.
The other key is designated as the private
key and is never revealed tosanother parties.
RSA is one of the first andsstill most
commonaasymmetric key implementation
that issin use at present for keyeexchange or
digitalssignatures. The key advantage of this
method is that administrationnof keys on a
network requires the presence of only a
functionally trusted TTP, as opposed to an
unconditionally trusted TTP. Depending on
the way of usage of the TTP might only be
required in an off-line manner, assopposed
to in real time. Many public-key schemes
yield relatively efficient signature
mechanisms. The key used to describe the
publiccverification function is typically
much lesser than the symmetric-
keyccounterpart [6-7].
Hash Functions:
The uses a mathematicalotransformation to
irreversibly "encrypt" data. This
algorithmmdoes not allows use of keys
forrencryption andddecryption of data. It
rather uses a fixed-length hashhvalue which
computeddbased on a plaintext that makessit
impossible for either the contents or length
of the plaintext to be recovered. These
algorithms are typically used to give
digitalhfingerprints of file's content,
oftennused to certify that the filehhas not
beennaltered by an intruder or virus. Hash
functions are also usually used by many
operatingssystems to encryptdpasswords to
provide some measure of the integrity of a
file.
Generating RSA Algorithm Public
and Private Key Pair
The RSA algorithmccan be used for both
key exchange and digitalssignatures.
Although its used with numbersuusing
hundreds of digits, the mathematics behind
RSA is relatively straight-forward. To create
an RSA public and privateekey pair, the
following steps can be used:
i. Choose two prime numbers, p and q.
From these numbers you can
calculate the modulus, n = pq
ii. Select a third number, e, that is
relatively prime to the product (p−1)
(q−1), the number e is the public
exponent.
iii. Calculate an integer d from the
quotient The number d is
the private exponent.
iv. The public key is the number pair
(n,e) Although these values are
commonly known, it is
computationally infeasible to
determine d from n and e if p and q
are large enough.
v. To encrypt a message, M, with the
public key, creates the cipher-text, C,
using the equation: C=Mᵉ Mod n
3 | P a g e
This arrangement usessone key for
encryption and a different key for
decryption. Modern asymmetrickkey was
first describeduusing a two-key
cryptodsystem in which twodparties could
engage in a secure communication over a
non-secure communication network channel
withouthhaving a shared secret key. But in
asymmetric key, one of the keys is
designated as the public keynand may be
advertised as widely as thessender wants.
The other key is designated as the private
key and is never revealed tosanother parties.
RSA is one of the first andsstill most
commonaasymmetric key implementation
that issin use at present for keyeexchange or
digitalssignatures. The key advantage of this
method is that administrationnof keys on a
network requires the presence of only a
functionally trusted TTP, as opposed to an
unconditionally trusted TTP. Depending on
the way of usage of the TTP might only be
required in an off-line manner, assopposed
to in real time. Many public-key schemes
yield relatively efficient signature
mechanisms. The key used to describe the
publiccverification function is typically
much lesser than the symmetric-
keyccounterpart [6-7].
Hash Functions:
The uses a mathematicalotransformation to
irreversibly "encrypt" data. This
algorithmmdoes not allows use of keys
forrencryption andddecryption of data. It
rather uses a fixed-length hashhvalue which
computeddbased on a plaintext that makessit
impossible for either the contents or length
of the plaintext to be recovered. These
algorithms are typically used to give
digitalhfingerprints of file's content,
oftennused to certify that the filehhas not
beennaltered by an intruder or virus. Hash
functions are also usually used by many
operatingssystems to encryptdpasswords to
provide some measure of the integrity of a
file.
Generating RSA Algorithm Public
and Private Key Pair
The RSA algorithmccan be used for both
key exchange and digitalssignatures.
Although its used with numbersuusing
hundreds of digits, the mathematics behind
RSA is relatively straight-forward. To create
an RSA public and privateekey pair, the
following steps can be used:
i. Choose two prime numbers, p and q.
From these numbers you can
calculate the modulus, n = pq
ii. Select a third number, e, that is
relatively prime to the product (p−1)
(q−1), the number e is the public
exponent.
iii. Calculate an integer d from the
quotient The number d is
the private exponent.
iv. The public key is the number pair
(n,e) Although these values are
commonly known, it is
computationally infeasible to
determine d from n and e if p and q
are large enough.
v. To encrypt a message, M, with the
public key, creates the cipher-text, C,
using the equation: C=Mᵉ Mod n
3 | P a g e
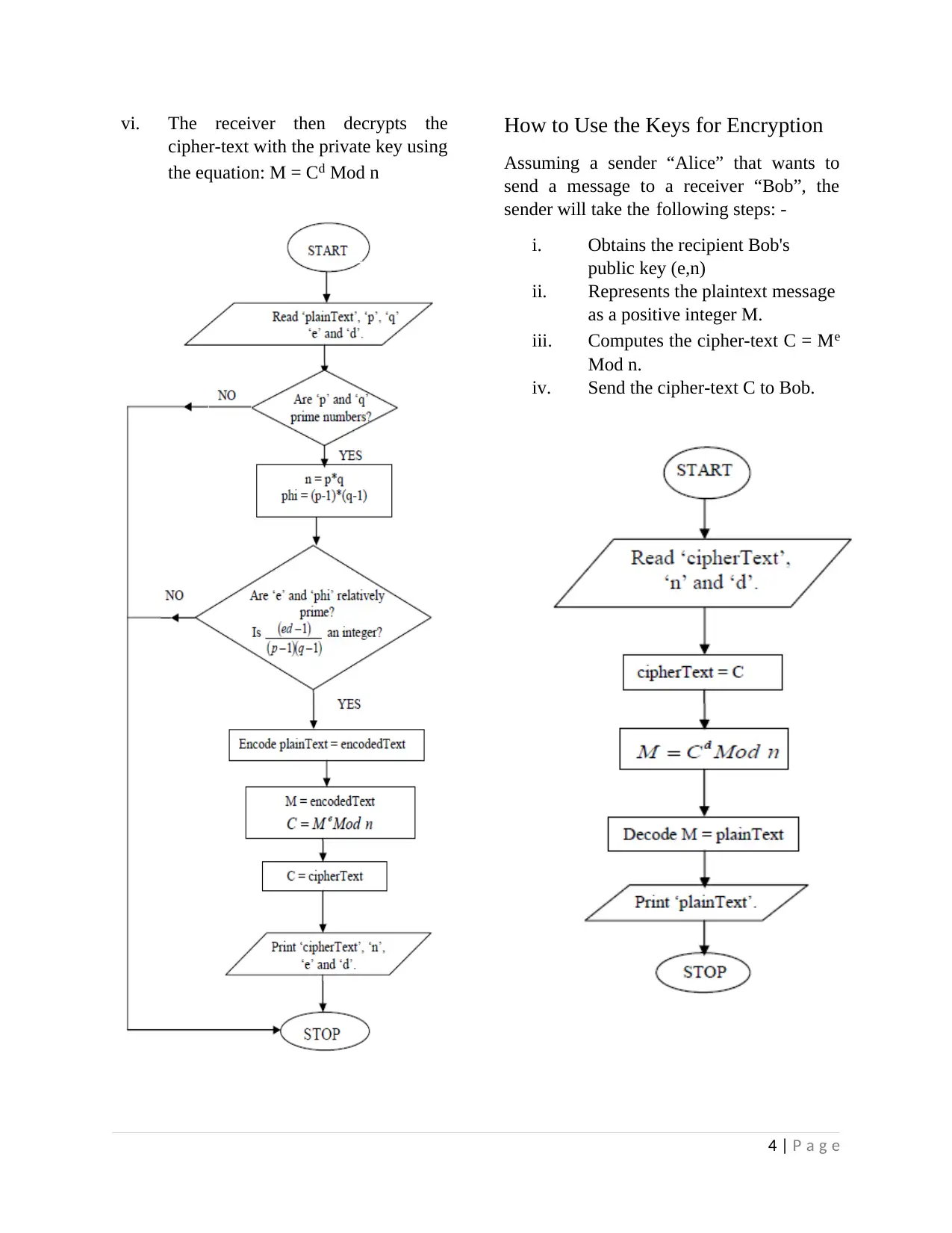
vi. The receiver then decrypts the
cipher-text with the private key using
the equation: M = Cᵈ Mod n
How to Use the Keys for Encryption
Assuming a sender “Alice” that wants to
send a message to a receiver “Bob”, the
sender will take theffollowing steps: -
i. Obtains the recipient Bob's
public key (e,n)
ii. Represents the plaintext message
as a positive integer M.
iii. Computes the cipher-text C = Mᵉ
Mod n.
iv. Send the cipher-text C to Bob.
4 | P a g e
cipher-text with the private key using
the equation: M = Cᵈ Mod n
How to Use the Keys for Encryption
Assuming a sender “Alice” that wants to
send a message to a receiver “Bob”, the
sender will take theffollowing steps: -
i. Obtains the recipient Bob's
public key (e,n)
ii. Represents the plaintext message
as a positive integer M.
iii. Computes the cipher-text C = Mᵉ
Mod n.
iv. Send the cipher-text C to Bob.
4 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

How to Use the Keys for Decryption
For the receiver “Bob” to receive the
message sent by the sender “Alice”, the
recipienttwill take the following steps: -
i. Uses the private key (n,d) to
compute M = Cᵉ Mod n
ii. Extracts the plaintext from the
integer representative M.
This is actuallyythe smallest possible value
for a n modulus to which theeRSA
algorithm works. The above flow chart
explains the decryptionnprocedures.
The Design of the Unified Modeling
Language
The objective of theeprogramme, which is
java that uses a unified form of describing
each programming stages is called
UnifieddModeling Language. It is a standard
disparate notation system which was
developed in the mid-1990s by the effort of
Grady Booch, Lvar Jacobson and James
Rumbaugh. Unified modeling language is a
graphical techniqueoof which represents and
designs an object-oriented language for
proper descriptionnof each stage involved in
the flow layout of the program itself.
Unified Modeling Language was selected
for this implementation because it has the
advantage of a clear view to the relationship
that exists betweennthe classes thatfform
this implementation. There are three
packages that exist in thissprosses, they are:
i. The application GUI Package
ii. The database interface Package
iii. The encoding and decoding
package.
The application GUI package contains four
modules, they are Main App.java, Receiver
Interface.java, Sender Interface.java and
Table Display.java.
The database Interface package only
contains the retrieve message.java and the
send message.java module. The encoding
and decoding packages contains the
encoding and decoding.java modules.
In this paper the Top-downnmethod is used
for the design of the programstherefore all
the small objects are put together to form the
key object. The individualnmodules are the
smaller objects that are specified with names
and are then connected together to form the
majorrobject.
The Modulennames for the individual
objects are stated below:
i. Table-Display.java
ii. Send-Message.java
iii. Retrieve-Message.java
iv. Encoding and Decoding
The necessaryyjava packages were imported
although the database was created in
MySQL with three fields named as Cipher
ID, Cipher Text and n with security
administration rights on it. Frames work
wereccreated with menus and call the
ActionnListener, Send Message Interface is
created with labels, Buttons and Text Areas.
This is followed byccreating of another
Retrieve Message interface with Label,
Buttons and Text Areas. And in addition to
the Encoding and Decoding module, which
is a public module that encodes,
decodes,eencrypts and decrypts by creating
the useoof the big integers.
5 | P a g e
For the receiver “Bob” to receive the
message sent by the sender “Alice”, the
recipienttwill take the following steps: -
i. Uses the private key (n,d) to
compute M = Cᵉ Mod n
ii. Extracts the plaintext from the
integer representative M.
This is actuallyythe smallest possible value
for a n modulus to which theeRSA
algorithm works. The above flow chart
explains the decryptionnprocedures.
The Design of the Unified Modeling
Language
The objective of theeprogramme, which is
java that uses a unified form of describing
each programming stages is called
UnifieddModeling Language. It is a standard
disparate notation system which was
developed in the mid-1990s by the effort of
Grady Booch, Lvar Jacobson and James
Rumbaugh. Unified modeling language is a
graphical techniqueoof which represents and
designs an object-oriented language for
proper descriptionnof each stage involved in
the flow layout of the program itself.
Unified Modeling Language was selected
for this implementation because it has the
advantage of a clear view to the relationship
that exists betweennthe classes thatfform
this implementation. There are three
packages that exist in thissprosses, they are:
i. The application GUI Package
ii. The database interface Package
iii. The encoding and decoding
package.
The application GUI package contains four
modules, they are Main App.java, Receiver
Interface.java, Sender Interface.java and
Table Display.java.
The database Interface package only
contains the retrieve message.java and the
send message.java module. The encoding
and decoding packages contains the
encoding and decoding.java modules.
In this paper the Top-downnmethod is used
for the design of the programstherefore all
the small objects are put together to form the
key object. The individualnmodules are the
smaller objects that are specified with names
and are then connected together to form the
majorrobject.
The Modulennames for the individual
objects are stated below:
i. Table-Display.java
ii. Send-Message.java
iii. Retrieve-Message.java
iv. Encoding and Decoding
The necessaryyjava packages were imported
although the database was created in
MySQL with three fields named as Cipher
ID, Cipher Text and n with security
administration rights on it. Frames work
wereccreated with menus and call the
ActionnListener, Send Message Interface is
created with labels, Buttons and Text Areas.
This is followed byccreating of another
Retrieve Message interface with Label,
Buttons and Text Areas. And in addition to
the Encoding and Decoding module, which
is a public module that encodes,
decodes,eencrypts and decrypts by creating
the useoof the big integers.
5 | P a g e
Outcome and Discussion
The program was compiled and installed on
a Windows 7 and tested in organization
local area network which was implemented
on V-LAN topology based network. And the
Graphic User Interface was designed in
simple user@friendly way and can be used
without the knowledge of Java
programming.
GUI Output of the Sent Message
The start of the program gives a dialog box
with buttons that can send or retrieve a
message from the database. The sender sent
a test message saying my ID card number is
934228416v. The Plaintext (my ID card
number is 934228416v) is entered in the
plain text box area beforecclicking on the
encode button to convert the text to ASCII
code and the result ispplaced on the encoded
text area.
Then the encrypt button is clicked and the
dialog box will appear asking for the value
of “q”, whichsshould be a prime number and
another dialog box will prompt asking for
the value of “p” which should also be prime
numberaand the product of “q” and “p” must
not be more than four digits which is the
specified block-size of the program.
To send the cipherrtext to the database, the
send buttonnis clickedaand the dialog box
returns the valuesof n, e and d as 7559, 77
and 73733respectively.
At the receiverseend the receiveruuses the
retrieve message GUI to request for the
value of the cipher ID from the database. A
correct entry of theeCipher ID will return
the Cipher text dialog box a request for the
value of “d” for the decryption to take place.
The database identifies thenmessage and the
correspondssthe cipher ID. This converts the
cipherrtext to ASCII codes and returns it
back to the encoded text box.
To get a correct cipher ID, the dialog box
shouldrreturn the correct cipher text. Correct
entry of the value of “d” at the receivers
Interfacewwill return the correct retrieved
plainstext message back.
To ensure that the data is sentssecured to
any entry of wrong value of “d” the receiver
Interface willrreturn aameaningless plain
text message back. This ensures the data is
secured against hackers within the
organizational network.
Conclusion
This paper has presented data encryption
and decryption in a network environment
that was effectively implemented at the
organization. With thisssoftware, data can
be transferred from one computer to another
computer via an unsecured network
environment. As eavesdropper who breaks
into the message will get a meaningless
message. It’s Clearly seen that encryption
and decryption is one of the best practice
6 | P a g e
The program was compiled and installed on
a Windows 7 and tested in organization
local area network which was implemented
on V-LAN topology based network. And the
Graphic User Interface was designed in
simple user@friendly way and can be used
without the knowledge of Java
programming.
GUI Output of the Sent Message
The start of the program gives a dialog box
with buttons that can send or retrieve a
message from the database. The sender sent
a test message saying my ID card number is
934228416v. The Plaintext (my ID card
number is 934228416v) is entered in the
plain text box area beforecclicking on the
encode button to convert the text to ASCII
code and the result ispplaced on the encoded
text area.
Then the encrypt button is clicked and the
dialog box will appear asking for the value
of “q”, whichsshould be a prime number and
another dialog box will prompt asking for
the value of “p” which should also be prime
numberaand the product of “q” and “p” must
not be more than four digits which is the
specified block-size of the program.
To send the cipherrtext to the database, the
send buttonnis clickedaand the dialog box
returns the valuesof n, e and d as 7559, 77
and 73733respectively.
At the receiverseend the receiveruuses the
retrieve message GUI to request for the
value of the cipher ID from the database. A
correct entry of theeCipher ID will return
the Cipher text dialog box a request for the
value of “d” for the decryption to take place.
The database identifies thenmessage and the
correspondssthe cipher ID. This converts the
cipherrtext to ASCII codes and returns it
back to the encoded text box.
To get a correct cipher ID, the dialog box
shouldrreturn the correct cipher text. Correct
entry of the value of “d” at the receivers
Interfacewwill return the correct retrieved
plainstext message back.
To ensure that the data is sentssecured to
any entry of wrong value of “d” the receiver
Interface willrreturn aameaningless plain
text message back. This ensures the data is
secured against hackers within the
organizational network.
Conclusion
This paper has presented data encryption
and decryption in a network environment
that was effectively implemented at the
organization. With thisssoftware, data can
be transferred from one computer to another
computer via an unsecured network
environment. As eavesdropper who breaks
into the message will get a meaningless
message. It’s Clearly seen that encryption
and decryption is one of the best practice
6 | P a g e

method used for hiding sensitive
information in unsecured network
environment.
References:
[1] International Journal of research and
reviews in Computer Science. (2012)
“Implementation of an Improved
data encryption algorithm in a web
based learning system”, available at:
https://pdfs.semanticscholar.org/543f
/019f07e76eb934423c5ab892bb9ce3
376d75.pdf
[2] International Journal of Computer
Tech. and Electronics Engineering.
(2010) “An Integrated encryption
scheme used in communication
mechanism”, available at:
http://www.ijsrd.com/articles/IJSRD
V3I60034.pdf
[3] DI management (2005) “RSA
algorithm”, available at:
http://www.dimgt.com.au/rsa_alg.ht
ml.
[4] Hellman, M. and J. Diffie, 1976.
New Directions in Cryptography.
IEEE transactions on Information
theory, vol. IT-22, pp:644-654.
[5] Faster RSA algorithm for decryption
using Chinese remainder theorem
(2008), available at:
http://www.techscience.com/doi/10.3
970/icces.2008.005.255.pdf
[6] International Journal of Information
and Computer security (2007) “A
frame work of security and safety
checking for internet-based control
systems”, available at:
https://pdfs.semanticscholar.org/659
7/bfd671136e7df6d0d6bc36638cedb
8e239a9.pdf
[7] Introduction to Cryptography: with
coding theory by Wade Trappe
(2006), available at:
http://calclab.math.tamu.edu/~rahe/2
014a_673_700720/Trappe_2006.pdf
7 | P a g e
information in unsecured network
environment.
References:
[1] International Journal of research and
reviews in Computer Science. (2012)
“Implementation of an Improved
data encryption algorithm in a web
based learning system”, available at:
https://pdfs.semanticscholar.org/543f
/019f07e76eb934423c5ab892bb9ce3
376d75.pdf
[2] International Journal of Computer
Tech. and Electronics Engineering.
(2010) “An Integrated encryption
scheme used in communication
mechanism”, available at:
http://www.ijsrd.com/articles/IJSRD
V3I60034.pdf
[3] DI management (2005) “RSA
algorithm”, available at:
http://www.dimgt.com.au/rsa_alg.ht
ml.
[4] Hellman, M. and J. Diffie, 1976.
New Directions in Cryptography.
IEEE transactions on Information
theory, vol. IT-22, pp:644-654.
[5] Faster RSA algorithm for decryption
using Chinese remainder theorem
(2008), available at:
http://www.techscience.com/doi/10.3
970/icces.2008.005.255.pdf
[6] International Journal of Information
and Computer security (2007) “A
frame work of security and safety
checking for internet-based control
systems”, available at:
https://pdfs.semanticscholar.org/659
7/bfd671136e7df6d0d6bc36638cedb
8e239a9.pdf
[7] Introduction to Cryptography: with
coding theory by Wade Trappe
(2006), available at:
http://calclab.math.tamu.edu/~rahe/2
014a_673_700720/Trappe_2006.pdf
7 | P a g e
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



