Security Technologies: Critical Evaluation of FortiSIEM Tool
VerifiedAdded on 2023/06/10
|17
|3517
|226
Report
AI Summary
This report provides a critical evaluation of the FortiSIEM security tool, examining its purpose, development, and resource requirements. It details the types of vulnerabilities FortiSIEM addresses, including CVE-2017-5753, CVE-2017-5715, and CVE-2018-5711, and discusses how the tool could be used to hack into a future smart grid. The report also highlights FortiSIEM's strengths, such as its ability to enhance reaction to cyber attacks and provide a comprehensive IT security framework, as well as its weaknesses, including installation difficulties and the lack of stack sharing or high-accessibility features. The document concludes with a discussion of the resources required to use FortiSIEM, including hardware, software, and specific knowledge, emphasizing the importance of proper estimation for optimal performance.

Critical Evaluation of a Security Tool
Name
Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Description of the FortiSIEM tool
FortiSIEM security tool was first initiated due to the ever exponentially growing
number of cases of cyberattacks all around the universe. Combined with many ability
deficiencies, and asset requirements, security had in the past turned into everyone's
concern except that its perceivability, occasional relationship and remediation are
individual obligations (Kavanagh, Rochford and Bussa, 2015.). Successful security
requires the accessibility of every one of the gadgets plus all the foundation in
realtime. Furthermore, the setting as in what gadgets speak to a danger or threat is
important. Their ability so one is able to deal with the risk the business faces and not
the clamor numerous security instruments make. FortiSIEM has since been very
beneficial since it gives the cross relationship, applies machine learning and UEBA to
enhance reaction to cyber attacks and to stop breaks before they happen.
FortiSIEM gives an across the board, flawlessly incorporated and benefit oriented IT
security framework that spreads execution, accessibility, change, and security
checking parts of system gadgets, servers, and applications. It is offered in two
adaptations:
It is a VMware based virtual apparatus, which you can convey as a solitary machine
or a group of virtual machines in an exceptionally accessible, scaled-out lattice
engineering. This is the thing that is mainly alluded to as FortiSIEM Enterprise.
FortiSIEM security tool was first initiated due to the ever exponentially growing
number of cases of cyberattacks all around the universe. Combined with many ability
deficiencies, and asset requirements, security had in the past turned into everyone's
concern except that its perceivability, occasional relationship and remediation are
individual obligations (Kavanagh, Rochford and Bussa, 2015.). Successful security
requires the accessibility of every one of the gadgets plus all the foundation in
realtime. Furthermore, the setting as in what gadgets speak to a danger or threat is
important. Their ability so one is able to deal with the risk the business faces and not
the clamor numerous security instruments make. FortiSIEM has since been very
beneficial since it gives the cross relationship, applies machine learning and UEBA to
enhance reaction to cyber attacks and to stop breaks before they happen.
FortiSIEM gives an across the board, flawlessly incorporated and benefit oriented IT
security framework that spreads execution, accessibility, change, and security
checking parts of system gadgets, servers, and applications. It is offered in two
adaptations:
It is a VMware based virtual apparatus, which you can convey as a solitary machine
or a group of virtual machines in an exceptionally accessible, scaled-out lattice
engineering. This is the thing that is mainly alluded to as FortiSIEM Enterprise.

Programming as-a-Service (SaaS), where you send a Collector virtual on-premises for
a client, and the majority of the client information is transmitted to a data center for a
FortiSIEM server (Zimmerman, Lerner, and Menezes, 2014). This is the thing that we
allude to as FortiSIEM Multi-Tenant, since gatherer arrangements are normally
utilized by associations, for example, Managed Service Providers to screen the
administrations of their client.
A Security Information and Event Monitoring (SIEM) is an essential instrument used
in data framework security as it goes for giving an unmistakable perspective of an
association's data innovation security. This device will give constant and up and
coming security checking, discovery of dangers, and take into account a suitable
reaction to occurrences that happen inside the association. Besides, it fits the
investigation of framework logs and capacity. Any frequencies would then be able to
be accounted for continuously at whatever point this instrument is used (Dourish,
2002).
Following the quick changes in innovation for a long decade now, numerous SIEM
apparatuses have been outlined and created by programming organizations to help
address the issues of little and colossal ventures. Nonetheless, not these devices meet
every one of the prerequisites expected by the customer associations. Organizations
must pick the best device that will extraordinarily and requiring little to no effort meet
its framework security and business needs (Wenge et al., 2014).
a client, and the majority of the client information is transmitted to a data center for a
FortiSIEM server (Zimmerman, Lerner, and Menezes, 2014). This is the thing that we
allude to as FortiSIEM Multi-Tenant, since gatherer arrangements are normally
utilized by associations, for example, Managed Service Providers to screen the
administrations of their client.
A Security Information and Event Monitoring (SIEM) is an essential instrument used
in data framework security as it goes for giving an unmistakable perspective of an
association's data innovation security. This device will give constant and up and
coming security checking, discovery of dangers, and take into account a suitable
reaction to occurrences that happen inside the association. Besides, it fits the
investigation of framework logs and capacity. Any frequencies would then be able to
be accounted for continuously at whatever point this instrument is used (Dourish,
2002).
Following the quick changes in innovation for a long decade now, numerous SIEM
apparatuses have been outlined and created by programming organizations to help
address the issues of little and colossal ventures. Nonetheless, not these devices meet
every one of the prerequisites expected by the customer associations. Organizations
must pick the best device that will extraordinarily and requiring little to no effort meet
its framework security and business needs (Wenge et al., 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Other prestigious little organizations have prescribed that different associations like
them have to put resources into an item called FortiSIEM. This is the most proper
item for little and medium estimated organizations and undertakings.
Each association goes for giving a nonstop and smooth execution and guarantee an
impeccable security framework for every one of their frameworks and information.
FortiSIEM was intended to enable associations to achieve such goals. FortiSIEM
accumulates all occasions and log information from each gadget in the system and
completes an examination of the data to discover security rates assuming any. This
item will dissect immense measures of information from crosswise over unequal
spaces progressively.
FortiSIEM produces point by point writes about security rates in this way including
an additional consequence of danger recognition by fitting outcomes from its
investigation with various outside risk insight sources. Whenever FortiSIEM
distinguishes a malevolent action, it will altogether search for the fundamental reason
for the action and from there on send the outcomes to other security programming
projects, for example, firewalls so all appropriate methods can be executed to
counteract such assaults later on. It is without a doubt clear here that associations
must use the FortiSIEM apparatuses keeping in mind the end goal to expand its
protection from digital assaults and limit dangers (Bhat et al., 2014).
them have to put resources into an item called FortiSIEM. This is the most proper
item for little and medium estimated organizations and undertakings.
Each association goes for giving a nonstop and smooth execution and guarantee an
impeccable security framework for every one of their frameworks and information.
FortiSIEM was intended to enable associations to achieve such goals. FortiSIEM
accumulates all occasions and log information from each gadget in the system and
completes an examination of the data to discover security rates assuming any. This
item will dissect immense measures of information from crosswise over unequal
spaces progressively.
FortiSIEM produces point by point writes about security rates in this way including
an additional consequence of danger recognition by fitting outcomes from its
investigation with various outside risk insight sources. Whenever FortiSIEM
distinguishes a malevolent action, it will altogether search for the fundamental reason
for the action and from there on send the outcomes to other security programming
projects, for example, firewalls so all appropriate methods can be executed to
counteract such assaults later on. It is without a doubt clear here that associations
must use the FortiSIEM apparatuses keeping in mind the end goal to expand its
protection from digital assaults and limit dangers (Bhat et al., 2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

FortiSIEM was outlined in a perplexing way in that it was normal that clients would
have a little hard time when utilizing this item soon after the primary arrangement. In
spite of these desires, numerous clients have inspected this item and they affirm that it
is really easy to introduce and actualize. This item was produced by Fortinet. They
made utilization of extraordinary calculations to give it capacities of preparing
extensive volumes of standards in microseconds and give enhanced identification time
spans. Fortinet built up an online graphical interface for communicating and making
utilization of FortiSIEM. It can likewise be let go in broad daylight and private virtual
machines. Different elements that have completed an audit of FortiSIEM claim that it
is immaculate in following the security of any system or IT framework.
At the point when Security Information and Event Monitoring device is executed, any
association that gives response time a need will ensure that every one of their interests
in most recent database stockpiling advancements and system security will stay
unblemished constantly. This item gives an ideal opportunity to organize directors to
effortlessly discover and settle any system security dangers while in the meantime
guaranteeing that they consent to the world gauges of system security.
have a little hard time when utilizing this item soon after the primary arrangement. In
spite of these desires, numerous clients have inspected this item and they affirm that it
is really easy to introduce and actualize. This item was produced by Fortinet. They
made utilization of extraordinary calculations to give it capacities of preparing
extensive volumes of standards in microseconds and give enhanced identification time
spans. Fortinet built up an online graphical interface for communicating and making
utilization of FortiSIEM. It can likewise be let go in broad daylight and private virtual
machines. Different elements that have completed an audit of FortiSIEM claim that it
is immaculate in following the security of any system or IT framework.
At the point when Security Information and Event Monitoring device is executed, any
association that gives response time a need will ensure that every one of their interests
in most recent database stockpiling advancements and system security will stay
unblemished constantly. This item gives an ideal opportunity to organize directors to
effortlessly discover and settle any system security dangers while in the meantime
guaranteeing that they consent to the world gauges of system security.

From this evaluation, it is clear that FortiSIEM is the ideal Security Information and
Event Monitoring instrument that should be actualized. Regardless of all the
previously mentioned benefits of FortiSIEM, it additionally has a couple of
downsides. A few clients who have had an opportunity to utilize it have given fair
surveys that this item is extremely hard to introduce. One client from
www.scmagazineuk.com guaranteed that FortiSIEM contains a fire of adolescence,
for instance, its trouble to setup crisp in a workstation. That there is such a great
amount to getting it up and running.
Again and again, FortiSIEM has demonstrated to have a deterministic aim of uniting
security and operational abilities with a sole purpose of recognizing and taking care of
issues in a virtual and a genuine organization condition. As though that isn't sufficient,
FortiSIEM has kept on getting empowering client surveys on the level of how it can
be altered to address client issues. At last, right when associations uses FortiSIEM,
they unquestionably show their duty with respect to anchor delicate data and besides
to accomplish managerial and mechanical consistence requirements.
Vulnerabilities
FortiSIEM generally has solved most of the cve vulnerabilities, the references to these
vulnerabilities that have in the past been a big hazard to small and huge entreprises
include:
Mantis Reference Vulnerability
Event Monitoring instrument that should be actualized. Regardless of all the
previously mentioned benefits of FortiSIEM, it additionally has a couple of
downsides. A few clients who have had an opportunity to utilize it have given fair
surveys that this item is extremely hard to introduce. One client from
www.scmagazineuk.com guaranteed that FortiSIEM contains a fire of adolescence,
for instance, its trouble to setup crisp in a workstation. That there is such a great
amount to getting it up and running.
Again and again, FortiSIEM has demonstrated to have a deterministic aim of uniting
security and operational abilities with a sole purpose of recognizing and taking care of
issues in a virtual and a genuine organization condition. As though that isn't sufficient,
FortiSIEM has kept on getting empowering client surveys on the level of how it can
be altered to address client issues. At last, right when associations uses FortiSIEM,
they unquestionably show their duty with respect to anchor delicate data and besides
to accomplish managerial and mechanical consistence requirements.
Vulnerabilities
FortiSIEM generally has solved most of the cve vulnerabilities, the references to these
vulnerabilities that have in the past been a big hazard to small and huge entreprises
include:
Mantis Reference Vulnerability
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
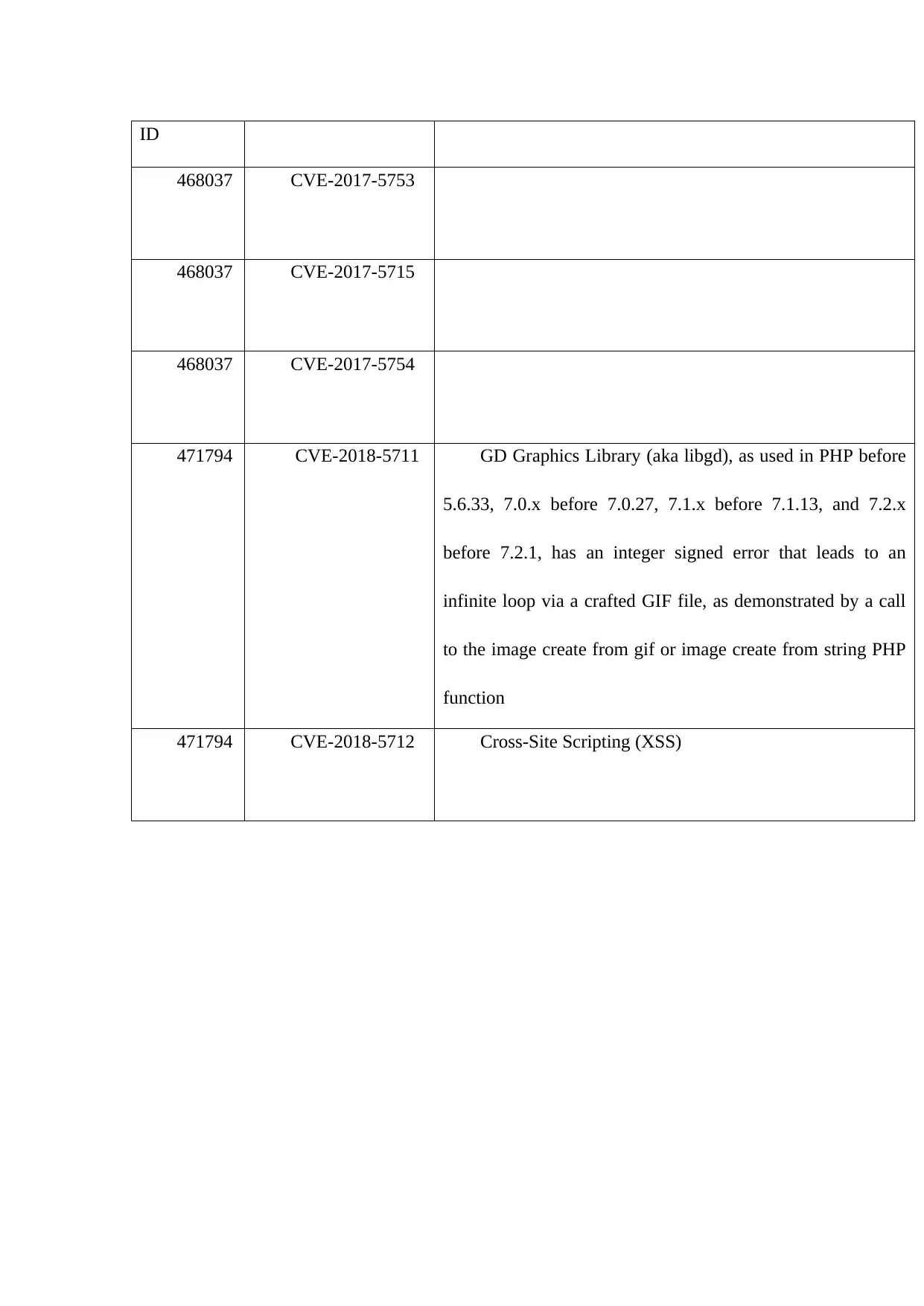
ID
468037 CVE-2017-5753
468037 CVE-2017-5715
468037 CVE-2017-5754
471794 CVE-2018-5711 GD Graphics Library (aka libgd), as used in PHP before
5.6.33, 7.0.x before 7.0.27, 7.1.x before 7.1.13, and 7.2.x
before 7.2.1, has an integer signed error that leads to an
infinite loop via a crafted GIF file, as demonstrated by a call
to the image create from gif or image create from string PHP
function
471794 CVE-2018-5712 Cross-Site Scripting (XSS)
468037 CVE-2017-5753
468037 CVE-2017-5715
468037 CVE-2017-5754
471794 CVE-2018-5711 GD Graphics Library (aka libgd), as used in PHP before
5.6.33, 7.0.x before 7.0.27, 7.1.x before 7.1.13, and 7.2.x
before 7.2.1, has an integer signed error that leads to an
infinite loop via a crafted GIF file, as demonstrated by a call
to the image create from gif or image create from string PHP
function
471794 CVE-2018-5712 Cross-Site Scripting (XSS)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The latest version of FortiSIEM has been released to address several
vulnerabilities that did exist in its previous versions and even other security tools as
well. FortiSIEM is now able to run in a system while the system cannot run any
update which in the past have cause excessive clock skew on the system collector.
Furthermore, many security tools in the past could allow the NTP reset the system
clock back by maybe few hours which may lead to missing some other security
incidences. FortiSIEM now ensures that the clock is never reset in all AWS
deployments whenever the system time is not correct during boot time. Other security
tools also have had poor performance monitorign in that they never reported memory
and even session count through the SNMP protocol. FortiSIEM has since solved this
vulnerability. Moreover, there is always this vulnerability by other SIEM tools that
makes a user not be able to change from Enterprise to a Service Provider or the other
way round during the time of applying new licenses on an existing system. FortiSIEM
has also made this change of mode possible. Improper multi-context determination
has been causing failure in Cisco ASA configuration discovery in the older versions
of FortiSIEM, the current version does not allow for any improper multi-context
determination in monitoring system performance.
vulnerabilities that did exist in its previous versions and even other security tools as
well. FortiSIEM is now able to run in a system while the system cannot run any
update which in the past have cause excessive clock skew on the system collector.
Furthermore, many security tools in the past could allow the NTP reset the system
clock back by maybe few hours which may lead to missing some other security
incidences. FortiSIEM now ensures that the clock is never reset in all AWS
deployments whenever the system time is not correct during boot time. Other security
tools also have had poor performance monitorign in that they never reported memory
and even session count through the SNMP protocol. FortiSIEM has since solved this
vulnerability. Moreover, there is always this vulnerability by other SIEM tools that
makes a user not be able to change from Enterprise to a Service Provider or the other
way round during the time of applying new licenses on an existing system. FortiSIEM
has also made this change of mode possible. Improper multi-context determination
has been causing failure in Cisco ASA configuration discovery in the older versions
of FortiSIEM, the current version does not allow for any improper multi-context
determination in monitoring system performance.

FortiSIEM unfortunately does not have stack sharing or high-accessibility, and these
are imperative things to that must be actualized in any security tools that are reputable
and future proof. This deficiency has made fortiSIEM customers to do similar things
in another way by utilizing third party vendors, however not normally having these
highlights makes it convoluted (Zimmerman,Lerner and Menezes, 2014).
Furthermore, the tool is provided as a stand alone virtual appliance that comes with all
features in an .ova file, however, customers and users using this tool have n the past
reported that the installation process takes really a great deal of time. The setup
usually conflicts with many storage formats.
Resources Required to use the tool
The FortiSIEM virtual machine arrangement works as a turnkey, visitor have
application running inside the most prevalent hypervisors with the choice of utilizing
NFS or localhost method of storage. The execution procedure is adaptable and can be
refined in stages to help an assortment of circulated and half and half cloud usage The
FortiSIEM virtual apparatus is set on a system where it can get operational
information, and also build up sessions with the foundation. Remote destinations can
utilize the FortiSIEM Collector customer to locally find, gather, pack and safely
transmit of task information back to the FortiSIEM virtual apparatus. FortiSIEM'
scale-out design takes into consideration virtual apparatus bunching to expand
handling limit and accessibility
are imperative things to that must be actualized in any security tools that are reputable
and future proof. This deficiency has made fortiSIEM customers to do similar things
in another way by utilizing third party vendors, however not normally having these
highlights makes it convoluted (Zimmerman,Lerner and Menezes, 2014).
Furthermore, the tool is provided as a stand alone virtual appliance that comes with all
features in an .ova file, however, customers and users using this tool have n the past
reported that the installation process takes really a great deal of time. The setup
usually conflicts with many storage formats.
Resources Required to use the tool
The FortiSIEM virtual machine arrangement works as a turnkey, visitor have
application running inside the most prevalent hypervisors with the choice of utilizing
NFS or localhost method of storage. The execution procedure is adaptable and can be
refined in stages to help an assortment of circulated and half and half cloud usage The
FortiSIEM virtual apparatus is set on a system where it can get operational
information, and also build up sessions with the foundation. Remote destinations can
utilize the FortiSIEM Collector customer to locally find, gather, pack and safely
transmit of task information back to the FortiSIEM virtual apparatus. FortiSIEM'
scale-out design takes into consideration virtual apparatus bunching to expand
handling limit and accessibility
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

(Woolfe, Nguyen-Duy and Whittle, 2018). Extra virtual machines can be included
the-fly with ostensible arrangement, which will consequently disperse workload
crosswise over bunch individuals to stretch out occasion investigation throughput and
to decrease question reaction time.
This is a proposal for capacity limit, plate execution, and system throughput for an
ideal execution of FortiSIEM installations preparing over than 10,000 EPS. When all
is said in done, occasional ingestion at high EPS needs a smaller capacity IOPS than
for questions just on the grounds that inquiries need to filter higher volumes of
information that has amassed after some time. For instance, at 20,000 EPS, you have
86,400 times a greater number of information in multi day than in one moment, so a
question, for example, 'Top Event writes by mean the previous 1 day' should examine
20,000 x 86,400 = 1.72 billion occasions. In this way, it is vital to estimate your
FortiSIEM bunch to deal with your inquiry and report necessities first, which will
likewise deal with occasion ingestion extremely well. These are the best 3 activities to
undertake for satisfactory FortiSIEM query execution: Include more nodes of
workers, higher than what is needed for occasion ingestion alone. 10Gbps system on
NFS server is an absolute necessity, and if practical on Supervisor and Worker hubs
too. SSD Caching on the NFS server:The measure of the SSD ought to be as near the
size required to store hot information (Bhatt, Manadhata and Zomlot, 2014). In the
run of the common client situations, the most recent monthly information can be
viewed as hot information since month to month reports are very usually run.
the-fly with ostensible arrangement, which will consequently disperse workload
crosswise over bunch individuals to stretch out occasion investigation throughput and
to decrease question reaction time.
This is a proposal for capacity limit, plate execution, and system throughput for an
ideal execution of FortiSIEM installations preparing over than 10,000 EPS. When all
is said in done, occasional ingestion at high EPS needs a smaller capacity IOPS than
for questions just on the grounds that inquiries need to filter higher volumes of
information that has amassed after some time. For instance, at 20,000 EPS, you have
86,400 times a greater number of information in multi day than in one moment, so a
question, for example, 'Top Event writes by mean the previous 1 day' should examine
20,000 x 86,400 = 1.72 billion occasions. In this way, it is vital to estimate your
FortiSIEM bunch to deal with your inquiry and report necessities first, which will
likewise deal with occasion ingestion extremely well. These are the best 3 activities to
undertake for satisfactory FortiSIEM query execution: Include more nodes of
workers, higher than what is needed for occasion ingestion alone. 10Gbps system on
NFS server is an absolute necessity, and if practical on Supervisor and Worker hubs
too. SSD Caching on the NFS server:The measure of the SSD ought to be as near the
size required to store hot information (Bhatt, Manadhata and Zomlot, 2014). In the
run of the common client situations, the most recent monthly information can be
viewed as hot information since month to month reports are very usually run.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The FortiSIEM Virtual Appliance can be introduced utilizing either capacity arranged
inside the ESX server or NFS capacity. See the topic Configuring NFS Server for
more data on working with NFS mode of storage.
Occasion Data Storage Requirements: The capacity prerequisite appeared in the Event
Data Storage section is just for the event db information, yet the information segment
additionally incorporates CMDB reinforcements and inquiries. You should set
the/information segment to a bigger sum of capacity to suit for this.
Encryption for Communication Between FortiSIEM Virtual Appliances.All
correspondence between Collectors that are introduced on-premises and FortiSIEM
Supervisors and Workers is anchored by TLS 1.2 encryption. Correspondences are
overseen by OpenSSL/Apache HTTP Server/mod_ssl on the Supervisor/Worker side,
and libcurl, utilizing the NSS library for SSL, on the Collector side.The FortiSIEM
Manager/Workers utilize RSA testament with 2048 bits as default. You can control
the correct figures utilized for correspondences between virtual machines by altering
the SSLCipherSuite section in the file /and so orth/httpd/conf.d/ssl.conf on FortiSIEM
Supervisors and Specialists.
How FortiSIEM can be useful in the future
inside the ESX server or NFS capacity. See the topic Configuring NFS Server for
more data on working with NFS mode of storage.
Occasion Data Storage Requirements: The capacity prerequisite appeared in the Event
Data Storage section is just for the event db information, yet the information segment
additionally incorporates CMDB reinforcements and inquiries. You should set
the/information segment to a bigger sum of capacity to suit for this.
Encryption for Communication Between FortiSIEM Virtual Appliances.All
correspondence between Collectors that are introduced on-premises and FortiSIEM
Supervisors and Workers is anchored by TLS 1.2 encryption. Correspondences are
overseen by OpenSSL/Apache HTTP Server/mod_ssl on the Supervisor/Worker side,
and libcurl, utilizing the NSS library for SSL, on the Collector side.The FortiSIEM
Manager/Workers utilize RSA testament with 2048 bits as default. You can control
the correct figures utilized for correspondences between virtual machines by altering
the SSLCipherSuite section in the file /and so orth/httpd/conf.d/ssl.conf on FortiSIEM
Supervisors and Specialists.
How FortiSIEM can be useful in the future

FortiSIEM is a tool that many cybersecurity experts agree that its a very usefull tool
to hack into the future cyber security market. FortiSIEM has a feature of intelligently
identifying devices. This is a key feature since the future technology mainly targets
the IoT (Internet of Things) where almost everything done will be done by devices in
the homes, offices, manufacturing and many more sectors (Hils, Young and
D'Hoinne, 2015). FortiSIEM contains a very quick and intelligent discovery engine
which is able to automatically crawl into an IT infrastructure and be in a position to
identify network nodes, servers and an in depth scrutiny of all application programs
that utilize the network. Users are required to provide the correct credentials of all
devices, the starting router IP to enable easier and faster discovery and also provide
discovery the IP address ranges. With FortiSIEM tool, much will be achieved since a
wide array of information will in future be recognized even adding to hardware
information, licences, serial codes, programs and services running, programs installed
in systems and network devices configurations. The discovered devices by FortiSIEM
are automatically categorized into detailed functional groups, such as
Routers/Switches, Firewalls, and Network IPS, and this information is maintained
within an integrated configuration management database (CMDB). Some special
relationships are also discovered, for example WLAN Access Points to WLAN
Controllers, VMware guests to physical hosts, etc. The CMDB is kept up to date
through user-defined scheduled discoveries and FortiSIEM listening to changes as
part of performance monitoring (Bhattacharya and Rao, 2018). FortiSIEM uses a
unified event-based framework to analyze all data including logs, performance
to hack into the future cyber security market. FortiSIEM has a feature of intelligently
identifying devices. This is a key feature since the future technology mainly targets
the IoT (Internet of Things) where almost everything done will be done by devices in
the homes, offices, manufacturing and many more sectors (Hils, Young and
D'Hoinne, 2015). FortiSIEM contains a very quick and intelligent discovery engine
which is able to automatically crawl into an IT infrastructure and be in a position to
identify network nodes, servers and an in depth scrutiny of all application programs
that utilize the network. Users are required to provide the correct credentials of all
devices, the starting router IP to enable easier and faster discovery and also provide
discovery the IP address ranges. With FortiSIEM tool, much will be achieved since a
wide array of information will in future be recognized even adding to hardware
information, licences, serial codes, programs and services running, programs installed
in systems and network devices configurations. The discovered devices by FortiSIEM
are automatically categorized into detailed functional groups, such as
Routers/Switches, Firewalls, and Network IPS, and this information is maintained
within an integrated configuration management database (CMDB). Some special
relationships are also discovered, for example WLAN Access Points to WLAN
Controllers, VMware guests to physical hosts, etc. The CMDB is kept up to date
through user-defined scheduled discoveries and FortiSIEM listening to changes as
part of performance monitoring (Bhattacharya and Rao, 2018). FortiSIEM uses a
unified event-based framework to analyze all data including logs, performance
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




