Networking : Three Functions of the Internet Layer
VerifiedAdded on 2022/09/11
|5
|1063
|24
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
RUNNING HEAD: NETWORKING 0
Networking
Report
Student name
Networking
Report
Student name
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
NETWORKING 1
A-1
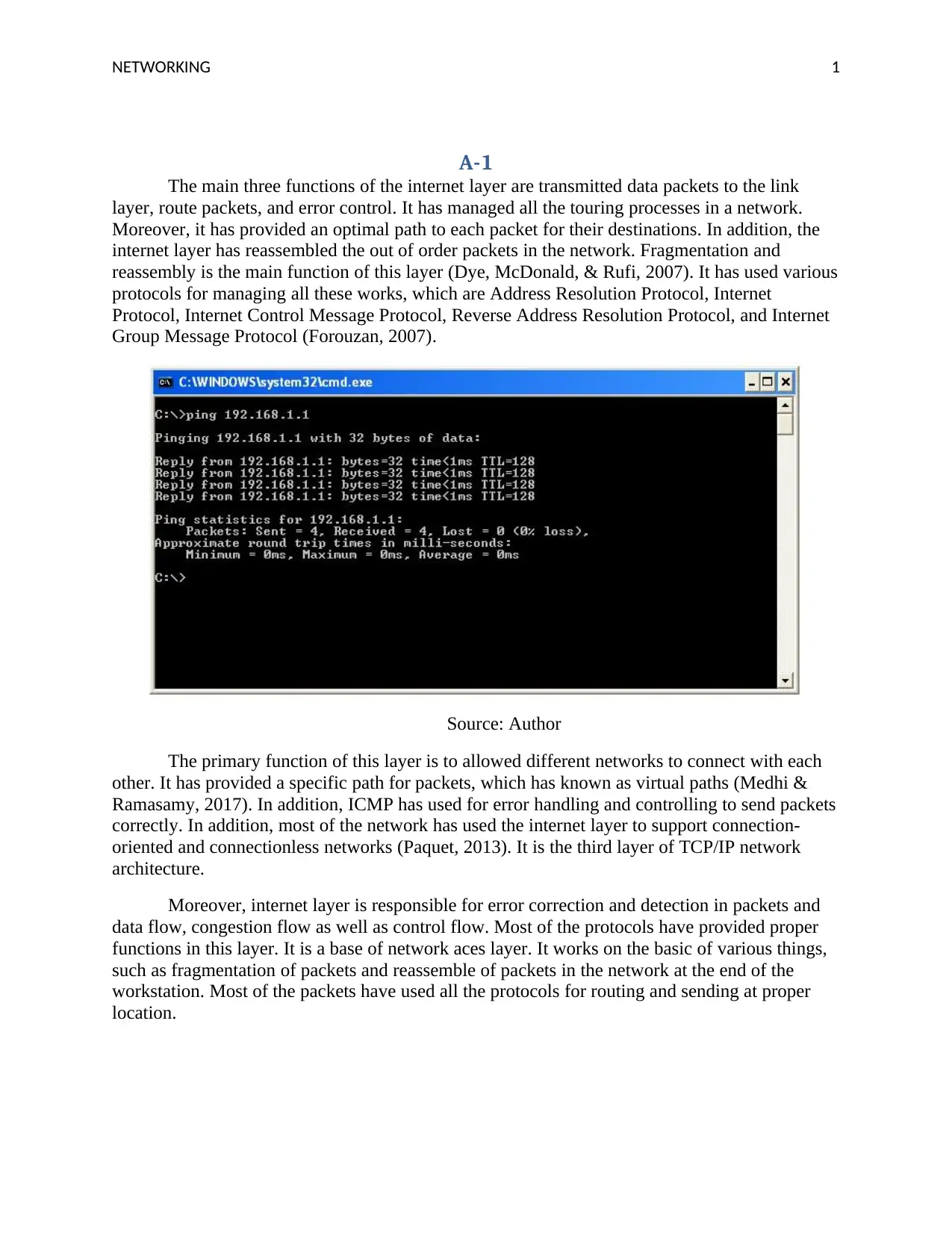
The main three functions of the internet layer are transmitted data packets to the link
layer, route packets, and error control. It has managed all the touring processes in a network.
Moreover, it has provided an optimal path to each packet for their destinations. In addition, the
internet layer has reassembled the out of order packets in the network. Fragmentation and
reassembly is the main function of this layer (Dye, McDonald, & Rufi, 2007). It has used various
protocols for managing all these works, which are Address Resolution Protocol, Internet
Protocol, Internet Control Message Protocol, Reverse Address Resolution Protocol, and Internet
Group Message Protocol (Forouzan, 2007).
Source: Author
The primary function of this layer is to allowed different networks to connect with each
other. It has provided a specific path for packets, which has known as virtual paths (Medhi &
Ramasamy, 2017). In addition, ICMP has used for error handling and controlling to send packets
correctly. In addition, most of the network has used the internet layer to support connection-
oriented and connectionless networks (Paquet, 2013). It is the third layer of TCP/IP network
architecture.
Moreover, internet layer is responsible for error correction and detection in packets and
data flow, congestion flow as well as control flow. Most of the protocols have provided proper
functions in this layer. It is a base of network aces layer. It works on the basic of various things,
such as fragmentation of packets and reassemble of packets in the network at the end of the
workstation. Most of the packets have used all the protocols for routing and sending at proper
location.
A-1
The main three functions of the internet layer are transmitted data packets to the link
layer, route packets, and error control. It has managed all the touring processes in a network.
Moreover, it has provided an optimal path to each packet for their destinations. In addition, the
internet layer has reassembled the out of order packets in the network. Fragmentation and
reassembly is the main function of this layer (Dye, McDonald, & Rufi, 2007). It has used various
protocols for managing all these works, which are Address Resolution Protocol, Internet
Protocol, Internet Control Message Protocol, Reverse Address Resolution Protocol, and Internet
Group Message Protocol (Forouzan, 2007).
Source: Author
The primary function of this layer is to allowed different networks to connect with each
other. It has provided a specific path for packets, which has known as virtual paths (Medhi &
Ramasamy, 2017). In addition, ICMP has used for error handling and controlling to send packets
correctly. In addition, most of the network has used the internet layer to support connection-
oriented and connectionless networks (Paquet, 2013). It is the third layer of TCP/IP network
architecture.
Moreover, internet layer is responsible for error correction and detection in packets and
data flow, congestion flow as well as control flow. Most of the protocols have provided proper
functions in this layer. It is a base of network aces layer. It works on the basic of various things,
such as fragmentation of packets and reassemble of packets in the network at the end of the
workstation. Most of the packets have used all the protocols for routing and sending at proper
location.

NETWORKING 2
A-2
Header Length field
This field has used for the identification of length of the IP header. It is a four-bit field. It
is known as internet Header Length (IHL) in the network. The minimum value of this field is 20
bytes and the maximum value is 60 bytes, which has generated after the addition of the 32 bits. It
has shown a total length of the packet that travels in the network (Sunshine, 2013). IPv4 has used
this field to identify the size of the packet. It has used for transmitting of packet by the internet
layer. In addition, internet layer has decided about flow control and congestion control based on
the size of the packet as well (Rouse, 2008).
Identification field
The identification field has used for providing an identity to each segment, which has
related to the packet. It is a 16-bit identification number to identify which IP packet they belong
to. It has used in the condition of fragmentation of a packet in different fragments (Tanenbaum,
2014). There are various segments of a packet. Thus, it is a conflict between differ segments.
Thus, identification field has used for the proper communication in the network.
A-3
227.12.14.87
It is a class D address, which has used for reserved for multicast groups. In this class, all
the packets have sent to all the users. It is not used for specific purposes. It does not have any
subnet mask. In addition, it has used for the particular situation of multicast. This address has
used for the multicasting applications, such as wireless networking and cable connection. This
class has reserved for the particular work, which has designed for particular works (Guru99,
2019).
14.23.120.8
It is a class an address, which has used for creating 16 million hosts in a single network,
which has used for the large scale of organization. The default subnet mask of this network is
255.0.0.0. Class A addresses have used for the large network in which a number of hosts are
more. This address has used for the large number of hosts in a single network. This class has
reserved for big organization, as they have number of hosts (Mitchell, 2019).
A-2
Header Length field
This field has used for the identification of length of the IP header. It is a four-bit field. It
is known as internet Header Length (IHL) in the network. The minimum value of this field is 20
bytes and the maximum value is 60 bytes, which has generated after the addition of the 32 bits. It
has shown a total length of the packet that travels in the network (Sunshine, 2013). IPv4 has used
this field to identify the size of the packet. It has used for transmitting of packet by the internet
layer. In addition, internet layer has decided about flow control and congestion control based on
the size of the packet as well (Rouse, 2008).
Identification field
The identification field has used for providing an identity to each segment, which has
related to the packet. It is a 16-bit identification number to identify which IP packet they belong
to. It has used in the condition of fragmentation of a packet in different fragments (Tanenbaum,
2014). There are various segments of a packet. Thus, it is a conflict between differ segments.
Thus, identification field has used for the proper communication in the network.
A-3
227.12.14.87
It is a class D address, which has used for reserved for multicast groups. In this class, all
the packets have sent to all the users. It is not used for specific purposes. It does not have any
subnet mask. In addition, it has used for the particular situation of multicast. This address has
used for the multicasting applications, such as wireless networking and cable connection. This
class has reserved for the particular work, which has designed for particular works (Guru99,
2019).
14.23.120.8
It is a class an address, which has used for creating 16 million hosts in a single network,
which has used for the large scale of organization. The default subnet mask of this network is
255.0.0.0. Class A addresses have used for the large network in which a number of hosts are
more. This address has used for the large number of hosts in a single network. This class has
reserved for big organization, as they have number of hosts (Mitchell, 2019).
NETWORKING 3
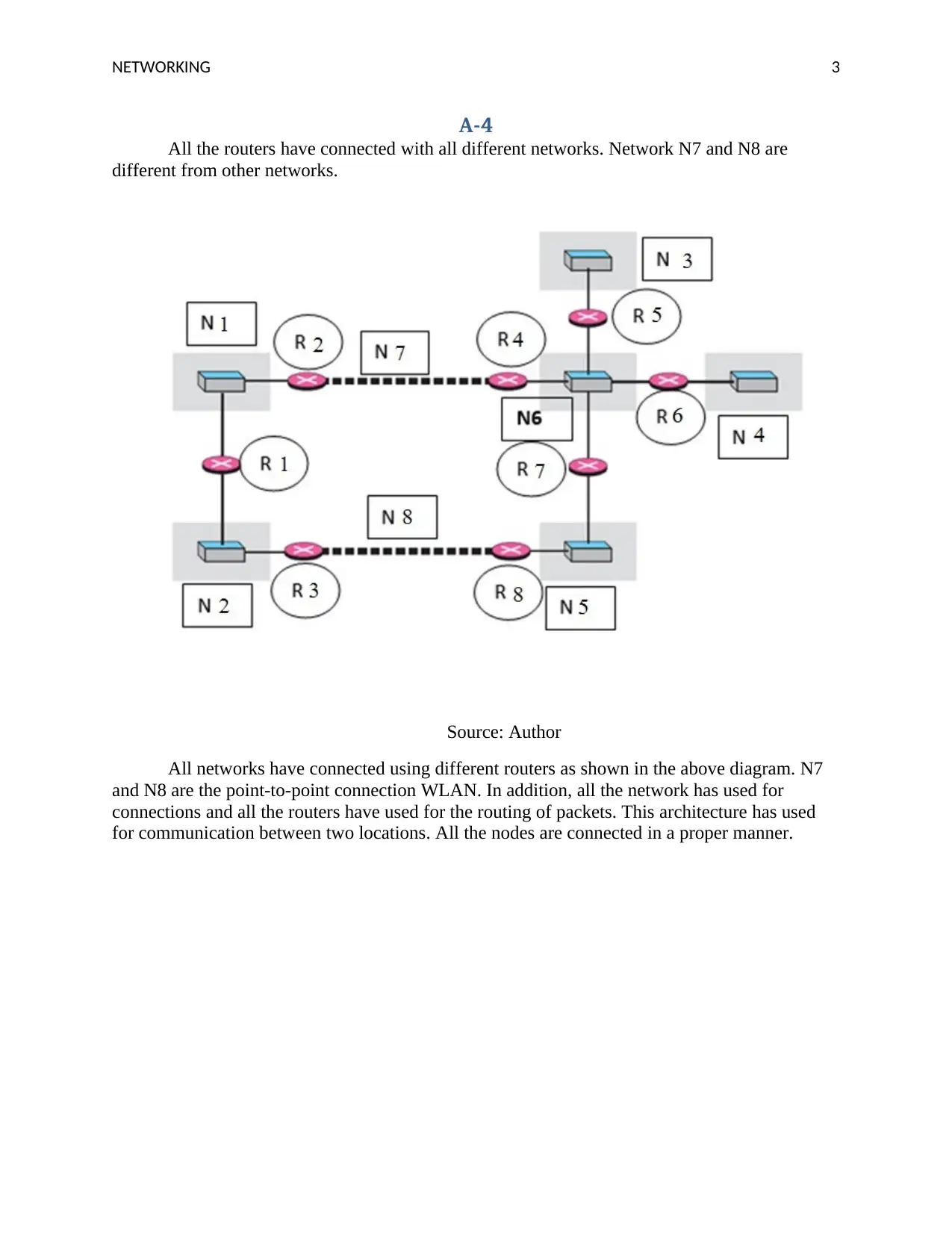
A-4
All the routers have connected with all different networks. Network N7 and N8 are
different from other networks.
Source: Author
All networks have connected using different routers as shown in the above diagram. N7
and N8 are the point-to-point connection WLAN. In addition, all the network has used for
connections and all the routers have used for the routing of packets. This architecture has used
for communication between two locations. All the nodes are connected in a proper manner.
A-4
All the routers have connected with all different networks. Network N7 and N8 are
different from other networks.
Source: Author
All networks have connected using different routers as shown in the above diagram. N7
and N8 are the point-to-point connection WLAN. In addition, all the network has used for
connections and all the routers have used for the routing of packets. This architecture has used
for communication between two locations. All the nodes are connected in a proper manner.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

NETWORKING 4
References
Dye, M., McDonald, R., & Rufi, A. (2007). Network Fundamentals, CCNA Exploration
Companion Guide. Indianapolis, USA: Cisco press.
Forouzan, A. (2007). Data communications & networking (8th ed.). New Delhi: Tata McGraw-
Hill Education.
Guru99. (2019). TCP/IP Model: What is TCP IP Stack? Protocol Layers, Advantages . Retrieved
from www.guru99.com: https://www.guru99.com/tcp-ip-model.html
Medhi, D., & Ramasamy, K. (2017). Network routing: algorithms, protocols, and architectures.
Morgan Kaufmann.
Mitchell, B. (2019, November 12). Understanding Transmission Control Protocol/Internet
Protocol (TCP/IP) . Retrieved from https://www.lifewire.com:
https://www.lifewire.com/transmission-control-protocol-and-internet-protocol-816255
Paquet, C. (2013). Network Security Concepts and Policies. Retrieved november 2, 2019, from
http://www.ciscopress.com/articles/article.asp?p=1998559&seqNum=3
Rouse, M. (2008). TCP/IP (Transmission Control Protocol/Internet Protocol) . Retrieved from
https://searchnetworking.techtarget.com:
https://searchnetworking.techtarget.com/definition/TCP-IP
Sunshine, C. (2013). Computer network architectures and protocols. New Jersy: Springer
Science & Business Media.
Tanenbaum, A. S. (2014). Computer networks. Harlow, Essex: Pearson.
References
Dye, M., McDonald, R., & Rufi, A. (2007). Network Fundamentals, CCNA Exploration
Companion Guide. Indianapolis, USA: Cisco press.
Forouzan, A. (2007). Data communications & networking (8th ed.). New Delhi: Tata McGraw-
Hill Education.
Guru99. (2019). TCP/IP Model: What is TCP IP Stack? Protocol Layers, Advantages . Retrieved
from www.guru99.com: https://www.guru99.com/tcp-ip-model.html
Medhi, D., & Ramasamy, K. (2017). Network routing: algorithms, protocols, and architectures.
Morgan Kaufmann.
Mitchell, B. (2019, November 12). Understanding Transmission Control Protocol/Internet
Protocol (TCP/IP) . Retrieved from https://www.lifewire.com:
https://www.lifewire.com/transmission-control-protocol-and-internet-protocol-816255
Paquet, C. (2013). Network Security Concepts and Policies. Retrieved november 2, 2019, from
http://www.ciscopress.com/articles/article.asp?p=1998559&seqNum=3
Rouse, M. (2008). TCP/IP (Transmission Control Protocol/Internet Protocol) . Retrieved from
https://searchnetworking.techtarget.com:
https://searchnetworking.techtarget.com/definition/TCP-IP
Sunshine, C. (2013). Computer network architectures and protocols. New Jersy: Springer
Science & Business Media.
Tanenbaum, A. S. (2014). Computer networks. Harlow, Essex: Pearson.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





