DTGOV Hybrid Cloud: Risks, Security, and Management Analysis
VerifiedAdded on 2023/01/23
|14
|3889
|22
Report
AI Summary
This report analyzes the implementation of a hybrid cloud strategy, focusing on the case of DTGOV. It explores the cloud computing architectures employed, including front-end and back-end architectures, and discusses the advantages and disadvantages of front-end architecture. The report identifies and assesses the risks associated with hybrid cloud and microservices, such as lack of encryption, inadequate security assessment, poor compliance, weak security management, poor data redundancy, denial of service, and poor intellectual property protection, providing detailed mitigation factors for each risk. It also outlines general information security steps and controls recommended for securing a hybrid cloud environment, including continuous risk assessment updates, review of security tools, vulnerability scanning, and the importance of data security. The report emphasizes the need for robust security measures to protect data and ensure the effective and secure implementation of a hybrid cloud strategy.

Running head: HYBRID CLOUD
HYBRID CLOUD
Name of Student
Name of University
Author’s Note
HYBRID CLOUD
Name of Student
Name of University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1HYBRID CLOUD
Answer 1
1. The cloud computing architectures that would be employed to assist includes
front end architecture and back end architecture. The back end architecture
would help the organization in providing security of information for the users
of cloud with the mechanism of traffic control. The server provides
middleware that helps in connecting devices and hence communicates with
one another (Srinivasan, Quadir & Vijayakumar, 2015). The back end
architecture includes a code that runs on a particular server, which receives
requests from various clients and hence contains a particular logic in order to
send the proper information back to the a appropriate client. The aback end
architecture would help the organization in storing data because it involves a
particular database that would persistently store the organizational data for
their application (Coyne, Dain & Forestier, 2018). Back end architecture
requires technology for processing the incoming request and hence generate
and send response to the clients. This would include three parts namely the
server, this receives request from the client, the application is another
component of the back end architecture, and this application runs on the server
which listens for requests, retrieves data from database and then sends a
particular response (Amin, Singh & Sethi, 2015). The next component is
database, which could be used in order to organize and persist data. The cloud
infrastructure that would be used by the organization would help the in
working with various applications (Garg, 2016). Front end is usually a site
which is visible to the customer, user or cloud. Front end architecture includes
the user interface along with the computer system of the client which is used
Answer 1
1. The cloud computing architectures that would be employed to assist includes
front end architecture and back end architecture. The back end architecture
would help the organization in providing security of information for the users
of cloud with the mechanism of traffic control. The server provides
middleware that helps in connecting devices and hence communicates with
one another (Srinivasan, Quadir & Vijayakumar, 2015). The back end
architecture includes a code that runs on a particular server, which receives
requests from various clients and hence contains a particular logic in order to
send the proper information back to the a appropriate client. The aback end
architecture would help the organization in storing data because it involves a
particular database that would persistently store the organizational data for
their application (Coyne, Dain & Forestier, 2018). Back end architecture
requires technology for processing the incoming request and hence generate
and send response to the clients. This would include three parts namely the
server, this receives request from the client, the application is another
component of the back end architecture, and this application runs on the server
which listens for requests, retrieves data from database and then sends a
particular response (Amin, Singh & Sethi, 2015). The next component is
database, which could be used in order to organize and persist data. The cloud
infrastructure that would be used by the organization would help the in
working with various applications (Garg, 2016). Front end is usually a site
which is visible to the customer, user or cloud. Front end architecture includes
the user interface along with the computer system of the client which is used

2HYBRID CLOUD
for the purpose of accessing the system of cloud (Rao, Naveena & David,
2015). Back end cloud computing architecture includes numerous servers, data
storage systems, programs, virtual machines and computers which constitute
the services of cloud computing. The back end side is responsible for giving
various security mechanisms, protocols and traffic control which connects
networked computer for the purpose of communication. Front end architecture
that could be implemented by the organization would consist of a collection of
processes and tools that would aim in improving as well as creating more
efficient as well as sustainable workflow. Front end architecture can be
implemented by the organization for various purposes like responsive web
design, scalable or modular CSS, UI frameworks, living style guides,
accessibility animation, progressive enhancement ad front end performance.
Application development can also be carried out with the usage of front end
architecture, this can be done with the use of JavaScript frameworks,
JavaScript preprocessors, code quality, testing and process automation. Front
end architecture can be used for numerous operations including building tools,
deployment, speed, monitoring various errors, logs as well as stability.
2. A particular visible interface that could be accessed on desktop or mobile
devices, the front end platform is considered as a component which can be
seen by various users as well as clients. The front end platform aims in
interacting with cloud data storage networks as well as serves through a
particular application such as middleware or a specific virtual session (Coyne,
Dain & Forestier, 2018). Back end platform, comprises of millions of data
storage systems and servers along with software that are accessed in a secured
manner over a particular public network through private connections. In order
for the purpose of accessing the system of cloud (Rao, Naveena & David,
2015). Back end cloud computing architecture includes numerous servers, data
storage systems, programs, virtual machines and computers which constitute
the services of cloud computing. The back end side is responsible for giving
various security mechanisms, protocols and traffic control which connects
networked computer for the purpose of communication. Front end architecture
that could be implemented by the organization would consist of a collection of
processes and tools that would aim in improving as well as creating more
efficient as well as sustainable workflow. Front end architecture can be
implemented by the organization for various purposes like responsive web
design, scalable or modular CSS, UI frameworks, living style guides,
accessibility animation, progressive enhancement ad front end performance.
Application development can also be carried out with the usage of front end
architecture, this can be done with the use of JavaScript frameworks,
JavaScript preprocessors, code quality, testing and process automation. Front
end architecture can be used for numerous operations including building tools,
deployment, speed, monitoring various errors, logs as well as stability.
2. A particular visible interface that could be accessed on desktop or mobile
devices, the front end platform is considered as a component which can be
seen by various users as well as clients. The front end platform aims in
interacting with cloud data storage networks as well as serves through a
particular application such as middleware or a specific virtual session (Coyne,
Dain & Forestier, 2018). Back end platform, comprises of millions of data
storage systems and servers along with software that are accessed in a secured
manner over a particular public network through private connections. In order
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3HYBRID CLOUD
to put the magnitude of back end platform in perspective, AWS of Amazon as
well as Microsoft together do not have more servers than 4 million in
hundreds of data centers in the world. The professional who works in front end
implementation is the one who would be placed between the engineers and
designers, these professionals would be working on design implementation
and are able to work along with the team of design for creating various user
interfaces which reflect the client’s requirements as well as the intent of the
design team. The professional tends to understand regarding the frameworks
that are used by the development team that works in the production application
for recommending implementation on their work in the present flavor of the
framework of the organization.
The front end architecture has numerous advantages including the fact that the
organization would be able to develop a huge number of presentation layers for a
different user, customer as well as supply channels. The presentation layers would
share similar services, this would ensure the fact that consistent interactions regardless
of the channels. Every presentation layer needs one sign on for accessing all the
needed functionality. The drawbacks include the fact that all the functionality should
be offered with the help of an API that is service based, the business as well as data
logic should be separate from the presentation layer. The transaction or a commit
model should act as a particular resource manager in the multiphase commit
processing that has been chosen. Some legacy as well as presently available
CRM/ERP packages meet the criteria so the organization must develop a particular
custom application. The presentation layer of the packaged application is not usually
stable, this might lead to various difficulties in supporting, lengthy time for
implementation and many more activities.
to put the magnitude of back end platform in perspective, AWS of Amazon as
well as Microsoft together do not have more servers than 4 million in
hundreds of data centers in the world. The professional who works in front end
implementation is the one who would be placed between the engineers and
designers, these professionals would be working on design implementation
and are able to work along with the team of design for creating various user
interfaces which reflect the client’s requirements as well as the intent of the
design team. The professional tends to understand regarding the frameworks
that are used by the development team that works in the production application
for recommending implementation on their work in the present flavor of the
framework of the organization.
The front end architecture has numerous advantages including the fact that the
organization would be able to develop a huge number of presentation layers for a
different user, customer as well as supply channels. The presentation layers would
share similar services, this would ensure the fact that consistent interactions regardless
of the channels. Every presentation layer needs one sign on for accessing all the
needed functionality. The drawbacks include the fact that all the functionality should
be offered with the help of an API that is service based, the business as well as data
logic should be separate from the presentation layer. The transaction or a commit
model should act as a particular resource manager in the multiphase commit
processing that has been chosen. Some legacy as well as presently available
CRM/ERP packages meet the criteria so the organization must develop a particular
custom application. The presentation layer of the packaged application is not usually
stable, this might lead to various difficulties in supporting, lengthy time for
implementation and many more activities.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4HYBRID CLOUD
Answer 2
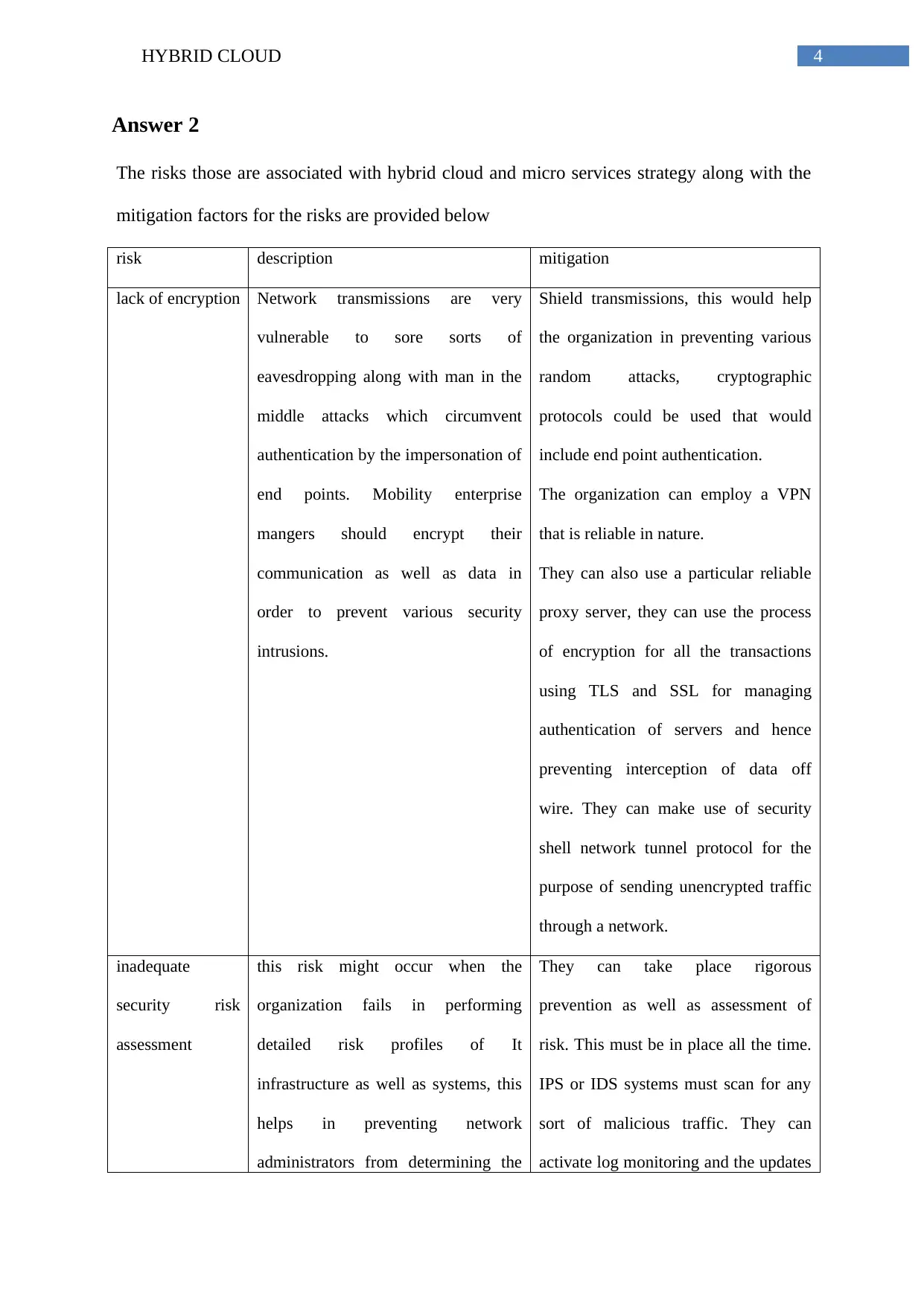
The risks those are associated with hybrid cloud and micro services strategy along with the
mitigation factors for the risks are provided below
risk description mitigation
lack of encryption Network transmissions are very
vulnerable to sore sorts of
eavesdropping along with man in the
middle attacks which circumvent
authentication by the impersonation of
end points. Mobility enterprise
mangers should encrypt their
communication as well as data in
order to prevent various security
intrusions.
Shield transmissions, this would help
the organization in preventing various
random attacks, cryptographic
protocols could be used that would
include end point authentication.
The organization can employ a VPN
that is reliable in nature.
They can also use a particular reliable
proxy server, they can use the process
of encryption for all the transactions
using TLS and SSL for managing
authentication of servers and hence
preventing interception of data off
wire. They can make use of security
shell network tunnel protocol for the
purpose of sending unencrypted traffic
through a network.
inadequate
security risk
assessment
this risk might occur when the
organization fails in performing
detailed risk profiles of It
infrastructure as well as systems, this
helps in preventing network
administrators from determining the
They can take place rigorous
prevention as well as assessment of
risk. This must be in place all the time.
IPS or IDS systems must scan for any
sort of malicious traffic. They can
activate log monitoring and the updates
Answer 2
The risks those are associated with hybrid cloud and micro services strategy along with the
mitigation factors for the risks are provided below
risk description mitigation
lack of encryption Network transmissions are very
vulnerable to sore sorts of
eavesdropping along with man in the
middle attacks which circumvent
authentication by the impersonation of
end points. Mobility enterprise
mangers should encrypt their
communication as well as data in
order to prevent various security
intrusions.
Shield transmissions, this would help
the organization in preventing various
random attacks, cryptographic
protocols could be used that would
include end point authentication.
The organization can employ a VPN
that is reliable in nature.
They can also use a particular reliable
proxy server, they can use the process
of encryption for all the transactions
using TLS and SSL for managing
authentication of servers and hence
preventing interception of data off
wire. They can make use of security
shell network tunnel protocol for the
purpose of sending unencrypted traffic
through a network.
inadequate
security risk
assessment
this risk might occur when the
organization fails in performing
detailed risk profiles of It
infrastructure as well as systems, this
helps in preventing network
administrators from determining the
They can take place rigorous
prevention as well as assessment of
risk. This must be in place all the time.
IPS or IDS systems must scan for any
sort of malicious traffic. They can
activate log monitoring and the updates
5HYBRID CLOUD
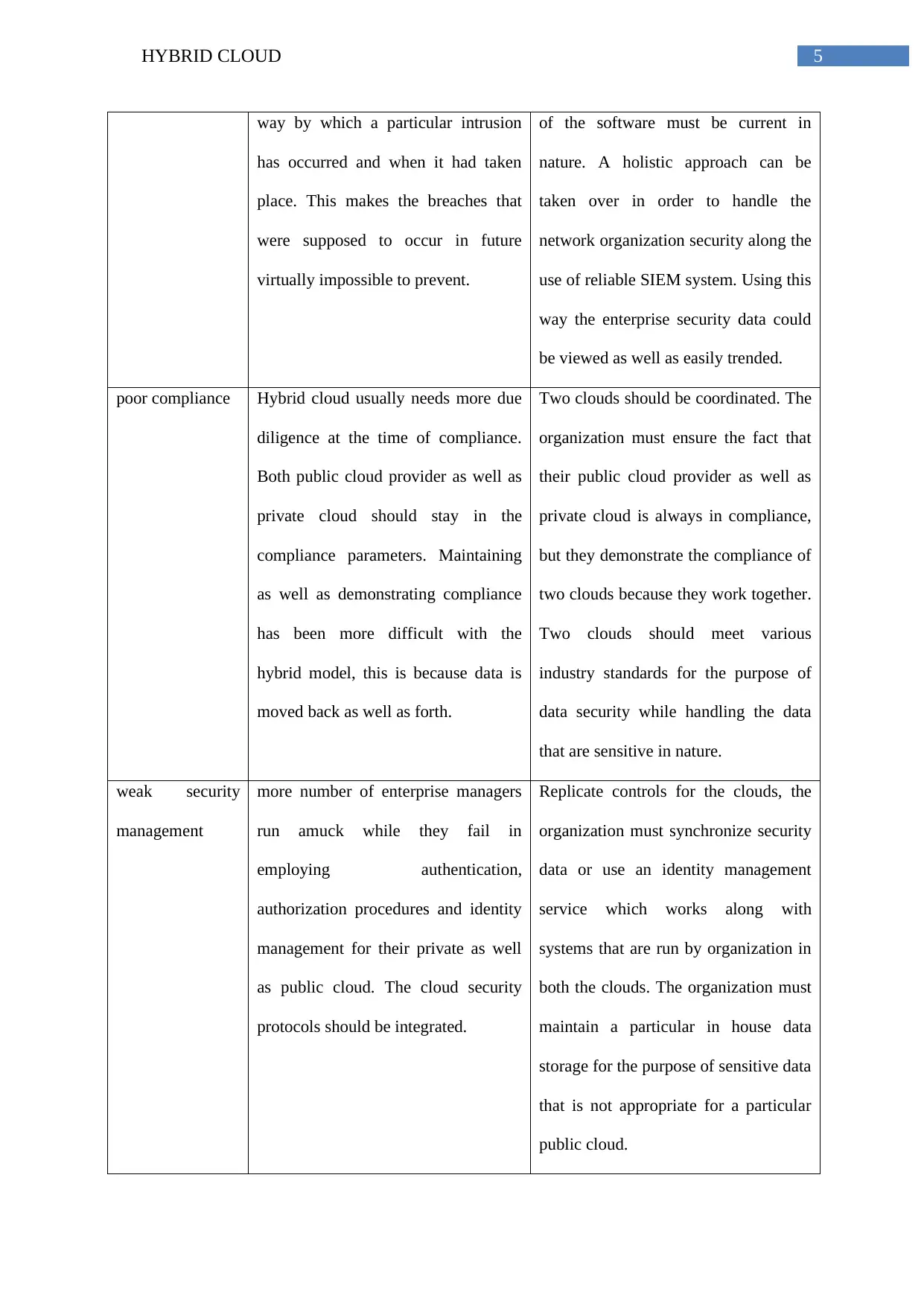
way by which a particular intrusion
has occurred and when it had taken
place. This makes the breaches that
were supposed to occur in future
virtually impossible to prevent.
of the software must be current in
nature. A holistic approach can be
taken over in order to handle the
network organization security along the
use of reliable SIEM system. Using this
way the enterprise security data could
be viewed as well as easily trended.
poor compliance Hybrid cloud usually needs more due
diligence at the time of compliance.
Both public cloud provider as well as
private cloud should stay in the
compliance parameters. Maintaining
as well as demonstrating compliance
has been more difficult with the
hybrid model, this is because data is
moved back as well as forth.
Two clouds should be coordinated. The
organization must ensure the fact that
their public cloud provider as well as
private cloud is always in compliance,
but they demonstrate the compliance of
two clouds because they work together.
Two clouds should meet various
industry standards for the purpose of
data security while handling the data
that are sensitive in nature.
weak security
management
more number of enterprise managers
run amuck while they fail in
employing authentication,
authorization procedures and identity
management for their private as well
as public cloud. The cloud security
protocols should be integrated.
Replicate controls for the clouds, the
organization must synchronize security
data or use an identity management
service which works along with
systems that are run by organization in
both the clouds. The organization must
maintain a particular in house data
storage for the purpose of sensitive data
that is not appropriate for a particular
public cloud.
way by which a particular intrusion
has occurred and when it had taken
place. This makes the breaches that
were supposed to occur in future
virtually impossible to prevent.
of the software must be current in
nature. A holistic approach can be
taken over in order to handle the
network organization security along the
use of reliable SIEM system. Using this
way the enterprise security data could
be viewed as well as easily trended.
poor compliance Hybrid cloud usually needs more due
diligence at the time of compliance.
Both public cloud provider as well as
private cloud should stay in the
compliance parameters. Maintaining
as well as demonstrating compliance
has been more difficult with the
hybrid model, this is because data is
moved back as well as forth.
Two clouds should be coordinated. The
organization must ensure the fact that
their public cloud provider as well as
private cloud is always in compliance,
but they demonstrate the compliance of
two clouds because they work together.
Two clouds should meet various
industry standards for the purpose of
data security while handling the data
that are sensitive in nature.
weak security
management
more number of enterprise managers
run amuck while they fail in
employing authentication,
authorization procedures and identity
management for their private as well
as public cloud. The cloud security
protocols should be integrated.
Replicate controls for the clouds, the
organization must synchronize security
data or use an identity management
service which works along with
systems that are run by organization in
both the clouds. The organization must
maintain a particular in house data
storage for the purpose of sensitive data
that is not appropriate for a particular
public cloud.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6HYBRID CLOUD
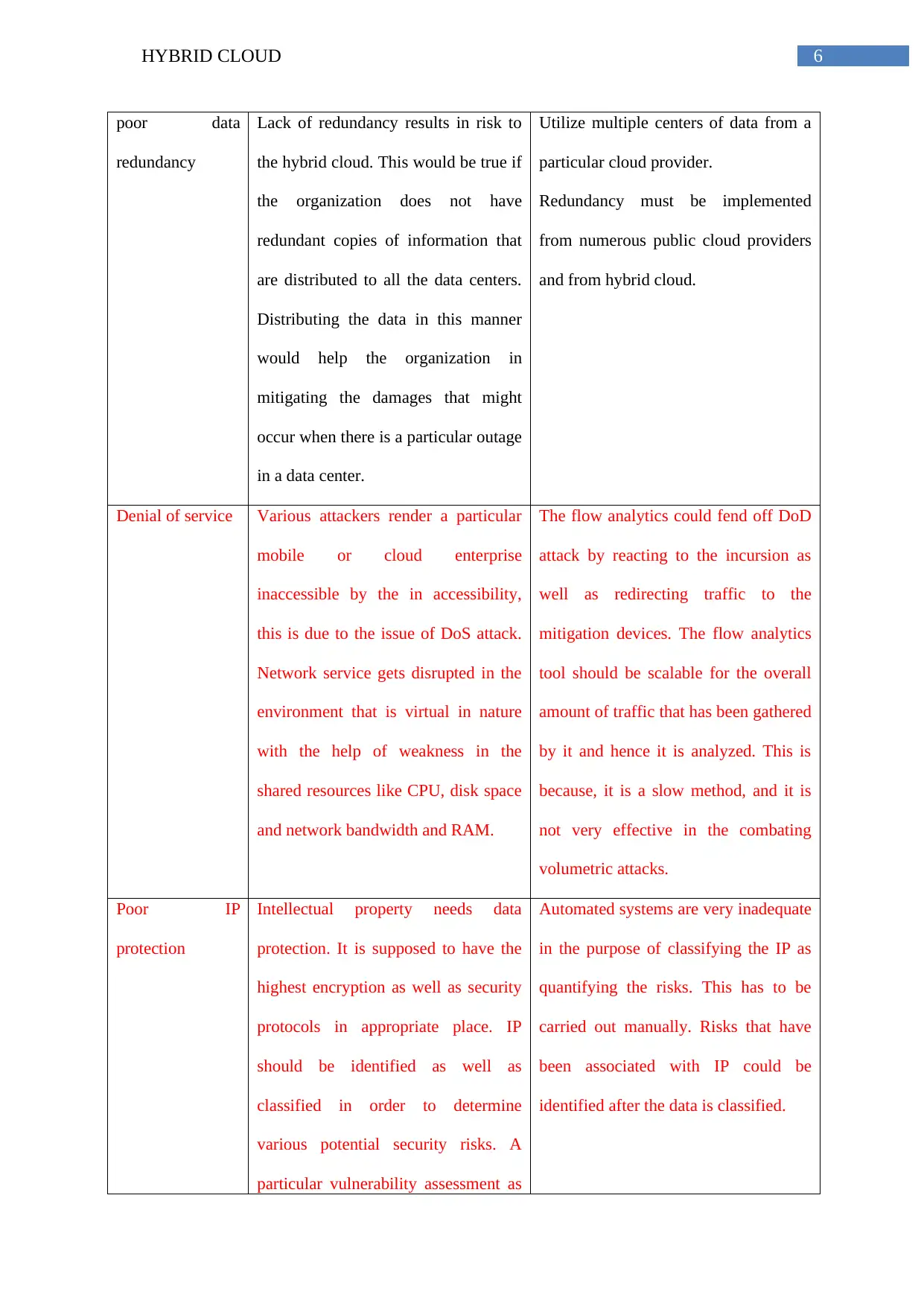
poor data
redundancy
Lack of redundancy results in risk to
the hybrid cloud. This would be true if
the organization does not have
redundant copies of information that
are distributed to all the data centers.
Distributing the data in this manner
would help the organization in
mitigating the damages that might
occur when there is a particular outage
in a data center.
Utilize multiple centers of data from a
particular cloud provider.
Redundancy must be implemented
from numerous public cloud providers
and from hybrid cloud.
Denial of service Various attackers render a particular
mobile or cloud enterprise
inaccessible by the in accessibility,
this is due to the issue of DoS attack.
Network service gets disrupted in the
environment that is virtual in nature
with the help of weakness in the
shared resources like CPU, disk space
and network bandwidth and RAM.
The flow analytics could fend off DoD
attack by reacting to the incursion as
well as redirecting traffic to the
mitigation devices. The flow analytics
tool should be scalable for the overall
amount of traffic that has been gathered
by it and hence it is analyzed. This is
because, it is a slow method, and it is
not very effective in the combating
volumetric attacks.
Poor IP
protection
Intellectual property needs data
protection. It is supposed to have the
highest encryption as well as security
protocols in appropriate place. IP
should be identified as well as
classified in order to determine
various potential security risks. A
particular vulnerability assessment as
Automated systems are very inadequate
in the purpose of classifying the IP as
quantifying the risks. This has to be
carried out manually. Risks that have
been associated with IP could be
identified after the data is classified.
poor data
redundancy
Lack of redundancy results in risk to
the hybrid cloud. This would be true if
the organization does not have
redundant copies of information that
are distributed to all the data centers.
Distributing the data in this manner
would help the organization in
mitigating the damages that might
occur when there is a particular outage
in a data center.
Utilize multiple centers of data from a
particular cloud provider.
Redundancy must be implemented
from numerous public cloud providers
and from hybrid cloud.
Denial of service Various attackers render a particular
mobile or cloud enterprise
inaccessible by the in accessibility,
this is due to the issue of DoS attack.
Network service gets disrupted in the
environment that is virtual in nature
with the help of weakness in the
shared resources like CPU, disk space
and network bandwidth and RAM.
The flow analytics could fend off DoD
attack by reacting to the incursion as
well as redirecting traffic to the
mitigation devices. The flow analytics
tool should be scalable for the overall
amount of traffic that has been gathered
by it and hence it is analyzed. This is
because, it is a slow method, and it is
not very effective in the combating
volumetric attacks.
Poor IP
protection
Intellectual property needs data
protection. It is supposed to have the
highest encryption as well as security
protocols in appropriate place. IP
should be identified as well as
classified in order to determine
various potential security risks. A
particular vulnerability assessment as
Automated systems are very inadequate
in the purpose of classifying the IP as
quantifying the risks. This has to be
carried out manually. Risks that have
been associated with IP could be
identified after the data is classified.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7HYBRID CLOUD
well as appropriate encryption is
required.
Table 1: risks that is associated with hybrid cloud and micro services strategy
(Source: Amin, Singh & Sethi, 2015)
Answer 3
Security of information is a vital step that must be carried out for the purpose of
implementing the hybrid cloud in an effective manner; the security would help people as
well as organization in keeping their data secured from unsafe hands (Sen, 2015). The
general information security steps and controls that would be recommended to the board for
the security of Hybrid cloud are as follows
Continuously update the risk assessment along with practices of analysis governance.
Using this, DTGOV would be able to review the security controls, compliance status and
capabilities of the cloud providers along with the tools as well as platforms for orchestration
and internal development (Garg, 2016). The organization must review various security tools
as well as controls and monitoring tools in the premise as well as the cloud. This would
provide the security teams with clarity regarding what controls are presently in place and
how they need to modify and at last what are the issues that are pressing the most.
The organization might contribute in configuring items for the purpose of developing
as well as maintaining for cloud based systems such as patch level and OS version, groups as
well as local users, permissions on the key file and various services that belong to hardened
network.
The organization should scan as well as access the vulnerabilities in a continuous
manner, throughout the instances of the cloud lifecycles with the use of some methods
(Garcia, 2018). The methods include relying on the APIs for avoiding various intrusive scans
well as appropriate encryption is
required.
Table 1: risks that is associated with hybrid cloud and micro services strategy
(Source: Amin, Singh & Sethi, 2015)
Answer 3
Security of information is a vital step that must be carried out for the purpose of
implementing the hybrid cloud in an effective manner; the security would help people as
well as organization in keeping their data secured from unsafe hands (Sen, 2015). The
general information security steps and controls that would be recommended to the board for
the security of Hybrid cloud are as follows
Continuously update the risk assessment along with practices of analysis governance.
Using this, DTGOV would be able to review the security controls, compliance status and
capabilities of the cloud providers along with the tools as well as platforms for orchestration
and internal development (Garg, 2016). The organization must review various security tools
as well as controls and monitoring tools in the premise as well as the cloud. This would
provide the security teams with clarity regarding what controls are presently in place and
how they need to modify and at last what are the issues that are pressing the most.
The organization might contribute in configuring items for the purpose of developing
as well as maintaining for cloud based systems such as patch level and OS version, groups as
well as local users, permissions on the key file and various services that belong to hardened
network.
The organization should scan as well as access the vulnerabilities in a continuous
manner, throughout the instances of the cloud lifecycles with the use of some methods
(Garcia, 2018). The methods include relying on the APIs for avoiding various intrusive scans

8HYBRID CLOUD
on ad hoc and scheduled basis, one more method includes relying on various agents who are
host based agents and are allowed to scan their virtual machines continuously along with
reporting any vulnerability that has to be noted (Shyshkina, 2018). In case the organization is
looking at the workloads of the cloud as enormously ever changing, dynamic environments
that they need to bake in the management strategy of vulnerability from the provided
definition of the environment in an automated way.
The organization must monitor various complex as well as virtualized IaaS
environments that make use of a host based tool where the agent reports to a particular server
of management, after that it sends logs as well as events to a particular central collection
platform (Elzamly, Hussin & Abu Naser, 2017). Logs as well as events that have been
generated by applications and services in the environment of cloud could include various
unusually logins or login failure of the users, huge amount of data import or exports from
and to the cloud environment which were not anticipated, various user activities that were
privileged, changes that were approved system images for the purpose of providing
privileges and hence identify the configuration and to logging a well as monitoring the
configuration.
Answer 4
Some recommendations on what should be included in DTGOV’s BCP as a result of
adoption of Hybrid cloud environment include the awareness of the platform, the
effectiveness of the migration tool or the deployment package of application to stay aware
regarding the target platform where the application would be deployed to (Malik, Wani &
Rashid, 2018). In numerous instances, there has been a need of movement that is
bidirectional in nature which means the infrastructure of the organization is being moved
from present environment to a particular new platform and then move back to the actual
on ad hoc and scheduled basis, one more method includes relying on various agents who are
host based agents and are allowed to scan their virtual machines continuously along with
reporting any vulnerability that has to be noted (Shyshkina, 2018). In case the organization is
looking at the workloads of the cloud as enormously ever changing, dynamic environments
that they need to bake in the management strategy of vulnerability from the provided
definition of the environment in an automated way.
The organization must monitor various complex as well as virtualized IaaS
environments that make use of a host based tool where the agent reports to a particular server
of management, after that it sends logs as well as events to a particular central collection
platform (Elzamly, Hussin & Abu Naser, 2017). Logs as well as events that have been
generated by applications and services in the environment of cloud could include various
unusually logins or login failure of the users, huge amount of data import or exports from
and to the cloud environment which were not anticipated, various user activities that were
privileged, changes that were approved system images for the purpose of providing
privileges and hence identify the configuration and to logging a well as monitoring the
configuration.
Answer 4
Some recommendations on what should be included in DTGOV’s BCP as a result of
adoption of Hybrid cloud environment include the awareness of the platform, the
effectiveness of the migration tool or the deployment package of application to stay aware
regarding the target platform where the application would be deployed to (Malik, Wani &
Rashid, 2018). In numerous instances, there has been a need of movement that is
bidirectional in nature which means the infrastructure of the organization is being moved
from present environment to a particular new platform and then move back to the actual
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9HYBRID CLOUD
platform. The basic example of this sort of requirement is in the DR scenario where
applications would continue running on present platform and would be able to leverage the
new platform in the DR scenario. One more change that has to be brought about is in the
business continuity (Chou, 2015). This change would help in avoiding any sort of potential
disruption as well as consequent downtime. There have been numerous mechanisms that
help in avoiding or reducing the downtime at the time of migration, including the blue green
migration or deployments, active or passive configurations along with graceful failover that
use rolling migrations for various components that are individual (Kirke Snyder, 2017). The
migration pattern needs to be chosen effectively on the basis of the firm and size of the
organization, this migration pattern that is chosen would drive the magnitude of the changes
that are required for the migration of applications to a different platform.
In order to address the hybrid cloud services, various new offerings or approaches
have been emerging such as cloud providers that are based n premises solution, cloud
providers that provide third party Hypervisor support and third party Hypervisor based
solutions (He & Wang, 2015). The offerings that have been enabled and help in providing
new approaches for the purpose of organizations to migrate the applications.
Answer 5
The requirements that DTGOV would need to consider for conducting remote server
administration, there are four points that belong to critical criteria and must be considered
when it comes to considering remote server administration includes reliability; this factor
includes the fact if the remote access as well as control work when the system would require
it the most (Shin & Roy, 2016). It also deals with the safety of remote access as well as
control tools; they provide safety from cyber-attack and hackers. The management of remote
access along with control tools is carried out in an effective manner
platform. The basic example of this sort of requirement is in the DR scenario where
applications would continue running on present platform and would be able to leverage the
new platform in the DR scenario. One more change that has to be brought about is in the
business continuity (Chou, 2015). This change would help in avoiding any sort of potential
disruption as well as consequent downtime. There have been numerous mechanisms that
help in avoiding or reducing the downtime at the time of migration, including the blue green
migration or deployments, active or passive configurations along with graceful failover that
use rolling migrations for various components that are individual (Kirke Snyder, 2017). The
migration pattern needs to be chosen effectively on the basis of the firm and size of the
organization, this migration pattern that is chosen would drive the magnitude of the changes
that are required for the migration of applications to a different platform.
In order to address the hybrid cloud services, various new offerings or approaches
have been emerging such as cloud providers that are based n premises solution, cloud
providers that provide third party Hypervisor support and third party Hypervisor based
solutions (He & Wang, 2015). The offerings that have been enabled and help in providing
new approaches for the purpose of organizations to migrate the applications.
Answer 5
The requirements that DTGOV would need to consider for conducting remote server
administration, there are four points that belong to critical criteria and must be considered
when it comes to considering remote server administration includes reliability; this factor
includes the fact if the remote access as well as control work when the system would require
it the most (Shin & Roy, 2016). It also deals with the safety of remote access as well as
control tools; they provide safety from cyber-attack and hackers. The management of remote
access along with control tools is carried out in an effective manner
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10HYBRID CLOUD
The requirements that DTGOV would need to consider for conducting resource
management includes planning of resources, this is considered as one of the core component
of the requirements. A particular resource plan must contain all the aspects that pertain to
every resource that are necessary for the project from the starting to the end (Dave, Meruliya
& Gajjar, 2018). It not only helps in determining the resources that are required, planning the
project is the most effective way that can be used for the purpose of organizing the proper as
well as effective usage of the resources. An effective planning of the resources must be
carried out by the organization. Maintenance of transparency is another category that must
be considered, alignment of resources and ensuring everyone has been working for attaining
a common objective in order to boost transparency along with fostering trust (Chou, 2015).
The requirements that DTGOV would need to consider for conducting SLA management
includes various metrics. These metrics include availability of service, this includes the time
for which a service is used, and this is measured by the time slot that has around 99 percent
of availability that is specified in other times. Deficit rates are also included in these metrics,
percentages or counts of errors in important deliverables are considered. The aspects that are
included in this aspect include failure in production, incomplete backups, restoring errors,
coding errors and many more.
Team forum
Question 1: Is the architecture selected by you appropriate for the organization?
Answer 1: yes, I think the architecture (back end and front end architectures) would be
perfect for the organization because they would help the organization in making their
operations effective as well as efficient in nature.
Question 2: for conducting remote server which step should be followed the most by the
organization?
The requirements that DTGOV would need to consider for conducting resource
management includes planning of resources, this is considered as one of the core component
of the requirements. A particular resource plan must contain all the aspects that pertain to
every resource that are necessary for the project from the starting to the end (Dave, Meruliya
& Gajjar, 2018). It not only helps in determining the resources that are required, planning the
project is the most effective way that can be used for the purpose of organizing the proper as
well as effective usage of the resources. An effective planning of the resources must be
carried out by the organization. Maintenance of transparency is another category that must
be considered, alignment of resources and ensuring everyone has been working for attaining
a common objective in order to boost transparency along with fostering trust (Chou, 2015).
The requirements that DTGOV would need to consider for conducting SLA management
includes various metrics. These metrics include availability of service, this includes the time
for which a service is used, and this is measured by the time slot that has around 99 percent
of availability that is specified in other times. Deficit rates are also included in these metrics,
percentages or counts of errors in important deliverables are considered. The aspects that are
included in this aspect include failure in production, incomplete backups, restoring errors,
coding errors and many more.
Team forum
Question 1: Is the architecture selected by you appropriate for the organization?
Answer 1: yes, I think the architecture (back end and front end architectures) would be
perfect for the organization because they would help the organization in making their
operations effective as well as efficient in nature.
Question 2: for conducting remote server which step should be followed the most by the
organization?

11HYBRID CLOUD
Answer 2: hybrid cloud would be helpful for DTGOV in order to store their data in an
effective manner, and micro services would allow the organization to update their operations
so that they are more useful for the organization.
Question 3: which step of control would be most useful for the organization with the usage
of the hybrid cloud?
Answer 3: the step of controlling the security might prove to be most useful for their
organization because their data would be secured in the cloud and this might create a chance
for the hackers to access these organizational data and use it fir ill purposes.
Question 4: are the information security steps as well as controls enough for the
organization?
Answer 4: the steps that are mentioned regarding the information security are sufficient for
the organization, if DTGOV follows all the steps, it would be beneficial for the organization.
Answer 2: hybrid cloud would be helpful for DTGOV in order to store their data in an
effective manner, and micro services would allow the organization to update their operations
so that they are more useful for the organization.
Question 3: which step of control would be most useful for the organization with the usage
of the hybrid cloud?
Answer 3: the step of controlling the security might prove to be most useful for their
organization because their data would be secured in the cloud and this might create a chance
for the hackers to access these organizational data and use it fir ill purposes.
Question 4: are the information security steps as well as controls enough for the
organization?
Answer 4: the steps that are mentioned regarding the information security are sufficient for
the organization, if DTGOV follows all the steps, it would be beneficial for the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





