ICT Ethical Hacking: DNS and DHCP Attacks and Prevention
Build three Virtual Machines (VM) including a Linux Server, DNS, and an additional service of your choice for a practical assignment on understanding countermeasures to protect vulnerable infrastructure.
33 Pages3485 Words255 Views
Added on 2023-06-12
About This Document
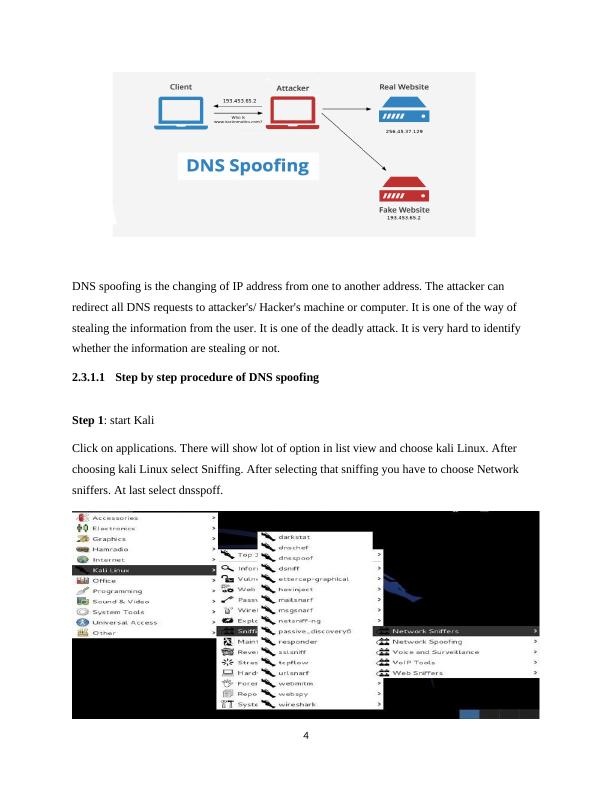
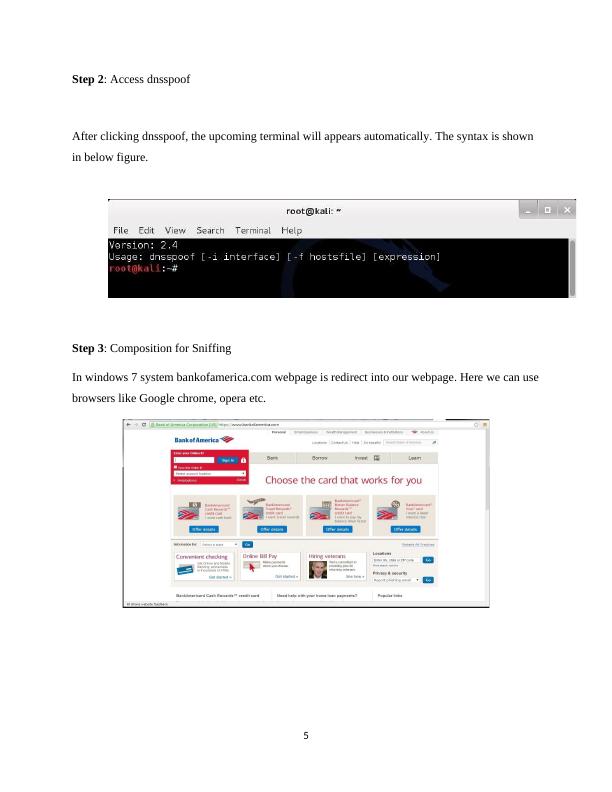
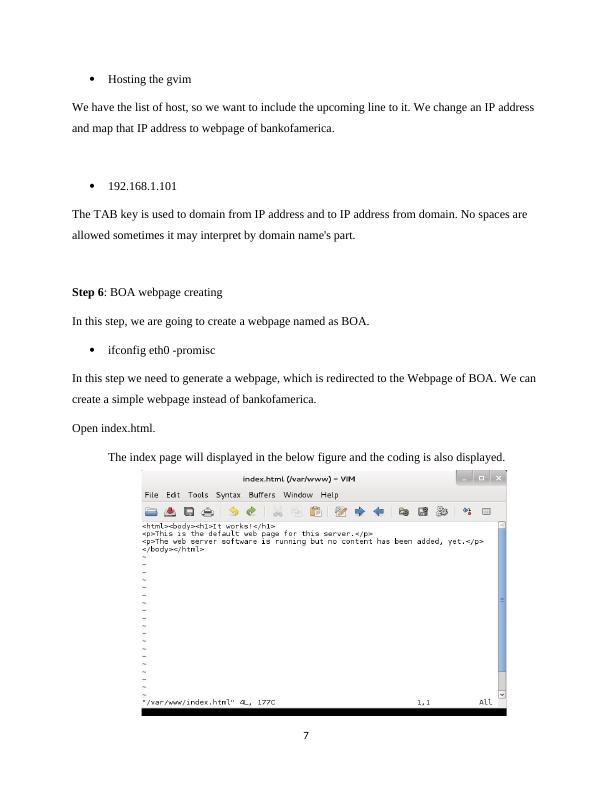
This article covers the basics of DNS and DHCP in ICT Ethical Hacking. It explains DNS Raid, DNS Transmission, and types of DNS attacks such as DNS Spoofing and DDOS. It also covers DHCP snooping concepts and types of snooping. The article provides step-by-step procedures for DNS spoofing and DHCP snooping and prevention methods for both attacks.
ICT Ethical Hacking: DNS and DHCP Attacks and Prevention
Build three Virtual Machines (VM) including a Linux Server, DNS, and an additional service of your choice for a practical assignment on understanding countermeasures to protect vulnerable infrastructure.
Added on 2023-06-12
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Network security and Protocols Assignment
|26
|4317
|64
System Management Assignment | Local Area Network (LAN)
|21
|2615
|254
Classification of Network Protocols
|6
|2727
|25
Designing and Configuring the Local Area Network
|16
|2307
|52
Networking Technologies Assignment
|9
|2023
|44
Support For Multiple Windows Servers Domains In A Local Area Networks
|18
|2298
|150