ICT Ethical Hacking Exploits
Prepare an Analysis Plan for a hypothetical pen testing scenario, including proposed analytical process, ethical considerations, required resources, and timeframe.
11 Pages2470 Words1 Views
Added on 2022-12-21
About This Document
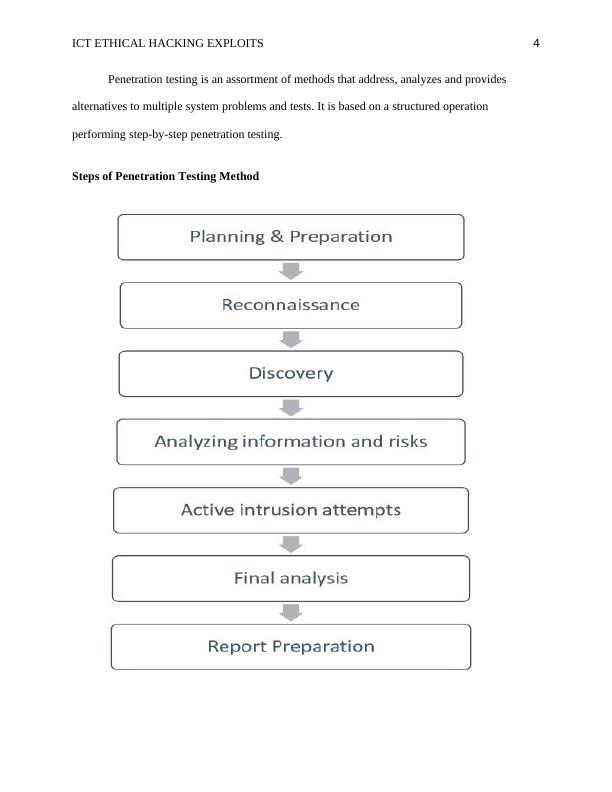
This document discusses the importance of conducting penetration testing to mitigate threats in information systems. It explores a case study on remote access interfaces and provides insights into the stages and considerations of penetration testing. The document also covers different types of penetration testing and common vulnerabilities. Legal issues related to penetration testing are also discussed.
ICT Ethical Hacking Exploits
Prepare an Analysis Plan for a hypothetical pen testing scenario, including proposed analytical process, ethical considerations, required resources, and timeframe.
Added on 2022-12-21
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
SOP for Penetration Testing
|26
|2681
|31
Ethical Hacking: Introduction, Pen Testing Approach, Results and Findings
|7
|1139
|93
Ethical Hacking & Countermeasures Report 2022
|25
|3747
|46
Speaking Cyber With Reference to Security Theories
|25
|4562
|16
Kali Linux Exploit using Metasploit
|4
|860
|293
Comparison of Metasploit and Hydra: Ethical Hacking Tools
|9
|779
|70