Internet of Things Applications and Security
VerifiedAdded on 2020/06/06
|11
|2361
|349
AI Summary
This assignment delves into the Internet of Things (IoT), examining its diverse applications across sectors like smart homes, agriculture, and wearables. It highlights the advantages brought by IoT while also addressing its limitations, particularly concerning data privacy and security. The assignment explores various IoT security technologies aimed at mitigating these risks.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Information Security
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

EXECUTIVE SUMMARY
IoT stands for Internet of Things. It is the network of physical devices, vehicles and
various other items embedded with sensors, electronics and software as well as network
connectivity. This enables these devices or objects to gather and exchange data over network.
There are various features and applications of IoT that are covered in this project. Certain issues
regarding security as well as privacy are also present in IoT. Some of the applications of IoT are
Connected Cars, Wearables, etc. It also contributes in the field of agriculture.
IoT stands for Internet of Things. It is the network of physical devices, vehicles and
various other items embedded with sensors, electronics and software as well as network
connectivity. This enables these devices or objects to gather and exchange data over network.
There are various features and applications of IoT that are covered in this project. Certain issues
regarding security as well as privacy are also present in IoT. Some of the applications of IoT are
Connected Cars, Wearables, etc. It also contributes in the field of agriculture.

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
Research report ......................................................................................................................1
Relevant technologies of IoT..................................................................................................1
Application of the IoT............................................................................................................3
Issues of IoT and their impact................................................................................................3
Summary of discussion...........................................................................................................4
Reflection on important lesson learnt from this discussion....................................................4
CONCLUSION................................................................................................................................5
REFERENCES................................................................................................................................6
APPENDIX......................................................................................................................................7
INTRODUCTION...........................................................................................................................1
Research report ......................................................................................................................1
Relevant technologies of IoT..................................................................................................1
Application of the IoT............................................................................................................3
Issues of IoT and their impact................................................................................................3
Summary of discussion...........................................................................................................4
Reflection on important lesson learnt from this discussion....................................................4
CONCLUSION................................................................................................................................5
REFERENCES................................................................................................................................6
APPENDIX......................................................................................................................................7

INTRODUCTION
The Internet of Things can be simply defined as a system of interconnected
computational devices, digital and mechanical machines, people, objects or animals that are
given with unique identifiers and capability of transferring data over a network by not including
interaction between man and computers or humans and humans (Kelly and et.al. 2013). It
includes various web enabled devices that are used for collecting, sending and acting on data
which they achieve from their surrounding environment using embedded sensors as well as
communication hardware and processors. Present report is based on the Internet of Things
whereby their features as well as security issues are described.
Research report
IoT is connecting the world. It is very important in this present era. Some of the features
or importance of IoT are described as below:
Environment monitoring: It can develop a device that helps in measuring soil or water.
This also give suggestion about quality of soil and states which type of soil is required by
different plants.It can also assist in making a warning system that warns before
occurrence of any disaster like Tsunami or earthquake (Lee and Lee, 2015). This can
prevent large number of lives and damages that might occur from those disasters.
Infrastructure management: Management of infrastructure can be done by using IoT.
The monitoring and tracking can be done and if any issue rises in any urban or rural
infrastructure like railway or bridges. This can effectively reduce the risk of any failure in
its strength as it can be monitored and alarmed as soon as possible for repairing it.
Energy management: Management of energy can be classified with systems which are
connected to internet with different sensors for reducing the consumption of power like
cloud based, remote control for oven, etc.
Medical and health care system: Health care systems assist in improving state of
patient. If IoT is introduced in the medical system then it can improve the overall health
care sector as it represents an automatic program that monitors the state of patients and
reminds them time of taking different medicines. .
Relevant technologies of IoT
There are various technologies for IoT security that are listed as below:
1
The Internet of Things can be simply defined as a system of interconnected
computational devices, digital and mechanical machines, people, objects or animals that are
given with unique identifiers and capability of transferring data over a network by not including
interaction between man and computers or humans and humans (Kelly and et.al. 2013). It
includes various web enabled devices that are used for collecting, sending and acting on data
which they achieve from their surrounding environment using embedded sensors as well as
communication hardware and processors. Present report is based on the Internet of Things
whereby their features as well as security issues are described.
Research report
IoT is connecting the world. It is very important in this present era. Some of the features
or importance of IoT are described as below:
Environment monitoring: It can develop a device that helps in measuring soil or water.
This also give suggestion about quality of soil and states which type of soil is required by
different plants.It can also assist in making a warning system that warns before
occurrence of any disaster like Tsunami or earthquake (Lee and Lee, 2015). This can
prevent large number of lives and damages that might occur from those disasters.
Infrastructure management: Management of infrastructure can be done by using IoT.
The monitoring and tracking can be done and if any issue rises in any urban or rural
infrastructure like railway or bridges. This can effectively reduce the risk of any failure in
its strength as it can be monitored and alarmed as soon as possible for repairing it.
Energy management: Management of energy can be classified with systems which are
connected to internet with different sensors for reducing the consumption of power like
cloud based, remote control for oven, etc.
Medical and health care system: Health care systems assist in improving state of
patient. If IoT is introduced in the medical system then it can improve the overall health
care sector as it represents an automatic program that monitors the state of patients and
reminds them time of taking different medicines. .
Relevant technologies of IoT
There are various technologies for IoT security that are listed as below:
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IoT network security: This is done to protect and secure the network connecting to IoT
devices to back end systems on the internet. The network security provided by IoT is
more challenging in comparison to conventional network security because the range of
standards, communication protocols and devices capabilities are wider and all of them
possess important issues and also increases the level of complexity. The primary
capabilities consists of conventional endpoint security features like firewalls, antivirus,
anti-malware and intrusion prevention and detection system. Some of the vendors are
Cisco, Senrio, Bayshore Networks, etc.
IoT authentication: It offers users the ability to authenticate an IoT device. This
involves management of large number of users on a single device. The authentication
power ranges from simple pins or passwords to more robust mechanism of authentication
like biometrics, two- factor authentication, etc. (Stamp, 2011). Most of the IoT scenes of
authentication are machine to machine based that do not involve any human. Sample
vendors are Gemalto, Convisint, Entrust Datacard, etc.
IoT encryption: Encryption of data in IoT edge devices and back end systems are done
by using standard cryptographic algorithms. This helps in maintaining data integrity and
also prevents information sniffing by hackers.
IoT PKI: IoT provides complete X.509 digital certificate, life-cycle capabilities and
cryptographic key consisting of private or public key generation, arrangement and
abrogation. Hardware specs for some of the IoT devices might bound their capability of
utilising PKI (Gubbi and et. al., 2013). Digital certificates could be safely loaded onto
IoT devices while manufacturing and then enabled by third party PKI software suites.
Those certificates can also be installed after the manufacturing. Some of the vendors are
DigiCert, HPE, WISeKey, etc.
IoT security analytics: It collects, aggregates, monitors and normalises data from IoT
devices with providing actionable report and alert on particular activities. These solutions
are created for adding sophisticated machine learning, big data techniques and artificial
intelligence for providing more prognostic modelling and anomaly detection, but such
capabilities are still rising. IoT security analytics would progressively be needed for
detecting specific attacks and instructions of IoT that cannot be determined by
2
devices to back end systems on the internet. The network security provided by IoT is
more challenging in comparison to conventional network security because the range of
standards, communication protocols and devices capabilities are wider and all of them
possess important issues and also increases the level of complexity. The primary
capabilities consists of conventional endpoint security features like firewalls, antivirus,
anti-malware and intrusion prevention and detection system. Some of the vendors are
Cisco, Senrio, Bayshore Networks, etc.
IoT authentication: It offers users the ability to authenticate an IoT device. This
involves management of large number of users on a single device. The authentication
power ranges from simple pins or passwords to more robust mechanism of authentication
like biometrics, two- factor authentication, etc. (Stamp, 2011). Most of the IoT scenes of
authentication are machine to machine based that do not involve any human. Sample
vendors are Gemalto, Convisint, Entrust Datacard, etc.
IoT encryption: Encryption of data in IoT edge devices and back end systems are done
by using standard cryptographic algorithms. This helps in maintaining data integrity and
also prevents information sniffing by hackers.
IoT PKI: IoT provides complete X.509 digital certificate, life-cycle capabilities and
cryptographic key consisting of private or public key generation, arrangement and
abrogation. Hardware specs for some of the IoT devices might bound their capability of
utilising PKI (Gubbi and et. al., 2013). Digital certificates could be safely loaded onto
IoT devices while manufacturing and then enabled by third party PKI software suites.
Those certificates can also be installed after the manufacturing. Some of the vendors are
DigiCert, HPE, WISeKey, etc.
IoT security analytics: It collects, aggregates, monitors and normalises data from IoT
devices with providing actionable report and alert on particular activities. These solutions
are created for adding sophisticated machine learning, big data techniques and artificial
intelligence for providing more prognostic modelling and anomaly detection, but such
capabilities are still rising. IoT security analytics would progressively be needed for
detecting specific attacks and instructions of IoT that cannot be determined by
2

conventional network security solutions like firewalls. Sample vendors are Cisco, SAP,
Indegy, etc.
IoT API security: This is necessary to protect the integrity of information between edge
devices and back to end systems for ensuring that only authenticating devices and apps
are communicating with APIs as well as detecting significant threats and attacks that are
done against certain APIs. Some vendors are MuleSoft, Akana, Axway, etc.
Application of the IoT
Some of the applications of IoT are listed as below:
Wearables: Corporations such as Samsung and Google are investing heavily in
manufacturing such devices as their demands are increasing in the market all over the
globe. Such devices are installed with sensors and software as well as used for collecting
data of users. It widely covers entertainment, health and fitness needs.
Connected cars: The automotive digital technology is focussing on optimising internal
functions of vehicles. A connected car is a vehicle that is capable of optimising its own
operations, maintenance and comfort of passengers by utilising on-board sensors and
internet connectivity (Tao and et. al., 2014). Different automotive companies are working
on solution of connected cars. Some of them are Apple, Tesla, BMW, etc.
IoT in agriculture: The demand of food supply is increasing by contiguous increment in
population of world. Government is supporting farmers in using modern or advanced
research and techniques for increasing the production of food. Smart farming is one of
the fastest growing fields in IoT. Farmers are utilising relevant insights from the data for
yielding better returns on investment. Sensing of soil moisture and nutrients, identifying
custom fertilisers and controlling water usage for growth of crops are some of the uses of
IoT.
Issues of IoT and their impact
Some of the issues faced by IoT are described as below:
Security: IoT faces a significant threat of security that is attracting various corporations
and government agencies from all over the globe. Hacking of cameras, small fridges,
baby monitors and even the radio in car are signalling an insecure situation that is being
caused by future of IoT (Whitman and Mattord, 2011). Malicious actors are doing
3
Indegy, etc.
IoT API security: This is necessary to protect the integrity of information between edge
devices and back to end systems for ensuring that only authenticating devices and apps
are communicating with APIs as well as detecting significant threats and attacks that are
done against certain APIs. Some vendors are MuleSoft, Akana, Axway, etc.
Application of the IoT
Some of the applications of IoT are listed as below:
Wearables: Corporations such as Samsung and Google are investing heavily in
manufacturing such devices as their demands are increasing in the market all over the
globe. Such devices are installed with sensors and software as well as used for collecting
data of users. It widely covers entertainment, health and fitness needs.
Connected cars: The automotive digital technology is focussing on optimising internal
functions of vehicles. A connected car is a vehicle that is capable of optimising its own
operations, maintenance and comfort of passengers by utilising on-board sensors and
internet connectivity (Tao and et. al., 2014). Different automotive companies are working
on solution of connected cars. Some of them are Apple, Tesla, BMW, etc.
IoT in agriculture: The demand of food supply is increasing by contiguous increment in
population of world. Government is supporting farmers in using modern or advanced
research and techniques for increasing the production of food. Smart farming is one of
the fastest growing fields in IoT. Farmers are utilising relevant insights from the data for
yielding better returns on investment. Sensing of soil moisture and nutrients, identifying
custom fertilisers and controlling water usage for growth of crops are some of the uses of
IoT.
Issues of IoT and their impact
Some of the issues faced by IoT are described as below:
Security: IoT faces a significant threat of security that is attracting various corporations
and government agencies from all over the globe. Hacking of cameras, small fridges,
baby monitors and even the radio in car are signalling an insecure situation that is being
caused by future of IoT (Whitman and Mattord, 2011). Malicious actors are doing
3

numerous attacks and carry out their evil activities. It has become more threat-able as
lives of common people are getting largely or deeply connected with IoT. Now, health
and lives of people can be targeted by the attackers.
Privacy: It is also generating many challenges to the privacy. The sophistication of IoT is
that it provides secret information in utmost details without taking the permission of users
(10 Real World Applications of Internet of Things (IoT), 2017). Hackers can take use of a
connected device in invading the house of individual virtually.
Legal Regulatory and Right issues: There is no applicable or practical law that can
embrace or cover the various layers of IoT across the globe. The scope of devices that are
linked with each other are creating different security issues and there is no legal law that
solves or concentrates on such vulnerability.
Summary of discussion
IoT is an essential part of the world now. It provides various features like infrastructure
administration, environmental monitoring as well as assist in medical and healthcare systems and
energy management. Various technologies are provided by Internet of Things such as IoT
network security, IoT authentication, IoT encryption, IoT PKI, IoT security analytics and IoT
API. Although, it provides certain benefits, it also has some limitations. It has issues in its
security and privacy. Hackers can attack on the networking where all devices of IoT are
connected with one another and takes the sophisticated data from there. This is proved to be
more threat-able for users now a days.
Solution of IoT issues
Some of the solution of above listed issues of IoT are described below:
Security issues can be resolved or decrease by using more secure protocols and
encryption technologies like SHTTP (Secure hyper text transfer protocol) and SRTP
(Secure real time protocol). This will give data privacy and encryption to the important
communication done on the network. Privacy issues can also be resolved from these
methodologies.
To solve the legal regulatory and right issue, government of Australia should impose
some laws or norms against hacking. They should provide some conditions under which
the data of one person cannot be hacked by another. If some one do so then he or she will
4
lives of common people are getting largely or deeply connected with IoT. Now, health
and lives of people can be targeted by the attackers.
Privacy: It is also generating many challenges to the privacy. The sophistication of IoT is
that it provides secret information in utmost details without taking the permission of users
(10 Real World Applications of Internet of Things (IoT), 2017). Hackers can take use of a
connected device in invading the house of individual virtually.
Legal Regulatory and Right issues: There is no applicable or practical law that can
embrace or cover the various layers of IoT across the globe. The scope of devices that are
linked with each other are creating different security issues and there is no legal law that
solves or concentrates on such vulnerability.
Summary of discussion
IoT is an essential part of the world now. It provides various features like infrastructure
administration, environmental monitoring as well as assist in medical and healthcare systems and
energy management. Various technologies are provided by Internet of Things such as IoT
network security, IoT authentication, IoT encryption, IoT PKI, IoT security analytics and IoT
API. Although, it provides certain benefits, it also has some limitations. It has issues in its
security and privacy. Hackers can attack on the networking where all devices of IoT are
connected with one another and takes the sophisticated data from there. This is proved to be
more threat-able for users now a days.
Solution of IoT issues
Some of the solution of above listed issues of IoT are described below:
Security issues can be resolved or decrease by using more secure protocols and
encryption technologies like SHTTP (Secure hyper text transfer protocol) and SRTP
(Secure real time protocol). This will give data privacy and encryption to the important
communication done on the network. Privacy issues can also be resolved from these
methodologies.
To solve the legal regulatory and right issue, government of Australia should impose
some laws or norms against hacking. They should provide some conditions under which
the data of one person cannot be hacked by another. If some one do so then he or she will
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

be punished by the government. They have to do certain amount of money in the form of
penalty and for more serious condition, they can even put behind bars.
Reflection on important lesson learnt from this discussion
I have learnt about the importance of Internet of Things in the present era. IoT aims to
connect all people in the world. It has various features. It provides its contribution in different
sectors like healthcare, architecture, energy as well as environment. By the help of IoT, patient
can take a pill that automatically reminds them the next time of taking other medicines. It
monitors as well as controls the overall functionalities of human body. I also learn about various
application of IoT such as Connected Cars, Wearables and IoT in agriculture. All these
applications provide additional features in relation to ordinary one. But there exist certain
security and privacy issues.
CONCLUSION
From the above report, it can be concluded that Internet of Things has now become the
part of life of every person in this world as all of them are connected with internet now a days.
IoT makes possible the sharing of data over network by providing unique identifiers to people,
animal, machine, etc. without taking interaction of human to human or man to machines. There
are various applications of IoT available in this world such as Connected Cars, Smart television,
Wearables, etc. It has been assessed that IoT also contributes in the field of agriculture. In-spite
of several benefits, there exists some limitations of IoT that are regarding privacy and secrecy of
data of users.
5
penalty and for more serious condition, they can even put behind bars.
Reflection on important lesson learnt from this discussion
I have learnt about the importance of Internet of Things in the present era. IoT aims to
connect all people in the world. It has various features. It provides its contribution in different
sectors like healthcare, architecture, energy as well as environment. By the help of IoT, patient
can take a pill that automatically reminds them the next time of taking other medicines. It
monitors as well as controls the overall functionalities of human body. I also learn about various
application of IoT such as Connected Cars, Wearables and IoT in agriculture. All these
applications provide additional features in relation to ordinary one. But there exist certain
security and privacy issues.
CONCLUSION
From the above report, it can be concluded that Internet of Things has now become the
part of life of every person in this world as all of them are connected with internet now a days.
IoT makes possible the sharing of data over network by providing unique identifiers to people,
animal, machine, etc. without taking interaction of human to human or man to machines. There
are various applications of IoT available in this world such as Connected Cars, Smart television,
Wearables, etc. It has been assessed that IoT also contributes in the field of agriculture. In-spite
of several benefits, there exists some limitations of IoT that are regarding privacy and secrecy of
data of users.
5

6

REFERENCES
Books & journals
Gubbi, J. & et.al. (2013). Internet of Things (IoT): A vision, architectural elements, and future
directions. Future generation computer systems. 29(7). 1645-1660.
Kelly & et.al. (2013). Towards the implementation of IoT for environmental condition
monitoring in homes. IEEE Sensors Journal. 13(10). 3846-3853.
Lee, I. & Lee, K. (2015). The Internet of Things (IoT): Applications, investments, and challenges
for enterprises. Business Horizons. 58(4). 431-440.
Stamp, M. (2011). Information security: principles and practice. John Wiley & Sons.
Tao & et.al. (2014). IoT-based intelligent perception and access of manufacturing resource
toward cloud manufacturing. IEEE Transactions on Industrial Informatics. 10(2).1547-
1557.
Whitman, M. E. & Mattord, H. J. (2011). Principles of information security. Cengage Learning.
Online
10 Real World Applications of Internet of Things (IoT). 2017. [Online]. Available through:
<https://www.analyticsvidhya.com/blog/2016/08/10-youtube-videos-explaining-the-real-
world-applications-of-internet-of-things-iot/>. [Accessed on 22nd September 2017.
7
Books & journals
Gubbi, J. & et.al. (2013). Internet of Things (IoT): A vision, architectural elements, and future
directions. Future generation computer systems. 29(7). 1645-1660.
Kelly & et.al. (2013). Towards the implementation of IoT for environmental condition
monitoring in homes. IEEE Sensors Journal. 13(10). 3846-3853.
Lee, I. & Lee, K. (2015). The Internet of Things (IoT): Applications, investments, and challenges
for enterprises. Business Horizons. 58(4). 431-440.
Stamp, M. (2011). Information security: principles and practice. John Wiley & Sons.
Tao & et.al. (2014). IoT-based intelligent perception and access of manufacturing resource
toward cloud manufacturing. IEEE Transactions on Industrial Informatics. 10(2).1547-
1557.
Whitman, M. E. & Mattord, H. J. (2011). Principles of information security. Cengage Learning.
Online
10 Real World Applications of Internet of Things (IoT). 2017. [Online]. Available through:
<https://www.analyticsvidhya.com/blog/2016/08/10-youtube-videos-explaining-the-real-
world-applications-of-internet-of-things-iot/>. [Accessed on 22nd September 2017.
7
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
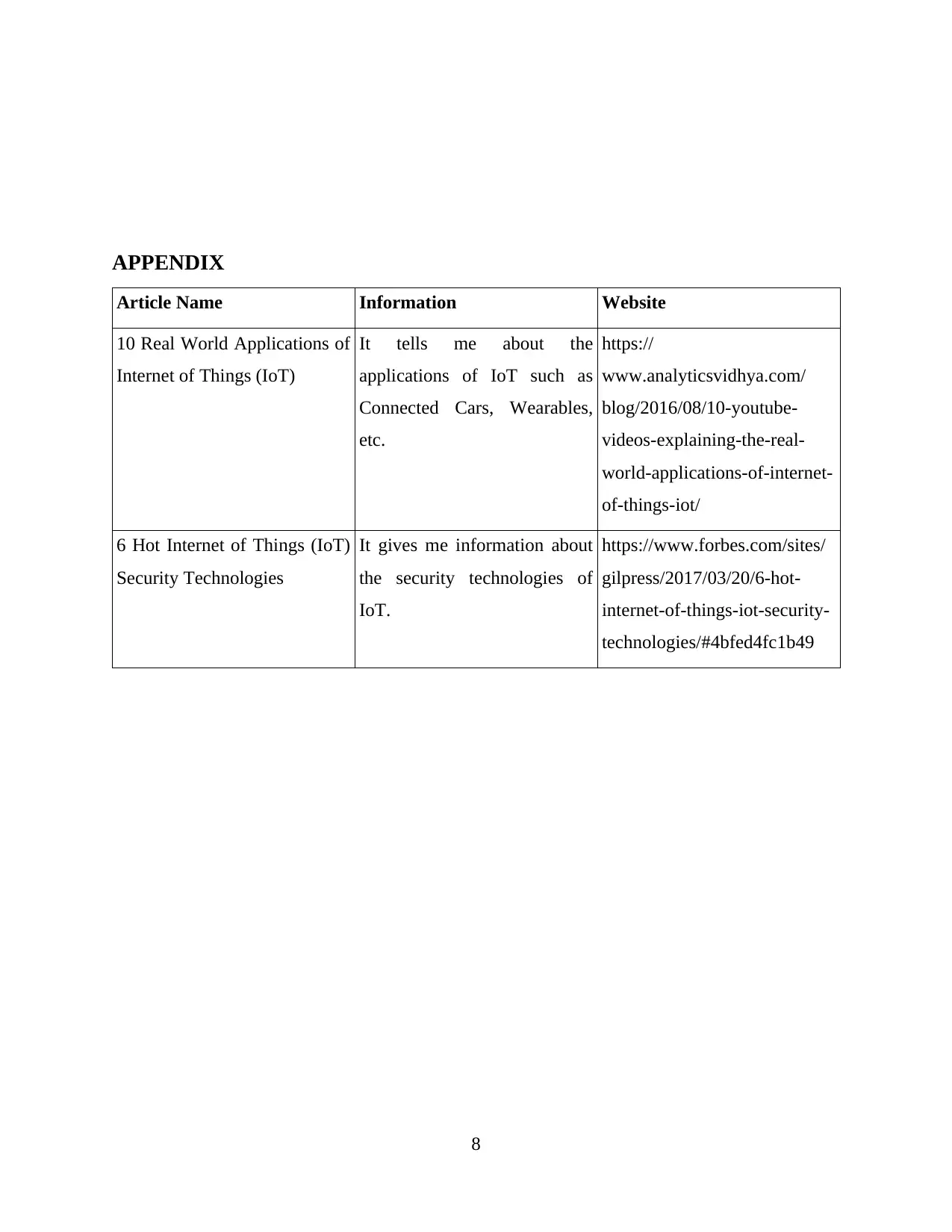
APPENDIX
Article Name Information Website
10 Real World Applications of
Internet of Things (IoT)
It tells me about the
applications of IoT such as
Connected Cars, Wearables,
etc.
https://
www.analyticsvidhya.com/
blog/2016/08/10-youtube-
videos-explaining-the-real-
world-applications-of-internet-
of-things-iot/
6 Hot Internet of Things (IoT)
Security Technologies
It gives me information about
the security technologies of
IoT.
https://www.forbes.com/sites/
gilpress/2017/03/20/6-hot-
internet-of-things-iot-security-
technologies/#4bfed4fc1b49
8
Article Name Information Website
10 Real World Applications of
Internet of Things (IoT)
It tells me about the
applications of IoT such as
Connected Cars, Wearables,
etc.
https://
www.analyticsvidhya.com/
blog/2016/08/10-youtube-
videos-explaining-the-real-
world-applications-of-internet-
of-things-iot/
6 Hot Internet of Things (IoT)
Security Technologies
It gives me information about
the security technologies of
IoT.
https://www.forbes.com/sites/
gilpress/2017/03/20/6-hot-
internet-of-things-iot-security-
technologies/#4bfed4fc1b49
8
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




