Internetworking: Revision Questions Answers
VerifiedAdded on 2022/09/06
|4
|1404
|14
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Internetworking: Revision Questions
What are the key characteristics of:
Distance Vector
- Has periodic updates, at the end of a given period of time, updates will be sent to any router
taking part in distance vector protocol.
- Has neighbours whom with which they routing information
- Broadcasts to find the available neighbours
Link – State
- Uses Dijkstra algorithm
- Use cost as the parameter for best path calculation
- Link state updates part the network
- Updates are triggered by changes in network topology
- Has fast time convergence
- Uses hierarchical structure
Path Vector
- Uses path to reach the destination
- Is a loop free protocol
What are the characteristics of:
- Internal routing protocols IGP is a Routing Protocol which is deployed to look for a network
path information within an internal network routing.
external routing protocols
- Exterior Gateway Protocol (EGP) is a Routing Protocol which is deployed to find network route
information between different ASs.
Explain the main functions of RIP
- Is a distance routing protocol which uses hop count as the main metric. This protocol defines
how the routers are supposed to share information during the moving of the traffic among the
interconnected group of LANs.
What are the main limitations of the routing protocol?
- RIP cannot support a network which has more than fifteen hops within the same network
- Does not support the variable-length subnet mask.
- Has limited security
- Has slower convergency time.
What timers can be found in RIP?
- Invalid timer – a route is declared invalid after 180 sec
- Update – takes place 30 sec
- Hold down – timer which happens after hold down timer after 180 sec
- Flush time – timer which expire after route entry has been removed from routing table 240
sec.
How does each work?
1
What are the key characteristics of:
Distance Vector
- Has periodic updates, at the end of a given period of time, updates will be sent to any router
taking part in distance vector protocol.
- Has neighbours whom with which they routing information
- Broadcasts to find the available neighbours
Link – State
- Uses Dijkstra algorithm
- Use cost as the parameter for best path calculation
- Link state updates part the network
- Updates are triggered by changes in network topology
- Has fast time convergence
- Uses hierarchical structure
Path Vector
- Uses path to reach the destination
- Is a loop free protocol
What are the characteristics of:
- Internal routing protocols IGP is a Routing Protocol which is deployed to look for a network
path information within an internal network routing.
external routing protocols
- Exterior Gateway Protocol (EGP) is a Routing Protocol which is deployed to find network route
information between different ASs.
Explain the main functions of RIP
- Is a distance routing protocol which uses hop count as the main metric. This protocol defines
how the routers are supposed to share information during the moving of the traffic among the
interconnected group of LANs.
What are the main limitations of the routing protocol?
- RIP cannot support a network which has more than fifteen hops within the same network
- Does not support the variable-length subnet mask.
- Has limited security
- Has slower convergency time.
What timers can be found in RIP?
- Invalid timer – a route is declared invalid after 180 sec
- Update – takes place 30 sec
- Hold down – timer which happens after hold down timer after 180 sec
- Flush time – timer which expire after route entry has been removed from routing table 240
sec.
How does each work?
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

- See explanation after each above.
How do they relate to each other?
- The update timer updates after every 30 sec, invalid timer is triggered when there has been no
update after 180 sec, the hold-down timer is activated as soon as the route has been declared
invalid and the flush which is set to 240 resets the route once it has stayed in for 240 sec
How does RIP manage to maintain its routing table up-to-date?
- RIP maintains its routing table up-to-date by broadcasting its entire routing table to its closest
neighbours.
Explain the main functions of OSPF
- OSPF is a routing protocol which is used to find the best path during their passing through a
number of linked networks.
Explain the key advantages of OSPF over RIP
- Supports VLSM: the OSPF supports the classless routing
- Network reachability: OSPF is able to support networks which have more than 15 hops.
- Fast convergence: the OSPF converges fast as compared to RIP
- Metric: OSPF uses costs as its metric as compared to hop count for RIP which is very slow.
- Efficiency: RIP’s 30 seconds frequent updates makes it inefficient.
What is an Autonomous System?
- This is a globally assigned unique number. The autonomous system share information with
autonomous system by use of BGP.
What is an OSPF area?
- An OSPF network can be divided into sub-domains called areas. An area is a logical collection
of OSPF networks, routers, and links that have the same area identification.
What is a Link State Database? How is it used?
- This is a tree image of the of the OSPF topology holding all the OSPF routing information. The
Link state Database is used to sore the routing information of the OSPF routing.
What is Link State Advertising (LSA)? How is it used?
- This is an OSPF data packet which contains link-state advertisement together with the
information which is share between OSPF routers.
What are the five steps to initiate routing in an OSPF area?
i. Establishment of the neighbour adjacencies.
ii. Exchange of the link-state advertisements
iii. Topology table building
iv. SPF algorithm execution
v. Routing table building
How does OSPF manage to maintain its routing table up-to-date?
- Hello protocol is used to maintain the routing-table by providing dynamic discovery of
neighbour relationships
Explain how loopback within each routing protocols (RIP, OSPF, BGP) is prevented
2
How do they relate to each other?
- The update timer updates after every 30 sec, invalid timer is triggered when there has been no
update after 180 sec, the hold-down timer is activated as soon as the route has been declared
invalid and the flush which is set to 240 resets the route once it has stayed in for 240 sec
How does RIP manage to maintain its routing table up-to-date?
- RIP maintains its routing table up-to-date by broadcasting its entire routing table to its closest
neighbours.
Explain the main functions of OSPF
- OSPF is a routing protocol which is used to find the best path during their passing through a
number of linked networks.
Explain the key advantages of OSPF over RIP
- Supports VLSM: the OSPF supports the classless routing
- Network reachability: OSPF is able to support networks which have more than 15 hops.
- Fast convergence: the OSPF converges fast as compared to RIP
- Metric: OSPF uses costs as its metric as compared to hop count for RIP which is very slow.
- Efficiency: RIP’s 30 seconds frequent updates makes it inefficient.
What is an Autonomous System?
- This is a globally assigned unique number. The autonomous system share information with
autonomous system by use of BGP.
What is an OSPF area?
- An OSPF network can be divided into sub-domains called areas. An area is a logical collection
of OSPF networks, routers, and links that have the same area identification.
What is a Link State Database? How is it used?
- This is a tree image of the of the OSPF topology holding all the OSPF routing information. The
Link state Database is used to sore the routing information of the OSPF routing.
What is Link State Advertising (LSA)? How is it used?
- This is an OSPF data packet which contains link-state advertisement together with the
information which is share between OSPF routers.
What are the five steps to initiate routing in an OSPF area?
i. Establishment of the neighbour adjacencies.
ii. Exchange of the link-state advertisements
iii. Topology table building
iv. SPF algorithm execution
v. Routing table building
How does OSPF manage to maintain its routing table up-to-date?
- Hello protocol is used to maintain the routing-table by providing dynamic discovery of
neighbour relationships
Explain how loopback within each routing protocols (RIP, OSPF, BGP) is prevented
2

- RIP – Hold-down timers: this mechanism is used by RIP to hinder bad routes from being
propagated by mistake. As soon a route is put in hold-timer state, it does not advertise nor
receive advertisements.
- OSPF – OSPF hierarchical design helps in prevention of loops. In order for routers in an OSPF
area to communicate, they have to be connected to the Area 0, by passing through Area 0,
makes the entire hierarchy to point to a logical point-to-pint topology and no reverse route is
allowed.
- BGP - Split Horizon: this is a routing configuration which stops a route from being send back to
the path from which it was received from.
Explain the key characteristics of BGP?
- It is a distance vector routing protocol
- It supports classless routing.
- Uses autonomous systems as the building blocks
- Uses a number of metrics
- Route exchange takes place only with the neighbours.
Compare Autonomous Systems (in BGP) and areas (in OSPF)
- Whereas Autonomous System in BGB shares routing information with other Autonomous
System using the BGP protocol, areas are used with OSPF to share routing information with
same areas in a network system
What does the term ‘fully converged’ mean for RIP and for OSPF?
- In RIP and OSPF, a fully converged network is one which has the nodes have an understanding
of the path take through the packets.
What is subnetting?
- Subnetting is the subdivision of a network into logical segments.
What is supernetting?
- This is the procedure of summarizing a bunch of connecting subnetted networks into a one
large network.
Can you identify the five (5) classes of IP addresses in classful addressing.
- Class A
- Class B
- Class C
- Class D
- Class E
What is broadcast address?
- This is the address in a network in which each device is connected to multiple-access
communication network devices are permitted to receive datagrams.
What is network address?
- This is a number which assigned to a networking interface to the purpose of identifying the
interface uniquely on the internet.
What is network mask?
- This is a mask used to divide an IP address into two divisions specifying the network area and
the host area.
3
propagated by mistake. As soon a route is put in hold-timer state, it does not advertise nor
receive advertisements.
- OSPF – OSPF hierarchical design helps in prevention of loops. In order for routers in an OSPF
area to communicate, they have to be connected to the Area 0, by passing through Area 0,
makes the entire hierarchy to point to a logical point-to-pint topology and no reverse route is
allowed.
- BGP - Split Horizon: this is a routing configuration which stops a route from being send back to
the path from which it was received from.
Explain the key characteristics of BGP?
- It is a distance vector routing protocol
- It supports classless routing.
- Uses autonomous systems as the building blocks
- Uses a number of metrics
- Route exchange takes place only with the neighbours.
Compare Autonomous Systems (in BGP) and areas (in OSPF)
- Whereas Autonomous System in BGB shares routing information with other Autonomous
System using the BGP protocol, areas are used with OSPF to share routing information with
same areas in a network system
What does the term ‘fully converged’ mean for RIP and for OSPF?
- In RIP and OSPF, a fully converged network is one which has the nodes have an understanding
of the path take through the packets.
What is subnetting?
- Subnetting is the subdivision of a network into logical segments.
What is supernetting?
- This is the procedure of summarizing a bunch of connecting subnetted networks into a one
large network.
Can you identify the five (5) classes of IP addresses in classful addressing.
- Class A
- Class B
- Class C
- Class D
- Class E
What is broadcast address?
- This is the address in a network in which each device is connected to multiple-access
communication network devices are permitted to receive datagrams.
What is network address?
- This is a number which assigned to a networking interface to the purpose of identifying the
interface uniquely on the internet.
What is network mask?
- This is a mask used to divide an IP address into two divisions specifying the network area and
the host area.
3
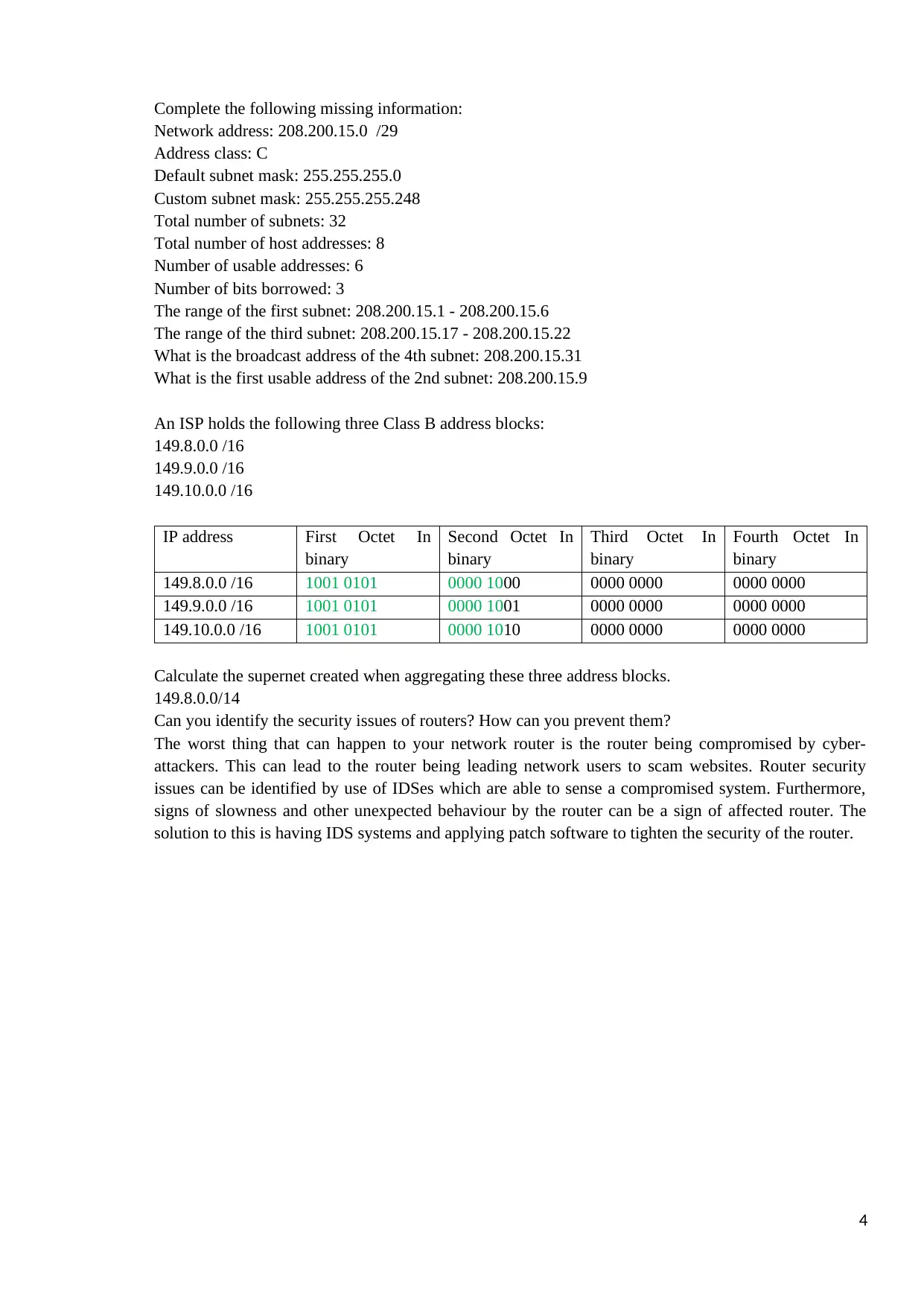
Complete the following missing information:
Network address: 208.200.15.0 /29
Address class: C
Default subnet mask: 255.255.255.0
Custom subnet mask: 255.255.255.248
Total number of subnets: 32
Total number of host addresses: 8
Number of usable addresses: 6
Number of bits borrowed: 3
The range of the first subnet: 208.200.15.1 - 208.200.15.6
The range of the third subnet: 208.200.15.17 - 208.200.15.22
What is the broadcast address of the 4th subnet: 208.200.15.31
What is the first usable address of the 2nd subnet: 208.200.15.9
An ISP holds the following three Class B address blocks:
149.8.0.0 /16
149.9.0.0 /16
149.10.0.0 /16
IP address First Octet In
binary
Second Octet In
binary
Third Octet In
binary
Fourth Octet In
binary
149.8.0.0 /16 1001 0101 0000 1000 0000 0000 0000 0000
149.9.0.0 /16 1001 0101 0000 1001 0000 0000 0000 0000
149.10.0.0 /16 1001 0101 0000 1010 0000 0000 0000 0000
Calculate the supernet created when aggregating these three address blocks.
149.8.0.0/14
Can you identify the security issues of routers? How can you prevent them?
The worst thing that can happen to your network router is the router being compromised by cyber-
attackers. This can lead to the router being leading network users to scam websites. Router security
issues can be identified by use of IDSes which are able to sense a compromised system. Furthermore,
signs of slowness and other unexpected behaviour by the router can be a sign of affected router. The
solution to this is having IDS systems and applying patch software to tighten the security of the router.
4
Network address: 208.200.15.0 /29
Address class: C
Default subnet mask: 255.255.255.0
Custom subnet mask: 255.255.255.248
Total number of subnets: 32
Total number of host addresses: 8
Number of usable addresses: 6
Number of bits borrowed: 3
The range of the first subnet: 208.200.15.1 - 208.200.15.6
The range of the third subnet: 208.200.15.17 - 208.200.15.22
What is the broadcast address of the 4th subnet: 208.200.15.31
What is the first usable address of the 2nd subnet: 208.200.15.9
An ISP holds the following three Class B address blocks:
149.8.0.0 /16
149.9.0.0 /16
149.10.0.0 /16
IP address First Octet In
binary
Second Octet In
binary
Third Octet In
binary
Fourth Octet In
binary
149.8.0.0 /16 1001 0101 0000 1000 0000 0000 0000 0000
149.9.0.0 /16 1001 0101 0000 1001 0000 0000 0000 0000
149.10.0.0 /16 1001 0101 0000 1010 0000 0000 0000 0000
Calculate the supernet created when aggregating these three address blocks.
149.8.0.0/14
Can you identify the security issues of routers? How can you prevent them?
The worst thing that can happen to your network router is the router being compromised by cyber-
attackers. This can lead to the router being leading network users to scam websites. Router security
issues can be identified by use of IDSes which are able to sense a compromised system. Furthermore,
signs of slowness and other unexpected behaviour by the router can be a sign of affected router. The
solution to this is having IDS systems and applying patch software to tighten the security of the router.
4
1 out of 4
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




