Internet of Things on Cyber Security: HSBC Bank DDoS Incident
VerifiedAdded on 2023/06/10
|19
|5169
|132
AI Summary
This article discusses the negative and positive impacts of the internet of things on cyber security, with a focus on the HSBC bank DDoS incident. It also includes structured analysis techniques such as force field analysis, SWOT analysis, and structured brainstorming.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT
1
INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT.
Student Name
Institutional Affiliation
Facilitator
Course
Date
1
INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT.
Student Name
Institutional Affiliation
Facilitator
Course
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 2
Abstract
The internet of things involves the physical devices connectivity to the internet to
improve the efficiency and ease control of systems. The various devices interconnected to each
other exchange useful sensitive data which is prone to cyber-attacks by unauthorized personnel
(Abomhara, 2015). According to the incident of HSBC bank DDoS attack of 2016, the internet
of things negative implications on the cyber security include the open debugging interfaces
associated with the internet of things which poses great risks for attacks from the hackers,
challenges in security maintenance by the organizations’ IT experts since with the internet of
things adoption organizations make it possible for their employees to work from home, the
building of security around the internet of things rather than building it directly into the devices,
lack of government laws to regulate the internet of things adoption in various countries and the
compromise of the individuals privacy associated with the internet of things. Although the
internet of things poses a great risk the cyber security it still helps improve the business
productivity efficiency, helps in better decision making and increases revenue generated by the
business organizations. Three structural analysis techniques were used in analyzing the impacts
which are the force field analysis, SWOT analysis and the structural brainstorming. Both
techniques led to a conclusion that internet of things poses great risk to cyber security and is
anticipated to follow the same trend as the internet of things devices increase in future which will
be difficult to control.
Abstract
The internet of things involves the physical devices connectivity to the internet to
improve the efficiency and ease control of systems. The various devices interconnected to each
other exchange useful sensitive data which is prone to cyber-attacks by unauthorized personnel
(Abomhara, 2015). According to the incident of HSBC bank DDoS attack of 2016, the internet
of things negative implications on the cyber security include the open debugging interfaces
associated with the internet of things which poses great risks for attacks from the hackers,
challenges in security maintenance by the organizations’ IT experts since with the internet of
things adoption organizations make it possible for their employees to work from home, the
building of security around the internet of things rather than building it directly into the devices,
lack of government laws to regulate the internet of things adoption in various countries and the
compromise of the individuals privacy associated with the internet of things. Although the
internet of things poses a great risk the cyber security it still helps improve the business
productivity efficiency, helps in better decision making and increases revenue generated by the
business organizations. Three structural analysis techniques were used in analyzing the impacts
which are the force field analysis, SWOT analysis and the structural brainstorming. Both
techniques led to a conclusion that internet of things poses great risk to cyber security and is
anticipated to follow the same trend as the internet of things devices increase in future which will
be difficult to control.

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 3
Table of Contents
Abstract.......................................................................................................................................................2
Introduction.................................................................................................................................................4
Intelligence Analysis and Data Collection...................................................................................................5
Negative impacts of the internet of things on cyber security...................................................................6
Positive impacts of the internet of things.................................................................................................9
Structured Analysis Techniques................................................................................................................11
Force Field Analysis..............................................................................................................................11
SWOT Analysis.....................................................................................................................................13
Structured Brainstorming.......................................................................................................................15
Discussion of the findings.........................................................................................................................16
Conclusion.................................................................................................................................................17
References.................................................................................................................................................18
Table of Contents
Abstract.......................................................................................................................................................2
Introduction.................................................................................................................................................4
Intelligence Analysis and Data Collection...................................................................................................5
Negative impacts of the internet of things on cyber security...................................................................6
Positive impacts of the internet of things.................................................................................................9
Structured Analysis Techniques................................................................................................................11
Force Field Analysis..............................................................................................................................11
SWOT Analysis.....................................................................................................................................13
Structured Brainstorming.......................................................................................................................15
Discussion of the findings.........................................................................................................................16
Conclusion.................................................................................................................................................17
References.................................................................................................................................................18

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 4
Introduction
The internet of things refers to the connection of the physical devices which generally
include the home appliances and other related items to the internet. These items are generally
embedded with connectivity to enable direct connection and the exchange of data, software,
electronics, sensors and actuators (Vermesan & Friess, 2013). A computing system is actually
put in place to enable a unique identification of the embedded items.
The Incident chosen for this case is the Distributed Denial of Services executed in
Britain’s HSBC bank in the year 2016. HSBC is among the largest financial institutions in the
world based in Britain. On January 29th, 2016, HSBC bank reported to his customers to have
been targeted by the distributed denial of service attackers which led to its customers being
disrupted from their easy access to their online banking portals (Brynielsson, Franke & Varga,
2016). The attacks were executed at an awkward moment for banking customers and this is a
clear indication that IoT can be used maliciously by people with selfish interests. First, the day
the incident was reported, it was a payday for many people and perhaps the most suspicious, it
was just two days before the tax payment deadline in UK and as a result, millions of tax payers
faced a 3% penalty because of not paying their taxes on time. Could it have been a plan by the
tax department to exploit the citizens? This has remained to be question by the victims of the
incident (Brynielsson, Franke & Varga, 2016).
Intelligence Analysis and Data Collection
Intelligent analysis refers to the process through which individual as well as collective
cognitive methods are applied in collecting data and information from which meaning
Introduction
The internet of things refers to the connection of the physical devices which generally
include the home appliances and other related items to the internet. These items are generally
embedded with connectivity to enable direct connection and the exchange of data, software,
electronics, sensors and actuators (Vermesan & Friess, 2013). A computing system is actually
put in place to enable a unique identification of the embedded items.
The Incident chosen for this case is the Distributed Denial of Services executed in
Britain’s HSBC bank in the year 2016. HSBC is among the largest financial institutions in the
world based in Britain. On January 29th, 2016, HSBC bank reported to his customers to have
been targeted by the distributed denial of service attackers which led to its customers being
disrupted from their easy access to their online banking portals (Brynielsson, Franke & Varga,
2016). The attacks were executed at an awkward moment for banking customers and this is a
clear indication that IoT can be used maliciously by people with selfish interests. First, the day
the incident was reported, it was a payday for many people and perhaps the most suspicious, it
was just two days before the tax payment deadline in UK and as a result, millions of tax payers
faced a 3% penalty because of not paying their taxes on time. Could it have been a plan by the
tax department to exploit the citizens? This has remained to be question by the victims of the
incident (Brynielsson, Franke & Varga, 2016).
Intelligence Analysis and Data Collection
Intelligent analysis refers to the process through which individual as well as collective
cognitive methods are applied in collecting data and information from which meaning
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 5
conclusions are made (Covington & Carskadden, 2013). From the impacts of IoT to different
people, the arguments expected from different people are likely to be different. For those who
have been hit negatively by the new technology, negative impacts are likely to ensue while for
those who have reaped positively from this technology are likely to give positive feedback. To
avoid being biased, the paper will rely on data from both sides to settle at the conclusion. For that
matter, data will be obtained from the victims who are believed to have been hit negatively by
the IoT technology in HSBC bank of Britain as well as those of New York Magazine while on
the other hand will consider the opinions of business organizations like Apple and Samsung
(Brynielsson, Franke & Varga, 2016).
Negative impacts of the internet of things on cyber security
The internet of things involves a network connection of many devices which can create
entry points of unauthorized personnel into the interconnected systems and gain access to crucial
confidential information of the system owners (Sicari, Rizzardi, Grieco & Coen-Porisini, 2015).
Some of the negative impacts of the internet of things on cyber security include:
Distributed Denial of Services as witnessed in HSBC bank, HSBC is among the largest
financial institutions in the world based in Britain. On January 29th, 2016, HSBC bank reported
to his customers to have been targeted by the distributed denial of service attackers which led to
its customers being disrupted from their easy access to their online banking portals. The attacks
were executed at an awkward moment for banking customers and this is a clear indication that
IoT can be used maliciously by people with selfish interests. First, the day the incident was
reported, it was a payday for many people and perhaps the most suspicious, it was just two days
before the tax payment deadline in UK and as a result, millions of tax payers faced a 3% penalty
because of not paying their taxes on time (Brynielsson, Franke & Varga, 2016).
conclusions are made (Covington & Carskadden, 2013). From the impacts of IoT to different
people, the arguments expected from different people are likely to be different. For those who
have been hit negatively by the new technology, negative impacts are likely to ensue while for
those who have reaped positively from this technology are likely to give positive feedback. To
avoid being biased, the paper will rely on data from both sides to settle at the conclusion. For that
matter, data will be obtained from the victims who are believed to have been hit negatively by
the IoT technology in HSBC bank of Britain as well as those of New York Magazine while on
the other hand will consider the opinions of business organizations like Apple and Samsung
(Brynielsson, Franke & Varga, 2016).
Negative impacts of the internet of things on cyber security
The internet of things involves a network connection of many devices which can create
entry points of unauthorized personnel into the interconnected systems and gain access to crucial
confidential information of the system owners (Sicari, Rizzardi, Grieco & Coen-Porisini, 2015).
Some of the negative impacts of the internet of things on cyber security include:
Distributed Denial of Services as witnessed in HSBC bank, HSBC is among the largest
financial institutions in the world based in Britain. On January 29th, 2016, HSBC bank reported
to his customers to have been targeted by the distributed denial of service attackers which led to
its customers being disrupted from their easy access to their online banking portals. The attacks
were executed at an awkward moment for banking customers and this is a clear indication that
IoT can be used maliciously by people with selfish interests. First, the day the incident was
reported, it was a payday for many people and perhaps the most suspicious, it was just two days
before the tax payment deadline in UK and as a result, millions of tax payers faced a 3% penalty
because of not paying their taxes on time (Brynielsson, Franke & Varga, 2016).

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 6
Most of the internet of things interconnected devices contains an open debugging system.
Debugging refers to the process through which problems associated with computer programs or
rather systems controlled by the use of computers through the internet which may hinder the
correct operation of the programs are detected and then resolved to restore the program back to
its operation mode. The debugging process begins immediately when a code has been written
and continues as the code written undergoes combination with some other programming units in
order to form software products. Programs with vast number of lines of code can ease their
debugging process by use of various strategies with the most commonly used ones being code
reviews, unit tests and pair programming. The difficulties associated with the debugging process
vary according to the complexity of the systems, the programming languages used and the
availability of the debugging tools. An open debugging interface associated with the internet of
things devices means that the process is not secured and can be accessed by various individuals
some of which are unauthorized and have bad intentions on the system (Elmaghraby & Losavio,
2014). The open debugging process provides an opportunity for the hackers to extend their
harmful activities to the devices such as coding spyware which is a harmful code and highly
affects the devices. The weak protocols make it easier for many people to access the system’s
confidential information and this poses great chances through which the systems may be harmed
as majority of the users do not actually follow the appropriate determined practices of cyber
security. The debugging process involves first making attempts towards reproducing the problem
for identification of a bug, the program input is then simplified for easier debugging and this can
be done manually by the use of an approach known as the divide and conquer approach, after all
that the programmer can then operate various parts of the initial test case and check if the
problem has been solved or it still exists. After the sufficient simplification of the test case, the
Most of the internet of things interconnected devices contains an open debugging system.
Debugging refers to the process through which problems associated with computer programs or
rather systems controlled by the use of computers through the internet which may hinder the
correct operation of the programs are detected and then resolved to restore the program back to
its operation mode. The debugging process begins immediately when a code has been written
and continues as the code written undergoes combination with some other programming units in
order to form software products. Programs with vast number of lines of code can ease their
debugging process by use of various strategies with the most commonly used ones being code
reviews, unit tests and pair programming. The difficulties associated with the debugging process
vary according to the complexity of the systems, the programming languages used and the
availability of the debugging tools. An open debugging interface associated with the internet of
things devices means that the process is not secured and can be accessed by various individuals
some of which are unauthorized and have bad intentions on the system (Elmaghraby & Losavio,
2014). The open debugging process provides an opportunity for the hackers to extend their
harmful activities to the devices such as coding spyware which is a harmful code and highly
affects the devices. The weak protocols make it easier for many people to access the system’s
confidential information and this poses great chances through which the systems may be harmed
as majority of the users do not actually follow the appropriate determined practices of cyber
security. The debugging process involves first making attempts towards reproducing the problem
for identification of a bug, the program input is then simplified for easier debugging and this can
be done manually by the use of an approach known as the divide and conquer approach, after all
that the programmer can then operate various parts of the initial test case and check if the
problem has been solved or it still exists. After the sufficient simplification of the test case, the

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 7
debugging tools can be used for the examination of the program states and the tracking of the
origin of problems within the system. Throughout this open debugging system, hackers can
easily access the systems and also run the codes but harmful ones intended to bring down the
systems or to access the valuable information which may be of interest to them.
Employees and the IT experts may be located in different places. Many organizations
have embraced the internet of things and adopted it in various ways. These practices are all
aimed at improving the business value, which improves productivity (Xia, Yang, Wang & Vinel,
2012). This is done by producing more using less, meaning the production costs are lowered and
profit levels are raised. Some of the internet of things techniques adopted by many businesses is
the enabling of employees to work from their homes. The highly trained IT experts recruited by
these organizations to oversee cyber security on the companies’ sites face difficulties in
controlling the organizations’ system with the employees working at their home comfort zones
rather than at the workplace with the IT personnel which could have made it easier for them to
link the employees activities together and adequately control and protect them. The hackers or
rather the unauthorized personnel take the advantage of the difficulties associated with the work
from home technology and can break into the organizations’ sites and access the companies
valuable data or even their customers data and anything of interest to them. Through this, the
companies’ system may be tampered with and incur greater losses as even their accounts may be
deprived of money through the unauthorized access to their systems.
Most of the internet of things device, have security build around them instead of the
security being built directly into them. Direct building of security into the device before the
hardware implementation into the system improves the device protection and testing can be done
debugging tools can be used for the examination of the program states and the tracking of the
origin of problems within the system. Throughout this open debugging system, hackers can
easily access the systems and also run the codes but harmful ones intended to bring down the
systems or to access the valuable information which may be of interest to them.
Employees and the IT experts may be located in different places. Many organizations
have embraced the internet of things and adopted it in various ways. These practices are all
aimed at improving the business value, which improves productivity (Xia, Yang, Wang & Vinel,
2012). This is done by producing more using less, meaning the production costs are lowered and
profit levels are raised. Some of the internet of things techniques adopted by many businesses is
the enabling of employees to work from their homes. The highly trained IT experts recruited by
these organizations to oversee cyber security on the companies’ sites face difficulties in
controlling the organizations’ system with the employees working at their home comfort zones
rather than at the workplace with the IT personnel which could have made it easier for them to
link the employees activities together and adequately control and protect them. The hackers or
rather the unauthorized personnel take the advantage of the difficulties associated with the work
from home technology and can break into the organizations’ sites and access the companies
valuable data or even their customers data and anything of interest to them. Through this, the
companies’ system may be tampered with and incur greater losses as even their accounts may be
deprived of money through the unauthorized access to their systems.
Most of the internet of things device, have security build around them instead of the
security being built directly into them. Direct building of security into the device before the
hardware implementation into the system improves the device protection and testing can be done
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 8
anytime, for the security. When the security is built around the device and a new hardware is
implemented into the system, then it becomes the target for hackers as they attempt to poke and
prove it weak. This means that the weak security may provide direct network access by the
unauthorized personnel. Building security around the internet of things devices instead of
building it directly into the devices therefore increases the chances of vulnerability to the
unauthorized personnel external attacks.
Most of the internet of things adoption is not regulated in many countries. As the internet
of things gains interest, majority of its activities which are adopted by many companies are not
regulated by the country’s laws. There is the general assumption by many governments around
the world that the internet of things is leading to technology advancements little do they consider
the repercussions associated with the same. Many companies have come up with manufactured
devices which violate the customers privacy as they are connected to the unprotected network
which can easily be accessed by unauthorized personnel and check their confidential
information. The manufacturers go a step further and put in place distortive terms of privacy on
their manufactured goods which cannot be understood by the average consumer who is of middle
level education which prevents the consumers from fighting for their rights in the court of law in
case the products compromise the expectations in future. Governments should intervene and put
in place rules and regulations governing the internet of things for consumer protection in terms
of maintaining their information confidential and secure from being accessed by unauthorized
personnel.
Internet of things compromises the privacy of individuals. Most of the public spaces are
fitted with monitoring devices in the name of security purposes. These devices record and store
anytime, for the security. When the security is built around the device and a new hardware is
implemented into the system, then it becomes the target for hackers as they attempt to poke and
prove it weak. This means that the weak security may provide direct network access by the
unauthorized personnel. Building security around the internet of things devices instead of
building it directly into the devices therefore increases the chances of vulnerability to the
unauthorized personnel external attacks.
Most of the internet of things adoption is not regulated in many countries. As the internet
of things gains interest, majority of its activities which are adopted by many companies are not
regulated by the country’s laws. There is the general assumption by many governments around
the world that the internet of things is leading to technology advancements little do they consider
the repercussions associated with the same. Many companies have come up with manufactured
devices which violate the customers privacy as they are connected to the unprotected network
which can easily be accessed by unauthorized personnel and check their confidential
information. The manufacturers go a step further and put in place distortive terms of privacy on
their manufactured goods which cannot be understood by the average consumer who is of middle
level education which prevents the consumers from fighting for their rights in the court of law in
case the products compromise the expectations in future. Governments should intervene and put
in place rules and regulations governing the internet of things for consumer protection in terms
of maintaining their information confidential and secure from being accessed by unauthorized
personnel.
Internet of things compromises the privacy of individuals. Most of the public spaces are
fitted with monitoring devices in the name of security purposes. These devices record and store

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 9
peoples data without their permission and knowledge. For example, the data that is collected by
fitness trackers is linked to the online user accounts. The information may be names, dates of
birth, and even the email addresses. The information collected and stored despite being
unprotected and vulnerable to cyber-attacks may be used in the ways the consumers or
individuals did not anticipate. This compromise the individuals’ privacy as their information can
be accessed by anyone and be used in various ways without their consent. People should be
aware of the various recording internet of things devices collecting their data and should provide
directives on how their data recorded should be used failure to which they have the option of
suing the other party in a court of law.
Positive impacts of the internet of things
Despite the fact that internet of things poses great risks on cyber security as it continues
to grow at a higher rate, it has some positive impacts too. Some of these impacts are witnessed as
businesses utilize them to maximize their profitability. Cisco Systems unveiled the following
positive impacts:
Internet of things improves efficiency in many businesses (Li & Tryfonas, 2016). Various
monotonous and vast data related tasks of an organization can be automated and be performed
and continuously monitored by machines. This helps an organization to improve the accuracy
with which it performs its tasks as the system errors can be detected and eradicated at early
stages. This enables the business organizations to save time as they improve their productivity
and also ensures that the employees within the organization are satisfied and retained for
continued business operations.
peoples data without their permission and knowledge. For example, the data that is collected by
fitness trackers is linked to the online user accounts. The information may be names, dates of
birth, and even the email addresses. The information collected and stored despite being
unprotected and vulnerable to cyber-attacks may be used in the ways the consumers or
individuals did not anticipate. This compromise the individuals’ privacy as their information can
be accessed by anyone and be used in various ways without their consent. People should be
aware of the various recording internet of things devices collecting their data and should provide
directives on how their data recorded should be used failure to which they have the option of
suing the other party in a court of law.
Positive impacts of the internet of things
Despite the fact that internet of things poses great risks on cyber security as it continues
to grow at a higher rate, it has some positive impacts too. Some of these impacts are witnessed as
businesses utilize them to maximize their profitability. Cisco Systems unveiled the following
positive impacts:
Internet of things improves efficiency in many businesses (Li & Tryfonas, 2016). Various
monotonous and vast data related tasks of an organization can be automated and be performed
and continuously monitored by machines. This helps an organization to improve the accuracy
with which it performs its tasks as the system errors can be detected and eradicated at early
stages. This enables the business organizations to save time as they improve their productivity
and also ensures that the employees within the organization are satisfied and retained for
continued business operations.

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 10
Internet of things improves the decision making process. The analysis of large data
enables the formulation of smart decisions (Karnouskos, 2011). Every decision made can be
attributed to the analysis results with minimum assumptions. Almost all the business aspects can
be evaluated based on the analyzed data. Better decisions made means that efficient production is
undertaken and thus minimizing the production costs. Also new ideas can be generated from the
analyzed data which can be in the form of forecasts from the analyzed data.
Internet of things enables business organizations to generate revenue (Jeschke, Brecher,
Meisen, Özdemir & Eschert, 2017). First the internet of things maximizes productivity by
lowering the expenses and improving efficiency. As the process continues and the business gets
used to the internet of things business operations, it can generate new functions which aid the
business in realizing more revenue. Those businesses which play it safe within the market by the
use of the internet of things and outdo their competitors generate more revenue and hence high
profits than the others.
Structured Analysis Techniques
Structured Analysis Techniques refers to notations in form of diagrams which are
designed to help people to descried and understand systems (Moran, 2010). This technique
allows the definition of the organization’s need for information technology developments for use
in industrial information systems, and to explain and to explain and show the manufacturing
processes and the procedures to be followed.
Force Field Analysis
This is a crucial analysis tool which is used for the understanding of the requirements for
change in various organizations (Thomas, 2013). It enables the analysts to properly investigate
Internet of things improves the decision making process. The analysis of large data
enables the formulation of smart decisions (Karnouskos, 2011). Every decision made can be
attributed to the analysis results with minimum assumptions. Almost all the business aspects can
be evaluated based on the analyzed data. Better decisions made means that efficient production is
undertaken and thus minimizing the production costs. Also new ideas can be generated from the
analyzed data which can be in the form of forecasts from the analyzed data.
Internet of things enables business organizations to generate revenue (Jeschke, Brecher,
Meisen, Özdemir & Eschert, 2017). First the internet of things maximizes productivity by
lowering the expenses and improving efficiency. As the process continues and the business gets
used to the internet of things business operations, it can generate new functions which aid the
business in realizing more revenue. Those businesses which play it safe within the market by the
use of the internet of things and outdo their competitors generate more revenue and hence high
profits than the others.
Structured Analysis Techniques
Structured Analysis Techniques refers to notations in form of diagrams which are
designed to help people to descried and understand systems (Moran, 2010). This technique
allows the definition of the organization’s need for information technology developments for use
in industrial information systems, and to explain and to explain and show the manufacturing
processes and the procedures to be followed.
Force Field Analysis
This is a crucial analysis tool which is used for the understanding of the requirements for
change in various organizations (Thomas, 2013). It enables the analysts to properly investigate
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 11
and understand the forces and the factors which are supportive or controversial to a given
outcome. This helps avoid premature judgment without having critically investigated the
scenario outcome or rather the scenario results in terms of its profitability or drawbacks. This
may also be termed as the feasibility study of a given scenario. By use of this analysis tool,
analysts can determine the strength and the weakness of the determinant factors and propose the
strategies to either reduce or improve the effects of the determinant factors. For a desired change
to be achieved, the equilibrium must be disrupted by either increasing or improving the
conditions favoring the change or reducing the restraining forces. There are always forces or
rather factors which strength the achievement of the desired change and those which weaken or
hinder the achievement of the same.
From the incident of HSBC bank DDoS attack and another same case witnessed in New
York Magazine in 2015 and besides the many cases IoT has been praised of, it can be considered
to have both positive and negative impacts on the cyber security. The negative impacts of the
internet of things on cyber security has been discussed above and the following factors have been
formulated; open debugging interfaces associated with most internet of things devices, the
adoption of the internet of things technology by businesses which has enabled employees to
work from their home challenges, most of the internet of things device have security build
around them instead of the security being built directly into them, lack of government laws to
regulate of the adoption of the internet of things technology by majority of businesses in various
countries and the compromise of individuals privacy by the internet of things. The positive
impact of the internet of things on businesses is that it enables them to improve their efficiency,
make better decisions and generate more revenue. From the formulated factors, the following
model has been generated to represent the scenario:
and understand the forces and the factors which are supportive or controversial to a given
outcome. This helps avoid premature judgment without having critically investigated the
scenario outcome or rather the scenario results in terms of its profitability or drawbacks. This
may also be termed as the feasibility study of a given scenario. By use of this analysis tool,
analysts can determine the strength and the weakness of the determinant factors and propose the
strategies to either reduce or improve the effects of the determinant factors. For a desired change
to be achieved, the equilibrium must be disrupted by either increasing or improving the
conditions favoring the change or reducing the restraining forces. There are always forces or
rather factors which strength the achievement of the desired change and those which weaken or
hinder the achievement of the same.
From the incident of HSBC bank DDoS attack and another same case witnessed in New
York Magazine in 2015 and besides the many cases IoT has been praised of, it can be considered
to have both positive and negative impacts on the cyber security. The negative impacts of the
internet of things on cyber security has been discussed above and the following factors have been
formulated; open debugging interfaces associated with most internet of things devices, the
adoption of the internet of things technology by businesses which has enabled employees to
work from their home challenges, most of the internet of things device have security build
around them instead of the security being built directly into them, lack of government laws to
regulate of the adoption of the internet of things technology by majority of businesses in various
countries and the compromise of individuals privacy by the internet of things. The positive
impact of the internet of things on businesses is that it enables them to improve their efficiency,
make better decisions and generate more revenue. From the formulated factors, the following
model has been generated to represent the scenario:
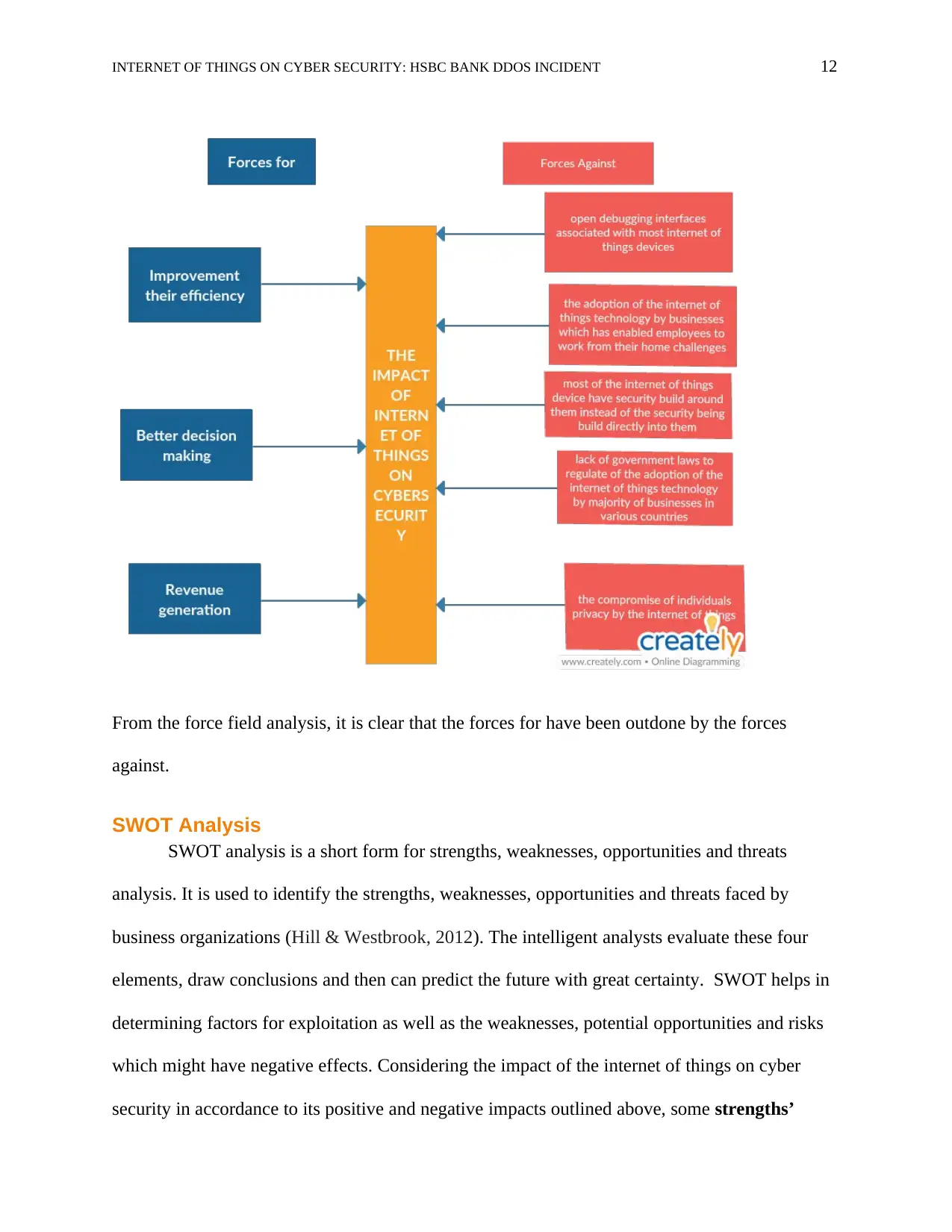
INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 12
From the force field analysis, it is clear that the forces for have been outdone by the forces
against.
SWOT Analysis
SWOT analysis is a short form for strengths, weaknesses, opportunities and threats
analysis. It is used to identify the strengths, weaknesses, opportunities and threats faced by
business organizations (Hill & Westbrook, 2012). The intelligent analysts evaluate these four
elements, draw conclusions and then can predict the future with great certainty. SWOT helps in
determining factors for exploitation as well as the weaknesses, potential opportunities and risks
which might have negative effects. Considering the impact of the internet of things on cyber
security in accordance to its positive and negative impacts outlined above, some strengths’
From the force field analysis, it is clear that the forces for have been outdone by the forces
against.
SWOT Analysis
SWOT analysis is a short form for strengths, weaknesses, opportunities and threats
analysis. It is used to identify the strengths, weaknesses, opportunities and threats faced by
business organizations (Hill & Westbrook, 2012). The intelligent analysts evaluate these four
elements, draw conclusions and then can predict the future with great certainty. SWOT helps in
determining factors for exploitation as well as the weaknesses, potential opportunities and risks
which might have negative effects. Considering the impact of the internet of things on cyber
security in accordance to its positive and negative impacts outlined above, some strengths’

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 13
which have greatly lead to the adoption of internet of things though faces serious cyber-attacks
are the efficiency in businesses production processes, aid in better decision making and
generation of higher levels of income. The weaknesses associated with the internet of things in
as much as cyber security is concerned is concerned are the open debugging interfaces associated
with the internet of things which poses great risks for attacks from the hackers, challenges in
security maintenance by the organizations’ IT experts since with the internet of things adoption
organizations make it possible for their employees to work from home, the building of security
around the internet of things rather than building it directly into the devices, lack of government
laws to regulate the internet of things adoption in various countries and the compromise of the
individuals privacy associated with the internet of things. The internet of things has a bright
future as it is being adopted by many businesses in their productivity and thus it has a great
opportunity for expansion. Internets of things have various threats considering its future. Hackers
can now illegally access the businesses and individuals crucial information, what about the future
lifetime when there will be many IoT devices connected to the internet which will not be easy to
manage? The following SWOT structure technique has been used to illustrate this case:
which have greatly lead to the adoption of internet of things though faces serious cyber-attacks
are the efficiency in businesses production processes, aid in better decision making and
generation of higher levels of income. The weaknesses associated with the internet of things in
as much as cyber security is concerned is concerned are the open debugging interfaces associated
with the internet of things which poses great risks for attacks from the hackers, challenges in
security maintenance by the organizations’ IT experts since with the internet of things adoption
organizations make it possible for their employees to work from home, the building of security
around the internet of things rather than building it directly into the devices, lack of government
laws to regulate the internet of things adoption in various countries and the compromise of the
individuals privacy associated with the internet of things. The internet of things has a bright
future as it is being adopted by many businesses in their productivity and thus it has a great
opportunity for expansion. Internets of things have various threats considering its future. Hackers
can now illegally access the businesses and individuals crucial information, what about the future
lifetime when there will be many IoT devices connected to the internet which will not be easy to
manage? The following SWOT structure technique has been used to illustrate this case:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
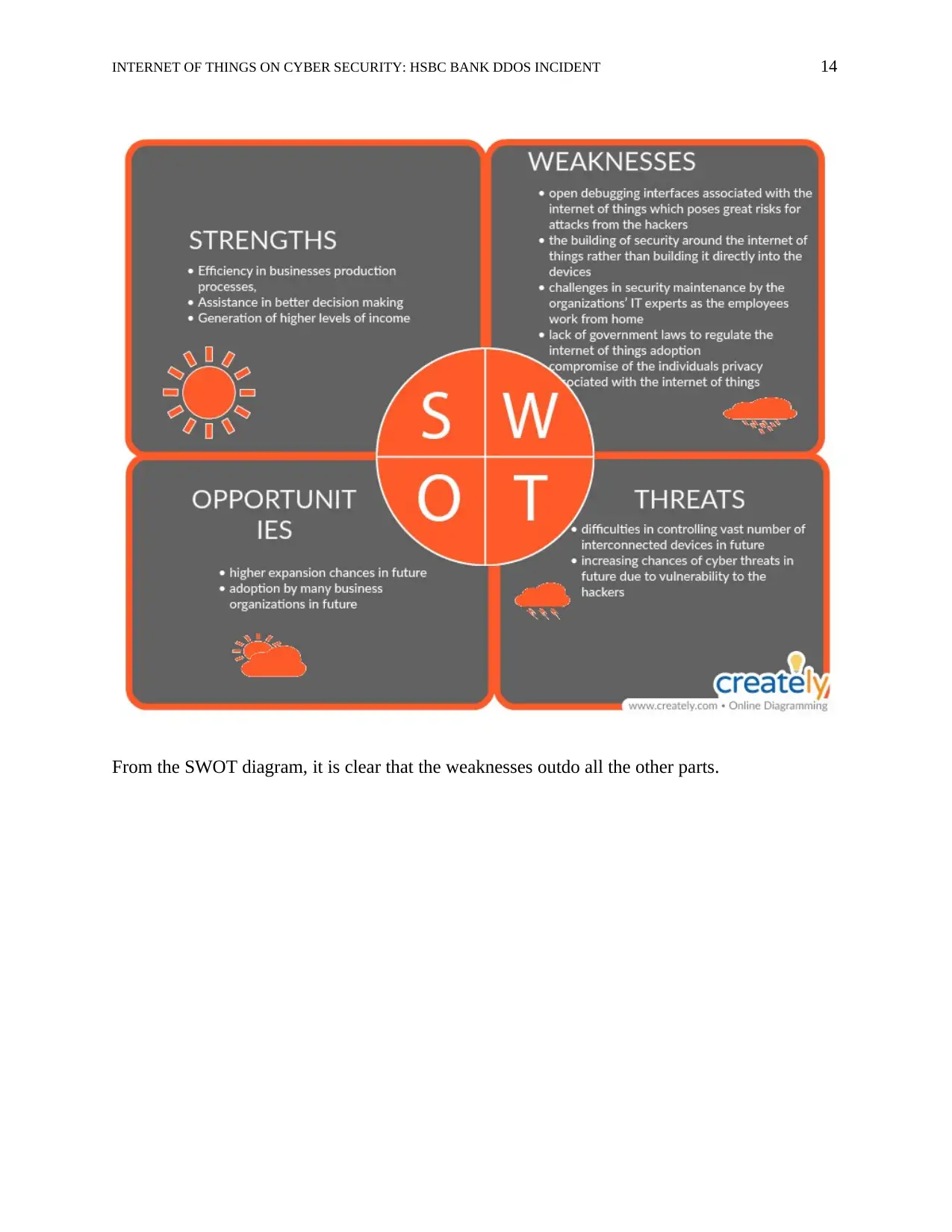
INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 14
From the SWOT diagram, it is clear that the weaknesses outdo all the other parts.
From the SWOT diagram, it is clear that the weaknesses outdo all the other parts.

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 15
Structured Brainstorming
Structured brainstorming is a process which involves a group of individuals who actively
contribute new ideas in an environment which is non-evaluative. This analysis tool is used by
many organizations to solve problems within the organization. The participants are provided
with guidelines with which to follow in the entire process. This analysis tool is of benefit to
organizations as it involves the collection of valuable ideas from all the team members
concerning a specific issue and also promotes equality with the organizations as each team
member gives an opinion which is respectable by all the other team members.
Steps to be followed
i. The objective is clearly stated. For our case, the main objective is to investigate
the impact of the internet of things on the cyber security. The Victims of the
HSBC bank DDoS attack should be aware of what is expected from them during
the session.
ii. All the participants are given a chance to give their ideas, for our case each team
member should give ideas of how he or she feels or thinks of the internet of things
affects the cyber security
iii. Every team member’s idea or suggestion should be highly respected without any
criticism
iv. The process is repeated until all the points are exhausted
v. A review of all the points is done and the duplicates are discarded.
Structured Brainstorming
Structured brainstorming is a process which involves a group of individuals who actively
contribute new ideas in an environment which is non-evaluative. This analysis tool is used by
many organizations to solve problems within the organization. The participants are provided
with guidelines with which to follow in the entire process. This analysis tool is of benefit to
organizations as it involves the collection of valuable ideas from all the team members
concerning a specific issue and also promotes equality with the organizations as each team
member gives an opinion which is respectable by all the other team members.
Steps to be followed
i. The objective is clearly stated. For our case, the main objective is to investigate
the impact of the internet of things on the cyber security. The Victims of the
HSBC bank DDoS attack should be aware of what is expected from them during
the session.
ii. All the participants are given a chance to give their ideas, for our case each team
member should give ideas of how he or she feels or thinks of the internet of things
affects the cyber security
iii. Every team member’s idea or suggestion should be highly respected without any
criticism
iv. The process is repeated until all the points are exhausted
v. A review of all the points is done and the duplicates are discarded.

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 16
Discussion of the findings
From the structural analysis of the impact of the internet of things on cyber security from
the HSBC bank incident, various factors were determined which either have negative or positive
impact on the cyber security (Byres & Lowe, 2014). The negative impacts of the internet of
things on the cyber security include the open debugging interfaces associated with the internet of
things which is used as an opportunity for attacks from the potential hackers, security
maintenance by the organizations’ IT experts is a challenge due to the fact that the internet of
things adoption organizations makes it possible for their employees to work from home and
hence are not near the IT experts to easily protect the companies’ sites, the building of security
around the internet of things rather than building it directly into the devices; the introduction of
the hardware with the security build around the internet of things devices is a potential loop hole
for the hackers to have access into the device’s information, lack of government laws to regulate
the internet of things adoption in various countries which may lead to customer rights violation
as they are not fairly treated and the compromise of the individuals privacy associated with the
internet of things as their data is collected without their knowledge and actually used for various
purpose without their consent.
Internet of things though poses great risks to the cyber security also positive impacts
business organizations’ productivity. Businesses can improve their efficiency in production by
automating the production process. This means that mistakes which may be present in the
production process are detected in earlier stages and corrected accordingly. The vast data
analysis associated with the internet of things provides basis for businesses to draw crucial
conclusions, make better decisions and predict the future with greater certainty. Businesses are
Discussion of the findings
From the structural analysis of the impact of the internet of things on cyber security from
the HSBC bank incident, various factors were determined which either have negative or positive
impact on the cyber security (Byres & Lowe, 2014). The negative impacts of the internet of
things on the cyber security include the open debugging interfaces associated with the internet of
things which is used as an opportunity for attacks from the potential hackers, security
maintenance by the organizations’ IT experts is a challenge due to the fact that the internet of
things adoption organizations makes it possible for their employees to work from home and
hence are not near the IT experts to easily protect the companies’ sites, the building of security
around the internet of things rather than building it directly into the devices; the introduction of
the hardware with the security build around the internet of things devices is a potential loop hole
for the hackers to have access into the device’s information, lack of government laws to regulate
the internet of things adoption in various countries which may lead to customer rights violation
as they are not fairly treated and the compromise of the individuals privacy associated with the
internet of things as their data is collected without their knowledge and actually used for various
purpose without their consent.
Internet of things though poses great risks to the cyber security also positive impacts
business organizations’ productivity. Businesses can improve their efficiency in production by
automating the production process. This means that mistakes which may be present in the
production process are detected in earlier stages and corrected accordingly. The vast data
analysis associated with the internet of things provides basis for businesses to draw crucial
conclusions, make better decisions and predict the future with greater certainty. Businesses are
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 17
also able to generate high revenue as they minimize production costs and outdo their
competitors.
Conclusion
The internet of things involves the connection of the physical devices to the internet for
easy and control of the activities involved. The process involves a vast number of devices linked
together for the exchange of data. With the internet of things, businesses can use the various
ways available to improve their value (Jing, Vasilakos, Wan, Lu & Qiu, 2014). Cisco unveiled
that this comes along with various negatives effects as the connectivity and the constant
exchange of data associated with the internet of things poses a great risk for the compromise of
the information. The major negative effects which act as a treat to the cyber security include the
open debugging interfaces associated with the internet of things which poses great risks for
attacks from the hackers, challenges in security maintenance by the organizations’ IT experts
since with the internet of things adoption organizations make it possible for their employees to
work from home, the building of security around the internet of things rather than building it
directly into the devices, lack of government laws to regulate the internet of things adoption in
various countries and the compromise of the individuals privacy associated with the internet of
things. The positive impacts of the internet of things on business organizations include the
efficiency in businesses production processes, assistance in better decision making and
generation of higher levels of income. Internet of things is gaining interest from various business
organizations as well as the individuals and is anticipated to raise rapidly in future hence posing
greater risks associated with the control of the many devices connected to the internet.
also able to generate high revenue as they minimize production costs and outdo their
competitors.
Conclusion
The internet of things involves the connection of the physical devices to the internet for
easy and control of the activities involved. The process involves a vast number of devices linked
together for the exchange of data. With the internet of things, businesses can use the various
ways available to improve their value (Jing, Vasilakos, Wan, Lu & Qiu, 2014). Cisco unveiled
that this comes along with various negatives effects as the connectivity and the constant
exchange of data associated with the internet of things poses a great risk for the compromise of
the information. The major negative effects which act as a treat to the cyber security include the
open debugging interfaces associated with the internet of things which poses great risks for
attacks from the hackers, challenges in security maintenance by the organizations’ IT experts
since with the internet of things adoption organizations make it possible for their employees to
work from home, the building of security around the internet of things rather than building it
directly into the devices, lack of government laws to regulate the internet of things adoption in
various countries and the compromise of the individuals privacy associated with the internet of
things. The positive impacts of the internet of things on business organizations include the
efficiency in businesses production processes, assistance in better decision making and
generation of higher levels of income. Internet of things is gaining interest from various business
organizations as well as the individuals and is anticipated to raise rapidly in future hence posing
greater risks associated with the control of the many devices connected to the internet.

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 18
References
Abomhara, M. (2015). Cyber security and the internet of things: vulnerabilities, threats, intruders
and attacks. Journal of Cyber Security and Mobility, 4(1), 65-88.
Brynielsson, J., Franke, U., & Varga, S. (2016). Cyber situational awareness testing.
In Combatting Cybercrime and Cyberterrorism (pp. 209-233). Springer, Cham.
Byres, E., & Lowe, J. (2014, October). The myths and facts behind cyber security risks for
industrial control systems. In Proceedings of the VDE Kongress (Vol. 116, pp. 213-218).
Chen, E. T. (2017). The Internet of Things: Opportunities, Issues, and Challenges. In The
Internet of Things in the Modern Business Environment (pp. 167-187). IGI Global.
Covington, M. J., & Carskadden, R. (2013, June). Threat implications of the internet of things.
In Cyber Conflict (CyCon), 2013 5th International Conference on (pp. 1-12). IEEE.
Elmaghraby, A. S., & Losavio, M. M. (2014). Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of advanced research, 5(4), 491-497.
Hill, T., & Westbrook, R. (2012). SWOT analysis: it's time for a product recall. Long range
planning, 30(1), 46-52.
Jeschke, S., Brecher, C., Meisen, T., Özdemir, D., & Eschert, T. (2017). Industrial internet of
things and cyber manufacturing systems. In Industrial Internet of Things (pp. 3-19).
Springer, Cham.
Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., & Qiu, D. (2014). Security of the Internet of Things:
perspectives and challenges. Wireless Networks, 20(8), 2481-2501.
References
Abomhara, M. (2015). Cyber security and the internet of things: vulnerabilities, threats, intruders
and attacks. Journal of Cyber Security and Mobility, 4(1), 65-88.
Brynielsson, J., Franke, U., & Varga, S. (2016). Cyber situational awareness testing.
In Combatting Cybercrime and Cyberterrorism (pp. 209-233). Springer, Cham.
Byres, E., & Lowe, J. (2014, October). The myths and facts behind cyber security risks for
industrial control systems. In Proceedings of the VDE Kongress (Vol. 116, pp. 213-218).
Chen, E. T. (2017). The Internet of Things: Opportunities, Issues, and Challenges. In The
Internet of Things in the Modern Business Environment (pp. 167-187). IGI Global.
Covington, M. J., & Carskadden, R. (2013, June). Threat implications of the internet of things.
In Cyber Conflict (CyCon), 2013 5th International Conference on (pp. 1-12). IEEE.
Elmaghraby, A. S., & Losavio, M. M. (2014). Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of advanced research, 5(4), 491-497.
Hill, T., & Westbrook, R. (2012). SWOT analysis: it's time for a product recall. Long range
planning, 30(1), 46-52.
Jeschke, S., Brecher, C., Meisen, T., Özdemir, D., & Eschert, T. (2017). Industrial internet of
things and cyber manufacturing systems. In Industrial Internet of Things (pp. 3-19).
Springer, Cham.
Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., & Qiu, D. (2014). Security of the Internet of Things:
perspectives and challenges. Wireless Networks, 20(8), 2481-2501.

INTERNET OF THINGS ON CYBER SECURITY: HSBC BANK DDOS INCIDENT 19
Karnouskos, S. (2011, July). Cyber-physical systems in the smartgrid. In Industrial Informatics
(INDIN), 2011 9th IEEE International Conference on (pp. 20-23). IEEE.
Li, S., Tryfonas, T., & Li, H. (2016). The Internet of Things: a security point of view. Internet
Research, 26(2), 337-359.
Moran, P. (2010). Structural vs. relational embeddedness: Social capital and managerial
performance. Strategic management journal, 26(12), 1129-1151.
Sadeghi, A. R., Wachsmann, C., & Waidner, M. (2015, June). Security and privacy challenges in
industrial internet of things. In Proceedings of the 52nd annual design automation
conference (p. 54). ACM.
Sicari, S., Rizzardi, A., Grieco, L. A., & Coen-Porisini, A. (2015). Security, privacy and trust in
Internet of Things: The road ahead. Computer networks, 76, 146-164.
Thomas, J. (2013). Force field analysis: A new way to evaluate your strategy. Long range
planning, 18(6), 54-59.
Vermesan, O., & Friess, P. (Eds.). (2013). Internet of things: converging technologies for smart
environments and integrated ecosystems. River Publishers.
Xia, F., Yang, L. T., Wang, L., & Vinel, A. (2012). Internet of things. International Journal of
Communication Systems, 25(9), 1101-1102.
Karnouskos, S. (2011, July). Cyber-physical systems in the smartgrid. In Industrial Informatics
(INDIN), 2011 9th IEEE International Conference on (pp. 20-23). IEEE.
Li, S., Tryfonas, T., & Li, H. (2016). The Internet of Things: a security point of view. Internet
Research, 26(2), 337-359.
Moran, P. (2010). Structural vs. relational embeddedness: Social capital and managerial
performance. Strategic management journal, 26(12), 1129-1151.
Sadeghi, A. R., Wachsmann, C., & Waidner, M. (2015, June). Security and privacy challenges in
industrial internet of things. In Proceedings of the 52nd annual design automation
conference (p. 54). ACM.
Sicari, S., Rizzardi, A., Grieco, L. A., & Coen-Porisini, A. (2015). Security, privacy and trust in
Internet of Things: The road ahead. Computer networks, 76, 146-164.
Thomas, J. (2013). Force field analysis: A new way to evaluate your strategy. Long range
planning, 18(6), 54-59.
Vermesan, O., & Friess, P. (Eds.). (2013). Internet of things: converging technologies for smart
environments and integrated ecosystems. River Publishers.
Xia, F., Yang, L. T., Wang, L., & Vinel, A. (2012). Internet of things. International Journal of
Communication Systems, 25(9), 1101-1102.
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





