Password Cracking with Hydra Tool
VerifiedAdded on 2020/11/23
|19
|1773
|353
Report
AI Summary
This assignment focuses on password cracking using the Hydra tool in Kali Linux. It explains how Hydra identifies vulnerable systems and utilizes wordlists to crack passwords. The document delves into the steps involved in launching a brute-force attack against an FTP server and provides examples of commands used with Hydra. Additionally, it explores alternative password cracking tools like John the Ripper and highlights the ethical considerations associated with these techniques.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

IT Security
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Introduction of Hydra- ....................................................................................................................3
Features of tool-...............................................................................................................................3
Technique used by tool to exploit vulnerabilities of information systematically............................4
CONCLUSION..............................................................................................................................15
REFERENCES..............................................................................................................................16
Introduction of Hydra- ....................................................................................................................3
Features of tool-...............................................................................................................................3
Technique used by tool to exploit vulnerabilities of information systematically............................4
CONCLUSION..............................................................................................................................15
REFERENCES..............................................................................................................................16

Introduction of Hydra-
Hydra is basically the well known or respected network that help for cracking the
password. It will support the different protocol such as FTP, telnet, subversion, POP3 and Fire-
bird etc. these are different type of protocol that help for hydra tool to manage their privacy and
security. This tool makes it possible for the purpose of security and researcher to show that how
it would be beneficial for gain the unauthorized access in the system remotely. Hydra is
generally brute forces cracking password tool in the term of information security. Password
cracking is methodology for guessing password from the database that store all information and
also transmit within network.
Hydra will support to the operating system that designed for the purpose of validation,
exploration and word net development (Geil and et.al., 2018). The word net is represented as
relational database that retrieve and manage the entire system in effective manner. This system is
beneficial for user to browse and edit large number of monolingual word nets at the time of
executions. This tool provides the user friendly graphical user interface with various option for
displaying the data.
Features of tool-
A software attack where attacker try to guess the password and crack the encrypted
password either the use of script and manually. A password is based on the technical secret string
of characters that applicable for authentication to gain the access of resources. It must bet kept in
the hidden and secret to other those who are not allowed to easily access the resources. Password
can be used for secure the data of computers and it is needed for maintaining and storing the
information in proper manner(Bada, Sasse and Nurse, 2019). Hydra is a tool that help for crack
the password of hardware and software system.
There are important features of hydra tool whereas multiple user access the information
effectively.
This tool is maintain the data in the database system so that it is automatically updated
which helps for user to easily access data at time.
This will perform the data consistency and complete verification of data. It also checks
the obligatory element of syn set that describe the relevant information.
Hydra is basically the well known or respected network that help for cracking the
password. It will support the different protocol such as FTP, telnet, subversion, POP3 and Fire-
bird etc. these are different type of protocol that help for hydra tool to manage their privacy and
security. This tool makes it possible for the purpose of security and researcher to show that how
it would be beneficial for gain the unauthorized access in the system remotely. Hydra is
generally brute forces cracking password tool in the term of information security. Password
cracking is methodology for guessing password from the database that store all information and
also transmit within network.
Hydra will support to the operating system that designed for the purpose of validation,
exploration and word net development (Geil and et.al., 2018). The word net is represented as
relational database that retrieve and manage the entire system in effective manner. This system is
beneficial for user to browse and edit large number of monolingual word nets at the time of
executions. This tool provides the user friendly graphical user interface with various option for
displaying the data.
Features of tool-
A software attack where attacker try to guess the password and crack the encrypted
password either the use of script and manually. A password is based on the technical secret string
of characters that applicable for authentication to gain the access of resources. It must bet kept in
the hidden and secret to other those who are not allowed to easily access the resources. Password
can be used for secure the data of computers and it is needed for maintaining and storing the
information in proper manner(Bada, Sasse and Nurse, 2019). Hydra is a tool that help for crack
the password of hardware and software system.
There are important features of hydra tool whereas multiple user access the information
effectively.
This tool is maintain the data in the database system so that it is automatically updated
which helps for user to easily access data at time.
This will perform the data consistency and complete verification of data. It also checks
the obligatory element of syn set that describe the relevant information.

Hydra is mainly coupled with the annotation tool chooser that has been successfully work
in proper manner. It is also used for the development of bulgarian wordnet (Mendoza,
2018).
User can easily access the proper validation queries to check the entire data effectively
and efficiently.
Hydra tool is test the local remote network, computers, server and other services form the
specified hardware or router on network (Zhang, 2018).
This type of tool check the reversed string, username and password. On the other hand, it
also helps for slow down the process of attackers on the network server.
Technique used by tool to exploit vulnerabilities of information systematically
Vulnerabilities are the weakness that can be exploited by the technology such as
unauthorized action, attacker within hardware system. Attacker can use the at least one technique
or tool to connect within the system weakness.
Exploiting vulnerabilities-
CSRF and Driven by pharming- It is based on web based attack to perform different
action within the sensitive information on the behalf of trusted user without having knowledge. It
is mainly possible when the request coming from browser of authenticated user is not verified
through website. It is concern about the protection and immediately applied on it. This technique
is wild drive through pharming attack (Björk, 2018). An email infected with the various type of
spam through text messages and files. This exploit consists of router request to web interface for
changing the Internet protocol association.
CSRF attack follows after clicked on the malicious link and other fake website. The
vulnerability is the most common issues in the implementation and it cannot be possible for user
to remove and eliminate unless the firmware update available.
UpnP (Universal plug and play)- It is based on the set of protocols that simplify
between the company and network devices such as routers, phones, access point and printers etc.
It is automatically specified the rules about to discover each other and also establish
communication between them (Chang, Zhong and Grabosky, 2018). This technique cannot be
offered the authentication services and does not perform the administrative actions. It only
rewrites the specification that included strong authentication method which based on temporary
in proper manner. It is also used for the development of bulgarian wordnet (Mendoza,
2018).
User can easily access the proper validation queries to check the entire data effectively
and efficiently.
Hydra tool is test the local remote network, computers, server and other services form the
specified hardware or router on network (Zhang, 2018).
This type of tool check the reversed string, username and password. On the other hand, it
also helps for slow down the process of attackers on the network server.
Technique used by tool to exploit vulnerabilities of information systematically
Vulnerabilities are the weakness that can be exploited by the technology such as
unauthorized action, attacker within hardware system. Attacker can use the at least one technique
or tool to connect within the system weakness.
Exploiting vulnerabilities-
CSRF and Driven by pharming- It is based on web based attack to perform different
action within the sensitive information on the behalf of trusted user without having knowledge. It
is mainly possible when the request coming from browser of authenticated user is not verified
through website. It is concern about the protection and immediately applied on it. This technique
is wild drive through pharming attack (Björk, 2018). An email infected with the various type of
spam through text messages and files. This exploit consists of router request to web interface for
changing the Internet protocol association.
CSRF attack follows after clicked on the malicious link and other fake website. The
vulnerability is the most common issues in the implementation and it cannot be possible for user
to remove and eliminate unless the firmware update available.
UpnP (Universal plug and play)- It is based on the set of protocols that simplify
between the company and network devices such as routers, phones, access point and printers etc.
It is automatically specified the rules about to discover each other and also establish
communication between them (Chang, Zhong and Grabosky, 2018). This technique cannot be
offered the authentication services and does not perform the administrative actions. It only
rewrites the specification that included strong authentication method which based on temporary
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

solution for user and consider to the disable flash in browsers. In this way, it exploits the UpnP
voluntaries without using the flash.
Experimental set up and evidence of usage of tool
Hydra is available form different website to easily install ans setup hydra and SQL database
manually(ChangKuhn and Weil, 2018). Hydra is basically helped for auditor that find out the
weak password in the client server. There are some important point that performed different
function when using the hydra:
Make the network become secure as possible
Test the setup of network
Test the setup of server
Configure the services
Configure the ACL
Choose the strong password
Used SSL
Use the Cryptography algorithm
Used IDS Throw the hydra against security aspect and also try to check the commands.
For Example-
This is using command line to run the proper command to perform the executions.
Python hydra.py
This is the example to show that how to run the hydra in the kali linux environment and assume
that hydra is also located in the home/ user/ hydra on the computer machine.
1. In the local directory, hydra is executable file that store in hydra.Py :
user@machine:~/hydra$ python hydra.py
2. It is also using the full path to execute file:
user@machine:~$ python /home/user/hydra/hydra.py
3. It can be used the relative path of hydra
user@machine:~$ python hydra/hydra.py
voluntaries without using the flash.
Experimental set up and evidence of usage of tool
Hydra is available form different website to easily install ans setup hydra and SQL database
manually(ChangKuhn and Weil, 2018). Hydra is basically helped for auditor that find out the
weak password in the client server. There are some important point that performed different
function when using the hydra:
Make the network become secure as possible
Test the setup of network
Test the setup of server
Configure the services
Configure the ACL
Choose the strong password
Used SSL
Use the Cryptography algorithm
Used IDS Throw the hydra against security aspect and also try to check the commands.
For Example-
This is using command line to run the proper command to perform the executions.
Python hydra.py
This is the example to show that how to run the hydra in the kali linux environment and assume
that hydra is also located in the home/ user/ hydra on the computer machine.
1. In the local directory, hydra is executable file that store in hydra.Py :
user@machine:~/hydra$ python hydra.py
2. It is also using the full path to execute file:
user@machine:~$ python /home/user/hydra/hydra.py
3. It can be used the relative path of hydra
user@machine:~$ python hydra/hydra.py

Installing hydra tool-
Hydra is mainly pre-install on the kali linux operating system which many differ from other
operation system because it can support to the different platform such as
Unix – Linux, Solaris
Windows with Cygwin
Mobile system which based on the linux, Qnx (iPhone, Android and iPaq)
It is necessary to download, configure, compile or install with the help for proper command on
the system.
Use link- Http://github.com/vanhauser-thc/ thc-hydra.git cd thc-hydra./ configure
make
install
It is needed for some dependency libraries:
apt install libssl-dev libssh-dev libidn11-dev libpcre3-dev libgtk2.0-dev libmysqlclient-dev
libpq-dev libsvn-dev firebird-dev libncp-dev
Usage of Hydra-
After successfully installed hydra, it can be use the hydra tool to run the command on the
terminal by manually.
For CLI: hydra
For CLI-wizard: hydra Wizard
For GUI:
xhydra
Hydra is mainly pre-install on the kali linux operating system which many differ from other
operation system because it can support to the different platform such as
Unix – Linux, Solaris
Windows with Cygwin
Mobile system which based on the linux, Qnx (iPhone, Android and iPaq)
It is necessary to download, configure, compile or install with the help for proper command on
the system.
Use link- Http://github.com/vanhauser-thc/ thc-hydra.git cd thc-hydra./ configure
make
install
It is needed for some dependency libraries:
apt install libssl-dev libssh-dev libidn11-dev libpcre3-dev libgtk2.0-dev libmysqlclient-dev
libpq-dev libsvn-dev firebird-dev libncp-dev
Usage of Hydra-
After successfully installed hydra, it can be use the hydra tool to run the command on the
terminal by manually.
For CLI: hydra
For CLI-wizard: hydra Wizard
For GUI:
xhydra
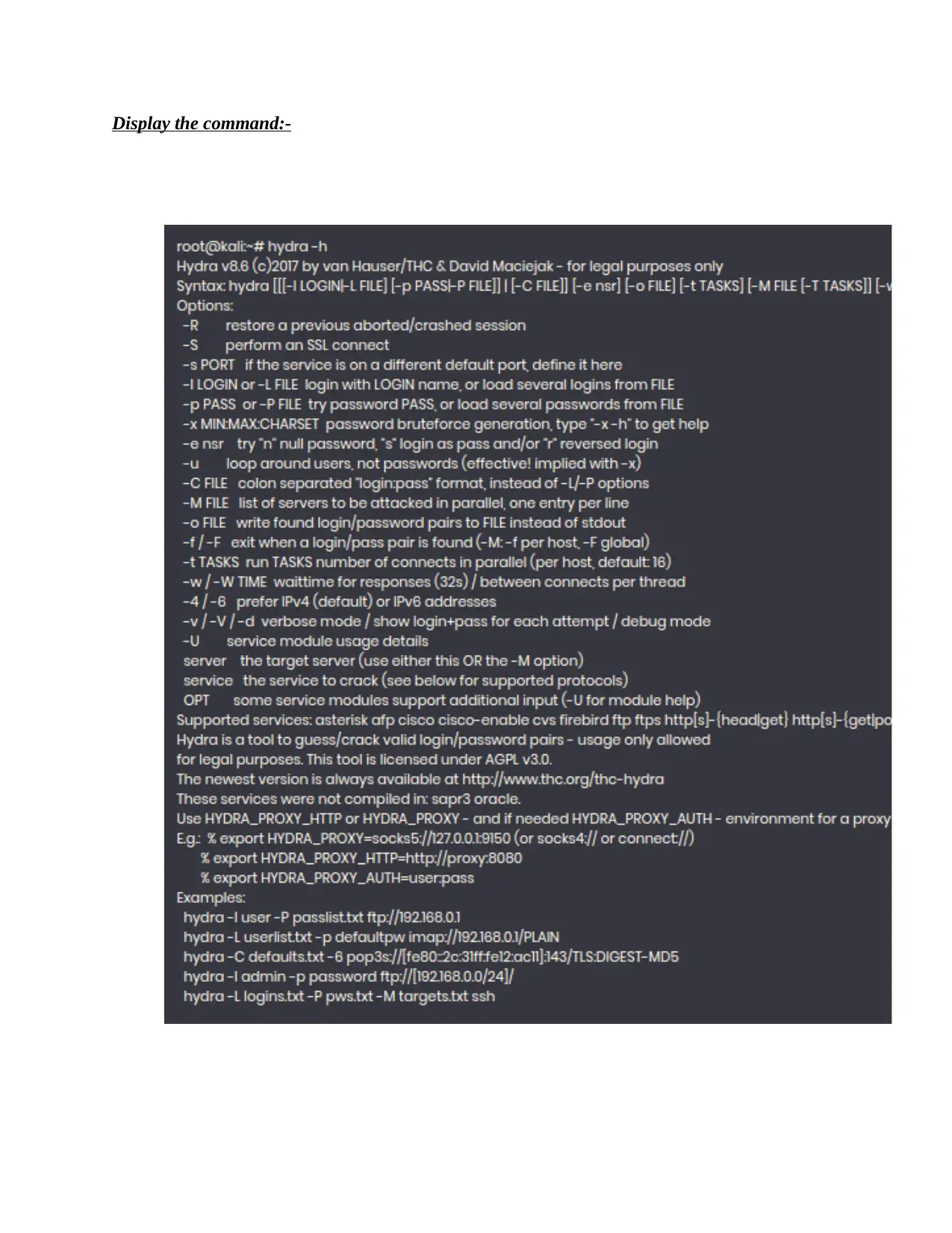
Display the command:-
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Hydra tool is supported the brute-force services which help for login form through web based
such as social media login, router login and banking login etc. It also handles the request through
HTTP{s} {get post}- form.
such as social media login, router login and banking login etc. It also handles the request through
HTTP{s} {get post}- form.
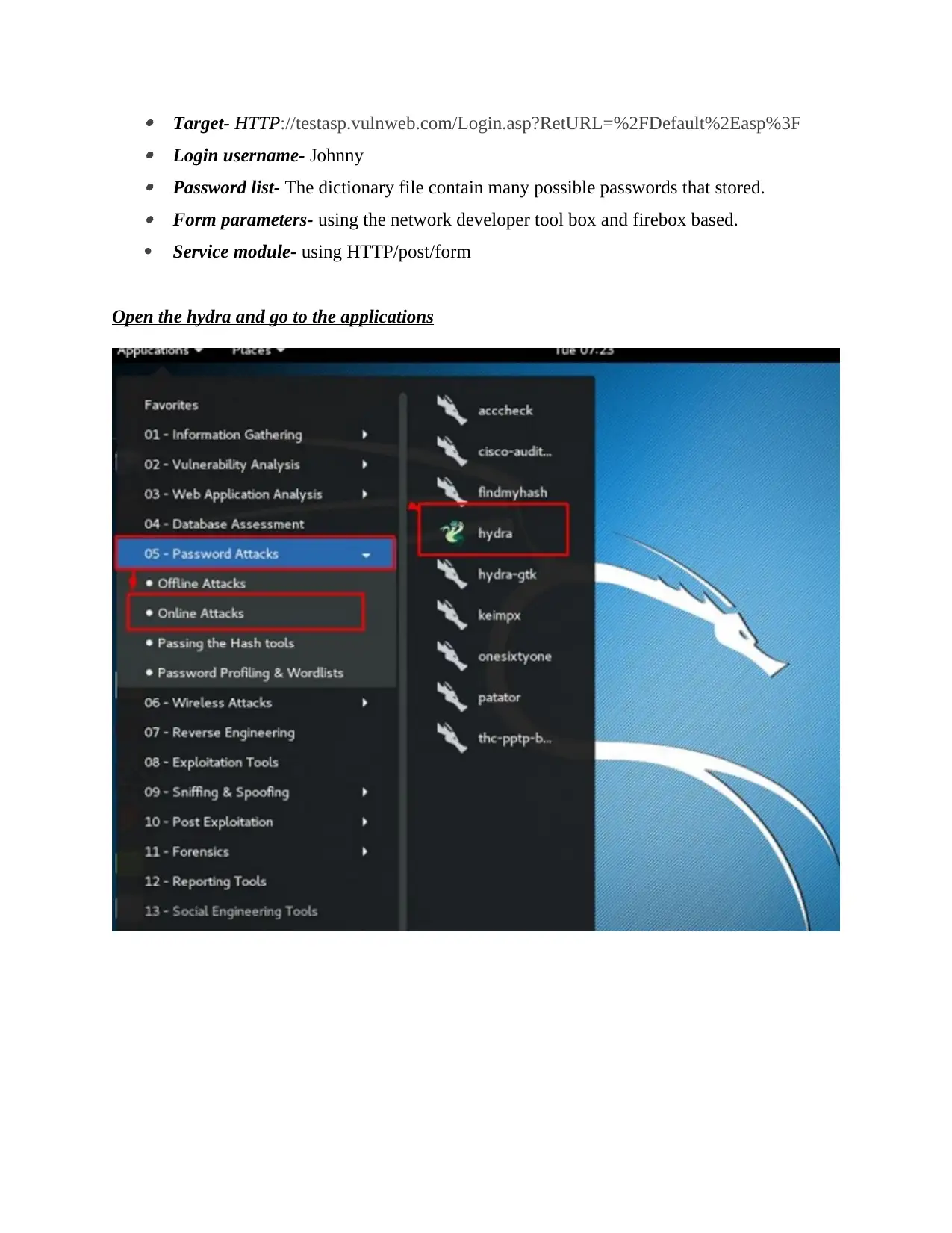
Target- HTTP://testasp.vulnweb.com/Login.asp?RetURL=%2FDefault%2Easp%3F Login username- Johnny Password list- The dictionary file contain many possible passwords that stored. Form parameters- using the network developer tool box and firebox based.
Service module- using HTTP/post/form
Open the hydra and go to the applications
Service module- using HTTP/post/form
Open the hydra and go to the applications

It also open the terminal of command console:
In case, we will use the brute force FTP service in the machines
IP address : 193.168.1.101
It also created a kali word file that shows path : user/ share/ word-list/metasploit:
In case, we will use the brute force FTP service in the machines
IP address : 193.168.1.101
It also created a kali word file that shows path : user/ share/ word-list/metasploit:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Afterwards, it follows the command to identify that password of file that created by kali.
Hydra – user/share/wordlist/ metasploit / user- -
/user/share/wordlists/ metasploit/ pass ftp :// 192.168.1.101 – v
At last, the password has been found .
Hydra – user/share/wordlist/ metasploit / user- -
/user/share/wordlists/ metasploit/ pass ftp :// 192.168.1.101 – v
At last, the password has been found .
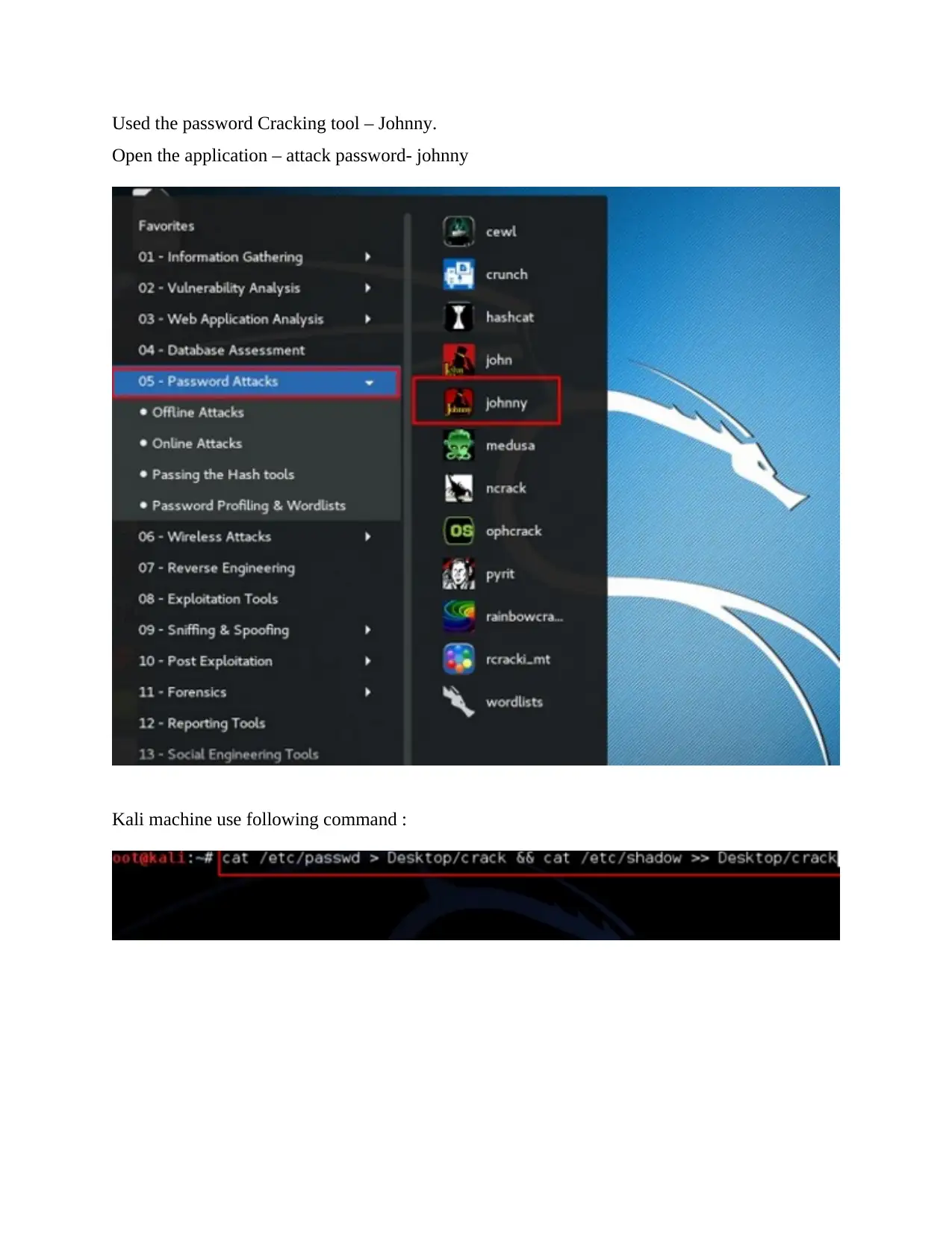
Used the password Cracking tool – Johnny.
Open the application – attack password- johnny
Kali machine use following command :
Open the application – attack password- johnny
Kali machine use following command :

Open the password file in the followings ways:
Click on the attack button:
Click on the attack button:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Complete the execution process of attack.

CONCLUSION
As per discussion, it concluded that kali linux is used the hydra tool for the purpose of
password cracking. It is described the entire features of hydra tool and how they efficient of
identifying the confidential information of website and users. It summarized the technology that
used hydra for the purpose to exploit the vulnerabilities in the term of information
systematically.
As per discussion, it concluded that kali linux is used the hydra tool for the purpose of
password cracking. It is described the entire features of hydra tool and how they efficient of
identifying the confidential information of website and users. It summarized the technology that
used hydra for the purpose to exploit the vulnerabilities in the term of information
systematically.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and journals
Bada, M., Sasse, A.M. and Nurse, J.R., 2019. Cyber security awareness campaigns: Why do they
fail to change behaviour?. arXiv preprint arXiv:1901.02672.
Björk, L., 2018. Writing a Best Current Practice about security in an already established network
design.
Chang, L.Y., Zhong, L.Y. and Grabosky, P.N., 2018. Citizen co‐production of cyber security:
Self‐help, vigilantes, and cybercrime. Regulation & Governance, 12(1), pp.101-114.
Chang, M., Kuhn, R. and Weil, T., 2018. Cyberthreats and Security. IT Professional, 20(3).
pp.20-22.
Geil, A., Sagers, G., Spaulding, A.D. and Wolf, J.R., 2018. Cyber security on the farm: an
assessment of cyber security practices in the United States agriculture
industry. International Food and Agribusiness Management Review, 21(3). pp.317-334.
Mendoza, I.E., 2018. Information Security Management as a Business Strategy and Its Financial
Impact. In Economic Growth in Latin America and the Impact of the Global Financial
Crisis (pp. 73-93). IGI Global.
Zhang, D., 2018, October. Big data security and privacy protection. In 8th International
Conference on Management and Computer Science (ICMCS 2018). Atlantis Press.
Books and journals
Bada, M., Sasse, A.M. and Nurse, J.R., 2019. Cyber security awareness campaigns: Why do they
fail to change behaviour?. arXiv preprint arXiv:1901.02672.
Björk, L., 2018. Writing a Best Current Practice about security in an already established network
design.
Chang, L.Y., Zhong, L.Y. and Grabosky, P.N., 2018. Citizen co‐production of cyber security:
Self‐help, vigilantes, and cybercrime. Regulation & Governance, 12(1), pp.101-114.
Chang, M., Kuhn, R. and Weil, T., 2018. Cyberthreats and Security. IT Professional, 20(3).
pp.20-22.
Geil, A., Sagers, G., Spaulding, A.D. and Wolf, J.R., 2018. Cyber security on the farm: an
assessment of cyber security practices in the United States agriculture
industry. International Food and Agribusiness Management Review, 21(3). pp.317-334.
Mendoza, I.E., 2018. Information Security Management as a Business Strategy and Its Financial
Impact. In Economic Growth in Latin America and the Impact of the Global Financial
Crisis (pp. 73-93). IGI Global.
Zhang, D., 2018, October. Big data security and privacy protection. In 8th International
Conference on Management and Computer Science (ICMCS 2018). Atlantis Press.


1
1 out of 19
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)





