ITC 596 - IT Risk Assessment in Aztech Corporation: BYOD Impact
VerifiedAdded on 2020/04/07
|11
|4779
|90
Report
AI Summary
This report presents a comprehensive IT risk assessment conducted on Aztech Corporation, focusing on the implications of a proposed BYOD (Bring Your Own Device) project within its financial services operations. The assessment analyzes the potential risks associated with data security, legal frameworks, financial dimensions, and compliance with government regulations, particularly in the context of the Australian financial sector. The report highlights the importance of IT infrastructure in modern organizations, emphasizing the need for accuracy, precision, and the adoption of technologies like ERP systems, cloud computing, and secure payment gateways. It reviews the project's impact on Aztech's current security posture, addressing legal implications under the Australian Act of Freedom to Information, and assessing the challenges of BYOD implementation, including device compatibility, policy development, and mutual agreements between the company and its employees. The assessment identifies data security as the most vulnerable risk, emphasizing the need for stringent policies to protect sensitive information. The report also discusses the advantages of BYOD, such as cost reduction and operational flexibility, while acknowledging the increased risks it introduces.

ITC 596 – IT RISK ASSESSMENT in AZTECH CORPORATION
NAME
UNIVERSITY
ROLL NO
ASSESSMENT TITLE
NAME
UNIVERSITY
ROLL NO
ASSESSMENT TITLE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RUNNING HEAD: IT Risk Assessment in Aztech
EXECUTIVE SUMMARY
The following report is represented in the form of a risk assessment performed on the IT
department of Aztech with respect to the project proposal given by strategist to deploy the
BYOD within Aztech’s workplace environment. The report is generated post-consideration of a
collection of project portfolios in the hands of senior executives. Risk assessment has been
conducted keeping in mind the nature of industry the company operates in and its workforce
strength. The assessment also covers the legal frameworks, financial dimensions and security
concerns over the use of “Bring Your Own Device” while identifying the potential risks that can
hamper the company’s survival in the long run. To summarise the above points, the evaluation
has identified the risk of data security as the most vulnerable one in the entire risk domain for
companies operating within financial service sector.
PROJECT’S REVIEW BASED ON FINANCIAL ASPECTS AND GOVERNMENTAL REGULATIONS
The modern organisations that operate in the 21st century have seen a lot of advancements in
the field of Information and Communication technology. The ICT has been used extensively in
various areas to make the business processes easier to conduct. Almost all the private and
government sectors have adopted a series of IT applications and system software to facilitate
their day-to-day departmental operations and improve the efficiency of whatever they carry
out. The adoption has also been international and this thing get complicated with a lots of
integrated functionalities associated with a single IT infrastructure. In the private organisations
that offer financial services, accuracy and precision with numerical figures become highly
significant because the same yields productivity for clients. For getting calculative and keeping
electronic records of everything, the organisational departments use the Enterprise Resource
Planning or the ERP methods, cloud computation, tools & utilities for data analytics, secured or
encrypted gateways for money transactions, digitized communication, integration of different
software for coordinated operations and many more things. A well-recognised use of IT
applications can be observed in place where the investment options are dematerialized. It has
provided a successful dimension for the relevant industry. All Australian organisations that offer
financial services have emerged as strong portion of the country’s economy for years. This is
evident from the way organisations could face the global financial crisis between the year 2008
and 2011. These organisations have already developed high degree of readiness for meeting
the present regulations and technological barriers of the present century. Additionally the
environmental challenges are also offered through stringent standards and regulatory bodies. It
becomes an obligation to demonstrate higher degree of compliance with the government as
well as the society when the demographic and cultural dimensions witness quick changes.
Technological trends make way for modified rules and regulations on the use of social media,
platforms utilized in cell phones, data security, system changes at the core-level etc. Thus, the
risk assessment of financial service providers in Australia becomes tough to conduct because
multiple changes at once (Saini, et al 2011).
EXECUTIVE SUMMARY
The following report is represented in the form of a risk assessment performed on the IT
department of Aztech with respect to the project proposal given by strategist to deploy the
BYOD within Aztech’s workplace environment. The report is generated post-consideration of a
collection of project portfolios in the hands of senior executives. Risk assessment has been
conducted keeping in mind the nature of industry the company operates in and its workforce
strength. The assessment also covers the legal frameworks, financial dimensions and security
concerns over the use of “Bring Your Own Device” while identifying the potential risks that can
hamper the company’s survival in the long run. To summarise the above points, the evaluation
has identified the risk of data security as the most vulnerable one in the entire risk domain for
companies operating within financial service sector.
PROJECT’S REVIEW BASED ON FINANCIAL ASPECTS AND GOVERNMENTAL REGULATIONS
The modern organisations that operate in the 21st century have seen a lot of advancements in
the field of Information and Communication technology. The ICT has been used extensively in
various areas to make the business processes easier to conduct. Almost all the private and
government sectors have adopted a series of IT applications and system software to facilitate
their day-to-day departmental operations and improve the efficiency of whatever they carry
out. The adoption has also been international and this thing get complicated with a lots of
integrated functionalities associated with a single IT infrastructure. In the private organisations
that offer financial services, accuracy and precision with numerical figures become highly
significant because the same yields productivity for clients. For getting calculative and keeping
electronic records of everything, the organisational departments use the Enterprise Resource
Planning or the ERP methods, cloud computation, tools & utilities for data analytics, secured or
encrypted gateways for money transactions, digitized communication, integration of different
software for coordinated operations and many more things. A well-recognised use of IT
applications can be observed in place where the investment options are dematerialized. It has
provided a successful dimension for the relevant industry. All Australian organisations that offer
financial services have emerged as strong portion of the country’s economy for years. This is
evident from the way organisations could face the global financial crisis between the year 2008
and 2011. These organisations have already developed high degree of readiness for meeting
the present regulations and technological barriers of the present century. Additionally the
environmental challenges are also offered through stringent standards and regulatory bodies. It
becomes an obligation to demonstrate higher degree of compliance with the government as
well as the society when the demographic and cultural dimensions witness quick changes.
Technological trends make way for modified rules and regulations on the use of social media,
platforms utilized in cell phones, data security, system changes at the core-level etc. Thus, the
risk assessment of financial service providers in Australia becomes tough to conduct because
multiple changes at once (Saini, et al 2011).

RUNNING HEAD: IT Risk Assessment in Aztech
It was highly recommended by Drucker, the notable man behind management principles that
business organisations of any size should analyse the market and anticipate the potential
changes that could either lift or decline their current rate of commercial success. He
emphasised on capitalizing on the opportunities so that any type of business project can be
effectively executed. This report is designed to carry out an analysis of the risks and
opportunities associated with the previously mentioned IT project in Aztek Corporation which
operates in the financial service sector of Australia.
Background to the Case Study
Aztech Corporation holds the position as one of the leading organisations in Australian Financial
market. After its incorporation in the year 1960, it established its corporate office in the district
of Sydney and the office soon became operational. The business firm deals in an extended
range of financial services which includes primarily general and life insurances. It also offers
investment products to retailers and other members of corporations who are active in equity
and debt business. Apart from that, it also has a wide range of mortgage and loan services for
specific consumers who comprise a dominant part of its Aztech’s product segment. Presently,
the company owns 20 regional offices where over a thousand employees have been working.
As of the year 2014, the company has a fair reputation in financial sector of Australia and is on
the progress of achieving high CSR or Corporate Social Responsibility in its operational regions.
The reaction of the company to capricious changes in the IT infrastructure and trends has been
proactive since it develops and upgrades its applications to meet the extended requirements
from time to time. Aztech became the first of its kind to introduce the online payment services
in the year 1999 by featuring secured and gateways that are end-to-end encrypted.
Introduction of payment gateways was a convenient factor for the investors who could execute
their business affairs from any location without facing geographical barriers. When the
company introduced the SAP Enterprise Resource Planning systems in the year 2005, things
took a slanted direction and the firm started observing increased efficiency of
interdepartmental functions. Aztech’s segment of business and its administrative offices were
linked together based on a real time environment. Its operations became more transparent
thus creating higher appeals to clients hailing from corporate and retail sectors.
Aztech’s official website is secured and requires both its clients and its employees to register
themselves with the site. While the clients and employees are remotely located at their
respective places, their system IP’s are tracked by the ERP system incorporated within the
organisation’s main server. The login information of employees is recorded for attendance
purposes once they access their registered accounts. The application software installed in each
of the employee’s and client’s systems is designed to filter the users by means of a distinctive
passcode. For instance, the interface present inside a client’s system or an employee’s system
would not allow the data regarding loan products to be accessed by someone who is associated
with the department of insurance.
It was highly recommended by Drucker, the notable man behind management principles that
business organisations of any size should analyse the market and anticipate the potential
changes that could either lift or decline their current rate of commercial success. He
emphasised on capitalizing on the opportunities so that any type of business project can be
effectively executed. This report is designed to carry out an analysis of the risks and
opportunities associated with the previously mentioned IT project in Aztek Corporation which
operates in the financial service sector of Australia.
Background to the Case Study
Aztech Corporation holds the position as one of the leading organisations in Australian Financial
market. After its incorporation in the year 1960, it established its corporate office in the district
of Sydney and the office soon became operational. The business firm deals in an extended
range of financial services which includes primarily general and life insurances. It also offers
investment products to retailers and other members of corporations who are active in equity
and debt business. Apart from that, it also has a wide range of mortgage and loan services for
specific consumers who comprise a dominant part of its Aztech’s product segment. Presently,
the company owns 20 regional offices where over a thousand employees have been working.
As of the year 2014, the company has a fair reputation in financial sector of Australia and is on
the progress of achieving high CSR or Corporate Social Responsibility in its operational regions.
The reaction of the company to capricious changes in the IT infrastructure and trends has been
proactive since it develops and upgrades its applications to meet the extended requirements
from time to time. Aztech became the first of its kind to introduce the online payment services
in the year 1999 by featuring secured and gateways that are end-to-end encrypted.
Introduction of payment gateways was a convenient factor for the investors who could execute
their business affairs from any location without facing geographical barriers. When the
company introduced the SAP Enterprise Resource Planning systems in the year 2005, things
took a slanted direction and the firm started observing increased efficiency of
interdepartmental functions. Aztech’s segment of business and its administrative offices were
linked together based on a real time environment. Its operations became more transparent
thus creating higher appeals to clients hailing from corporate and retail sectors.
Aztech’s official website is secured and requires both its clients and its employees to register
themselves with the site. While the clients and employees are remotely located at their
respective places, their system IP’s are tracked by the ERP system incorporated within the
organisation’s main server. The login information of employees is recorded for attendance
purposes once they access their registered accounts. The application software installed in each
of the employee’s and client’s systems is designed to filter the users by means of a distinctive
passcode. For instance, the interface present inside a client’s system or an employee’s system
would not allow the data regarding loan products to be accessed by someone who is associated
with the department of insurance.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RUNNING HEAD: IT Risk Assessment in Aztech
By accessing the company’s primary website, a registered user can have access to relevant
information pertaining to investments and loan products. He/she can also do purchasing on the
same platform without needing the employees to get involved. The process is quite automated
but the same is made possible because of a series of interconnected software, database and
payment gateways that make registration and online transactions possible.
The rules and regulations laid down by the Australian government comes into play in the trade
cycle around each kind of investment and the trade & business policies are defined separately
for each of the investment option. The differences in rules are as per the legislation drafted by
the Australian Commission of Securities and Investments. The transactions of various clients in
Aztech are carried out the company’s concerned IT department by means of virtual
management. The registered bank account of each client is linked to his/her respective
dematerialization account. This provides the clients with suitable interface for making
investments in various financial instruments from their personal locations.
Even with such smoothness of virtual operations, the overall IT infrastructure of the company is
kept simple for attracting large number of retail and corporate investors. Indeed, it is a well-
known fact that technical complexities even on a computer screen can turn down prospects
because of individual’s apprehension of financial losses. On the other hand, application
software that provides a friendly interface and easily understandable functionalities is likely to
appeal to any client. Aztech has its own dedicated department for resolving the customer
grievances and responding to their business-related queries. The Customer Service Executives
provide real-time support by means of telephonic conversation and the voice interactions are
stored securely as digital data in the company’s database. The organisation’s website meant for
online trading is kept updated on hourly basis for delivering real-time information related to
exchanges and buying & selling values of different commodities that are traded. To remain
competitive in today’s global arena, it is highly expected of an organisation to have a
competitive IT infrastructure and professionals (Campbell, et al 2010).
IMPACT OF PROJECT ON THE CURRENT SECURITY POSTURE OF AZTEC
The BYOD project proposed by strategist refers to the concept of “Bring Your Own Device”. It
implies that the employees of an organisation can bring their own personal devices to the
workplace for accomplishing their assigned jobs. These devices may include the personal
laptops, cell phones, PDAs, tablets or any other device that supports an interface for office
works. In case of Aztech, the works correspond to trading, business analytics, database
management and handling of transactions. Several companies around the globe have already
adopted such an idea in their workplaces. The thing to notice is that the personal devices act as
the sole devices that their respective owners rely upon. However, this does not lower the
essence of virtually located applications because devices only act as individual hardware. There
is always an underlying need of integrating these personal devices with the ERP applications
that support the business activities. Precisely, employees are only advantaged in accessing the
virtual intranet or extranet of a corporation through their personal devices (Leavitt, 2013).
By accessing the company’s primary website, a registered user can have access to relevant
information pertaining to investments and loan products. He/she can also do purchasing on the
same platform without needing the employees to get involved. The process is quite automated
but the same is made possible because of a series of interconnected software, database and
payment gateways that make registration and online transactions possible.
The rules and regulations laid down by the Australian government comes into play in the trade
cycle around each kind of investment and the trade & business policies are defined separately
for each of the investment option. The differences in rules are as per the legislation drafted by
the Australian Commission of Securities and Investments. The transactions of various clients in
Aztech are carried out the company’s concerned IT department by means of virtual
management. The registered bank account of each client is linked to his/her respective
dematerialization account. This provides the clients with suitable interface for making
investments in various financial instruments from their personal locations.
Even with such smoothness of virtual operations, the overall IT infrastructure of the company is
kept simple for attracting large number of retail and corporate investors. Indeed, it is a well-
known fact that technical complexities even on a computer screen can turn down prospects
because of individual’s apprehension of financial losses. On the other hand, application
software that provides a friendly interface and easily understandable functionalities is likely to
appeal to any client. Aztech has its own dedicated department for resolving the customer
grievances and responding to their business-related queries. The Customer Service Executives
provide real-time support by means of telephonic conversation and the voice interactions are
stored securely as digital data in the company’s database. The organisation’s website meant for
online trading is kept updated on hourly basis for delivering real-time information related to
exchanges and buying & selling values of different commodities that are traded. To remain
competitive in today’s global arena, it is highly expected of an organisation to have a
competitive IT infrastructure and professionals (Campbell, et al 2010).
IMPACT OF PROJECT ON THE CURRENT SECURITY POSTURE OF AZTEC
The BYOD project proposed by strategist refers to the concept of “Bring Your Own Device”. It
implies that the employees of an organisation can bring their own personal devices to the
workplace for accomplishing their assigned jobs. These devices may include the personal
laptops, cell phones, PDAs, tablets or any other device that supports an interface for office
works. In case of Aztech, the works correspond to trading, business analytics, database
management and handling of transactions. Several companies around the globe have already
adopted such an idea in their workplaces. The thing to notice is that the personal devices act as
the sole devices that their respective owners rely upon. However, this does not lower the
essence of virtually located applications because devices only act as individual hardware. There
is always an underlying need of integrating these personal devices with the ERP applications
that support the business activities. Precisely, employees are only advantaged in accessing the
virtual intranet or extranet of a corporation through their personal devices (Leavitt, 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RUNNING HEAD: IT Risk Assessment in Aztech
The concept of BYOD has three critical dimensions that need compliance for such kind of
projects to be adopted at a conventional workplace. The first critical dimension underlines the
need of common or generic application software that is capable of running smoothly in diverse
range of personal devices that different employees might bring. Compatibility and functioning
becomes an issue when either the operating systems are differently designed or the hardware
incorporated in a particular device does not fulfil the requirements for an application to
function. The issue of a common interface also becomes an issue in case the implemented
technologies have generational gap. With employee strength of over 1000, a company can
never expect the employees to have a single kind of device with everyone. The second critical
dimension highlights the company’s obligation for drafting a customized policy that addresses
the range of usage associated with personal devices within the workplace setting to cover up
for the degree of accessibility vested in each executive. This is to assure that the sensitive data
within the office database is not compromised at any cost. The policies are to be stringent when
the count of employees is large and there is high possibility for anonymous access.
The third dimension has its criticality defined along the mutual agreement arrived at by the
owners and managers on one side and the employees on the other, regarding acknowledgment
in terms of legal aspects of using personal devices in the company’s workplace setting. The third
one depends on the policies frames as per the business owners want. BYOD do have certain
advantages that are convincing when it comes to rapid adoption of new technologies, reduced
cost of IT infrastructure post-implementation of it and increased level of operational flexibility.
However, it also increases the number of subtle risks that an organisation often will not detect
while performing its business operations. Bringing personal devices to the workplace has 3
different kinds of implications that are quite sensitive with regards to the business process
being carried out. In the relevant case of Aztech Corporation, it indicates the financial services
offered by the company to retail and corporate investors.
Legal Implications
The Australian Act of Freedom to Information which was introduced in the year 1982. Initially
the legislation of FOI appeared simple but over 30 years after its introduction, the Act became
overhauled. It has so far encouraged the culture of information disclosure across government
sector and the same is nearly applicable to the private sectors also (Stewart, 2015). This
legislation primarily scrutinizes the effectiveness of BYOD in any organisation and to what
extent the control can be implemented without any hassle. The degree of control being
referred to in this case require Aztech to comply with all the legal obligations, so basically it
increases the risk of liabilities for the company in context with the employees assigned with
jobs to be performed at the workplace. Personal devices in fact, provide a higher degree of
freedom to their respective owners but such freedom may not be required as far as the office
works and confidentiality are concerned. The increase in liability will actually be accounted for
by the licensing of generic software application required to run all the personal devices in a
similar manner, the inadvertent damage that is supposed to be introduced to an employee’s
personal files, the undesired investigation procedures that can breach an employee’s privacy
and the company’s request for any response to incidents. In any of the mentioned factor,
personal devices compromise with the privacy of an employee and Aztech Corporation shall be
The concept of BYOD has three critical dimensions that need compliance for such kind of
projects to be adopted at a conventional workplace. The first critical dimension underlines the
need of common or generic application software that is capable of running smoothly in diverse
range of personal devices that different employees might bring. Compatibility and functioning
becomes an issue when either the operating systems are differently designed or the hardware
incorporated in a particular device does not fulfil the requirements for an application to
function. The issue of a common interface also becomes an issue in case the implemented
technologies have generational gap. With employee strength of over 1000, a company can
never expect the employees to have a single kind of device with everyone. The second critical
dimension highlights the company’s obligation for drafting a customized policy that addresses
the range of usage associated with personal devices within the workplace setting to cover up
for the degree of accessibility vested in each executive. This is to assure that the sensitive data
within the office database is not compromised at any cost. The policies are to be stringent when
the count of employees is large and there is high possibility for anonymous access.
The third dimension has its criticality defined along the mutual agreement arrived at by the
owners and managers on one side and the employees on the other, regarding acknowledgment
in terms of legal aspects of using personal devices in the company’s workplace setting. The third
one depends on the policies frames as per the business owners want. BYOD do have certain
advantages that are convincing when it comes to rapid adoption of new technologies, reduced
cost of IT infrastructure post-implementation of it and increased level of operational flexibility.
However, it also increases the number of subtle risks that an organisation often will not detect
while performing its business operations. Bringing personal devices to the workplace has 3
different kinds of implications that are quite sensitive with regards to the business process
being carried out. In the relevant case of Aztech Corporation, it indicates the financial services
offered by the company to retail and corporate investors.
Legal Implications
The Australian Act of Freedom to Information which was introduced in the year 1982. Initially
the legislation of FOI appeared simple but over 30 years after its introduction, the Act became
overhauled. It has so far encouraged the culture of information disclosure across government
sector and the same is nearly applicable to the private sectors also (Stewart, 2015). This
legislation primarily scrutinizes the effectiveness of BYOD in any organisation and to what
extent the control can be implemented without any hassle. The degree of control being
referred to in this case require Aztech to comply with all the legal obligations, so basically it
increases the risk of liabilities for the company in context with the employees assigned with
jobs to be performed at the workplace. Personal devices in fact, provide a higher degree of
freedom to their respective owners but such freedom may not be required as far as the office
works and confidentiality are concerned. The increase in liability will actually be accounted for
by the licensing of generic software application required to run all the personal devices in a
similar manner, the inadvertent damage that is supposed to be introduced to an employee’s
personal files, the undesired investigation procedures that can breach an employee’s privacy
and the company’s request for any response to incidents. In any of the mentioned factor,
personal devices compromise with the privacy of an employee and Aztech Corporation shall be

RUNNING HEAD: IT Risk Assessment in Aztech
no exception. The Australian Act for Privacy introduced brought in the year 1988 has a negative
impact on the BYOD project to perform effectively at Aztech Corporation. An analysis of the
pros and cons of the aforementioned Act reveals that in case the personal data is compromised,
the company is at a position to mitigate the consequences resulting out of breach of personal
data (Iqbal, 2012). The Archive Act of 1983 also affects the implementation of such a project of
BYOD within Aztech’s workplace. The Act was established by the NAA or the National Archive of
Australia in the year 1983 with a key motive to assist the governmental agencies to perform
management of significant records and make 20 years old record to be available to the general
public. The record refers to written documentations, digital content, audios and video files of
any nature within the listed spectrum. However, the act serves disadvantageous for private
companies like that of Aztech. Once a corporate file gets corrupted within an employee’s
personal device, the only solution as per the Act is to extract the data from a pile of records
that might be too sensitive from a employee’s consideration. The decision-making regarding
the preservation of corporate data would involves all employees which would result in
ambiguity and delay in the process. The process of using personal devices to minimize the
workload would go against the very sole concept of BYOD (Downer & Bhattacharya, 2015).
Implications from Financial Aspects
The concept of BYOD might sound beneficial to Aztech when it comes to reduced cost of
hardware but that can be achieved only when the employees agree to pay for their own
personal devices. This is not highly practical case as rarely an employee would voluntarily invest
his/her personal money to buy something that supports the professional activities which are
anyway the responsibility of the company and not any individual. However, from a separate
perspective, the reduced cost of hardware implementation can be far outweighed by the
technical infrastructure that would be required to support a large number of personally
diversified devices within a workplace. Employees at Aztech primarily carry out operations
related to buying and selling of market shares, transfer of money and registration of clients.
These processes obviously require a common digital platform and an interface to run smoothly
in each of the personal devices present within the company’s workplace. Disparity is highly
speculated because of some will arrive with laptops and PDAs while some may be confined to
only cell phones that run on OSS or Open Source Software. To exacerbate this, further disparity
among the handsets’ operating systems can complicate the gross budget developed for
technological implementation. In similar cases, the BYOD also opens multiple loopholes for
breach of security. Lastly, in some case even the employees might be required to compromise
with their devices’ originality when extra devices are required for performing specific business
activities (DoD, 2014).
no exception. The Australian Act for Privacy introduced brought in the year 1988 has a negative
impact on the BYOD project to perform effectively at Aztech Corporation. An analysis of the
pros and cons of the aforementioned Act reveals that in case the personal data is compromised,
the company is at a position to mitigate the consequences resulting out of breach of personal
data (Iqbal, 2012). The Archive Act of 1983 also affects the implementation of such a project of
BYOD within Aztech’s workplace. The Act was established by the NAA or the National Archive of
Australia in the year 1983 with a key motive to assist the governmental agencies to perform
management of significant records and make 20 years old record to be available to the general
public. The record refers to written documentations, digital content, audios and video files of
any nature within the listed spectrum. However, the act serves disadvantageous for private
companies like that of Aztech. Once a corporate file gets corrupted within an employee’s
personal device, the only solution as per the Act is to extract the data from a pile of records
that might be too sensitive from a employee’s consideration. The decision-making regarding
the preservation of corporate data would involves all employees which would result in
ambiguity and delay in the process. The process of using personal devices to minimize the
workload would go against the very sole concept of BYOD (Downer & Bhattacharya, 2015).
Implications from Financial Aspects
The concept of BYOD might sound beneficial to Aztech when it comes to reduced cost of
hardware but that can be achieved only when the employees agree to pay for their own
personal devices. This is not highly practical case as rarely an employee would voluntarily invest
his/her personal money to buy something that supports the professional activities which are
anyway the responsibility of the company and not any individual. However, from a separate
perspective, the reduced cost of hardware implementation can be far outweighed by the
technical infrastructure that would be required to support a large number of personally
diversified devices within a workplace. Employees at Aztech primarily carry out operations
related to buying and selling of market shares, transfer of money and registration of clients.
These processes obviously require a common digital platform and an interface to run smoothly
in each of the personal devices present within the company’s workplace. Disparity is highly
speculated because of some will arrive with laptops and PDAs while some may be confined to
only cell phones that run on OSS or Open Source Software. To exacerbate this, further disparity
among the handsets’ operating systems can complicate the gross budget developed for
technological implementation. In similar cases, the BYOD also opens multiple loopholes for
breach of security. Lastly, in some case even the employees might be required to compromise
with their devices’ originality when extra devices are required for performing specific business
activities (DoD, 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RUNNING HEAD: IT Risk Assessment in Aztech
Security-Related Implications
These implications are high because it correlates various other considerations apart from just IT
infrastructure, the size of a company or the nature of business it conducts. These implications
also take into account the nature of data already present in the personal devices that the
employees are supposed to carry to the workplace. For example, in Aztech Corporation, the
employees might pertain to certain software that is unapproved or not reviewed. In such cases,
the corporate data which is sensitive is totally unprotected and therefore can be mishandled or
leaked while an employee is at his personal location. The anonymous users of corporate data
thus points towards the peer group that an employee stays with like his/her family members,
relatives or close friends. Even there are possibilities of data to be stolen in case a particular
device is exposed to third party. This is not practical because the financial information of clients
that Aztech deals with, cannot be compromised under any circumstances. The data would
contain a lot of sensitive information like the personal bank accounts details, the transactions
performed and even the encrypted information. Third party cloud services are also not a
solution to the above problem because there are a plethora of users who are linked with third
party cloud service-providers. In a separate context, Aztech being a private business
organisation can also be questioned on its integrity if the security postures of the permitted
personal devices are weak. At last, the professionals in financial service sector might not be
experts on IT security and therefore their personal management of security risks is far different
from the corporate management which utilizes either an intranet or an extranet along with a
centralized and protected server (Carden, 2012).
A Generalised Risk Assessment of the Considered Project and Approaches
In the process of ICT management, most of the business organisations keep on striving to
develop the most efficient strategies that could be brought to effect at their respective
workplaces. BYOD technically creates a link or bridges the gap among technologies,
organisational policies and the resources within the IT departments. The resources here in case
of Aztech shall imply the personal smart phones, laptops, tablets and PDAs. But there are
underlying risks to BYOD project that are not understood by many. At the most basic level, the
major risk of BYOD is strongly associated with the smartphones that the employees are
supposed to use while staying at Aztech’s regional offices and the corporate office. According to
a report published by EYGM (2013), there are 14 major challenges that emerge when a BYOD is
being deployed. Out of these challenges, the major barriers will be brought by 4 top most
concerning factors. Considering the case of Aztech Corporation, there will be 3 intermediate
barriers and the remaining 7 are adjustable or they can be mitigated by strategic approaches.
Security-Related Implications
These implications are high because it correlates various other considerations apart from just IT
infrastructure, the size of a company or the nature of business it conducts. These implications
also take into account the nature of data already present in the personal devices that the
employees are supposed to carry to the workplace. For example, in Aztech Corporation, the
employees might pertain to certain software that is unapproved or not reviewed. In such cases,
the corporate data which is sensitive is totally unprotected and therefore can be mishandled or
leaked while an employee is at his personal location. The anonymous users of corporate data
thus points towards the peer group that an employee stays with like his/her family members,
relatives or close friends. Even there are possibilities of data to be stolen in case a particular
device is exposed to third party. This is not practical because the financial information of clients
that Aztech deals with, cannot be compromised under any circumstances. The data would
contain a lot of sensitive information like the personal bank accounts details, the transactions
performed and even the encrypted information. Third party cloud services are also not a
solution to the above problem because there are a plethora of users who are linked with third
party cloud service-providers. In a separate context, Aztech being a private business
organisation can also be questioned on its integrity if the security postures of the permitted
personal devices are weak. At last, the professionals in financial service sector might not be
experts on IT security and therefore their personal management of security risks is far different
from the corporate management which utilizes either an intranet or an extranet along with a
centralized and protected server (Carden, 2012).
A Generalised Risk Assessment of the Considered Project and Approaches
In the process of ICT management, most of the business organisations keep on striving to
develop the most efficient strategies that could be brought to effect at their respective
workplaces. BYOD technically creates a link or bridges the gap among technologies,
organisational policies and the resources within the IT departments. The resources here in case
of Aztech shall imply the personal smart phones, laptops, tablets and PDAs. But there are
underlying risks to BYOD project that are not understood by many. At the most basic level, the
major risk of BYOD is strongly associated with the smartphones that the employees are
supposed to use while staying at Aztech’s regional offices and the corporate office. According to
a report published by EYGM (2013), there are 14 major challenges that emerge when a BYOD is
being deployed. Out of these challenges, the major barriers will be brought by 4 top most
concerning factors. Considering the case of Aztech Corporation, there will be 3 intermediate
barriers and the remaining 7 are adjustable or they can be mitigated by strategic approaches.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
RUNNING HEAD: IT Risk Assessment in Aztech
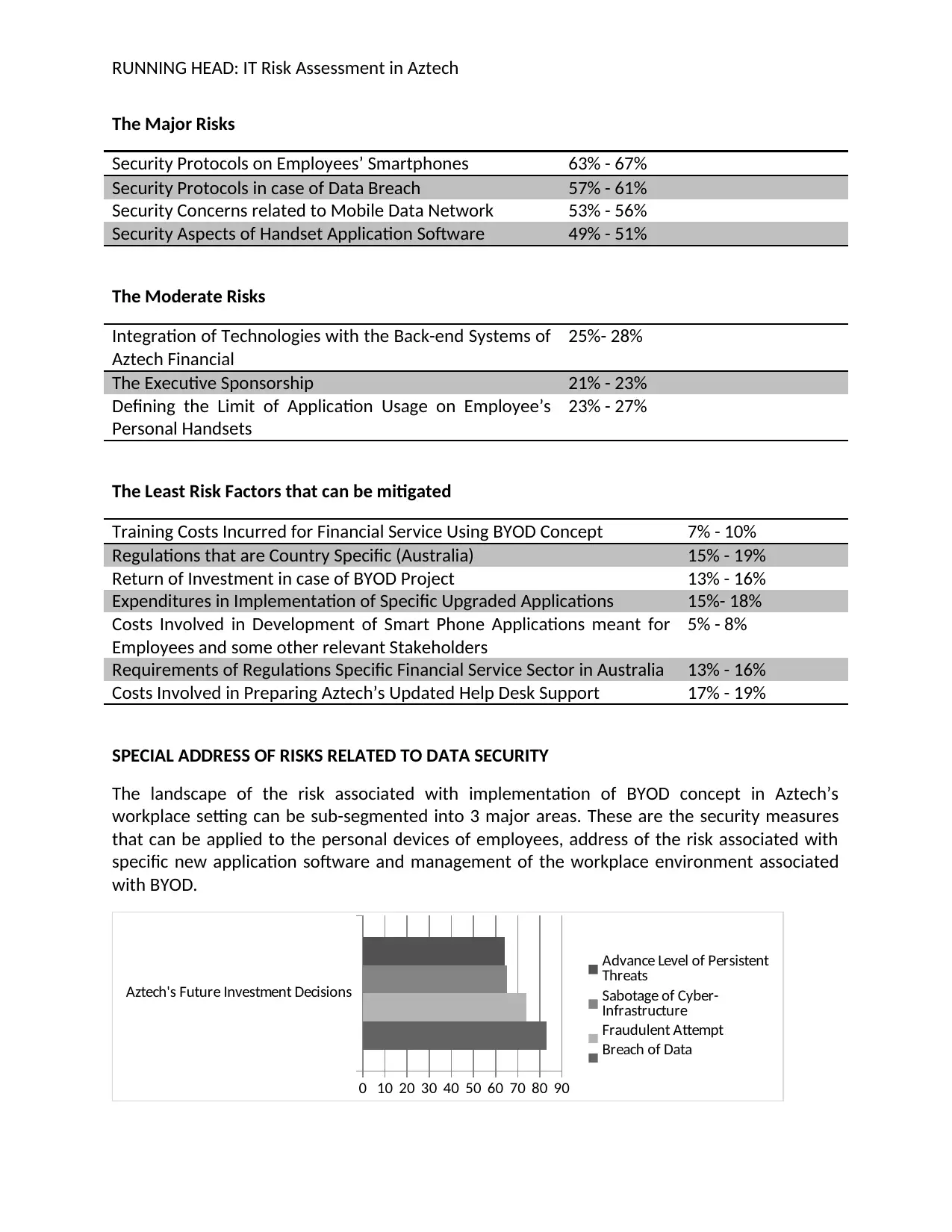
The Major Risks
Security Protocols on Employees’ Smartphones 63% - 67%
Security Protocols in case of Data Breach 57% - 61%
Security Concerns related to Mobile Data Network 53% - 56%
Security Aspects of Handset Application Software 49% - 51%
The Moderate Risks
Integration of Technologies with the Back-end Systems of
Aztech Financial
25%- 28%
The Executive Sponsorship 21% - 23%
Defining the Limit of Application Usage on Employee’s
Personal Handsets
23% - 27%
The Least Risk Factors that can be mitigated
Training Costs Incurred for Financial Service Using BYOD Concept 7% - 10%
Regulations that are Country Specific (Australia) 15% - 19%
Return of Investment in case of BYOD Project 13% - 16%
Expenditures in Implementation of Specific Upgraded Applications 15%- 18%
Costs Involved in Development of Smart Phone Applications meant for
Employees and some other relevant Stakeholders
5% - 8%
Requirements of Regulations Specific Financial Service Sector in Australia 13% - 16%
Costs Involved in Preparing Aztech’s Updated Help Desk Support 17% - 19%
SPECIAL ADDRESS OF RISKS RELATED TO DATA SECURITY
The landscape of the risk associated with implementation of BYOD concept in Aztech’s
workplace setting can be sub-segmented into 3 major areas. These are the security measures
that can be applied to the personal devices of employees, address of the risk associated with
specific new application software and management of the workplace environment associated
with BYOD.
Aztech's Future Investment Decisions
0 10 20 30 40 50 60 70 80 90
Advance Level of Persistent
Threats
Sabotage of Cyber-
Infrastructure
Fraudulent Attempt
Breach of Data
The Major Risks
Security Protocols on Employees’ Smartphones 63% - 67%
Security Protocols in case of Data Breach 57% - 61%
Security Concerns related to Mobile Data Network 53% - 56%
Security Aspects of Handset Application Software 49% - 51%
The Moderate Risks
Integration of Technologies with the Back-end Systems of
Aztech Financial
25%- 28%
The Executive Sponsorship 21% - 23%
Defining the Limit of Application Usage on Employee’s
Personal Handsets
23% - 27%
The Least Risk Factors that can be mitigated
Training Costs Incurred for Financial Service Using BYOD Concept 7% - 10%
Regulations that are Country Specific (Australia) 15% - 19%
Return of Investment in case of BYOD Project 13% - 16%
Expenditures in Implementation of Specific Upgraded Applications 15%- 18%
Costs Involved in Development of Smart Phone Applications meant for
Employees and some other relevant Stakeholders
5% - 8%
Requirements of Regulations Specific Financial Service Sector in Australia 13% - 16%
Costs Involved in Preparing Aztech’s Updated Help Desk Support 17% - 19%
SPECIAL ADDRESS OF RISKS RELATED TO DATA SECURITY
The landscape of the risk associated with implementation of BYOD concept in Aztech’s
workplace setting can be sub-segmented into 3 major areas. These are the security measures
that can be applied to the personal devices of employees, address of the risk associated with
specific new application software and management of the workplace environment associated
with BYOD.
Aztech's Future Investment Decisions
0 10 20 30 40 50 60 70 80 90
Advance Level of Persistent
Threats
Sabotage of Cyber-
Infrastructure
Fraudulent Attempt
Breach of Data

RUNNING HEAD: IT Risk Assessment in Aztech
Security Setting for Personal Handsets of Employees
In earlier days, there existed a single-phone environment in the corporate sector because the
manufacturers and brands were few. They were secure because of the uniform distribution of
handset variants. The policy control for security could be effectively managed by the
manufacturers because of the unified interface they provided to users. The proposed BYOD
concept that is supposed to be applied to the case of Aztech Corporation changes the security
architecture at a fundamental level as the company’s employees are supposed to bring a
diversified range of devices that are individually personalized and have very less to do with the
business environment of an enterprise. The five fundamental security concerns with regards to
the mobile devices are
1. Theft of an Employee’s Personal Device either outside or within the Workplace setting of
Aztech (Password Protected Device and Encryption)
2. Shallow awareness of IT security practices or absolute Lack of it in Aztech primary segment of
professionals whose work profiles do not align with those of IT Professionals, the company
being in the financial service sector (The Risk Assessment Framework known to IT Department
of Aztech)
3. The ownership associated with end user of the device (Rooting or Jailbreak of the
Smartphones’ Operating System)
4. Idle state of Personal Devices with an elevated access to Internet data (Access to Business
Data through VPN connection in a Lost or Stolen Smart phone of Aztech’s Employee)
5. Access to the personal device on a physical level either within the workplace or outdoor
(Absence of Hardware Encryption in 3G Devices)
The above concerns can be addressed by use of a MDM or a Mobile Device Management
Program that is to be adopted by the company itself post-implementation of BYOD concept
within its workplace. Apart from that the company needs to set a baseline for security
standards as various hardware and operating systems will just mess up the confidentiality
protocols. The authentication for corporate data needs to be stringent one on the monitors of
personal devices. In addition to all these, a vital addition of Aztech’s risk awareness program is
also required followed by consistent evaluation of device usage (Absalom, 2012).
Risk Possessed from the Application Software in Personal Laptops and Mobile Handsets
There has been a steep increase in the incident of malware attacks in organisations that follow
B2C models. Aztech falls under the same category. Malicious codes and security loopholes are
less likely to be identified by employees at Aztech and thus it skyrockets the chances of theft of
corporate data. The embedded codes can compromise with the local files on an intranet or an
extranet. To effectively counter these breaches, the data sharing performed between each
BYOD devices are needed to be filtered at the initial phase to make sure that all loopholes in a
personal device are detected and subsequently covered (Ghosh, et al 2013).
Security Setting for Personal Handsets of Employees
In earlier days, there existed a single-phone environment in the corporate sector because the
manufacturers and brands were few. They were secure because of the uniform distribution of
handset variants. The policy control for security could be effectively managed by the
manufacturers because of the unified interface they provided to users. The proposed BYOD
concept that is supposed to be applied to the case of Aztech Corporation changes the security
architecture at a fundamental level as the company’s employees are supposed to bring a
diversified range of devices that are individually personalized and have very less to do with the
business environment of an enterprise. The five fundamental security concerns with regards to
the mobile devices are
1. Theft of an Employee’s Personal Device either outside or within the Workplace setting of
Aztech (Password Protected Device and Encryption)
2. Shallow awareness of IT security practices or absolute Lack of it in Aztech primary segment of
professionals whose work profiles do not align with those of IT Professionals, the company
being in the financial service sector (The Risk Assessment Framework known to IT Department
of Aztech)
3. The ownership associated with end user of the device (Rooting or Jailbreak of the
Smartphones’ Operating System)
4. Idle state of Personal Devices with an elevated access to Internet data (Access to Business
Data through VPN connection in a Lost or Stolen Smart phone of Aztech’s Employee)
5. Access to the personal device on a physical level either within the workplace or outdoor
(Absence of Hardware Encryption in 3G Devices)
The above concerns can be addressed by use of a MDM or a Mobile Device Management
Program that is to be adopted by the company itself post-implementation of BYOD concept
within its workplace. Apart from that the company needs to set a baseline for security
standards as various hardware and operating systems will just mess up the confidentiality
protocols. The authentication for corporate data needs to be stringent one on the monitors of
personal devices. In addition to all these, a vital addition of Aztech’s risk awareness program is
also required followed by consistent evaluation of device usage (Absalom, 2012).
Risk Possessed from the Application Software in Personal Laptops and Mobile Handsets
There has been a steep increase in the incident of malware attacks in organisations that follow
B2C models. Aztech falls under the same category. Malicious codes and security loopholes are
less likely to be identified by employees at Aztech and thus it skyrockets the chances of theft of
corporate data. The embedded codes can compromise with the local files on an intranet or an
extranet. To effectively counter these breaches, the data sharing performed between each
BYOD devices are needed to be filtered at the initial phase to make sure that all loopholes in a
personal device are detected and subsequently covered (Ghosh, et al 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RUNNING HEAD: IT Risk Assessment in Aztech
CONCLUSION
From the above assessment, it can be opined the variability associated with a BYOD
environment is significantly in case of hardware as well the software that provides access to
Aztech’s sensitive data on clients’ profile and their bank account details. Variation in OS
platforms also makes the wiping of devices complicated. The employees themselves account for
55% of the security risk in a BYOD environment while the remaining 27% is contributed by third
party individuals who somehow have legitimate access to Aztech’s internal database. Also it can
be argued that the activities performed by Aztech’s employees are needed to be visible mostly
on the cloud system followed by systems that are on the premise. Mobile devices still account
for half of the visibility required and therefore it is advisable to adopt the laptops and PDAs if
possible in the place of personal smartphones because the variability factor is less in the former
case.
CONCLUSION
From the above assessment, it can be opined the variability associated with a BYOD
environment is significantly in case of hardware as well the software that provides access to
Aztech’s sensitive data on clients’ profile and their bank account details. Variation in OS
platforms also makes the wiping of devices complicated. The employees themselves account for
55% of the security risk in a BYOD environment while the remaining 27% is contributed by third
party individuals who somehow have legitimate access to Aztech’s internal database. Also it can
be argued that the activities performed by Aztech’s employees are needed to be visible mostly
on the cloud system followed by systems that are on the premise. Mobile devices still account
for half of the visibility required and therefore it is advisable to adopt the laptops and PDAs if
possible in the place of personal smartphones because the variability factor is less in the former
case.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RUNNING HEAD: IT Risk Assessment in Aztech
Reference
Absalom, R., 2012. International Data Privacy Legislation Review: A Guide for BYOD Policies.
Ovum Consulting, IT006, 234, pp.3-5.
Campbell, J., McDonald, C. and Sethibe, T., 2010. Public and private sector IT governance:
Identifying contextual differences. Australasian Journal of Information Systems, 16(2).
Carden, M., 2012, August. Digital Archiving at the National Archives of Australia: Putting
Principles into Practice. In International Council on Archives Congress, Brisbane,
Australia, August (pp. 20-24).
Department of Defence, 2014. Bring Your Own Device (BYOD) for Executives. Australian
Government. Retrieved 26 September 2017 from
https://www.asd.gov.au/publications/protect/BYOD_Considerations_for_Execs.pdf
Downer, K. and Bhattacharya, M., 2015, December. BYOD security: A new business challenge. In
Smart City/SocialCom/SustainCom (SmartCity), 2015 IEEE International Conference on
(pp. 1128-1133). IEEE.
EYGM, 2013. Bring your own device Security and risk considerations for your mobile device
program. Retrieved 27 September 2017 from
http://www.ey.com/Publication/vwLUAssets/EY_-
_Bring_your_own_device:_mobile_security_and_risk/$FILE/Bring_your_own_device.pdf
Ghosh, A., Gajar, P.K. and Rai, S., 2013. Bring your own device (BYOD): Security risks and
mitigating strategies. Journal of Global Research in Computer Science, 4(4), pp.62-70.
Iqbal, S., 2012. Australian Government Launches Discussion Paper on Privacy Breach
Notification. Retrieved 27 September 2017 from https://www.insideprivacy.com/data-
security/australian-government-launches-discussion-paper-on-privacy-breach-
notification/
Leavitt, N., 2013. Today's mobile security requires a new approach. Computer, 46(11), pp.16-19.
Olalere, M., Abdullah, M.T., Mahmod, R. and Abdullah, A., 2015. A review of bring your own
device on security issues. Sage Open, 5(2), p.2158244015580372.
Saini, S.L., Saini, D.K., Yousif, J.H. and Khandage, S.V., 2011. Cloud computing and enterprise
resource planning systems. In Proceedings of the world Congress on Engineering (Vol. 1,
pp. 6-8).
Stewart, D., 2015. Assessing Access to Information in Australia: The Impact of Freedom of
Information Laws on the Scrutiny and Operation of the Commonwealth Government.
Reference
Absalom, R., 2012. International Data Privacy Legislation Review: A Guide for BYOD Policies.
Ovum Consulting, IT006, 234, pp.3-5.
Campbell, J., McDonald, C. and Sethibe, T., 2010. Public and private sector IT governance:
Identifying contextual differences. Australasian Journal of Information Systems, 16(2).
Carden, M., 2012, August. Digital Archiving at the National Archives of Australia: Putting
Principles into Practice. In International Council on Archives Congress, Brisbane,
Australia, August (pp. 20-24).
Department of Defence, 2014. Bring Your Own Device (BYOD) for Executives. Australian
Government. Retrieved 26 September 2017 from
https://www.asd.gov.au/publications/protect/BYOD_Considerations_for_Execs.pdf
Downer, K. and Bhattacharya, M., 2015, December. BYOD security: A new business challenge. In
Smart City/SocialCom/SustainCom (SmartCity), 2015 IEEE International Conference on
(pp. 1128-1133). IEEE.
EYGM, 2013. Bring your own device Security and risk considerations for your mobile device
program. Retrieved 27 September 2017 from
http://www.ey.com/Publication/vwLUAssets/EY_-
_Bring_your_own_device:_mobile_security_and_risk/$FILE/Bring_your_own_device.pdf
Ghosh, A., Gajar, P.K. and Rai, S., 2013. Bring your own device (BYOD): Security risks and
mitigating strategies. Journal of Global Research in Computer Science, 4(4), pp.62-70.
Iqbal, S., 2012. Australian Government Launches Discussion Paper on Privacy Breach
Notification. Retrieved 27 September 2017 from https://www.insideprivacy.com/data-
security/australian-government-launches-discussion-paper-on-privacy-breach-
notification/
Leavitt, N., 2013. Today's mobile security requires a new approach. Computer, 46(11), pp.16-19.
Olalere, M., Abdullah, M.T., Mahmod, R. and Abdullah, A., 2015. A review of bring your own
device on security issues. Sage Open, 5(2), p.2158244015580372.
Saini, S.L., Saini, D.K., Yousif, J.H. and Khandage, S.V., 2011. Cloud computing and enterprise
resource planning systems. In Proceedings of the world Congress on Engineering (Vol. 1,
pp. 6-8).
Stewart, D., 2015. Assessing Access to Information in Australia: The Impact of Freedom of
Information Laws on the Scrutiny and Operation of the Commonwealth Government.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





