ITECH1102 | Roles and Functions of Network Connectivity in Today’s Computing
VerifiedAdded on 2022/08/27
|15
|2028
|23
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: ITECH1102
Content Analysis Assignment
1
Content Analysis Assignment
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

ITECH1102
Table of Content
Roles and Functions of Network Connectivity in Today’s Computing...............................3
Principles of Communication in Networks......................................................................5
Data Types...................................................................................................................7
Data Transmission through Network Layers...............................................................9
Roles and Functionalities of Hardware and Software Entities serving Network
Communication..........................................................................................................................10
NIC/Ethernet Connection..........................................................................................10
Protocols & Interactions for Network Communication.................................................11
Basics of Cloud Computing...........................................................................................12
Cloud Storage Services..............................................................................................12
Fed Uni Cloud & Services.........................................................................................13
Advantages of the Cloud Services.............................................................................13
Disadvantages of Cloud Services..............................................................................13
Cloud Infrastructure depends on Virtualization.........................................................13
References.........................................................................................................................15
2
Table of Content
Roles and Functions of Network Connectivity in Today’s Computing...............................3
Principles of Communication in Networks......................................................................5
Data Types...................................................................................................................7
Data Transmission through Network Layers...............................................................9
Roles and Functionalities of Hardware and Software Entities serving Network
Communication..........................................................................................................................10
NIC/Ethernet Connection..........................................................................................10
Protocols & Interactions for Network Communication.................................................11
Basics of Cloud Computing...........................................................................................12
Cloud Storage Services..............................................................................................12
Fed Uni Cloud & Services.........................................................................................13
Advantages of the Cloud Services.............................................................................13
Disadvantages of Cloud Services..............................................................................13
Cloud Infrastructure depends on Virtualization.........................................................13
References.........................................................................................................................15
2

ITECH1102
Content Analysis Assignment
This assessment portrays to support the students to completely understand their course
material.
Roles and Functions of Network Connectivity in Today’s Computing
The computer network refers to a telecommunication network, enabling to establish data
exchange among different computers. Whereas, the computer network refers to a discipline of
engineering whose main aim directs towards the analysis and study of communication process
between several computers or computing devices which are interlinked with each other for
sharing resources and exchanging information. Earlier, the data was exchanged physically from
one computer another using the magnetic media such as floppy disks/magnetic tapes. But, today
the current computing system is transformed with the implementation of networked computing
devices. It offers instant data exchanging capacity, for example email.
There are various computer networking devices like switches, hubs, routers, proxy,
modems, bridges, gateways and NICs ("Network and connectivity", 2017). To establish network
interaction, two or more devices are required such as Desktop and web server. For facilitating
networking, all the device require NIC (Network Interface Card), which is distinctively
differentiates from other NICs. Thus, NIC helps the networking device to establish
communication with another networking devices. It converts packets of data amongst two
distinct technologies of data transmission. A personal computer uses the technology of parallel
data transmission for transmitting data amongst its inhouse parts, where the media which allows
the connectivity amongst various personal computers utilizes a serial data transmission
3
Content Analysis Assignment
This assessment portrays to support the students to completely understand their course
material.
Roles and Functions of Network Connectivity in Today’s Computing
The computer network refers to a telecommunication network, enabling to establish data
exchange among different computers. Whereas, the computer network refers to a discipline of
engineering whose main aim directs towards the analysis and study of communication process
between several computers or computing devices which are interlinked with each other for
sharing resources and exchanging information. Earlier, the data was exchanged physically from
one computer another using the magnetic media such as floppy disks/magnetic tapes. But, today
the current computing system is transformed with the implementation of networked computing
devices. It offers instant data exchanging capacity, for example email.
There are various computer networking devices like switches, hubs, routers, proxy,
modems, bridges, gateways and NICs ("Network and connectivity", 2017). To establish network
interaction, two or more devices are required such as Desktop and web server. For facilitating
networking, all the device require NIC (Network Interface Card), which is distinctively
differentiates from other NICs. Thus, NIC helps the networking device to establish
communication with another networking devices. It converts packets of data amongst two
distinct technologies of data transmission. A personal computer uses the technology of parallel
data transmission for transmitting data amongst its inhouse parts, where the media which allows
the connectivity amongst various personal computers utilizes a serial data transmission
3

ITECH1102
technology ("Computer Networking Devices Explained with Function", 2019). In general, NIC
both is transmitting and receiving binary data. Various types of NICs are present like:
Media specific
Network design specific
Figure: Network hub
For proving data exchange, Ethernet Hubs help in connecting multiple devices. The hub traffic of
a port is broadcasted to rest of the ports, and supports to assist monitoring the network traffic.
Today, rather than the hubs, switches are chosen more as they are devices which are smart.
Switches work at second layer (Data link layer) of ISO-OSI layers.
Figure: OSI Model
Routers are present on the Network layer (i.e., the third layer) for connecting the networks
together.
4
technology ("Computer Networking Devices Explained with Function", 2019). In general, NIC
both is transmitting and receiving binary data. Various types of NICs are present like:
Media specific
Network design specific
Figure: Network hub
For proving data exchange, Ethernet Hubs help in connecting multiple devices. The hub traffic of
a port is broadcasted to rest of the ports, and supports to assist monitoring the network traffic.
Today, rather than the hubs, switches are chosen more as they are devices which are smart.
Switches work at second layer (Data link layer) of ISO-OSI layers.
Figure: OSI Model
Routers are present on the Network layer (i.e., the third layer) for connecting the networks
together.
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
ITECH1102
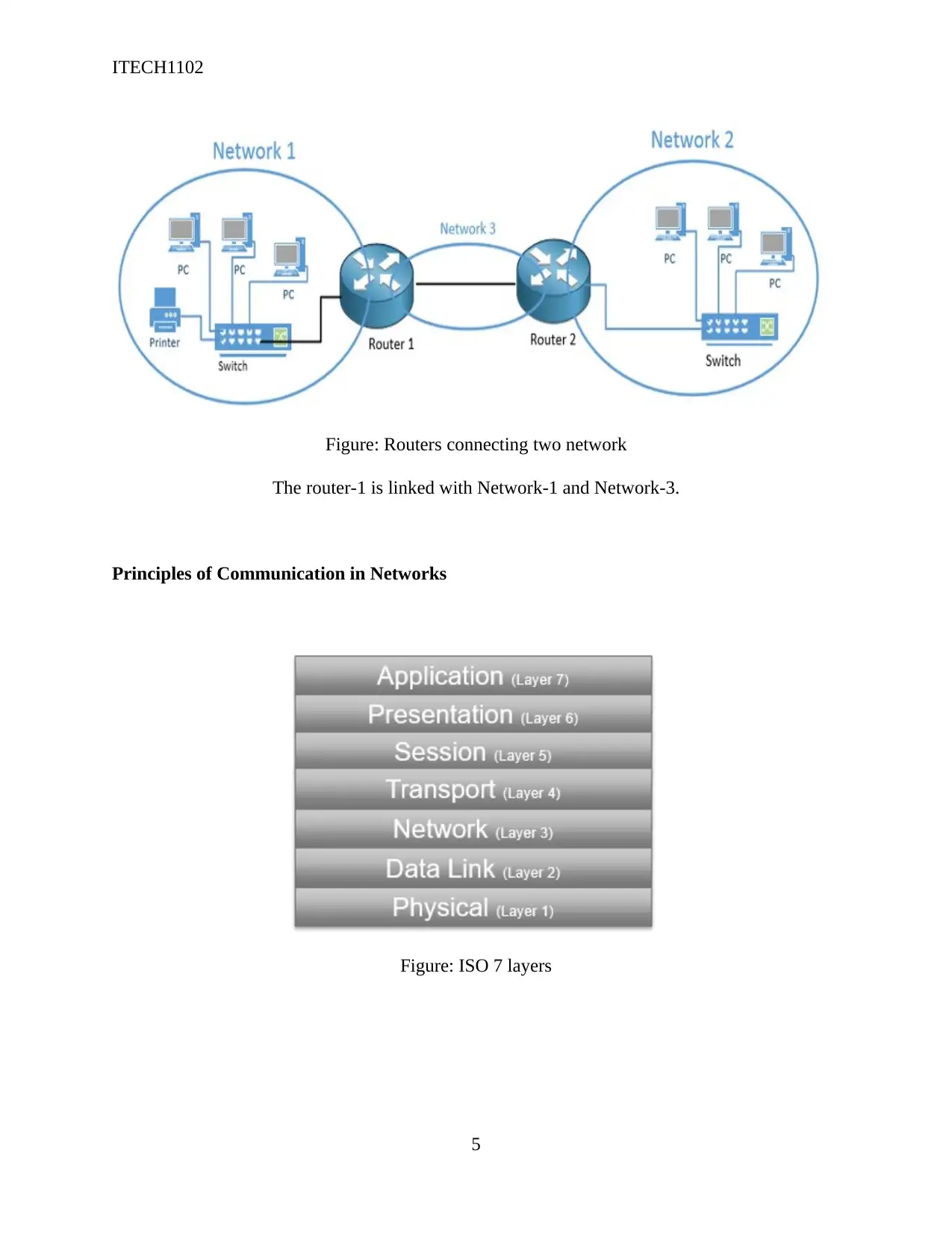
Figure: Routers connecting two network
The router-1 is linked with Network-1 and Network-3.
Principles of Communication in Networks
Figure: ISO 7 layers
5
Figure: Routers connecting two network
The router-1 is linked with Network-1 and Network-3.
Principles of Communication in Networks
Figure: ISO 7 layers
5

ITECH1102
The principle includes that each layer could be stated and implemented more or less independent
of the above or below layers until it offers consistent interfaces ("4. Networking Principles",
n.d.).
In order to handle the login/logout issues of a bank the Session Layer is responsible.
Layer-7: It helps to transfer the file, email and so on.
Layer-6: It helps to represent the data, for example, encryption.
Layer-5: It establishes, manages and terminates the connections.
Layer-4: It ensures end-to-end delivery among the hosts.
Layer-3: It carries out routing technologies, internetworking, and addressing.
Layer-2: It implements local data exchange.
Layer-1: It takes care of the physical characteristics such as electrical signals, cabling and so on.
Respectively, the hubs and switches are used in the respective layers. And, each of the layers are
responsible to do its functions to transmit the request.
Additionally, every single layer has a unique purpose to accomplish, and it utilizes different
protocols for communication.
6
The principle includes that each layer could be stated and implemented more or less independent
of the above or below layers until it offers consistent interfaces ("4. Networking Principles",
n.d.).
In order to handle the login/logout issues of a bank the Session Layer is responsible.
Layer-7: It helps to transfer the file, email and so on.
Layer-6: It helps to represent the data, for example, encryption.
Layer-5: It establishes, manages and terminates the connections.
Layer-4: It ensures end-to-end delivery among the hosts.
Layer-3: It carries out routing technologies, internetworking, and addressing.
Layer-2: It implements local data exchange.
Layer-1: It takes care of the physical characteristics such as electrical signals, cabling and so on.
Respectively, the hubs and switches are used in the respective layers. And, each of the layers are
responsible to do its functions to transmit the request.
Additionally, every single layer has a unique purpose to accomplish, and it utilizes different
protocols for communication.
6
ITECH1102
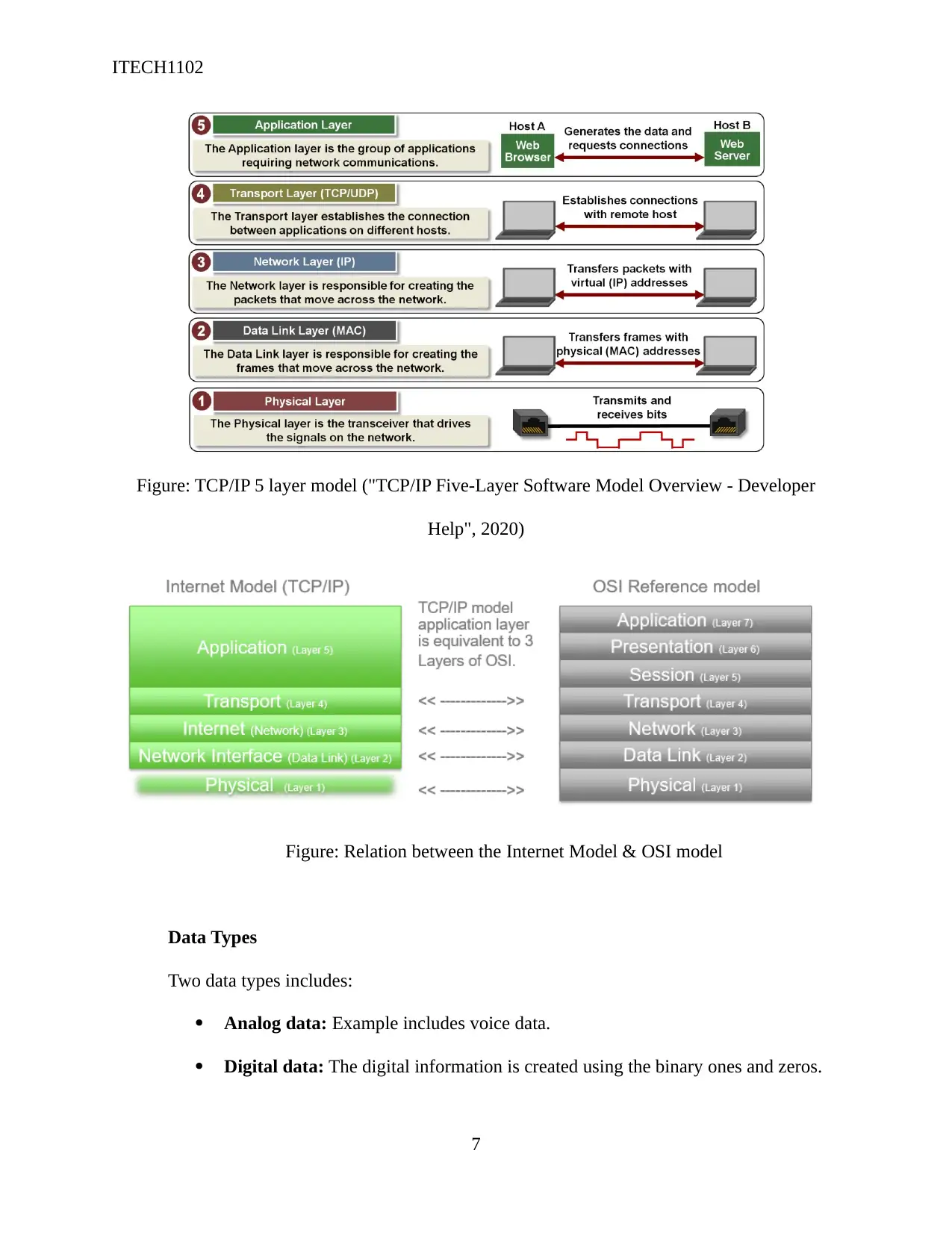
Figure: TCP/IP 5 layer model ("TCP/IP Five-Layer Software Model Overview - Developer
Help", 2020)
Figure: Relation between the Internet Model & OSI model
Data Types
Two data types includes:
Analog data: Example includes voice data.
Digital data: The digital information is created using the binary ones and zeros.
7
Figure: TCP/IP 5 layer model ("TCP/IP Five-Layer Software Model Overview - Developer
Help", 2020)
Figure: Relation between the Internet Model & OSI model
Data Types
Two data types includes:
Analog data: Example includes voice data.
Digital data: The digital information is created using the binary ones and zeros.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
ITECH1102
Thus, the data can be transmitted via digital or analog media.
Cables are connected to computers for digital data’s transmission, and the radio devices
such as Wi-Fi access point, and for analog the telephone system Microwave dishes.
Therefore, optical fiber cables are a medium used for computer networking and
telecommunication.
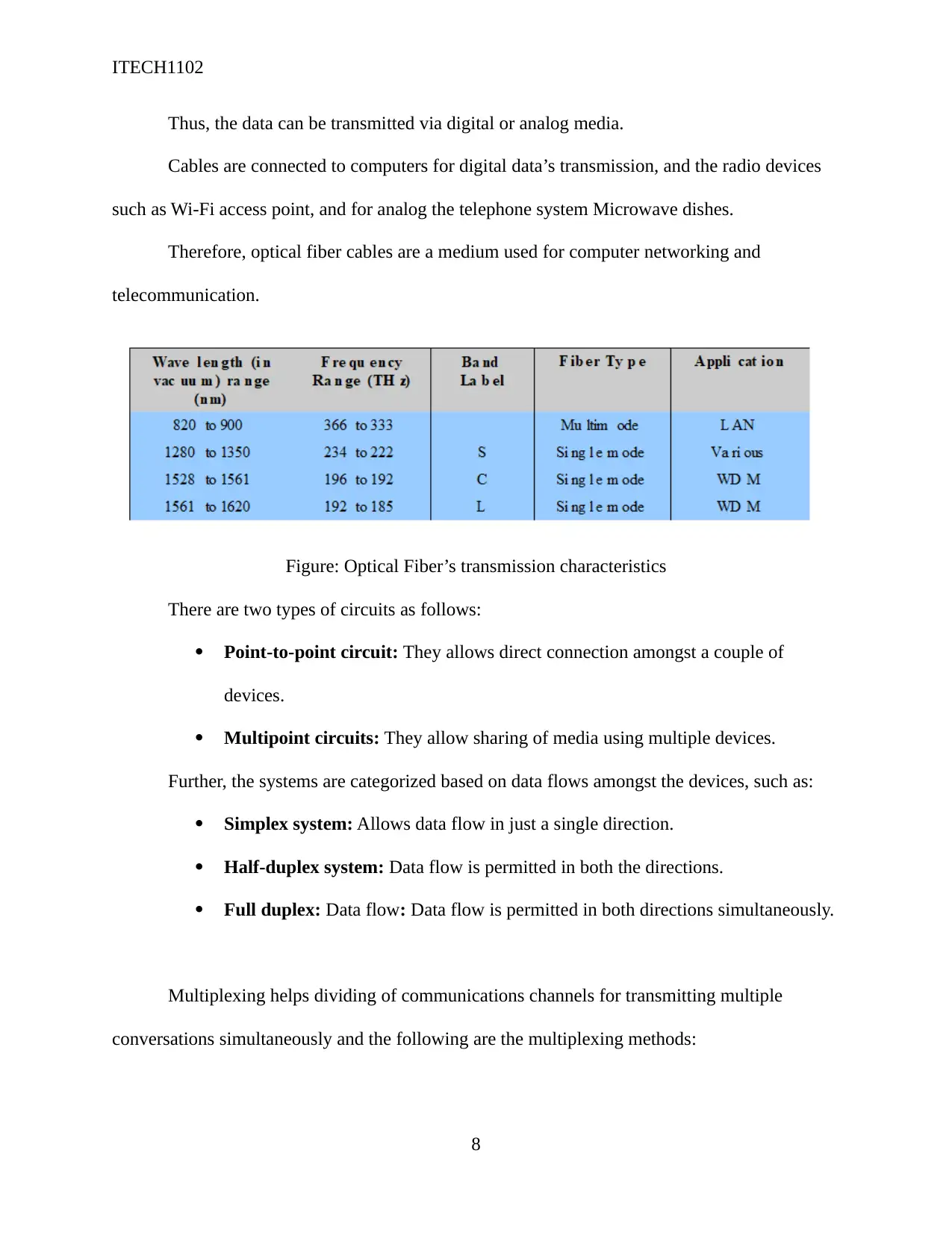
Figure: Optical Fiber’s transmission characteristics
There are two types of circuits as follows:
Point-to-point circuit: They allows direct connection amongst a couple of
devices.
Multipoint circuits: They allow sharing of media using multiple devices.
Further, the systems are categorized based on data flows amongst the devices, such as:
Simplex system: Allows data flow in just a single direction.
Half-duplex system: Data flow is permitted in both the directions.
Full duplex: Data flow: Data flow is permitted in both directions simultaneously.
Multiplexing helps dividing of communications channels for transmitting multiple
conversations simultaneously and the following are the multiplexing methods:
8
Thus, the data can be transmitted via digital or analog media.
Cables are connected to computers for digital data’s transmission, and the radio devices
such as Wi-Fi access point, and for analog the telephone system Microwave dishes.
Therefore, optical fiber cables are a medium used for computer networking and
telecommunication.
Figure: Optical Fiber’s transmission characteristics
There are two types of circuits as follows:
Point-to-point circuit: They allows direct connection amongst a couple of
devices.
Multipoint circuits: They allow sharing of media using multiple devices.
Further, the systems are categorized based on data flows amongst the devices, such as:
Simplex system: Allows data flow in just a single direction.
Half-duplex system: Data flow is permitted in both the directions.
Full duplex: Data flow: Data flow is permitted in both directions simultaneously.
Multiplexing helps dividing of communications channels for transmitting multiple
conversations simultaneously and the following are the multiplexing methods:
8

ITECH1102
Data Transmission through Network Layers
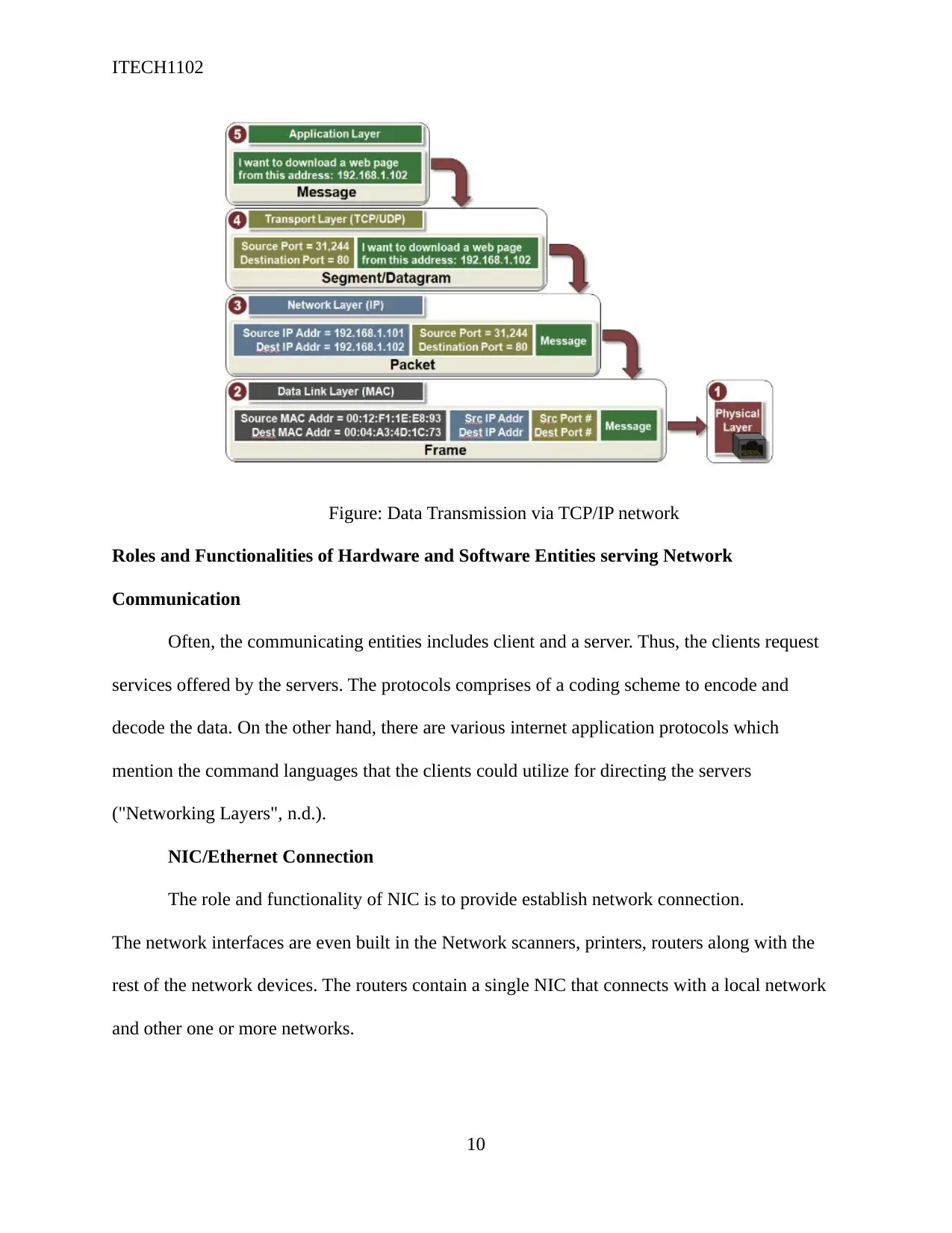
The below diagram shows how each layer functions collectively for data sending and
receiving the across a TCP/IP network. The top layer (Application layer) helps in sending the
information to the bottom layers. It helps in data packet’s transmission to the data-link layer. It
independently routes every single data packets, and when the out-of-order packets arrive their
destination, they are reassembled. Additionally, it even handles the errors (Ram, 2018).
Sockets, IP addresses and Ports
Sockets are written like, 192.168.22.33:47658. IP address is linked with 65536 ports (0 –
65535). Socket helps to identify the conversation of transport layer (UDP/TCP). For viewing
active sockets on Windows Netstat is used, which needs administrator privileges.
ARP
ARP (Address Resolution Protocol) asks who contains the IP Address 192.168.12.124,
and is responded by the targeted machine ("How Address Resolution Protocol (ARP) works?",
n.d.).
Determining network addresses and IP addresses
The computers communicating with another machine is aware of its and the destination's
IP addresses. The network address could be determined with the assistance of subnet mask
9
Data Transmission through Network Layers
The below diagram shows how each layer functions collectively for data sending and
receiving the across a TCP/IP network. The top layer (Application layer) helps in sending the
information to the bottom layers. It helps in data packet’s transmission to the data-link layer. It
independently routes every single data packets, and when the out-of-order packets arrive their
destination, they are reassembled. Additionally, it even handles the errors (Ram, 2018).
Sockets, IP addresses and Ports
Sockets are written like, 192.168.22.33:47658. IP address is linked with 65536 ports (0 –
65535). Socket helps to identify the conversation of transport layer (UDP/TCP). For viewing
active sockets on Windows Netstat is used, which needs administrator privileges.
ARP
ARP (Address Resolution Protocol) asks who contains the IP Address 192.168.12.124,
and is responded by the targeted machine ("How Address Resolution Protocol (ARP) works?",
n.d.).
Determining network addresses and IP addresses
The computers communicating with another machine is aware of its and the destination's
IP addresses. The network address could be determined with the assistance of subnet mask
9
ITECH1102
Figure: Data Transmission via TCP/IP network
Roles and Functionalities of Hardware and Software Entities serving Network
Communication
Often, the communicating entities includes client and a server. Thus, the clients request
services offered by the servers. The protocols comprises of a coding scheme to encode and
decode the data. On the other hand, there are various internet application protocols which
mention the command languages that the clients could utilize for directing the servers
("Networking Layers", n.d.).
NIC/Ethernet Connection
The role and functionality of NIC is to provide establish network connection.
The network interfaces are even built in the Network scanners, printers, routers along with the
rest of the network devices. The routers contain a single NIC that connects with a local network
and other one or more networks.
10
Figure: Data Transmission via TCP/IP network
Roles and Functionalities of Hardware and Software Entities serving Network
Communication
Often, the communicating entities includes client and a server. Thus, the clients request
services offered by the servers. The protocols comprises of a coding scheme to encode and
decode the data. On the other hand, there are various internet application protocols which
mention the command languages that the clients could utilize for directing the servers
("Networking Layers", n.d.).
NIC/Ethernet Connection
The role and functionality of NIC is to provide establish network connection.
The network interfaces are even built in the Network scanners, printers, routers along with the
rest of the network devices. The routers contain a single NIC that connects with a local network
and other one or more networks.
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
ITECH1102
Packet switching takes place on small home network, large network, on the internet, and also the
mobile telephone system.
Protocols & Interactions for Network Communication
There are various Application protocols that are utilized to exchange the data such as:
1) HTTP (Hypertext Transfer Protocol): It help to manage the web traffic.
2) POP (Post Office Protocol): It assists to access the email.
3) FTP (File Transfer Protocol): It supports with file transferring.
4) NTP (Network Time Protocol)
5) SSH (Secure Shell)
6) SMB (Server Message Block)
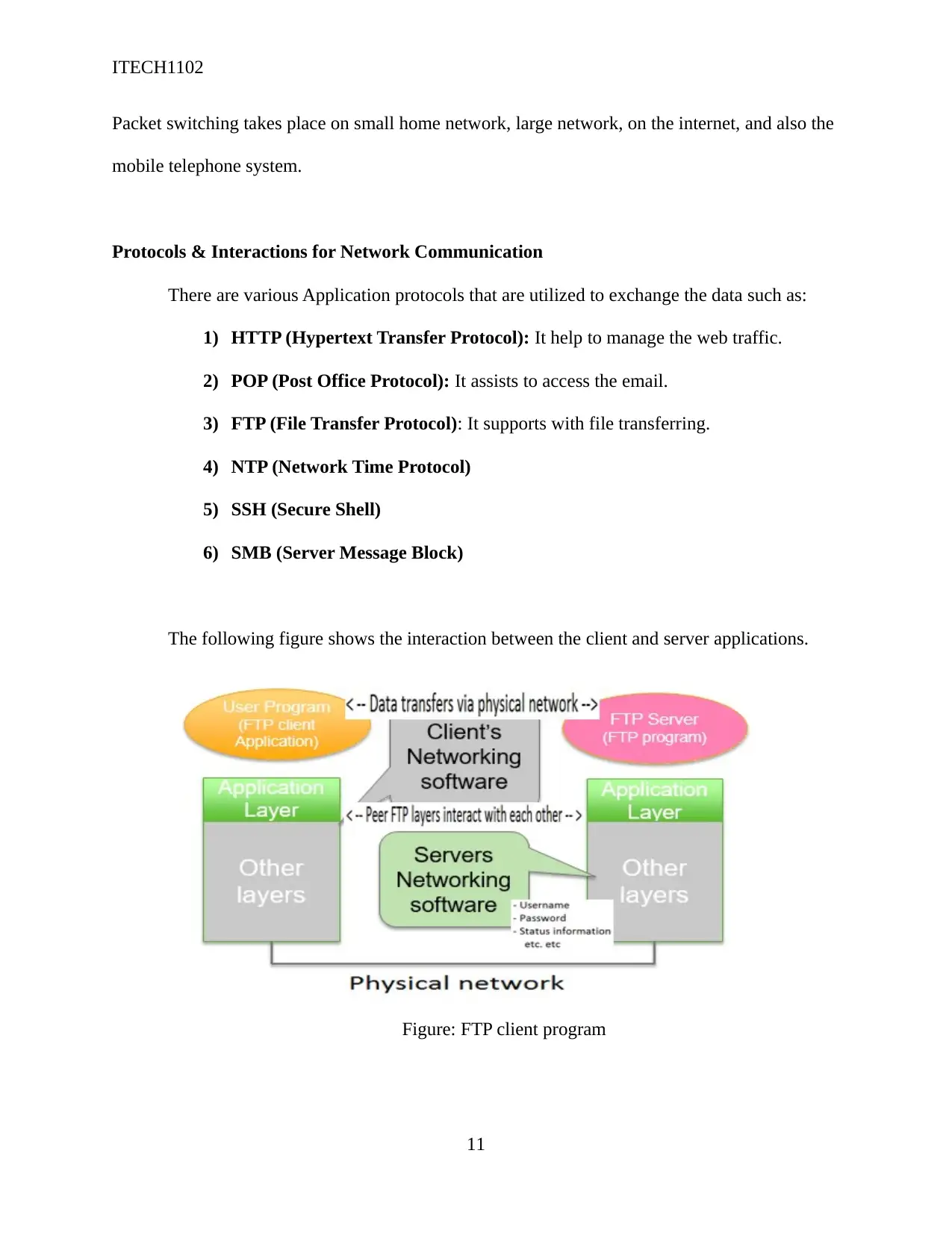
The following figure shows the interaction between the client and server applications.
Figure: FTP client program
11
Packet switching takes place on small home network, large network, on the internet, and also the
mobile telephone system.
Protocols & Interactions for Network Communication
There are various Application protocols that are utilized to exchange the data such as:
1) HTTP (Hypertext Transfer Protocol): It help to manage the web traffic.
2) POP (Post Office Protocol): It assists to access the email.
3) FTP (File Transfer Protocol): It supports with file transferring.
4) NTP (Network Time Protocol)
5) SSH (Secure Shell)
6) SMB (Server Message Block)
The following figure shows the interaction between the client and server applications.
Figure: FTP client program
11

ITECH1102
Figure; Comunication betweem Applications
Every single protocol defines rules which the applications as well as the linked server
programs should obey to have a successful communication amongst each other. The application
layer protocol’s role includes establishing consistent rules between the senders and receivers;
specify the message and handle the message dialogue (Hallberg, 2013).
Basics of Cloud Computing
Cloud computing denotes to an exercise that is utilizing a network of remote servers,
which are hosted on the internet for the storage, management and processing of the data, instead
of the local server/PC. Cloud computing ensures the availability of computing resources by a
third party, and such resources are hosted on the Internet.
Cloud Storage Services
These are the services that are provided by the following players- Microsoft’s OneDrive,
Dropbox, Apple’s iCloud, and the Google Drive. It facilitates limited empty storage/additional
space for storage based on the subscription. Based on the service, file synchronisation on the
12
Figure; Comunication betweem Applications
Every single protocol defines rules which the applications as well as the linked server
programs should obey to have a successful communication amongst each other. The application
layer protocol’s role includes establishing consistent rules between the senders and receivers;
specify the message and handle the message dialogue (Hallberg, 2013).
Basics of Cloud Computing
Cloud computing denotes to an exercise that is utilizing a network of remote servers,
which are hosted on the internet for the storage, management and processing of the data, instead
of the local server/PC. Cloud computing ensures the availability of computing resources by a
third party, and such resources are hosted on the Internet.
Cloud Storage Services
These are the services that are provided by the following players- Microsoft’s OneDrive,
Dropbox, Apple’s iCloud, and the Google Drive. It facilitates limited empty storage/additional
space for storage based on the subscription. Based on the service, file synchronisation on the
12

ITECH1102
local devices, capacity for sharing with some particular users, file access through access links
and so on are provided.
Fed Uni Cloud & Services
Fed Uni contains various services that run on local/cloud servers. Such local servers are
upgraded, maintained, backed-up, patched and so on with the assistance of Fed Uni technical
staff. Certain services are shifted to the cloud service providers. Even, Fed Uni contains various
servers hosting the services along with management of the workstation, management of the
identity etc.
Advantages of the Cloud Services
Allows instant deployment of advanced/new services.
Resolves various daily tasks of the technical staff.
It is underpinned with virtualization technologies that are stable.
It provides infinite resource’s illusion.
Disadvantages of Cloud Services
These services are charged.
The prices depend on the Memory, capacity, Disk type, CPU power, Backup, I/O,
and the type of service requested.
Cloud Infrastructure depends on Virtualization
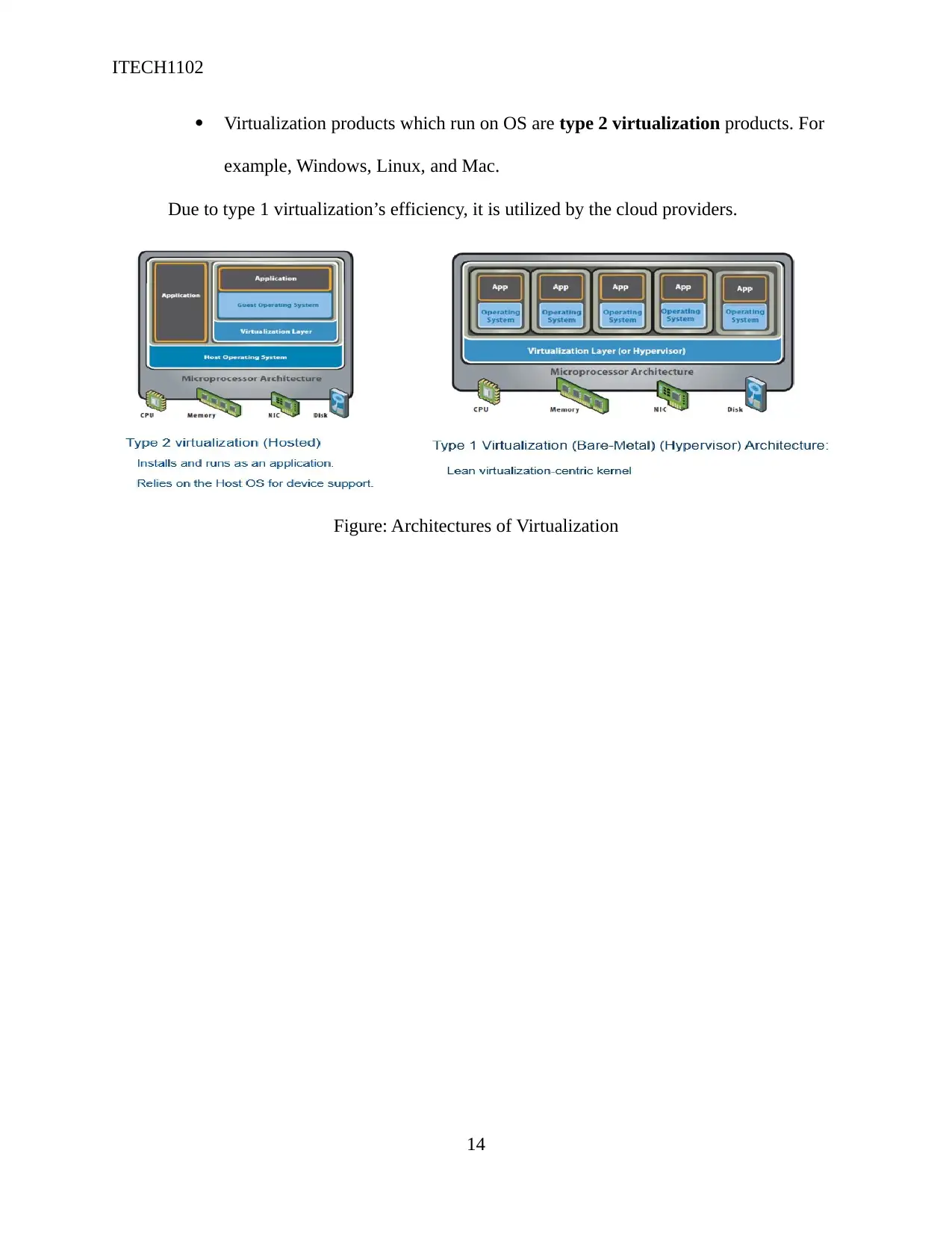
Virtualization uses the below mentioned terms:
Virtualization software running is referred as a host system, and the virtual OSs
are denoted as guests.
Type 1 virtualization systems: They run directly on hardware. For example,
virtual box setup for labs.
13
local devices, capacity for sharing with some particular users, file access through access links
and so on are provided.
Fed Uni Cloud & Services
Fed Uni contains various services that run on local/cloud servers. Such local servers are
upgraded, maintained, backed-up, patched and so on with the assistance of Fed Uni technical
staff. Certain services are shifted to the cloud service providers. Even, Fed Uni contains various
servers hosting the services along with management of the workstation, management of the
identity etc.
Advantages of the Cloud Services
Allows instant deployment of advanced/new services.
Resolves various daily tasks of the technical staff.
It is underpinned with virtualization technologies that are stable.
It provides infinite resource’s illusion.
Disadvantages of Cloud Services
These services are charged.
The prices depend on the Memory, capacity, Disk type, CPU power, Backup, I/O,
and the type of service requested.
Cloud Infrastructure depends on Virtualization
Virtualization uses the below mentioned terms:
Virtualization software running is referred as a host system, and the virtual OSs
are denoted as guests.
Type 1 virtualization systems: They run directly on hardware. For example,
virtual box setup for labs.
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
ITECH1102
Virtualization products which run on OS are type 2 virtualization products. For
example, Windows, Linux, and Mac.
Due to type 1 virtualization’s efficiency, it is utilized by the cloud providers.
Figure: Architectures of Virtualization
14
Virtualization products which run on OS are type 2 virtualization products. For
example, Windows, Linux, and Mac.
Due to type 1 virtualization’s efficiency, it is utilized by the cloud providers.
Figure: Architectures of Virtualization
14

ITECH1102
References
4. Networking Principles. Retrieved 7 January 2020, from
http://www.gerhardmueller.de/docs/UnixCommunicationFacilities/ip/node7.html
Computer Networking Devices Explained with Function. (2019). Retrieved 7 January 2020, from
https://www.computernetworkingnotes.com/networking-tutorials/computer-networking-
devices-explained-with-function.html
Hallberg, B. (2013). Networking. New York: McGraw-Hill Publishing.
How Address Resolution Protocol (ARP) works?. Retrieved 8 January 2020, from
https://www.geeksforgeeks.org/how-address-resolution-protocol-arp-works/
Network and connectivity. (2017). Boston Scientific Corporation. Retrieved from
https://www.bostonscientific.com/content/dam/Manuals/us/current-rev-en/360165-
002_LATITUDE_Programming_System_3300_Networking_Manual_OM_en-USA_S.pdf
Networking Layers. Retrieved 7 January 2020, from
https://www.d.umn.edu/~gshute/net/layers.xhtml
Ram, V. (2018). The Internet Layer in the TCP/IP Model. Retrieved 7 January 2020, from
https://www.tutorialspoint.com/The-Internet-Layer-in-the-TCP-IP-Model
TCP/IP Five-Layer Software Model Overview - Developer Help. (2020). Retrieved 8 January
2020, from https://microchipdeveloper.com/tcpip:tcp-ip-five-layer-model
15
References
4. Networking Principles. Retrieved 7 January 2020, from
http://www.gerhardmueller.de/docs/UnixCommunicationFacilities/ip/node7.html
Computer Networking Devices Explained with Function. (2019). Retrieved 7 January 2020, from
https://www.computernetworkingnotes.com/networking-tutorials/computer-networking-
devices-explained-with-function.html
Hallberg, B. (2013). Networking. New York: McGraw-Hill Publishing.
How Address Resolution Protocol (ARP) works?. Retrieved 8 January 2020, from
https://www.geeksforgeeks.org/how-address-resolution-protocol-arp-works/
Network and connectivity. (2017). Boston Scientific Corporation. Retrieved from
https://www.bostonscientific.com/content/dam/Manuals/us/current-rev-en/360165-
002_LATITUDE_Programming_System_3300_Networking_Manual_OM_en-USA_S.pdf
Networking Layers. Retrieved 7 January 2020, from
https://www.d.umn.edu/~gshute/net/layers.xhtml
Ram, V. (2018). The Internet Layer in the TCP/IP Model. Retrieved 7 January 2020, from
https://www.tutorialspoint.com/The-Internet-Layer-in-the-TCP-IP-Model
TCP/IP Five-Layer Software Model Overview - Developer Help. (2020). Retrieved 8 January
2020, from https://microchipdeveloper.com/tcpip:tcp-ip-five-layer-model
15
1 out of 15
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





