Local Area Networking Technologies: Design and Implementation
VerifiedAdded on 2023/04/22
|43
|6137
|122
Report
AI Summary
This report provides a comprehensive overview of local area networking (LAN) technologies. It begins by examining various network topologies such as mesh, bus, ring, star, tree, and hybrid, ultimately recommending the star topology for its ease of installation, configuration, and troubleshooting. The report then delves into traffic-intensive services affecting network performance, including bonding, speed, and distance, as well as quality of service (QoS) parameters like delay, jitter, and bandwidth. It addresses LAN concerns like availability, security, and scalability, proposing a hierarchical network model for improved flexibility and security. The design and implementation of a LAN infrastructure are detailed, covering device selection (routers, switches, servers, computers), network component evaluation, and security considerations. Finally, the report discusses network management, including monitoring with tools like Wireshark, improving security and reliability, and evaluating network performance.

Local Area Networking 1
LOCAL AREA NETWORKING TECHNOLOGIES
By (Student names)
(Class Name)
(Tutor Name)
(University Name)
(Date)
LOCAL AREA NETWORKING TECHNOLOGIES
By (Student names)
(Class Name)
(Tutor Name)
(University Name)
(Date)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Local Area Networking 2
Table of Contents
Task 1: Understand the impact of LAN technologies.....................................................................4
1.1. Network topologies available in the market.....................................................................4
Mesh topology..........................................................................................................................4
Bus Topology............................................................................................................................5
RING Topology.........................................................................................................................6
STAR Topology.........................................................................................................................7
TREE Topology........................................................................................................................8
HYBRID Topology....................................................................................................................9
Most appropriate and suitable technology/topology: Star topology......................................10
1.2 Traffic intensive services of network performance and Quality of Services.......................10
Traffic intensive services of network performance.................................................................10
Quality of Services (QoS).......................................................................................................11
1.3 Local Area Network concerns and recommendations.........................................................12
Hierarchical network model...................................................................................................12
Task 2: Designing LAN infrastructures.........................................................................................14
2.1 Design network infrastructure..............................................................................................14
Topology.................................................................................................................................14
Devices...................................................................................................................................14
Technology.............................................................................................................................15
2.2: Network components and design.......................................................................................17
Evaluating Network components and design.........................................................................17
Security& Applications...........................................................................................................17
Users & Scalability.................................................................................................................18
Task 3: Implementing LAN infrastructures..................................................................................20
3.1: Building and configuring the entire network......................................................................20
Configuration..........................................................................................................................20
Technology and security........................................................................................................26
Documentation.......................................................................................................................26
Security...................................................................................................................................29
3.2: Reviewing and testing the entire network...........................................................................29
Table of Contents
Task 1: Understand the impact of LAN technologies.....................................................................4
1.1. Network topologies available in the market.....................................................................4
Mesh topology..........................................................................................................................4
Bus Topology............................................................................................................................5
RING Topology.........................................................................................................................6
STAR Topology.........................................................................................................................7
TREE Topology........................................................................................................................8
HYBRID Topology....................................................................................................................9
Most appropriate and suitable technology/topology: Star topology......................................10
1.2 Traffic intensive services of network performance and Quality of Services.......................10
Traffic intensive services of network performance.................................................................10
Quality of Services (QoS).......................................................................................................11
1.3 Local Area Network concerns and recommendations.........................................................12
Hierarchical network model...................................................................................................12
Task 2: Designing LAN infrastructures.........................................................................................14
2.1 Design network infrastructure..............................................................................................14
Topology.................................................................................................................................14
Devices...................................................................................................................................14
Technology.............................................................................................................................15
2.2: Network components and design.......................................................................................17
Evaluating Network components and design.........................................................................17
Security& Applications...........................................................................................................17
Users & Scalability.................................................................................................................18
Task 3: Implementing LAN infrastructures..................................................................................20
3.1: Building and configuring the entire network......................................................................20
Configuration..........................................................................................................................20
Technology and security........................................................................................................26
Documentation.......................................................................................................................26
Security...................................................................................................................................29
3.2: Reviewing and testing the entire network...........................................................................29

Local Area Networking 3
Task 4: Managing LAN infrastructure..........................................................................................34
4.1 Network monitoring: WIRE SHARK..................................................................................34
Wire shark monitoring tool....................................................................................................34
4.2: Improving security, reliability, and performance in a local area network..........................35
4.3: Evaluating the network performance..................................................................................36
Task 4: Managing LAN infrastructure..........................................................................................34
4.1 Network monitoring: WIRE SHARK..................................................................................34
Wire shark monitoring tool....................................................................................................34
4.2: Improving security, reliability, and performance in a local area network..........................35
4.3: Evaluating the network performance..................................................................................36
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Local Area Networking 4
Task 1: Understand the impact of LAN technologies
1.1. Network topologies available in the market
The network topology is the design of the network infrastructure which illustrates the general
layout of the network devices and it allows effective communications, therefore the proposed
local area network topology will essentially define the geographical arrangement of the proposed
network devices. Below are the various types of network topologies in the market (Benjamin,
2003, p. 34).
Mesh topology.
The mesh topology is a point to point designs of topology that make use of the dedicated
links between the network devices , however it is not the best design since it wastes allot of
transmission media and also it is quite challenging to do installation and configuration. The
increase of the network devices in this type of network leads to decrease in the communications
speed. One of the feature of mesh topology is robustness (Blair & Durai, 2016, p. 57)
Figure 1: Mesh topology
Task 1: Understand the impact of LAN technologies
1.1. Network topologies available in the market
The network topology is the design of the network infrastructure which illustrates the general
layout of the network devices and it allows effective communications, therefore the proposed
local area network topology will essentially define the geographical arrangement of the proposed
network devices. Below are the various types of network topologies in the market (Benjamin,
2003, p. 34).
Mesh topology.
The mesh topology is a point to point designs of topology that make use of the dedicated
links between the network devices , however it is not the best design since it wastes allot of
transmission media and also it is quite challenging to do installation and configuration. The
increase of the network devices in this type of network leads to decrease in the communications
speed. One of the feature of mesh topology is robustness (Blair & Durai, 2016, p. 57)
Figure 1: Mesh topology
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Local Area Networking 5
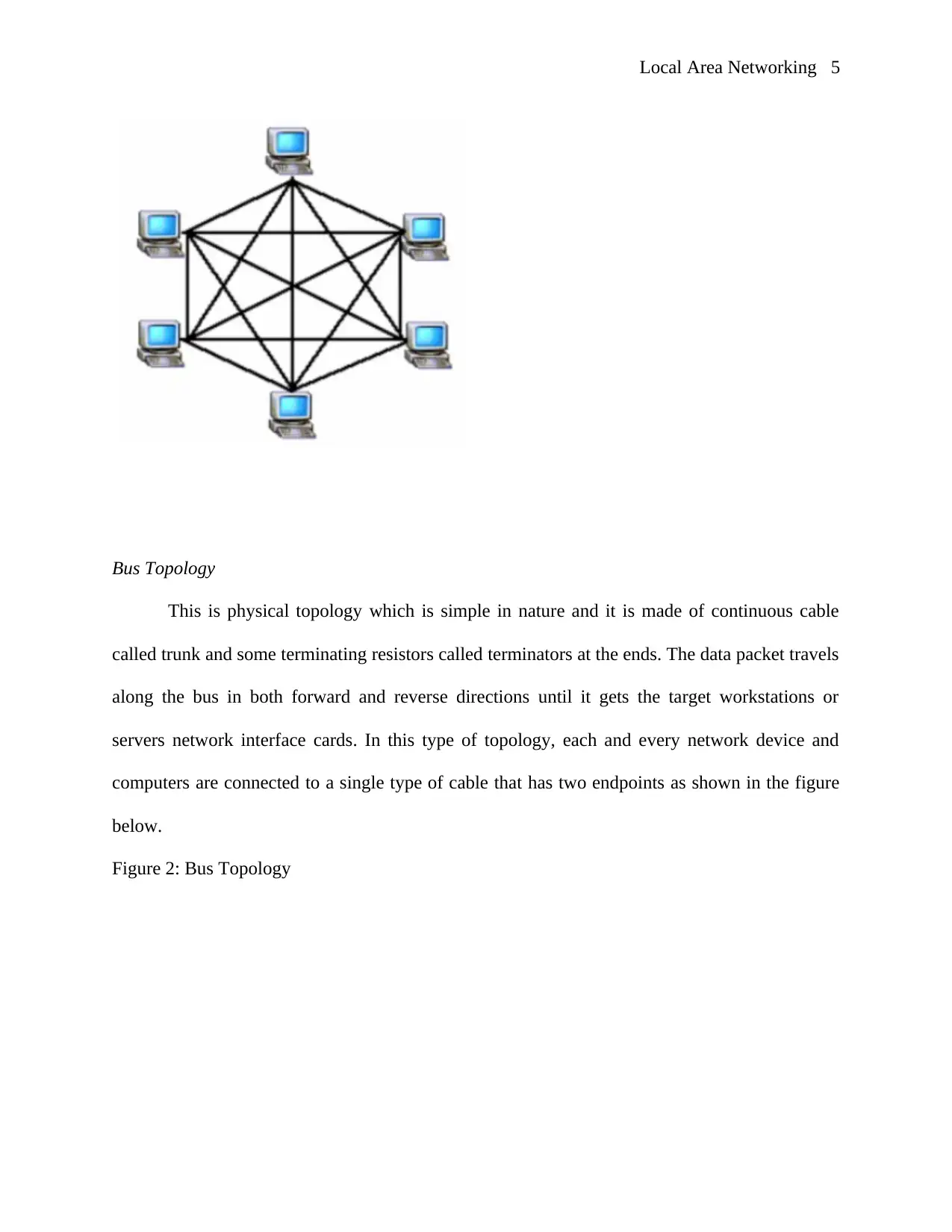
Bus Topology
This is physical topology which is simple in nature and it is made of continuous cable
called trunk and some terminating resistors called terminators at the ends. The data packet travels
along the bus in both forward and reverse directions until it gets the target workstations or
servers network interface cards. In this type of topology, each and every network device and
computers are connected to a single type of cable that has two endpoints as shown in the figure
below.
Figure 2: Bus Topology
Bus Topology
This is physical topology which is simple in nature and it is made of continuous cable
called trunk and some terminating resistors called terminators at the ends. The data packet travels
along the bus in both forward and reverse directions until it gets the target workstations or
servers network interface cards. In this type of topology, each and every network device and
computers are connected to a single type of cable that has two endpoints as shown in the figure
below.
Figure 2: Bus Topology
Local Area Networking 6
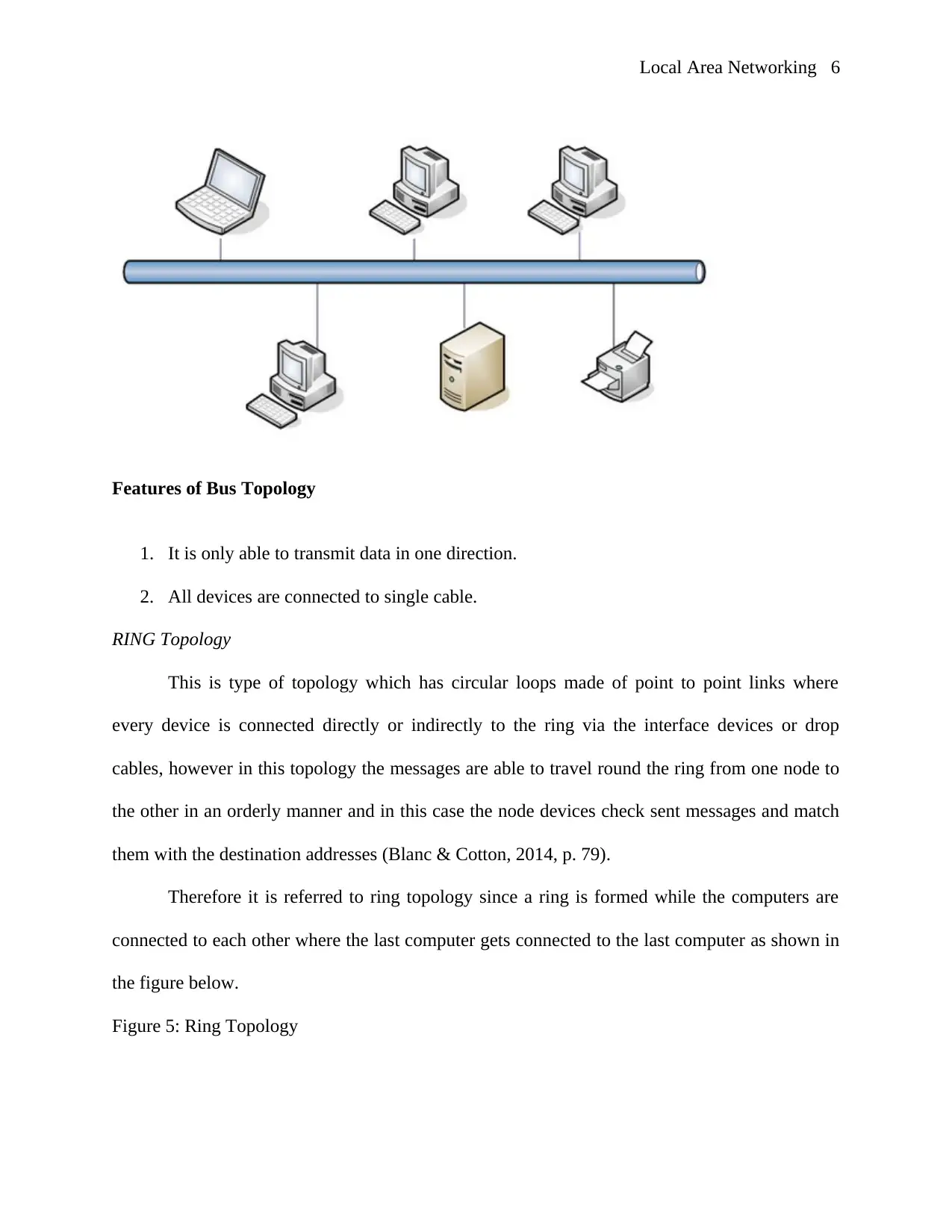
Features of Bus Topology
1. It is only able to transmit data in one direction.
2. All devices are connected to single cable.
RING Topology
This is type of topology which has circular loops made of point to point links where
every device is connected directly or indirectly to the ring via the interface devices or drop
cables, however in this topology the messages are able to travel round the ring from one node to
the other in an orderly manner and in this case the node devices check sent messages and match
them with the destination addresses (Blanc & Cotton, 2014, p. 79).
Therefore it is referred to ring topology since a ring is formed while the computers are
connected to each other where the last computer gets connected to the last computer as shown in
the figure below.
Figure 5: Ring Topology
Features of Bus Topology
1. It is only able to transmit data in one direction.
2. All devices are connected to single cable.
RING Topology
This is type of topology which has circular loops made of point to point links where
every device is connected directly or indirectly to the ring via the interface devices or drop
cables, however in this topology the messages are able to travel round the ring from one node to
the other in an orderly manner and in this case the node devices check sent messages and match
them with the destination addresses (Blanc & Cotton, 2014, p. 79).
Therefore it is referred to ring topology since a ring is formed while the computers are
connected to each other where the last computer gets connected to the last computer as shown in
the figure below.
Figure 5: Ring Topology
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Local Area Networking 7
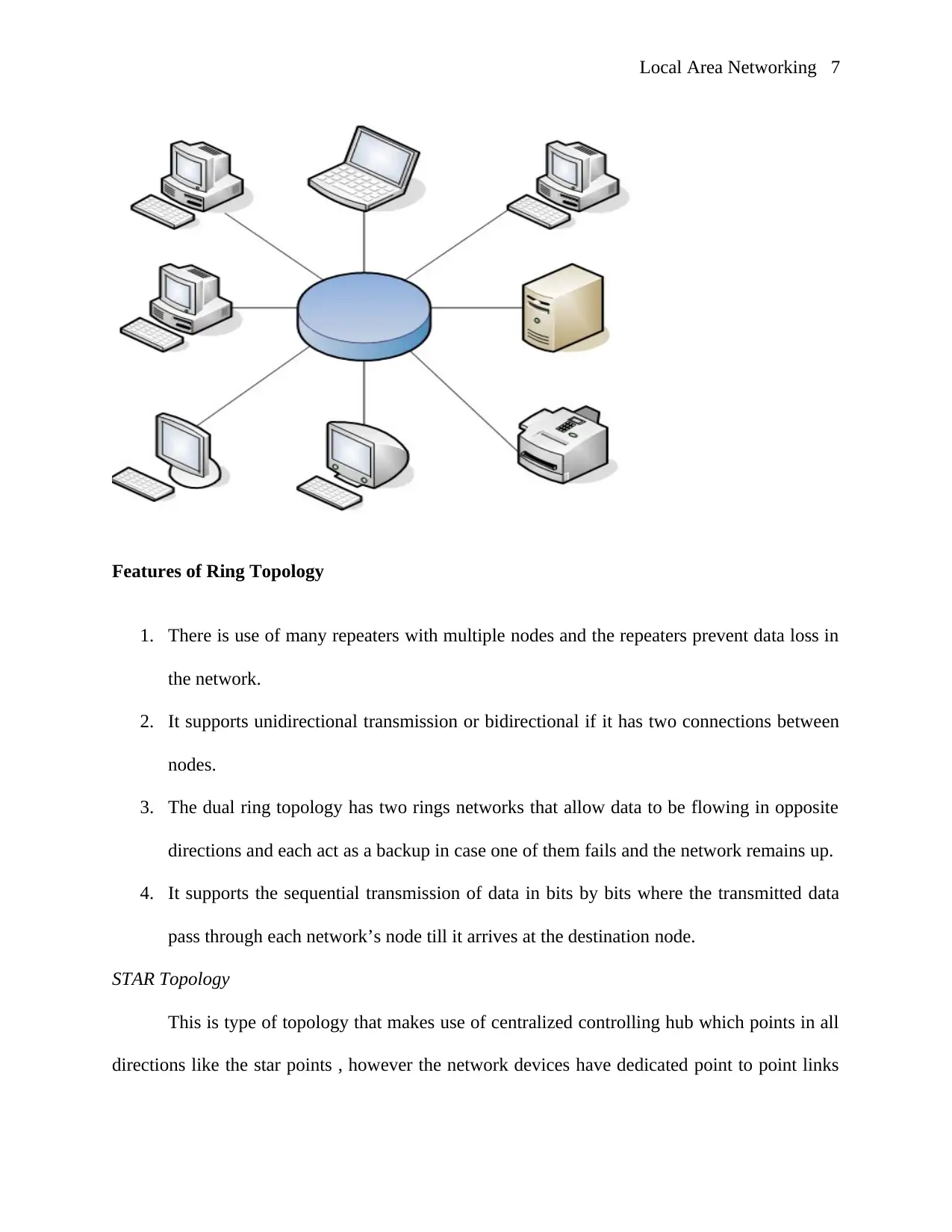
Features of Ring Topology
1. There is use of many repeaters with multiple nodes and the repeaters prevent data loss in
the network.
2. It supports unidirectional transmission or bidirectional if it has two connections between
nodes.
3. The dual ring topology has two rings networks that allow data to be flowing in opposite
directions and each act as a backup in case one of them fails and the network remains up.
4. It supports the sequential transmission of data in bits by bits where the transmitted data
pass through each network’s node till it arrives at the destination node.
STAR Topology
This is type of topology that makes use of centralized controlling hub which points in all
directions like the star points , however the network devices have dedicated point to point links
Features of Ring Topology
1. There is use of many repeaters with multiple nodes and the repeaters prevent data loss in
the network.
2. It supports unidirectional transmission or bidirectional if it has two connections between
nodes.
3. The dual ring topology has two rings networks that allow data to be flowing in opposite
directions and each act as a backup in case one of them fails and the network remains up.
4. It supports the sequential transmission of data in bits by bits where the transmitted data
pass through each network’s node till it arrives at the destination node.
STAR Topology
This is type of topology that makes use of centralized controlling hub which points in all
directions like the star points , however the network devices have dedicated point to point links
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Local Area Networking 8
to the central hub , therefore this type of topology is used to control the collisions by keeping the
communication lines open and free from the network traffics (Burridge, 2015).
Therefore this topology enables the connection of devices to one hub through the network
cables where the hub acts as a central node to which all nodes devices are connected to as shown
in the figure below.
Figure 6: Start Topology
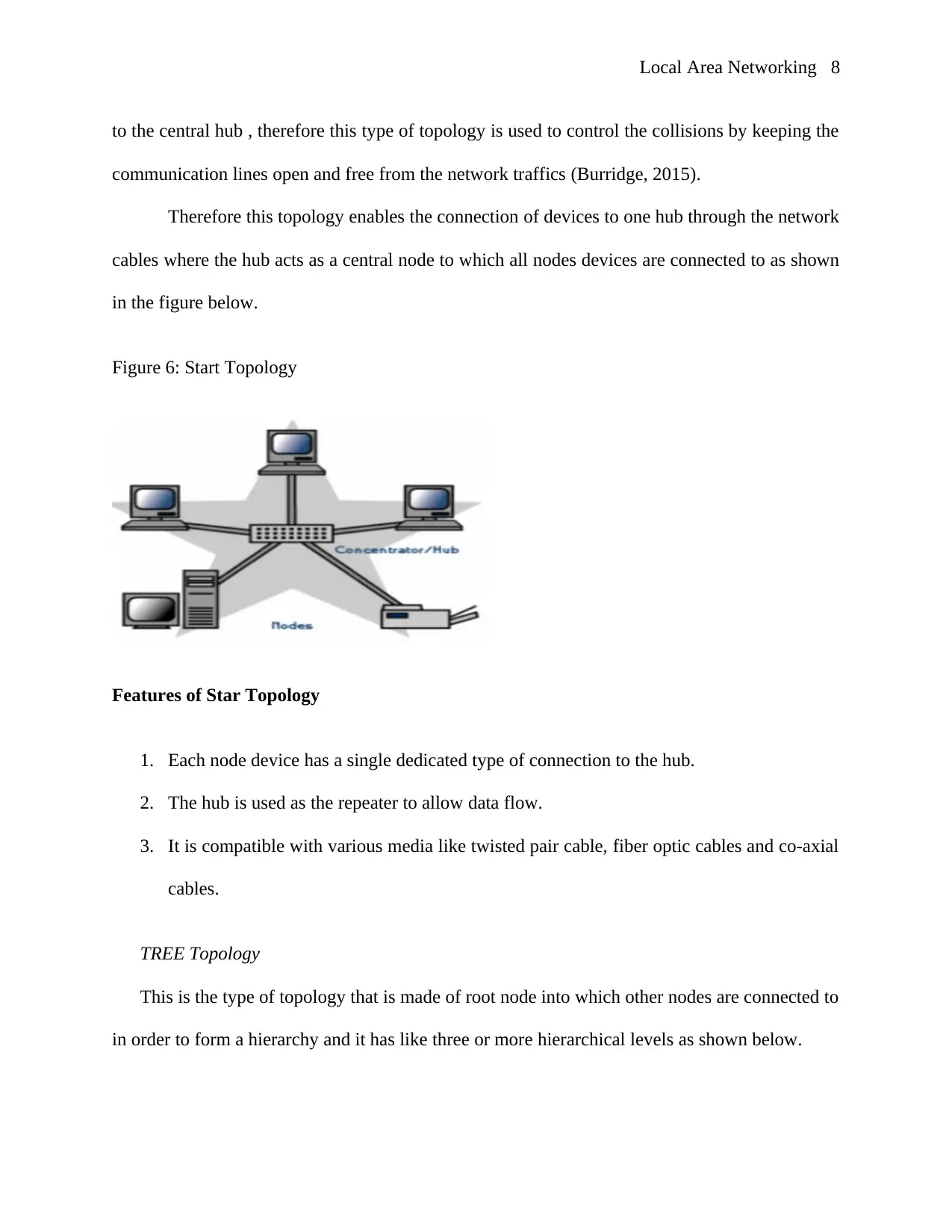
Features of Star Topology
1. Each node device has a single dedicated type of connection to the hub.
2. The hub is used as the repeater to allow data flow.
3. It is compatible with various media like twisted pair cable, fiber optic cables and co-axial
cables.
TREE Topology
This is the type of topology that is made of root node into which other nodes are connected to
in order to form a hierarchy and it has like three or more hierarchical levels as shown below.
to the central hub , therefore this type of topology is used to control the collisions by keeping the
communication lines open and free from the network traffics (Burridge, 2015).
Therefore this topology enables the connection of devices to one hub through the network
cables where the hub acts as a central node to which all nodes devices are connected to as shown
in the figure below.
Figure 6: Start Topology
Features of Star Topology
1. Each node device has a single dedicated type of connection to the hub.
2. The hub is used as the repeater to allow data flow.
3. It is compatible with various media like twisted pair cable, fiber optic cables and co-axial
cables.
TREE Topology
This is the type of topology that is made of root node into which other nodes are connected to
in order to form a hierarchy and it has like three or more hierarchical levels as shown below.
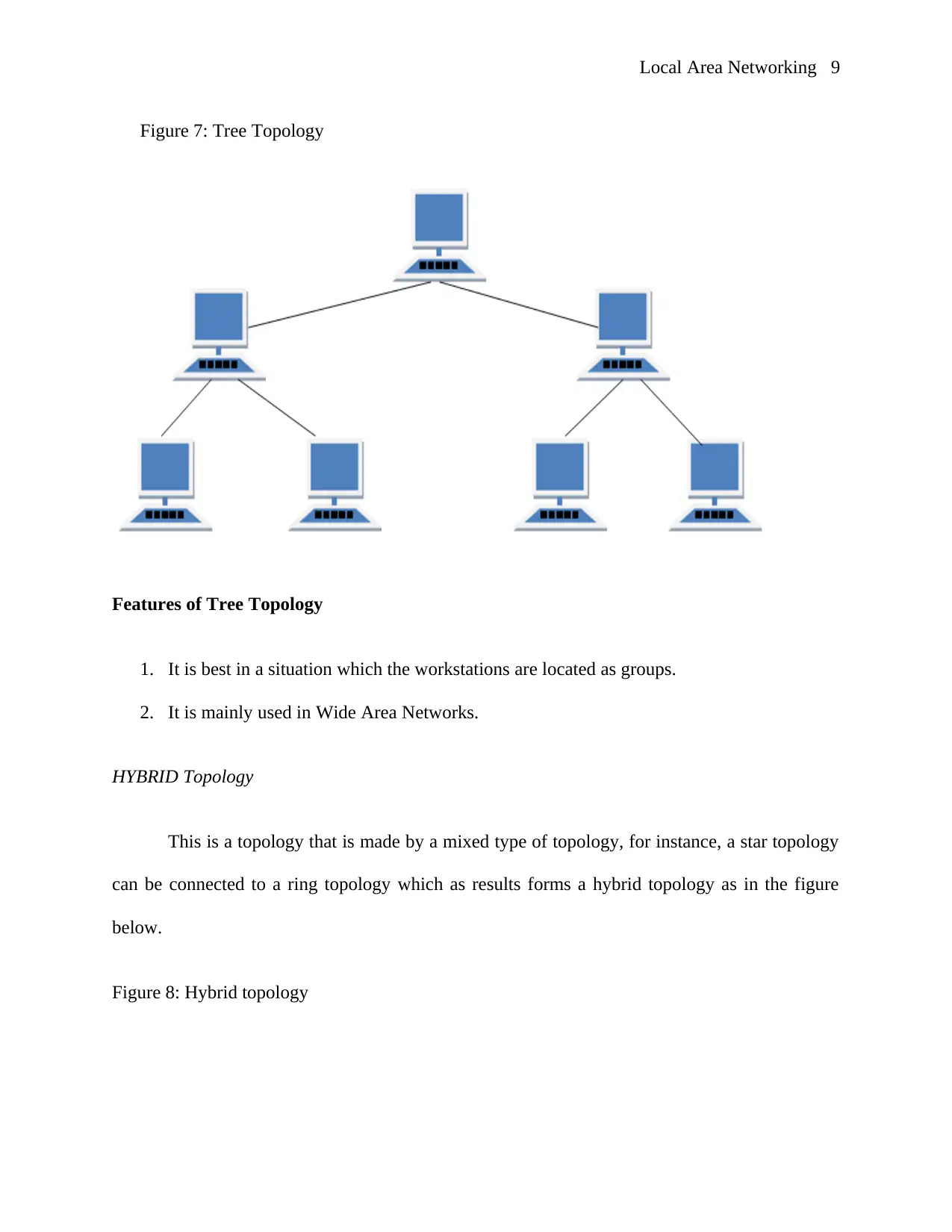
Local Area Networking 9
Figure 7: Tree Topology
Features of Tree Topology
1. It is best in a situation which the workstations are located as groups.
2. It is mainly used in Wide Area Networks.
HYBRID Topology
This is a topology that is made by a mixed type of topology, for instance, a star topology
can be connected to a ring topology which as results forms a hybrid topology as in the figure
below.
Figure 8: Hybrid topology
Figure 7: Tree Topology
Features of Tree Topology
1. It is best in a situation which the workstations are located as groups.
2. It is mainly used in Wide Area Networks.
HYBRID Topology
This is a topology that is made by a mixed type of topology, for instance, a star topology
can be connected to a ring topology which as results forms a hybrid topology as in the figure
below.
Figure 8: Hybrid topology
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Local Area Networking 10
Features of Hybrid Topology
1. It is formed by two combined topologies.
2. It adopts both advantages and disadvantages of the combined topologies used.
Most appropriate and suitable technology/topology: Star topology
In the proposed network infrastructure the star topology is the most appropriate topology,
this is because there is use of many VLANs that are used to connect the four departmental
networks and the various network servers, however this network installation is easy to install,
configure, troubleshoot, modify, upgrade and failure of one node do not affect other nodes in the
network (Cerpa, 2010, p. 69).
1.2 Traffic intensive services of network performance and Quality of Services
Traffic intensive services of network performance
The network traffic intensive service determines the performance of the network and is
determined by various factors which include the following.
i. Bonding-
Features of Hybrid Topology
1. It is formed by two combined topologies.
2. It adopts both advantages and disadvantages of the combined topologies used.
Most appropriate and suitable technology/topology: Star topology
In the proposed network infrastructure the star topology is the most appropriate topology,
this is because there is use of many VLANs that are used to connect the four departmental
networks and the various network servers, however this network installation is easy to install,
configure, troubleshoot, modify, upgrade and failure of one node do not affect other nodes in the
network (Cerpa, 2010, p. 69).
1.2 Traffic intensive services of network performance and Quality of Services
Traffic intensive services of network performance
The network traffic intensive service determines the performance of the network and is
determined by various factors which include the following.
i. Bonding-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Local Area Networking 11
This is used in the creation of the network redundancy in the network connections where the
physical links create logical links which are aggregated with IEEE 802.3ad
ii. Speed-
This is the networking speed, throughput, and bandwidth that measures the amount of data that
moves through the network in a given duration of time, therefore the connection speed is the
network speed which is considered while buying networking devices to be used.
iii. Distance-
This is far that data packet travels in order to receive from one point on the network to the other
end and it refers to distances traveled by data packets before they are rebuilt by a switch (Dean,
2013, p. 156).
Quality of Services (QoS)
The quality of service in the network is measurable through the use of various parameters
which includes the following:
Delay: This is the specification of the duration taken by the bit of data packet to travel
across the entire network from a certain node device to the other which is measured in
terms of seconds.
Delay variation: This is the in the end to end one-way delays between a set of selected
packets in the flow where the lost packets get ignored.
Bandwidth (maximum data transfer rates): This refers to the total amount of data
which is transmitted in any given time in seconds through the network.
Packet loss rates: This is the rate at which the data packet that travels over the
network fails to arrive at its destinations.
This is used in the creation of the network redundancy in the network connections where the
physical links create logical links which are aggregated with IEEE 802.3ad
ii. Speed-
This is the networking speed, throughput, and bandwidth that measures the amount of data that
moves through the network in a given duration of time, therefore the connection speed is the
network speed which is considered while buying networking devices to be used.
iii. Distance-
This is far that data packet travels in order to receive from one point on the network to the other
end and it refers to distances traveled by data packets before they are rebuilt by a switch (Dean,
2013, p. 156).
Quality of Services (QoS)
The quality of service in the network is measurable through the use of various parameters
which includes the following:
Delay: This is the specification of the duration taken by the bit of data packet to travel
across the entire network from a certain node device to the other which is measured in
terms of seconds.
Delay variation: This is the in the end to end one-way delays between a set of selected
packets in the flow where the lost packets get ignored.
Bandwidth (maximum data transfer rates): This refers to the total amount of data
which is transmitted in any given time in seconds through the network.
Packet loss rates: This is the rate at which the data packet that travels over the
network fails to arrive at its destinations.

Local Area Networking 12
Excessive latency: This refers to the delay that could happen in the data
communications over the computer networks which could even have some impacts on
the network bandwidth as well.
Jitter: This refers to the variations occurring in the delay of the received data packets
which occurs due to the network’s congestions, improper queues, configurations
errors, and thus the delay vary instead of being constant (Forouzan & Mosharraf,
2012, p. 89).
When the network is operating without any quality of service will impact the operation of the
organization business operations as follows:
It does not guarantee services to the customers.
It is not credible and is less reliable too.
There are no guaranteed profits.
It easily loss to the competitors of their service.
It has less delivery and has no satisfaction to customers.
It experiences long outage and downtime.
It results to use of more time on customer calls while giving explanations.
Number of complaints are received from the customers, stakeholders and the
shareholders.
1.3 Local Area Network concerns and recommendations
One of the concerns with LAN is availability, security, and scalability. This can be sorted
out by implementing a hierarchical network model
Excessive latency: This refers to the delay that could happen in the data
communications over the computer networks which could even have some impacts on
the network bandwidth as well.
Jitter: This refers to the variations occurring in the delay of the received data packets
which occurs due to the network’s congestions, improper queues, configurations
errors, and thus the delay vary instead of being constant (Forouzan & Mosharraf,
2012, p. 89).
When the network is operating without any quality of service will impact the operation of the
organization business operations as follows:
It does not guarantee services to the customers.
It is not credible and is less reliable too.
There are no guaranteed profits.
It easily loss to the competitors of their service.
It has less delivery and has no satisfaction to customers.
It experiences long outage and downtime.
It results to use of more time on customer calls while giving explanations.
Number of complaints are received from the customers, stakeholders and the
shareholders.
1.3 Local Area Network concerns and recommendations
One of the concerns with LAN is availability, security, and scalability. This can be sorted
out by implementing a hierarchical network model
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 43
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





