MN621 Advanced Network Design: A Hospital Network Design Report
VerifiedAdded on 2024/05/15
|23
|2615
|329
Report
AI Summary
This report provides a comprehensive solution for designing and implementing a hospital network. It begins with a detailed questionnaire designed to gather requirements from users, management, and other staff, with justifications provided for each question. The report outlines a validation and verification plan involving various stakeholders to ensure all requirements are met. It then details the network design, including the use of EIGRP protocol, multilayer switches, and Cisco routers. The report also discusses network design reliability, focusing on performance monitoring, malicious activity detection, and bandwidth sufficiency. Finally, the network is tested on a given application set to ensure its functionality and reliability. Desklib offers this and many other solved assignments to aid students in their studies.

MN621 Advanced Network Design
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction..........................................................................................................................................3
Part 1....................................................................................................................................................4
Questionnaire.......................................................................................................................................4
Justification of designed Questionnaire...............................................................................................5
Validation and verification plan...........................................................................................................7
Part 2..................................................................................................................................................10
Gather the information to develop the network without talk to users and staff.........................10
Part 3..................................................................................................................................................11
Network Design..................................................................................................................................11
Network design reliability..................................................................................................................13
Application Sets..................................................................................................................................14
Conclusion..........................................................................................................................................22
References..........................................................................................................................................23
2
Introduction..........................................................................................................................................3
Part 1....................................................................................................................................................4
Questionnaire.......................................................................................................................................4
Justification of designed Questionnaire...............................................................................................5
Validation and verification plan...........................................................................................................7
Part 2..................................................................................................................................................10
Gather the information to develop the network without talk to users and staff.........................10
Part 3..................................................................................................................................................11
Network Design..................................................................................................................................11
Network design reliability..................................................................................................................13
Application Sets..................................................................................................................................14
Conclusion..........................................................................................................................................22
References..........................................................................................................................................23
2

Introduction
In this report, a hospital network is to be designed and implemented. For designing the network
requirements are to be gathered from the stakeholders, for that a questionnaire is to be
developed in this report. A detailed justification will be provided for the all questions. The network
will be implemented using Cisco Packet Tracer and will be tested on the given application set.
3
In this report, a hospital network is to be designed and implemented. For designing the network
requirements are to be gathered from the stakeholders, for that a questionnaire is to be
developed in this report. A detailed justification will be provided for the all questions. The network
will be implemented using Cisco Packet Tracer and will be tested on the given application set.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Part 1
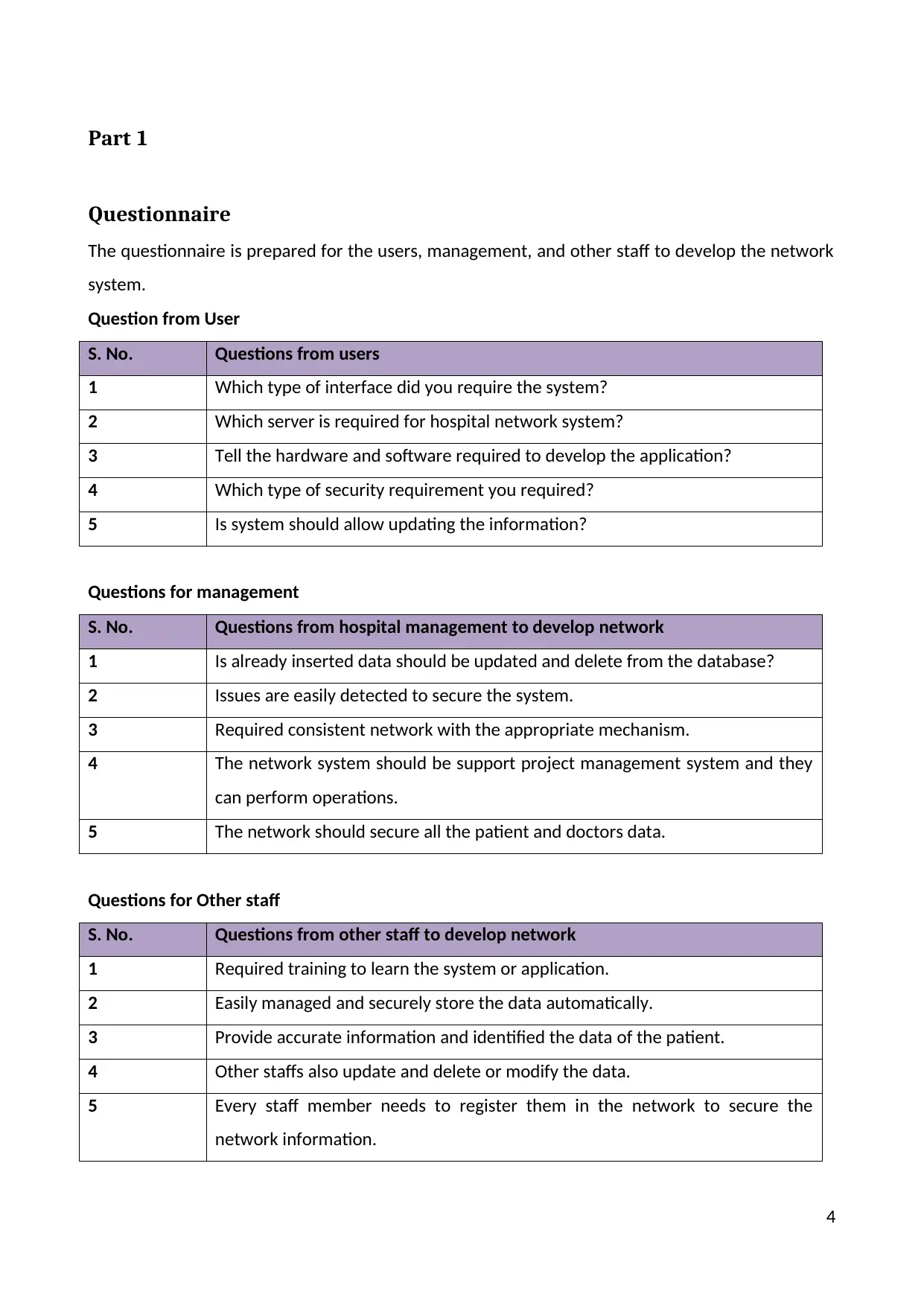
Questionnaire
The questionnaire is prepared for the users, management, and other staff to develop the network
system.
Question from User
S. No. Questions from users
1 Which type of interface did you require the system?
2 Which server is required for hospital network system?
3 Tell the hardware and software required to develop the application?
4 Which type of security requirement you required?
5 Is system should allow updating the information?
Questions for management
S. No. Questions from hospital management to develop network
1 Is already inserted data should be updated and delete from the database?
2 Issues are easily detected to secure the system.
3 Required consistent network with the appropriate mechanism.
4 The network system should be support project management system and they
can perform operations.
5 The network should secure all the patient and doctors data.
Questions for Other staff
S. No. Questions from other staff to develop network
1 Required training to learn the system or application.
2 Easily managed and securely store the data automatically.
3 Provide accurate information and identified the data of the patient.
4 Other staffs also update and delete or modify the data.
5 Every staff member needs to register them in the network to secure the
network information.
4
Questionnaire
The questionnaire is prepared for the users, management, and other staff to develop the network
system.
Question from User
S. No. Questions from users
1 Which type of interface did you require the system?
2 Which server is required for hospital network system?
3 Tell the hardware and software required to develop the application?
4 Which type of security requirement you required?
5 Is system should allow updating the information?
Questions for management
S. No. Questions from hospital management to develop network
1 Is already inserted data should be updated and delete from the database?
2 Issues are easily detected to secure the system.
3 Required consistent network with the appropriate mechanism.
4 The network system should be support project management system and they
can perform operations.
5 The network should secure all the patient and doctors data.
Questions for Other staff
S. No. Questions from other staff to develop network
1 Required training to learn the system or application.
2 Easily managed and securely store the data automatically.
3 Provide accurate information and identified the data of the patient.
4 Other staffs also update and delete or modify the data.
5 Every staff member needs to register them in the network to secure the
network information.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Justification of designed Questionnaire
Justification of user questions:
1. The first question of the user provides the information of system interface. Which type of
interface did it require? The user tells us about the system interface requirement for
hospital network system. With this question, we also get what technology they want for
the network. According to the scenario, the network is designed by using LAN technology.
2. The second question is providing the information of a server that is required to develop the
network for hospital application. For network development, the required server is a
database server, DNS server etc.
3. The third question of user provides the information about required hardware and software
details to develop the network system for the hospital application. The hardware and
software requirement is given as select windows server with latest version to run the
application and network should support the internet information easily.
4. Fourth question is designed to take the information about the security in the hospital
network. The user wants a login and registered feature in the network. Is the network has
register and login feature in the network then it can be secure from the malware users and
untrusted users?
5. Fifth question of user questionnaire provides the information about the network flexibility
with the data. According to the user requirement, the user should able to modify their
stored data in the network.
Justification of management questionnaire:
1. First question of management questionnaire provide the information of what they with
network regarding data modification. The management staff can able to modify the data
from the stored data in the network. The management staff should log in to the network
and then they can able to modify the data in the network.
2. With second questions, the developer should apply the security strategies to secure the
network. The strategy should be able to detect the issues and threats from the network
when they are occurred and should be able to resolve them. The network should be secure
from the malware users, hacker and from internal attackers.
3. The network should be able to run on every platform of the hospital management. The
network should be used LAN technology to provide the consistent network. The network
5
Justification of user questions:
1. The first question of the user provides the information of system interface. Which type of
interface did it require? The user tells us about the system interface requirement for
hospital network system. With this question, we also get what technology they want for
the network. According to the scenario, the network is designed by using LAN technology.
2. The second question is providing the information of a server that is required to develop the
network for hospital application. For network development, the required server is a
database server, DNS server etc.
3. The third question of user provides the information about required hardware and software
details to develop the network system for the hospital application. The hardware and
software requirement is given as select windows server with latest version to run the
application and network should support the internet information easily.
4. Fourth question is designed to take the information about the security in the hospital
network. The user wants a login and registered feature in the network. Is the network has
register and login feature in the network then it can be secure from the malware users and
untrusted users?
5. Fifth question of user questionnaire provides the information about the network flexibility
with the data. According to the user requirement, the user should able to modify their
stored data in the network.
Justification of management questionnaire:
1. First question of management questionnaire provide the information of what they with
network regarding data modification. The management staff can able to modify the data
from the stored data in the network. The management staff should log in to the network
and then they can able to modify the data in the network.
2. With second questions, the developer should apply the security strategies to secure the
network. The strategy should be able to detect the issues and threats from the network
when they are occurred and should be able to resolve them. The network should be secure
from the malware users, hacker and from internal attackers.
3. The network should be able to run on every platform of the hospital management. The
network should be used LAN technology to provide the consistent network. The network
5

should be consistent by using the Ethernet and cables. To develop the network use
appropriate strategies and mechanism.
4. The hospital management staff should able to perform the operation in the network
without any problems. The network should allow the management staff to make changes
in the network according to the requirement.
5. The fifth question of the management questionnaire provides the information about the
network security. The network should be secure for the hospital management team,
doctors, and patient who are registered in the hospital network. The network should use
encryption technique to identify the incoming data of the patient. The patient and doctors
should register them first in the network then they are able to make modification in the
stored data.
Justification of the other staff questionnaire:
1. The other staff required training to learn the network. So, the organization should provide
training to learn the network. Every staff should know about the network functionality and
how they perform the operation in the network. With this question the staffs want a
training session from the organization to understand the network working.
2. The network should be easily managed by the staff member of the hospital without any
extra effort. The hospital should require technical staff to perform the operation in the
network. With the help of technical staff, the other member also performs the different
operation in the designed network of the hospital.
3. The network should secure all the important information of the organization, staff, and
patient. So, secure the information, apply the encryption technique in the network. The
developer also applies any other security approach to secure the information from the
hackers and internal attackers.
4. The network should allow other staff members to make modification in the network if
required. To update the data and access the network the every staff member should
register in the network.
5. The network should be secure form the malware users. In a network, the developer should
implement some security techniques that secure the network from the attacker and that
type of users who are not registered in the network. To access the network the users, staff,
and another member of the hospital should register them in the network and then login in
the system. With these questions, the developer and designer should identify what is the
requirement to develop the network system for the hospital [5].
6
appropriate strategies and mechanism.
4. The hospital management staff should able to perform the operation in the network
without any problems. The network should allow the management staff to make changes
in the network according to the requirement.
5. The fifth question of the management questionnaire provides the information about the
network security. The network should be secure for the hospital management team,
doctors, and patient who are registered in the hospital network. The network should use
encryption technique to identify the incoming data of the patient. The patient and doctors
should register them first in the network then they are able to make modification in the
stored data.
Justification of the other staff questionnaire:
1. The other staff required training to learn the network. So, the organization should provide
training to learn the network. Every staff should know about the network functionality and
how they perform the operation in the network. With this question the staffs want a
training session from the organization to understand the network working.
2. The network should be easily managed by the staff member of the hospital without any
extra effort. The hospital should require technical staff to perform the operation in the
network. With the help of technical staff, the other member also performs the different
operation in the designed network of the hospital.
3. The network should secure all the important information of the organization, staff, and
patient. So, secure the information, apply the encryption technique in the network. The
developer also applies any other security approach to secure the information from the
hackers and internal attackers.
4. The network should allow other staff members to make modification in the network if
required. To update the data and access the network the every staff member should
register in the network.
5. The network should be secure form the malware users. In a network, the developer should
implement some security techniques that secure the network from the attacker and that
type of users who are not registered in the network. To access the network the users, staff,
and another member of the hospital should register them in the network and then login in
the system. With these questions, the developer and designer should identify what is the
requirement to develop the network system for the hospital [5].
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
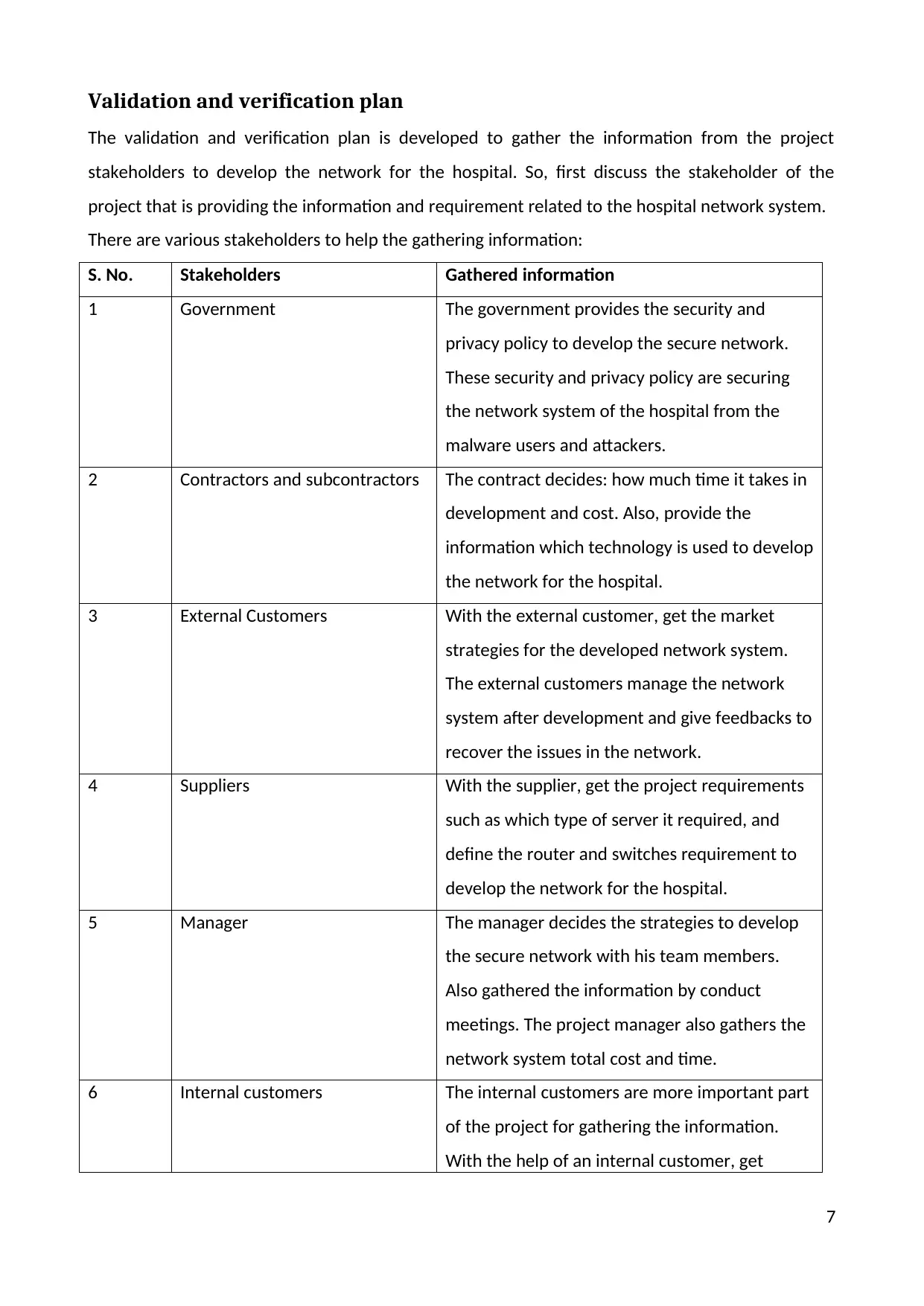
Validation and verification plan
The validation and verification plan is developed to gather the information from the project
stakeholders to develop the network for the hospital. So, first discuss the stakeholder of the
project that is providing the information and requirement related to the hospital network system.
There are various stakeholders to help the gathering information:
S. No. Stakeholders Gathered information
1 Government The government provides the security and
privacy policy to develop the secure network.
These security and privacy policy are securing
the network system of the hospital from the
malware users and attackers.
2 Contractors and subcontractors The contract decides: how much time it takes in
development and cost. Also, provide the
information which technology is used to develop
the network for the hospital.
3 External Customers With the external customer, get the market
strategies for the developed network system.
The external customers manage the network
system after development and give feedbacks to
recover the issues in the network.
4 Suppliers With the supplier, get the project requirements
such as which type of server it required, and
define the router and switches requirement to
develop the network for the hospital.
5 Manager The manager decides the strategies to develop
the secure network with his team members.
Also gathered the information by conduct
meetings. The project manager also gathers the
network system total cost and time.
6 Internal customers The internal customers are more important part
of the project for gathering the information.
With the help of an internal customer, get
7
The validation and verification plan is developed to gather the information from the project
stakeholders to develop the network for the hospital. So, first discuss the stakeholder of the
project that is providing the information and requirement related to the hospital network system.
There are various stakeholders to help the gathering information:
S. No. Stakeholders Gathered information
1 Government The government provides the security and
privacy policy to develop the secure network.
These security and privacy policy are securing
the network system of the hospital from the
malware users and attackers.
2 Contractors and subcontractors The contract decides: how much time it takes in
development and cost. Also, provide the
information which technology is used to develop
the network for the hospital.
3 External Customers With the external customer, get the market
strategies for the developed network system.
The external customers manage the network
system after development and give feedbacks to
recover the issues in the network.
4 Suppliers With the supplier, get the project requirements
such as which type of server it required, and
define the router and switches requirement to
develop the network for the hospital.
5 Manager The manager decides the strategies to develop
the secure network with his team members.
Also gathered the information by conduct
meetings. The project manager also gathers the
network system total cost and time.
6 Internal customers The internal customers are more important part
of the project for gathering the information.
With the help of an internal customer, get
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
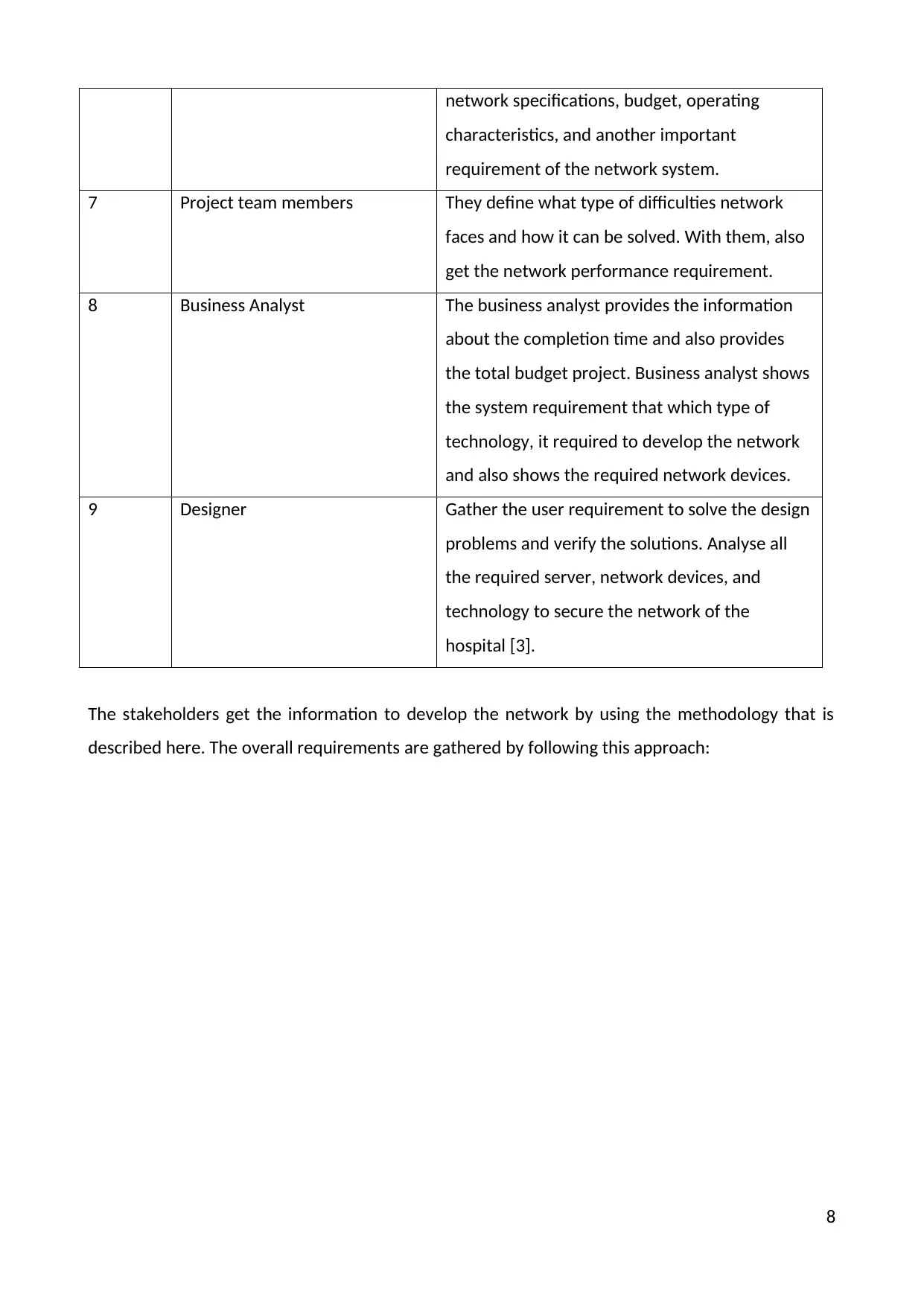
network specifications, budget, operating
characteristics, and another important
requirement of the network system.
7 Project team members They define what type of difficulties network
faces and how it can be solved. With them, also
get the network performance requirement.
8 Business Analyst The business analyst provides the information
about the completion time and also provides
the total budget project. Business analyst shows
the system requirement that which type of
technology, it required to develop the network
and also shows the required network devices.
9 Designer Gather the user requirement to solve the design
problems and verify the solutions. Analyse all
the required server, network devices, and
technology to secure the network of the
hospital [3].
The stakeholders get the information to develop the network by using the methodology that is
described here. The overall requirements are gathered by following this approach:
8
characteristics, and another important
requirement of the network system.
7 Project team members They define what type of difficulties network
faces and how it can be solved. With them, also
get the network performance requirement.
8 Business Analyst The business analyst provides the information
about the completion time and also provides
the total budget project. Business analyst shows
the system requirement that which type of
technology, it required to develop the network
and also shows the required network devices.
9 Designer Gather the user requirement to solve the design
problems and verify the solutions. Analyse all
the required server, network devices, and
technology to secure the network of the
hospital [3].
The stakeholders get the information to develop the network by using the methodology that is
described here. The overall requirements are gathered by following this approach:
8
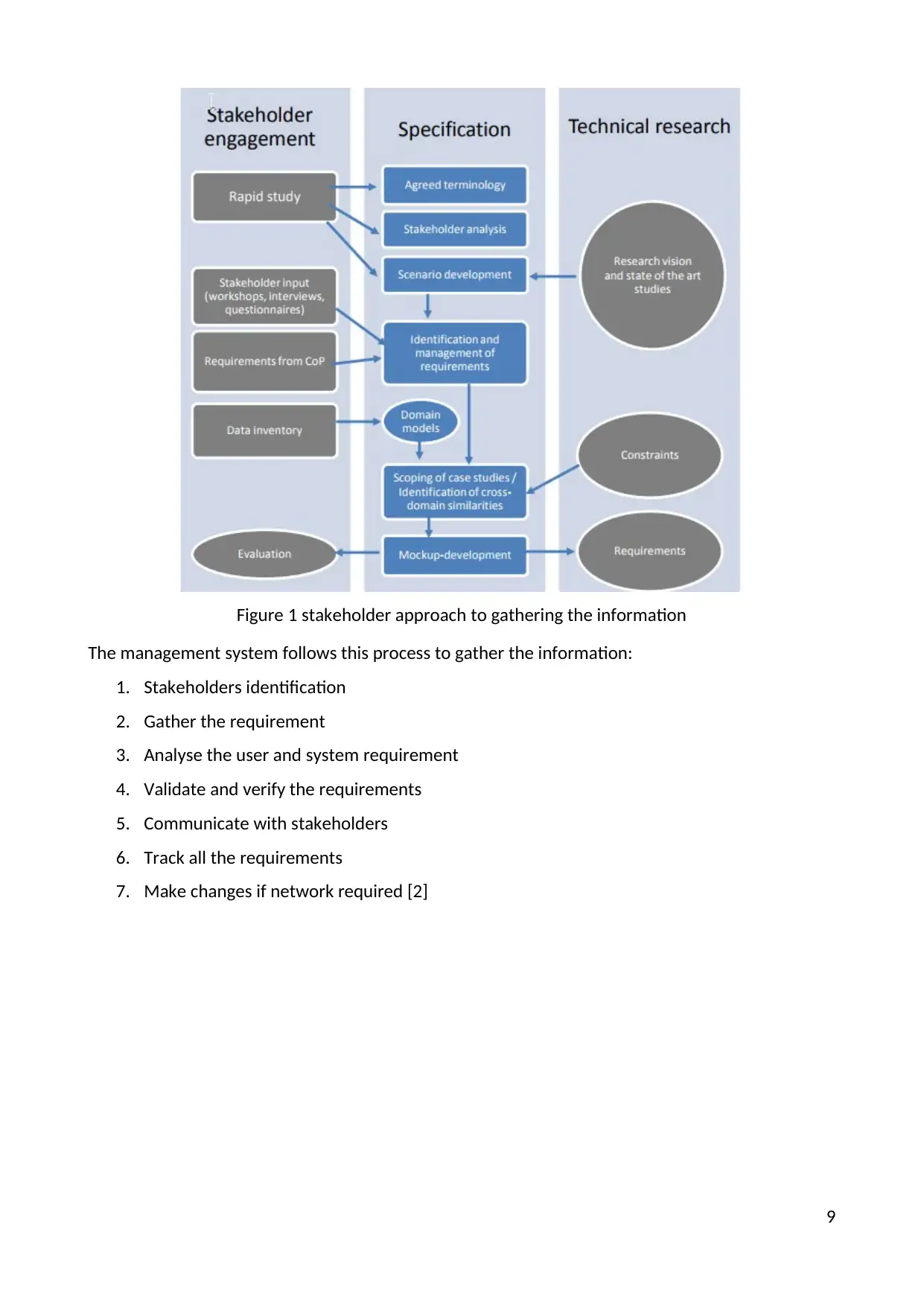
Figure 1 stakeholder approach to gathering the information
The management system follows this process to gather the information:
1. Stakeholders identification
2. Gather the requirement
3. Analyse the user and system requirement
4. Validate and verify the requirements
5. Communicate with stakeholders
6. Track all the requirements
7. Make changes if network required [2]
9
The management system follows this process to gather the information:
1. Stakeholders identification
2. Gather the requirement
3. Analyse the user and system requirement
4. Validate and verify the requirements
5. Communicate with stakeholders
6. Track all the requirements
7. Make changes if network required [2]
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Part 2
Gather the information to develop the network without talk to users and staff
To collect the information and requirement without meeting or talk to the users and staff of the
hospital, I have started to research about the technologies, and this type of network form the past
research work and past study that is done by researchers. From this past research work, I can
analyze which type of network is required to develop for the hospital. To know the user
requirement, I can observe the requirement to study the documentation that is done by users and
also read the feedbacks which are given by the user on this type of network. With this
observation, documentation, and feedbacks, I can analyze all the requirement of the user and
staff. To gather the information and requirement, first I have analyzed the problem and then start
to research work on this problem. After that, I found information to solve the problem. The
information also gets by identified the gaps from the already completed research work. There is
research work is already done on same technology with the same network, so, I will study them to
know the information and requirement to develop the network system for the hospital without
conduct meeting with users and staff.
10
Gather the information to develop the network without talk to users and staff
To collect the information and requirement without meeting or talk to the users and staff of the
hospital, I have started to research about the technologies, and this type of network form the past
research work and past study that is done by researchers. From this past research work, I can
analyze which type of network is required to develop for the hospital. To know the user
requirement, I can observe the requirement to study the documentation that is done by users and
also read the feedbacks which are given by the user on this type of network. With this
observation, documentation, and feedbacks, I can analyze all the requirement of the user and
staff. To gather the information and requirement, first I have analyzed the problem and then start
to research work on this problem. After that, I found information to solve the problem. The
information also gets by identified the gaps from the already completed research work. There is
research work is already done on same technology with the same network, so, I will study them to
know the information and requirement to develop the network system for the hospital without
conduct meeting with users and staff.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Part 3
Network Design
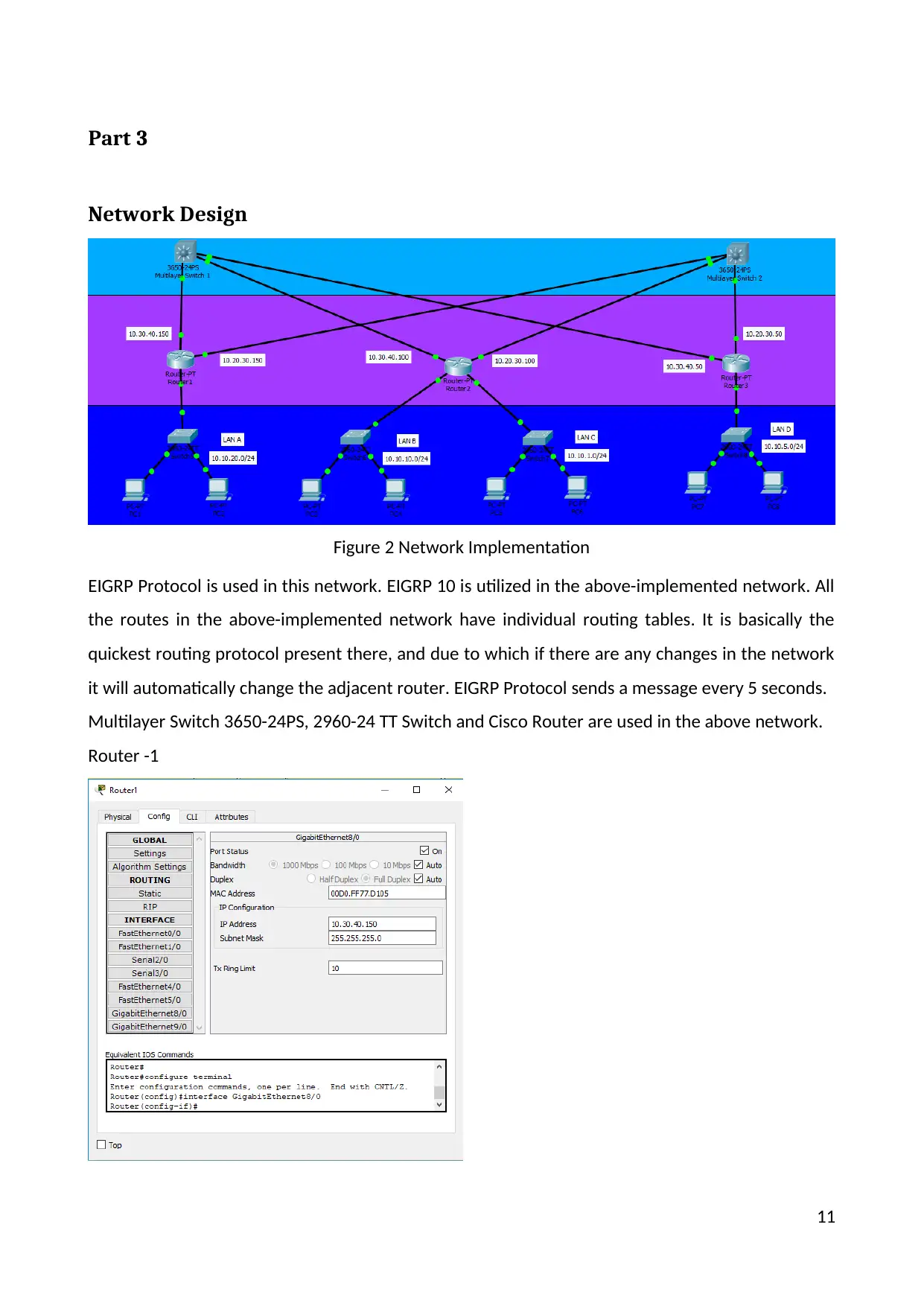
Figure 2 Network Implementation
EIGRP Protocol is used in this network. EIGRP 10 is utilized in the above-implemented network. All
the routes in the above-implemented network have individual routing tables. It is basically the
quickest routing protocol present there, and due to which if there are any changes in the network
it will automatically change the adjacent router. EIGRP Protocol sends a message every 5 seconds.
Multilayer Switch 3650-24PS, 2960-24 TT Switch and Cisco Router are used in the above network.
Router -1
11
Network Design
Figure 2 Network Implementation
EIGRP Protocol is used in this network. EIGRP 10 is utilized in the above-implemented network. All
the routes in the above-implemented network have individual routing tables. It is basically the
quickest routing protocol present there, and due to which if there are any changes in the network
it will automatically change the adjacent router. EIGRP Protocol sends a message every 5 seconds.
Multilayer Switch 3650-24PS, 2960-24 TT Switch and Cisco Router are used in the above network.
Router -1
11
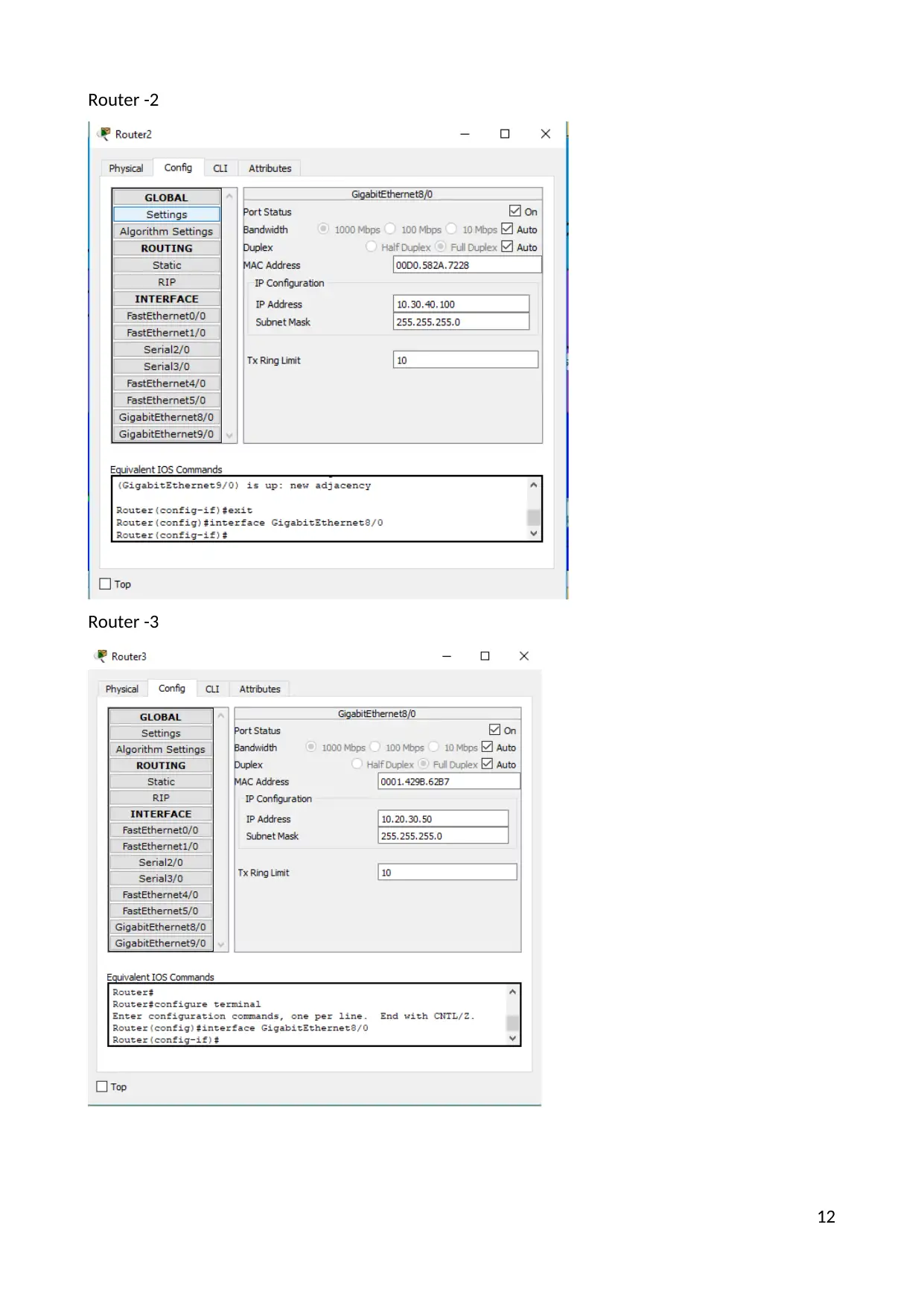
Router -2
Router -3
12
Router -3
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




