Mobile Application Development and Security Report - Semester 1
VerifiedAdded on 2020/12/26
|11
|2841
|346
Report
AI Summary
This report provides a comprehensive overview of mobile platforms and application development. It begins by discussing the concept and history of mobile platforms, comparing Android, BlackBerry, and iOS operating systems, highlighting their strengths and weaknesses. The report then evaluates current and future trends in mobile application development, including blockchain, AI, on-demand apps, and wearable integrations. Task 2 delves into mobile application development platforms, recommending Xamarin, and outlines the SDLC stages for designing a mobile application. The report further assesses mobile application design and the impact of cyber security threats, including data leakage, unsecured Wi-Fi, and network spoofing. Finally, it evaluates the Internet of Things (IoT), its current applications in smart homes and wearables, and its relationship with cloud-based services, concluding with a discussion on the role of mobile applications in ubiquitous computing. The report is a student assignment, aimed at providing a detailed understanding of the mobile application landscape.

MOBILE ASSIGNMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................3
TASK 1............................................................................................................................................3
AC 1.1 Discussing the concept and history of leading mobile platforms..............................3
AC1.2 Comparing three Mobile operating systems with their strength and weakness..........4
AC1.3 evaluating the current and future trends in the developments of mobile applications5
TASK 2............................................................................................................................................6
AC2.1 Development platform for mobile application............................................................6
AC2.2 Designing a mobile application through SDLC stages...............................................6
TASK 3............................................................................................................................................6
AC3.1 Evaluating the design of a mobile application ...........................................................6
AC3.2 Evaluating the impact of cyber security ...................................................................6
TASK 4............................................................................................................................................7
AC4.1 Evaluation of internet if things (IoT)..........................................................................7
AC4.2 Investigating the relationship between IoT and cloud based services........................8
AC4.3 Producing a brief report on the role of mobile application in ubiquitous computing.9
CONCLUSION..............................................................................................................................10
INTRODUCTION...........................................................................................................................3
TASK 1............................................................................................................................................3
AC 1.1 Discussing the concept and history of leading mobile platforms..............................3
AC1.2 Comparing three Mobile operating systems with their strength and weakness..........4
AC1.3 evaluating the current and future trends in the developments of mobile applications5
TASK 2............................................................................................................................................6
AC2.1 Development platform for mobile application............................................................6
AC2.2 Designing a mobile application through SDLC stages...............................................6
TASK 3............................................................................................................................................6
AC3.1 Evaluating the design of a mobile application ...........................................................6
AC3.2 Evaluating the impact of cyber security ...................................................................6
TASK 4............................................................................................................................................7
AC4.1 Evaluation of internet if things (IoT)..........................................................................7
AC4.2 Investigating the relationship between IoT and cloud based services........................8
AC4.3 Producing a brief report on the role of mobile application in ubiquitous computing.9
CONCLUSION..............................................................................................................................10

INTRODUCTION
Mobile platform refers to type of hardware or software environment which has been
created for the laptops, tablets, smartphones and for other portable devices. Thus, this report will
articulate the concept and history of mobile platform by comparing three operating systems.
Further, evaluation will develop on development of mobile application and the type of
application in the past. Justification will also be provided on developed design on the basis of its
functionality, usability and reliability. Lastly, this report will analyse the environment of mobile
applications.
TASK 1
AC 1.1 Discussing the concept and history of leading mobile platforms
The most basic idea of developing mobile phones is only to send and receive voice calls.
Other than this, very first technological concept is the idea of card where content is been
presented to users in most consistent way (Chen and et.al., 2015). Third concept is regarding the
use of multiscreen which however becomes a use of “every screen”. But since then things get
changed, huge technological advancement has been created by this platform where an
environment of software/hardware will get develop for devices like laptops, tablets, smartphone
and for other portable devices.
Mobile platform refers to type of hardware or software environment which has been
created for the laptops, tablets, smartphones and for other portable devices. Thus, this report will
articulate the concept and history of mobile platform by comparing three operating systems.
Further, evaluation will develop on development of mobile application and the type of
application in the past. Justification will also be provided on developed design on the basis of its
functionality, usability and reliability. Lastly, this report will analyse the environment of mobile
applications.
TASK 1
AC 1.1 Discussing the concept and history of leading mobile platforms
The most basic idea of developing mobile phones is only to send and receive voice calls.
Other than this, very first technological concept is the idea of card where content is been
presented to users in most consistent way (Chen and et.al., 2015). Third concept is regarding the
use of multiscreen which however becomes a use of “every screen”. But since then things get
changed, huge technological advancement has been created by this platform where an
environment of software/hardware will get develop for devices like laptops, tablets, smartphone
and for other portable devices.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
However, in accordance with history of such platform, it is analysed that Java games,
calculator or monthly calendar are the only one which comes under the category of such
application. The very first generation of mobile phones were personal digital assistance where
only phone and mobile camera is there. Further, under the late 90's some brands like Plam, Nokia
and research in motion have dominated the market with their effective operating system. Those
were the devices through which user will able to capture and customised information through
onboard keyboards (Huang and Wu, 2017). The very first cellular phone call was developed by
Martin Cooper of Motorola which is on 3rd April 1973, after that it took other 10 years for other
researcher to hit the market. Other than this, apps are generally emerged from early PDA's where
starting was simple first snake game in phone Nokia 6110. It was initially stored to first 500 apps
in store of Apple.
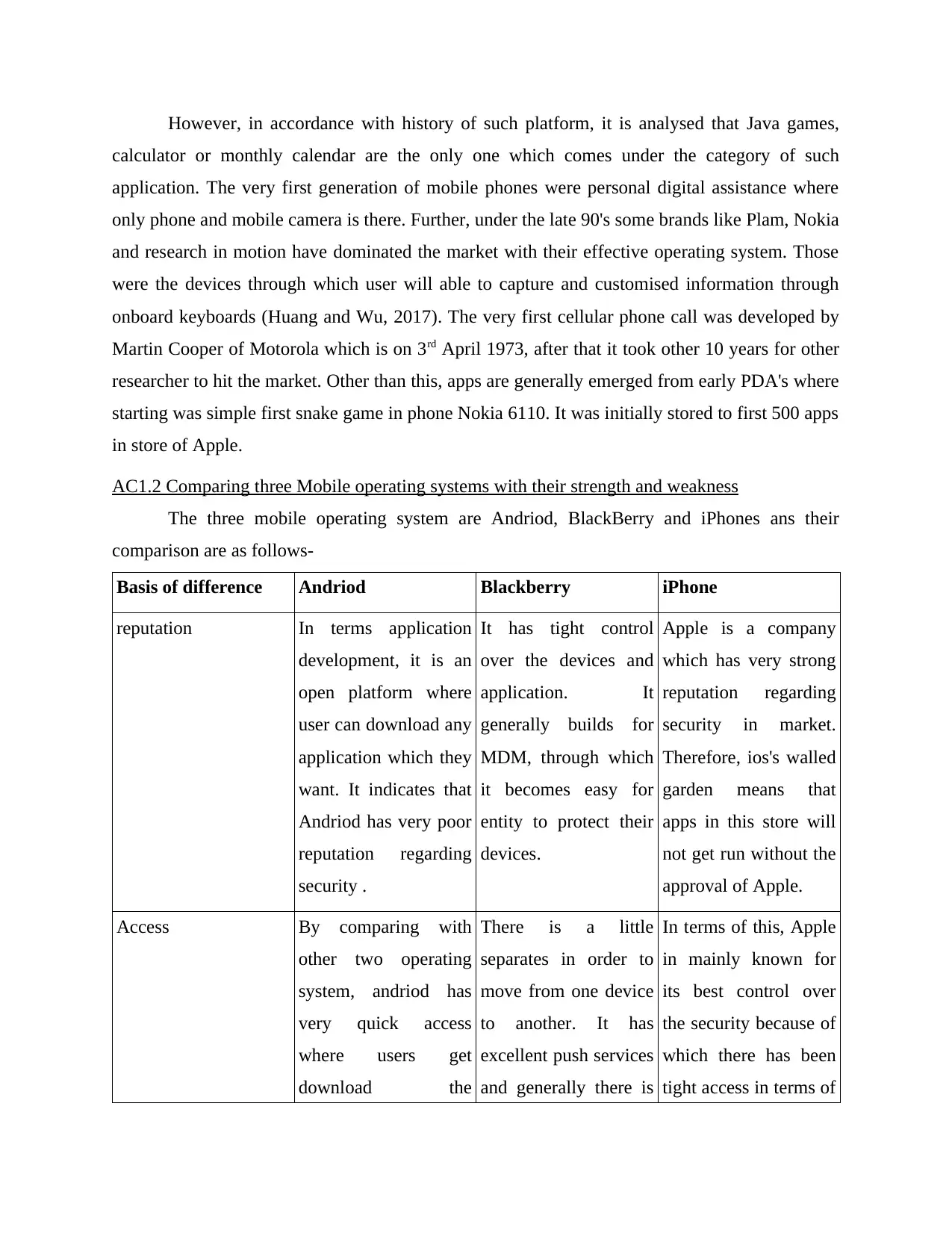
AC1.2 Comparing three Mobile operating systems with their strength and weakness
The three mobile operating system are Andriod, BlackBerry and iPhones ans their
comparison are as follows-
Basis of difference Andriod Blackberry iPhone
reputation In terms application
development, it is an
open platform where
user can download any
application which they
want. It indicates that
Andriod has very poor
reputation regarding
security .
It has tight control
over the devices and
application. It
generally builds for
MDM, through which
it becomes easy for
entity to protect their
devices.
Apple is a company
which has very strong
reputation regarding
security in market.
Therefore, ios's walled
garden means that
apps in this store will
not get run without the
approval of Apple.
Access By comparing with
other two operating
system, andriod has
very quick access
where users get
download the
There is a little
separates in order to
move from one device
to another. It has
excellent push services
and generally there is
In terms of this, Apple
in mainly known for
its best control over
the security because of
which there has been
tight access in terms of
calculator or monthly calendar are the only one which comes under the category of such
application. The very first generation of mobile phones were personal digital assistance where
only phone and mobile camera is there. Further, under the late 90's some brands like Plam, Nokia
and research in motion have dominated the market with their effective operating system. Those
were the devices through which user will able to capture and customised information through
onboard keyboards (Huang and Wu, 2017). The very first cellular phone call was developed by
Martin Cooper of Motorola which is on 3rd April 1973, after that it took other 10 years for other
researcher to hit the market. Other than this, apps are generally emerged from early PDA's where
starting was simple first snake game in phone Nokia 6110. It was initially stored to first 500 apps
in store of Apple.
AC1.2 Comparing three Mobile operating systems with their strength and weakness
The three mobile operating system are Andriod, BlackBerry and iPhones ans their
comparison are as follows-
Basis of difference Andriod Blackberry iPhone
reputation In terms application
development, it is an
open platform where
user can download any
application which they
want. It indicates that
Andriod has very poor
reputation regarding
security .
It has tight control
over the devices and
application. It
generally builds for
MDM, through which
it becomes easy for
entity to protect their
devices.
Apple is a company
which has very strong
reputation regarding
security in market.
Therefore, ios's walled
garden means that
apps in this store will
not get run without the
approval of Apple.
Access By comparing with
other two operating
system, andriod has
very quick access
where users get
download the
There is a little
separates in order to
move from one device
to another. It has
excellent push services
and generally there is
In terms of this, Apple
in mainly known for
its best control over
the security because of
which there has been
tight access in terms of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
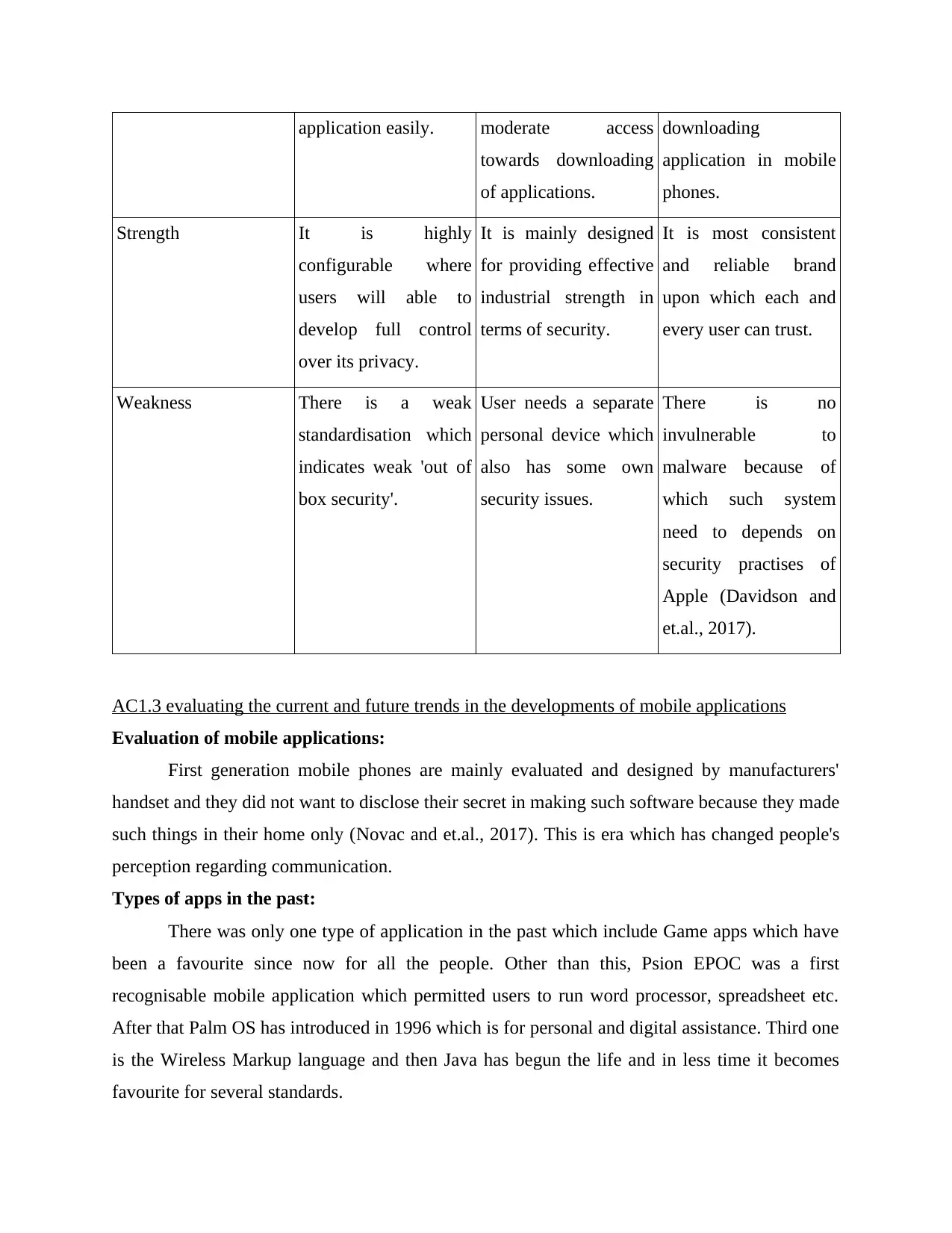
application easily. moderate access
towards downloading
of applications.
downloading
application in mobile
phones.
Strength It is highly
configurable where
users will able to
develop full control
over its privacy.
It is mainly designed
for providing effective
industrial strength in
terms of security.
It is most consistent
and reliable brand
upon which each and
every user can trust.
Weakness There is a weak
standardisation which
indicates weak 'out of
box security'.
User needs a separate
personal device which
also has some own
security issues.
There is no
invulnerable to
malware because of
which such system
need to depends on
security practises of
Apple (Davidson and
et.al., 2017).
AC1.3 evaluating the current and future trends in the developments of mobile applications
Evaluation of mobile applications:
First generation mobile phones are mainly evaluated and designed by manufacturers'
handset and they did not want to disclose their secret in making such software because they made
such things in their home only (Novac and et.al., 2017). This is era which has changed people's
perception regarding communication.
Types of apps in the past:
There was only one type of application in the past which include Game apps which have
been a favourite since now for all the people. Other than this, Psion EPOC was a first
recognisable mobile application which permitted users to run word processor, spreadsheet etc.
After that Palm OS has introduced in 1996 which is for personal and digital assistance. Third one
is the Wireless Markup language and then Java has begun the life and in less time it becomes
favourite for several standards.
towards downloading
of applications.
downloading
application in mobile
phones.
Strength It is highly
configurable where
users will able to
develop full control
over its privacy.
It is mainly designed
for providing effective
industrial strength in
terms of security.
It is most consistent
and reliable brand
upon which each and
every user can trust.
Weakness There is a weak
standardisation which
indicates weak 'out of
box security'.
User needs a separate
personal device which
also has some own
security issues.
There is no
invulnerable to
malware because of
which such system
need to depends on
security practises of
Apple (Davidson and
et.al., 2017).
AC1.3 evaluating the current and future trends in the developments of mobile applications
Evaluation of mobile applications:
First generation mobile phones are mainly evaluated and designed by manufacturers'
handset and they did not want to disclose their secret in making such software because they made
such things in their home only (Novac and et.al., 2017). This is era which has changed people's
perception regarding communication.
Types of apps in the past:
There was only one type of application in the past which include Game apps which have
been a favourite since now for all the people. Other than this, Psion EPOC was a first
recognisable mobile application which permitted users to run word processor, spreadsheet etc.
After that Palm OS has introduced in 1996 which is for personal and digital assistance. Third one
is the Wireless Markup language and then Java has begun the life and in less time it becomes
favourite for several standards.

Current mobile trend:
In current era, trend in the mobile application is regarding Soaring Block-chain
technology, Artificial intelligence and machine learning, surge for on-demand application,
integration of wearable apps, chatbots and virtual reality are the main current trend which has
taken the marketplace (Pimmer, Mateescu and Gröhbiel, 2016).
Future mobile trend:
Future trend is also of wearable devices, internet of things and mobile connected smart
objects, M-commerce, motion and locating sensing, innovative mobile user experience design,
application performance management and for enterprise mobile management through which a
new digital world gets developed.
TASK 2
AC2.1 Development platform for mobile application
There are several apps building platform through which creative and effective designs
will get made. But in this huge market, it is essential to choose the right platform which must be
cost effective and easy to use. Thus, in order to build a good design mobile software, Xamarin
will be prefered because it is choice for native applications (Gökçearslan and et.al., 2016). It is
the type of platform which reuses the logic of business layers and in which data gets access
across the platforms. This is considered as most beneficial design because it provides functions
such as offline mode, local data, etc. with effective image acceptance which is to be
implemented. It mainly builds on C# programming language which runs of .NET common
language infrastructure. Thus, it is the tool which has been widely used for the apps like iOS,
Windows and for Andriod platforms.
Main advantage of this application is that it only has fewer bugs because of which it
provides faster time to market. It also involves lesser codes which helps in creating fewer bugs
and single test will help in validating the code of both platforms. It also provides opportunity to
developed in their selection from host of free and paid components.
In current era, trend in the mobile application is regarding Soaring Block-chain
technology, Artificial intelligence and machine learning, surge for on-demand application,
integration of wearable apps, chatbots and virtual reality are the main current trend which has
taken the marketplace (Pimmer, Mateescu and Gröhbiel, 2016).
Future mobile trend:
Future trend is also of wearable devices, internet of things and mobile connected smart
objects, M-commerce, motion and locating sensing, innovative mobile user experience design,
application performance management and for enterprise mobile management through which a
new digital world gets developed.
TASK 2
AC2.1 Development platform for mobile application
There are several apps building platform through which creative and effective designs
will get made. But in this huge market, it is essential to choose the right platform which must be
cost effective and easy to use. Thus, in order to build a good design mobile software, Xamarin
will be prefered because it is choice for native applications (Gökçearslan and et.al., 2016). It is
the type of platform which reuses the logic of business layers and in which data gets access
across the platforms. This is considered as most beneficial design because it provides functions
such as offline mode, local data, etc. with effective image acceptance which is to be
implemented. It mainly builds on C# programming language which runs of .NET common
language infrastructure. Thus, it is the tool which has been widely used for the apps like iOS,
Windows and for Andriod platforms.
Main advantage of this application is that it only has fewer bugs because of which it
provides faster time to market. It also involves lesser codes which helps in creating fewer bugs
and single test will help in validating the code of both platforms. It also provides opportunity to
developed in their selection from host of free and paid components.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

AC2.2 Designing a mobile application through SDLC stages
TASK 3
AC3.1 Evaluating the design of a mobile application .
AC3.2 Evaluating the impact of cyber security .
Current threat on mobile applications:
Mobile apps are always resulted in causing unintentional leakage of data which cause a
real problem for users of mobile without checking the type of security (Cerrudo, 2015).
Such data leakage are often hosted through the enterprise called hostile which is a signed
mobile applications.
Unsecured Wi-Fi are the second one which burs users through their own cellular data. It
is analysed that people who generally gave their access to free wifi networks mainly have
face hacking in their accounts.
Network spoofing is another threat where hackers set up fake access point which is also
in high traffic public locations such as in coffee shops, libraries and airports through
which attacker analyse the information regarding email id and password of users.
Impact of cyber security on mobile apps:
In today's world, impact of mobile apps has grown which increases the risk of being
attacked. However, according to the study presented by Gartner 75% of mobile application gets
failed during their test of security. Thus, cyber security has initiated some practises which needs
to be develop by web designer before it gets release for public (Sharma and Tandekar, 2017).
However, some code which need to presented before developing any website includes:
Code Shield which uses by developer in order to provide the security to their
applications. Before introducing any application, it must go through number of security
tests.
App protection solution needs to be used by developed so that proper security will get
presented for mobile applications.
Customer engagement apps needs to be go through reverse engineering through which
possibility of theft of personal information gets protect.
TASK 3
AC3.1 Evaluating the design of a mobile application .
AC3.2 Evaluating the impact of cyber security .
Current threat on mobile applications:
Mobile apps are always resulted in causing unintentional leakage of data which cause a
real problem for users of mobile without checking the type of security (Cerrudo, 2015).
Such data leakage are often hosted through the enterprise called hostile which is a signed
mobile applications.
Unsecured Wi-Fi are the second one which burs users through their own cellular data. It
is analysed that people who generally gave their access to free wifi networks mainly have
face hacking in their accounts.
Network spoofing is another threat where hackers set up fake access point which is also
in high traffic public locations such as in coffee shops, libraries and airports through
which attacker analyse the information regarding email id and password of users.
Impact of cyber security on mobile apps:
In today's world, impact of mobile apps has grown which increases the risk of being
attacked. However, according to the study presented by Gartner 75% of mobile application gets
failed during their test of security. Thus, cyber security has initiated some practises which needs
to be develop by web designer before it gets release for public (Sharma and Tandekar, 2017).
However, some code which need to presented before developing any website includes:
Code Shield which uses by developer in order to provide the security to their
applications. Before introducing any application, it must go through number of security
tests.
App protection solution needs to be used by developed so that proper security will get
presented for mobile applications.
Customer engagement apps needs to be go through reverse engineering through which
possibility of theft of personal information gets protect.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TASK 4
AC4.1 Evaluation of internet if things (IoT)
The internet on things is not new, however it was gaining more attention and traction
lately. It is widely getting used because of its concept which entails the use of electronic devices
through which data gets captured and monitor and gets connected through private and public
cloud. This helps in automatically trigger certain events. It has huge demand in the industries like
energy, automotive and for consumer spaces because this will help in reporting and reacting to
certain things which provides new level of convenience, efficiency and automation. Its current
most popular things are:
Smart home:
It is one of the most ranked channel among all internet on things and according to a
statistics more than 60,000 people are searching for the term “smart home” each month. It
mainly helps in analysing the data base of the entity for smart home which generally include 256
companies and their start ups because of which most of the companies are active in this tool
other than any application of internet on things (Lueth, 2015). This is the application in which
total amount of funding for such start up has exceeds $2.5 billion.
Wearables:
This is the another major used thing on internet. There are plenty of innovation are
awaiting and it is analysed that after Apple announces regarding new smart watch in April 2015
most consumer wait for it because of which plenty of new wearable innovation have taken place.
Smart city:
It generally includes wide variety of use of cases which is from traffic management to
distribution of water, to waste management and to monitor the urban society and environment
concern (Nagappan and Shihab, 2016). It mainly helps in recognising the amount of pollution
such as noise in city.
Its future application:
It is analysed that by the year 2025, there will be more than 21 billion people who will
use IoT devices because of its increasing demand.
Cybercriminals will also continue its use in order to facilitate the Ddos where strain of
malware will term as “open source”. It means that the code will be available for anyone
to modify the changes.
AC4.1 Evaluation of internet if things (IoT)
The internet on things is not new, however it was gaining more attention and traction
lately. It is widely getting used because of its concept which entails the use of electronic devices
through which data gets captured and monitor and gets connected through private and public
cloud. This helps in automatically trigger certain events. It has huge demand in the industries like
energy, automotive and for consumer spaces because this will help in reporting and reacting to
certain things which provides new level of convenience, efficiency and automation. Its current
most popular things are:
Smart home:
It is one of the most ranked channel among all internet on things and according to a
statistics more than 60,000 people are searching for the term “smart home” each month. It
mainly helps in analysing the data base of the entity for smart home which generally include 256
companies and their start ups because of which most of the companies are active in this tool
other than any application of internet on things (Lueth, 2015). This is the application in which
total amount of funding for such start up has exceeds $2.5 billion.
Wearables:
This is the another major used thing on internet. There are plenty of innovation are
awaiting and it is analysed that after Apple announces regarding new smart watch in April 2015
most consumer wait for it because of which plenty of new wearable innovation have taken place.
Smart city:
It generally includes wide variety of use of cases which is from traffic management to
distribution of water, to waste management and to monitor the urban society and environment
concern (Nagappan and Shihab, 2016). It mainly helps in recognising the amount of pollution
such as noise in city.
Its future application:
It is analysed that by the year 2025, there will be more than 21 billion people who will
use IoT devices because of its increasing demand.
Cybercriminals will also continue its use in order to facilitate the Ddos where strain of
malware will term as “open source”. It means that the code will be available for anyone
to modify the changes.

Cities and entities will also enhance its adoption in order to save time and money. With
the help of this process cities will able to automate, remotely manage and collect data for
preventing the environment.
AC4.2 Investigating the relationship between IoT and cloud based services
When these both gets combines, then they deliver the powerful innovation which helps in
interacting with the devices with one another and change then in storing, managing and for
consuming information. It is true that cloud computing will be a backbone of everything which
IoT has to offer. collaboration between IoT and the cloud services in mobile devices impact on
our day to day life as IoT devices can deliver massive amounts of data and use infrastructure
resources in an inconsistent manner; the cloud can provide the scalability and flexibility to deal
with this.
IoT traffic and the number of devices are set to erupt over the next few years, leading to
increased interactions between devices and huge volumes of data generated. This means your
business will need a cost-efficient way to store, process, and access data from the IoT solutions
and scale resources to handle peaks of demand when necessary
There are many technical hurdles which helps in deploying an effective solution for IoT,
cloud computing helps in accelerating development of such burdens.
IoT devices deliver huge amount of data and resources for infrastructure in inconsistent
manner, here cloud computing helps in providing the scalability and flexibility in
procedure to deal with.
In terms of IoT, data security has always been a concern where cloud computing helps in
improving such security.
AC4.3 Producing a brief report on the role of mobile application in ubiquitous computing
Future role of mobile application in uniquitous computing is Therefore, application mobility is
an important aspect of ubiquitous computing. Let’s consider the problem of migrating
applications across different ubiquitous computing environments (i.e. across different rooms,
buildings or even cities). Migration is a tough problem because different environments have
different resources (devices or services) available. In this globalised world, this era is generally
known as digital era, where life without technology have become impossible to live. Especially
mobile phones have become an important part in everyday life. It because growing tremendous
transformation in mobile phones are no longer ordinary an ordinary communication. The intense
the help of this process cities will able to automate, remotely manage and collect data for
preventing the environment.
AC4.2 Investigating the relationship between IoT and cloud based services
When these both gets combines, then they deliver the powerful innovation which helps in
interacting with the devices with one another and change then in storing, managing and for
consuming information. It is true that cloud computing will be a backbone of everything which
IoT has to offer. collaboration between IoT and the cloud services in mobile devices impact on
our day to day life as IoT devices can deliver massive amounts of data and use infrastructure
resources in an inconsistent manner; the cloud can provide the scalability and flexibility to deal
with this.
IoT traffic and the number of devices are set to erupt over the next few years, leading to
increased interactions between devices and huge volumes of data generated. This means your
business will need a cost-efficient way to store, process, and access data from the IoT solutions
and scale resources to handle peaks of demand when necessary
There are many technical hurdles which helps in deploying an effective solution for IoT,
cloud computing helps in accelerating development of such burdens.
IoT devices deliver huge amount of data and resources for infrastructure in inconsistent
manner, here cloud computing helps in providing the scalability and flexibility in
procedure to deal with.
In terms of IoT, data security has always been a concern where cloud computing helps in
improving such security.
AC4.3 Producing a brief report on the role of mobile application in ubiquitous computing
Future role of mobile application in uniquitous computing is Therefore, application mobility is
an important aspect of ubiquitous computing. Let’s consider the problem of migrating
applications across different ubiquitous computing environments (i.e. across different rooms,
buildings or even cities). Migration is a tough problem because different environments have
different resources (devices or services) available. In this globalised world, this era is generally
known as digital era, where life without technology have become impossible to live. Especially
mobile phones have become an important part in everyday life. It because growing tremendous
transformation in mobile phones are no longer ordinary an ordinary communication. The intense
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

development in mobile technology and availability of high speed internet results into a new level
of communication development. All these becomes possible with the development in mobile
applications across the world.
However, today the availability of mobile application gets increased which change the
way people feel and experience computing (Hu and et.al., 2015). For example: Ubiquitous
computing visualize an environment in which only physical and seamless devices integrated
because of which users can access data and their application anywhere in the environment. Thus,
it can be said that the mobile apps have created an era or have transformed the way people
socialise, work and play. In today's' world social apps have fundamental influence the way
people interact with each other. It provides a flexibility where people easily able to communicate
all over the world. Employers nowadays using mobile apps for their work related reasons which
helps a lot in enhancing the productivity of the businesses.
CONCLUSION
From the above study it has been summarised that the mobile application has made the life of
people more easy. The intense development in mobile technology and availability of high speed
internet results into a new level of communication development. This has made the life of people
easier.
of communication development. All these becomes possible with the development in mobile
applications across the world.
However, today the availability of mobile application gets increased which change the
way people feel and experience computing (Hu and et.al., 2015). For example: Ubiquitous
computing visualize an environment in which only physical and seamless devices integrated
because of which users can access data and their application anywhere in the environment. Thus,
it can be said that the mobile apps have created an era or have transformed the way people
socialise, work and play. In today's' world social apps have fundamental influence the way
people interact with each other. It provides a flexibility where people easily able to communicate
all over the world. Employers nowadays using mobile apps for their work related reasons which
helps a lot in enhancing the productivity of the businesses.
CONCLUSION
From the above study it has been summarised that the mobile application has made the life of
people more easy. The intense development in mobile technology and availability of high speed
internet results into a new level of communication development. This has made the life of people
easier.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





