ICTS0782 Assignment: Network Components, IPv6 Addressing, and Routing
VerifiedAdded on 2023/04/25
|53
|3138
|62
Homework Assignment
AI Summary
This assignment solution, created by Jashandeeep Singh for the ICTS0782 course, provides a detailed overview of network components and protocols. It begins with an explanation of key components such as servers, switches, routers, and LAN cables, followed by IP planning for different groups. The solution also covers the OSI model, explaining the function of each layer. Furthermore, the assignment delves into the CSMA/CD protocol, its functionality, and its application in networks. It then explores the inevitability of IPv6, its advantages, and different addressing modes like unicast, multicast, and anycast. The solution also discusses routing, router booting processes, and the components involved. Finally, it differentiates between PPP and PPPoE protocols. This assignment provides a comprehensive understanding of networking fundamentals and advanced concepts.

Name: Jashandeeep Singh
Student ID: 18020733
Course: ICTS0782
Student ID: 18020733
Course: ICTS0782
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
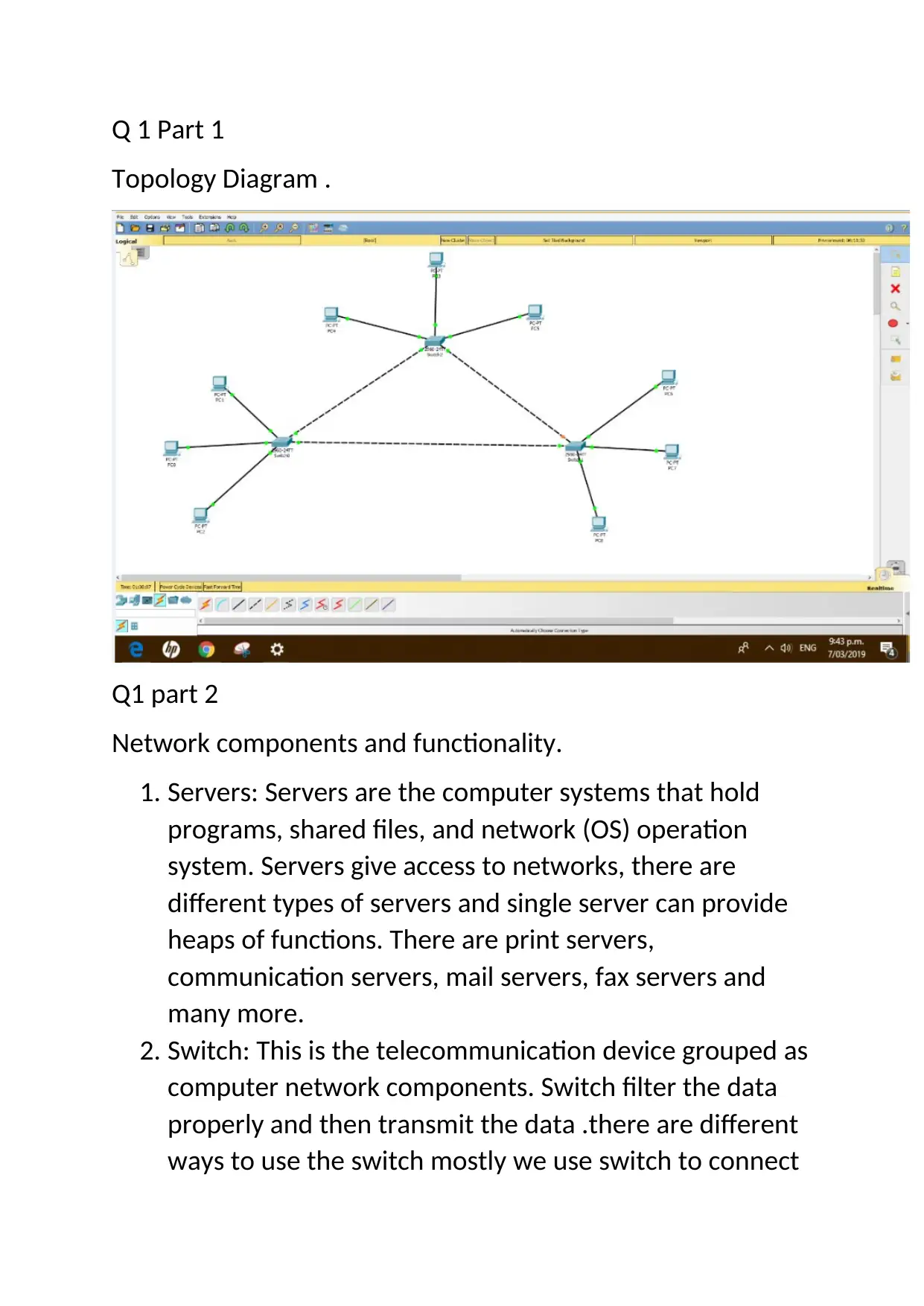
Q 1 Part 1
Topology Diagram .
Q1 part 2
Network components and functionality.
1. Servers: Servers are the computer systems that hold
programs, shared files, and network (OS) operation
system. Servers give access to networks, there are
different types of servers and single server can provide
heaps of functions. There are print servers,
communication servers, mail servers, fax servers and
many more.
2. Switch: This is the telecommunication device grouped as
computer network components. Switch filter the data
properly and then transmit the data .there are different
ways to use the switch mostly we use switch to connect
Topology Diagram .
Q1 part 2
Network components and functionality.
1. Servers: Servers are the computer systems that hold
programs, shared files, and network (OS) operation
system. Servers give access to networks, there are
different types of servers and single server can provide
heaps of functions. There are print servers,
communication servers, mail servers, fax servers and
many more.
2. Switch: This is the telecommunication device grouped as
computer network components. Switch filter the data
properly and then transmit the data .there are different
ways to use the switch mostly we use switch to connect

a PC or Laptop to router .The switch also look like
modems but switches have heaps of connection ports
and modems comes with two or three ports.
Moreover, .The switch and hubs have same RJ-45 ports.
3. Router: The router is used to connect LAN with an
internet connections .When we have two LAN networks
and we want to share internet connection to other
computers we use a Router. There are two types of
Routers wireless and wired .In simple words, A router is
a network device that used to forwards data between
networks.
4. LAN cable : Lan cable also the part of computer network
components .the LAN cable is also known as Ethernet cable
and data cable .The function of LAN cable to connect devices
to the internet and this cable also used to connect other
devices such as computers ,printers and many more.
Q 2 Part c
IP planning for Sales Group.
Network Address: 192.168.20.0
Broadcast Address: 192.168.20.255
IP range from: 192.168.20.1 to 192.168.20.254
modems but switches have heaps of connection ports
and modems comes with two or three ports.
Moreover, .The switch and hubs have same RJ-45 ports.
3. Router: The router is used to connect LAN with an
internet connections .When we have two LAN networks
and we want to share internet connection to other
computers we use a Router. There are two types of
Routers wireless and wired .In simple words, A router is
a network device that used to forwards data between
networks.
4. LAN cable : Lan cable also the part of computer network
components .the LAN cable is also known as Ethernet cable
and data cable .The function of LAN cable to connect devices
to the internet and this cable also used to connect other
devices such as computers ,printers and many more.
Q 2 Part c
IP planning for Sales Group.
Network Address: 192.168.20.0
Broadcast Address: 192.168.20.255
IP range from: 192.168.20.1 to 192.168.20.254
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IP planning for Marketing Group.
Network Address: 192.168.20.0
Broadcast Address: 192.168.20.255
IP range from: 192.168.20.1 to 192.168.20.254
IP planning for Admin Group.
Network Address: 192.168.20.0
Broadcast Address: 192.168.20.255
IP range from: 192.168.20.1 to 192.168.20.254
Network Address: 192.168.20.0
Broadcast Address: 192.168.20.255
IP range from: 192.168.20.1 to 192.168.20.254
IP planning for Admin Group.
Network Address: 192.168.20.0
Broadcast Address: 192.168.20.255
IP range from: 192.168.20.1 to 192.168.20.254
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Q 2.
Ans: According to the OSI models data reached to their
destination through 7 OSI layers.
There are seven OSI layers:
1. Physical layer is Layer 1.
2. Data link layer is layer 2.
3. Network layer is layer 3.
4. Transport layer is layer 4.
5. Session layer is layer 5.
6. Presentation layer is layer 6.
7. Application layer is layer 7. (Search Network, n.d.)
The data send process start from layer 7, application layer
place header field which include data such as screen fonts
and size, and then passes the information and data to Layer 6
(presentation layer).Moreover, The presentation data covert
data properly for example text messages converted to ASCII
and then pass data to layer 5 (Session layer).After, The
session layer place layer 5 header data and manage the data
and information flow, and pass the data to Layer 4 (Transport
layer). (OSI layers, n.d.)
After data, Layer 3 handles the routing and the addressing
and check the right direction of data, and pass the data to
Ans: According to the OSI models data reached to their
destination through 7 OSI layers.
There are seven OSI layers:
1. Physical layer is Layer 1.
2. Data link layer is layer 2.
3. Network layer is layer 3.
4. Transport layer is layer 4.
5. Session layer is layer 5.
6. Presentation layer is layer 6.
7. Application layer is layer 7. (Search Network, n.d.)
The data send process start from layer 7, application layer
place header field which include data such as screen fonts
and size, and then passes the information and data to Layer 6
(presentation layer).Moreover, The presentation data covert
data properly for example text messages converted to ASCII
and then pass data to layer 5 (Session layer).After, The
session layer place layer 5 header data and manage the data
and information flow, and pass the data to Layer 4 (Transport
layer). (OSI layers, n.d.)
After data, Layer 3 handles the routing and the addressing
and check the right direction of data, and pass the data to
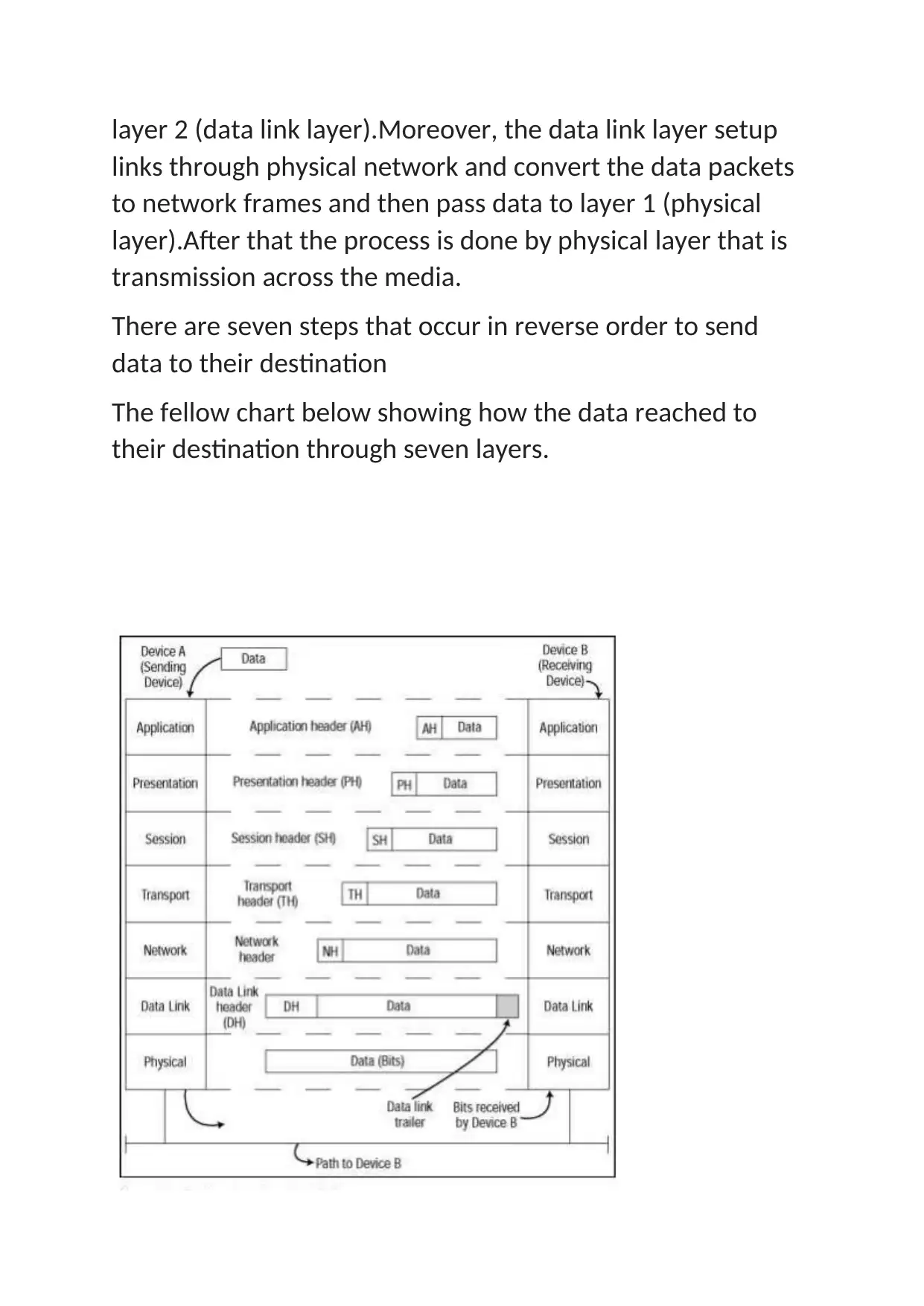
layer 2 (data link layer).Moreover, the data link layer setup
links through physical network and convert the data packets
to network frames and then pass data to layer 1 (physical
layer).After that the process is done by physical layer that is
transmission across the media.
There are seven steps that occur in reverse order to send
data to their destination
The fellow chart below showing how the data reached to
their destination through seven layers.
links through physical network and convert the data packets
to network frames and then pass data to layer 1 (physical
layer).After that the process is done by physical layer that is
transmission across the media.
There are seven steps that occur in reverse order to send
data to their destination
The fellow chart below showing how the data reached to
their destination through seven layers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Q2 Part B.
CSMA/CD one of the best protocol that we can use to find
the collision and retransmit the data.
CSMA /CD means carrier sense multiple collision
detection.CSMA/CD works with several steps, the process is
based on typical group conversation. IT is very crucial the
participants speak one by one and do not speak all at once
that can make confusing. Apart from that everyone need to
speak one by one so they can understand communication
properly. (Digital Guide, n.d.)
CSMA/CD is mostly used in networks, repeaters and
hubs .The reason is that these devices run half duplex mode
and all the ports of these devices in the same domain
collision.
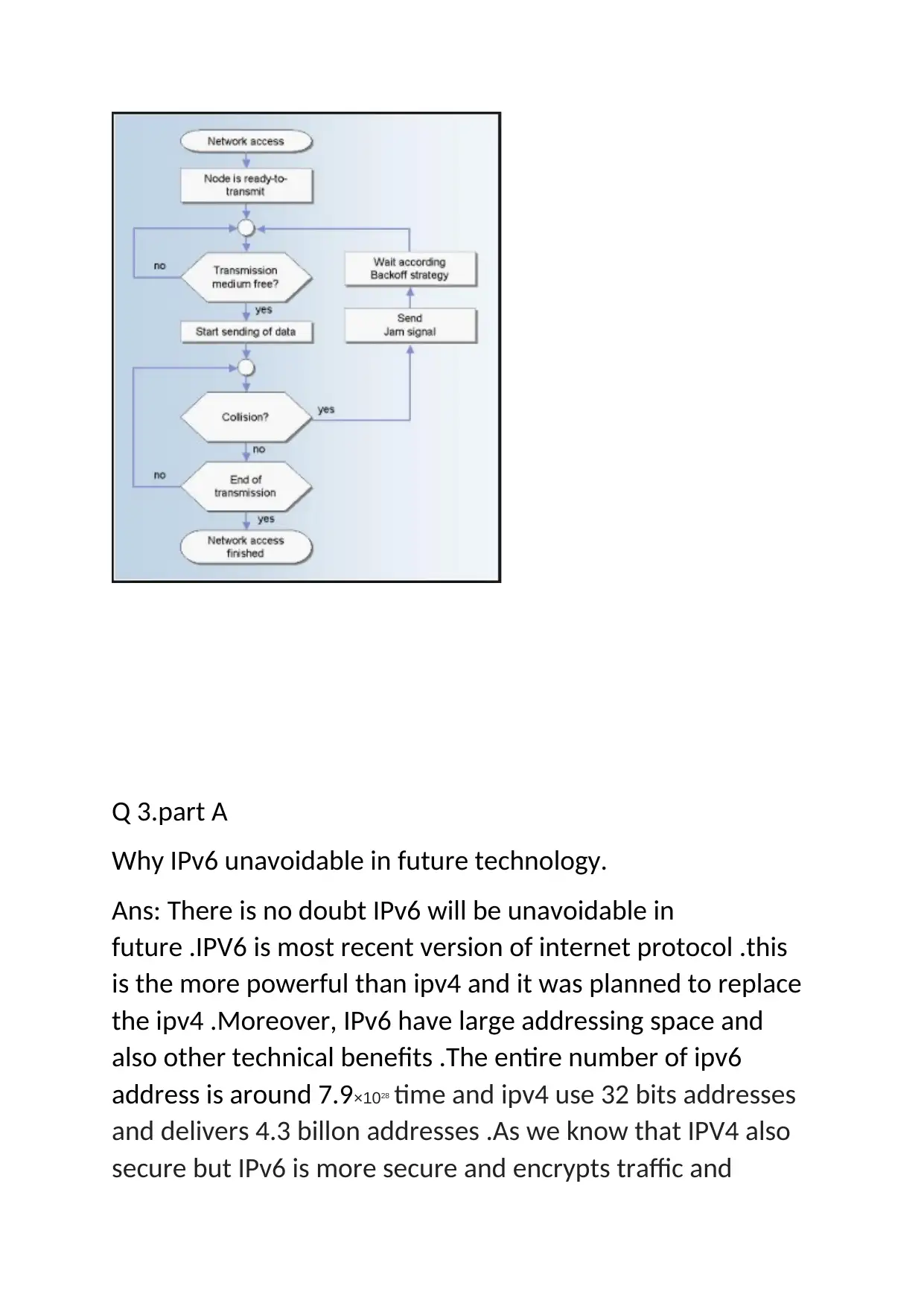
Moreover, the packet collisions happen when the
transmission happen from another host at the same time .To
prevent this collisions, CSMA/CD forces the station
transmitting to ensure for the availability of the digital
signals. The flow of the protocol below. (Digital Guide, n.d.)
CSMA/CD one of the best protocol that we can use to find
the collision and retransmit the data.
CSMA /CD means carrier sense multiple collision
detection.CSMA/CD works with several steps, the process is
based on typical group conversation. IT is very crucial the
participants speak one by one and do not speak all at once
that can make confusing. Apart from that everyone need to
speak one by one so they can understand communication
properly. (Digital Guide, n.d.)
CSMA/CD is mostly used in networks, repeaters and
hubs .The reason is that these devices run half duplex mode
and all the ports of these devices in the same domain
collision.
Moreover, the packet collisions happen when the
transmission happen from another host at the same time .To
prevent this collisions, CSMA/CD forces the station
transmitting to ensure for the availability of the digital
signals. The flow of the protocol below. (Digital Guide, n.d.)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Q 3.part A
Why IPv6 unavoidable in future technology.
Ans: There is no doubt IPv6 will be unavoidable in
future .IPV6 is most recent version of internet protocol .this
is the more powerful than ipv4 and it was planned to replace
the ipv4 .Moreover, IPv6 have large addressing space and
also other technical benefits .The entire number of ipv6
address is around 7.9×1028 time and ipv4 use 32 bits addresses
and delivers 4.3 billon addresses .As we know that IPV4 also
secure but IPv6 is more secure and encrypts traffic and
Why IPv6 unavoidable in future technology.
Ans: There is no doubt IPv6 will be unavoidable in
future .IPV6 is most recent version of internet protocol .this
is the more powerful than ipv4 and it was planned to replace
the ipv4 .Moreover, IPv6 have large addressing space and
also other technical benefits .The entire number of ipv6
address is around 7.9×1028 time and ipv4 use 32 bits addresses
and delivers 4.3 billon addresses .As we know that IPV4 also
secure but IPv6 is more secure and encrypts traffic and

always check the packet reliability to deliver the VPN like
protection for the standard traffic.
There are number of reasons why ipv6 is unavoidable in
future. (Secure edge, 2018)
1. Huge addresses space.
2. Multicasting.
3. Extension in SLAAC privacy.
4. Easy processing by routers.
5. Headers extension.
6. addresses uniqueness.
7. High security than IPV4.
Security, Efficiency and Inevitability are three main reasons
people will switch to IPV6 in future.
Q 3 part B
Ans: There are three different types of Ipv6 addressing
modes.
Unicast
Multicast
Any cast
1. Unicast : The unicast transmissions from one node to
another node .most of the protocols over the internet
are unicast for example Https / Http web,Smtps / smtp
(sending emails), FTP ( transfer files) ,SSH ( secure
protection for the standard traffic.
There are number of reasons why ipv6 is unavoidable in
future. (Secure edge, 2018)
1. Huge addresses space.
2. Multicasting.
3. Extension in SLAAC privacy.
4. Easy processing by routers.
5. Headers extension.
6. addresses uniqueness.
7. High security than IPV4.
Security, Efficiency and Inevitability are three main reasons
people will switch to IPV6 in future.
Q 3 part B
Ans: There are three different types of Ipv6 addressing
modes.
Unicast
Multicast
Any cast
1. Unicast : The unicast transmissions from one node to
another node .most of the protocols over the internet
are unicast for example Https / Http web,Smtps / smtp
(sending emails), FTP ( transfer files) ,SSH ( secure
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

terminal) ,DNS , SCP, etc. The three transport layer
protocols work with the unicast transmission mode.
UDP, TCP and SCTP are three transport layers.
The picture below is the example of unicast addressing .
protocols work with the unicast transmission mode.
UDP, TCP and SCTP are three transport layers.
The picture below is the example of unicast addressing .
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
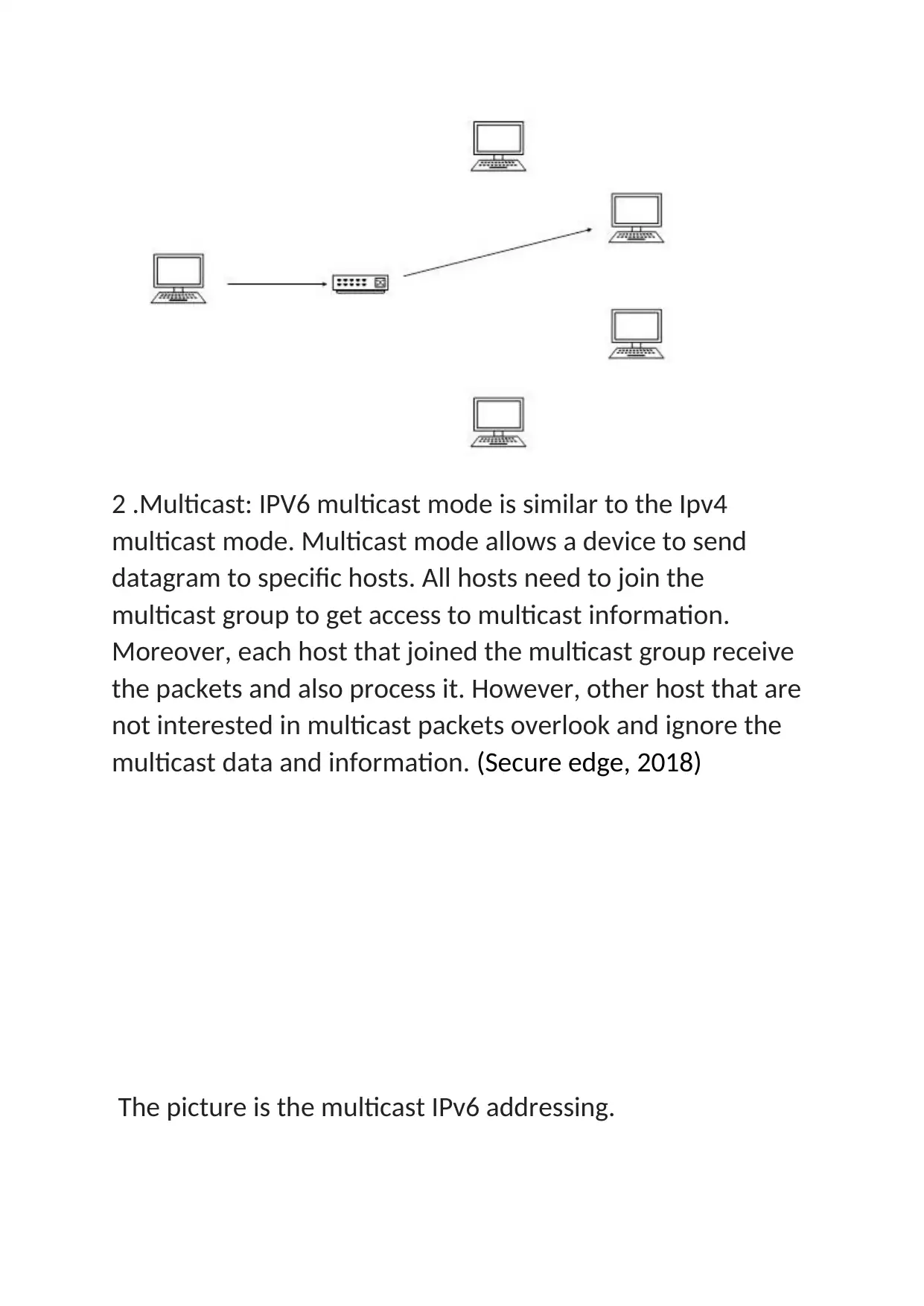
2 .Multicast: IPV6 multicast mode is similar to the Ipv4
multicast mode. Multicast mode allows a device to send
datagram to specific hosts. All hosts need to join the
multicast group to get access to multicast information.
Moreover, each host that joined the multicast group receive
the packets and also process it. However, other host that are
not interested in multicast packets overlook and ignore the
multicast data and information. (Secure edge, 2018)
The picture is the multicast IPv6 addressing.
multicast mode. Multicast mode allows a device to send
datagram to specific hosts. All hosts need to join the
multicast group to get access to multicast information.
Moreover, each host that joined the multicast group receive
the packets and also process it. However, other host that are
not interested in multicast packets overlook and ignore the
multicast data and information. (Secure edge, 2018)
The picture is the multicast IPv6 addressing.
.
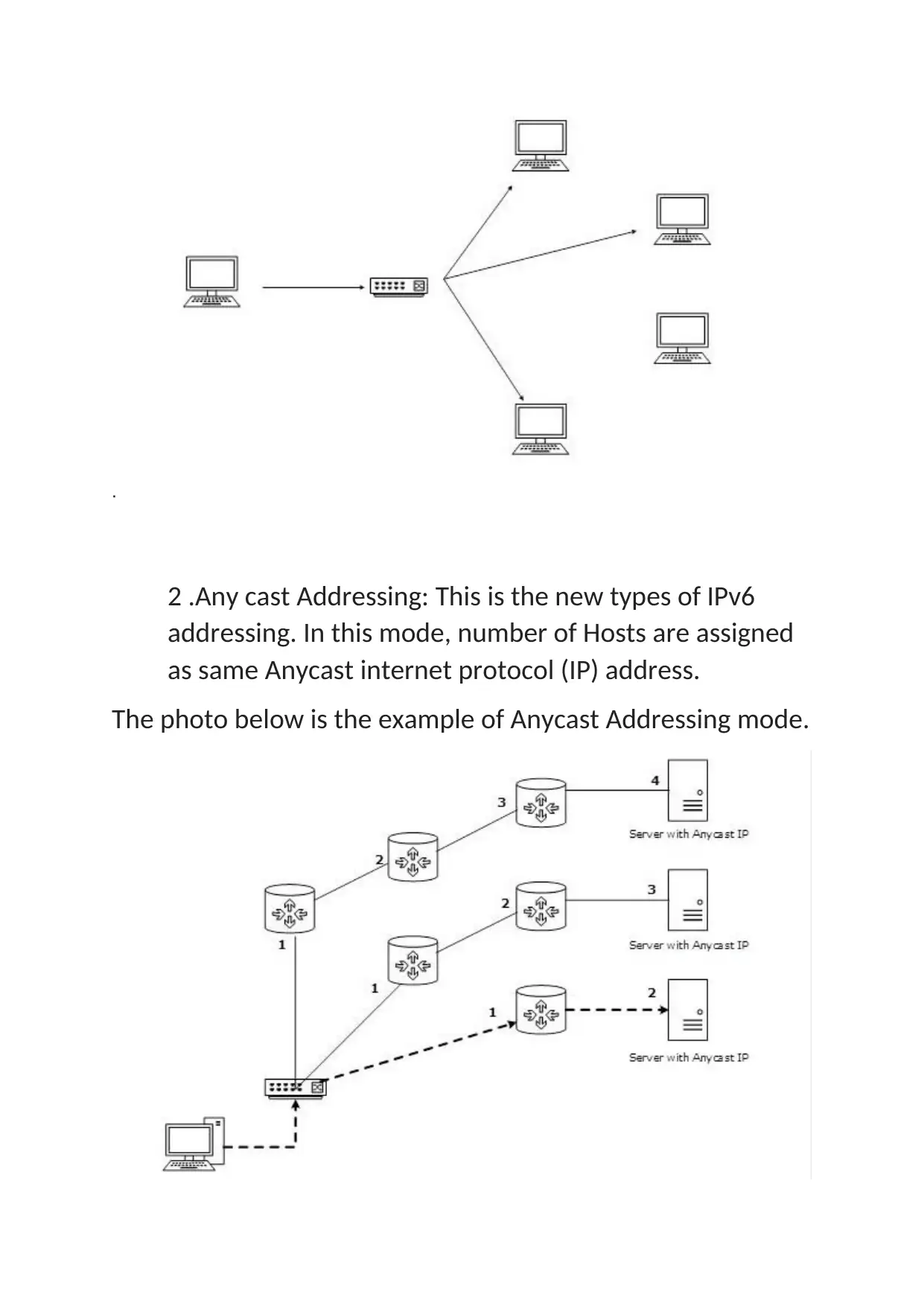
2 .Any cast Addressing: This is the new types of IPv6
addressing. In this mode, number of Hosts are assigned
as same Anycast internet protocol (IP) address.
The photo below is the example of Anycast Addressing mode.
2 .Any cast Addressing: This is the new types of IPv6
addressing. In this mode, number of Hosts are assigned
as same Anycast internet protocol (IP) address.
The photo below is the example of Anycast Addressing mode.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 53
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





