Network Design and Analysis
VerifiedAdded on 2022/08/31
|25
|5819
|34
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: NETWORK DESIGN AND ANALYSIS
Network Design and Analysis
Name of the Student
Name of the University
Author Note
Network Design and Analysis
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1NETWORK DESIGN AND ANALYSIS
Executive Summary
Over time the importance of network infrastructure in public places of interest have grown
significantly. This report will be taking a detailed look at the network requirements and
suggesting a network design for one such public place of tourist attraction which is the
Edinburgh Zoo. First the report will be presenting how the network for the Edinburgh Zoo is
acquired and then will be listing the benefits that the zoo can enjoy from such a network.
Next the networking model based on which the network of the Edinburgh Zoo is to be
designed will be shown and discussed. After that report will be presenting the logical network
diagram for the Edinburgh Zoo and is to provide justification for the same. Thereafter the
cabling requirements of the zoo needs to be specified for which the physical network diagram
is first drawn. Following this the required serial and Ethernet cabling costs for respective
measurements are given. Then the specific network infrastructure devices that get used in the
network of the zoo are discussed. After this, two products for each device is suggested along
with justification. Next the IP addressing for the network is given before discussing about the
foreground and background services of the network. Following this the network monitoring
with appropriate tool is suggested. After listing the three security threats to the network and
suggesting how the network can be kept secure, the report ends with conclusions.
Executive Summary
Over time the importance of network infrastructure in public places of interest have grown
significantly. This report will be taking a detailed look at the network requirements and
suggesting a network design for one such public place of tourist attraction which is the
Edinburgh Zoo. First the report will be presenting how the network for the Edinburgh Zoo is
acquired and then will be listing the benefits that the zoo can enjoy from such a network.
Next the networking model based on which the network of the Edinburgh Zoo is to be
designed will be shown and discussed. After that report will be presenting the logical network
diagram for the Edinburgh Zoo and is to provide justification for the same. Thereafter the
cabling requirements of the zoo needs to be specified for which the physical network diagram
is first drawn. Following this the required serial and Ethernet cabling costs for respective
measurements are given. Then the specific network infrastructure devices that get used in the
network of the zoo are discussed. After this, two products for each device is suggested along
with justification. Next the IP addressing for the network is given before discussing about the
foreground and background services of the network. Following this the network monitoring
with appropriate tool is suggested. After listing the three security threats to the network and
suggesting how the network can be kept secure, the report ends with conclusions.

2NETWORK DESIGN AND ANALYSIS
Table of Contents
Introduction................................................................................................................................3
Benefits of Networking..............................................................................................................4
Network Design.........................................................................................................................4
Networking Model.................................................................................................................4
Logical Design.......................................................................................................................5
Cabling Requirements............................................................................................................7
Physical Network Design...................................................................................................7
Infrastructure Devices............................................................................................................8
Sample Devices Suggested....................................................................................................9
IPv4 Addressing.......................................................................................................................11
Network Services.....................................................................................................................13
Network Monitoring.................................................................................................................15
Network Security.....................................................................................................................18
Conclusion................................................................................................................................19
References................................................................................................................................21
Table of Contents
Introduction................................................................................................................................3
Benefits of Networking..............................................................................................................4
Network Design.........................................................................................................................4
Networking Model.................................................................................................................4
Logical Design.......................................................................................................................5
Cabling Requirements............................................................................................................7
Physical Network Design...................................................................................................7
Infrastructure Devices............................................................................................................8
Sample Devices Suggested....................................................................................................9
IPv4 Addressing.......................................................................................................................11
Network Services.....................................................................................................................13
Network Monitoring.................................................................................................................15
Network Security.....................................................................................................................18
Conclusion................................................................................................................................19
References................................................................................................................................21

3NETWORK DESIGN AND ANALYSIS
Introduction
This report tries to show how relevant network infrastructure is for public places like
a zoo in today’s times. This report studies the network requirements of Edinburgh Zoo and
suggests a network design accordingly. The report begins by presenting how the network for
the Edinburgh Zoo is acquired and then lists the benefits that the zoo can enjoy from such a
network (Zhao et al. 2018). Next the networking model based on which the network of the
Edinburgh Zoo is to be designed gets shown and discussed. After that report presents the
logical network diagram for the Edinburgh Zoo and also provides the justification
(D’Andreagiovanni, and Gleixner 2016). Thereafter the cabling requirements of the zoo
needs is to be specified for which the physical network diagram gets drawn. Following this
the required costs of serial and Ethernet cabling for the respective measurements are given.
Then the specific network infrastructure devices which are getting used in the network of the
zoo are discussed. After this, examples of two products for each device is suggested while
also justifying their use. Next the IP addressing for the network is given before discussing
about the foreground and background services of the network. Following this the network
monitoring with appropriate tool is suggested. After listing the three security threats to the
network and suggesting how the network can be kept secure, the report ends with
conclusions.
Introduction
This report tries to show how relevant network infrastructure is for public places like
a zoo in today’s times. This report studies the network requirements of Edinburgh Zoo and
suggests a network design accordingly. The report begins by presenting how the network for
the Edinburgh Zoo is acquired and then lists the benefits that the zoo can enjoy from such a
network (Zhao et al. 2018). Next the networking model based on which the network of the
Edinburgh Zoo is to be designed gets shown and discussed. After that report presents the
logical network diagram for the Edinburgh Zoo and also provides the justification
(D’Andreagiovanni, and Gleixner 2016). Thereafter the cabling requirements of the zoo
needs is to be specified for which the physical network diagram gets drawn. Following this
the required costs of serial and Ethernet cabling for the respective measurements are given.
Then the specific network infrastructure devices which are getting used in the network of the
zoo are discussed. After this, examples of two products for each device is suggested while
also justifying their use. Next the IP addressing for the network is given before discussing
about the foreground and background services of the network. Following this the network
monitoring with appropriate tool is suggested. After listing the three security threats to the
network and suggesting how the network can be kept secure, the report ends with
conclusions.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4NETWORK DESIGN AND ANALYSIS
Benefits of Networking
A network with wireless connection support can be suggested for the Edinburgh Zoo.
Here, the network for the Zoo is acquired by the adjoining hotel from the ISP. From this hotel
the network is spread throughout the Zoo. As a result the Zoo can benefit from this network
in the following ways:
Efficient distribution of network throughout the Zoo
Network support for wired as well as wireless devices from anywhere within the Zoo
Multiple wireless access points across different regions of the Zoo
Uniform network signals and bandwidth across different sites of attraction
Independent configuration of every network segment
Isolation of communication among different network segments
Network Design
Networking Model
Figure 1: Router on a Stick networking model
Benefits of Networking
A network with wireless connection support can be suggested for the Edinburgh Zoo.
Here, the network for the Zoo is acquired by the adjoining hotel from the ISP. From this hotel
the network is spread throughout the Zoo. As a result the Zoo can benefit from this network
in the following ways:
Efficient distribution of network throughout the Zoo
Network support for wired as well as wireless devices from anywhere within the Zoo
Multiple wireless access points across different regions of the Zoo
Uniform network signals and bandwidth across different sites of attraction
Independent configuration of every network segment
Isolation of communication among different network segments
Network Design
Networking Model
Figure 1: Router on a Stick networking model
5NETWORK DESIGN AND ANALYSIS
The network design of the Zoo is to be established in the ‘router on a stick model’ so
as to provide maximum benefits to the visitors as well as the administrators of the Zoo
network. This model enables VLAN based configuration of separate network segments such
that systems connected to one network segment can communicate with the systems connected
by another network system. This is ensured through inter VLAN routing via the L3 switch.
ACL restrictions can be used to restrict access to a specific network segment.
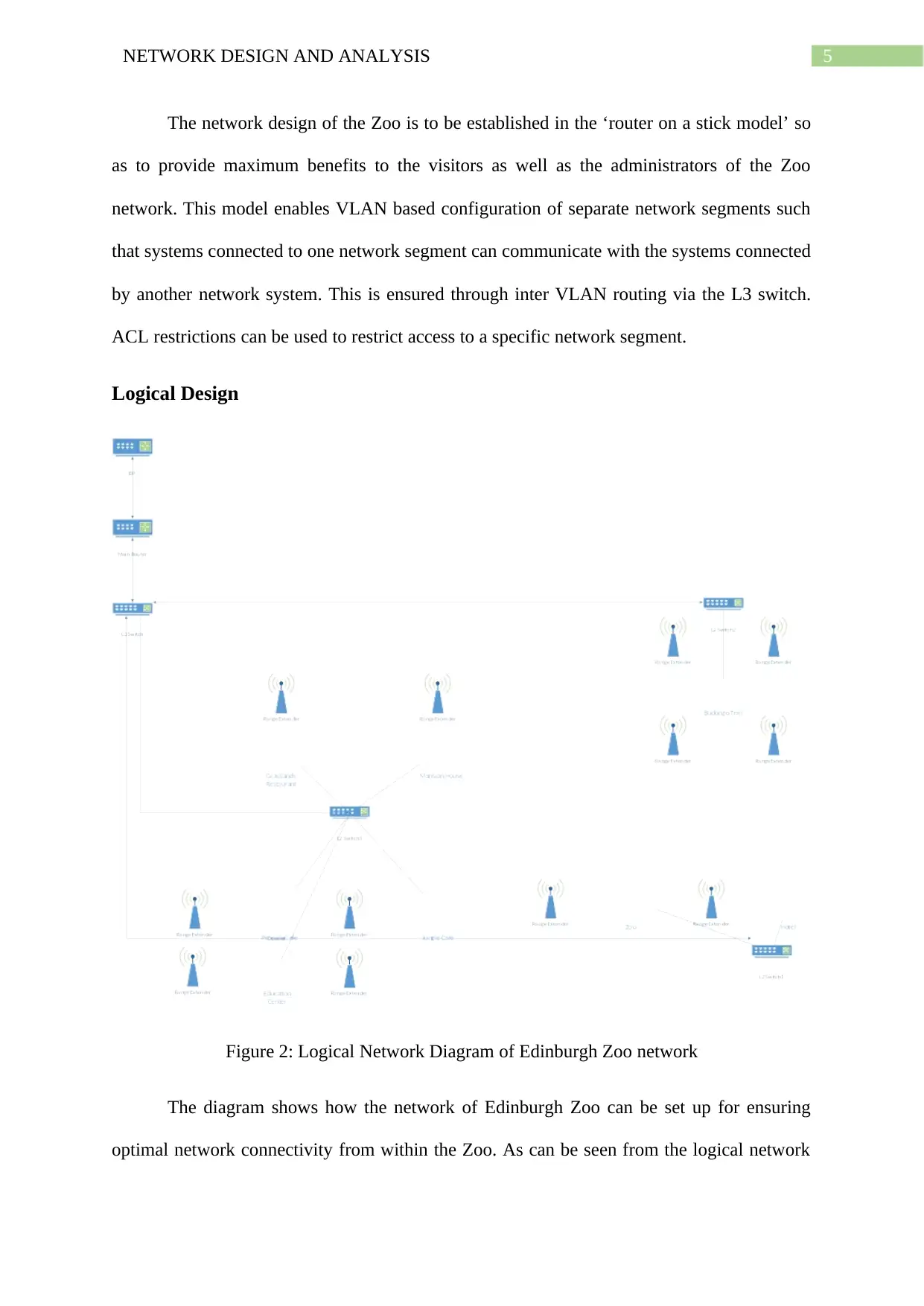
Logical Design
Figure 2: Logical Network Diagram of Edinburgh Zoo network
The diagram shows how the network of Edinburgh Zoo can be set up for ensuring
optimal network connectivity from within the Zoo. As can be seen from the logical network
The network design of the Zoo is to be established in the ‘router on a stick model’ so
as to provide maximum benefits to the visitors as well as the administrators of the Zoo
network. This model enables VLAN based configuration of separate network segments such
that systems connected to one network segment can communicate with the systems connected
by another network system. This is ensured through inter VLAN routing via the L3 switch.
ACL restrictions can be used to restrict access to a specific network segment.
Logical Design
Figure 2: Logical Network Diagram of Edinburgh Zoo network
The diagram shows how the network of Edinburgh Zoo can be set up for ensuring
optimal network connectivity from within the Zoo. As can be seen from the logical network

6NETWORK DESIGN AND ANALYSIS
diagram, the main router and the layer 3 switch for the Edinburgh Zoo network is installed in
the Hotel adjoining the entrance of the Edinburgh Zoo entrance. The network is acquired by
the router in the Hotel from the ISP. From a layer 2 switch connected to the layer 3 switch the
network connections are provided to the wireless routers of the hotel and the Zoo entrance
(Wu and Zhang 2018). Similarly, the layer 3 switch connects with other layer 2 switches
installed further inside the Zoo for providing connections to the wireless routers in major
buildings like the education center, mansion hall, cafes and other buildings of interest
(Fortuna et al. 2016). These wireless routers connect the various workstations of the Zoo
administrators and also serve as wireless access points for the smart devices carried by the
visitors. They also provide wireless connectivity to surveillance cameras, motion detectors
and other smart monitoring devices used for tracking the animals being kept in the Zoo (Park
et al. 2017). The range of these wireless routers can be extended further with the use of range
extenders.
diagram, the main router and the layer 3 switch for the Edinburgh Zoo network is installed in
the Hotel adjoining the entrance of the Edinburgh Zoo entrance. The network is acquired by
the router in the Hotel from the ISP. From a layer 2 switch connected to the layer 3 switch the
network connections are provided to the wireless routers of the hotel and the Zoo entrance
(Wu and Zhang 2018). Similarly, the layer 3 switch connects with other layer 2 switches
installed further inside the Zoo for providing connections to the wireless routers in major
buildings like the education center, mansion hall, cafes and other buildings of interest
(Fortuna et al. 2016). These wireless routers connect the various workstations of the Zoo
administrators and also serve as wireless access points for the smart devices carried by the
visitors. They also provide wireless connectivity to surveillance cameras, motion detectors
and other smart monitoring devices used for tracking the animals being kept in the Zoo (Park
et al. 2017). The range of these wireless routers can be extended further with the use of range
extenders.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK DESIGN AND ANALYSIS
Cabling Requirements
Physical Network Design
Figure 2: Physical Network Diagram of Edinburgh Zoo network
The above diagram presents the physical network design of Edinburgh Zoo (Lane
2018). It is found that the wireless range extenders are present in a specific direction from
their respective routers. This is because the range extenders are to be positioned strategically
in different sites of attraction to provide maximum network coverage within the zoo (Taha,
Salehi and Abraham 2018). The range extenders ensure this by extending the maximum range
of the network they receive from the wireless routers (Kabashkin and Kundler 2017). The
Cabling Requirements
Physical Network Design
Figure 2: Physical Network Diagram of Edinburgh Zoo network
The above diagram presents the physical network design of Edinburgh Zoo (Lane
2018). It is found that the wireless range extenders are present in a specific direction from
their respective routers. This is because the range extenders are to be positioned strategically
in different sites of attraction to provide maximum network coverage within the zoo (Taha,
Salehi and Abraham 2018). The range extenders ensure this by extending the maximum range
of the network they receive from the wireless routers (Kabashkin and Kundler 2017). The

8NETWORK DESIGN AND ANALYSIS
network is to be built using different types of cables including serial cables as well as straight
through and crossover Ethernet cables.
Serial Cables: The main router of the Zoo Network is connected to routers of the ISP WAN
network through serial cables that connect to the WIC-1T and WIC-2T ports of the routers.
15 ft of such DTE/DCE serial cables can cost USD 50.
Ethernet Cables: The internal LAN network of the Zoo is to be connected with the help of
two distinct types of Ethernet Cat 6 cables, the straight through and crossover cables. The
straight through cables are used to facilitate connections between the router and the layer 3
switch, between the layer 2 switch and the wireless router and between this wireless router
and the workstations (Yang, Li and Qiu 2016). The crossover Ethernet cables are used to
distribute the network from the layer 3 switch to the layer 2 switches. 100 ft of Cat 6 Ethernet
cables can cost USD 17.
Infrastructure Devices
Router: A generic router is to be used by the Zoo to obtain the required network from the
ISP and distribute it to rest of the sections of the network (Swapna et al. 2019). Since inter
VLAN routing is being applied in the network, this router needs to have appropriate subnet
configurations for the VLANs created. As the network requires to connect both workstations
and varying number of smart devices, DHCP pools for each VLAN should also be
configured. This will ensure automatic allocation of IP addresses to the devices attempting to
connect to the Zoo network.
Layer 3 Switch: These are switches that are built with routing capabilities. These switches
store the list of all the VLANs in the VLAN database. The switch distributes the network to
the switches of respective VLANs by providing the connections through its interfaces in
trunk mode (Namazi and Lin 2019). The trunking functionality enables communications
network is to be built using different types of cables including serial cables as well as straight
through and crossover Ethernet cables.
Serial Cables: The main router of the Zoo Network is connected to routers of the ISP WAN
network through serial cables that connect to the WIC-1T and WIC-2T ports of the routers.
15 ft of such DTE/DCE serial cables can cost USD 50.
Ethernet Cables: The internal LAN network of the Zoo is to be connected with the help of
two distinct types of Ethernet Cat 6 cables, the straight through and crossover cables. The
straight through cables are used to facilitate connections between the router and the layer 3
switch, between the layer 2 switch and the wireless router and between this wireless router
and the workstations (Yang, Li and Qiu 2016). The crossover Ethernet cables are used to
distribute the network from the layer 3 switch to the layer 2 switches. 100 ft of Cat 6 Ethernet
cables can cost USD 17.
Infrastructure Devices
Router: A generic router is to be used by the Zoo to obtain the required network from the
ISP and distribute it to rest of the sections of the network (Swapna et al. 2019). Since inter
VLAN routing is being applied in the network, this router needs to have appropriate subnet
configurations for the VLANs created. As the network requires to connect both workstations
and varying number of smart devices, DHCP pools for each VLAN should also be
configured. This will ensure automatic allocation of IP addresses to the devices attempting to
connect to the Zoo network.
Layer 3 Switch: These are switches that are built with routing capabilities. These switches
store the list of all the VLANs in the VLAN database. The switch distributes the network to
the switches of respective VLANs by providing the connections through its interfaces in
trunk mode (Namazi and Lin 2019). The trunking functionality enables communications

9NETWORK DESIGN AND ANALYSIS
between multiple switches having different VLANs thus making the inter VLAN routing
successful.
Layer 2 Switch: These are the switches that are responsible for directly connecting the host
devices (Aweya 2018). However, since both workstations and smart devices are to be
connected, Wireless routers are connected to these switches. These switches do not have
routing features.
Wireless Router/Access Points: In addition to providing connections to workstations
through Ethernet cables these routers also contain wireless antennas that enable Wi-Fi
services for devices that support it thus doubling up as wireless access points.
Wireless Range Extender: The wireless range extenders are the standalone network
equipment that sits between the wireless routers and the location where the network needs to
be provided (Wijesundara et al. 2016). Just like wireless repeaters these devices receive
wireless network signal from the wireless router and rebroadcasts this signal so that the
desired network coverage can be achieved (Lin et al. 2016). The range extenders use a
different wireless channel than that of the wireless router.
Sample Devices Suggested
Router: The sample router that can be suggested for the zoo can be the Cisco RV340 and
RV320 Dual WAN Gigabit VPN routers (Gjerseth 2017). This router is offered by Cisco for
small business networks or for implementations with equivalent network requirements. These
routers contain the following port specifications:
2 WAN ports for RJ-45 connector Ethernet cables to serve load balancing and
resiliency needs.
4 LAN ports for high performance connections in LAN networks.
2 USB ports that also support modems or flash drives with 3G and 4G connectivity
between multiple switches having different VLANs thus making the inter VLAN routing
successful.
Layer 2 Switch: These are the switches that are responsible for directly connecting the host
devices (Aweya 2018). However, since both workstations and smart devices are to be
connected, Wireless routers are connected to these switches. These switches do not have
routing features.
Wireless Router/Access Points: In addition to providing connections to workstations
through Ethernet cables these routers also contain wireless antennas that enable Wi-Fi
services for devices that support it thus doubling up as wireless access points.
Wireless Range Extender: The wireless range extenders are the standalone network
equipment that sits between the wireless routers and the location where the network needs to
be provided (Wijesundara et al. 2016). Just like wireless repeaters these devices receive
wireless network signal from the wireless router and rebroadcasts this signal so that the
desired network coverage can be achieved (Lin et al. 2016). The range extenders use a
different wireless channel than that of the wireless router.
Sample Devices Suggested
Router: The sample router that can be suggested for the zoo can be the Cisco RV340 and
RV320 Dual WAN Gigabit VPN routers (Gjerseth 2017). This router is offered by Cisco for
small business networks or for implementations with equivalent network requirements. These
routers contain the following port specifications:
2 WAN ports for RJ-45 connector Ethernet cables to serve load balancing and
resiliency needs.
4 LAN ports for high performance connections in LAN networks.
2 USB ports that also support modems or flash drives with 3G and 4G connectivity
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10NETWORK DESIGN AND ANALYSIS
Ensures 900 Mbps TCP throughput for fast and productive domain access
The key connections that the Edinburgh Zoo requires from the main router are one WAN
connection with the ISP and one LAN connection with the layer 3 switch. Hence, the RV340
router is enough for the zoo. Other more expensive routers like the RV345 which contains 16
LAN ports are not required. These routers can cost about 360 GBP.
Layer 3 Switch: The layer 3 switches that can be suggested are the Cisco SG350-10p and
SG350-24p switches offered by Cisco. This is because the switch enables configuration of
multiple VLANs, allows to configure Access Control Lists and supports several other routing
mechanisms. These switches offer 10 or 24 Gigabit Ethernet ports and are therefore enough
for the zoo network. These layer 3 switches can cost in the range of 300 to 450 GBP.
Layer 2 Switch: The layer 2 switch that can be suggested is the Cisco SG112-16 and SG112-
24 switches. These switches are both rack mountable or can be installed in desktop mode
(Kocz et al. 2019). The Power over Ethernet feature of the switch also negates the
requirement of installing it in specific buildings and can even be used to form an on premise
network. The switch contains 16 or 24 ports and hence is enough for the zoo and can also
support future expansions of the internal LAN network. These layer 2 switches can cost
upwards from 150 GBP.
Wireless Router: The wireless routers that can be suggested are the RV110W and RV130W
routers being offered by Cisco. These routers contain integrated 4-port Gigabit Ethernet
switches so that they can direct connect the workstations (Yao, Sheng and Mi 2016). They
also support built-in high-speed Wireless-N access points while also offering USB 3G and
4G failover systems and hence ideal for the zoo network (Pratama, Sugesti and Mayasari
2017). These wireless routers can cost 90 GBP.
Ensures 900 Mbps TCP throughput for fast and productive domain access
The key connections that the Edinburgh Zoo requires from the main router are one WAN
connection with the ISP and one LAN connection with the layer 3 switch. Hence, the RV340
router is enough for the zoo. Other more expensive routers like the RV345 which contains 16
LAN ports are not required. These routers can cost about 360 GBP.
Layer 3 Switch: The layer 3 switches that can be suggested are the Cisco SG350-10p and
SG350-24p switches offered by Cisco. This is because the switch enables configuration of
multiple VLANs, allows to configure Access Control Lists and supports several other routing
mechanisms. These switches offer 10 or 24 Gigabit Ethernet ports and are therefore enough
for the zoo network. These layer 3 switches can cost in the range of 300 to 450 GBP.
Layer 2 Switch: The layer 2 switch that can be suggested is the Cisco SG112-16 and SG112-
24 switches. These switches are both rack mountable or can be installed in desktop mode
(Kocz et al. 2019). The Power over Ethernet feature of the switch also negates the
requirement of installing it in specific buildings and can even be used to form an on premise
network. The switch contains 16 or 24 ports and hence is enough for the zoo and can also
support future expansions of the internal LAN network. These layer 2 switches can cost
upwards from 150 GBP.
Wireless Router: The wireless routers that can be suggested are the RV110W and RV130W
routers being offered by Cisco. These routers contain integrated 4-port Gigabit Ethernet
switches so that they can direct connect the workstations (Yao, Sheng and Mi 2016). They
also support built-in high-speed Wireless-N access points while also offering USB 3G and
4G failover systems and hence ideal for the zoo network (Pratama, Sugesti and Mayasari
2017). These wireless routers can cost 90 GBP.
11NETWORK DESIGN AND ANALYSIS
Range Extender: A suitable range extender for the zoo network can be the Cisco Linksys
RE1000 and 2000 Wi-Fi Range Extenders (Ndlovu, Kogeda and Lall 2018). The product
contains 2 internal antennas and supports the standards IEEE 802.11n, 802.11g, 802.11b and
802.3u. Therefore, the product is appropriate for the zoo network and can be acquired at USD
65-70 GBP per unit.
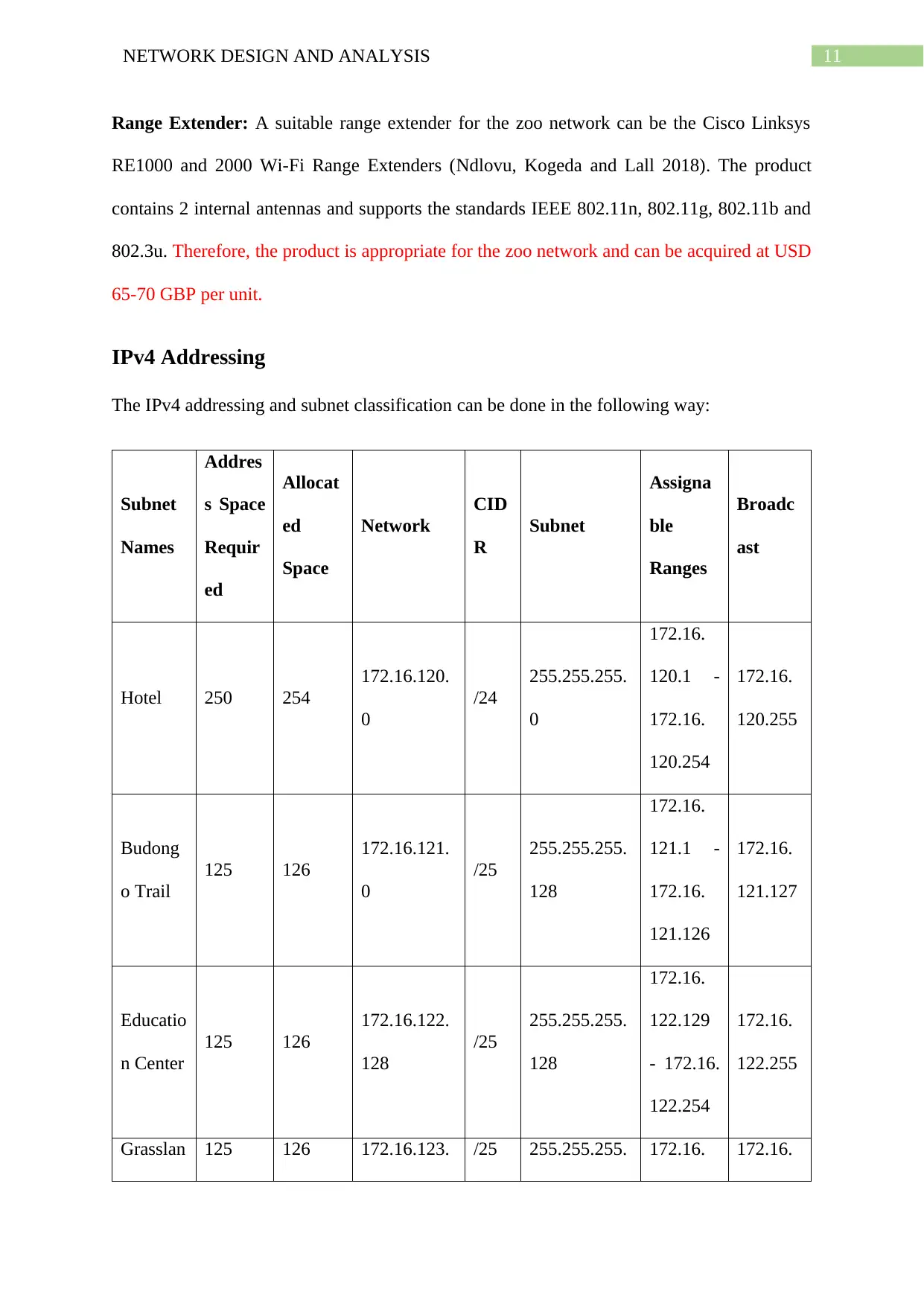
IPv4 Addressing
The IPv4 addressing and subnet classification can be done in the following way:
Subnet
Names
Addres
s Space
Requir
ed
Allocat
ed
Space
Network
CID
R
Subnet
Assigna
ble
Ranges
Broadc
ast
Hotel 250 254
172.16.120.
0
/24
255.255.255.
0
172.16.
120.1 -
172.16.
120.254
172.16.
120.255
Budong
o Trail
125 126
172.16.121.
0
/25
255.255.255.
128
172.16.
121.1 -
172.16.
121.126
172.16.
121.127
Educatio
n Center
125 126
172.16.122.
128
/25
255.255.255.
128
172.16.
122.129
- 172.16.
122.254
172.16.
122.255
Grasslan 125 126 172.16.123. /25 255.255.255. 172.16. 172.16.
Range Extender: A suitable range extender for the zoo network can be the Cisco Linksys
RE1000 and 2000 Wi-Fi Range Extenders (Ndlovu, Kogeda and Lall 2018). The product
contains 2 internal antennas and supports the standards IEEE 802.11n, 802.11g, 802.11b and
802.3u. Therefore, the product is appropriate for the zoo network and can be acquired at USD
65-70 GBP per unit.
IPv4 Addressing
The IPv4 addressing and subnet classification can be done in the following way:
Subnet
Names
Addres
s Space
Requir
ed
Allocat
ed
Space
Network
CID
R
Subnet
Assigna
ble
Ranges
Broadc
ast
Hotel 250 254
172.16.120.
0
/24
255.255.255.
0
172.16.
120.1 -
172.16.
120.254
172.16.
120.255
Budong
o Trail
125 126
172.16.121.
0
/25
255.255.255.
128
172.16.
121.1 -
172.16.
121.126
172.16.
121.127
Educatio
n Center
125 126
172.16.122.
128
/25
255.255.255.
128
172.16.
122.129
- 172.16.
122.254
172.16.
122.255
Grasslan 125 126 172.16.123. /25 255.255.255. 172.16. 172.16.
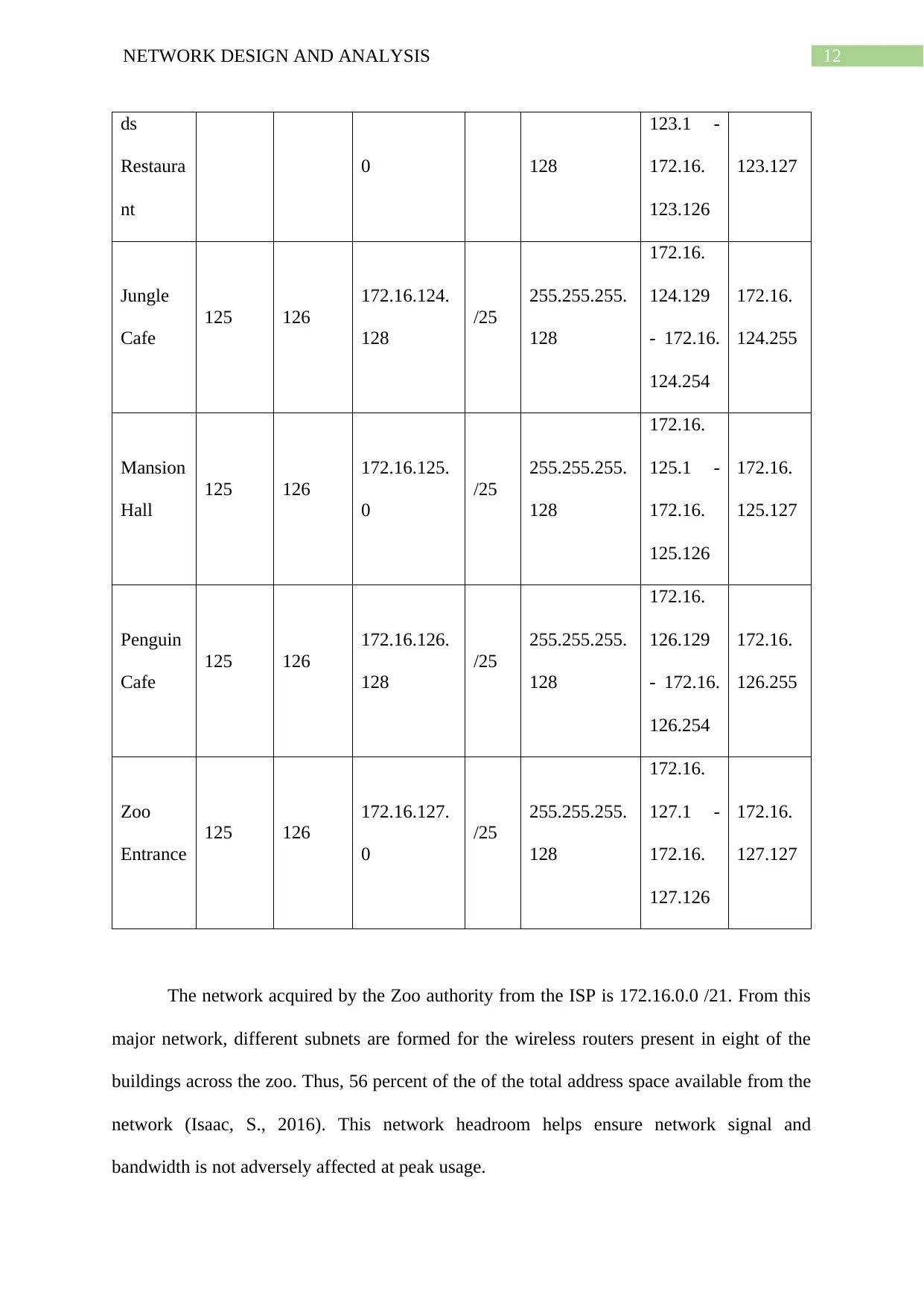
12NETWORK DESIGN AND ANALYSIS
ds
Restaura
nt
0 128
123.1 -
172.16.
123.126
123.127
Jungle
Cafe
125 126
172.16.124.
128
/25
255.255.255.
128
172.16.
124.129
- 172.16.
124.254
172.16.
124.255
Mansion
Hall
125 126
172.16.125.
0
/25
255.255.255.
128
172.16.
125.1 -
172.16.
125.126
172.16.
125.127
Penguin
Cafe
125 126
172.16.126.
128
/25
255.255.255.
128
172.16.
126.129
- 172.16.
126.254
172.16.
126.255
Zoo
Entrance
125 126
172.16.127.
0
/25
255.255.255.
128
172.16.
127.1 -
172.16.
127.126
172.16.
127.127
The network acquired by the Zoo authority from the ISP is 172.16.0.0 /21. From this
major network, different subnets are formed for the wireless routers present in eight of the
buildings across the zoo. Thus, 56 percent of the of the total address space available from the
network (Isaac, S., 2016). This network headroom helps ensure network signal and
bandwidth is not adversely affected at peak usage.
ds
Restaura
nt
0 128
123.1 -
172.16.
123.126
123.127
Jungle
Cafe
125 126
172.16.124.
128
/25
255.255.255.
128
172.16.
124.129
- 172.16.
124.254
172.16.
124.255
Mansion
Hall
125 126
172.16.125.
0
/25
255.255.255.
128
172.16.
125.1 -
172.16.
125.126
172.16.
125.127
Penguin
Cafe
125 126
172.16.126.
128
/25
255.255.255.
128
172.16.
126.129
- 172.16.
126.254
172.16.
126.255
Zoo
Entrance
125 126
172.16.127.
0
/25
255.255.255.
128
172.16.
127.1 -
172.16.
127.126
172.16.
127.127
The network acquired by the Zoo authority from the ISP is 172.16.0.0 /21. From this
major network, different subnets are formed for the wireless routers present in eight of the
buildings across the zoo. Thus, 56 percent of the of the total address space available from the
network (Isaac, S., 2016). This network headroom helps ensure network signal and
bandwidth is not adversely affected at peak usage.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13NETWORK DESIGN AND ANALYSIS
The subnet classification of the major network has been conducted with respect to the
key buildings present across the zoo. Each of these subnets are configured in the network
through their specific VLANs (Ma and Yu 2016). Each of these VLANs represent
connections of their particular wireless router. The smart devices automatically obtain the
appropriate network as they come within the range of the signal provided by a specific
wireless router (Lin, Chen and Chin 2016). This automatic configuration thus changes on the
fly for the smart devices carried by the visitors.
The network segments for providing wireless access to visitors in the zoo are to be
kept separate from the wireless network provided by the wireless router in the hotel (Farooq-
I-Azam, Ni and Ansari 2016). This is done to ensure the privacy of the tourists staying in the
hotel. This kind of restriction is imposed on the network by configuring access control lists in
the main router and then implementing the access group to the subnet of the hotel. The
configuration includes specifying deny rules for ICMP connections of other subnet networks
to the hotel subnet network which is 172.16.120.0 (Lima et al. 2019). Here the hotel
accommodates about double the people than the average number of visitors estimated to be
present in a specific part of the zoo and hence the address space allocated to the hotel is twice
that of the subnet serving connections to a specific portion of the zoo.
Network Services
The network of Edinburgh Zoo can be used to offer various foreground networking
services like Emailing, chatting or even background services like automatic connections with
nearest wireless router and domain name service (DNS) (Mondal et al. 2016). The visitors of
the zoo can be temporarily be assigned registered account IDs to the internal web portal of
the zoo as well as the mailing domain which are hosted in the in the workstations or servers
used by the zoo network administrators. This ensures that the tourists and visitors get all the
The subnet classification of the major network has been conducted with respect to the
key buildings present across the zoo. Each of these subnets are configured in the network
through their specific VLANs (Ma and Yu 2016). Each of these VLANs represent
connections of their particular wireless router. The smart devices automatically obtain the
appropriate network as they come within the range of the signal provided by a specific
wireless router (Lin, Chen and Chin 2016). This automatic configuration thus changes on the
fly for the smart devices carried by the visitors.
The network segments for providing wireless access to visitors in the zoo are to be
kept separate from the wireless network provided by the wireless router in the hotel (Farooq-
I-Azam, Ni and Ansari 2016). This is done to ensure the privacy of the tourists staying in the
hotel. This kind of restriction is imposed on the network by configuring access control lists in
the main router and then implementing the access group to the subnet of the hotel. The
configuration includes specifying deny rules for ICMP connections of other subnet networks
to the hotel subnet network which is 172.16.120.0 (Lima et al. 2019). Here the hotel
accommodates about double the people than the average number of visitors estimated to be
present in a specific part of the zoo and hence the address space allocated to the hotel is twice
that of the subnet serving connections to a specific portion of the zoo.
Network Services
The network of Edinburgh Zoo can be used to offer various foreground networking
services like Emailing, chatting or even background services like automatic connections with
nearest wireless router and domain name service (DNS) (Mondal et al. 2016). The visitors of
the zoo can be temporarily be assigned registered account IDs to the internal web portal of
the zoo as well as the mailing domain which are hosted in the in the workstations or servers
used by the zoo network administrators. This ensures that the tourists and visitors get all the

14NETWORK DESIGN AND ANALYSIS
help they need in making their way around the sites of attraction of Edinburgh Zoo. This also
helps if visitors lose track of their own family members or finds themselves lost. They can
always contact the authorities using their temporary account credentials and can also
communicate with their lost member through smartphones and thus can successfully make
their way back to the missing family member (Yang et al. 2018). Since the servers or
workstations hosting these services will be managed by the zoo authorities, these will be
using the zoo network which is the 172.16.127.0 network. After configuration the DNS
address will be shared automatically to the smart devices that are accessing network through
the DHCP protocol. In this way the web portal will be made accessible to the internal LAN
network of the Edinburgh Zoo.
However, to ensure that the visitors do not make mis use of these facilities offered
limited access to the internet should be allowed. This involves blocking of torrent sites,
imposing usage limits which can be renewed with permission and extra fees. This way the
zoo can keep check of people only gathering in the zoo to enjoy free Internet.
In other words, with the foreground services like email, chat and web portal, the zoo
is being able to stay in touch with the visitors or ensure the visitors can communicate with
one another or helping the visitors consult with the overall zoo map from the web portal. The
foreground services thus enable the zoo authorities to run emergency response services
throughout the hours for which the zoo remains open. These can also help the visitors report
zoo authorities if they notice health issues among the animals that are being kept in the zoo.
Thus, such services can present a win-win situation for the Edinburgh Zoo and hence shall be
provided to all visitors mandatorily.
On the other hand with background services like auto connections DNS and Firewall,
the zoo authorities are not only making sure that the foreground services are made available
help they need in making their way around the sites of attraction of Edinburgh Zoo. This also
helps if visitors lose track of their own family members or finds themselves lost. They can
always contact the authorities using their temporary account credentials and can also
communicate with their lost member through smartphones and thus can successfully make
their way back to the missing family member (Yang et al. 2018). Since the servers or
workstations hosting these services will be managed by the zoo authorities, these will be
using the zoo network which is the 172.16.127.0 network. After configuration the DNS
address will be shared automatically to the smart devices that are accessing network through
the DHCP protocol. In this way the web portal will be made accessible to the internal LAN
network of the Edinburgh Zoo.
However, to ensure that the visitors do not make mis use of these facilities offered
limited access to the internet should be allowed. This involves blocking of torrent sites,
imposing usage limits which can be renewed with permission and extra fees. This way the
zoo can keep check of people only gathering in the zoo to enjoy free Internet.
In other words, with the foreground services like email, chat and web portal, the zoo
is being able to stay in touch with the visitors or ensure the visitors can communicate with
one another or helping the visitors consult with the overall zoo map from the web portal. The
foreground services thus enable the zoo authorities to run emergency response services
throughout the hours for which the zoo remains open. These can also help the visitors report
zoo authorities if they notice health issues among the animals that are being kept in the zoo.
Thus, such services can present a win-win situation for the Edinburgh Zoo and hence shall be
provided to all visitors mandatorily.
On the other hand with background services like auto connections DNS and Firewall,
the zoo authorities are not only making sure that the foreground services are made available

15NETWORK DESIGN AND ANALYSIS
to these users but are also being able to strictly monitor their network usage prevent access to
specific network segments and preventing the visitor smartphones from getting infected from
malwares and other security threats of the public Internet (Ori 2016). This is highly essential
as the security provided by the zoo authorities instil certain level of confidence among the
visitors and tourists so that they can make use of the zoo network without fears about their
private information getting stolen or their credentials being known to the attack when
conducting digital payments and transactions.
Network Monitoring
Among the most useful network monitoring tools that the authorities of the Edinburgh Zoo
can use to maintain or diagnose the services of the zoo network can be protocol analysers.
Wireshark is free to use open source network protocol analyser that can record network
activity and can provide detailed network and protocol information of the packets captured.
These tools are used by both attackers and network administrators for scanning and
diagnosing the network. While the attacker scans the network for vulnerabilities to conduct
attacks subsequently, the network administrators work to identify the problems and issues
that currently exists in the network. The network administrators, if chooses to, can even set
filters to sort the packets that are listed according to their protocol type. In this way they can
find the packets using the unsecured HTTP protocol, which can be the prime threat of
attackers from the public Internet who are always trying to invade such networks and steal
sensitive data. This tool can even show the network administrators the TCP throughput, TCP
sequence graphs, flow graphs and many other statistical graphs of the current network that be
necessary for analysing the network performance.
to these users but are also being able to strictly monitor their network usage prevent access to
specific network segments and preventing the visitor smartphones from getting infected from
malwares and other security threats of the public Internet (Ori 2016). This is highly essential
as the security provided by the zoo authorities instil certain level of confidence among the
visitors and tourists so that they can make use of the zoo network without fears about their
private information getting stolen or their credentials being known to the attack when
conducting digital payments and transactions.
Network Monitoring
Among the most useful network monitoring tools that the authorities of the Edinburgh Zoo
can use to maintain or diagnose the services of the zoo network can be protocol analysers.
Wireshark is free to use open source network protocol analyser that can record network
activity and can provide detailed network and protocol information of the packets captured.
These tools are used by both attackers and network administrators for scanning and
diagnosing the network. While the attacker scans the network for vulnerabilities to conduct
attacks subsequently, the network administrators work to identify the problems and issues
that currently exists in the network. The network administrators, if chooses to, can even set
filters to sort the packets that are listed according to their protocol type. In this way they can
find the packets using the unsecured HTTP protocol, which can be the prime threat of
attackers from the public Internet who are always trying to invade such networks and steal
sensitive data. This tool can even show the network administrators the TCP throughput, TCP
sequence graphs, flow graphs and many other statistical graphs of the current network that be
necessary for analysing the network performance.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
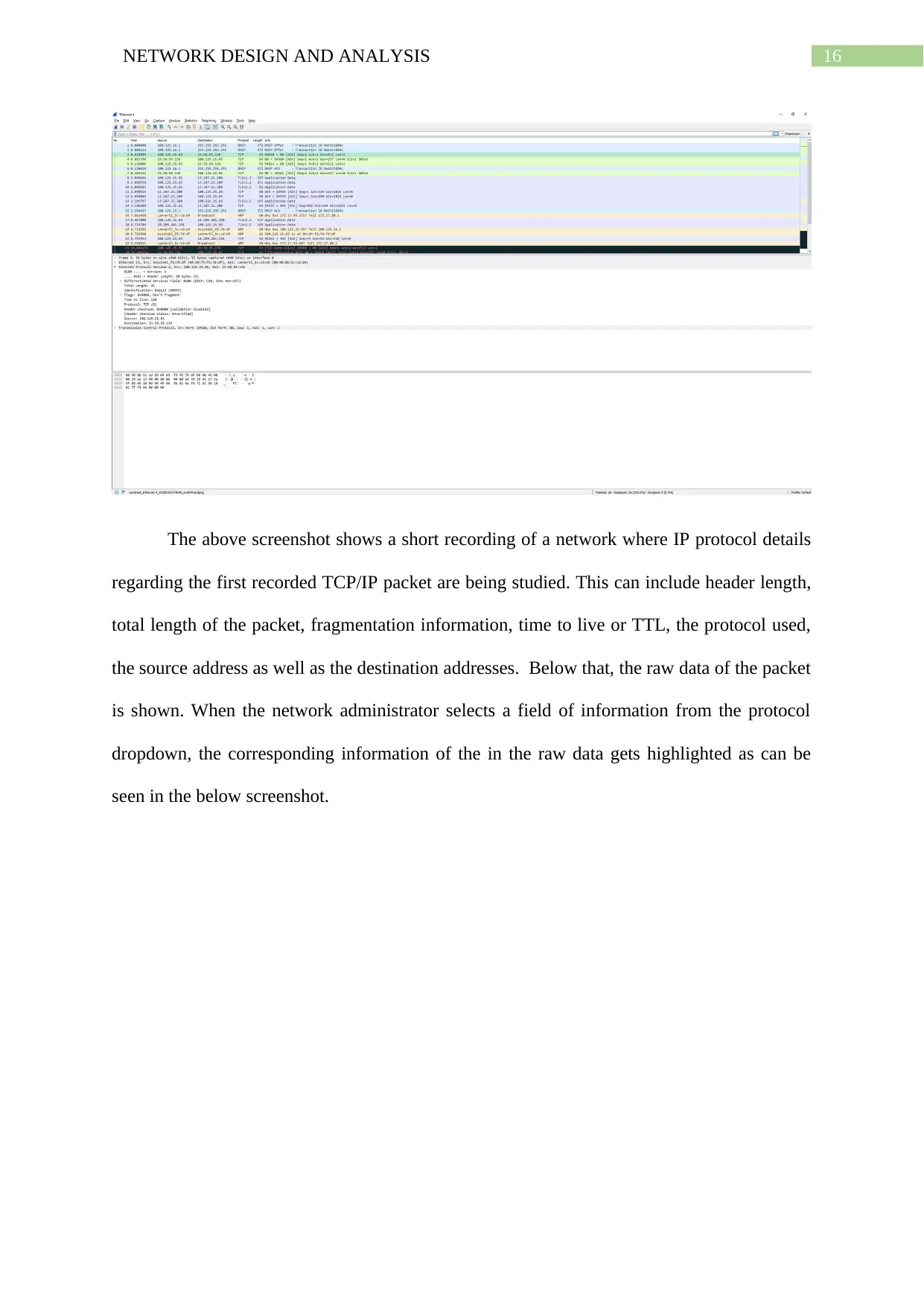
16NETWORK DESIGN AND ANALYSIS
The above screenshot shows a short recording of a network where IP protocol details
regarding the first recorded TCP/IP packet are being studied. This can include header length,
total length of the packet, fragmentation information, time to live or TTL, the protocol used,
the source address as well as the destination addresses. Below that, the raw data of the packet
is shown. When the network administrator selects a field of information from the protocol
dropdown, the corresponding information of the in the raw data gets highlighted as can be
seen in the below screenshot.
The above screenshot shows a short recording of a network where IP protocol details
regarding the first recorded TCP/IP packet are being studied. This can include header length,
total length of the packet, fragmentation information, time to live or TTL, the protocol used,
the source address as well as the destination addresses. Below that, the raw data of the packet
is shown. When the network administrator selects a field of information from the protocol
dropdown, the corresponding information of the in the raw data gets highlighted as can be
seen in the below screenshot.
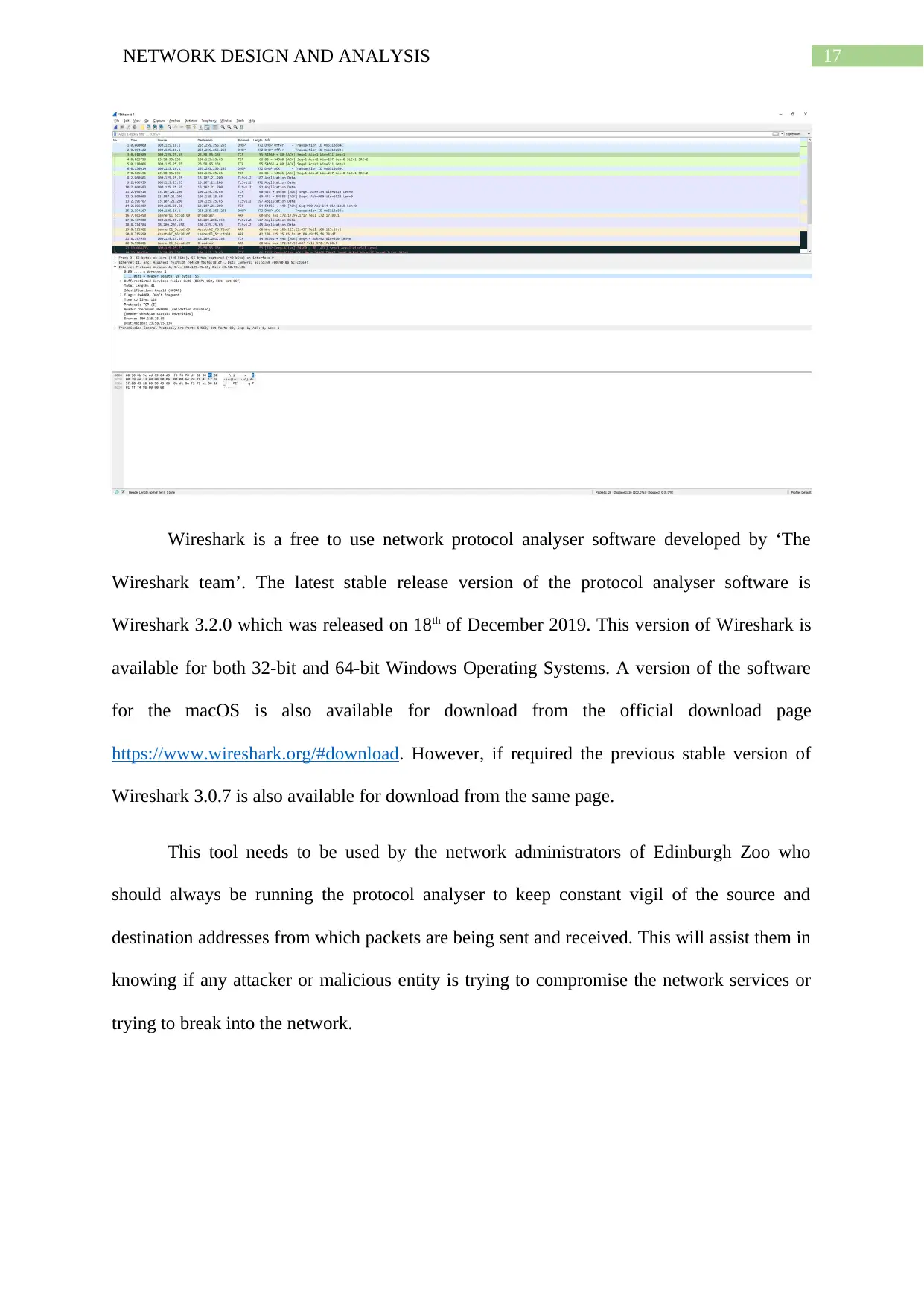
17NETWORK DESIGN AND ANALYSIS
Wireshark is a free to use network protocol analyser software developed by ‘The
Wireshark team’. The latest stable release version of the protocol analyser software is
Wireshark 3.2.0 which was released on 18th of December 2019. This version of Wireshark is
available for both 32-bit and 64-bit Windows Operating Systems. A version of the software
for the macOS is also available for download from the official download page
https://www.wireshark.org/#download. However, if required the previous stable version of
Wireshark 3.0.7 is also available for download from the same page.
This tool needs to be used by the network administrators of Edinburgh Zoo who
should always be running the protocol analyser to keep constant vigil of the source and
destination addresses from which packets are being sent and received. This will assist them in
knowing if any attacker or malicious entity is trying to compromise the network services or
trying to break into the network.
Wireshark is a free to use network protocol analyser software developed by ‘The
Wireshark team’. The latest stable release version of the protocol analyser software is
Wireshark 3.2.0 which was released on 18th of December 2019. This version of Wireshark is
available for both 32-bit and 64-bit Windows Operating Systems. A version of the software
for the macOS is also available for download from the official download page
https://www.wireshark.org/#download. However, if required the previous stable version of
Wireshark 3.0.7 is also available for download from the same page.
This tool needs to be used by the network administrators of Edinburgh Zoo who
should always be running the protocol analyser to keep constant vigil of the source and
destination addresses from which packets are being sent and received. This will assist them in
knowing if any attacker or malicious entity is trying to compromise the network services or
trying to break into the network.

18NETWORK DESIGN AND ANALYSIS
Network Security
The LAN network created for the Edinburgh Zoo makes extensive use of wireless
network and is directly obtaining Internet access from the ISP through the main router. As a
result, the three possible threats to the network can be the following:
Man-In-The Middle (MITM) Attack: In this kind of information security attack, attackers
attempt to secretly relay or more often modify the communication that takes place among two
users who think they are only communicating directly with one another. An example of
MITM attacks can be active eavesdropping.
Advanced Persistent Threat (APT): Advanced Persistent Threats or APT refers to a broad
category of network attacks where an intruder or a whole group of them achieves in
establishing illegal but long-lasting presence on the network.
Social Engineering Attack: Social Engineering refers to the wide range of phishing attacks
performed by malicious actors via interactions with the network user. The attackers achieve
in tricking users by making them open click bait emails making them opening links to
infected web pages.
The internal LAN network of the Edinburgh Zoo needs to be kept secured from all the
above information security threats. This can be ensured by both hardware and software level
security software applications.
When it comes to security solutions the first and foremost are antivirus and firewall
security applications for business class use cases (Blackthorne et al. 2016). The Symantec
Endpoint Protection is a comprehensive security solution that combines industry leading
firewall and antivirus solutions in a complete package that secures every end point of a
business network. O
Network Security
The LAN network created for the Edinburgh Zoo makes extensive use of wireless
network and is directly obtaining Internet access from the ISP through the main router. As a
result, the three possible threats to the network can be the following:
Man-In-The Middle (MITM) Attack: In this kind of information security attack, attackers
attempt to secretly relay or more often modify the communication that takes place among two
users who think they are only communicating directly with one another. An example of
MITM attacks can be active eavesdropping.
Advanced Persistent Threat (APT): Advanced Persistent Threats or APT refers to a broad
category of network attacks where an intruder or a whole group of them achieves in
establishing illegal but long-lasting presence on the network.
Social Engineering Attack: Social Engineering refers to the wide range of phishing attacks
performed by malicious actors via interactions with the network user. The attackers achieve
in tricking users by making them open click bait emails making them opening links to
infected web pages.
The internal LAN network of the Edinburgh Zoo needs to be kept secured from all the
above information security threats. This can be ensured by both hardware and software level
security software applications.
When it comes to security solutions the first and foremost are antivirus and firewall
security applications for business class use cases (Blackthorne et al. 2016). The Symantec
Endpoint Protection is a comprehensive security solution that combines industry leading
firewall and antivirus solutions in a complete package that secures every end point of a
business network. O
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19NETWORK DESIGN AND ANALYSIS
Apart from that the zoo authorities should ensure that their web portal that is being
hosted in servers or workstations have acquired SSL certifications from trusted providers who
provide encryption services. This will ensure all the credentials entered by the visitors in the
login pages or sensitive information entered in other forms to remain completely hidden from
the prying eyes of the attacker.
When it comes to hardware level security, both the main router the zoo network and
the wireless routers support IPsec VPN services (Hakiri et al. 2017). Hence, all the
connections to and from these routing devises can be managed through these IPsec VPN
tunnels. IPsec VPNs are secure network protocol suites that are used for authenticating and
encrypting data packets for providing secure communications (Bensalah, El Kamoun and
Bahnasse 2017). Add to this the Cisco wireless range extenders support 128-bit hardware
encryption and offers Wi-Fi Protected Access 2 (WPA2) pass key based data protection. As a
result, it is also easy for the Edinburgh Zoo to keep the wireless network coverage throughout
the zoo tightly secured.
In addition, the network of Edinburgh Zoo is highly segmented by means of VLANs.
Therefore, on the off chance that an attacker breaks into the network or suppose a part of the
network gets infected by malwares, worms or virus, the network administrators can isolate
the network attack to the specific network segment immediately after detection. Next, they
can reset the network activities of the affected segment by reconfiguring the subnet with
backup data and diagnostic information. In addition to this, VLANs can help protect the
private information of the tourists accommodated in the adjoining hotel.
Apart from that the zoo authorities should ensure that their web portal that is being
hosted in servers or workstations have acquired SSL certifications from trusted providers who
provide encryption services. This will ensure all the credentials entered by the visitors in the
login pages or sensitive information entered in other forms to remain completely hidden from
the prying eyes of the attacker.
When it comes to hardware level security, both the main router the zoo network and
the wireless routers support IPsec VPN services (Hakiri et al. 2017). Hence, all the
connections to and from these routing devises can be managed through these IPsec VPN
tunnels. IPsec VPNs are secure network protocol suites that are used for authenticating and
encrypting data packets for providing secure communications (Bensalah, El Kamoun and
Bahnasse 2017). Add to this the Cisco wireless range extenders support 128-bit hardware
encryption and offers Wi-Fi Protected Access 2 (WPA2) pass key based data protection. As a
result, it is also easy for the Edinburgh Zoo to keep the wireless network coverage throughout
the zoo tightly secured.
In addition, the network of Edinburgh Zoo is highly segmented by means of VLANs.
Therefore, on the off chance that an attacker breaks into the network or suppose a part of the
network gets infected by malwares, worms or virus, the network administrators can isolate
the network attack to the specific network segment immediately after detection. Next, they
can reset the network activities of the affected segment by reconfiguring the subnet with
backup data and diagnostic information. In addition to this, VLANs can help protect the
private information of the tourists accommodated in the adjoining hotel.

20NETWORK DESIGN AND ANALYSIS
Conclusion
In conclusion, the report succeeds in showing the relevance of network infrastructure
for public places like a zoo in today’s times. This report is found to study the network
requirements of Edinburgh Zoo and suggest a network design accordingly. The report is
observed to presenting how the network for the Edinburgh Zoo gets acquired and also lists
the advantages which the zoo can enjoy from such a network. Next the networking model
based on which the network of the Edinburgh Zoo is to be designed gets shown and
discussed. After that report presents the logical network diagram for the Edinburgh Zoo and
also provides the justification. Thereafter the cabling requirements of the zoo needs is to be
specified for which the physical network diagram gets drawn. Following this the required
costs of serial and Ethernet cabling for the respective measurements are given. Then the
specific network infrastructure devices which are getting used in the network of the zoo are
discussed. After this, examples of two products for each device is suggested while also
justifying their use. Next the IP addressing for the network is given before discussing about
the foreground and background services of the network. Following this the network
monitoring with appropriate tool is suggested. After listing the three security threats to the
network and the features of the network that can help secure itself from these threats are
discussed.
Conclusion
In conclusion, the report succeeds in showing the relevance of network infrastructure
for public places like a zoo in today’s times. This report is found to study the network
requirements of Edinburgh Zoo and suggest a network design accordingly. The report is
observed to presenting how the network for the Edinburgh Zoo gets acquired and also lists
the advantages which the zoo can enjoy from such a network. Next the networking model
based on which the network of the Edinburgh Zoo is to be designed gets shown and
discussed. After that report presents the logical network diagram for the Edinburgh Zoo and
also provides the justification. Thereafter the cabling requirements of the zoo needs is to be
specified for which the physical network diagram gets drawn. Following this the required
costs of serial and Ethernet cabling for the respective measurements are given. Then the
specific network infrastructure devices which are getting used in the network of the zoo are
discussed. After this, examples of two products for each device is suggested while also
justifying their use. Next the IP addressing for the network is given before discussing about
the foreground and background services of the network. Following this the network
monitoring with appropriate tool is suggested. After listing the three security threats to the
network and the features of the network that can help secure itself from these threats are
discussed.

21NETWORK DESIGN AND ANALYSIS
References
Aweya, J., 2018. Introduction To Switch/Router Architectures.
Bensalah, F., El Kamoun, N. and Bahnasse, A., 2017. Evaluation of tunnel layer impact on
VOIP performances (IP-MPLS-MPLS VPN-MPLS VPN IPsec). International Journal of
Computer Science and Network Security (IJCSNS), 17(3), p.87.
Blackthorne, J., Bulazel, A., Fasano, A., Biernat, P. and Yener, B., 2016. AVLeak:
fingerprinting antivirus emulators through black-box testing. In 10th {USENIX} Workshop on
Offensive Technologies ({WOOT} 16).
D’Andreagiovanni, F. and Gleixner, A.M., 2016, May. Towards an accurate solution of
wireless network design problems. In International Symposium on Combinatorial
Optimization (pp. 135-147). Springer, Cham.
Farooq-I-Azam, M., Ni, Q. and Ansari, E.A., 2016. Intelligent energy efficient localization
using variable range beacons in industrial wireless sensor networks. IEEE Transactions on
Industrial Informatics, 12(6), pp.2206-2216.
Fortuna, C., De Poorter, E., Škraba, P. and Moerman, I., 2016. Data driven wireless network
design: a multi-level modeling approach. Wireless Personal Communications, 88(1), pp.63-
77.
Gjerseth, A.Z., 2017. IoT and Modbus protocol development (Master's thesis, Høgskolen i
Sørøst-Norge)
Hakiri, A., Sellami, B., Patil, P., Berthou, P. and Gokhale, A., 2017, October. Managing
wireless fog networks using software-defined networking. In 2017 IEEE/ACS 14th
International Conference on Computer Systems and Applications (AICCSA) (pp. 1149-1156).
IEEE.
References
Aweya, J., 2018. Introduction To Switch/Router Architectures.
Bensalah, F., El Kamoun, N. and Bahnasse, A., 2017. Evaluation of tunnel layer impact on
VOIP performances (IP-MPLS-MPLS VPN-MPLS VPN IPsec). International Journal of
Computer Science and Network Security (IJCSNS), 17(3), p.87.
Blackthorne, J., Bulazel, A., Fasano, A., Biernat, P. and Yener, B., 2016. AVLeak:
fingerprinting antivirus emulators through black-box testing. In 10th {USENIX} Workshop on
Offensive Technologies ({WOOT} 16).
D’Andreagiovanni, F. and Gleixner, A.M., 2016, May. Towards an accurate solution of
wireless network design problems. In International Symposium on Combinatorial
Optimization (pp. 135-147). Springer, Cham.
Farooq-I-Azam, M., Ni, Q. and Ansari, E.A., 2016. Intelligent energy efficient localization
using variable range beacons in industrial wireless sensor networks. IEEE Transactions on
Industrial Informatics, 12(6), pp.2206-2216.
Fortuna, C., De Poorter, E., Škraba, P. and Moerman, I., 2016. Data driven wireless network
design: a multi-level modeling approach. Wireless Personal Communications, 88(1), pp.63-
77.
Gjerseth, A.Z., 2017. IoT and Modbus protocol development (Master's thesis, Høgskolen i
Sørøst-Norge)
Hakiri, A., Sellami, B., Patil, P., Berthou, P. and Gokhale, A., 2017, October. Managing
wireless fog networks using software-defined networking. In 2017 IEEE/ACS 14th
International Conference on Computer Systems and Applications (AICCSA) (pp. 1149-1156).
IEEE.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22NETWORK DESIGN AND ANALYSIS
Isaac, S., 2016. Comparative Analysis of IPV4 and IPV6. International Journal of Computer
Science and Information Technologies, 7(2), pp.675-678.
Kabashkin, I. and Kundler, J., 2017. Reliability of sensor nodes in wireless sensor networks
of cyber physical systems. Procedia Computer Science, 104, pp.380-384.
Kocz, J., Ravi, V., Catha, M., D'Addario, L., Hallinan, G., Hobbs, R., Kulkarni, S., Shi, J.,
Vedantham, H., Weinreb, S. and Woody, D., 2019. DSA-10: A Prototype Array for
Localizing Fast Radio Bursts. arXiv preprint arXiv:1906.08699.
Lane, N., 2018. Development and integration of Honeywell’s One-Wireless network
(Doctoral dissertation, Murdoch University).
Lima, F.H., Vieira, L.F., Vieira, M.A., Vieira, A.B. and Nacif, J.A.M., 2019. Water ping:
ICMP for the internet of underwater things. Computer Networks, 152, pp.54-63.
Lin, C.C., Chen, T.H. and Chin, H.H., 2016. Adaptive router node placement with gateway
positions and QoS constraints in dynamic wireless mesh networks. Journal of Network and
Computer Applications, 74, pp.149-164.
Lin, C.C., Tseng, P.T., Wu, T.Y. and Deng, D.J., 2016. Social-aware dynamic router node
placement in wireless mesh networks. Wireless Networks, 22(4), pp.1235-1250.
Ma, X. and Yu, T., 2016. An algorithm of physical network topology discovery in multi-
VLANs. Telkomnika, 14(3A), p.375.
Mondal, H.K., Gade, S.H., Kishore, R., Kaushik, S. and Deb, S., 2016, March. Power
efficient router architecture for wireless Network-on-Chip. In 2016 17th International
Symposium on Quality Electronic Design (ISQED) (pp. 227-233). IEEE.
Isaac, S., 2016. Comparative Analysis of IPV4 and IPV6. International Journal of Computer
Science and Information Technologies, 7(2), pp.675-678.
Kabashkin, I. and Kundler, J., 2017. Reliability of sensor nodes in wireless sensor networks
of cyber physical systems. Procedia Computer Science, 104, pp.380-384.
Kocz, J., Ravi, V., Catha, M., D'Addario, L., Hallinan, G., Hobbs, R., Kulkarni, S., Shi, J.,
Vedantham, H., Weinreb, S. and Woody, D., 2019. DSA-10: A Prototype Array for
Localizing Fast Radio Bursts. arXiv preprint arXiv:1906.08699.
Lane, N., 2018. Development and integration of Honeywell’s One-Wireless network
(Doctoral dissertation, Murdoch University).
Lima, F.H., Vieira, L.F., Vieira, M.A., Vieira, A.B. and Nacif, J.A.M., 2019. Water ping:
ICMP for the internet of underwater things. Computer Networks, 152, pp.54-63.
Lin, C.C., Chen, T.H. and Chin, H.H., 2016. Adaptive router node placement with gateway
positions and QoS constraints in dynamic wireless mesh networks. Journal of Network and
Computer Applications, 74, pp.149-164.
Lin, C.C., Tseng, P.T., Wu, T.Y. and Deng, D.J., 2016. Social-aware dynamic router node
placement in wireless mesh networks. Wireless Networks, 22(4), pp.1235-1250.
Ma, X. and Yu, T., 2016. An algorithm of physical network topology discovery in multi-
VLANs. Telkomnika, 14(3A), p.375.
Mondal, H.K., Gade, S.H., Kishore, R., Kaushik, S. and Deb, S., 2016, March. Power
efficient router architecture for wireless Network-on-Chip. In 2016 17th International
Symposium on Quality Electronic Design (ISQED) (pp. 227-233). IEEE.

23NETWORK DESIGN AND ANALYSIS
Namazi, A. and Lin, C., 2019. NRES: Non-blocking Ruggedized Ethernet Switch for
Airborne Applications (No. 412TW-PA-19264). INTELLIGENT AUTOMATION INC
ROCKVILLE MD ROCKVILLE United States.
Ndlovu, L., Kogeda, O.P. and Lall, M., 2018. Enhanced service discovery model for wireless
mesh networks. Journal of Advanced Computational Intelligence and Intelligent Informatics,
22(1), pp.44-53.
Ori, A., 2016. Firewall or smooth horizon?. General Relativity and Gravitation, 48(1), p.9.
Park, P., Ergen, S.C., Fischione, C., Lu, C. and Johansson, K.H., 2017. Wireless network
design for control systems: A survey. IEEE Communications Surveys & Tutorials, 20(2),
pp.978-1013.
Pratama, A.P., Sugesti, E.S. and Mayasari, R., 2017. Analisis Packet Loss Pada Wlan 802.11
n Qos Mode Basic Service Set Berbasis. eProceedings of Engineering, 4(3).
Swapna, A.I., Rosa, R.V., Rothenberg, C.E., Sakellariou, I., Mamatas, L. and Papadimitriou,
P., 2019, September. Towards A Marketplace for Multi-domain Cloud Network Slicing: Use
Cases. In 2019 ACM/IEEE Symposium on Architectures for Networking and
Communications Systems (ANCS) (pp. 1-4). IEEE.
Taha, J., Salehi, V. and Abraham, F., 2018, October. Development of a Low Powered
Wireless IoT Sensor Network based on MBSE. In 2018 IEEE International Systems
Engineering Symposium (ISSE) (pp. 1-8). IEEE.
Wijesundara, M., Tapparello, C., Gamage, A., Gokulan, Y., Gittelson, L., Howard, T. and
Heinzelman, W., 2016, December. Design of a kinetic energy harvester for elephant mounted
wireless sensor nodes of jumbonet. In 2016 IEEE Global Communications Conference
(GLOBECOM) (pp. 1-7). IEEE.
Namazi, A. and Lin, C., 2019. NRES: Non-blocking Ruggedized Ethernet Switch for
Airborne Applications (No. 412TW-PA-19264). INTELLIGENT AUTOMATION INC
ROCKVILLE MD ROCKVILLE United States.
Ndlovu, L., Kogeda, O.P. and Lall, M., 2018. Enhanced service discovery model for wireless
mesh networks. Journal of Advanced Computational Intelligence and Intelligent Informatics,
22(1), pp.44-53.
Ori, A., 2016. Firewall or smooth horizon?. General Relativity and Gravitation, 48(1), p.9.
Park, P., Ergen, S.C., Fischione, C., Lu, C. and Johansson, K.H., 2017. Wireless network
design for control systems: A survey. IEEE Communications Surveys & Tutorials, 20(2),
pp.978-1013.
Pratama, A.P., Sugesti, E.S. and Mayasari, R., 2017. Analisis Packet Loss Pada Wlan 802.11
n Qos Mode Basic Service Set Berbasis. eProceedings of Engineering, 4(3).
Swapna, A.I., Rosa, R.V., Rothenberg, C.E., Sakellariou, I., Mamatas, L. and Papadimitriou,
P., 2019, September. Towards A Marketplace for Multi-domain Cloud Network Slicing: Use
Cases. In 2019 ACM/IEEE Symposium on Architectures for Networking and
Communications Systems (ANCS) (pp. 1-4). IEEE.
Taha, J., Salehi, V. and Abraham, F., 2018, October. Development of a Low Powered
Wireless IoT Sensor Network based on MBSE. In 2018 IEEE International Systems
Engineering Symposium (ISSE) (pp. 1-8). IEEE.
Wijesundara, M., Tapparello, C., Gamage, A., Gokulan, Y., Gittelson, L., Howard, T. and
Heinzelman, W., 2016, December. Design of a kinetic energy harvester for elephant mounted
wireless sensor nodes of jumbonet. In 2016 IEEE Global Communications Conference
(GLOBECOM) (pp. 1-7). IEEE.

24NETWORK DESIGN AND ANALYSIS
Wu, Q. and Zhang, R., 2018, December. Intelligent reflecting surface enhanced wireless
network: Joint active and passive beamforming design. In 2018 IEEE Global
Communications Conference (GLOBECOM) (pp. 1-6). IEEE.
Yang, A.M., Yang, X.L., Chang, J.C., Bai, B., Kong, F.B. and Ran, Q.B., 2018. Research on
a fusion scheme of cellular network and wireless sensor for cyber physical social systems.
Ieee Access, 6, pp.18786-18794.
Yang, Y., Li, Q. and Qiu, M., 2016. Broadband nanophotonic wireless links and networks
using on-chip integrated plasmonic antennas. Scientific reports, 6, p.19490.
Yao, Y., Sheng, B. and Mi, N., 2016. A new packet scheduling algorithm for access points in
crowded WLANs. Ad Hoc Networks, 36, pp.100-110.
Zhao, N., Yu, F.R., Wang, H.M., Duong, T.Q. and Chang, Z., 2018. IEEE Access Special
Section Editorial: Exploiting the Benefits of Interference in Wireless Networks: Energy
Harvesting and Security. IEEE Access, 6, pp.30612-30616.
Wu, Q. and Zhang, R., 2018, December. Intelligent reflecting surface enhanced wireless
network: Joint active and passive beamforming design. In 2018 IEEE Global
Communications Conference (GLOBECOM) (pp. 1-6). IEEE.
Yang, A.M., Yang, X.L., Chang, J.C., Bai, B., Kong, F.B. and Ran, Q.B., 2018. Research on
a fusion scheme of cellular network and wireless sensor for cyber physical social systems.
Ieee Access, 6, pp.18786-18794.
Yang, Y., Li, Q. and Qiu, M., 2016. Broadband nanophotonic wireless links and networks
using on-chip integrated plasmonic antennas. Scientific reports, 6, p.19490.
Yao, Y., Sheng, B. and Mi, N., 2016. A new packet scheduling algorithm for access points in
crowded WLANs. Ad Hoc Networks, 36, pp.100-110.
Zhao, N., Yu, F.R., Wang, H.M., Duong, T.Q. and Chang, Z., 2018. IEEE Access Special
Section Editorial: Exploiting the Benefits of Interference in Wireless Networks: Energy
Harvesting and Security. IEEE Access, 6, pp.30612-30616.
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





