Network Design Document Assignment
VerifiedAdded on 2021/06/17
|28
|7511
|217
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Network Design Document
Project Client Organisation:
Contact:
System Name <<To be created by team and client>>
Date of Design
Document
<<Date of this version>>
Document Status Draft / Approved <<delete one>>
Document Reference <<FileName.doc>>
Version Number Version 1<<update as necessary, in whole numbers>>
Prepared by <<Technical Writer>>
Team Members << Names of other team members>>
7630317365527025157.docx 1 of 31
Project Client Organisation:
Contact:
System Name <<To be created by team and client>>
Date of Design
Document
<<Date of this version>>
Document Status Draft / Approved <<delete one>>
Document Reference <<FileName.doc>>
Version Number Version 1<<update as necessary, in whole numbers>>
Prepared by <<Technical Writer>>
Team Members << Names of other team members>>
7630317365527025157.docx 1 of 31
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

7630317365527025157.docx 2 of 31
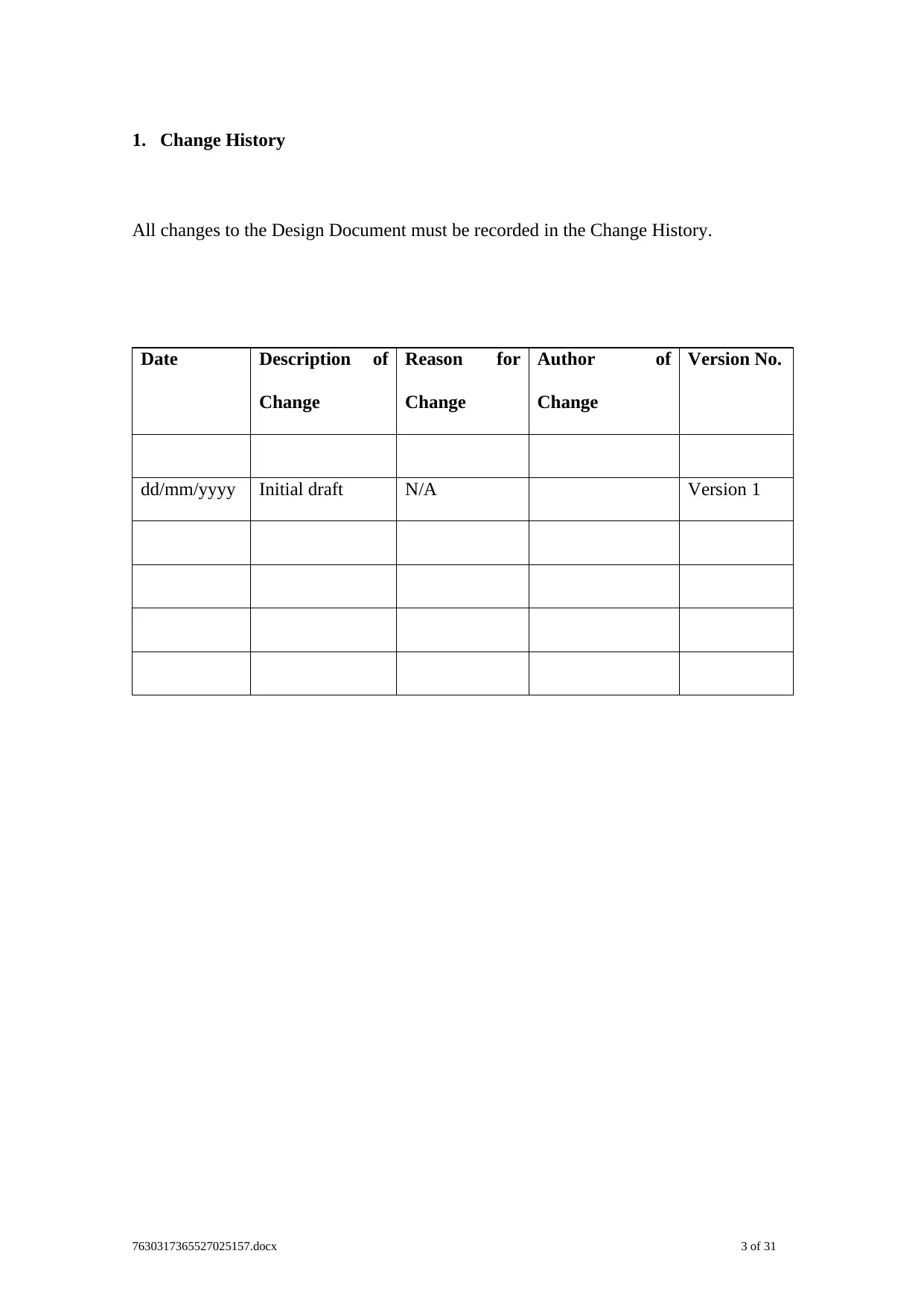
1. Change History
All changes to the Design Document must be recorded in the Change History.
Date Description of
Change
Reason for
Change
Author of
Change
Version No.
dd/mm/yyyy Initial draft N/A Version 1
7630317365527025157.docx 3 of 31
All changes to the Design Document must be recorded in the Change History.
Date Description of
Change
Reason for
Change
Author of
Change
Version No.
dd/mm/yyyy Initial draft N/A Version 1
7630317365527025157.docx 3 of 31

2. Table of Contents
1. CHANGE HISTORY..............................................................................................................................3
2. TABLE OF CONTENTS........................................................................................................................4
3. EXECUTIVE SUMMARY.....................................................................................................................5
4. PROJECT GOALS..................................................................................................................................6
5. LOGICAL DESIGN................................................................................................................................7
5.1. LOGICAL NETWORK DIAGRAM.........................................................................................................7
5.2. ADDRESSING AND NAMING STRUCTURE..........................................................................................7
5.3. ROUTING AND SWITCHING PROTOCOLS...........................................................................................8
5.4. SECURITY........................................................................................................................................11
5.5. VIRTUAL LANS..............................................................................................................................12
5.6. WIRELESS NETWORKS....................................................................................................................12
5.7. QOS DESIGN...................................................................................................................................13
5.8. NETWORK MANAGEMENT..............................................................................................................14
6. PHYSICAL DESIGN............................................................................................................................15
6.1. NETWORK TOPOLOGY.....................................................................................................................15
6.2. LAN TECHNOLOGIES......................................................................................................................16
6.3. WAN TECHNOLOGIES.....................................................................................................................17
6.4. PHYSICAL NETWORK DIAGRAM.....................................................................................................18
6.5. MINIMAL SERVER AND PC REQUIREMENTS....................................................................................19
6.6. WIRELESS TECHNOLOGIES..............................................................................................................20
7. TEST PLAN...........................................................................................................................................22
7.1. OVERALL PROJECT SCOPE AND OBJECTIVE...................................................................................22
7.2. TEST OBJECTIVE AND SUCCESS CRITERIA.......................................................................................22
7.3. TEST RESOURCE REQUIRED.............................................................................................................22
7.4. TEST SCHEDULE..............................................................................................................................22
7630317365527025157.docx 4 of 31
1. CHANGE HISTORY..............................................................................................................................3
2. TABLE OF CONTENTS........................................................................................................................4
3. EXECUTIVE SUMMARY.....................................................................................................................5
4. PROJECT GOALS..................................................................................................................................6
5. LOGICAL DESIGN................................................................................................................................7
5.1. LOGICAL NETWORK DIAGRAM.........................................................................................................7
5.2. ADDRESSING AND NAMING STRUCTURE..........................................................................................7
5.3. ROUTING AND SWITCHING PROTOCOLS...........................................................................................8
5.4. SECURITY........................................................................................................................................11
5.5. VIRTUAL LANS..............................................................................................................................12
5.6. WIRELESS NETWORKS....................................................................................................................12
5.7. QOS DESIGN...................................................................................................................................13
5.8. NETWORK MANAGEMENT..............................................................................................................14
6. PHYSICAL DESIGN............................................................................................................................15
6.1. NETWORK TOPOLOGY.....................................................................................................................15
6.2. LAN TECHNOLOGIES......................................................................................................................16
6.3. WAN TECHNOLOGIES.....................................................................................................................17
6.4. PHYSICAL NETWORK DIAGRAM.....................................................................................................18
6.5. MINIMAL SERVER AND PC REQUIREMENTS....................................................................................19
6.6. WIRELESS TECHNOLOGIES..............................................................................................................20
7. TEST PLAN...........................................................................................................................................22
7.1. OVERALL PROJECT SCOPE AND OBJECTIVE...................................................................................22
7.2. TEST OBJECTIVE AND SUCCESS CRITERIA.......................................................................................22
7.3. TEST RESOURCE REQUIRED.............................................................................................................22
7.4. TEST SCHEDULE..............................................................................................................................22
7630317365527025157.docx 4 of 31
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

7.5. DEVELOPMENT OF THE TEST CASES................................................................................................23
8. REFERENCES.......................................................................................................................................24
7630317365527025157.docx 5 of 31
8. REFERENCES.......................................................................................................................................24
7630317365527025157.docx 5 of 31

3. Executive Summary
The report is prepared for the development of a network solution for the Orange site
and connect it with the other branches with the establishment of a VPN connection
between the other sites. The network is designed with the preparation of an IP addressing
plan and documented in the report for the management of the current network
infrastructure of the organization. The report is prepared by documenting the major goals
of the organization and the scope for the further improvement of the network design. A
logical design of the network is prepared and attached with the report for providing a brief
overview of the network design. A proper addressing and naming scheme is followed for
the development of the network and assigning an IP address to all the interface of the
network device installed in the network. The IP addressing scheme is used for
configuration of the servers with DHCP such that it can be used for automatically assign
the IP address to nodes connected in network. The routing and the switching protocol used
for the configuration of the network are analysed and the routers are configured with the
routing protocol such that it can be used for communicating with the hosts connected with
the interface of the other branches of the organization. The security measures that should
be implemented for the development of the network solution is analysed for securing the
network. The network management strategy that should be followed for management of
network resources are also documented in report. The physical network design is also
attached with the report with the details of the network topology selected for the
development of the local area network and the wide area network of the organization. A
physical network diagram is attached with the report for providing an overview of the
network and the minimum server and the Pc requirement that should be used for network
are also given in the report. It also defines the wireless technologies that can be
7630317365527025157.docx 6 of 31
The report is prepared for the development of a network solution for the Orange site
and connect it with the other branches with the establishment of a VPN connection
between the other sites. The network is designed with the preparation of an IP addressing
plan and documented in the report for the management of the current network
infrastructure of the organization. The report is prepared by documenting the major goals
of the organization and the scope for the further improvement of the network design. A
logical design of the network is prepared and attached with the report for providing a brief
overview of the network design. A proper addressing and naming scheme is followed for
the development of the network and assigning an IP address to all the interface of the
network device installed in the network. The IP addressing scheme is used for
configuration of the servers with DHCP such that it can be used for automatically assign
the IP address to nodes connected in network. The routing and the switching protocol used
for the configuration of the network are analysed and the routers are configured with the
routing protocol such that it can be used for communicating with the hosts connected with
the interface of the other branches of the organization. The security measures that should
be implemented for the development of the network solution is analysed for securing the
network. The network management strategy that should be followed for management of
network resources are also documented in report. The physical network design is also
attached with the report with the details of the network topology selected for the
development of the local area network and the wide area network of the organization. A
physical network diagram is attached with the report for providing an overview of the
network and the minimum server and the Pc requirement that should be used for network
are also given in the report. It also defines the wireless technologies that can be
7630317365527025157.docx 6 of 31

implemented for enabling the users to connect their wireless devices with the network are
discussed.
4. Project Goals
The main goals identified for the development of the network framework for the
organization is listed below:
To configure the servers with the active directory, DNS, DHCP, File, Firewall,
Backups, MYSQL and Hyper V Cluster.
To create a network design for the LAN and the WAN and create a site to site VPN
link between the sites for enabling secure communication between the sites
To connect the hosts with the network and build the Pc following the minimum
configuration
To configure the routers and the servers with a proper IP addressing plan enabling
routing for allocate address for each of the VLAN used for breaking the network
into different subnets.
To create different VLAN in the switch and provide a proper name to the VLAN
for easy management of the network and monitor the activity of the users
connected in the network.
To configure the firewall in the windows server for restricting the outside users to
access the core resources of the organizational network and align the business rules
for the development of the firewall policy.
To configure the active directory such that the users can be grouped and privilege
must be provided to them for restricting them to modify the network configuration
To create a backup of the server and add redundancy in the network such that it
can be used for handing disaster recovery
7630317365527025157.docx 7 of 31
discussed.
4. Project Goals
The main goals identified for the development of the network framework for the
organization is listed below:
To configure the servers with the active directory, DNS, DHCP, File, Firewall,
Backups, MYSQL and Hyper V Cluster.
To create a network design for the LAN and the WAN and create a site to site VPN
link between the sites for enabling secure communication between the sites
To connect the hosts with the network and build the Pc following the minimum
configuration
To configure the routers and the servers with a proper IP addressing plan enabling
routing for allocate address for each of the VLAN used for breaking the network
into different subnets.
To create different VLAN in the switch and provide a proper name to the VLAN
for easy management of the network and monitor the activity of the users
connected in the network.
To configure the firewall in the windows server for restricting the outside users to
access the core resources of the organizational network and align the business rules
for the development of the firewall policy.
To configure the active directory such that the users can be grouped and privilege
must be provided to them for restricting them to modify the network configuration
To create a backup of the server and add redundancy in the network such that it
can be used for handing disaster recovery
7630317365527025157.docx 7 of 31
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

To virtualize the servers such it can be migrated to the cloud platform for
increasing the scalability of the network.
5. Logical Design
For the preparation of the logical network diagram the each of the network site is
divided into different subnets and different VLANs are created on the switch for
connecting the site with each other. The devices required for interconnecting the network
with each other are analysed for preparation of the list of hardware component. The
configuration that should be made for enabling remote connection with the network are
analysed for the development of the network. The diagram is properly labelled with the
addressing scheme and documented in the report such that it can be used by the network
development team for configuring the network device according to the network plan.
5.1. Logical Network Diagram
5.2. Addressing and Naming Structure
Subnet - 1
Network Address 10.16.66.0
7630317365527025157.docx 8 of 31
increasing the scalability of the network.
5. Logical Design
For the preparation of the logical network diagram the each of the network site is
divided into different subnets and different VLANs are created on the switch for
connecting the site with each other. The devices required for interconnecting the network
with each other are analysed for preparation of the list of hardware component. The
configuration that should be made for enabling remote connection with the network are
analysed for the development of the network. The diagram is properly labelled with the
addressing scheme and documented in the report such that it can be used by the network
development team for configuring the network device according to the network plan.
5.1. Logical Network Diagram
5.2. Addressing and Naming Structure
Subnet - 1
Network Address 10.16.66.0
7630317365527025157.docx 8 of 31
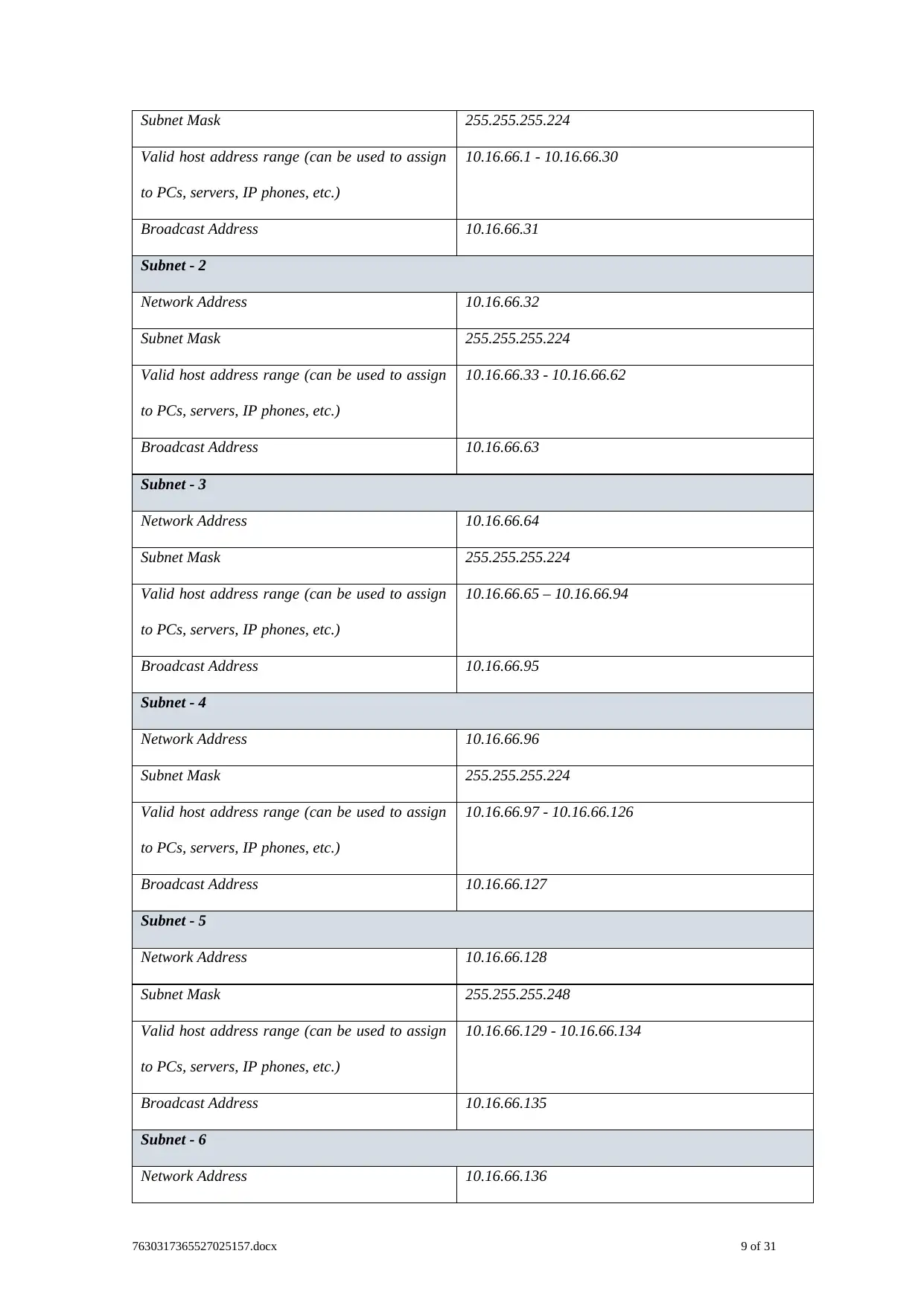
Subnet Mask 255.255.255.224
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.1 - 10.16.66.30
Broadcast Address 10.16.66.31
Subnet - 2
Network Address 10.16.66.32
Subnet Mask 255.255.255.224
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.33 - 10.16.66.62
Broadcast Address 10.16.66.63
Subnet - 3
Network Address 10.16.66.64
Subnet Mask 255.255.255.224
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.65 – 10.16.66.94
Broadcast Address 10.16.66.95
Subnet - 4
Network Address 10.16.66.96
Subnet Mask 255.255.255.224
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.97 - 10.16.66.126
Broadcast Address 10.16.66.127
Subnet - 5
Network Address 10.16.66.128
Subnet Mask 255.255.255.248
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.129 - 10.16.66.134
Broadcast Address 10.16.66.135
Subnet - 6
Network Address 10.16.66.136
7630317365527025157.docx 9 of 31
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.1 - 10.16.66.30
Broadcast Address 10.16.66.31
Subnet - 2
Network Address 10.16.66.32
Subnet Mask 255.255.255.224
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.33 - 10.16.66.62
Broadcast Address 10.16.66.63
Subnet - 3
Network Address 10.16.66.64
Subnet Mask 255.255.255.224
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.65 – 10.16.66.94
Broadcast Address 10.16.66.95
Subnet - 4
Network Address 10.16.66.96
Subnet Mask 255.255.255.224
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.97 - 10.16.66.126
Broadcast Address 10.16.66.127
Subnet - 5
Network Address 10.16.66.128
Subnet Mask 255.255.255.248
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.129 - 10.16.66.134
Broadcast Address 10.16.66.135
Subnet - 6
Network Address 10.16.66.136
7630317365527025157.docx 9 of 31
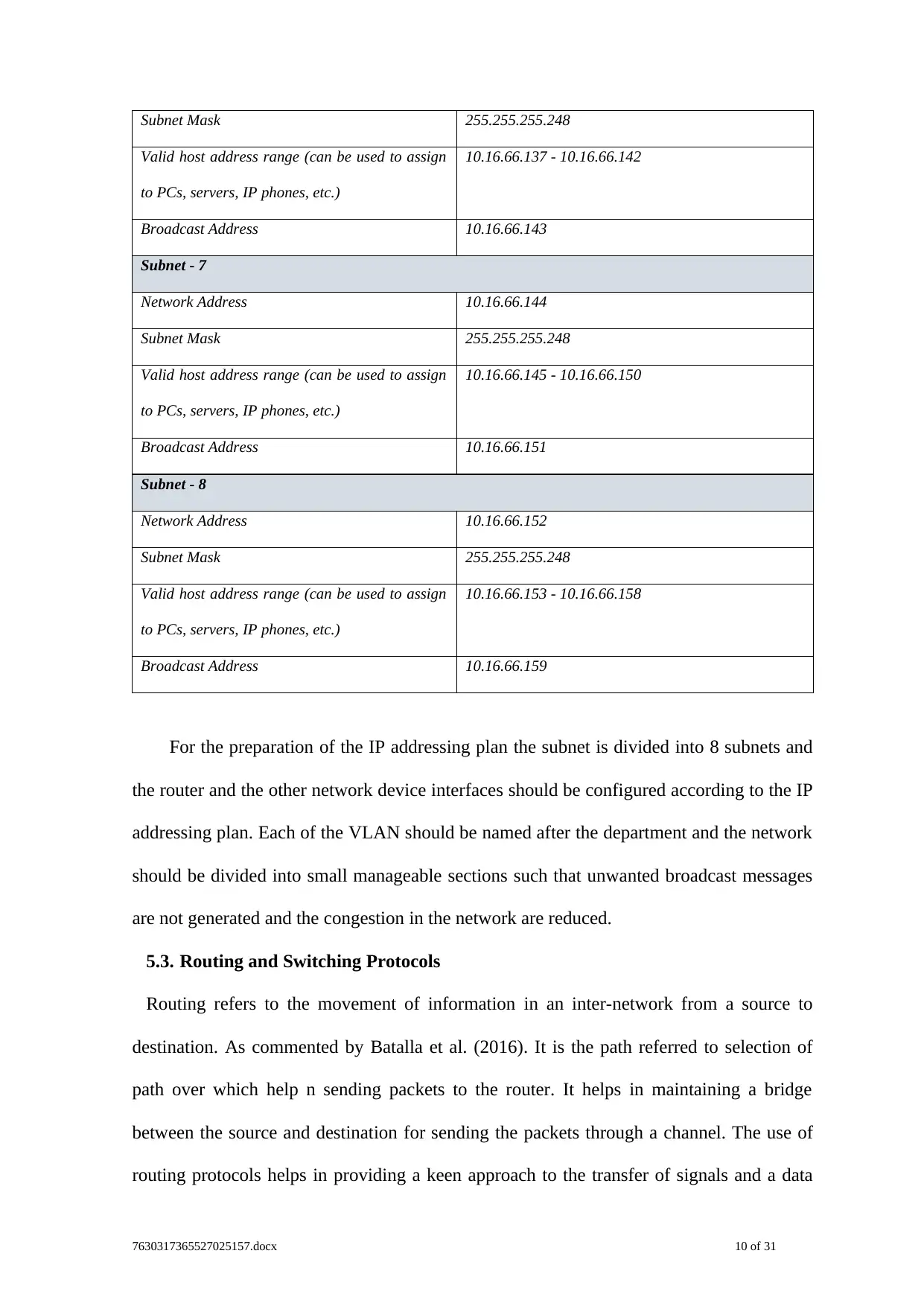
Subnet Mask 255.255.255.248
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.137 - 10.16.66.142
Broadcast Address 10.16.66.143
Subnet - 7
Network Address 10.16.66.144
Subnet Mask 255.255.255.248
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.145 - 10.16.66.150
Broadcast Address 10.16.66.151
Subnet - 8
Network Address 10.16.66.152
Subnet Mask 255.255.255.248
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.153 - 10.16.66.158
Broadcast Address 10.16.66.159
For the preparation of the IP addressing plan the subnet is divided into 8 subnets and
the router and the other network device interfaces should be configured according to the IP
addressing plan. Each of the VLAN should be named after the department and the network
should be divided into small manageable sections such that unwanted broadcast messages
are not generated and the congestion in the network are reduced.
5.3. Routing and Switching Protocols
Routing refers to the movement of information in an inter-network from a source to
destination. As commented by Batalla et al. (2016). It is the path referred to selection of
path over which help n sending packets to the router. It helps in maintaining a bridge
between the source and destination for sending the packets through a channel. The use of
routing protocols helps in providing a keen approach to the transfer of signals and a data
7630317365527025157.docx 10 of 31
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.137 - 10.16.66.142
Broadcast Address 10.16.66.143
Subnet - 7
Network Address 10.16.66.144
Subnet Mask 255.255.255.248
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.145 - 10.16.66.150
Broadcast Address 10.16.66.151
Subnet - 8
Network Address 10.16.66.152
Subnet Mask 255.255.255.248
Valid host address range (can be used to assign
to PCs, servers, IP phones, etc.)
10.16.66.153 - 10.16.66.158
Broadcast Address 10.16.66.159
For the preparation of the IP addressing plan the subnet is divided into 8 subnets and
the router and the other network device interfaces should be configured according to the IP
addressing plan. Each of the VLAN should be named after the department and the network
should be divided into small manageable sections such that unwanted broadcast messages
are not generated and the congestion in the network are reduced.
5.3. Routing and Switching Protocols
Routing refers to the movement of information in an inter-network from a source to
destination. As commented by Batalla et al. (2016). It is the path referred to selection of
path over which help n sending packets to the router. It helps in maintaining a bridge
between the source and destination for sending the packets through a channel. The use of
routing protocols helps in providing a keen approach to the transfer of signals and a data
7630317365527025157.docx 10 of 31
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

packets through the channel between source and destination. The distinction helps in
routing and bridging with different data and information with help of moving information
from source to destination. However, the routing algorithm is a part of network layer
software that is responsible for the transfer of data packets through a channel.
As mentioned by Javed, Afzal & Kim (2018), routing protocols uses metrics for
evaluating the path bandwidth and reliability of the routing algorithm for determining
optimal path to destination. This include the destination information and address. Routing
algorithm helps in filling routing tables with a variety of information. When a switch gets
an appropriate function, it starts checking goal deliver and endeavours to connect this
address with a next jump. As stated by Velez et al. (2015), by dissecting various updates
from single other switch, a switch can create an image of the system topology. There are
various routing algorithm metrics that helps in determining the best route. Some of the
routing metrics have been discussed below:
Path length: As commented by Vinel et al. (2016), it is a common routing metric. This
protocol helps in allowing network administrators for assigning arbitrary costs to each
network link. Path length refers to cost of cost included in each link traversed. Other
routing protocols helps in defining hop count that include number of passes in the
internetworking products.
Routing delay: As mentioned by Sampei (2017),it refers to the length of time required
for moving the packets from source to destination by internet. However, delay depends on
various factors that include bandwidth of medium internet links.
Bandwidth: It refers to availability traffic capacity of link. Every single other thing being
equivalent, a 10-Mbps Ethernet connection would be desirable over a 64-kbps rented line.
In spite of the fact that transmission capacity is a rating of the most extreme achievable
throughput on a connection, courses through connections with more noteworthy data
transfer capacity do not really give preferred courses over courses through slower
7630317365527025157.docx 11 of 31
routing and bridging with different data and information with help of moving information
from source to destination. However, the routing algorithm is a part of network layer
software that is responsible for the transfer of data packets through a channel.
As mentioned by Javed, Afzal & Kim (2018), routing protocols uses metrics for
evaluating the path bandwidth and reliability of the routing algorithm for determining
optimal path to destination. This include the destination information and address. Routing
algorithm helps in filling routing tables with a variety of information. When a switch gets
an appropriate function, it starts checking goal deliver and endeavours to connect this
address with a next jump. As stated by Velez et al. (2015), by dissecting various updates
from single other switch, a switch can create an image of the system topology. There are
various routing algorithm metrics that helps in determining the best route. Some of the
routing metrics have been discussed below:
Path length: As commented by Vinel et al. (2016), it is a common routing metric. This
protocol helps in allowing network administrators for assigning arbitrary costs to each
network link. Path length refers to cost of cost included in each link traversed. Other
routing protocols helps in defining hop count that include number of passes in the
internetworking products.
Routing delay: As mentioned by Sampei (2017),it refers to the length of time required
for moving the packets from source to destination by internet. However, delay depends on
various factors that include bandwidth of medium internet links.
Bandwidth: It refers to availability traffic capacity of link. Every single other thing being
equivalent, a 10-Mbps Ethernet connection would be desirable over a 64-kbps rented line.
In spite of the fact that transmission capacity is a rating of the most extreme achievable
throughput on a connection, courses through connections with more noteworthy data
transfer capacity do not really give preferred courses over courses through slower
7630317365527025157.docx 11 of 31

interfaces. For instance, if a quicker connection is busier, real time required to send a
parcel to goal could be more prominent.
Load: As commented by El-Bawab et al. (2018), it alludes to how much a system asset,
for example, a switch, is occupied. Load can be computed in an assortment of ways,
including CPU usage and parcels prepared every second. Observing these parameters
consistently can be asset serious itself.
Communication cost: It is another critical metric, particularly in light of the fact that a
few organizations may not think about execution as much as they think about working
consumptions. In spite of the fact that line postponement might be longer, they will send
parcels over their own lines as opposed to through people in general lines that cost cash for
use time.
As mentioned by Zinner et al. 2017), reliability with regards to steering calculations,
alludes to the constancy (normally depicted as far as the bit-mistake rate) of each system
interface. Some system connections may go down more frequently than others. After a
system comes up short, certain system connections may be repaired more effectively or
more rapidly than different connections. Any unwavering quality factor can be considered
in the task of the dependability evaluations, which are discretionary numeric qualities,
typically appointed to arrange connects by organize managers.
5.4. Security
For securing the network from illegal access different security measures can be
applied and it is the key for the success of the network. Different factors should be
considered such as location of the firewalls, devices installed in the DMZ zone, Access
control list and the VPN tunnelling for end to end point connection. The firewall should be
installed in the entry point of the DMZ zone such that the access of the resources in the
DMZ zone should be restricted and another firewall should be installed in the exit point
such that the internal and the external network can be secured from the illegal access. For
7630317365527025157.docx 12 of 31
parcel to goal could be more prominent.
Load: As commented by El-Bawab et al. (2018), it alludes to how much a system asset,
for example, a switch, is occupied. Load can be computed in an assortment of ways,
including CPU usage and parcels prepared every second. Observing these parameters
consistently can be asset serious itself.
Communication cost: It is another critical metric, particularly in light of the fact that a
few organizations may not think about execution as much as they think about working
consumptions. In spite of the fact that line postponement might be longer, they will send
parcels over their own lines as opposed to through people in general lines that cost cash for
use time.
As mentioned by Zinner et al. 2017), reliability with regards to steering calculations,
alludes to the constancy (normally depicted as far as the bit-mistake rate) of each system
interface. Some system connections may go down more frequently than others. After a
system comes up short, certain system connections may be repaired more effectively or
more rapidly than different connections. Any unwavering quality factor can be considered
in the task of the dependability evaluations, which are discretionary numeric qualities,
typically appointed to arrange connects by organize managers.
5.4. Security
For securing the network from illegal access different security measures can be
applied and it is the key for the success of the network. Different factors should be
considered such as location of the firewalls, devices installed in the DMZ zone, Access
control list and the VPN tunnelling for end to end point connection. The firewall should be
installed in the entry point of the DMZ zone such that the access of the resources in the
DMZ zone should be restricted and another firewall should be installed in the exit point
such that the internal and the external network can be secured from the illegal access. For
7630317365527025157.docx 12 of 31

increasing the security of the network the wireless access point should also be secured with
the application of the WPA PSk 2 encryption algorithm. Client server architecture model
can be used for increasing the security of the network. The implementation of a RADIUS
server helps in communicating with the rest of the network with the central server and it
acts as a central point of failure. Different authorization mechanism should be followed for
the management of the network service and allow the remote users to connect with the
network.
5.5. Virtual LANs
The virtual LANs consists of a subset of the ports for a single switch or it is a subset
of the ports on multiple switches. With the creation of the VLAN the traffic generated on
the traffic are not seen on the network and it enables the network administrator to partition
the network into smaller subnet for managing the network efficiently and meet the
functional and the security requirement of the organizational network. For the development
of the VLAN the IEEE 802.1 Q standard is followed and it also enables to reduce the
congestion in the network and increasing the network performance. The switch port of a
switch can be assigned to a VLAN and it can also be allowed to divide the network into
different groups that can be based on the departments. Different rules can be set on the
network for allowing the user to access the servers installed in the network.
Eight different VLAN are created for the network and one of the server is installed in
the DMZ zone in the DMZ VLAN while the other server is installed in the server VLAN
for increasing the security of network and protect the resources for external agents. The
main users of VLAN are the users working in the department and the switch are configured
with the trunk protocol such that the port can be used for inter VLAN routing. The VLAN
should be assigned with a range of IP address such that it can be used by the network for
communicating with the other users connected in different VLAN of the network.
7630317365527025157.docx 13 of 31
the application of the WPA PSk 2 encryption algorithm. Client server architecture model
can be used for increasing the security of the network. The implementation of a RADIUS
server helps in communicating with the rest of the network with the central server and it
acts as a central point of failure. Different authorization mechanism should be followed for
the management of the network service and allow the remote users to connect with the
network.
5.5. Virtual LANs
The virtual LANs consists of a subset of the ports for a single switch or it is a subset
of the ports on multiple switches. With the creation of the VLAN the traffic generated on
the traffic are not seen on the network and it enables the network administrator to partition
the network into smaller subnet for managing the network efficiently and meet the
functional and the security requirement of the organizational network. For the development
of the VLAN the IEEE 802.1 Q standard is followed and it also enables to reduce the
congestion in the network and increasing the network performance. The switch port of a
switch can be assigned to a VLAN and it can also be allowed to divide the network into
different groups that can be based on the departments. Different rules can be set on the
network for allowing the user to access the servers installed in the network.
Eight different VLAN are created for the network and one of the server is installed in
the DMZ zone in the DMZ VLAN while the other server is installed in the server VLAN
for increasing the security of network and protect the resources for external agents. The
main users of VLAN are the users working in the department and the switch are configured
with the trunk protocol such that the port can be used for inter VLAN routing. The VLAN
should be assigned with a range of IP address such that it can be used by the network for
communicating with the other users connected in different VLAN of the network.
7630317365527025157.docx 13 of 31
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5.6. Wireless Networks
A wireless access point is connected for each of the department and a separate VLAN
should be used for the wireless network such that the intruder cannot access the core
resources of the network by connecting their wireless device in the network. The wireless
access point should be installed in each of the floor of the building and 2.4 Ghz channel
should be used for the transmission of the wireless signals over the network. The area of
coverage of the wireless access point should be analysed for covering the local area
network and encryption algorithm should be applied in the wireless access point such that
it cannot be accessed by the unauthorised users. Proper authentication mechanism should
be followed by the users for connecting with the wireless network and use it for sending
and receiving the data packets to the destination address using the network.
The WAN solution is prepared for the organization and IEEE 802.11 b is used for
providing a data rate of 11 mbps to all the network device connected with the
organizational network. The bit rate can be decreased to 5.2, 2 or 1 mbps if the quality and
the strength of the signal decreases. Thus there is a requirement to cover the organizational
area with the wireless access point.
5.7. QoS Design
Quality of service has helped in enabling technology for maintaining the data
networks. The business models include the QoS agreement for providing a better
networking system in the company. As mentioned by Natalizio et al (2018), the QoS helps
in evolving business networks in the market. The use of the QoS mechanism in the
business networks have helped in providing a secure network system to the organization.
The end-to-end Qos has helped in reaching out of a huge number of devices connected in
network. The use of QoS design have been applicable to the slow speed wide area
networks or Internet. However, many researchers have argued with this policy and stated it
as a myth. As mentioned by Tanaka (2w014), networks without QoS enabled has been
7630317365527025157.docx 14 of 31
A wireless access point is connected for each of the department and a separate VLAN
should be used for the wireless network such that the intruder cannot access the core
resources of the network by connecting their wireless device in the network. The wireless
access point should be installed in each of the floor of the building and 2.4 Ghz channel
should be used for the transmission of the wireless signals over the network. The area of
coverage of the wireless access point should be analysed for covering the local area
network and encryption algorithm should be applied in the wireless access point such that
it cannot be accessed by the unauthorised users. Proper authentication mechanism should
be followed by the users for connecting with the wireless network and use it for sending
and receiving the data packets to the destination address using the network.
The WAN solution is prepared for the organization and IEEE 802.11 b is used for
providing a data rate of 11 mbps to all the network device connected with the
organizational network. The bit rate can be decreased to 5.2, 2 or 1 mbps if the quality and
the strength of the signal decreases. Thus there is a requirement to cover the organizational
area with the wireless access point.
5.7. QoS Design
Quality of service has helped in enabling technology for maintaining the data
networks. The business models include the QoS agreement for providing a better
networking system in the company. As mentioned by Natalizio et al (2018), the QoS helps
in evolving business networks in the market. The use of the QoS mechanism in the
business networks have helped in providing a secure network system to the organization.
The end-to-end Qos has helped in reaching out of a huge number of devices connected in
network. The use of QoS design have been applicable to the slow speed wide area
networks or Internet. However, many researchers have argued with this policy and stated it
as a myth. As mentioned by Tanaka (2w014), networks without QoS enabled has been
7630317365527025157.docx 14 of 31

described it as a best-effort networks. This administration class is expected for flagging
movement that backings IP voice and video communication. Movement in this class ought
to be checked CS3 also, provisioned with a (direct, yet committed) ensured data transfer
capacity line. WRED ought not be empowered on this class, as flagging activity ought not
be dropped (if this class is encountering drops, at that point the transmission capacity
designated to it ought to be re-provisioned). Illustration activity incorporates SCCP, SIP.
As stated by He, Bukralia & Huang (2017), there is a virtual blast of media applications on
the IP coordinate with a wide range of sorts of voice, video, also, information applications.
For instance, voice streams can be standard IP Telephony, top quality sound, Internet
VoIP, and so on. Correspondingly, there are numerous kinds of video, including on-request
or communicate work area video, low-definition intelligent video, (for example, webcams),
top quality intelligent video, (for example, Cisco TelePresence), IP video observation,
advanced signage, and amusement situated video applications. Thus, there is a practically
boundless number of information applications. Furthermore, past the current media blast,
numerous new applications are coordinating various kinds of media streams into end-client
applications.
5.8. Network Management
As commented by Ma et al. (2015), network management is a service that helps in
employing several protocols, tools, applications and devices for assisting human network
managers for controlling and monitoring proper network. A network management system
deals with the collection of application for enabling network components needs to be
controlled and monitored. The design comprises of two key components:
As commented by Young, Shakiba, Kwok, & Montazeri (2014), an overseeing
gadget, called an administration station, or an administrator and oversaw gadgets, called
administration specialists or essentially an operator. An administration station fills in as the
interface between the human system administrator and the system administration
7630317365527025157.docx 15 of 31
movement that backings IP voice and video communication. Movement in this class ought
to be checked CS3 also, provisioned with a (direct, yet committed) ensured data transfer
capacity line. WRED ought not be empowered on this class, as flagging activity ought not
be dropped (if this class is encountering drops, at that point the transmission capacity
designated to it ought to be re-provisioned). Illustration activity incorporates SCCP, SIP.
As stated by He, Bukralia & Huang (2017), there is a virtual blast of media applications on
the IP coordinate with a wide range of sorts of voice, video, also, information applications.
For instance, voice streams can be standard IP Telephony, top quality sound, Internet
VoIP, and so on. Correspondingly, there are numerous kinds of video, including on-request
or communicate work area video, low-definition intelligent video, (for example, webcams),
top quality intelligent video, (for example, Cisco TelePresence), IP video observation,
advanced signage, and amusement situated video applications. Thus, there is a practically
boundless number of information applications. Furthermore, past the current media blast,
numerous new applications are coordinating various kinds of media streams into end-client
applications.
5.8. Network Management
As commented by Ma et al. (2015), network management is a service that helps in
employing several protocols, tools, applications and devices for assisting human network
managers for controlling and monitoring proper network. A network management system
deals with the collection of application for enabling network components needs to be
controlled and monitored. The design comprises of two key components:
As commented by Young, Shakiba, Kwok, & Montazeri (2014), an overseeing
gadget, called an administration station, or an administrator and oversaw gadgets, called
administration specialists or essentially an operator. An administration station fills in as the
interface between the human system administrator and the system administration
7630317365527025157.docx 15 of 31

framework. It is the stage for administration applications to perform administration works
through collaborations with the administration operators. The network management
strategy that should be followed for management of network resources are also
documented in report. The physical network design is also attached with report with details
of network topology selected for development of local area network and the wide area
network of the organization. The administration specialist reacts to the solicitations from
the administration station and furthermore furnishes the administration station with
spontaneous data. As mentioned by Han et al. (2016), setup administration is worried about
introducing a system, provisioning the system assets furthermore, administrations, and
checking and controlling the system. All the more particularly, the obligations of design
administration incorporate setting, looking after, including, and refreshing the relationship
among segments and the status of the segments amid organize activity. Setup
administration comprises of both gadget design and system arrangement.
Gadget setup can be performed either locally or remotely. Computerized organize
arrangement,
For example, Dynamic Host Configuration Protocol (DHCP) and Domain Name
Services (DNS), plays a key part in arrange administration.
As suggested by Hagenauer, Dressler & Sommer (2014), security management helps
in protecting networks and system from unauthorized access and security attacks. The
mechanism included in the security management contains encryption, authentication and
authorization. Therefore, security, management deals with the distribution, generation and
security systems including firewalls and virus detection system. As commented by Guo,
Zhu & Yang (2017), the use of updated anti-virus and firewalls helps in maintaining and
restricting viruses and malwares in network. Accounting system management helps in
enabling charges for using the managed objects for measuring and determining the cost.
This helps in calculating the budget of the network project in market.
7630317365527025157.docx 16 of 31
through collaborations with the administration operators. The network management
strategy that should be followed for management of network resources are also
documented in report. The physical network design is also attached with report with details
of network topology selected for development of local area network and the wide area
network of the organization. The administration specialist reacts to the solicitations from
the administration station and furthermore furnishes the administration station with
spontaneous data. As mentioned by Han et al. (2016), setup administration is worried about
introducing a system, provisioning the system assets furthermore, administrations, and
checking and controlling the system. All the more particularly, the obligations of design
administration incorporate setting, looking after, including, and refreshing the relationship
among segments and the status of the segments amid organize activity. Setup
administration comprises of both gadget design and system arrangement.
Gadget setup can be performed either locally or remotely. Computerized organize
arrangement,
For example, Dynamic Host Configuration Protocol (DHCP) and Domain Name
Services (DNS), plays a key part in arrange administration.
As suggested by Hagenauer, Dressler & Sommer (2014), security management helps
in protecting networks and system from unauthorized access and security attacks. The
mechanism included in the security management contains encryption, authentication and
authorization. Therefore, security, management deals with the distribution, generation and
security systems including firewalls and virus detection system. As commented by Guo,
Zhu & Yang (2017), the use of updated anti-virus and firewalls helps in maintaining and
restricting viruses and malwares in network. Accounting system management helps in
enabling charges for using the managed objects for measuring and determining the cost.
This helps in calculating the budget of the network project in market.
7630317365527025157.docx 16 of 31
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

6. Physical Design
6.1. Network Topology
As commented by Prakash et al. (2018), topology focuses on the method by which
various computers and devices are connected in a network. The selection of topology
depends on the user requirements. Various types of topologies are discussed below:
Mesh Topology: As commented by Jabeur, Sahli & Zeadally (2015), this topology
refers to the connection of each node with every node connected in a network. However,
mesh topology is not flexible and has a poor expandability as adding a new node becomes
difficult for the network administrator. However, there is no need to provide an extra
information about the source point of data packet along with the destination point of the
data packet.
Bus Topology: In this topology, all the nodes are connected in a linear transmission
medium. Full-duplex operation used to happen between stations and tap that helps in
allowing data transmission in the bus. At each finish of transport there is an eliminator that
ingests any flag, keeping impression of flag from endpoints. In event that the eliminator is
absent, the endpoint demonstrations like a mirror and mirrors the flag back causing
obstruction and different issues.
Star topology: As commented by Lauren & Pigg (2016), this topology refers to a
connection in which all the nodes are connected in the common central node. Therefore,
each node is independently and directly connected with the central node for the data
transmission process. A very high speed data transfer speed can be achieved by the star
topology as all the computers are connected directly with the central node. This topology
can be maintained and managed by the network administrator other than other topologies.
Ring topology: As mentioned by Leonardi (2015), Ring topology includes various
repeaters that are connected together by a point-to-point closed loop.
7630317365527025157.docx 17 of 31
6.1. Network Topology
As commented by Prakash et al. (2018), topology focuses on the method by which
various computers and devices are connected in a network. The selection of topology
depends on the user requirements. Various types of topologies are discussed below:
Mesh Topology: As commented by Jabeur, Sahli & Zeadally (2015), this topology
refers to the connection of each node with every node connected in a network. However,
mesh topology is not flexible and has a poor expandability as adding a new node becomes
difficult for the network administrator. However, there is no need to provide an extra
information about the source point of data packet along with the destination point of the
data packet.
Bus Topology: In this topology, all the nodes are connected in a linear transmission
medium. Full-duplex operation used to happen between stations and tap that helps in
allowing data transmission in the bus. At each finish of transport there is an eliminator that
ingests any flag, keeping impression of flag from endpoints. In event that the eliminator is
absent, the endpoint demonstrations like a mirror and mirrors the flag back causing
obstruction and different issues.
Star topology: As commented by Lauren & Pigg (2016), this topology refers to a
connection in which all the nodes are connected in the common central node. Therefore,
each node is independently and directly connected with the central node for the data
transmission process. A very high speed data transfer speed can be achieved by the star
topology as all the computers are connected directly with the central node. This topology
can be maintained and managed by the network administrator other than other topologies.
Ring topology: As mentioned by Leonardi (2015), Ring topology includes various
repeaters that are connected together by a point-to-point closed loop.
7630317365527025157.docx 17 of 31

6.2. LAN technologies
Now a day computer technology is rapidly growing all over the world. As commented by
Pinchuk (2015), through the internet many systems are now networked together for
established an online connection to the globe. Local area network (LAN) interconnect the
computers of companies and individuals. LAN users can store much information, data and
applications as has their disposal.
As mentioned by Roy e al. (2014), users of LAN offered high bit rates for meeting
requirements of bandwidth consuming services including video conferences, streaming
video for this kind of facility in LAN, a WLAN user will expect a high demand from their
system. For this reason certified computer engineers are still working on this and they are
trying to improve the technology of LAN as well as WLAN.
6.3. WAN technologies
As commented by Rodriguez et al. (2017), WLAN technology was found in the year
of 1990 for no selling of LAN network to enterprise or campus environment.at the
beginning wlan products were slow, expensive and bulky. Even mobile network
connectivity was simple network that was not stranger and secure network.
Architecture
Architecture of a wireless network is divided into cells s controlled by a base
station. Standards of wireless networks are currently being used in communications
technology are IEEE 802.11, hiper lan, Bluetooth, .homerf and Narrowband of wlan.
Spread spectrum
Spectrum technology is allowed to spread for developed military use by continually
changing frequency of transmitted signal. Uses of spectrum technology is more than
narrowband technology
Frequency hopping spread spectrum
7630317365527025157.docx 18 of 31
Now a day computer technology is rapidly growing all over the world. As commented by
Pinchuk (2015), through the internet many systems are now networked together for
established an online connection to the globe. Local area network (LAN) interconnect the
computers of companies and individuals. LAN users can store much information, data and
applications as has their disposal.
As mentioned by Roy e al. (2014), users of LAN offered high bit rates for meeting
requirements of bandwidth consuming services including video conferences, streaming
video for this kind of facility in LAN, a WLAN user will expect a high demand from their
system. For this reason certified computer engineers are still working on this and they are
trying to improve the technology of LAN as well as WLAN.
6.3. WAN technologies
As commented by Rodriguez et al. (2017), WLAN technology was found in the year
of 1990 for no selling of LAN network to enterprise or campus environment.at the
beginning wlan products were slow, expensive and bulky. Even mobile network
connectivity was simple network that was not stranger and secure network.
Architecture
Architecture of a wireless network is divided into cells s controlled by a base
station. Standards of wireless networks are currently being used in communications
technology are IEEE 802.11, hiper lan, Bluetooth, .homerf and Narrowband of wlan.
Spread spectrum
Spectrum technology is allowed to spread for developed military use by continually
changing frequency of transmitted signal. Uses of spectrum technology is more than
narrowband technology
Frequency hopping spread spectrum
7630317365527025157.docx 18 of 31

As commented by Dong, Piuri, Chan & Jain (2016), frequency hopping spread
spectrum technology is mainly used to synchronised changing the frequency of both
transmitter and receiver and produce a single transmission signal.
Wireless devices are need to be small and wireless networks are limited in bandwidth but it
faced some challenges. These are-
A. Data rate enhancements
B. Low power networking.
C. Radio signal interference.
D. System interoperability.
As commented by Thirumalai & Senthilkumar (2017), for support future high
speed applications now current data rates need to be improve if multimedia services are
provided. Data rates is just a small function of various factors.
Wireless mobile’s size and battery power limitation place a limit at range.
As mentioned by Anderson et al. (2016), security is a major challenge in wireless
networking, especially in e-commerce and m commerce applications.
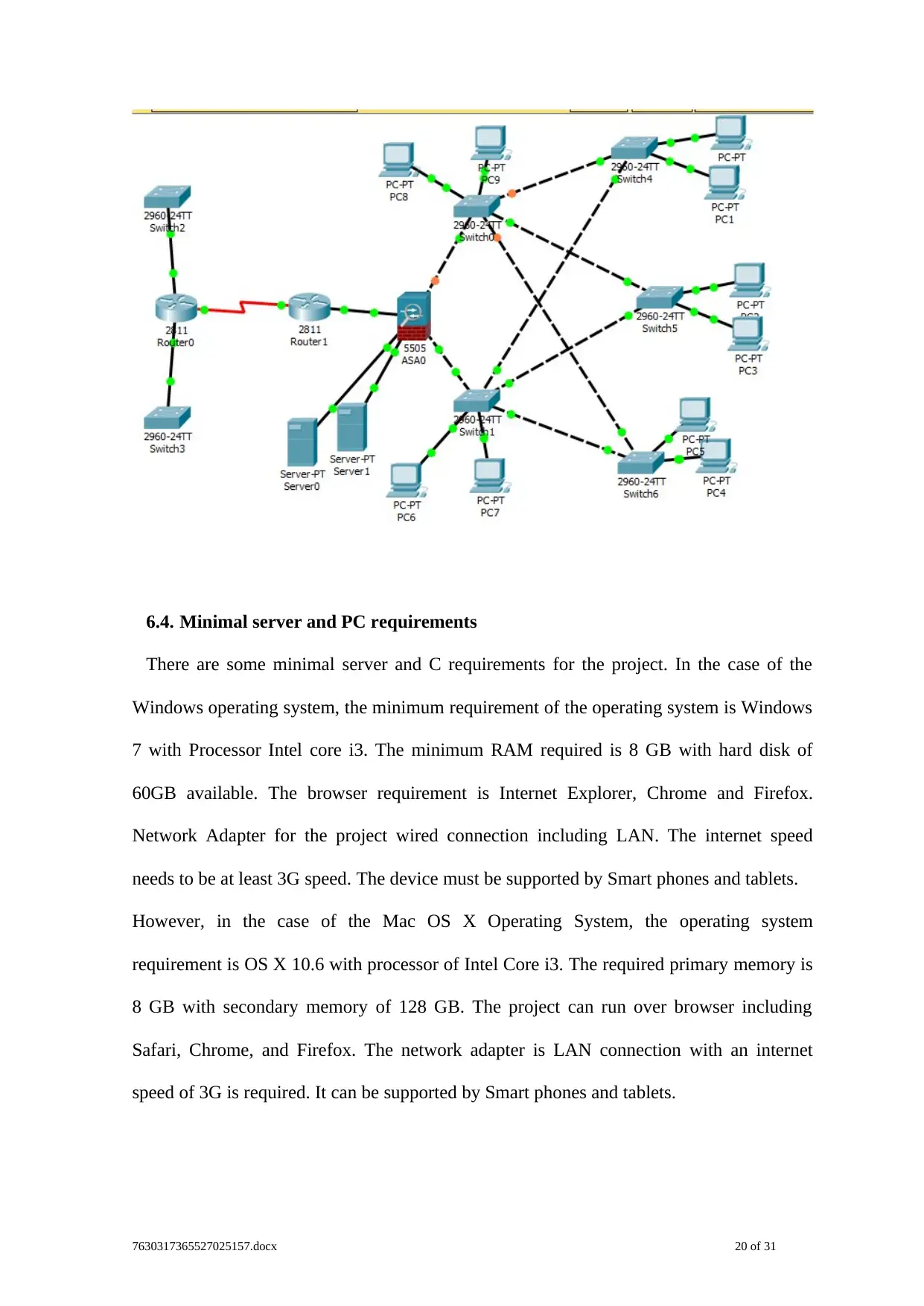
6.4 Physical Network Diagram
For the development of the physical network diagram a feasibility study is performed on
the network and it is location that should be used for the deployment of the different
network device are analysed. The name and device of the router that should be deployed in
the network are used for designing the physical network diagram. Cisco packet tracer 7.1.
is used for the development of the logical network diagram and it should be configured
with different routing protocols and technology for enabling communication with the other
device connected in the host. The IP addressing scheme should be used for the configuring
the routers with the Cisco 2811 series routers are used for the configuration of the network.
Cisco 2960 series switch is used for connecting each of the department and creating
different VLANs for the department and reduce the congestion in the network.
7630317365527025157.docx 19 of 31
spectrum technology is mainly used to synchronised changing the frequency of both
transmitter and receiver and produce a single transmission signal.
Wireless devices are need to be small and wireless networks are limited in bandwidth but it
faced some challenges. These are-
A. Data rate enhancements
B. Low power networking.
C. Radio signal interference.
D. System interoperability.
As commented by Thirumalai & Senthilkumar (2017), for support future high
speed applications now current data rates need to be improve if multimedia services are
provided. Data rates is just a small function of various factors.
Wireless mobile’s size and battery power limitation place a limit at range.
As mentioned by Anderson et al. (2016), security is a major challenge in wireless
networking, especially in e-commerce and m commerce applications.
6.4 Physical Network Diagram
For the development of the physical network diagram a feasibility study is performed on
the network and it is location that should be used for the deployment of the different
network device are analysed. The name and device of the router that should be deployed in
the network are used for designing the physical network diagram. Cisco packet tracer 7.1.
is used for the development of the logical network diagram and it should be configured
with different routing protocols and technology for enabling communication with the other
device connected in the host. The IP addressing scheme should be used for the configuring
the routers with the Cisco 2811 series routers are used for the configuration of the network.
Cisco 2960 series switch is used for connecting each of the department and creating
different VLANs for the department and reduce the congestion in the network.
7630317365527025157.docx 19 of 31
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
6.4. Minimal server and PC requirements
There are some minimal server and C requirements for the project. In the case of the
Windows operating system, the minimum requirement of the operating system is Windows
7 with Processor Intel core i3. The minimum RAM required is 8 GB with hard disk of
60GB available. The browser requirement is Internet Explorer, Chrome and Firefox.
Network Adapter for the project wired connection including LAN. The internet speed
needs to be at least 3G speed. The device must be supported by Smart phones and tablets.
However, in the case of the Mac OS X Operating System, the operating system
requirement is OS X 10.6 with processor of Intel Core i3. The required primary memory is
8 GB with secondary memory of 128 GB. The project can run over browser including
Safari, Chrome, and Firefox. The network adapter is LAN connection with an internet
speed of 3G is required. It can be supported by Smart phones and tablets.
7630317365527025157.docx 20 of 31
There are some minimal server and C requirements for the project. In the case of the
Windows operating system, the minimum requirement of the operating system is Windows
7 with Processor Intel core i3. The minimum RAM required is 8 GB with hard disk of
60GB available. The browser requirement is Internet Explorer, Chrome and Firefox.
Network Adapter for the project wired connection including LAN. The internet speed
needs to be at least 3G speed. The device must be supported by Smart phones and tablets.
However, in the case of the Mac OS X Operating System, the operating system
requirement is OS X 10.6 with processor of Intel Core i3. The required primary memory is
8 GB with secondary memory of 128 GB. The project can run over browser including
Safari, Chrome, and Firefox. The network adapter is LAN connection with an internet
speed of 3G is required. It can be supported by Smart phones and tablets.
7630317365527025157.docx 20 of 31

6.5. Wireless technologies
As commented by Çetinkaya (2016), the wireless technologies refers to the communication
and data transmission with the help of Electromagnetic waves in the atmosphere. The
channel for the wireless communication have been always air. There is no physical and
direct connection between sender and receiver in this technology. As commented by
Luchin et al. (2018), both the sender and receiver are connected with the help of wireless
technology and protocols. The use of electromagnetic waves helps in gaining the speed of
light and that makes the fastest communication. Therefore, wireless communication is
more preferred in long distance communication. As suggested by Liu & Zhang (2015), the
wireless technologies have been increasing on a daily basis. Therefore, the maintenance of
the communication technology need to be properly done. An administration station fills in
as the interface between the human system administrator and the system administration
framework.
It is the stage for administration applications to perform administration works through
collaborations with the administration operators. The administration specialist reacts to the
solicitations from the administration station and furthermore furnishes the administration
station with spontaneous data. There are various types of wireless technologies including
the cellular system and Bluetooth. As stated by Wu et al. (2016), bluetooth has been
developed for removing the wired connection between short distances. Therefore, the
replacement of the wired technology have helped in minimizing the cost ad budget of the
network system. The use of Bluetooth gave been generally used in the mobile devices at a
shirt distance. The use of Bluetooth technology have been maintaining the communication
at a shirt distance. The use of maintenance of the Bluetooth technology have been
maintaining the fast communication of the data and information in the channel. As
mentioned by Peng, Li, Zhao & Wang (2015), the use of Bluetooth technology have been
misnaming the congestion of network and replacing the complex wired technology.
7630317365527025157.docx 21 of 31
As commented by Çetinkaya (2016), the wireless technologies refers to the communication
and data transmission with the help of Electromagnetic waves in the atmosphere. The
channel for the wireless communication have been always air. There is no physical and
direct connection between sender and receiver in this technology. As commented by
Luchin et al. (2018), both the sender and receiver are connected with the help of wireless
technology and protocols. The use of electromagnetic waves helps in gaining the speed of
light and that makes the fastest communication. Therefore, wireless communication is
more preferred in long distance communication. As suggested by Liu & Zhang (2015), the
wireless technologies have been increasing on a daily basis. Therefore, the maintenance of
the communication technology need to be properly done. An administration station fills in
as the interface between the human system administrator and the system administration
framework.
It is the stage for administration applications to perform administration works through
collaborations with the administration operators. The administration specialist reacts to the
solicitations from the administration station and furthermore furnishes the administration
station with spontaneous data. There are various types of wireless technologies including
the cellular system and Bluetooth. As stated by Wu et al. (2016), bluetooth has been
developed for removing the wired connection between short distances. Therefore, the
replacement of the wired technology have helped in minimizing the cost ad budget of the
network system. The use of Bluetooth gave been generally used in the mobile devices at a
shirt distance. The use of Bluetooth technology have been maintaining the communication
at a shirt distance. The use of maintenance of the Bluetooth technology have been
maintaining the fast communication of the data and information in the channel. As
mentioned by Peng, Li, Zhao & Wang (2015), the use of Bluetooth technology have been
misnaming the congestion of network and replacing the complex wired technology.
7630317365527025157.docx 21 of 31

The range of the Bluetooth technology have been 10 metres with 0dbm transmitted
power. However, it can be increased upto 100 metres. As commented by Chen et al.
(2015), the Bluetooth technology is mainly used in the mobile communication and other
electronic devices. Data packets are send through the source and is reached to the
destination through air as a medium. There are various Bluetooth devices including
mobile, printer, audio box, headphones and laptops. Therefore, the use of the Bluetooth
technology has been spread a lot of devices. Therefore, the use of the Bluetooth technology
have been creating a positive impact in the wireless communication.
7630317365527025157.docx 22 of 31
power. However, it can be increased upto 100 metres. As commented by Chen et al.
(2015), the Bluetooth technology is mainly used in the mobile communication and other
electronic devices. Data packets are send through the source and is reached to the
destination through air as a medium. There are various Bluetooth devices including
mobile, printer, audio box, headphones and laptops. Therefore, the use of the Bluetooth
technology has been spread a lot of devices. Therefore, the use of the Bluetooth technology
have been creating a positive impact in the wireless communication.
7630317365527025157.docx 22 of 31
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

7. Test Plan
7.1. Overall Project Scope and Objective
The test plan is prepared for the orange site of Globex Corporation for the identification of
the requirement and align the network for increasing the security of the department. The
LAN and WAN solutions are created for a site to site VPN connection is created for
increasing the security of thee network. The design of the network should be evaluated for
the identification of the weakness of the network and identification of the limitations of the
network.
7.2. Test objective and success criteria
The response time of the network should be identified and network load and the path
should be estimated for the analysis of the peak estimated load of the network. The
acceptance criteria of the network should be minimum of 2 mbps and the impact of the test
traffic on the network should be identified. The congestion in the network and the packet
loss should also be identified for the analysis of the test result and implement the network
failover plan.
7.3. Test resource required
Hardware, software and the test tools are required for the completion of the test and it
should be included in the test plan for the estimation of the resource. The exact hardware
should be documented with the software versions and the components used for the
different test scenarios.
The hardware needed to be tested
Product Description Quantity
2811 Cisco 2811 Router 2
2960 Cisco 2960 24 port switch 7
7630317365527025157.docx 23 of 31
7.1. Overall Project Scope and Objective
The test plan is prepared for the orange site of Globex Corporation for the identification of
the requirement and align the network for increasing the security of the department. The
LAN and WAN solutions are created for a site to site VPN connection is created for
increasing the security of thee network. The design of the network should be evaluated for
the identification of the weakness of the network and identification of the limitations of the
network.
7.2. Test objective and success criteria
The response time of the network should be identified and network load and the path
should be estimated for the analysis of the peak estimated load of the network. The
acceptance criteria of the network should be minimum of 2 mbps and the impact of the test
traffic on the network should be identified. The congestion in the network and the packet
loss should also be identified for the analysis of the test result and implement the network
failover plan.
7.3. Test resource required
Hardware, software and the test tools are required for the completion of the test and it
should be included in the test plan for the estimation of the resource. The exact hardware
should be documented with the software versions and the components used for the
different test scenarios.
The hardware needed to be tested
Product Description Quantity
2811 Cisco 2811 Router 2
2960 Cisco 2960 24 port switch 7
7630317365527025157.docx 23 of 31
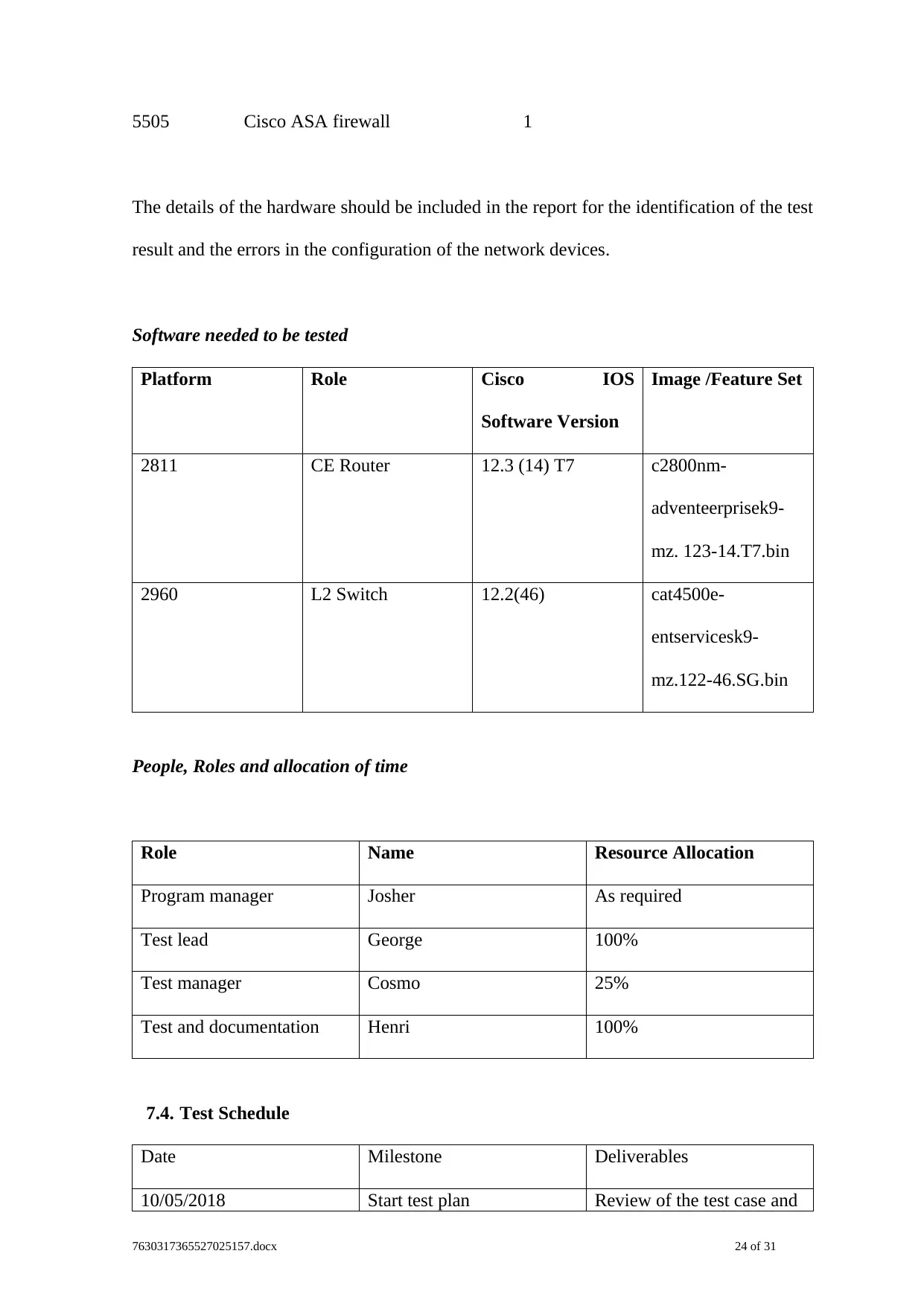
5505 Cisco ASA firewall 1
The details of the hardware should be included in the report for the identification of the test
result and the errors in the configuration of the network devices.
Software needed to be tested
Platform Role Cisco IOS
Software Version
Image /Feature Set
2811 CE Router 12.3 (14) T7 c2800nm-
adventeerprisek9-
mz. 123-14.T7.bin
2960 L2 Switch 12.2(46) cat4500e-
entservicesk9-
mz.122-46.SG.bin
People, Roles and allocation of time
Role Name Resource Allocation
Program manager Josher As required
Test lead George 100%
Test manager Cosmo 25%
Test and documentation Henri 100%
7.4. Test Schedule
Date Milestone Deliverables
10/05/2018 Start test plan Review of the test case and
7630317365527025157.docx 24 of 31
The details of the hardware should be included in the report for the identification of the test
result and the errors in the configuration of the network devices.
Software needed to be tested
Platform Role Cisco IOS
Software Version
Image /Feature Set
2811 CE Router 12.3 (14) T7 c2800nm-
adventeerprisek9-
mz. 123-14.T7.bin
2960 L2 Switch 12.2(46) cat4500e-
entservicesk9-
mz.122-46.SG.bin
People, Roles and allocation of time
Role Name Resource Allocation
Program manager Josher As required
Test lead George 100%
Test manager Cosmo 25%
Test and documentation Henri 100%
7.4. Test Schedule
Date Milestone Deliverables
10/05/2018 Start test plan Review of the test case and
7630317365527025157.docx 24 of 31
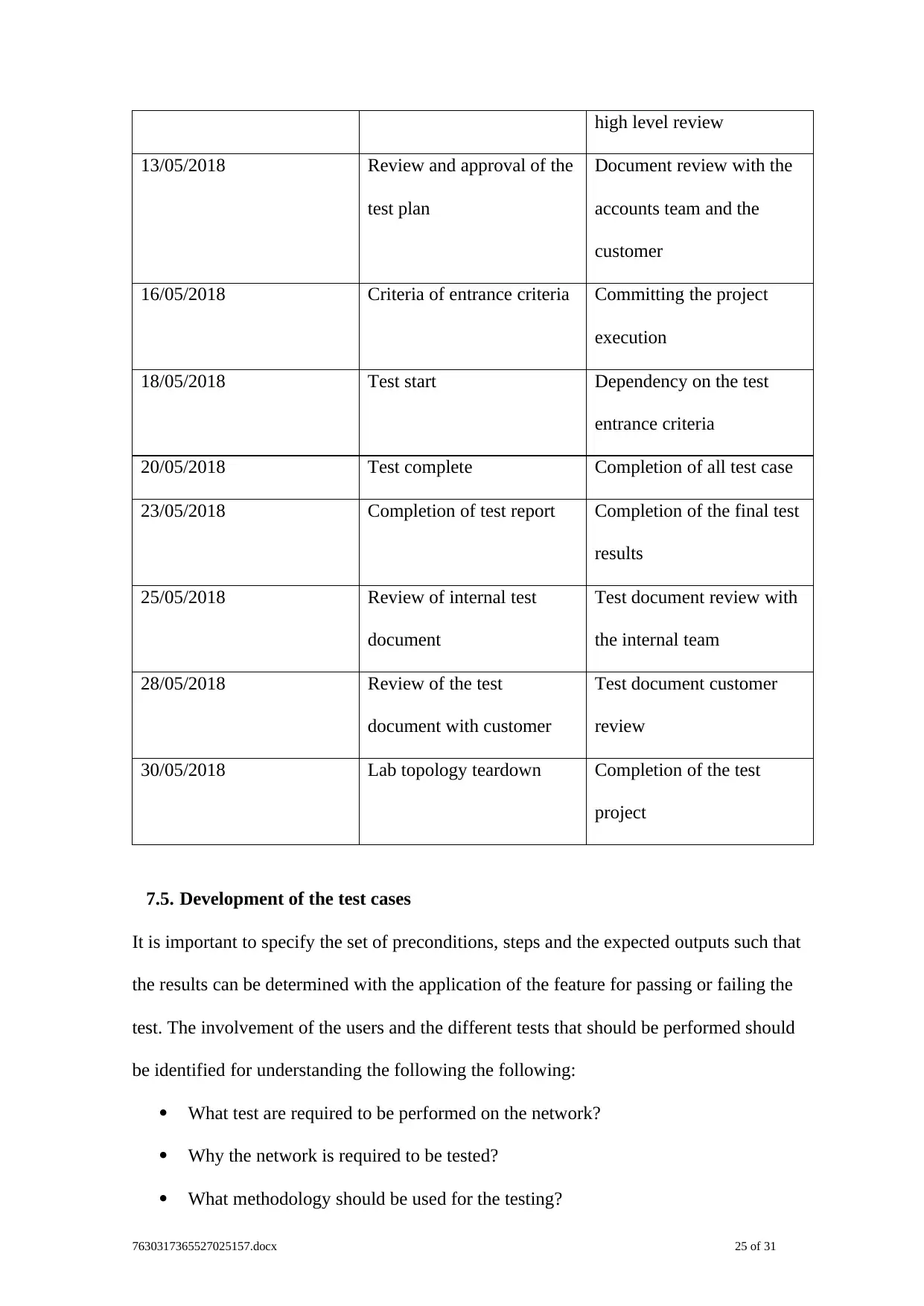
high level review
13/05/2018 Review and approval of the
test plan
Document review with the
accounts team and the
customer
16/05/2018 Criteria of entrance criteria Committing the project
execution
18/05/2018 Test start Dependency on the test
entrance criteria
20/05/2018 Test complete Completion of all test case
23/05/2018 Completion of test report Completion of the final test
results
25/05/2018 Review of internal test
document
Test document review with
the internal team
28/05/2018 Review of the test
document with customer
Test document customer
review
30/05/2018 Lab topology teardown Completion of the test
project
7.5. Development of the test cases
It is important to specify the set of preconditions, steps and the expected outputs such that
the results can be determined with the application of the feature for passing or failing the
test. The involvement of the users and the different tests that should be performed should
be identified for understanding the following the following:
What test are required to be performed on the network?
Why the network is required to be tested?
What methodology should be used for the testing?
7630317365527025157.docx 25 of 31
13/05/2018 Review and approval of the
test plan
Document review with the
accounts team and the
customer
16/05/2018 Criteria of entrance criteria Committing the project
execution
18/05/2018 Test start Dependency on the test
entrance criteria
20/05/2018 Test complete Completion of all test case
23/05/2018 Completion of test report Completion of the final test
results
25/05/2018 Review of internal test
document
Test document review with
the internal team
28/05/2018 Review of the test
document with customer
Test document customer
review
30/05/2018 Lab topology teardown Completion of the test
project
7.5. Development of the test cases
It is important to specify the set of preconditions, steps and the expected outputs such that
the results can be determined with the application of the feature for passing or failing the
test. The involvement of the users and the different tests that should be performed should
be identified for understanding the following the following:
What test are required to be performed on the network?
Why the network is required to be tested?
What methodology should be used for the testing?
7630317365527025157.docx 25 of 31
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

What are the information that are needed to be captured from the network device?
What format should be used for recording the test results?
7630317365527025157.docx 26 of 31
What format should be used for recording the test results?
7630317365527025157.docx 26 of 31

8. References
Anderson, J., Hu, H., Agarwal, U., Lowery, C., Li, H., & Apon, A. (2016, February).
Performance considerations of network functions virtualization using containers.
In Computing, Networking and Communications (ICNC), 2016 International
Conference on (pp. 1-7). IEEE.
Batalla, J. M., Mastorakis, G., Mavromoustakis, C. X., & Zurek, J. (2016). On cohabitating
networking technologies with common wireless access for home automation
system purposes. IEEE Wireless Communications, 23(5), 76-83.
Çetinkaya, E. K. (2016). A Brief Review of Security in Emerging Programmable
Computer Networking Technologies. IEEE-HKN Bridge Magazine, 112, 27-34.
Chen, W., Delgrossi, L., Kosch, T., & Saito, T. (2015). Automotive networking and
applications [Series Editorial]. IEEE Communications Magazine, 53(6), 124-125.
Dong, M., Piuri, V., Chan, S. H. G., & Jain, R. (2016). Introduction to Special Issue on
Multimedia Big Data: Networking. ACM Transactions on Multimedia Computing,
Communications, and Applications (TOMM), 12(5s), 70.
El-Bawab, T. S., Subrahmanyan, R., Atkin, G., & Dohler, M. (2018). ADVANCES IN
NEXT-GENERATION NETWORKING TECHNOLOGIES FOR SMART
HEALTHCARE. IEEE Communications Magazine, 2.
Guo, Y., Zhu, H., & Yang, L. (2017). Smart service system (sss): A novel architecture
enabling coordination of heterogeneous networking technologies and devices for
internet of things. China Communications, 14(3), 130-144.
Hagenauer, F., Dressler, F., & Sommer, C. (2014, December). Poster: A simulator for
heterogeneous vehicular networks. In Vehicular Networking Conference (VNC),
2014 IEEE (pp. 185-186). IEEE.
7630317365527025157.docx 27 of 31
Anderson, J., Hu, H., Agarwal, U., Lowery, C., Li, H., & Apon, A. (2016, February).
Performance considerations of network functions virtualization using containers.
In Computing, Networking and Communications (ICNC), 2016 International
Conference on (pp. 1-7). IEEE.
Batalla, J. M., Mastorakis, G., Mavromoustakis, C. X., & Zurek, J. (2016). On cohabitating
networking technologies with common wireless access for home automation
system purposes. IEEE Wireless Communications, 23(5), 76-83.
Çetinkaya, E. K. (2016). A Brief Review of Security in Emerging Programmable
Computer Networking Technologies. IEEE-HKN Bridge Magazine, 112, 27-34.
Chen, W., Delgrossi, L., Kosch, T., & Saito, T. (2015). Automotive networking and
applications [Series Editorial]. IEEE Communications Magazine, 53(6), 124-125.
Dong, M., Piuri, V., Chan, S. H. G., & Jain, R. (2016). Introduction to Special Issue on
Multimedia Big Data: Networking. ACM Transactions on Multimedia Computing,
Communications, and Applications (TOMM), 12(5s), 70.
El-Bawab, T. S., Subrahmanyan, R., Atkin, G., & Dohler, M. (2018). ADVANCES IN
NEXT-GENERATION NETWORKING TECHNOLOGIES FOR SMART
HEALTHCARE. IEEE Communications Magazine, 2.
Guo, Y., Zhu, H., & Yang, L. (2017). Smart service system (sss): A novel architecture
enabling coordination of heterogeneous networking technologies and devices for
internet of things. China Communications, 14(3), 130-144.
Hagenauer, F., Dressler, F., & Sommer, C. (2014, December). Poster: A simulator for
heterogeneous vehicular networks. In Vehicular Networking Conference (VNC),
2014 IEEE (pp. 185-186). IEEE.
7630317365527025157.docx 27 of 31

Han, G., Guizani, M., Lloret, J., Wu, H., Chan, S., & Rayes, A. (2016). Recent advances in
green industrial networking [Guest Editorial]. IEEE Communications
Magazine, 54(10), 14-15.
He, N., Bukralia, R., & Huang, H. W. (2017, October). Teaching wireless networking
technologies in the internet-of-things using ARM based microcontrollers.
In Frontiers in Education Conference (FIE) (pp. 1-4). IEEE.
Jabeur, N., Sahli, N., & Zeadally, S. (2015). Enabling cyber physical systems with wireless
sensor networking technologies, multiagent system paradigm, and natural
ecosystems. Mobile Information Systems, 2015.
Javed, F., Afzal, M. K., Sharif, M., & Kim, B. S. (2018). Internet of Things (IoTs)
Operating Systems Support, Networking Technologies, Applications, and
Challenges: A Comparative Review. IEEE Communications Surveys & Tutorials.
Lauren, B., & Pigg, S. (2016). Networking in a field of introverts: The egonets, networking
practices, and networking technologies of technical communication
entrepreneurs. IEEE Transactions on Professional Communication, 59(4), 342-362.
Leonardi, P. M. (2015). Ambient awareness and knowledge acquisition: using social media
to learn ‘who knows what’and ‘who knows whom’.
Liu, C. H., & Zhang, Y. (2015). Networking Technologies for CPS. In Cyber Physical
Systems (pp. 148-152). CRC Press.
Luchin, D. V., Trofimov, A. P., Filippov, D. V., & Yudin, V. V. (2018, March). Algorithm
of radio direction finding in the HF range in polarization fading conditions with
collocated antennas. In Electronic and Networking Technologies (MWENT), 2018
Moscow Workshop on (pp. 1-8). IEEE.
Ma, J., Sui, X., Li, Y., Yu, Z., Huang, B., & Bao, Y. (2015). Supporting Differentiated
Services in Computers via Networking Technologies. TinyToCS, 3.
7630317365527025157.docx 28 of 31
green industrial networking [Guest Editorial]. IEEE Communications
Magazine, 54(10), 14-15.
He, N., Bukralia, R., & Huang, H. W. (2017, October). Teaching wireless networking
technologies in the internet-of-things using ARM based microcontrollers.
In Frontiers in Education Conference (FIE) (pp. 1-4). IEEE.
Jabeur, N., Sahli, N., & Zeadally, S. (2015). Enabling cyber physical systems with wireless
sensor networking technologies, multiagent system paradigm, and natural
ecosystems. Mobile Information Systems, 2015.
Javed, F., Afzal, M. K., Sharif, M., & Kim, B. S. (2018). Internet of Things (IoTs)
Operating Systems Support, Networking Technologies, Applications, and
Challenges: A Comparative Review. IEEE Communications Surveys & Tutorials.
Lauren, B., & Pigg, S. (2016). Networking in a field of introverts: The egonets, networking
practices, and networking technologies of technical communication
entrepreneurs. IEEE Transactions on Professional Communication, 59(4), 342-362.
Leonardi, P. M. (2015). Ambient awareness and knowledge acquisition: using social media
to learn ‘who knows what’and ‘who knows whom’.
Liu, C. H., & Zhang, Y. (2015). Networking Technologies for CPS. In Cyber Physical
Systems (pp. 148-152). CRC Press.
Luchin, D. V., Trofimov, A. P., Filippov, D. V., & Yudin, V. V. (2018, March). Algorithm
of radio direction finding in the HF range in polarization fading conditions with
collocated antennas. In Electronic and Networking Technologies (MWENT), 2018
Moscow Workshop on (pp. 1-8). IEEE.
Ma, J., Sui, X., Li, Y., Yu, Z., Huang, B., & Bao, Y. (2015). Supporting Differentiated
Services in Computers via Networking Technologies. TinyToCS, 3.
7630317365527025157.docx 28 of 31
1 out of 28
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





