Network Infrastructure Security and Configuration for Coles
VerifiedAdded on 2022/09/17
|17
|2196
|46
Report
AI Summary
This report presents a detailed network design proposal for Coles Supermarkets, addressing the company's need for a computerized infrastructure. The report begins by outlining the project's requirements and scope, derived from a site visit to Coles' Melbourne locations and headquarters. It then presents a logical design diagram illustrating the network's architecture, including internet access, router configurations, and the use of VLANs to segment the network. The report provides an IP address table detailing subnet allocations and discusses the RIP routing protocol used for inter-network communication. Furthermore, it explains the implementation of access control list (ACL) commands to restrict network segment access, ensuring security. The configuration of routers, switches, hosts, access points, and servers is described step-by-step, followed by a timeline and budgeting estimates. The report concludes by summarizing the key findings and emphasizing the benefits of the proposed network design in enhancing Coles' network infrastructure.

Running head: NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Network Infrastructure Security and Configuration
Name of the Student
Name of the University
Author Note
Network Infrastructure Security and Configuration
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Summary
As per multiple researches of this decade, network topology design, routing protocols and access
restrictions along with VLANs and how network infrastructures of organizations can benefit from
them. This report is tasked with proposal of a configured network for Coles. First the report lists the
requirements and scope of the project that has been derived based on the component workflow
requirements which have been acquired from the site visit conducted on the Coles supermarkets in
Melbourne and their headquarters. Thereafter, the logical design diagram of the proposed network
gets presented and appropriate justification is also provided as per requirements of the business.
Next the IP address details of various subnets are provided in tabular format. After that the routing
protocol used by the network is mentioned and discussed before talking about the access privileges
configured with ACL commands. Then the report presents the timeline as well as budgeting
estimates and ends with concluding notes.
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Summary
As per multiple researches of this decade, network topology design, routing protocols and access
restrictions along with VLANs and how network infrastructures of organizations can benefit from
them. This report is tasked with proposal of a configured network for Coles. First the report lists the
requirements and scope of the project that has been derived based on the component workflow
requirements which have been acquired from the site visit conducted on the Coles supermarkets in
Melbourne and their headquarters. Thereafter, the logical design diagram of the proposed network
gets presented and appropriate justification is also provided as per requirements of the business.
Next the IP address details of various subnets are provided in tabular format. After that the routing
protocol used by the network is mentioned and discussed before talking about the access privileges
configured with ACL commands. Then the report presents the timeline as well as budgeting
estimates and ends with concluding notes.

2
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Table of Contents
Introduction...........................................................................................................................................4
Requirement Summary..........................................................................................................................4
Network Design and Explanation...........................................................................................................5
Logical Design Diagram.....................................................................................................................5
IP Address Table................................................................................................................................5
Routing Protocol used and Network Security....................................................................................7
Routing Protocol...............................................................................................................................7
Access Restrictions with ACL commands...........................................................................................8
Configuring the Network.......................................................................................................................9
Configuring the Router......................................................................................................................9
Configuring the Switch......................................................................................................................9
Configuring the Host.......................................................................................................................11
Configuring the Access points and Servers......................................................................................12
Configuring the Wireless Access Point........................................................................................12
Configuring the Server IP Addressing..........................................................................................13
Timeline and Budget............................................................................................................................13
Schedule of Activities......................................................................................................................13
Budgeting Table..............................................................................................................................14
Conclusion...........................................................................................................................................14
Bibliography.........................................................................................................................................16
Appendix A..........................................................................................................................................17
Industry Visit........................................................................................................................17
Coles.........................................................................................................................................17
..................................................................................................................................................17
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Table of Contents
Introduction...........................................................................................................................................4
Requirement Summary..........................................................................................................................4
Network Design and Explanation...........................................................................................................5
Logical Design Diagram.....................................................................................................................5
IP Address Table................................................................................................................................5
Routing Protocol used and Network Security....................................................................................7
Routing Protocol...............................................................................................................................7
Access Restrictions with ACL commands...........................................................................................8
Configuring the Network.......................................................................................................................9
Configuring the Router......................................................................................................................9
Configuring the Switch......................................................................................................................9
Configuring the Host.......................................................................................................................11
Configuring the Access points and Servers......................................................................................12
Configuring the Wireless Access Point........................................................................................12
Configuring the Server IP Addressing..........................................................................................13
Timeline and Budget............................................................................................................................13
Schedule of Activities......................................................................................................................13
Budgeting Table..............................................................................................................................14
Conclusion...........................................................................................................................................14
Bibliography.........................................................................................................................................16
Appendix A..........................................................................................................................................17
Industry Visit........................................................................................................................17
Coles.........................................................................................................................................17
..................................................................................................................................................17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Introduction
The report below makes an attempt to highlight the purpose of network designs, routing
protocols and access restrictions with the help of VLANs and how network infrastructures of
organizations can benefit from them. This report proposes a configured network for the company
Coles. The report starts with listing the requirements and scope of the project that has been derived
based on the component workflow requirements which have been acquired from the site visit
conducted on the Coles supermarkets in Melbourne and their headquarters. Thereafter, the logical
design diagram of the proposed network gets presented and appropriate justification is also
provided as per requirements of the business. Next the IP address details of various subnets are
provided in tabular format. After that the routing protocol used by the network is mentioned and
discussed before talking about the access privileges configured with ACL commands. Then the report
presents the timeline as well as budgeting estimates and ends with concluding notes.
Requirement Summary
The network of Coles Supermarkets needs to be built upon computerised infrastructure that use
remotely controlled components.
The network segment of supermarket is primarily meant to serve the controlled components like air
conditioners, heaters, lighting, cooling units and data collection from cooling counters provided by
LINDE Gas.
The remote access takes place through web access made available over wireless intranet of the
company, web access via modem, maintenance access via Wi-Fi.
The overall netwok is supposed to present an organized WAN infrastructure comprising of network
segments for both the supermarket located in Melbourne and the company office.
The network segment of the office building is meant to serve the workstations, servers and various
wireless devices that are being used.
The departments of the office building is supposed to be prohibited from accessing the departments
of the supermarket.
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Introduction
The report below makes an attempt to highlight the purpose of network designs, routing
protocols and access restrictions with the help of VLANs and how network infrastructures of
organizations can benefit from them. This report proposes a configured network for the company
Coles. The report starts with listing the requirements and scope of the project that has been derived
based on the component workflow requirements which have been acquired from the site visit
conducted on the Coles supermarkets in Melbourne and their headquarters. Thereafter, the logical
design diagram of the proposed network gets presented and appropriate justification is also
provided as per requirements of the business. Next the IP address details of various subnets are
provided in tabular format. After that the routing protocol used by the network is mentioned and
discussed before talking about the access privileges configured with ACL commands. Then the report
presents the timeline as well as budgeting estimates and ends with concluding notes.
Requirement Summary
The network of Coles Supermarkets needs to be built upon computerised infrastructure that use
remotely controlled components.
The network segment of supermarket is primarily meant to serve the controlled components like air
conditioners, heaters, lighting, cooling units and data collection from cooling counters provided by
LINDE Gas.
The remote access takes place through web access made available over wireless intranet of the
company, web access via modem, maintenance access via Wi-Fi.
The overall netwok is supposed to present an organized WAN infrastructure comprising of network
segments for both the supermarket located in Melbourne and the company office.
The network segment of the office building is meant to serve the workstations, servers and various
wireless devices that are being used.
The departments of the office building is supposed to be prohibited from accessing the departments
of the supermarket.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Network Design and Explanation
Logical Design Diagram
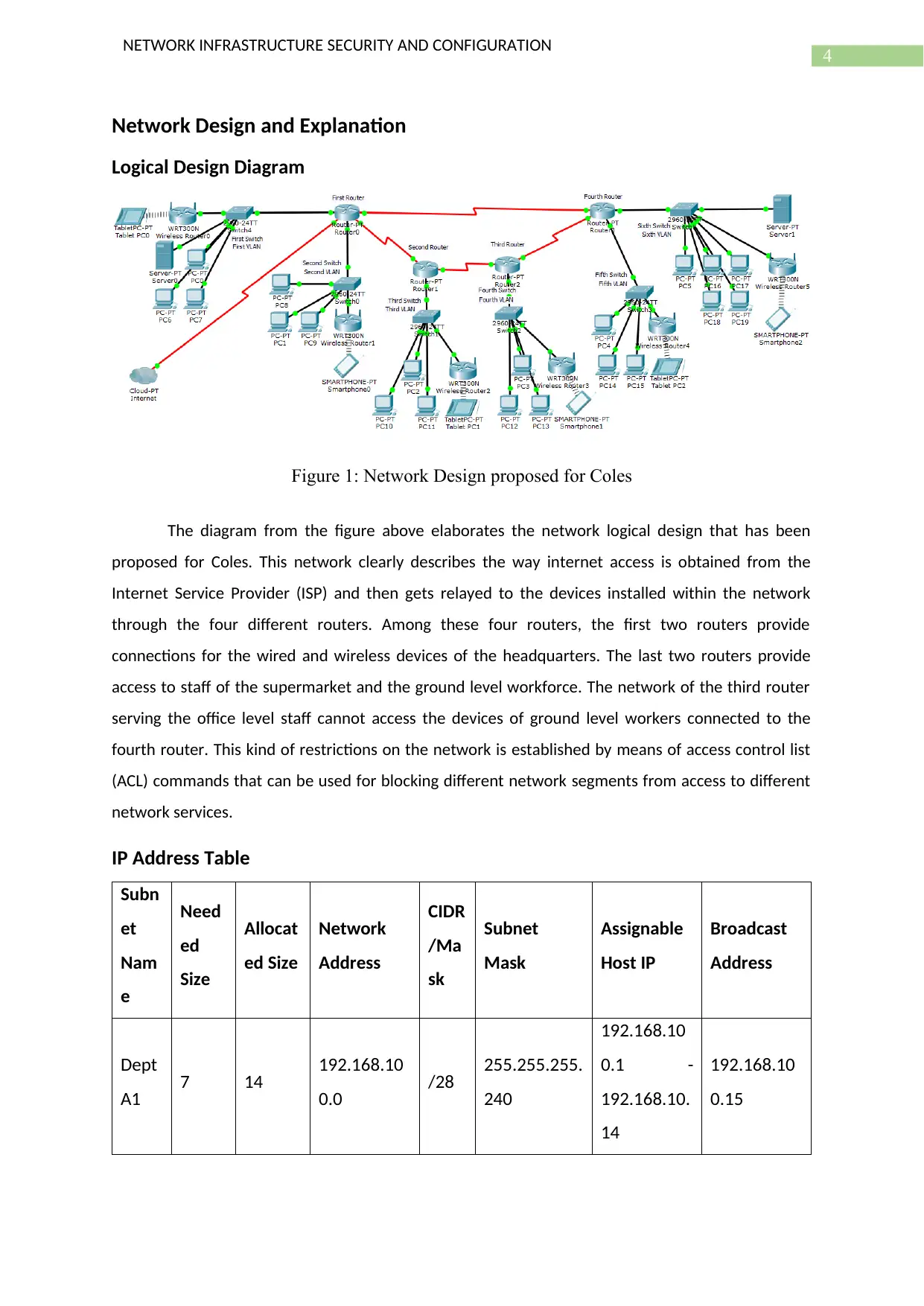
Figure 1: Network Design proposed for Coles
The diagram from the figure above elaborates the network logical design that has been
proposed for Coles. This network clearly describes the way internet access is obtained from the
Internet Service Provider (ISP) and then gets relayed to the devices installed within the network
through the four different routers. Among these four routers, the first two routers provide
connections for the wired and wireless devices of the headquarters. The last two routers provide
access to staff of the supermarket and the ground level workforce. The network of the third router
serving the office level staff cannot access the devices of ground level workers connected to the
fourth router. This kind of restrictions on the network is established by means of access control list
(ACL) commands that can be used for blocking different network segments from access to different
network services.
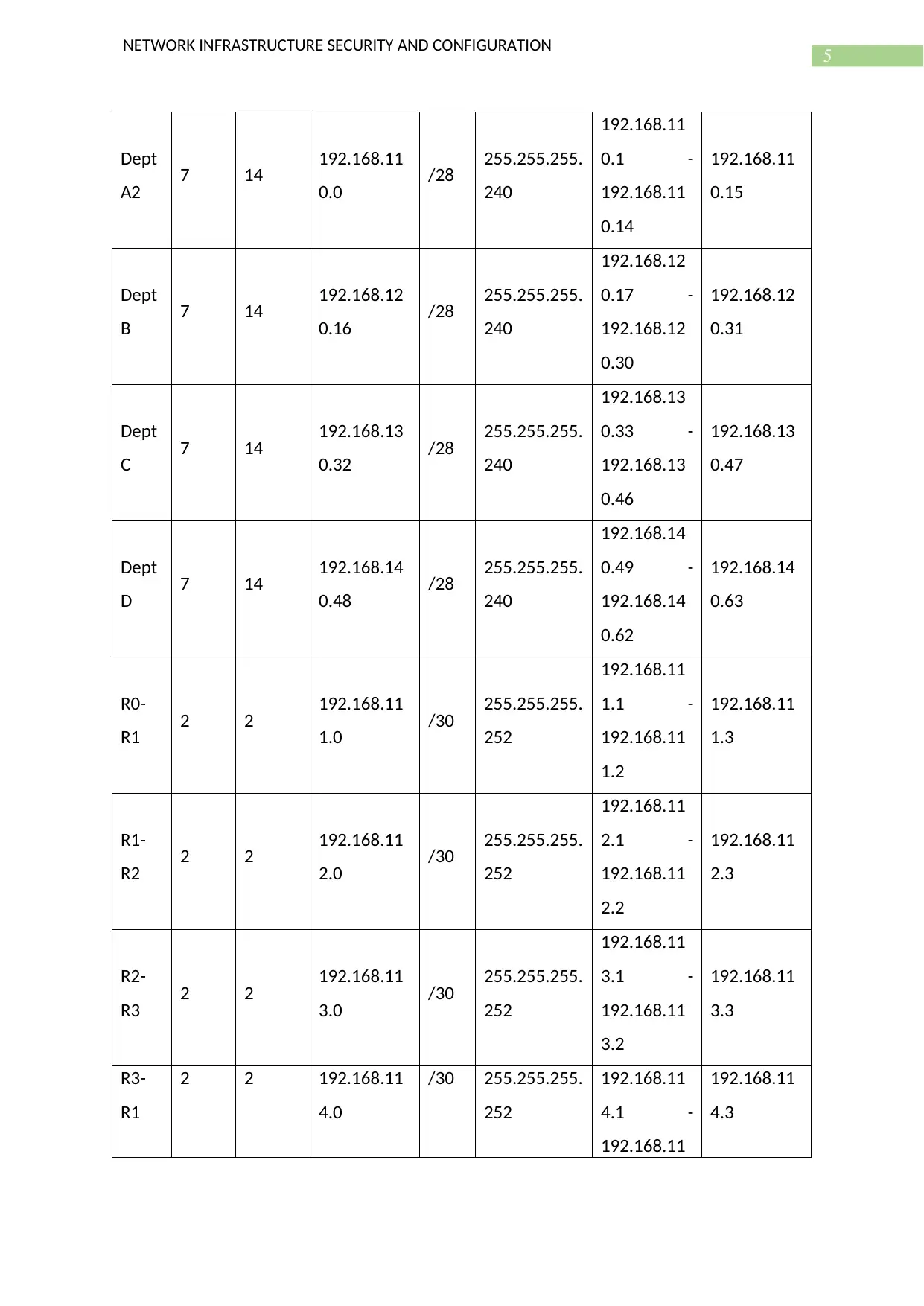
IP Address Table
Subn
et
Nam
e
Need
ed
Size
Allocat
ed Size
Network
Address
CIDR
/Ma
sk
Subnet
Mask
Assignable
Host IP
Broadcast
Address
Dept
A1 7 14 192.168.10
0.0 /28 255.255.255.
240
192.168.10
0.1 -
192.168.10.
14
192.168.10
0.15
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Network Design and Explanation
Logical Design Diagram
Figure 1: Network Design proposed for Coles
The diagram from the figure above elaborates the network logical design that has been
proposed for Coles. This network clearly describes the way internet access is obtained from the
Internet Service Provider (ISP) and then gets relayed to the devices installed within the network
through the four different routers. Among these four routers, the first two routers provide
connections for the wired and wireless devices of the headquarters. The last two routers provide
access to staff of the supermarket and the ground level workforce. The network of the third router
serving the office level staff cannot access the devices of ground level workers connected to the
fourth router. This kind of restrictions on the network is established by means of access control list
(ACL) commands that can be used for blocking different network segments from access to different
network services.
IP Address Table
Subn
et
Nam
e
Need
ed
Size
Allocat
ed Size
Network
Address
CIDR
/Ma
sk
Subnet
Mask
Assignable
Host IP
Broadcast
Address
Dept
A1 7 14 192.168.10
0.0 /28 255.255.255.
240
192.168.10
0.1 -
192.168.10.
14
192.168.10
0.15
5
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Dept
A2 7 14 192.168.11
0.0 /28 255.255.255.
240
192.168.11
0.1 -
192.168.11
0.14
192.168.11
0.15
Dept
B 7 14 192.168.12
0.16 /28 255.255.255.
240
192.168.12
0.17 -
192.168.12
0.30
192.168.12
0.31
Dept
C 7 14 192.168.13
0.32 /28 255.255.255.
240
192.168.13
0.33 -
192.168.13
0.46
192.168.13
0.47
Dept
D 7 14 192.168.14
0.48 /28 255.255.255.
240
192.168.14
0.49 -
192.168.14
0.62
192.168.14
0.63
R0-
R1 2 2 192.168.11
1.0 /30 255.255.255.
252
192.168.11
1.1 -
192.168.11
1.2
192.168.11
1.3
R1-
R2 2 2 192.168.11
2.0 /30 255.255.255.
252
192.168.11
2.1 -
192.168.11
2.2
192.168.11
2.3
R2-
R3 2 2 192.168.11
3.0 /30 255.255.255.
252
192.168.11
3.1 -
192.168.11
3.2
192.168.11
3.3
R3-
R1
2 2 192.168.11
4.0
/30 255.255.255.
252
192.168.11
4.1 -
192.168.11
192.168.11
4.3
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Dept
A2 7 14 192.168.11
0.0 /28 255.255.255.
240
192.168.11
0.1 -
192.168.11
0.14
192.168.11
0.15
Dept
B 7 14 192.168.12
0.16 /28 255.255.255.
240
192.168.12
0.17 -
192.168.12
0.30
192.168.12
0.31
Dept
C 7 14 192.168.13
0.32 /28 255.255.255.
240
192.168.13
0.33 -
192.168.13
0.46
192.168.13
0.47
Dept
D 7 14 192.168.14
0.48 /28 255.255.255.
240
192.168.14
0.49 -
192.168.14
0.62
192.168.14
0.63
R0-
R1 2 2 192.168.11
1.0 /30 255.255.255.
252
192.168.11
1.1 -
192.168.11
1.2
192.168.11
1.3
R1-
R2 2 2 192.168.11
2.0 /30 255.255.255.
252
192.168.11
2.1 -
192.168.11
2.2
192.168.11
2.3
R2-
R3 2 2 192.168.11
3.0 /30 255.255.255.
252
192.168.11
3.1 -
192.168.11
3.2
192.168.11
3.3
R3-
R1
2 2 192.168.11
4.0
/30 255.255.255.
252
192.168.11
4.1 -
192.168.11
192.168.11
4.3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
4.2
Routing Protocol used and Network Security
Routing Protocol
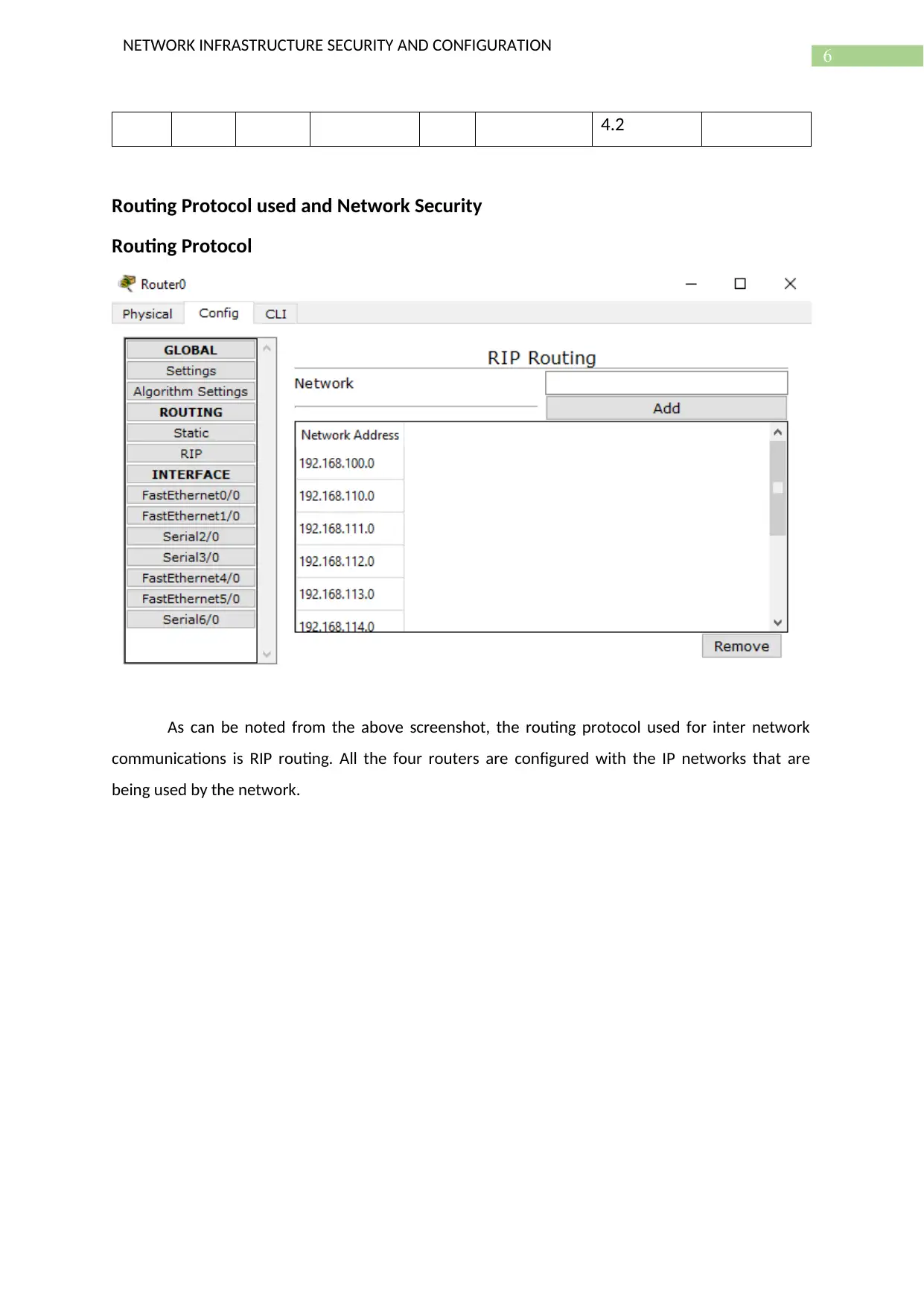
As can be noted from the above screenshot, the routing protocol used for inter network
communications is RIP routing. All the four routers are configured with the IP networks that are
being used by the network.
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
4.2
Routing Protocol used and Network Security
Routing Protocol
As can be noted from the above screenshot, the routing protocol used for inter network
communications is RIP routing. All the four routers are configured with the IP networks that are
being used by the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Access Restrictions with ACL commands
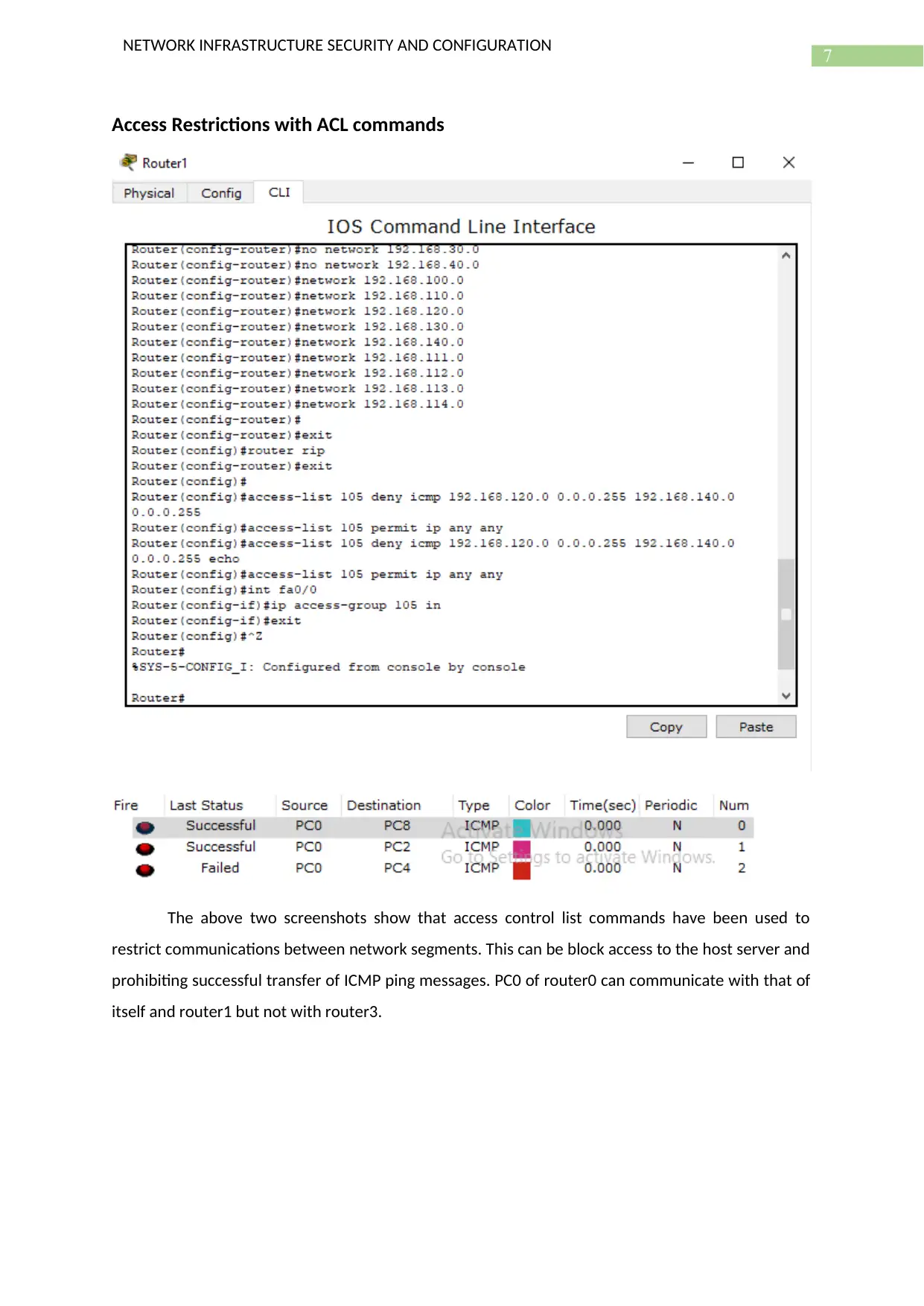
The above two screenshots show that access control list commands have been used to
restrict communications between network segments. This can be block access to the host server and
prohibiting successful transfer of ICMP ping messages. PC0 of router0 can communicate with that of
itself and router1 but not with router3.
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Access Restrictions with ACL commands
The above two screenshots show that access control list commands have been used to
restrict communications between network segments. This can be block access to the host server and
prohibiting successful transfer of ICMP ping messages. PC0 of router0 can communicate with that of
itself and router1 but not with router3.

8
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Configuring the Network
Configuring the Router
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#router rip
Router(config-router)#network 192.168.100.0
Router(config-router)#network 192.168.110.0
Router(config-router)#network 192.168.120.0
Router(config-router)#network 192.168.130.0
Router(config-router)#network 192.168.140.0
Router(config-router)#network 192.168.111.0
Router(config-router)#network 192.168.112.0
Router(config-router)#network 192.168.113.0
Router(config-router)#network 192.168.114.0
Router(config-router)#
Router(config-router)#exit
Router(config)#router rip
Router(config-router)#exit
Router(config)#
Router(config)#access-list 105 deny icmp 192.168.120.0 0.0.0.255 192.168.140.0 0.0.0.255
Router(config)#access-list 105 permit ip any any
Router(config)#access-list 105 deny icmp 192.168.120.0 0.0.0.255 192.168.140.0 0.0.0.255 echo
Router(config)#access-list 105 permit ip any any
Router(config)#int fa0/0
Router(config-if)#ip access-group 105 in
Router(config-if)#exit
Router(config)#^Z
Router#
%SYS-5-CONFIG_I: Configured from console by console
Router#
Router#wr
Building configuration...
[OK]
Router#
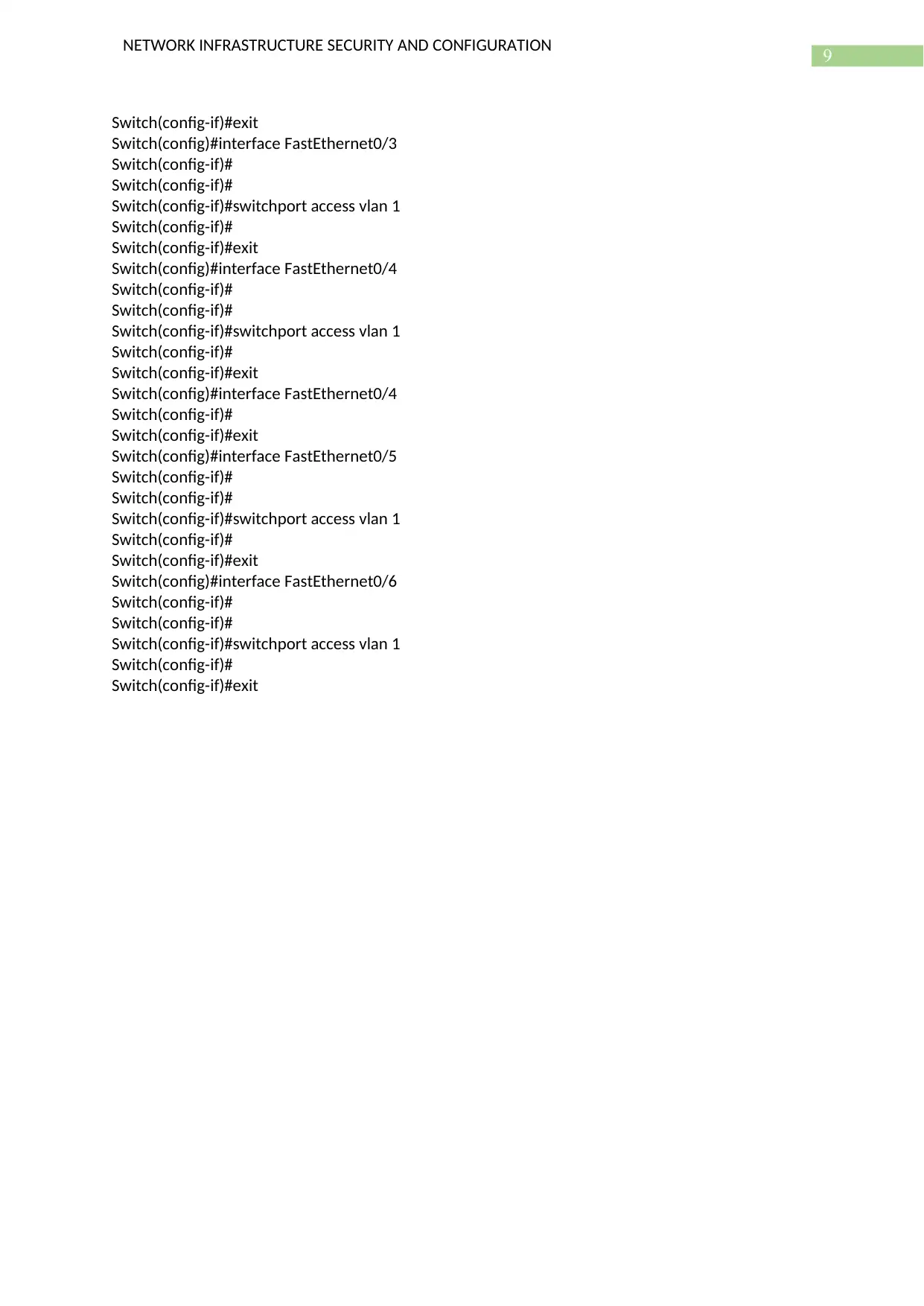
Configuring the Switch
Switch>enable
Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#
Switch(config)#interface FastEthernet0/2
Switch(config-if)#
Switch(config-if)#
Switch(config-if)#switchport access vlan 1
Switch(config-if)#
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Configuring the Network
Configuring the Router
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#router rip
Router(config-router)#network 192.168.100.0
Router(config-router)#network 192.168.110.0
Router(config-router)#network 192.168.120.0
Router(config-router)#network 192.168.130.0
Router(config-router)#network 192.168.140.0
Router(config-router)#network 192.168.111.0
Router(config-router)#network 192.168.112.0
Router(config-router)#network 192.168.113.0
Router(config-router)#network 192.168.114.0
Router(config-router)#
Router(config-router)#exit
Router(config)#router rip
Router(config-router)#exit
Router(config)#
Router(config)#access-list 105 deny icmp 192.168.120.0 0.0.0.255 192.168.140.0 0.0.0.255
Router(config)#access-list 105 permit ip any any
Router(config)#access-list 105 deny icmp 192.168.120.0 0.0.0.255 192.168.140.0 0.0.0.255 echo
Router(config)#access-list 105 permit ip any any
Router(config)#int fa0/0
Router(config-if)#ip access-group 105 in
Router(config-if)#exit
Router(config)#^Z
Router#
%SYS-5-CONFIG_I: Configured from console by console
Router#
Router#wr
Building configuration...
[OK]
Router#
Configuring the Switch
Switch>enable
Switch#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#
Switch(config)#interface FastEthernet0/2
Switch(config-if)#
Switch(config-if)#
Switch(config-if)#switchport access vlan 1
Switch(config-if)#
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Switch(config-if)#exit
Switch(config)#interface FastEthernet0/3
Switch(config-if)#
Switch(config-if)#
Switch(config-if)#switchport access vlan 1
Switch(config-if)#
Switch(config-if)#exit
Switch(config)#interface FastEthernet0/4
Switch(config-if)#
Switch(config-if)#
Switch(config-if)#switchport access vlan 1
Switch(config-if)#
Switch(config-if)#exit
Switch(config)#interface FastEthernet0/4
Switch(config-if)#
Switch(config-if)#exit
Switch(config)#interface FastEthernet0/5
Switch(config-if)#
Switch(config-if)#
Switch(config-if)#switchport access vlan 1
Switch(config-if)#
Switch(config-if)#exit
Switch(config)#interface FastEthernet0/6
Switch(config-if)#
Switch(config-if)#
Switch(config-if)#switchport access vlan 1
Switch(config-if)#
Switch(config-if)#exit
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Switch(config-if)#exit
Switch(config)#interface FastEthernet0/3
Switch(config-if)#
Switch(config-if)#
Switch(config-if)#switchport access vlan 1
Switch(config-if)#
Switch(config-if)#exit
Switch(config)#interface FastEthernet0/4
Switch(config-if)#
Switch(config-if)#
Switch(config-if)#switchport access vlan 1
Switch(config-if)#
Switch(config-if)#exit
Switch(config)#interface FastEthernet0/4
Switch(config-if)#
Switch(config-if)#exit
Switch(config)#interface FastEthernet0/5
Switch(config-if)#
Switch(config-if)#
Switch(config-if)#switchport access vlan 1
Switch(config-if)#
Switch(config-if)#exit
Switch(config)#interface FastEthernet0/6
Switch(config-if)#
Switch(config-if)#
Switch(config-if)#switchport access vlan 1
Switch(config-if)#
Switch(config-if)#exit
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
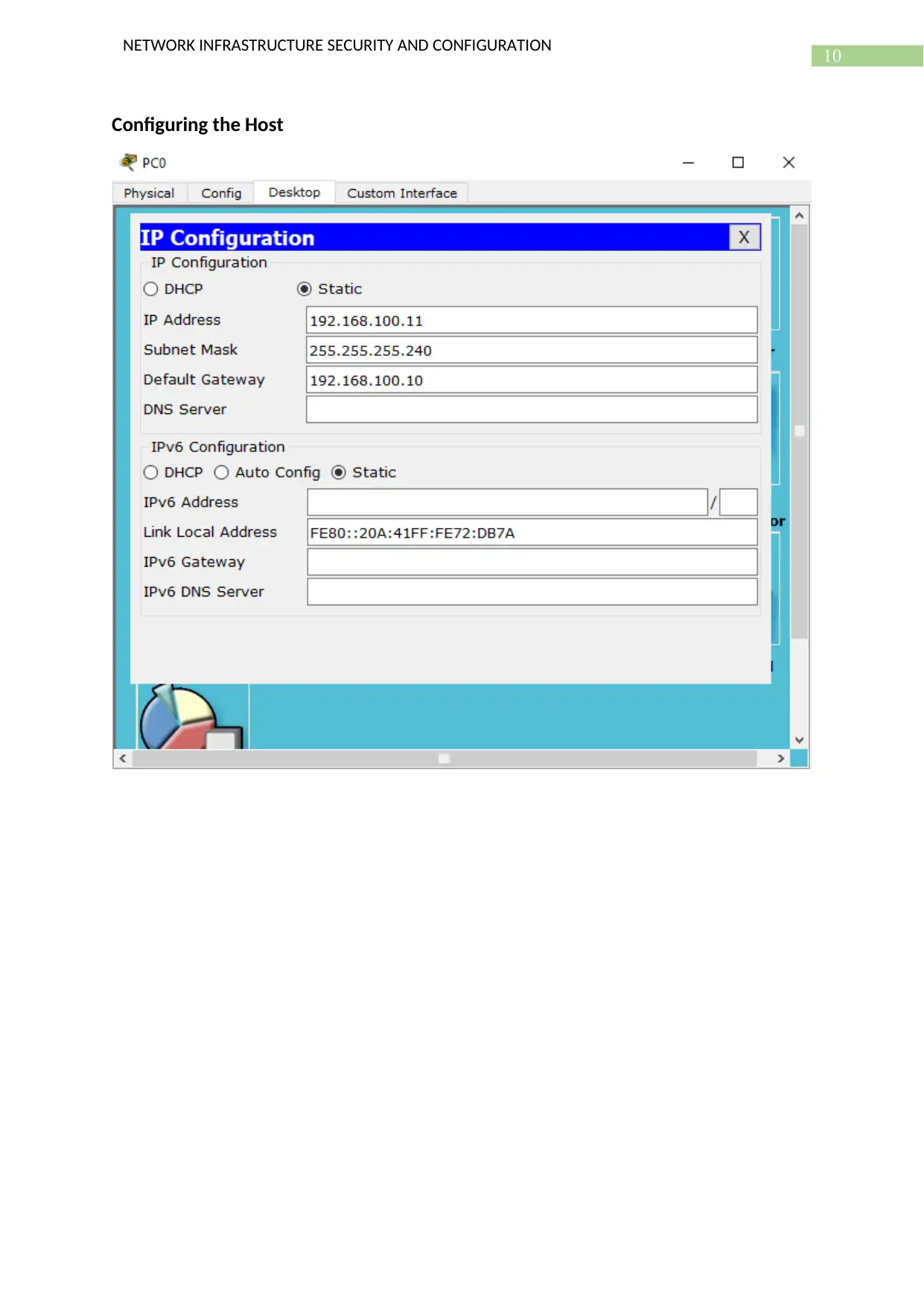
Configuring the Host
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Configuring the Host
11
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
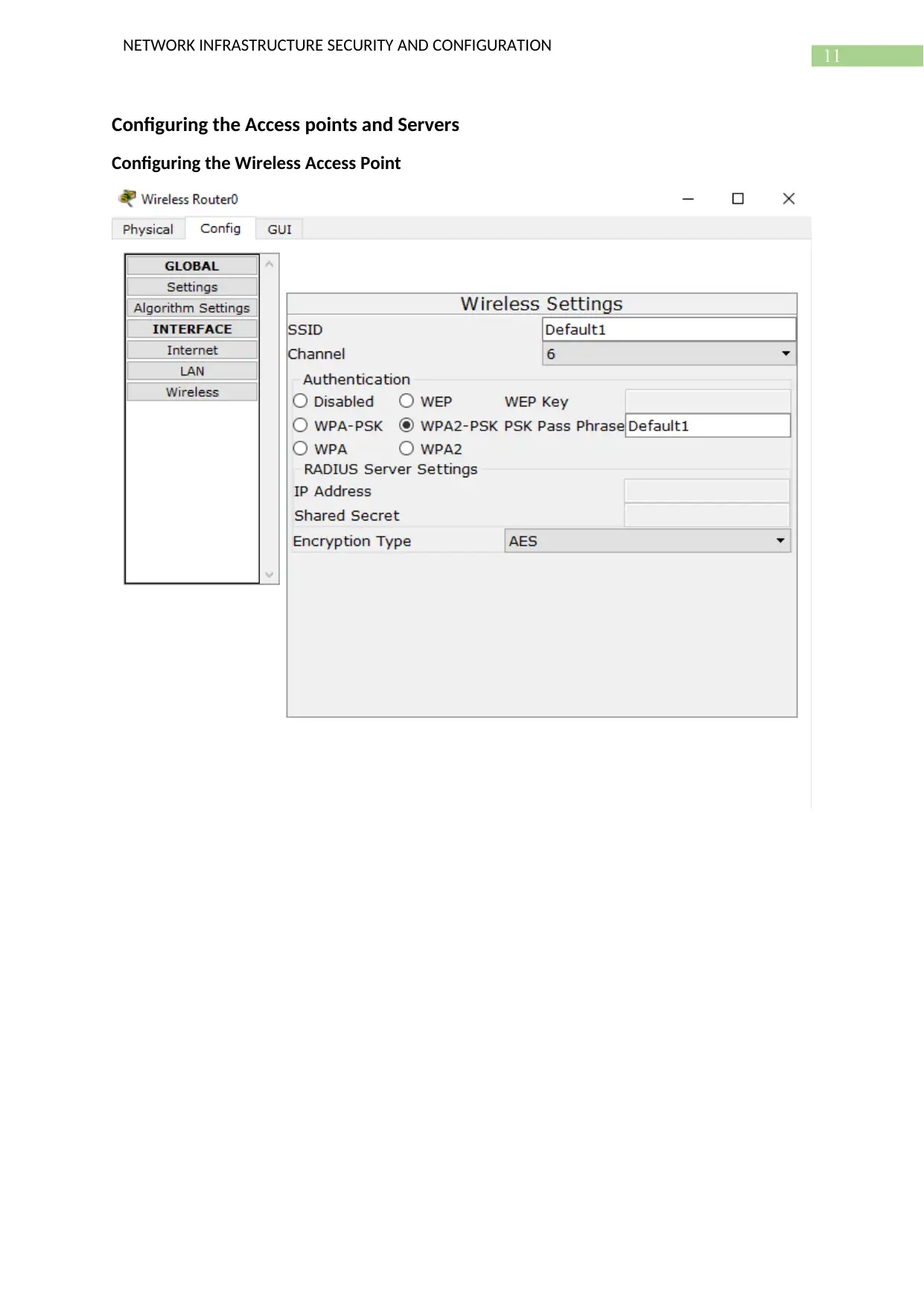
Configuring the Access points and Servers
Configuring the Wireless Access Point
NETWORK INFRASTRUCTURE SECURITY AND CONFIGURATION
Configuring the Access points and Servers
Configuring the Wireless Access Point
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





