Report on Network Management and Security for STP Limited's Business
VerifiedAdded on 2020/05/11
|14
|3452
|119
Report
AI Summary
This report provides a comprehensive analysis of network management and security for STP Limited, a kitchen cabinet manufacturer with multiple locations. The report begins with a project background, outlining the need for an upgraded information system to enhance core business operations, including accounting and stock control. It then delves into network security, covering data protection, ISP security, mobile device security (including WLAN attacks and BYOD risks), and the importance of people, products, policies, and procedures. The report also details a plan for hardware purchases, including acquisition strategies, end-user feedback, and asset register considerations. Business continuity is addressed through data backup strategies, physical security measures, and the importance of successful planning and stock control systems. Risk management is examined, covering security policies, training and awareness programs, and technology integration. The report concludes with recommendations for STP Limited to improve its network security and business continuity, ensuring the protection of sensitive data and the smooth operation of its business activities.

Running head: NETWORK MANAGEMENT AND SECURITY
Network Management and Security
Name of the Student
Name of the University
Author’s note
Network Management and Security
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK MANAGEMENT AND SECURITY
Table of Contents
1.0. Project Background.............................................................................................................2
1.1. Network Project Background..........................................................................................2
1.2. Project enhancing the future growth of STP...................................................................2
1.2.1. Project scope............................................................................................................2
1.2.2. Project goal...............................................................................................................3
1.2.3. Strategic alignment of project..................................................................................3
2.0. Network Security................................................................................................................4
2.1. Securing data...................................................................................................................4
2.1.1. People, products, policies and procedures...............................................................4
2.1.2. ISP security and privacy considerations..................................................................4
2.2. Mobile device security....................................................................................................4
2.2.1. Wireless Local Area Network (WLAN) attacks......................................................4
2.2.2. BYOD risks..............................................................................................................5
3. Plan for hardware purchases..................................................................................................5
3.1. Acquisition of new hardware..........................................................................................5
3.2. End-user feedback and reviews.......................................................................................5
3.3. Purchasing strategies.......................................................................................................6
3.4. Asset register...................................................................................................................6
4.0. Business continuity.............................................................................................................7
4.1. Data Backup....................................................................................................................7
4.2. Physical Security.............................................................................................................7
4.3. Successful planning.........................................................................................................8
4.4. Stock Control system......................................................................................................8
5.0. Risk management................................................................................................................8
5.1. Security Policy................................................................................................................8
5.2. Training and awareness...................................................................................................9
5.3. Integration technology....................................................................................................9
6.0. Conclusions.........................................................................................................................9
7.0. Recommendations...............................................................................................................9
8.0. Bibliography......................................................................................................................11
Table of Contents
1.0. Project Background.............................................................................................................2
1.1. Network Project Background..........................................................................................2
1.2. Project enhancing the future growth of STP...................................................................2
1.2.1. Project scope............................................................................................................2
1.2.2. Project goal...............................................................................................................3
1.2.3. Strategic alignment of project..................................................................................3
2.0. Network Security................................................................................................................4
2.1. Securing data...................................................................................................................4
2.1.1. People, products, policies and procedures...............................................................4
2.1.2. ISP security and privacy considerations..................................................................4
2.2. Mobile device security....................................................................................................4
2.2.1. Wireless Local Area Network (WLAN) attacks......................................................4
2.2.2. BYOD risks..............................................................................................................5
3. Plan for hardware purchases..................................................................................................5
3.1. Acquisition of new hardware..........................................................................................5
3.2. End-user feedback and reviews.......................................................................................5
3.3. Purchasing strategies.......................................................................................................6
3.4. Asset register...................................................................................................................6
4.0. Business continuity.............................................................................................................7
4.1. Data Backup....................................................................................................................7
4.2. Physical Security.............................................................................................................7
4.3. Successful planning.........................................................................................................8
4.4. Stock Control system......................................................................................................8
5.0. Risk management................................................................................................................8
5.1. Security Policy................................................................................................................8
5.2. Training and awareness...................................................................................................9
5.3. Integration technology....................................................................................................9
6.0. Conclusions.........................................................................................................................9
7.0. Recommendations...............................................................................................................9
8.0. Bibliography......................................................................................................................11

2NETWORK MANAGEMENT AND SECURITY
1.0. Project Background
1.1. Network Project Background
STP Limited manufactures kitchen cabinets and they have the four offices across
Lithgow, Sydney, Bathurst and Wollongong. They are popular in manufacturing drawer
fronts and the cupboards to the customers. STP has decided to upgrade their existing
information system and embellish the core business operations. The business operations can
be facilitated greatly by the accounting system and the stock control system. The information
system has been planned to rejuvenate and thus the website management system and the
customer management system of STP Limited can be benefitted. The report is showcasing the
adoption of information system in the STP Limited premises. The report will explain the
various aspects of like the scope of the current project along with the prerequisites and the
project expectations correlated with the project. Various kinds of issues and problems have
upheld regarding unskilled employees, various kinds of threats and the vulnerabilities
associated with cloud technology and business procedures have risen. The inefficiency
regarding the product manufacturing has been focussed. The report has focussed mainly on
the staffs; the staffs must have the sound knowledge so that they can efficiently serve the
customers and the company as well.
1.2. Project enhancing the future growth of STP
1.2.1. Project scope
The project scope of STP Limited states that the database and the system must be
installed and configured in an effective way in Lithgow, Bathurst, Sydney and Wollongong.
The network connectivity of the company via ADSL (Asymmetric Digital Subscriber Line)
connected with the help of the modem and with the help of switch can help to deliver the
wireless network connectivity to the company. This wireless network connectivity aids to get
1.0. Project Background
1.1. Network Project Background
STP Limited manufactures kitchen cabinets and they have the four offices across
Lithgow, Sydney, Bathurst and Wollongong. They are popular in manufacturing drawer
fronts and the cupboards to the customers. STP has decided to upgrade their existing
information system and embellish the core business operations. The business operations can
be facilitated greatly by the accounting system and the stock control system. The information
system has been planned to rejuvenate and thus the website management system and the
customer management system of STP Limited can be benefitted. The report is showcasing the
adoption of information system in the STP Limited premises. The report will explain the
various aspects of like the scope of the current project along with the prerequisites and the
project expectations correlated with the project. Various kinds of issues and problems have
upheld regarding unskilled employees, various kinds of threats and the vulnerabilities
associated with cloud technology and business procedures have risen. The inefficiency
regarding the product manufacturing has been focussed. The report has focussed mainly on
the staffs; the staffs must have the sound knowledge so that they can efficiently serve the
customers and the company as well.
1.2. Project enhancing the future growth of STP
1.2.1. Project scope
The project scope of STP Limited states that the database and the system must be
installed and configured in an effective way in Lithgow, Bathurst, Sydney and Wollongong.
The network connectivity of the company via ADSL (Asymmetric Digital Subscriber Line)
connected with the help of the modem and with the help of switch can help to deliver the
wireless network connectivity to the company. This wireless network connectivity aids to get
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK MANAGEMENT AND SECURITY
connected to BYOD (Bring Your Device). The network connection has been developed in
such a way that the employees across the four locations can connect with each other and can
communicate which can be useful to know the stock availability of the company. The project
also shows light on the employees, the employees must have the proper technical knowledge
so that they can solve the issues quickly and serve the customers well, and the technical
knowledge can scale the business activities of STP. At the moment they only have one
technical staff. The technology can help to manage the website and the web staffs.
1.2.2. Project goal
The project goal is associated with the effective tools that the management staffs and
the technical staffs must use for their business purposes and this will help the technical staffs
of the enterprise to get the desired benefits, the network equipment has been discussed that
has the capability to increase the productivity. The project goal also involves the customer
employees’ relationship that can be helpful for both the business, for the products.
1.2.3. Strategic alignment of project
SWOT analysis can prove to be beneficial to the STP Limited as that can help to
recognize the strength, the weakness, the threats and the opportunities of the company. This
SWOT analysis will help to know the possible impact of the information system and the
cloud computing. The SWOT analysis has been discussed below in the tabular form.
Table 2.4 SWOT analysis of STP Limited network project
Internal
POSITIVE NEGATIVE
Strengths Weaknesses
Customer base
Advanced Sales targets
The cloud-based applications
Hard-working employees
Insider Threat
Not technically skilled employees
Not following specific rules and
procedures
External Opportunities Threats
The connection between the
employees and the customers.
The integration of information system
The empowerment of the employees
The financial information leaks and
the customer information leaks.
connected to BYOD (Bring Your Device). The network connection has been developed in
such a way that the employees across the four locations can connect with each other and can
communicate which can be useful to know the stock availability of the company. The project
also shows light on the employees, the employees must have the proper technical knowledge
so that they can solve the issues quickly and serve the customers well, and the technical
knowledge can scale the business activities of STP. At the moment they only have one
technical staff. The technology can help to manage the website and the web staffs.
1.2.2. Project goal
The project goal is associated with the effective tools that the management staffs and
the technical staffs must use for their business purposes and this will help the technical staffs
of the enterprise to get the desired benefits, the network equipment has been discussed that
has the capability to increase the productivity. The project goal also involves the customer
employees’ relationship that can be helpful for both the business, for the products.
1.2.3. Strategic alignment of project
SWOT analysis can prove to be beneficial to the STP Limited as that can help to
recognize the strength, the weakness, the threats and the opportunities of the company. This
SWOT analysis will help to know the possible impact of the information system and the
cloud computing. The SWOT analysis has been discussed below in the tabular form.
Table 2.4 SWOT analysis of STP Limited network project
Internal
POSITIVE NEGATIVE
Strengths Weaknesses
Customer base
Advanced Sales targets
The cloud-based applications
Hard-working employees
Insider Threat
Not technically skilled employees
Not following specific rules and
procedures
External Opportunities Threats
The connection between the
employees and the customers.
The integration of information system
The empowerment of the employees
The financial information leaks and
the customer information leaks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORK MANAGEMENT AND SECURITY
2.0. Network Security
2.1. Securing data
In STP Limited the information system can play a significant role to enhance the
business activities to the core. The information security can be both internal and external
(Ciampa 2015). The internal layers can prove to be beneficial as the regulations regarding the
products; people can be established and configured in the premises to achieve the
productivity.
2.1.1. People, products, policies and procedures
STP Limited’s information system can prosper the business activities via the Internet
connection. Certain rules and procedures can help to business in a secured manner and in
smooth manner (Queensland Government 2016). The policies and the procedures can assist
in storing and access the data.
2.1.2. ISP security and privacy considerations
STP Limited is heavily dependent on the Internet connection to conduct the business
procedures, also along with that, the secure WAN connection can help to provide the security
against the vulnerable threats and risks (Telstra 2016). The BigPond Network is capable to
provide the secured network and STP Limited by implementing the security feature can
lessen the negative impacts of cyber threats. The ISP is capable to conduct the payment
system and that in agile, efficient and secure manner.
2.2. Mobile device security
2.2.1. Wireless Local Area Network (WLAN) attacks
The wireless networking is full of risks; the employees generally prefer to conduct the
business operations via this wireless network (Gupta & Hammond 2005). The hackers taking
advantage of the insecure weak network can access the system and in this way, the sensitive
2.0. Network Security
2.1. Securing data
In STP Limited the information system can play a significant role to enhance the
business activities to the core. The information security can be both internal and external
(Ciampa 2015). The internal layers can prove to be beneficial as the regulations regarding the
products; people can be established and configured in the premises to achieve the
productivity.
2.1.1. People, products, policies and procedures
STP Limited’s information system can prosper the business activities via the Internet
connection. Certain rules and procedures can help to business in a secured manner and in
smooth manner (Queensland Government 2016). The policies and the procedures can assist
in storing and access the data.
2.1.2. ISP security and privacy considerations
STP Limited is heavily dependent on the Internet connection to conduct the business
procedures, also along with that, the secure WAN connection can help to provide the security
against the vulnerable threats and risks (Telstra 2016). The BigPond Network is capable to
provide the secured network and STP Limited by implementing the security feature can
lessen the negative impacts of cyber threats. The ISP is capable to conduct the payment
system and that in agile, efficient and secure manner.
2.2. Mobile device security
2.2.1. Wireless Local Area Network (WLAN) attacks
The wireless networking is full of risks; the employees generally prefer to conduct the
business operations via this wireless network (Gupta & Hammond 2005). The hackers taking
advantage of the insecure weak network can access the system and in this way, the sensitive

5NETWORK MANAGEMENT AND SECURITY
information can get stolen. The WLAN attacks can only be lessened by applying certain
policies and procedures.
2.2.2. BYOD risks
The financial risks can incur due to the BYOD risks and because of this, the personal
information can get disclosed. The malicious activities involved with the software and the
operating system are also the matter of concern for the BYOD risk (Ciampa 2015). The
BYOD should be installed in a most effective way to get the maximum productivity and
safety from the data breaches.
3. Plan for hardware purchases
3.1. Acquisition of new hardware
The new hardware change in STP Limited has the capability to revolutionize the
production and the productivity (Batenburg et al 2015). The new hardware can facilitate the
strategies and the policies that can help to check the disruption and various production
problems.
3.2. End-user feedback and reviews
The software applications are developing day by day and for this reason, they
generally do not get well with the existing hardware of STP Limiteds (Haring ND). STP must
keep in mind the security breaches that can occur due to the information system. The security
breaches seem quite obvious. STP can stay protected and can protect their system by simply
installing the antivirus software to their system (Crawford et al 2005). The end user has the
chance to examine risks and basis on which the management team of STP can decide the
effective solution that can furnish the business growth.
information can get stolen. The WLAN attacks can only be lessened by applying certain
policies and procedures.
2.2.2. BYOD risks
The financial risks can incur due to the BYOD risks and because of this, the personal
information can get disclosed. The malicious activities involved with the software and the
operating system are also the matter of concern for the BYOD risk (Ciampa 2015). The
BYOD should be installed in a most effective way to get the maximum productivity and
safety from the data breaches.
3. Plan for hardware purchases
3.1. Acquisition of new hardware
The new hardware change in STP Limited has the capability to revolutionize the
production and the productivity (Batenburg et al 2015). The new hardware can facilitate the
strategies and the policies that can help to check the disruption and various production
problems.
3.2. End-user feedback and reviews
The software applications are developing day by day and for this reason, they
generally do not get well with the existing hardware of STP Limiteds (Haring ND). STP must
keep in mind the security breaches that can occur due to the information system. The security
breaches seem quite obvious. STP can stay protected and can protect their system by simply
installing the antivirus software to their system (Crawford et al 2005). The end user has the
chance to examine risks and basis on which the management team of STP can decide the
effective solution that can furnish the business growth.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6NETWORK MANAGEMENT AND SECURITY
3.3. Purchasing strategies
STP must use the monetary planning for the enterprise considering various aspects.
They must save their precious money to purchase the latest hardware that can be helpful to
stay protected against the malware attacks. The members of the company can collectively
take the best decision to make the best strategy for the business. The members should take the
suppliers into considerations and via asset register; the effective profitable hardware chosen
can assist in choosing the best hardware solutions for the betterment of the enterprise.
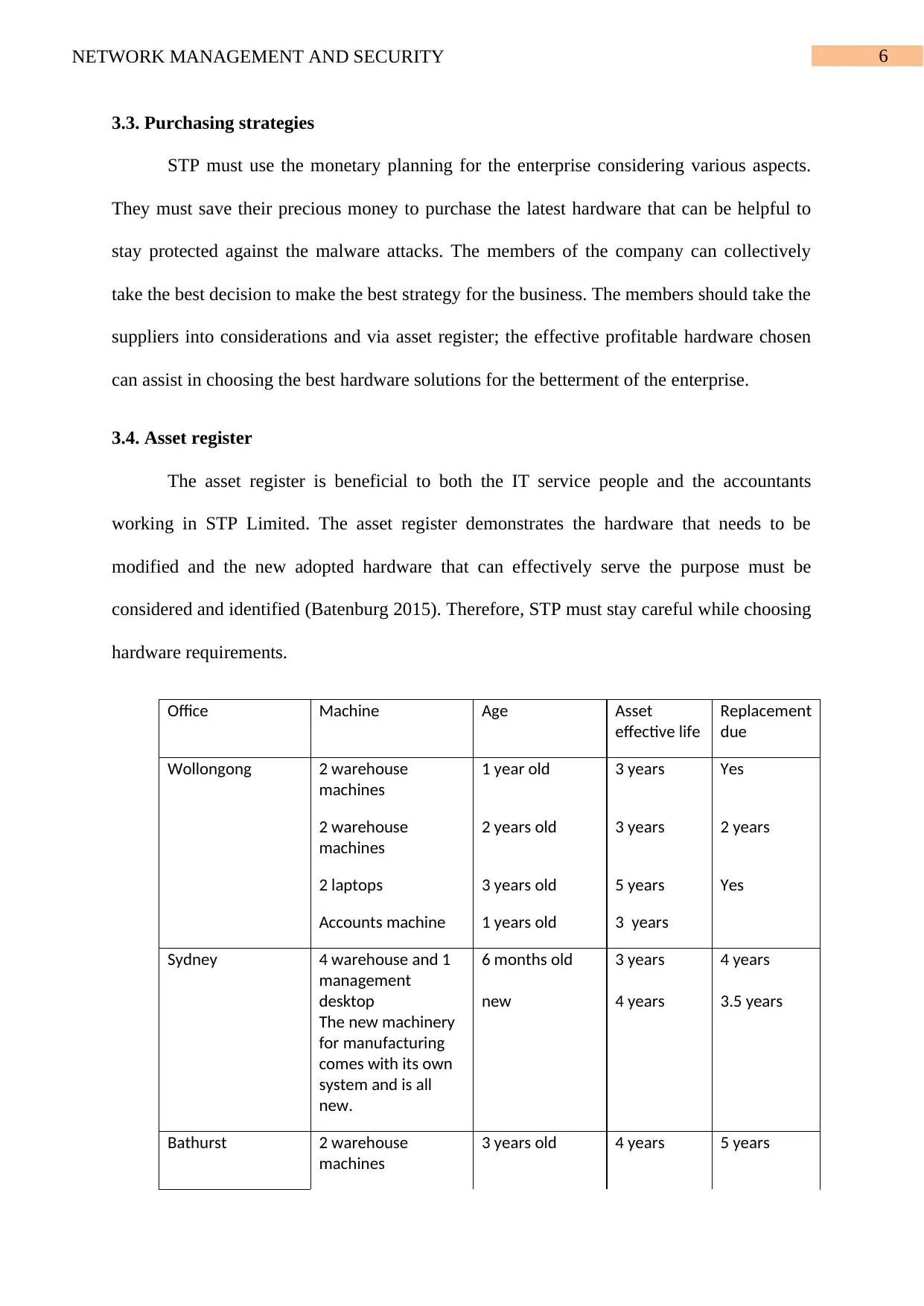
3.4. Asset register
The asset register is beneficial to both the IT service people and the accountants
working in STP Limited. The asset register demonstrates the hardware that needs to be
modified and the new adopted hardware that can effectively serve the purpose must be
considered and identified (Batenburg 2015). Therefore, STP must stay careful while choosing
hardware requirements.
Office Machine Age Asset
effective life
Replacement
due
Wollongong 2 warehouse
machines
1 year old 3 years Yes
2 warehouse
machines
2 years old 3 years 2 years
2 laptops 3 years old 5 years Yes
Accounts machine 1 years old 3 years
Sydney 4 warehouse and 1
management
desktop
The new machinery
for manufacturing
comes with its own
system and is all
new.
6 months old
new
3 years
4 years
4 years
3.5 years
Bathurst 2 warehouse
machines
3 years old 4 years 5 years
3.3. Purchasing strategies
STP must use the monetary planning for the enterprise considering various aspects.
They must save their precious money to purchase the latest hardware that can be helpful to
stay protected against the malware attacks. The members of the company can collectively
take the best decision to make the best strategy for the business. The members should take the
suppliers into considerations and via asset register; the effective profitable hardware chosen
can assist in choosing the best hardware solutions for the betterment of the enterprise.
3.4. Asset register
The asset register is beneficial to both the IT service people and the accountants
working in STP Limited. The asset register demonstrates the hardware that needs to be
modified and the new adopted hardware that can effectively serve the purpose must be
considered and identified (Batenburg 2015). Therefore, STP must stay careful while choosing
hardware requirements.
Office Machine Age Asset
effective life
Replacement
due
Wollongong 2 warehouse
machines
1 year old 3 years Yes
2 warehouse
machines
2 years old 3 years 2 years
2 laptops 3 years old 5 years Yes
Accounts machine 1 years old 3 years
Sydney 4 warehouse and 1
management
desktop
The new machinery
for manufacturing
comes with its own
system and is all
new.
6 months old
new
3 years
4 years
4 years
3.5 years
Bathurst 2 warehouse
machines
3 years old 4 years 5 years
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
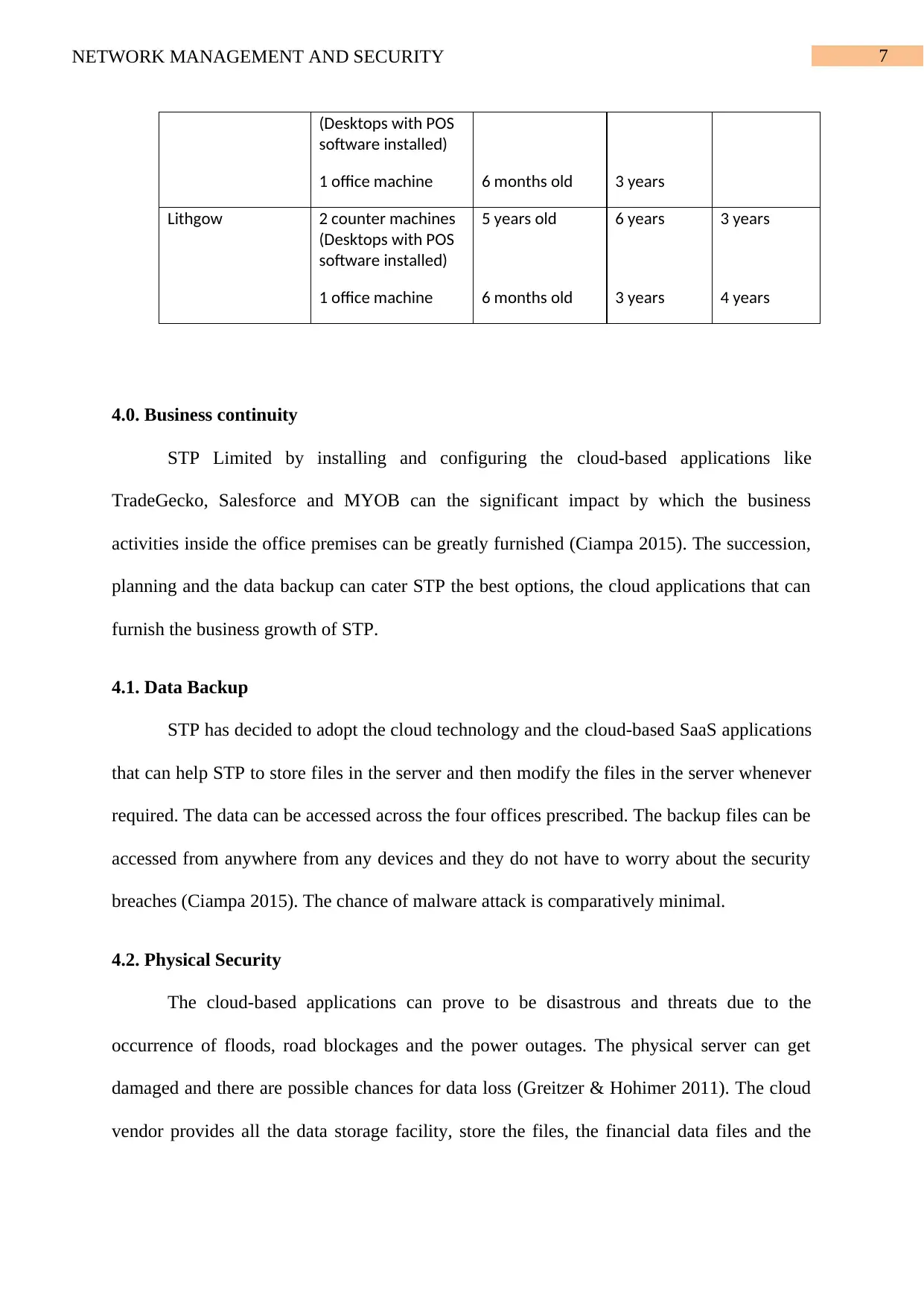
7NETWORK MANAGEMENT AND SECURITY
(Desktops with POS
software installed)
1 office machine 6 months old 3 years
Lithgow 2 counter machines
(Desktops with POS
software installed)
5 years old 6 years 3 years
1 office machine 6 months old 3 years 4 years
4.0. Business continuity
STP Limited by installing and configuring the cloud-based applications like
TradeGecko, Salesforce and MYOB can the significant impact by which the business
activities inside the office premises can be greatly furnished (Ciampa 2015). The succession,
planning and the data backup can cater STP the best options, the cloud applications that can
furnish the business growth of STP.
4.1. Data Backup
STP has decided to adopt the cloud technology and the cloud-based SaaS applications
that can help STP to store files in the server and then modify the files in the server whenever
required. The data can be accessed across the four offices prescribed. The backup files can be
accessed from anywhere from any devices and they do not have to worry about the security
breaches (Ciampa 2015). The chance of malware attack is comparatively minimal.
4.2. Physical Security
The cloud-based applications can prove to be disastrous and threats due to the
occurrence of floods, road blockages and the power outages. The physical server can get
damaged and there are possible chances for data loss (Greitzer & Hohimer 2011). The cloud
vendor provides all the data storage facility, store the files, the financial data files and the
(Desktops with POS
software installed)
1 office machine 6 months old 3 years
Lithgow 2 counter machines
(Desktops with POS
software installed)
5 years old 6 years 3 years
1 office machine 6 months old 3 years 4 years
4.0. Business continuity
STP Limited by installing and configuring the cloud-based applications like
TradeGecko, Salesforce and MYOB can the significant impact by which the business
activities inside the office premises can be greatly furnished (Ciampa 2015). The succession,
planning and the data backup can cater STP the best options, the cloud applications that can
furnish the business growth of STP.
4.1. Data Backup
STP has decided to adopt the cloud technology and the cloud-based SaaS applications
that can help STP to store files in the server and then modify the files in the server whenever
required. The data can be accessed across the four offices prescribed. The backup files can be
accessed from anywhere from any devices and they do not have to worry about the security
breaches (Ciampa 2015). The chance of malware attack is comparatively minimal.
4.2. Physical Security
The cloud-based applications can prove to be disastrous and threats due to the
occurrence of floods, road blockages and the power outages. The physical server can get
damaged and there are possible chances for data loss (Greitzer & Hohimer 2011). The cloud
vendor provides all the data storage facility, store the files, the financial data files and the

8NETWORK MANAGEMENT AND SECURITY
sensitive data of the customers thus they can stay protected against the threats occurred due to
the physical security.
4.3. Successful planning
Certain employees of the enterprise for some reasons cannot come to the office thus
the productivity can suffer. The employee can suffer from illness or may get died, thus to
retain the maximum productivity, they must prepare a successor for the replacement; they
must have the required knowledge so that they can fulfil the requirements of the enterprise, at
the time of need (Ciampa 2015). Therefore, they must be trained.
4.4. Stock Control system
The STP Limited must have the design plan ready to develop a website that can
facilitate the customers of the enterprise. They must showcase all the kitchen cabinets- all the
cupboards and the drawer fronts having various colours and various textures so that that can
attract the customers (George 2013). Once the item gets ordered and gets shipped, they must
update the database all the time according to the availability of the product.
5.0. Risk management
The adoption of the cloud technology and information system can lead to the
initiation of various kinds of threats, risks and the vulnerabilities (Gupta & Hammond 2005).
Thus these risks must be considered and necessary actions must be taken to handle and
manage the risks.
5.1. Security Policy
STP Limited must develop a risk model and based on that the enterprise should take
steps and action to reduce the risks and the safety measures can assist to carry out the
sensitive data of the customers thus they can stay protected against the threats occurred due to
the physical security.
4.3. Successful planning
Certain employees of the enterprise for some reasons cannot come to the office thus
the productivity can suffer. The employee can suffer from illness or may get died, thus to
retain the maximum productivity, they must prepare a successor for the replacement; they
must have the required knowledge so that they can fulfil the requirements of the enterprise, at
the time of need (Ciampa 2015). Therefore, they must be trained.
4.4. Stock Control system
The STP Limited must have the design plan ready to develop a website that can
facilitate the customers of the enterprise. They must showcase all the kitchen cabinets- all the
cupboards and the drawer fronts having various colours and various textures so that that can
attract the customers (George 2013). Once the item gets ordered and gets shipped, they must
update the database all the time according to the availability of the product.
5.0. Risk management
The adoption of the cloud technology and information system can lead to the
initiation of various kinds of threats, risks and the vulnerabilities (Gupta & Hammond 2005).
Thus these risks must be considered and necessary actions must be taken to handle and
manage the risks.
5.1. Security Policy
STP Limited must develop a risk model and based on that the enterprise should take
steps and action to reduce the risks and the safety measures can assist to carry out the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORK MANAGEMENT AND SECURITY
business activities in a secured manner (Ciampa 2015). The change, as well as the incident
management, can help to implement the security policies inside the organisation.
5.2. Training and awareness
The employees of STP Limited must be learned and should have the proper
knowledge of the security measures so that they detect the virus attack beforehand and can
take actions quickly to mitigate the risks (Bandyopadhyay et al 2011).
5.3. Integration technology
The information technology can benefit them. The SaaS model and the PaaS model
provide the cloud benefits that can facilitate STP Limited. PaaS involves the software
vendors the capability to run and execute the business applications (Chang, Dillon & Wu
2010). Salesforce.com is known to cater the SaaS functionality to the aforesaid enterprise.
6.0. Conclusions
It can be concluded from the above discourse STP Limited by adopting the
information system can get the security benefits by which they can defend the security
breaches and the data breaches. The solutions to mitigate the risks have been showcased in
the report, the three characteristics policies, procedures and the people must be considered
while taking security into consideration. This can effectively check and control the data
breaches and in this way, the security measures can be ensured inside the company premises.
STP Limited can be aware of the security measures that can assist to furnish the business
activities.
7.0. Recommendations
i. STP Limited should implement procedures and the policies so that the business operations
can be carried out in a secured manner and in a smooth manner.
business activities in a secured manner (Ciampa 2015). The change, as well as the incident
management, can help to implement the security policies inside the organisation.
5.2. Training and awareness
The employees of STP Limited must be learned and should have the proper
knowledge of the security measures so that they detect the virus attack beforehand and can
take actions quickly to mitigate the risks (Bandyopadhyay et al 2011).
5.3. Integration technology
The information technology can benefit them. The SaaS model and the PaaS model
provide the cloud benefits that can facilitate STP Limited. PaaS involves the software
vendors the capability to run and execute the business applications (Chang, Dillon & Wu
2010). Salesforce.com is known to cater the SaaS functionality to the aforesaid enterprise.
6.0. Conclusions
It can be concluded from the above discourse STP Limited by adopting the
information system can get the security benefits by which they can defend the security
breaches and the data breaches. The solutions to mitigate the risks have been showcased in
the report, the three characteristics policies, procedures and the people must be considered
while taking security into consideration. This can effectively check and control the data
breaches and in this way, the security measures can be ensured inside the company premises.
STP Limited can be aware of the security measures that can assist to furnish the business
activities.
7.0. Recommendations
i. STP Limited should implement procedures and the policies so that the business operations
can be carried out in a secured manner and in a smooth manner.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10NETWORK MANAGEMENT AND SECURITY
ii. STP Limited must make all the money transactions via the secure tunnel, they should not
initiate any transactions until the whole thing gets set up and the website is developed fully,
they must continue their business activities when the rogue discovery tools and the portal
access points are applied.
iii. The asset register must be maintained well and STP must be careful about the procedures.
iv. STP Limited must keep backup of all the financial data and the sensitive information of
the customers in safe and secure manner.
v. The employees must get trained well so that they can take the initiatives to control the
threats beforehand.
vi. The stock control system must be made strong by the technology, they must update the
database, must update the availabilities of cupboards and the drawers, once a customer order
a kitchen cabinet, they must update all the details, this can help both the employees and the
customers to know the actual availability of the kitchen products in the four offices.
ii. STP Limited must make all the money transactions via the secure tunnel, they should not
initiate any transactions until the whole thing gets set up and the website is developed fully,
they must continue their business activities when the rogue discovery tools and the portal
access points are applied.
iii. The asset register must be maintained well and STP must be careful about the procedures.
iv. STP Limited must keep backup of all the financial data and the sensitive information of
the customers in safe and secure manner.
v. The employees must get trained well so that they can take the initiatives to control the
threats beforehand.
vi. The stock control system must be made strong by the technology, they must update the
database, must update the availabilities of cupboards and the drawers, once a customer order
a kitchen cabinet, they must update all the details, this can help both the employees and the
customers to know the actual availability of the kitchen products in the four offices.

11NETWORK MANAGEMENT AND SECURITY
8.0. Bibliography
Australian Taxation Office (ATO) 2016, Taxation Ruling TR 2016/1, Australian Taxation
Office, viewed 6 October 2016,
<https://www.ato.gov.au/law/view/document?docid=txr/tr20161/nat/ato/00001>.
Bandyopadhyay, S, Ghalsasi, A, Marston, S, Li, Z & Zhang, J 2011, ‘Cloud computing—The
business perspective’, Decision support systems, vol. 51, no. 1, pp.176-189, doi:
10.1016/j.dss.2010.12.006
Chang, E, Dillon, T, Wu C 2010, ‘Cloud computing: Issues and challenges’, 2010 24th IEEE
International Conference on Advanced Information Networking and Applications, pp. 27-33,
doi: 10.1109/AINA.2010.187
Check Point Software Technologies Ltd 2006, Check point introduces new Safe@Office
unified threat management appliances with integrated ADSL modems; easy-to-manage
appliances allow internet service providers to provide security protection and connectivity in
a single solution, Business Wire, 16 May 2006, viewed 18 September 2016,
<http://search.proquest.com.ezproxy.usc.edu.au:2048/docview/445230481?
accountid=28745>.
Ciampa, M 2012, Security + guide to security fundamentals. 5th edn, Cengage, Boston.
Computer Weekly 2002, ‘Easy guide to purchasing PC’s’, Computer Weekly, February
2002, viewed 19 October 2016, <http://www.computerweekly.com/feature/Easy-guide-to-
purchasing-PCs>.
Crawford, M, Horstmann, B, Keller, S, Powell, A & Predmore, C 2005, 'Information security
threats and practices in small businesses', Information Systems Management, vol. 22, no. 2,
pp. 7-19, viewed 20 October 2016,
8.0. Bibliography
Australian Taxation Office (ATO) 2016, Taxation Ruling TR 2016/1, Australian Taxation
Office, viewed 6 October 2016,
<https://www.ato.gov.au/law/view/document?docid=txr/tr20161/nat/ato/00001>.
Bandyopadhyay, S, Ghalsasi, A, Marston, S, Li, Z & Zhang, J 2011, ‘Cloud computing—The
business perspective’, Decision support systems, vol. 51, no. 1, pp.176-189, doi:
10.1016/j.dss.2010.12.006
Chang, E, Dillon, T, Wu C 2010, ‘Cloud computing: Issues and challenges’, 2010 24th IEEE
International Conference on Advanced Information Networking and Applications, pp. 27-33,
doi: 10.1109/AINA.2010.187
Check Point Software Technologies Ltd 2006, Check point introduces new Safe@Office
unified threat management appliances with integrated ADSL modems; easy-to-manage
appliances allow internet service providers to provide security protection and connectivity in
a single solution, Business Wire, 16 May 2006, viewed 18 September 2016,
<http://search.proquest.com.ezproxy.usc.edu.au:2048/docview/445230481?
accountid=28745>.
Ciampa, M 2012, Security + guide to security fundamentals. 5th edn, Cengage, Boston.
Computer Weekly 2002, ‘Easy guide to purchasing PC’s’, Computer Weekly, February
2002, viewed 19 October 2016, <http://www.computerweekly.com/feature/Easy-guide-to-
purchasing-PCs>.
Crawford, M, Horstmann, B, Keller, S, Powell, A & Predmore, C 2005, 'Information security
threats and practices in small businesses', Information Systems Management, vol. 22, no. 2,
pp. 7-19, viewed 20 October 2016,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





