Cyber Security: Network Security Policy and Threat Analysis Report
VerifiedAdded on 2022/08/17
|16
|2075
|13
Report
AI Summary
This report provides a comprehensive analysis of network security, starting with the setup of a virtual environment using Kali Linux and Oracle VirtualBox. It then delves into the use of Wireshark for network analysis, demonstrating packet capture and identification of potential vulnerabilities. The report outlines likely security threats, categorizing them by asset, threat, loss, and countermeasures, covering equipment theft, fire, electrical issues, authentication problems (biometric and database), and various software-based threats such as viruses, rogue software, Trojan horses, worms, and rootkits. The second part of the report focuses on developing a network security policy for a multinational pharmaceutical company's R&D department. It details the background, purpose, and scope of the policy, defines roles and responsibilities, and establishes a policy framework. The framework includes physical precautions, firewalls, software updates, and strong password implementation. The report emphasizes the importance of distribution, training, implementation, and continuous monitoring, feedback, and reporting. It also addresses business continuity through distributed datacenters for data recovery. The report concludes with a list of relevant references.

Running head: NETWORK SECURITY
Network Security
Name of the Student:
Name of the University:
Author Note
Network Security
Name of the Student:
Name of the University:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK SECURITY
Table of Contents
Task 1...............................................................................................................................................2
Setting up a virtual environment..................................................................................................2
Using tools...................................................................................................................................5
List of likely security threats.......................................................................................................8
Task 2.............................................................................................................................................12
Background and purpose...........................................................................................................12
Scope..........................................................................................................................................12
Roles and responsibilities..........................................................................................................12
Policy framework.......................................................................................................................13
Distribution, training and implementation.................................................................................13
Monitoring, feedback and reporting..........................................................................................13
Business continuity....................................................................................................................14
References......................................................................................................................................15
NETWORK SECURITY
Table of Contents
Task 1...............................................................................................................................................2
Setting up a virtual environment..................................................................................................2
Using tools...................................................................................................................................5
List of likely security threats.......................................................................................................8
Task 2.............................................................................................................................................12
Background and purpose...........................................................................................................12
Scope..........................................................................................................................................12
Roles and responsibilities..........................................................................................................12
Policy framework.......................................................................................................................13
Distribution, training and implementation.................................................................................13
Monitoring, feedback and reporting..........................................................................................13
Business continuity....................................................................................................................14
References......................................................................................................................................15
2
NETWORK SECURITY
Task 1
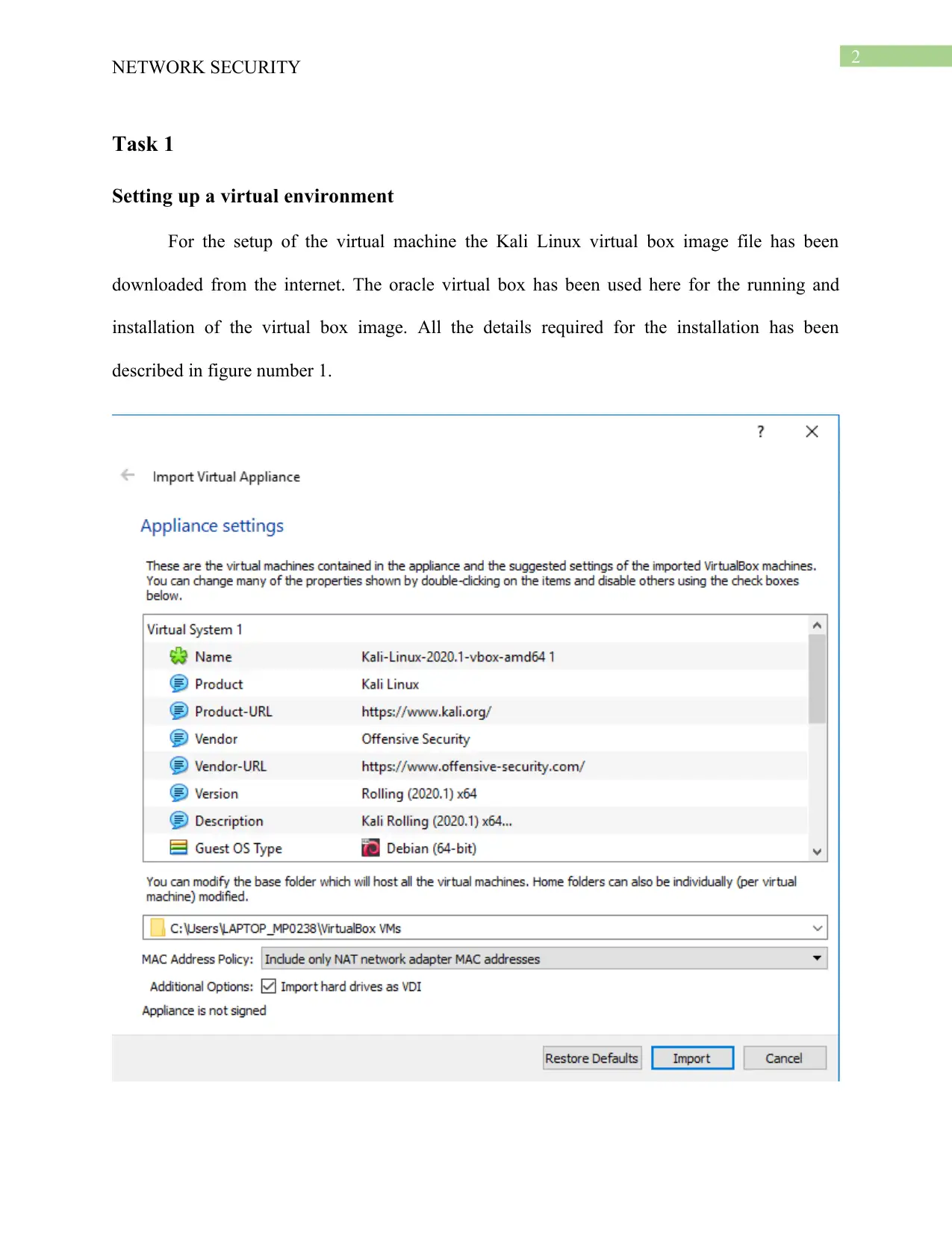
Setting up a virtual environment
For the setup of the virtual machine the Kali Linux virtual box image file has been
downloaded from the internet. The oracle virtual box has been used here for the running and
installation of the virtual box image. All the details required for the installation has been
described in figure number 1.
NETWORK SECURITY
Task 1
Setting up a virtual environment
For the setup of the virtual machine the Kali Linux virtual box image file has been
downloaded from the internet. The oracle virtual box has been used here for the running and
installation of the virtual box image. All the details required for the installation has been
described in figure number 1.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
NETWORK SECURITY
Figure 1: Virtual VMware settings
Source: (Created by author)
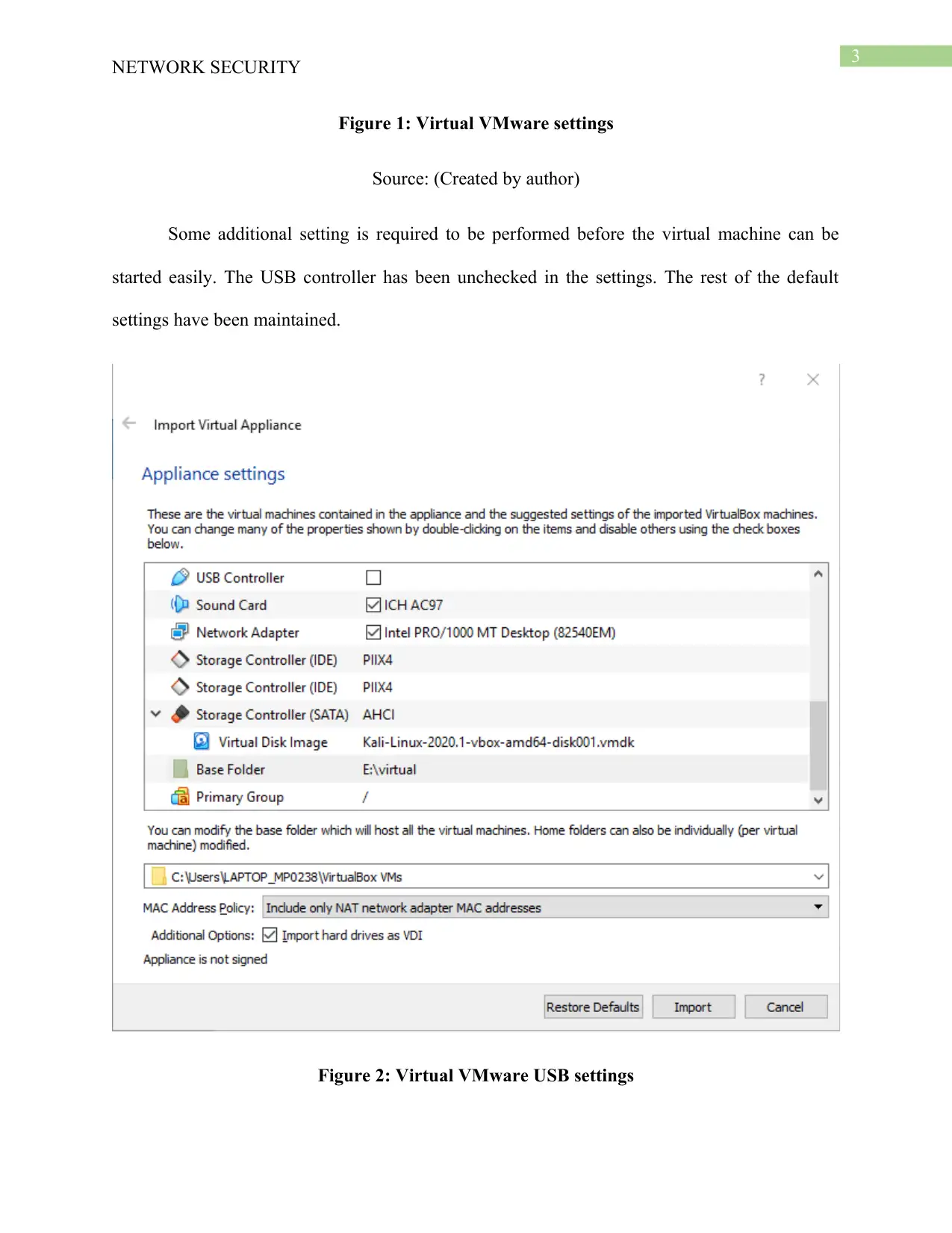
Some additional setting is required to be performed before the virtual machine can be
started easily. The USB controller has been unchecked in the settings. The rest of the default
settings have been maintained.
Figure 2: Virtual VMware USB settings
NETWORK SECURITY
Figure 1: Virtual VMware settings
Source: (Created by author)
Some additional setting is required to be performed before the virtual machine can be
started easily. The USB controller has been unchecked in the settings. The rest of the default
settings have been maintained.
Figure 2: Virtual VMware USB settings
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORK SECURITY
Source: (Created by author)
After all the settings have been applied for the system the welcome screen as per figure
number 4 appears. The terminal in the kali Linux operating is then used for running wire shark.
Figure 3: Virtual VMware additional settings
Source: (Created by author)
NETWORK SECURITY
Source: (Created by author)
After all the settings have been applied for the system the welcome screen as per figure
number 4 appears. The terminal in the kali Linux operating is then used for running wire shark.
Figure 3: Virtual VMware additional settings
Source: (Created by author)

5
NETWORK SECURITY
Figure 4: Kali Linux home screen
Source: (Created by author)
Using tools
The description of the use of the wire shark tool has been done here. Wire shark is one of
the very important network analyzer tool (Whitt and You 2018). It can be used for the analysis of
the network and identification of the vulnerabilities and the level of vulnerabilities identified in
the system. The real time analysis of the network of the can be performed in the system and for
troubleshooting the issues which are taking place currently in the network.
The issues with the packets which are dropped and the malicious activities in the network
can be easily rectified with the analysis and risk mitigations (Haer et al. 2017). This would be
helpful in preventing the network from the hacking.
NETWORK SECURITY
Figure 4: Kali Linux home screen
Source: (Created by author)
Using tools
The description of the use of the wire shark tool has been done here. Wire shark is one of
the very important network analyzer tool (Whitt and You 2018). It can be used for the analysis of
the network and identification of the vulnerabilities and the level of vulnerabilities identified in
the system. The real time analysis of the network of the can be performed in the system and for
troubleshooting the issues which are taking place currently in the network.
The issues with the packets which are dropped and the malicious activities in the network
can be easily rectified with the analysis and risk mitigations (Haer et al. 2017). This would be
helpful in preventing the network from the hacking.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
NETWORK SECURITY
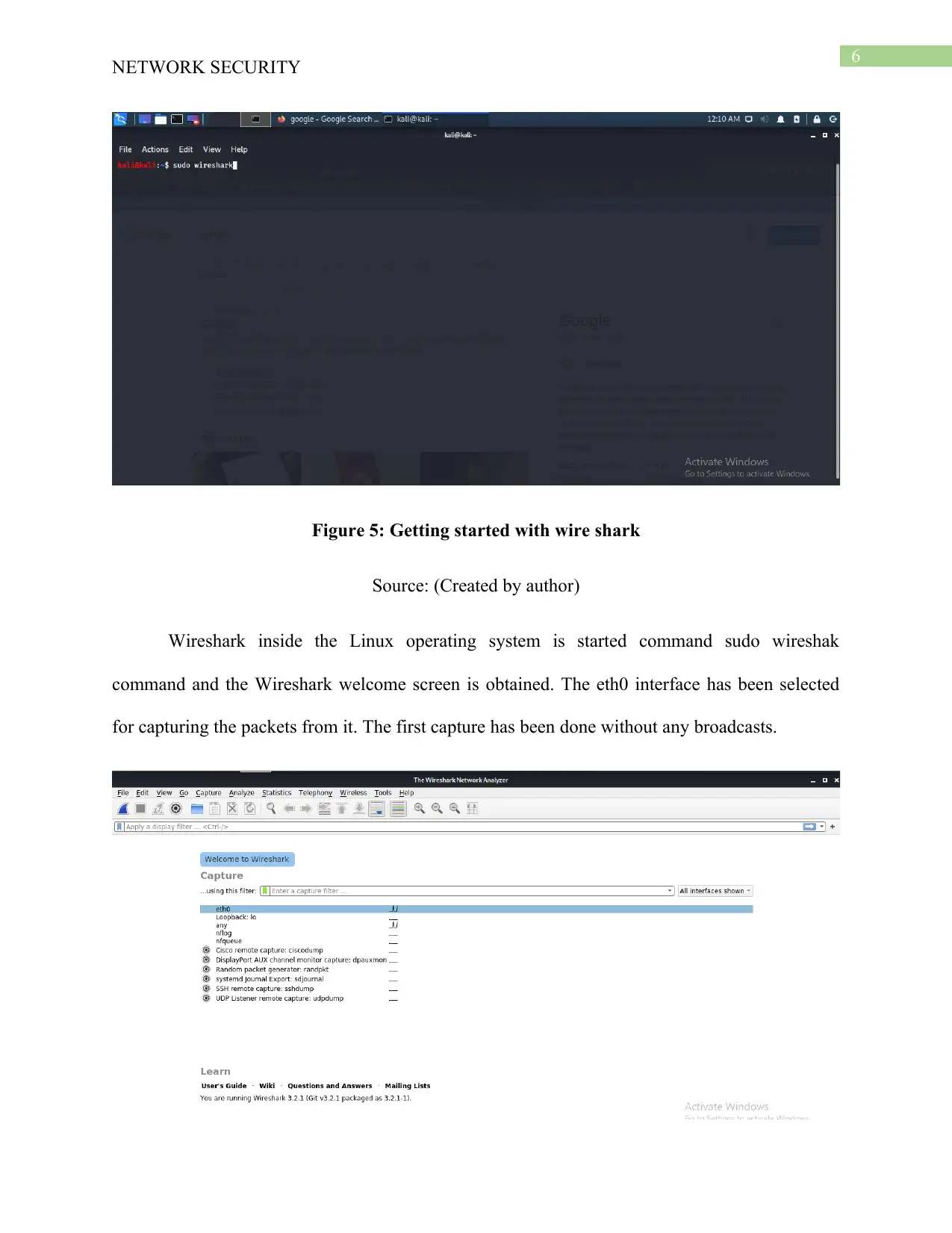
Figure 5: Getting started with wire shark
Source: (Created by author)
Wireshark inside the Linux operating system is started command sudo wireshak
command and the Wireshark welcome screen is obtained. The eth0 interface has been selected
for capturing the packets from it. The first capture has been done without any broadcasts.
NETWORK SECURITY
Figure 5: Getting started with wire shark
Source: (Created by author)
Wireshark inside the Linux operating system is started command sudo wireshak
command and the Wireshark welcome screen is obtained. The eth0 interface has been selected
for capturing the packets from it. The first capture has been done without any broadcasts.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
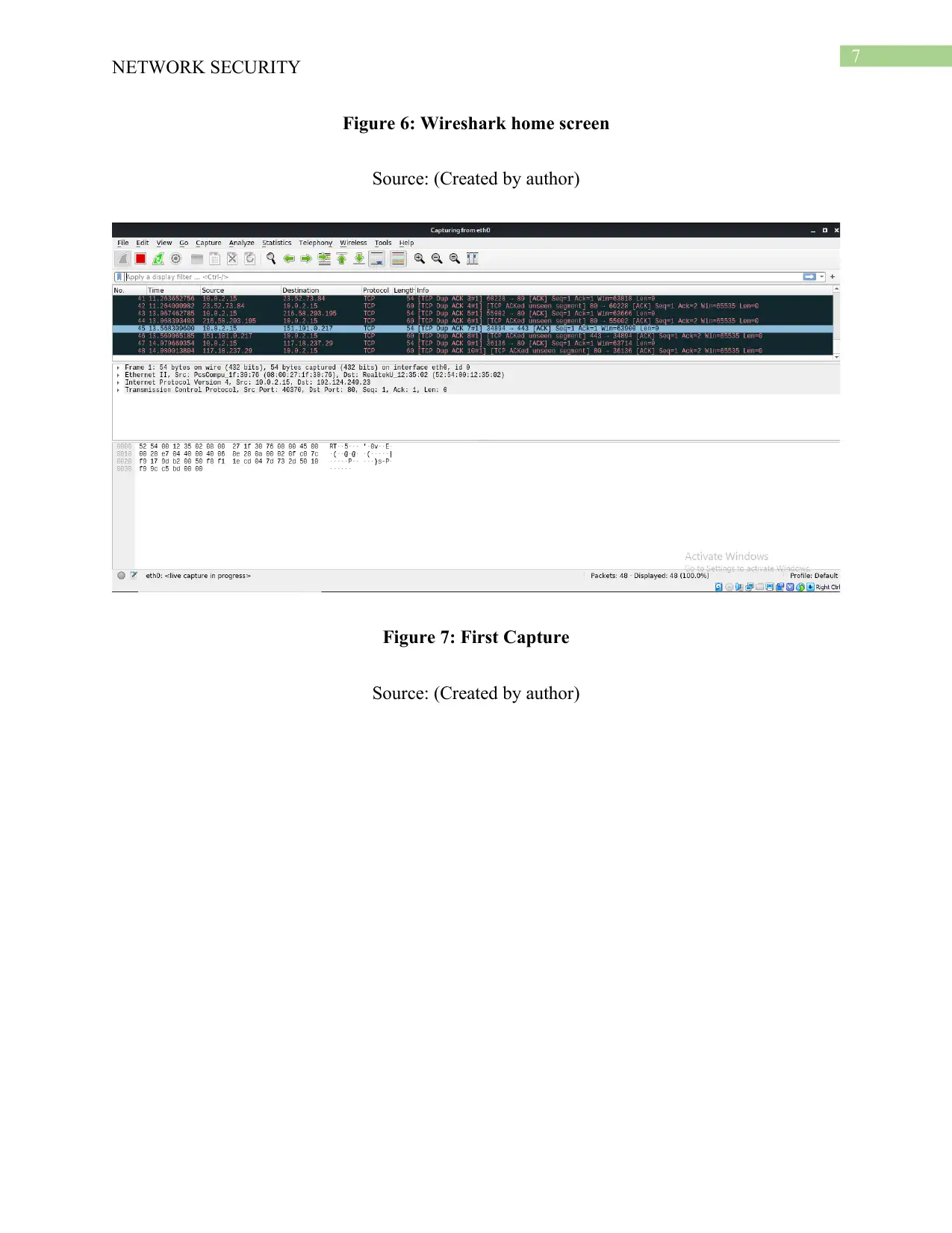
7
NETWORK SECURITY
Figure 6: Wireshark home screen
Source: (Created by author)
Figure 7: First Capture
Source: (Created by author)
NETWORK SECURITY
Figure 6: Wireshark home screen
Source: (Created by author)
Figure 7: First Capture
Source: (Created by author)
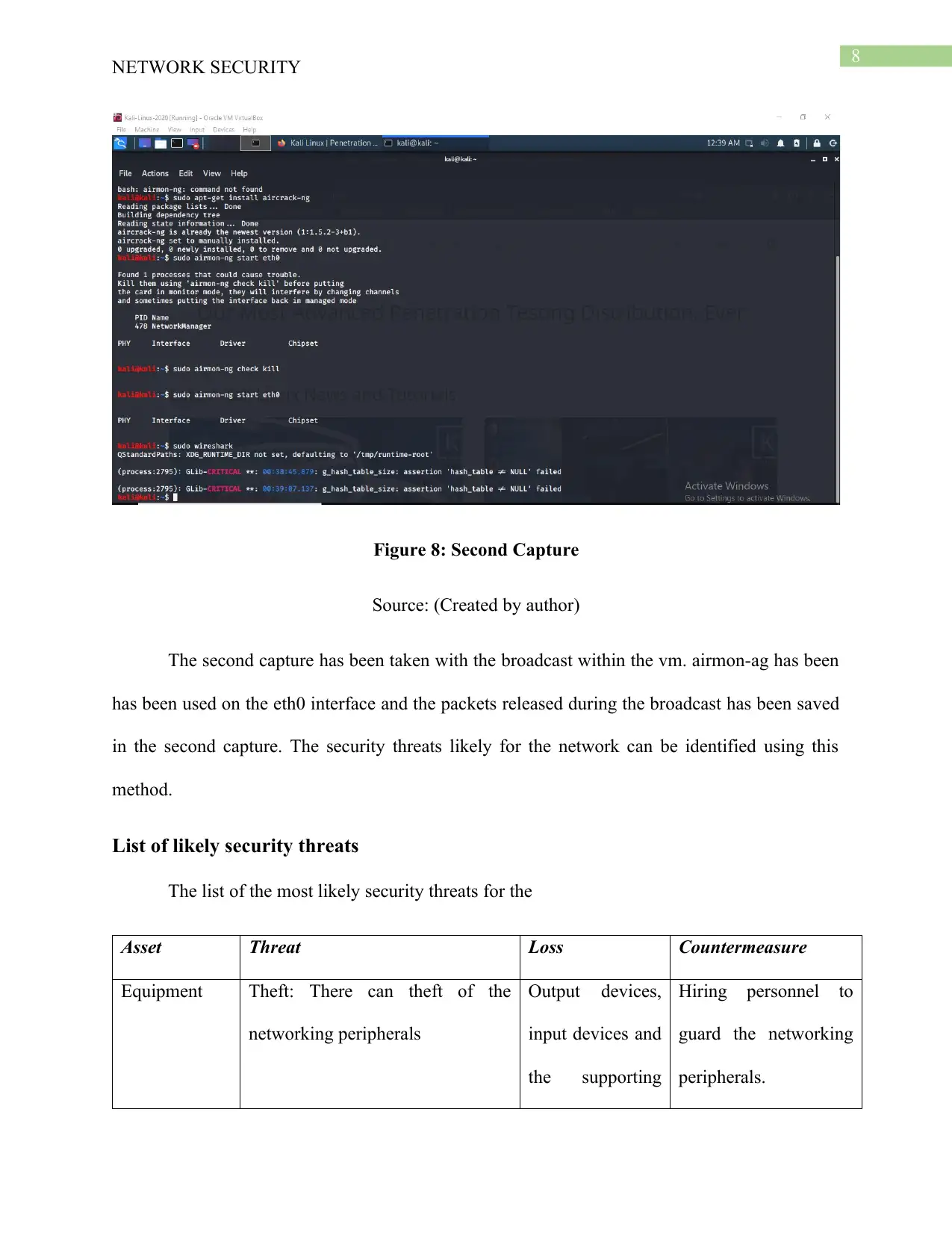
8
NETWORK SECURITY
Figure 8: Second Capture
Source: (Created by author)
The second capture has been taken with the broadcast within the vm. airmon-ag has been
has been used on the eth0 interface and the packets released during the broadcast has been saved
in the second capture. The security threats likely for the network can be identified using this
method.
List of likely security threats
The list of the most likely security threats for the
Asset Threat Loss Countermeasure
Equipment Theft: There can theft of the
networking peripherals
Output devices,
input devices and
the supporting
Hiring personnel to
guard the networking
peripherals.
NETWORK SECURITY
Figure 8: Second Capture
Source: (Created by author)
The second capture has been taken with the broadcast within the vm. airmon-ag has been
has been used on the eth0 interface and the packets released during the broadcast has been saved
in the second capture. The security threats likely for the network can be identified using this
method.
List of likely security threats
The list of the most likely security threats for the
Asset Threat Loss Countermeasure
Equipment Theft: There can theft of the
networking peripherals
Output devices,
input devices and
the supporting
Hiring personnel to
guard the networking
peripherals.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
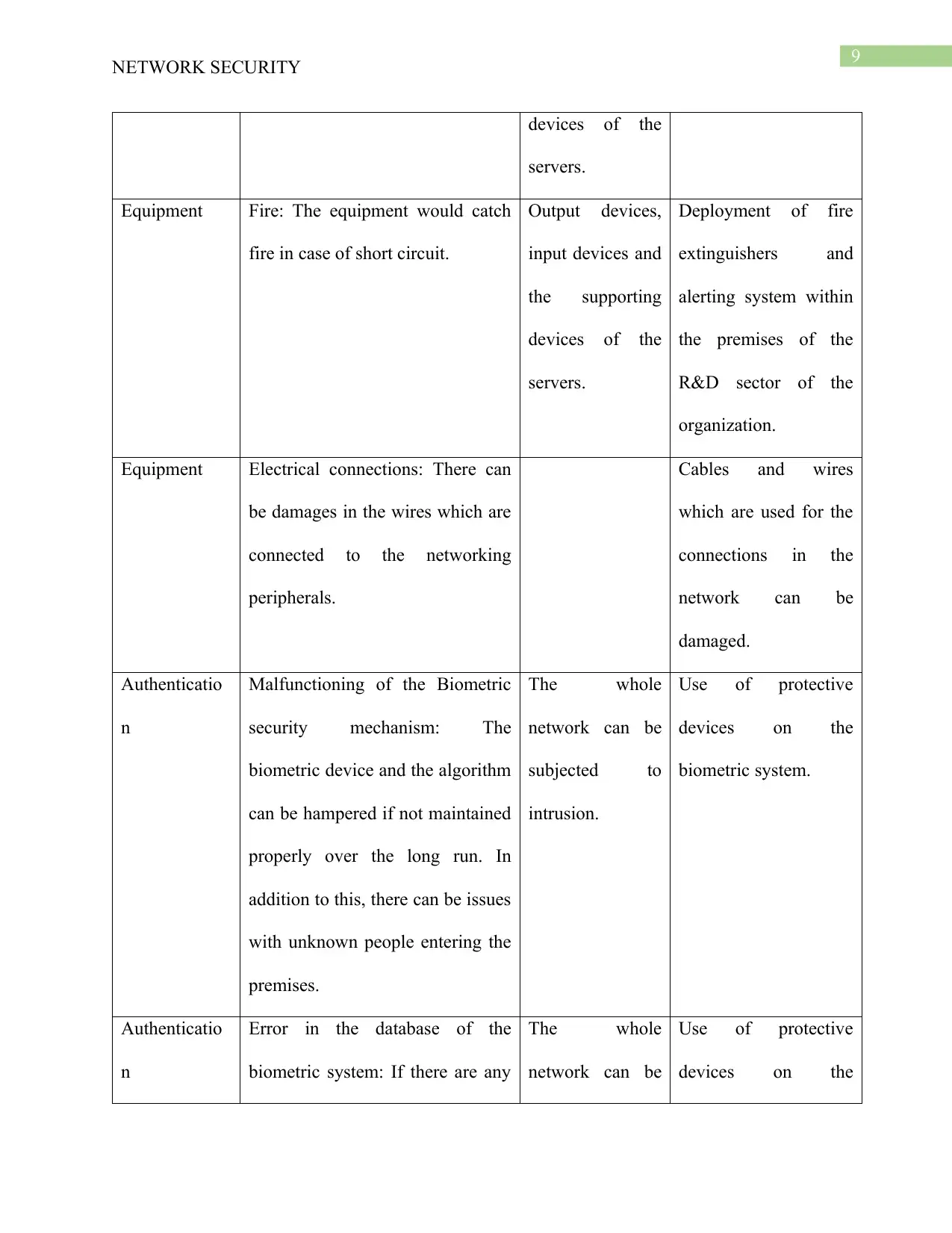
9
NETWORK SECURITY
devices of the
servers.
Equipment Fire: The equipment would catch
fire in case of short circuit.
Output devices,
input devices and
the supporting
devices of the
servers.
Deployment of fire
extinguishers and
alerting system within
the premises of the
R&D sector of the
organization.
Equipment Electrical connections: There can
be damages in the wires which are
connected to the networking
peripherals.
Cables and wires
which are used for the
connections in the
network can be
damaged.
Authenticatio
n
Malfunctioning of the Biometric
security mechanism: The
biometric device and the algorithm
can be hampered if not maintained
properly over the long run. In
addition to this, there can be issues
with unknown people entering the
premises.
The whole
network can be
subjected to
intrusion.
Use of protective
devices on the
biometric system.
Authenticatio
n
Error in the database of the
biometric system: If there are any
The whole
network can be
Use of protective
devices on the
NETWORK SECURITY
devices of the
servers.
Equipment Fire: The equipment would catch
fire in case of short circuit.
Output devices,
input devices and
the supporting
devices of the
servers.
Deployment of fire
extinguishers and
alerting system within
the premises of the
R&D sector of the
organization.
Equipment Electrical connections: There can
be damages in the wires which are
connected to the networking
peripherals.
Cables and wires
which are used for the
connections in the
network can be
damaged.
Authenticatio
n
Malfunctioning of the Biometric
security mechanism: The
biometric device and the algorithm
can be hampered if not maintained
properly over the long run. In
addition to this, there can be issues
with unknown people entering the
premises.
The whole
network can be
subjected to
intrusion.
Use of protective
devices on the
biometric system.
Authenticatio
n
Error in the database of the
biometric system: If there are any
The whole
network can be
Use of protective
devices on the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
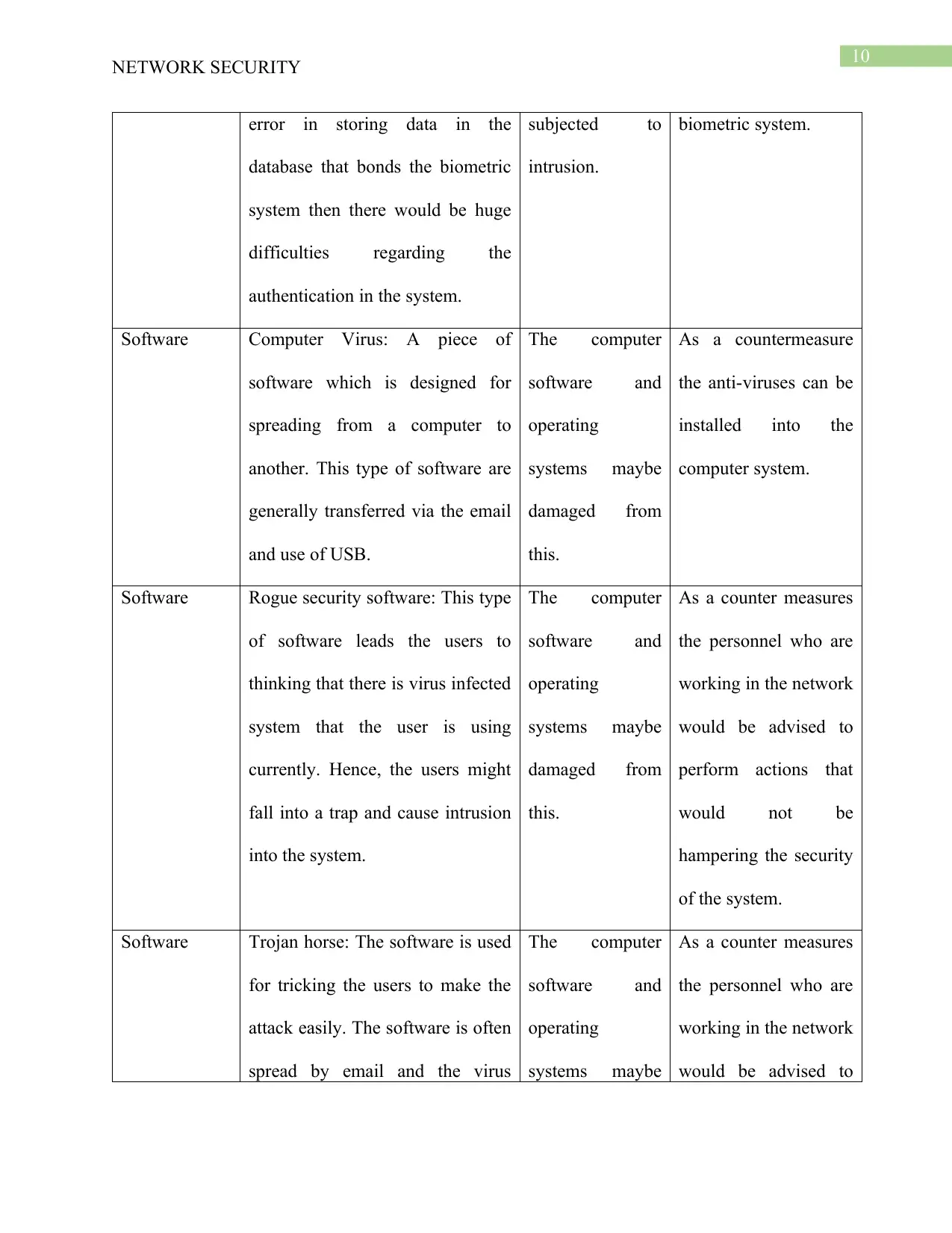
10
NETWORK SECURITY
error in storing data in the
database that bonds the biometric
system then there would be huge
difficulties regarding the
authentication in the system.
subjected to
intrusion.
biometric system.
Software Computer Virus: A piece of
software which is designed for
spreading from a computer to
another. This type of software are
generally transferred via the email
and use of USB.
The computer
software and
operating
systems maybe
damaged from
this.
As a countermeasure
the anti-viruses can be
installed into the
computer system.
Software Rogue security software: This type
of software leads the users to
thinking that there is virus infected
system that the user is using
currently. Hence, the users might
fall into a trap and cause intrusion
into the system.
The computer
software and
operating
systems maybe
damaged from
this.
As a counter measures
the personnel who are
working in the network
would be advised to
perform actions that
would not be
hampering the security
of the system.
Software Trojan horse: The software is used
for tricking the users to make the
attack easily. The software is often
spread by email and the virus
The computer
software and
operating
systems maybe
As a counter measures
the personnel who are
working in the network
would be advised to
NETWORK SECURITY
error in storing data in the
database that bonds the biometric
system then there would be huge
difficulties regarding the
authentication in the system.
subjected to
intrusion.
biometric system.
Software Computer Virus: A piece of
software which is designed for
spreading from a computer to
another. This type of software are
generally transferred via the email
and use of USB.
The computer
software and
operating
systems maybe
damaged from
this.
As a countermeasure
the anti-viruses can be
installed into the
computer system.
Software Rogue security software: This type
of software leads the users to
thinking that there is virus infected
system that the user is using
currently. Hence, the users might
fall into a trap and cause intrusion
into the system.
The computer
software and
operating
systems maybe
damaged from
this.
As a counter measures
the personnel who are
working in the network
would be advised to
perform actions that
would not be
hampering the security
of the system.
Software Trojan horse: The software is used
for tricking the users to make the
attack easily. The software is often
spread by email and the virus
The computer
software and
operating
systems maybe
As a counter measures
the personnel who are
working in the network
would be advised to
11
NETWORK SECURITY
spreads with advertisement. damaged from
this.
perform actions that
would not be
hampering the security
of the system.
Software Computer worm: A piece of
malware program would be able to
replicate a program in the current
and the spread itself to all parts of
the system.
The computer
software and
operating
systems maybe
damaged from
this.
As a counter measures
the personnel who are
working in the network
would be advised to
perform actions that
would not be
hampering the security
of the system.
Software Rootkit: A group of software
which provide remote control for
the access to the computer network
and these tool comes with the pre-
installed key loggers and password
stealers.
The computer
software and
operating
systems maybe
damaged from
this.
The Firewalls can be
installed into the
network so that they
would be able to stop
the rootkits from
functioning within the
system.
NETWORK SECURITY
spreads with advertisement. damaged from
this.
perform actions that
would not be
hampering the security
of the system.
Software Computer worm: A piece of
malware program would be able to
replicate a program in the current
and the spread itself to all parts of
the system.
The computer
software and
operating
systems maybe
damaged from
this.
As a counter measures
the personnel who are
working in the network
would be advised to
perform actions that
would not be
hampering the security
of the system.
Software Rootkit: A group of software
which provide remote control for
the access to the computer network
and these tool comes with the pre-
installed key loggers and password
stealers.
The computer
software and
operating
systems maybe
damaged from
this.
The Firewalls can be
installed into the
network so that they
would be able to stop
the rootkits from
functioning within the
system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





