Network Topology Design and Simulation Report
VerifiedAdded on 2022/08/18
|15
|2801
|19
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: NETWORK TOPOLOGY DESIGN AND SIMULATION
Network Topology Design and Simulation
Name of the Student
Name of the University
Author Note
Network Topology Design and Simulation
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1NETWORK TOPOLOGY DESIGN AND SIMULATION
Executive Summary
In order to ensure communications within an organization, network infrastructures play a
vital role. As a result business must give utmost importance to designing the topology for
their network. The purpose of the following report is to propose the design of such a network
topology for the institute. To do this the report provides the network topology design backed
by a rough overview of the network where the networking method gets described along with
the explanations for networking architectures and physical topologies. Then the report talks
about the cabling media and devices involved to build the network followed by explaining the
wireless network, the remote access, printer allocation, server room, networking hardware,
internet access and cost estimation. In these sections the report is to explain if there is enough
cabling and devices for future expansion of the network, how wireless network is being
obtained, printers used by the departments, role of servers, role of networking devices, how
internet access is ensured for entire campus and the cost to implement the network. Having
done that the report ends and provides the conclusions.
Executive Summary
In order to ensure communications within an organization, network infrastructures play a
vital role. As a result business must give utmost importance to designing the topology for
their network. The purpose of the following report is to propose the design of such a network
topology for the institute. To do this the report provides the network topology design backed
by a rough overview of the network where the networking method gets described along with
the explanations for networking architectures and physical topologies. Then the report talks
about the cabling media and devices involved to build the network followed by explaining the
wireless network, the remote access, printer allocation, server room, networking hardware,
internet access and cost estimation. In these sections the report is to explain if there is enough
cabling and devices for future expansion of the network, how wireless network is being
obtained, printers used by the departments, role of servers, role of networking devices, how
internet access is ensured for entire campus and the cost to implement the network. Having
done that the report ends and provides the conclusions.

2NETWORK TOPOLOGY DESIGN AND SIMULATION
Table of Contents
Introduction................................................................................................................................3
Network Design.........................................................................................................................4
Network Topology.................................................................................................................4
Overview................................................................................................................................4
Media..........................................................................................................................................5
Wireless Network.......................................................................................................................6
Remote Access...........................................................................................................................6
Printer Allocation.......................................................................................................................7
Server Room...............................................................................................................................7
Networking Hardware................................................................................................................8
Router.....................................................................................................................................8
Multilayer Switch...................................................................................................................8
Access Layer Switch..............................................................................................................8
Wireless Access Points..........................................................................................................8
Internet Access...........................................................................................................................9
IP Addressing.........................................................................................................................9
Cost Estimation........................................................................................................................11
Conclusion................................................................................................................................12
References................................................................................................................................13
Table of Contents
Introduction................................................................................................................................3
Network Design.........................................................................................................................4
Network Topology.................................................................................................................4
Overview................................................................................................................................4
Media..........................................................................................................................................5
Wireless Network.......................................................................................................................6
Remote Access...........................................................................................................................6
Printer Allocation.......................................................................................................................7
Server Room...............................................................................................................................7
Networking Hardware................................................................................................................8
Router.....................................................................................................................................8
Multilayer Switch...................................................................................................................8
Access Layer Switch..............................................................................................................8
Wireless Access Points..........................................................................................................8
Internet Access...........................................................................................................................9
IP Addressing.........................................................................................................................9
Cost Estimation........................................................................................................................11
Conclusion................................................................................................................................12
References................................................................................................................................13

3NETWORK TOPOLOGY DESIGN AND SIMULATION
Introduction
In order to ensure effective communications and network access to the Holmes
Institute, the report proposes the design of a network topology specifically for the institute
(Ozkan-Canbolat and Beraha 2016). This requires the report to draw the network topology
design in the Cisco Packet Tracer simulation software and then the design explained through
an overview of the network design (Hossain and Zannat 2019). Here, the networking model,
architecture and the physical networking topologies get described and how they are used in
the institute’s network (Airi and Anderson 2017). Then this report provides details regarding
the required cabling media and devices that were needed to build the network. This is
followed by explanation of the wireless networks, the remote access, and printer allocation,
server room, networking hardware, internet access and cost estimation. In these sections the
report explains how much cabling and networking media is enough for ensuring future
expansion and scalability of the network, how wireless network is being obtained, usage of
printers and servers, role of networking devices, how internet access is ensured for entire
campus and the cost to implement the network. Thereafter the report comes to an end with
concluding notes.
Introduction
In order to ensure effective communications and network access to the Holmes
Institute, the report proposes the design of a network topology specifically for the institute
(Ozkan-Canbolat and Beraha 2016). This requires the report to draw the network topology
design in the Cisco Packet Tracer simulation software and then the design explained through
an overview of the network design (Hossain and Zannat 2019). Here, the networking model,
architecture and the physical networking topologies get described and how they are used in
the institute’s network (Airi and Anderson 2017). Then this report provides details regarding
the required cabling media and devices that were needed to build the network. This is
followed by explanation of the wireless networks, the remote access, and printer allocation,
server room, networking hardware, internet access and cost estimation. In these sections the
report explains how much cabling and networking media is enough for ensuring future
expansion and scalability of the network, how wireless network is being obtained, usage of
printers and servers, role of networking devices, how internet access is ensured for entire
campus and the cost to implement the network. Thereafter the report comes to an end with
concluding notes.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
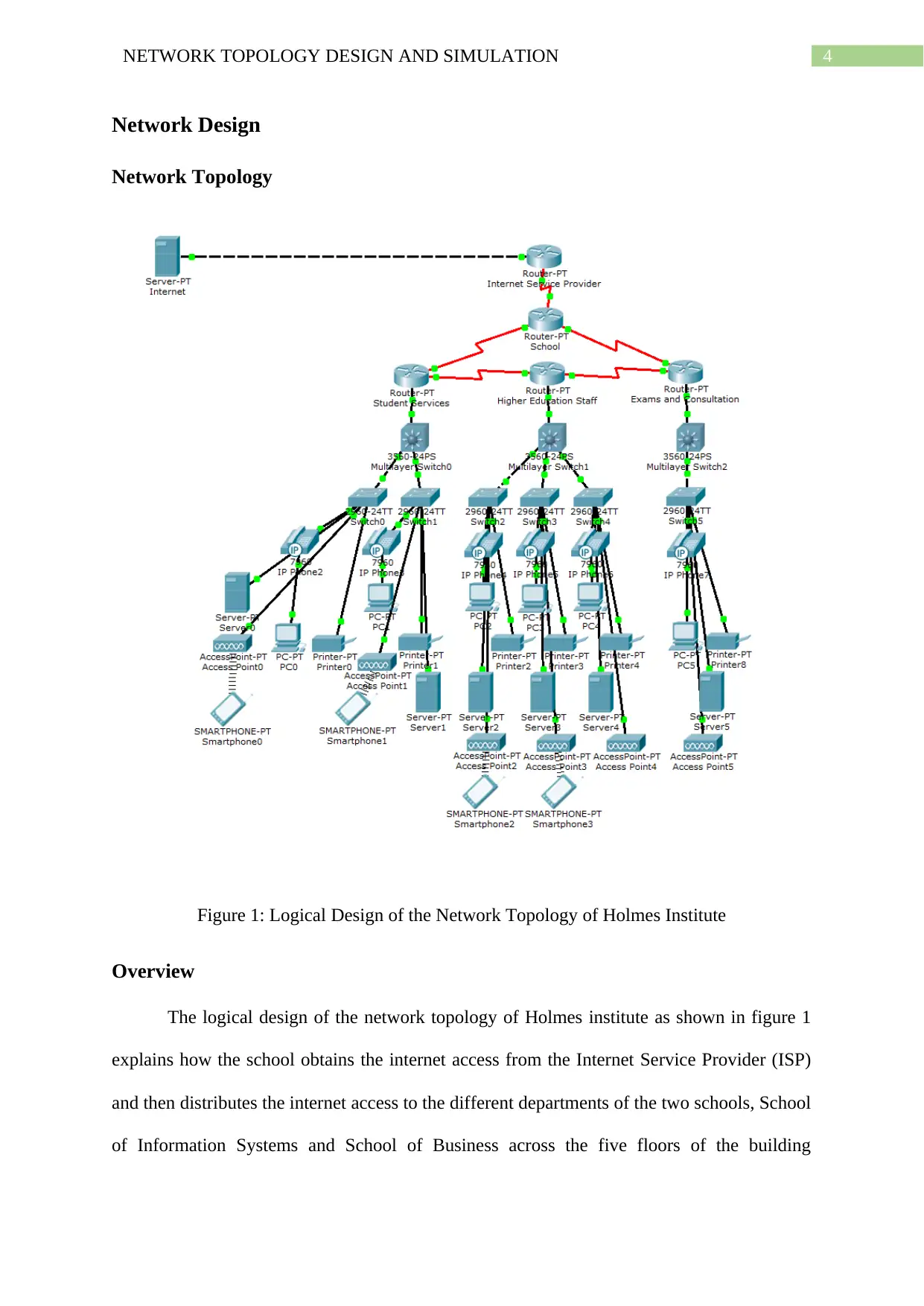
4NETWORK TOPOLOGY DESIGN AND SIMULATION
Network Design
Network Topology
Figure 1: Logical Design of the Network Topology of Holmes Institute
Overview
The logical design of the network topology of Holmes institute as shown in figure 1
explains how the school obtains the internet access from the Internet Service Provider (ISP)
and then distributes the internet access to the different departments of the two schools, School
of Information Systems and School of Business across the five floors of the building
Network Design
Network Topology
Figure 1: Logical Design of the Network Topology of Holmes Institute
Overview
The logical design of the network topology of Holmes institute as shown in figure 1
explains how the school obtains the internet access from the Internet Service Provider (ISP)
and then distributes the internet access to the different departments of the two schools, School
of Information Systems and School of Business across the five floors of the building

5NETWORK TOPOLOGY DESIGN AND SIMULATION
(Villanueva and Gustilo 2018). Requirements of these schools can change leading to
relocation of networks. Hence to support future expansions the distribution of network is
ensured though the WAN (Wide Area Network) networking topology as against LAN (Local
Area Network) (Leon, Parra and Bermudez 2018). However, for the internal networks of the
different departments, LAN networks do get used. In these LAN networks the networking
devices and hosts are connected in physical star topology (Saad, Weerasinghe and Beferull-
Lozano 2017). To save ports of the router, a multilayer (L3) switch is used to distribute the
routed network from the router to the different access layer switches (L2). Thus, the overall
network is found to follow a three-layered hierarchical network architecture by operating
routers and different types of switch in core, distribution and access layers respectively
(Ferdous 2019). The routers are obtained from Cisco and support IPsec VPN services
(Salman 2017). All the routers of the school are connected with one another through these
IPsec VPN tunnels. The main school router is also connected to the ISP through VPN tunnels
(Dodia and Zhauniarovich 2019). Hence, only the authorized remote users who already have
credentials of the VPN are able to access the school network and services offered by their
servers.
Media
The networking media used by the network of the institute differs significantly
depending on the networking topology (LAN/WAN) involved (Luo, 2017). The WAN
network between the different routers of the school departments, the main school router and
the ISP is implemented with the help of RS232 serial cables through the WIC-1T ports (Xu,
Chen and Liu 2016). For this, the network forms an internetwork between all of the school
routers ensuring that both the serial interfaces that come as default interface configuration of
the routers are used. The only exception is the main school router where an additional WIC-
1T port required to be added.
(Villanueva and Gustilo 2018). Requirements of these schools can change leading to
relocation of networks. Hence to support future expansions the distribution of network is
ensured though the WAN (Wide Area Network) networking topology as against LAN (Local
Area Network) (Leon, Parra and Bermudez 2018). However, for the internal networks of the
different departments, LAN networks do get used. In these LAN networks the networking
devices and hosts are connected in physical star topology (Saad, Weerasinghe and Beferull-
Lozano 2017). To save ports of the router, a multilayer (L3) switch is used to distribute the
routed network from the router to the different access layer switches (L2). Thus, the overall
network is found to follow a three-layered hierarchical network architecture by operating
routers and different types of switch in core, distribution and access layers respectively
(Ferdous 2019). The routers are obtained from Cisco and support IPsec VPN services
(Salman 2017). All the routers of the school are connected with one another through these
IPsec VPN tunnels. The main school router is also connected to the ISP through VPN tunnels
(Dodia and Zhauniarovich 2019). Hence, only the authorized remote users who already have
credentials of the VPN are able to access the school network and services offered by their
servers.
Media
The networking media used by the network of the institute differs significantly
depending on the networking topology (LAN/WAN) involved (Luo, 2017). The WAN
network between the different routers of the school departments, the main school router and
the ISP is implemented with the help of RS232 serial cables through the WIC-1T ports (Xu,
Chen and Liu 2016). For this, the network forms an internetwork between all of the school
routers ensuring that both the serial interfaces that come as default interface configuration of
the routers are used. The only exception is the main school router where an additional WIC-
1T port required to be added.

6NETWORK TOPOLOGY DESIGN AND SIMULATION
The networking media used by the LAN based internal networks of the different
departments are completely different. These connections make use of Ethernet cables in
straight through and crossover modes depending on the way they are used. These cables use
the Fast Ethernet and Gigabit Ethernet ports of the switches being used. Currently the overall
network of the institute is connecting (30 + 55 + 15) = 100 devices in the LAN networks
through seven of the interfaces of the multilayer switches. A 100 percent expansion will
require the network to connect 100 more devices. Each layer 2 switch can connect 24
devices. The current network already has a headroom of ((48-30) + (72-55) + (24-15)) = (18
+ 17 +9) = 44 ports. If the wireless access points are subtracted, the existing network will still
be able to connect (44 – 6) = 38 more devices. For the other 62 devices, three L2 switches
can easily be added to the network by connecting them to an interface of the L3 switches of
the three LAN networks.
Wireless Network
The wireless network connectivity within the network of the Holmes institute is
ensured with the help of wireless access points. A separate subnet is used so that different IP
addresses for the wireless access of all the hundred users of the institute can be assigned.
These wireless access points obtain power through the Ethernet cable based on PoE (Babar
and Gundale 2017). Hence, these devices do not require electrical arrangements for placing in
different parts of the campus.
Remote Access
Remote access to the network services of the institute are only given to authorized
users. These are the members of the institute with whom, the IPsec VPN credentials are
shared. This way the network keeps unwanted public and invaders of the public Internet at
bay.
The networking media used by the LAN based internal networks of the different
departments are completely different. These connections make use of Ethernet cables in
straight through and crossover modes depending on the way they are used. These cables use
the Fast Ethernet and Gigabit Ethernet ports of the switches being used. Currently the overall
network of the institute is connecting (30 + 55 + 15) = 100 devices in the LAN networks
through seven of the interfaces of the multilayer switches. A 100 percent expansion will
require the network to connect 100 more devices. Each layer 2 switch can connect 24
devices. The current network already has a headroom of ((48-30) + (72-55) + (24-15)) = (18
+ 17 +9) = 44 ports. If the wireless access points are subtracted, the existing network will still
be able to connect (44 – 6) = 38 more devices. For the other 62 devices, three L2 switches
can easily be added to the network by connecting them to an interface of the L3 switches of
the three LAN networks.
Wireless Network
The wireless network connectivity within the network of the Holmes institute is
ensured with the help of wireless access points. A separate subnet is used so that different IP
addresses for the wireless access of all the hundred users of the institute can be assigned.
These wireless access points obtain power through the Ethernet cable based on PoE (Babar
and Gundale 2017). Hence, these devices do not require electrical arrangements for placing in
different parts of the campus.
Remote Access
Remote access to the network services of the institute are only given to authorized
users. These are the members of the institute with whom, the IPsec VPN credentials are
shared. This way the network keeps unwanted public and invaders of the public Internet at
bay.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK TOPOLOGY DESIGN AND SIMULATION
The possible security rules of this network can be permitting or denying specific users
from accessing the institute network. These can be – (i) Using ACL commands to permit the
network users to access the network using HTTPS protocol and use of port 443 (Reed and
Kranch 2017). (ii) Using ACL commands to deny network users from using HTTP protocol
and from using port 80.
Two possible rules in the security policy document for the network can be the
following:
a. Users must set passwords having a minimal length 8 letters.
b. Every password must contain uppercase characters, lowercase characters, numbers
and special characters.
These steps can ensure the network users stay secure from various threats of the Internet
while to remain protected from malwares and phishing attacks network users are suggested to
increase their awareness on cybersecurity.
Printer Allocation
In the departments of the schools there are one layer 2 switch for every 24 host
devices. Out of these host devices, every switch provide connection to one Ethernet printer.
These printers however, remains shared over the network allowing hosts to access the printers
from different parts of the building.
Server Room
There are servers present in every part of the school building. In these server rooms,
different servers are performing different roles. This means for different departments there is
one application server while another server performs administrative activities like DNS,
DHCP, diagnostics and the like.
The possible security rules of this network can be permitting or denying specific users
from accessing the institute network. These can be – (i) Using ACL commands to permit the
network users to access the network using HTTPS protocol and use of port 443 (Reed and
Kranch 2017). (ii) Using ACL commands to deny network users from using HTTP protocol
and from using port 80.
Two possible rules in the security policy document for the network can be the
following:
a. Users must set passwords having a minimal length 8 letters.
b. Every password must contain uppercase characters, lowercase characters, numbers
and special characters.
These steps can ensure the network users stay secure from various threats of the Internet
while to remain protected from malwares and phishing attacks network users are suggested to
increase their awareness on cybersecurity.
Printer Allocation
In the departments of the schools there are one layer 2 switch for every 24 host
devices. Out of these host devices, every switch provide connection to one Ethernet printer.
These printers however, remains shared over the network allowing hosts to access the printers
from different parts of the building.
Server Room
There are servers present in every part of the school building. In these server rooms,
different servers are performing different roles. This means for different departments there is
one application server while another server performs administrative activities like DNS,
DHCP, diagnostics and the like.

8NETWORK TOPOLOGY DESIGN AND SIMULATION
Networking Hardware
Router
The routers used in the network are responsible for the routing of the networks and
making internet services available to all departments. These routers are using the dynamic
RIP routing protocol. With the help of this protocol, the inter network routing is ensured.
Multilayer Switch
The multilayer switch is responsible for distributing the routed network from the
router to multiple layer 2 switches. These make sure that extra ports need not be added to the
router for connecting those switches thereby reducing costs. These can also double up as a
switch and a router and helps devices remain connected to the same as well as other virtual
subnets.
Access Layer Switch
These are the layer 2 switches which directly connects the host devices like servers,
printers and workstations. These switches can also inspect incoming network traffic and can
be used to forward decisions. These switches make use of MAC addresses for determining
the path through which it is to forward the decisions.
Wireless Access Points
The wireless access points are used to enable the wired network services to be
accessed by laptops and smartphones through wireless network connectivity. These devices
use IEEE 802.11ac standard to make the wireless network services available. In general, the
IP addresses are assigned to devices supporting wireless network connectivity automatically
using DHCP.
Networking Hardware
Router
The routers used in the network are responsible for the routing of the networks and
making internet services available to all departments. These routers are using the dynamic
RIP routing protocol. With the help of this protocol, the inter network routing is ensured.
Multilayer Switch
The multilayer switch is responsible for distributing the routed network from the
router to multiple layer 2 switches. These make sure that extra ports need not be added to the
router for connecting those switches thereby reducing costs. These can also double up as a
switch and a router and helps devices remain connected to the same as well as other virtual
subnets.
Access Layer Switch
These are the layer 2 switches which directly connects the host devices like servers,
printers and workstations. These switches can also inspect incoming network traffic and can
be used to forward decisions. These switches make use of MAC addresses for determining
the path through which it is to forward the decisions.
Wireless Access Points
The wireless access points are used to enable the wired network services to be
accessed by laptops and smartphones through wireless network connectivity. These devices
use IEEE 802.11ac standard to make the wireless network services available. In general, the
IP addresses are assigned to devices supporting wireless network connectivity automatically
using DHCP.
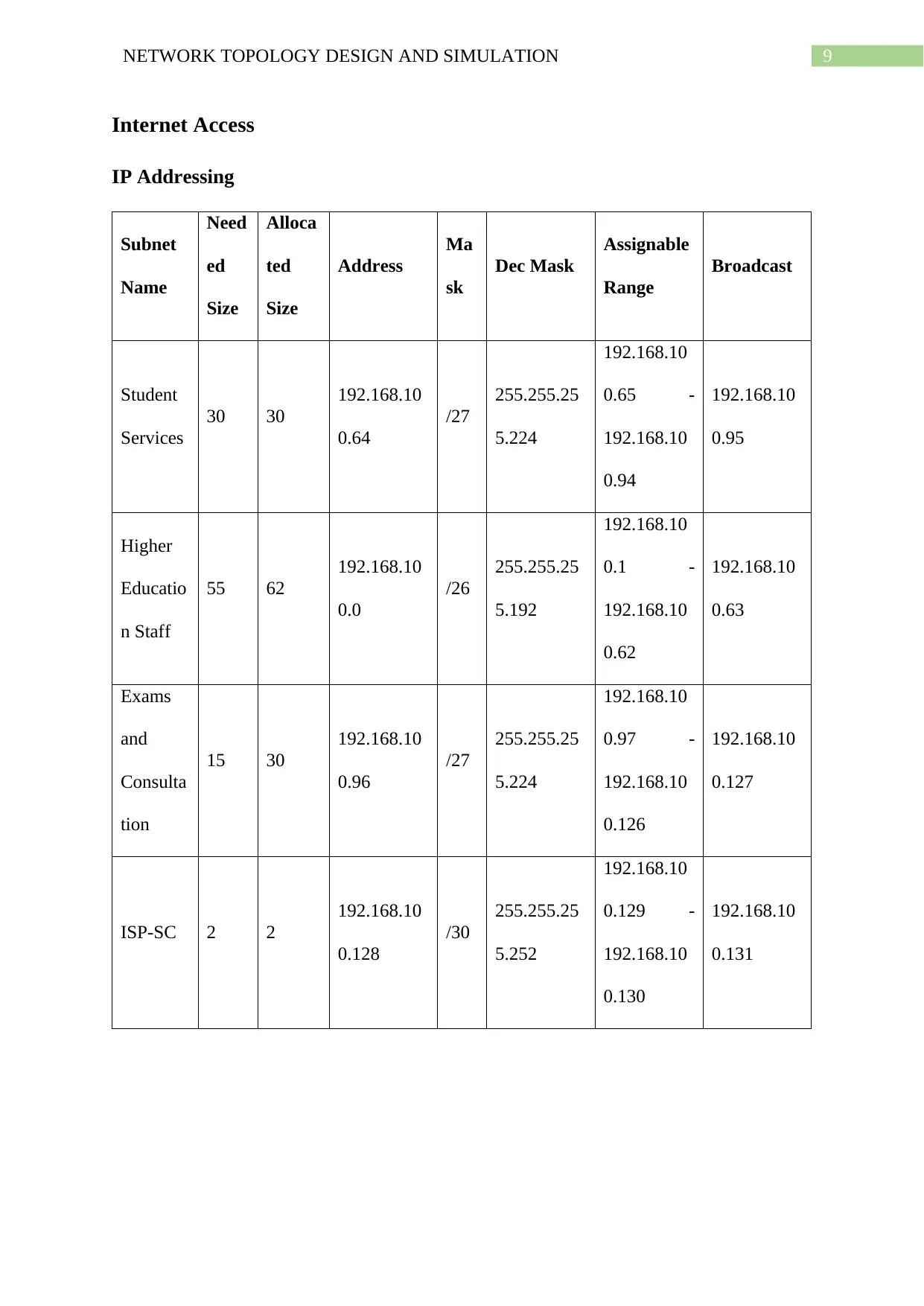
9NETWORK TOPOLOGY DESIGN AND SIMULATION
Internet Access
IP Addressing
Subnet
Name
Need
ed
Size
Alloca
ted
Size
Address
Ma
sk
Dec Mask
Assignable
Range
Broadcast
Student
Services
30 30
192.168.10
0.64
/27
255.255.25
5.224
192.168.10
0.65 -
192.168.10
0.94
192.168.10
0.95
Higher
Educatio
n Staff
55 62
192.168.10
0.0
/26
255.255.25
5.192
192.168.10
0.1 -
192.168.10
0.62
192.168.10
0.63
Exams
and
Consulta
tion
15 30
192.168.10
0.96
/27
255.255.25
5.224
192.168.10
0.97 -
192.168.10
0.126
192.168.10
0.127
ISP-SC 2 2
192.168.10
0.128
/30
255.255.25
5.252
192.168.10
0.129 -
192.168.10
0.130
192.168.10
0.131
Internet Access
IP Addressing
Subnet
Name
Need
ed
Size
Alloca
ted
Size
Address
Ma
sk
Dec Mask
Assignable
Range
Broadcast
Student
Services
30 30
192.168.10
0.64
/27
255.255.25
5.224
192.168.10
0.65 -
192.168.10
0.94
192.168.10
0.95
Higher
Educatio
n Staff
55 62
192.168.10
0.0
/26
255.255.25
5.192
192.168.10
0.1 -
192.168.10
0.62
192.168.10
0.63
Exams
and
Consulta
tion
15 30
192.168.10
0.96
/27
255.255.25
5.224
192.168.10
0.97 -
192.168.10
0.126
192.168.10
0.127
ISP-SC 2 2
192.168.10
0.128
/30
255.255.25
5.252
192.168.10
0.129 -
192.168.10
0.130
192.168.10
0.131
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
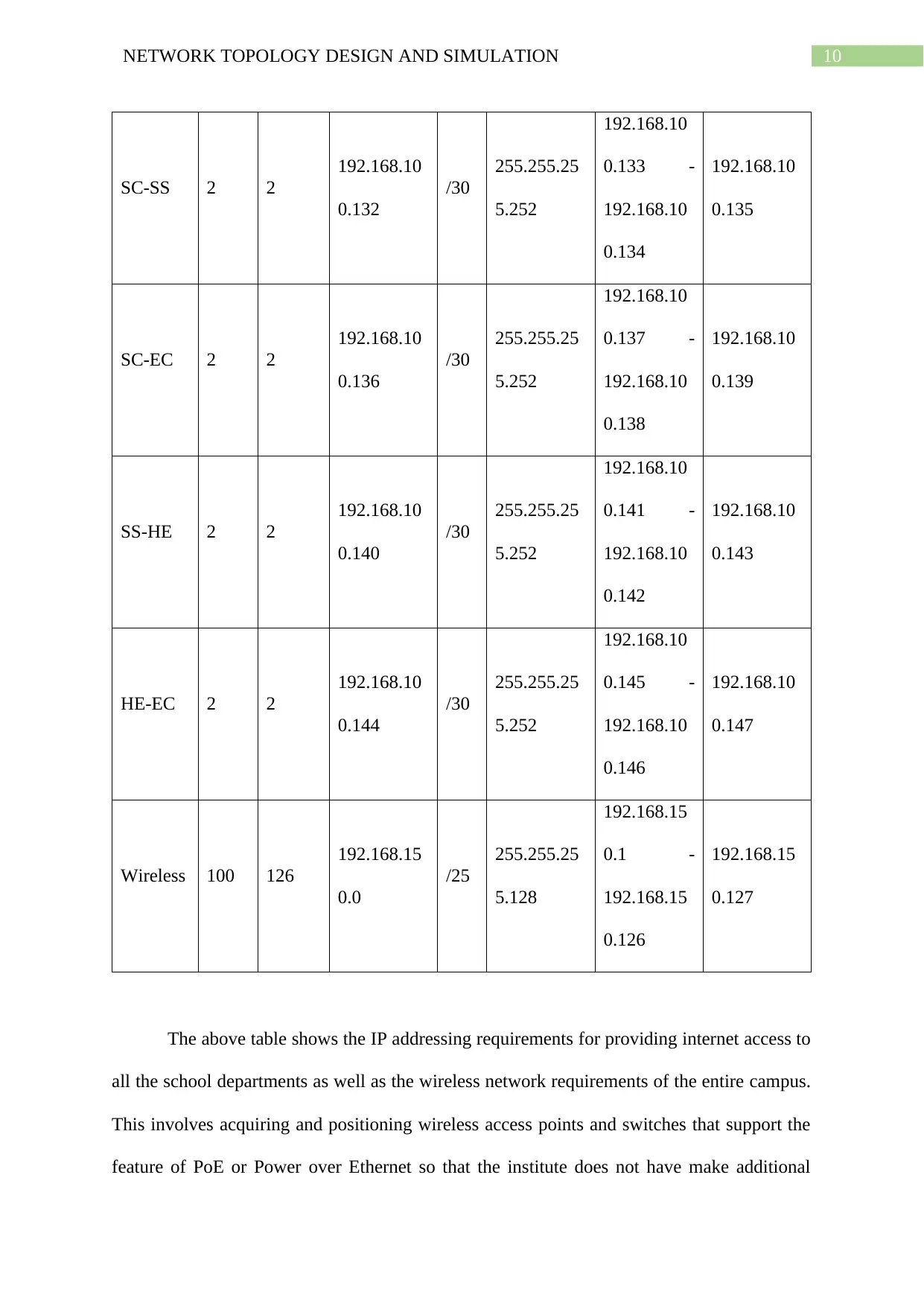
10NETWORK TOPOLOGY DESIGN AND SIMULATION
SC-SS 2 2
192.168.10
0.132
/30
255.255.25
5.252
192.168.10
0.133 -
192.168.10
0.134
192.168.10
0.135
SC-EC 2 2
192.168.10
0.136
/30
255.255.25
5.252
192.168.10
0.137 -
192.168.10
0.138
192.168.10
0.139
SS-HE 2 2
192.168.10
0.140
/30
255.255.25
5.252
192.168.10
0.141 -
192.168.10
0.142
192.168.10
0.143
HE-EC 2 2
192.168.10
0.144
/30
255.255.25
5.252
192.168.10
0.145 -
192.168.10
0.146
192.168.10
0.147
Wireless 100 126
192.168.15
0.0
/25
255.255.25
5.128
192.168.15
0.1 -
192.168.15
0.126
192.168.15
0.127
The above table shows the IP addressing requirements for providing internet access to
all the school departments as well as the wireless network requirements of the entire campus.
This involves acquiring and positioning wireless access points and switches that support the
feature of PoE or Power over Ethernet so that the institute does not have make additional
SC-SS 2 2
192.168.10
0.132
/30
255.255.25
5.252
192.168.10
0.133 -
192.168.10
0.134
192.168.10
0.135
SC-EC 2 2
192.168.10
0.136
/30
255.255.25
5.252
192.168.10
0.137 -
192.168.10
0.138
192.168.10
0.139
SS-HE 2 2
192.168.10
0.140
/30
255.255.25
5.252
192.168.10
0.141 -
192.168.10
0.142
192.168.10
0.143
HE-EC 2 2
192.168.10
0.144
/30
255.255.25
5.252
192.168.10
0.145 -
192.168.10
0.146
192.168.10
0.147
Wireless 100 126
192.168.15
0.0
/25
255.255.25
5.128
192.168.15
0.1 -
192.168.15
0.126
192.168.15
0.127
The above table shows the IP addressing requirements for providing internet access to
all the school departments as well as the wireless network requirements of the entire campus.
This involves acquiring and positioning wireless access points and switches that support the
feature of PoE or Power over Ethernet so that the institute does not have make additional
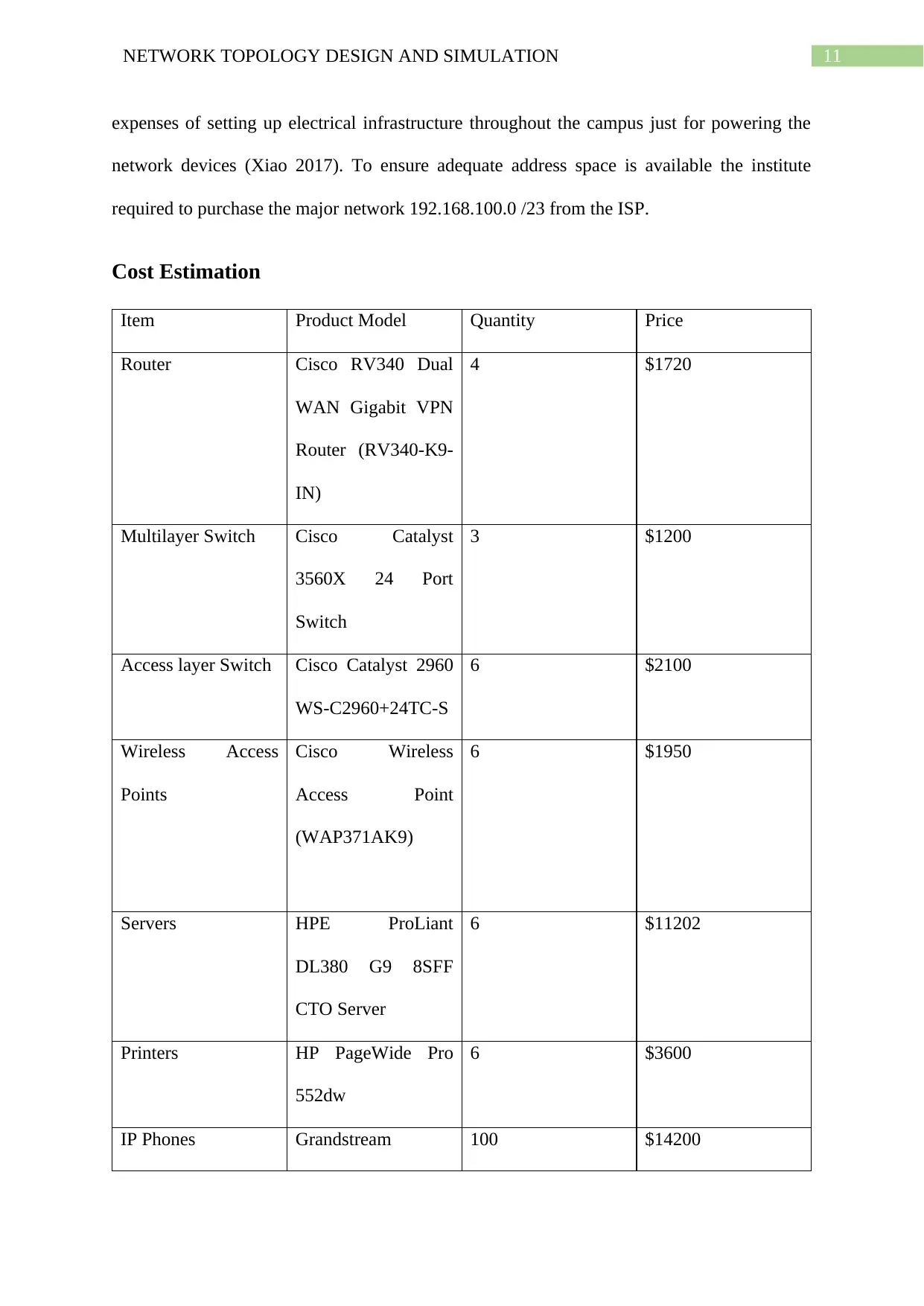
11NETWORK TOPOLOGY DESIGN AND SIMULATION
expenses of setting up electrical infrastructure throughout the campus just for powering the
network devices (Xiao 2017). To ensure adequate address space is available the institute
required to purchase the major network 192.168.100.0 /23 from the ISP.
Cost Estimation
Item Product Model Quantity Price
Router Cisco RV340 Dual
WAN Gigabit VPN
Router (RV340-K9-
IN)
4 $1720
Multilayer Switch Cisco Catalyst
3560X 24 Port
Switch
3 $1200
Access layer Switch Cisco Catalyst 2960
WS-C2960+24TC-S
6 $2100
Wireless Access
Points
Cisco Wireless
Access Point
(WAP371AK9)
6 $1950
Servers HPE ProLiant
DL380 G9 8SFF
CTO Server
6 $11202
Printers HP PageWide Pro
552dw
6 $3600
IP Phones Grandstream 100 $14200
expenses of setting up electrical infrastructure throughout the campus just for powering the
network devices (Xiao 2017). To ensure adequate address space is available the institute
required to purchase the major network 192.168.100.0 /23 from the ISP.
Cost Estimation
Item Product Model Quantity Price
Router Cisco RV340 Dual
WAN Gigabit VPN
Router (RV340-K9-
IN)
4 $1720
Multilayer Switch Cisco Catalyst
3560X 24 Port
Switch
3 $1200
Access layer Switch Cisco Catalyst 2960
WS-C2960+24TC-S
6 $2100
Wireless Access
Points
Cisco Wireless
Access Point
(WAP371AK9)
6 $1950
Servers HPE ProLiant
DL380 G9 8SFF
CTO Server
6 $11202
Printers HP PageWide Pro
552dw
6 $3600
IP Phones Grandstream 100 $14200

12NETWORK TOPOLOGY DESIGN AND SIMULATION
GXP2160
Workstations Lenovo
ThinkStation P500
100 $43000
Total Cost $78,972
Conclusion
To conclude, the report successfully proposes a network topology design specifically
for the Holmes Institute. For this the report required to present the network topology design
by drawing it in the Cisco Packet Tracer simulation software. The report is then observed to
provide explanations through an overview of the network design. In this overview, the report
also describes the networking model, architecture and the physical networking topologies and
how they help build the network of the institute. After that the report provides detailed
information on the required cabling and other media that were necessary for building the
network. This is followed by explanation of the wireless networks, the remote access, and
printer allocation, server room, networking hardware, internet access and cost estimation. In
these sections the report explains how much cabling and networking media is enough for
ensuring future expansion and scalability of the network, how wireless network is being
obtained, usage of printers and servers, role of networking devices, how internet access is
ensured for entire campus and the cost to implement the network. With these points covered
the report comes to an end.
GXP2160
Workstations Lenovo
ThinkStation P500
100 $43000
Total Cost $78,972
Conclusion
To conclude, the report successfully proposes a network topology design specifically
for the Holmes Institute. For this the report required to present the network topology design
by drawing it in the Cisco Packet Tracer simulation software. The report is then observed to
provide explanations through an overview of the network design. In this overview, the report
also describes the networking model, architecture and the physical networking topologies and
how they help build the network of the institute. After that the report provides detailed
information on the required cabling and other media that were necessary for building the
network. This is followed by explanation of the wireless networks, the remote access, and
printer allocation, server room, networking hardware, internet access and cost estimation. In
these sections the report explains how much cabling and networking media is enough for
ensuring future expansion and scalability of the network, how wireless network is being
obtained, usage of printers and servers, role of networking devices, how internet access is
ensured for entire campus and the cost to implement the network. With these points covered
the report comes to an end.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13NETWORK TOPOLOGY DESIGN AND SIMULATION
References
Airi, P. and Anderson, P.K., 2017. Cisco Packet Tracer as a teaching and learning tool for
computer networks in DWU. Contemporary PNG Studies, 26, p.88.
Babar, S.B. and Gundale, A.S., 2017. Sensor Network and Its Power Management using
POE.
Dodia, P. and Zhauniarovich, Y., 2019, November. Poster: SDN-based System to Filter Out
DRDoS Amplification Traffic in ISP Networks. In Proceedings of the 2019 ACM SIGSAC
Conference on Computer and Communications Security (pp. 2645-2647).
Ferdous, M., 2019. Network Monitoring and Bandwidth management of an ISP.
Hossain, M.A. and Zannat, M., 2019. Simulation and Design of University Area Network
Scenario (UANS) using Cisco Packet Tracer. Global Journal of Computer Science and
Technology.
Leon, A., Parra, O. and Bermudez, G., 2018. LAN-WAN-LAN end-to-end Network
Simulation with NS2. International Journal of Applied Engineering Research, 13(17),
pp.13136-13140.
Luo, Y., 2017, September. Analysis of Wide Area Network Security Technology System. In
2017 5th International Conference on Mechatronics, Materials, Chemistry and Computer
Engineering (ICMMCCE 2017). Atlantis Press.
Ozkan-Canbolat, E. and Beraha, A., 2016. A configurational approach to network topology
design for product innovation. Journal of Business Research, 69(11), pp.5216-5221.
References
Airi, P. and Anderson, P.K., 2017. Cisco Packet Tracer as a teaching and learning tool for
computer networks in DWU. Contemporary PNG Studies, 26, p.88.
Babar, S.B. and Gundale, A.S., 2017. Sensor Network and Its Power Management using
POE.
Dodia, P. and Zhauniarovich, Y., 2019, November. Poster: SDN-based System to Filter Out
DRDoS Amplification Traffic in ISP Networks. In Proceedings of the 2019 ACM SIGSAC
Conference on Computer and Communications Security (pp. 2645-2647).
Ferdous, M., 2019. Network Monitoring and Bandwidth management of an ISP.
Hossain, M.A. and Zannat, M., 2019. Simulation and Design of University Area Network
Scenario (UANS) using Cisco Packet Tracer. Global Journal of Computer Science and
Technology.
Leon, A., Parra, O. and Bermudez, G., 2018. LAN-WAN-LAN end-to-end Network
Simulation with NS2. International Journal of Applied Engineering Research, 13(17),
pp.13136-13140.
Luo, Y., 2017, September. Analysis of Wide Area Network Security Technology System. In
2017 5th International Conference on Mechatronics, Materials, Chemistry and Computer
Engineering (ICMMCCE 2017). Atlantis Press.
Ozkan-Canbolat, E. and Beraha, A., 2016. A configurational approach to network topology
design for product innovation. Journal of Business Research, 69(11), pp.5216-5221.

14NETWORK TOPOLOGY DESIGN AND SIMULATION
Reed, A. and Kranch, M., 2017, March. Identifying HTTPS-protected Netflix videos in real-
time. In Proceedings of the Seventh ACM on Conference on Data and Application Security
and Privacy (pp. 361-368).
Saad, L.B., Weerasinghe, T. and Beferull-Lozano, B., 2017. Topology design to increase
network lifetime in WSN for graph filtering in consensus processes. In 2017 25th European
Signal Processing Conference (EUSIPCO) (pp. 351-355). IEEE.
Salman, F.A., 2017. Implementation of IPsec-VPN tunneling using GNS3. Indonesian
Journal of Electrical Engineering and Computer Science, 7(3), pp.855-860.
Villanueva, L. and Gustilo, R.C., 2018. Artificial neural network based antenna sensitivity
assignments for chaotic Internet Service Provider network architecture. International Journal
of Engineering and Technology (UAE), 7(2), pp.14-17.
Xiao, Z., 2017. An Efficient Power Over Ethernet (PoE) Interface With Current-Balancing
and Hot-Swapping Control. IEEE Transactions on Industrial Electronics, 65(3), pp.2496-
2506.
Xu, W., Chen, F. and Liu, J., 2016, September. The Application of MATLAB Serial Interface
Communication Technology in Cylinder Displacement Acquisition System. In 2016 6th
International Conference on Management, Education, Information and Control (MEICI
2016). Atlantis Press.
Reed, A. and Kranch, M., 2017, March. Identifying HTTPS-protected Netflix videos in real-
time. In Proceedings of the Seventh ACM on Conference on Data and Application Security
and Privacy (pp. 361-368).
Saad, L.B., Weerasinghe, T. and Beferull-Lozano, B., 2017. Topology design to increase
network lifetime in WSN for graph filtering in consensus processes. In 2017 25th European
Signal Processing Conference (EUSIPCO) (pp. 351-355). IEEE.
Salman, F.A., 2017. Implementation of IPsec-VPN tunneling using GNS3. Indonesian
Journal of Electrical Engineering and Computer Science, 7(3), pp.855-860.
Villanueva, L. and Gustilo, R.C., 2018. Artificial neural network based antenna sensitivity
assignments for chaotic Internet Service Provider network architecture. International Journal
of Engineering and Technology (UAE), 7(2), pp.14-17.
Xiao, Z., 2017. An Efficient Power Over Ethernet (PoE) Interface With Current-Balancing
and Hot-Swapping Control. IEEE Transactions on Industrial Electronics, 65(3), pp.2496-
2506.
Xu, W., Chen, F. and Liu, J., 2016, September. The Application of MATLAB Serial Interface
Communication Technology in Cylinder Displacement Acquisition System. In 2016 6th
International Conference on Management, Education, Information and Control (MEICI
2016). Atlantis Press.
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





