Network Infrastructure Security and Configuration Report
VerifiedAdded on 2021/06/18
|5
|1189
|38
Report
AI Summary
This report delves into the critical aspects of network infrastructure, focusing on security and efficient configuration. It emphasizes the importance of a robust network for optimal business operations, covering various routing protocols like OSPF, EIGRP, and RIPv2. The report explores methods for securing these protocols through MD5 authentication to prevent attacks and ensure data integrity. It also explains the implementation of virtual links to connect different network areas and the redistribution process for seamless routing information exchange between different routing domains. The report addresses potential challenges such as routing loops and convergence issues, highlighting the use of metrics and route maps to mitigate these problems. Overall, the report provides a comprehensive overview of network infrastructure security, configuration, and implementation strategies.

To provide the best possible services the user and the customer of the business the crucial factor
is the network infrastructure of the business. Various type of the network traffic, including data
files, email, IP telephony and video application for multiple business units must support the
exchange by an enterprise network. To prevent the unnecessary distribution of traffic the
network must be configured, to ensure the optimization. The network has to be remained
available for the users and must be scale effectively and easily and that has to be ensured by the
network architecture. Internetwork is desirable when the routing protocol that is running
throughout the entire IP is single, for a number of reason multi protocol routing is common,
company mergers, multiple network administrator manage different multiple departments and
the environments of multi vendor. The multi protocol network is configured by Open Shortest
Path First (OSPF), Enhanced Interior Gateway Routing Protocol (EIGRP), and Routing
Information Protocol version two (RIPv2) for securing and efficiently use the network
infrastructure that is existing can be implemented. The connection to the boundary routers of
the Internet service providers (ISPs) will be configured by the Border Gateway Protocol (BGP)
to give permission to the organization to connect their network to the Internet.
is the network infrastructure of the business. Various type of the network traffic, including data
files, email, IP telephony and video application for multiple business units must support the
exchange by an enterprise network. To prevent the unnecessary distribution of traffic the
network must be configured, to ensure the optimization. The network has to be remained
available for the users and must be scale effectively and easily and that has to be ensured by the
network architecture. Internetwork is desirable when the routing protocol that is running
throughout the entire IP is single, for a number of reason multi protocol routing is common,
company mergers, multiple network administrator manage different multiple departments and
the environments of multi vendor. The multi protocol network is configured by Open Shortest
Path First (OSPF), Enhanced Interior Gateway Routing Protocol (EIGRP), and Routing
Information Protocol version two (RIPv2) for securing and efficiently use the network
infrastructure that is existing can be implemented. The connection to the boundary routers of
the Internet service providers (ISPs) will be configured by the Border Gateway Protocol (BGP)
to give permission to the organization to connect their network to the Internet.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
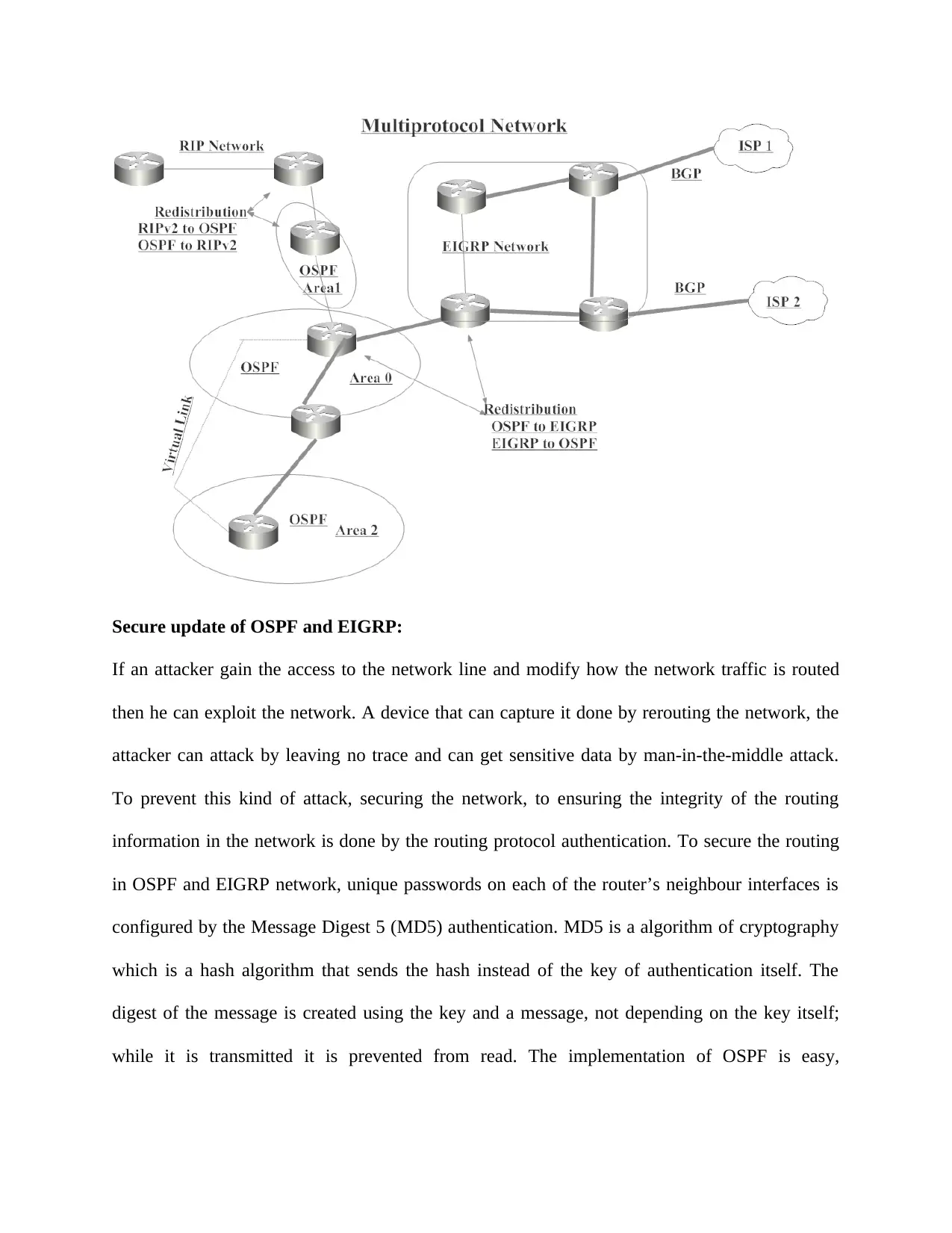
Secure update of OSPF and EIGRP:
If an attacker gain the access to the network line and modify how the network traffic is routed
then he can exploit the network. A device that can capture it done by rerouting the network, the
attacker can attack by leaving no trace and can get sensitive data by man-in-the-middle attack.
To prevent this kind of attack, securing the network, to ensuring the integrity of the routing
information in the network is done by the routing protocol authentication. To secure the routing
in OSPF and EIGRP network, unique passwords on each of the router’s neighbour interfaces is
configured by the Message Digest 5 (MD5) authentication. MD5 is a algorithm of cryptography
which is a hash algorithm that sends the hash instead of the key of authentication itself. The
digest of the message is created using the key and a message, not depending on the key itself;
while it is transmitted it is prevented from read. The implementation of OSPF is easy,
If an attacker gain the access to the network line and modify how the network traffic is routed
then he can exploit the network. A device that can capture it done by rerouting the network, the
attacker can attack by leaving no trace and can get sensitive data by man-in-the-middle attack.
To prevent this kind of attack, securing the network, to ensuring the integrity of the routing
information in the network is done by the routing protocol authentication. To secure the routing
in OSPF and EIGRP network, unique passwords on each of the router’s neighbour interfaces is
configured by the Message Digest 5 (MD5) authentication. MD5 is a algorithm of cryptography
which is a hash algorithm that sends the hash instead of the key of authentication itself. The
digest of the message is created using the key and a message, not depending on the key itself;
while it is transmitted it is prevented from read. The implementation of OSPF is easy,

implementation of EIGRP of the MD5 is bit difficult. The following commands will use to
implement the OFPF authentication:
{ Router(config-if)# ip ospf message-digest-key key-id md5 password
Router(config-if)# ip ospf authentication message-digest }
When the MD5 authentication configured on EIGRP, every router in the key chain must contains
the key ID and the password (key-string) and then the configuration of MD5 authentication must
be on the interfaces. If required then time limit is provided in the MD5 authentication configured
in the EIGRP for more control. Using the following commands the EIGRP authentication is
configured:
Router(config)#key chain keyname
Router(config-keychain)#key #
Router(config-keychain-key)#key-string password
Router(config)#interface interface-id
Router(config-if)#ip authentication mode eigrp Autonomous System (AS) md5
Router(config-if)#ip authentication key-chain eigrp AS keyname
To prevent the attacker from getting the key to view the configuration of the router and to
encrypt the key, one command is also configured on the router that is service password-
encryption.
Virtual Link Implementation
The sub domains that are divided by the OSPF protocol are called areas. Numbers of network
routers are consisted in the each area, and links with the same area ID. Within the area each
routers maintain their own database for the belonging area. Because all the information does not
contain by the router of another router that is outside of the same area, a smaller database can be
implement the OFPF authentication:
{ Router(config-if)# ip ospf message-digest-key key-id md5 password
Router(config-if)# ip ospf authentication message-digest }
When the MD5 authentication configured on EIGRP, every router in the key chain must contains
the key ID and the password (key-string) and then the configuration of MD5 authentication must
be on the interfaces. If required then time limit is provided in the MD5 authentication configured
in the EIGRP for more control. Using the following commands the EIGRP authentication is
configured:
Router(config)#key chain keyname
Router(config-keychain)#key #
Router(config-keychain-key)#key-string password
Router(config)#interface interface-id
Router(config-if)#ip authentication mode eigrp Autonomous System (AS) md5
Router(config-if)#ip authentication key-chain eigrp AS keyname
To prevent the attacker from getting the key to view the configuration of the router and to
encrypt the key, one command is also configured on the router that is service password-
encryption.
Virtual Link Implementation
The sub domains that are divided by the OSPF protocol are called areas. Numbers of network
routers are consisted in the each area, and links with the same area ID. Within the area each
routers maintain their own database for the belonging area. Because all the information does not
contain by the router of another router that is outside of the same area, a smaller database can be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

managed by the router. All the areas are autonomous system of OSPF authentication must
connect to the area 0 that is the called backbone area. If there is no connection established by the
router with the backbone area then the network engineer have to establish a virtual link to the
backbone of the area through a transit area or non-backbone area. Virtual links are the links that
are logical and uses the shortest path between the backbone area border router of the transit area
and area border router of the non-backbone connected area. The area having single common non-
backbone, there the virtual links can be configured between two routers those have an inter face
but cannot be configured across the multiple transit areas. The following command is used for
the configuration of the virtual link on each area border router’s interface:
Router(config)#router ospf area
Router(config-router)#area area-id virtual-link router-id
Where the area ID is area-id of the transmit area and the router ID is router-id of the virtual link
neighbour.
Redistribution Solution Implementation
In the network routing, to provide the full connectivity of the network and the redundant
connectivity between the routing domains redistribution process is used that is routing the
information from one domain to the another domain. Route distribution is must needed to allow
the routers for communicating and for the network traffic pass the network infrastructure is
configured by the OSPF, EIGRP, and RIPv2 routing protocols. The routing protocol
characteristics are different, metrics, classful and classless capabilities, administrative distance
can affect the distribution. There are boundary routers that incorrect the different protocol
regions and they have to be configured to run the all protocols for the exchanging routes.
Redistribution can be one way from the one domain to another or can be two ways that is bi-
connect to the area 0 that is the called backbone area. If there is no connection established by the
router with the backbone area then the network engineer have to establish a virtual link to the
backbone of the area through a transit area or non-backbone area. Virtual links are the links that
are logical and uses the shortest path between the backbone area border router of the transit area
and area border router of the non-backbone connected area. The area having single common non-
backbone, there the virtual links can be configured between two routers those have an inter face
but cannot be configured across the multiple transit areas. The following command is used for
the configuration of the virtual link on each area border router’s interface:
Router(config)#router ospf area
Router(config-router)#area area-id virtual-link router-id
Where the area ID is area-id of the transmit area and the router ID is router-id of the virtual link
neighbour.
Redistribution Solution Implementation
In the network routing, to provide the full connectivity of the network and the redundant
connectivity between the routing domains redistribution process is used that is routing the
information from one domain to the another domain. Route distribution is must needed to allow
the routers for communicating and for the network traffic pass the network infrastructure is
configured by the OSPF, EIGRP, and RIPv2 routing protocols. The routing protocol
characteristics are different, metrics, classful and classless capabilities, administrative distance
can affect the distribution. There are boundary routers that incorrect the different protocol
regions and they have to be configured to run the all protocols for the exchanging routes.
Redistribution can be one way from the one domain to another or can be two ways that is bi-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

directional. One point two way redistribution from RIPv2 to OSPF, OSPF to EIGRP and vice-
versa is implemented for our network infrastructure, so that the all three routers gets the router
information among them and propagated throughout the network. When implementing the
multiprotocol network many problems arise that are, routing loops, convergence time is
inconsistent, and the routing information is incompatible. The administrator must have to
configure metrics and build rout maps for the route traffic to avoid from routing loops and to
avoid the administrative issues of distance is used to prevent these issues from happening. The
redistributes routes that are having high metrics will not be used over the original routes if the
information is redistributed back on the main routing protocol. To define the different network
segment the route maps will configured with the access list. To configured the boundary routers
between the OSPF and RIPv2 the following commands will be used:
versa is implemented for our network infrastructure, so that the all three routers gets the router
information among them and propagated throughout the network. When implementing the
multiprotocol network many problems arise that are, routing loops, convergence time is
inconsistent, and the routing information is incompatible. The administrator must have to
configure metrics and build rout maps for the route traffic to avoid from routing loops and to
avoid the administrative issues of distance is used to prevent these issues from happening. The
redistributes routes that are having high metrics will not be used over the original routes if the
information is redistributed back on the main routing protocol. To define the different network
segment the route maps will configured with the access list. To configured the boundary routers
between the OSPF and RIPv2 the following commands will be used:
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





