Cyber Security: Nmap, Firewall Setup and Risk Mitigation Plan
VerifiedAdded on 2022/09/09
|15
|1453
|15
Report
AI Summary
This report provides an overview of network security, focusing on the use of Nmap, a network vulnerability scanning tool, within the Kali Linux environment. The paper details the functionality of Nmap in identifying network vulnerabilities, including open ports, operating systems, and device names. A risk mitigation plan is outlined, emphasizing the importance of understanding common network attacks, utilizing Nmap for both basic and advanced scanning techniques, inventorying vulnerabilities, and assessing associated risks. Furthermore, the report includes practical aspects of firewall setup within Kali Linux, detailing the steps involved in creating firewall rules to secure a network. The conclusion highlights the significance of firewalls as essential security systems and emphasizes the role of Nmap in vulnerability assessment. The report provides a valuable resource for understanding network security principles and implementing effective protective measures.

Running head: CYBER SECURITY
CYBER SECURITY
Name of the Student
Name of the University
Author Note
CYBER SECURITY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBER SECURITY 1
Executive summary:
The purpose of this paper is to discuss about Nmap tool which is known as network
vulnerability scanner tool. Nmap is basically used in kali Linux for penetration testing. In this
report, the discussion about firewall rule creation in kali Linux will be also done and on
behalf of that screenshots will be provided.
Executive summary:
The purpose of this paper is to discuss about Nmap tool which is known as network
vulnerability scanner tool. Nmap is basically used in kali Linux for penetration testing. In this
report, the discussion about firewall rule creation in kali Linux will be also done and on
behalf of that screenshots will be provided.

2CYBER SECURITY
Table of Contents
Introduction:...............................................................................................................................3
Nmap:.........................................................................................................................................3
Risk mitigation plan:..................................................................................................................7
Analysis of the scenario:............................................................................................................8
Firewall setup:............................................................................................................................8
Conclusion:..............................................................................................................................13
References:...............................................................................................................................14
Table of Contents
Introduction:...............................................................................................................................3
Nmap:.........................................................................................................................................3
Risk mitigation plan:..................................................................................................................7
Analysis of the scenario:............................................................................................................8
Firewall setup:............................................................................................................................8
Conclusion:..............................................................................................................................13
References:...............................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY
Introduction:
Nmap is a network vulnerability scanning tool that is used in kali Linux for
penetration testing on a network for identifying network vulnerabilities. In this paper a risk
mitigation plan will be prepared and some of the firewall rules will be created for securing
the network.
Nmap:
A common problem in the network system is that the network frameworks are very
much complicated for a normal person for understanding properly. For learning which port is
open as well as what are the rules, the tool called Nmap is used. The tool can scan the
network where the computers are connected as well as provide output a list of the ports,
operating systems, name of the devices etc. The tools can be used by the attackers for gaining
access to the ports that are uncontrolled. If a hacker can install the Nmap tool in a system
then the attacker will be having the ability to control the system.
Below is the result of a network scanning by Nmap:
Introduction:
Nmap is a network vulnerability scanning tool that is used in kali Linux for
penetration testing on a network for identifying network vulnerabilities. In this paper a risk
mitigation plan will be prepared and some of the firewall rules will be created for securing
the network.
Nmap:
A common problem in the network system is that the network frameworks are very
much complicated for a normal person for understanding properly. For learning which port is
open as well as what are the rules, the tool called Nmap is used. The tool can scan the
network where the computers are connected as well as provide output a list of the ports,
operating systems, name of the devices etc. The tools can be used by the attackers for gaining
access to the ports that are uncontrolled. If a hacker can install the Nmap tool in a system
then the attacker will be having the ability to control the system.
Below is the result of a network scanning by Nmap:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
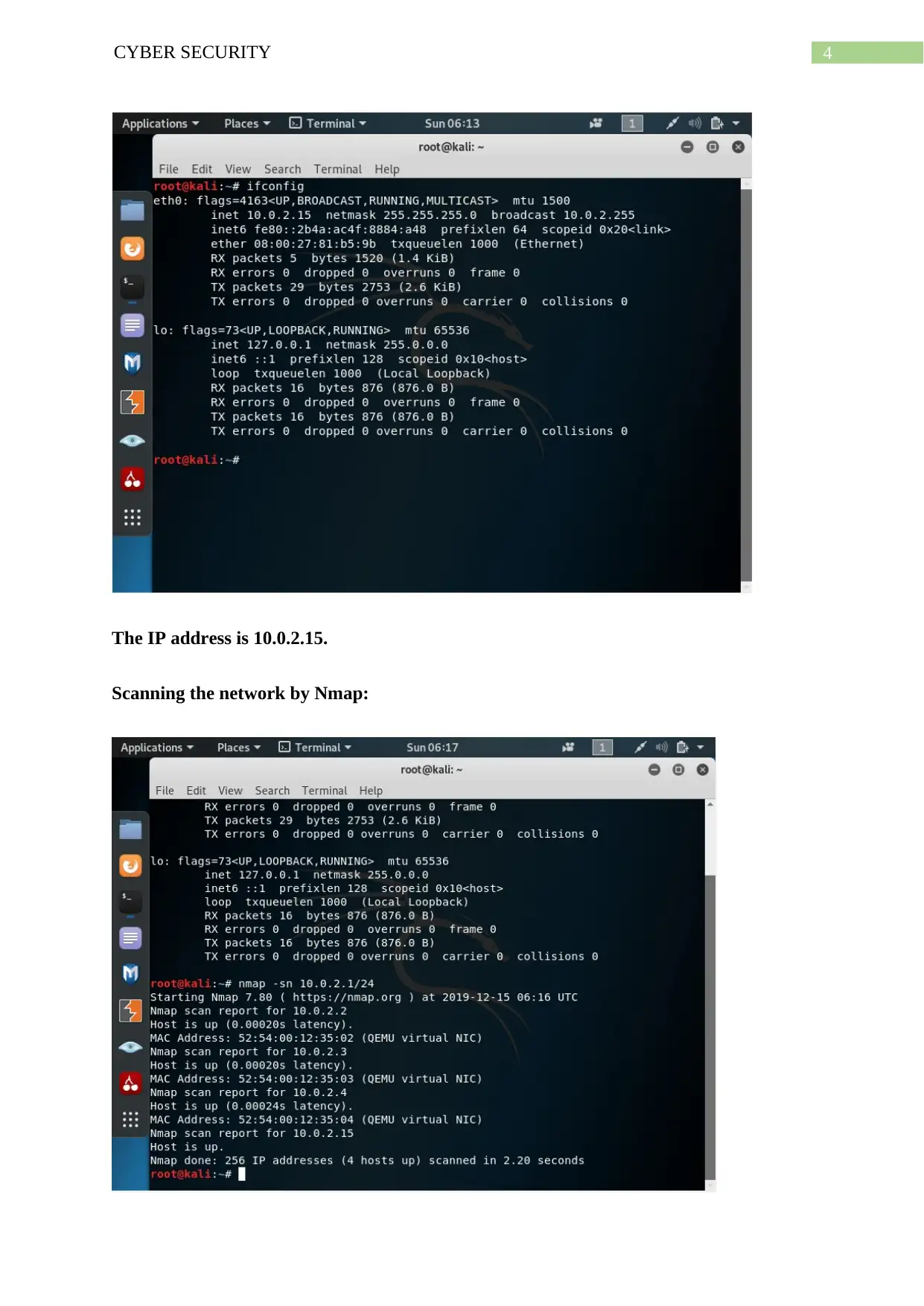
4CYBER SECURITY
The IP address is 10.0.2.15.
Scanning the network by Nmap:
The IP address is 10.0.2.15.
Scanning the network by Nmap:
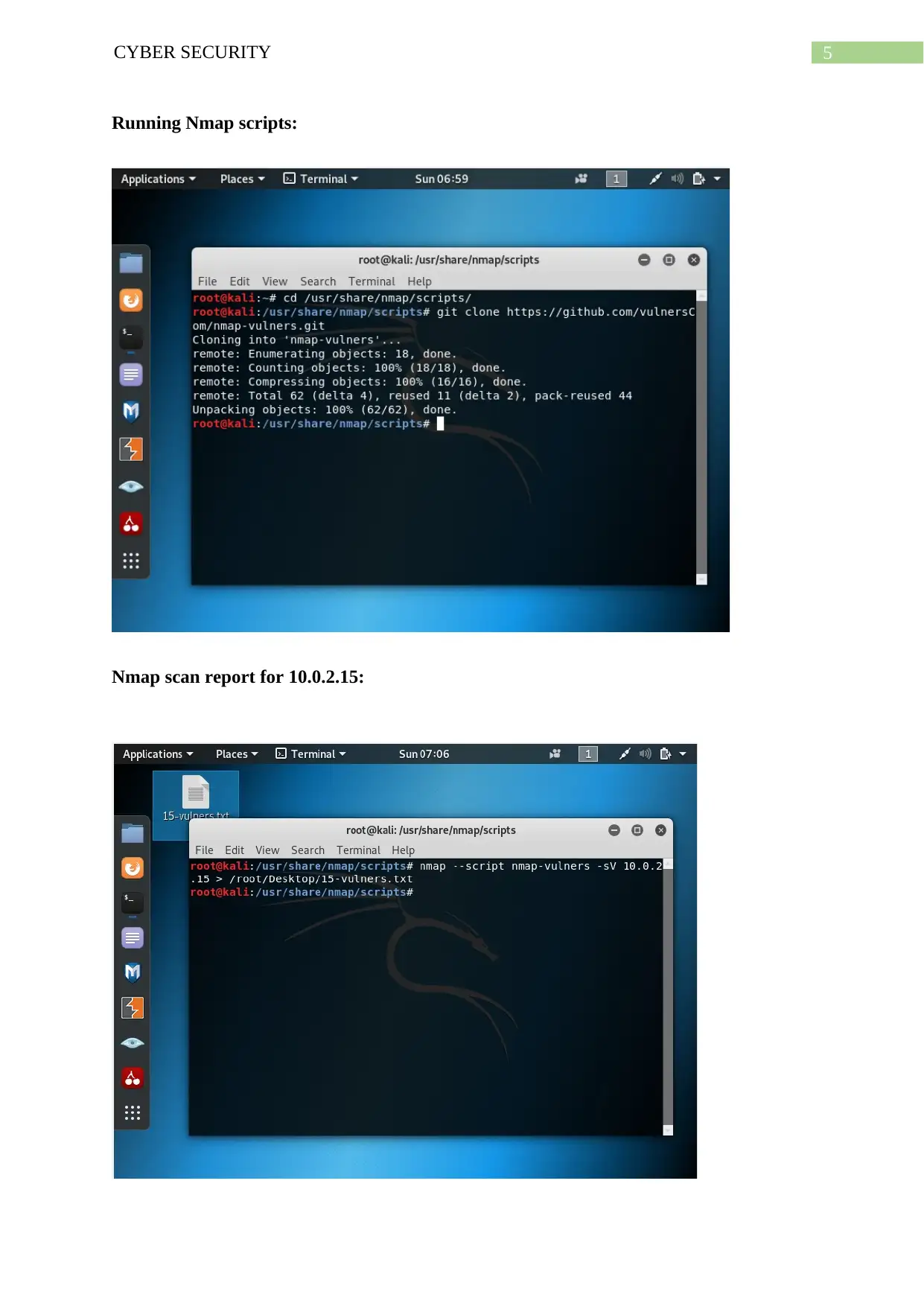
5CYBER SECURITY
Running Nmap scripts:
Nmap scan report for 10.0.2.15:
Running Nmap scripts:
Nmap scan report for 10.0.2.15:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
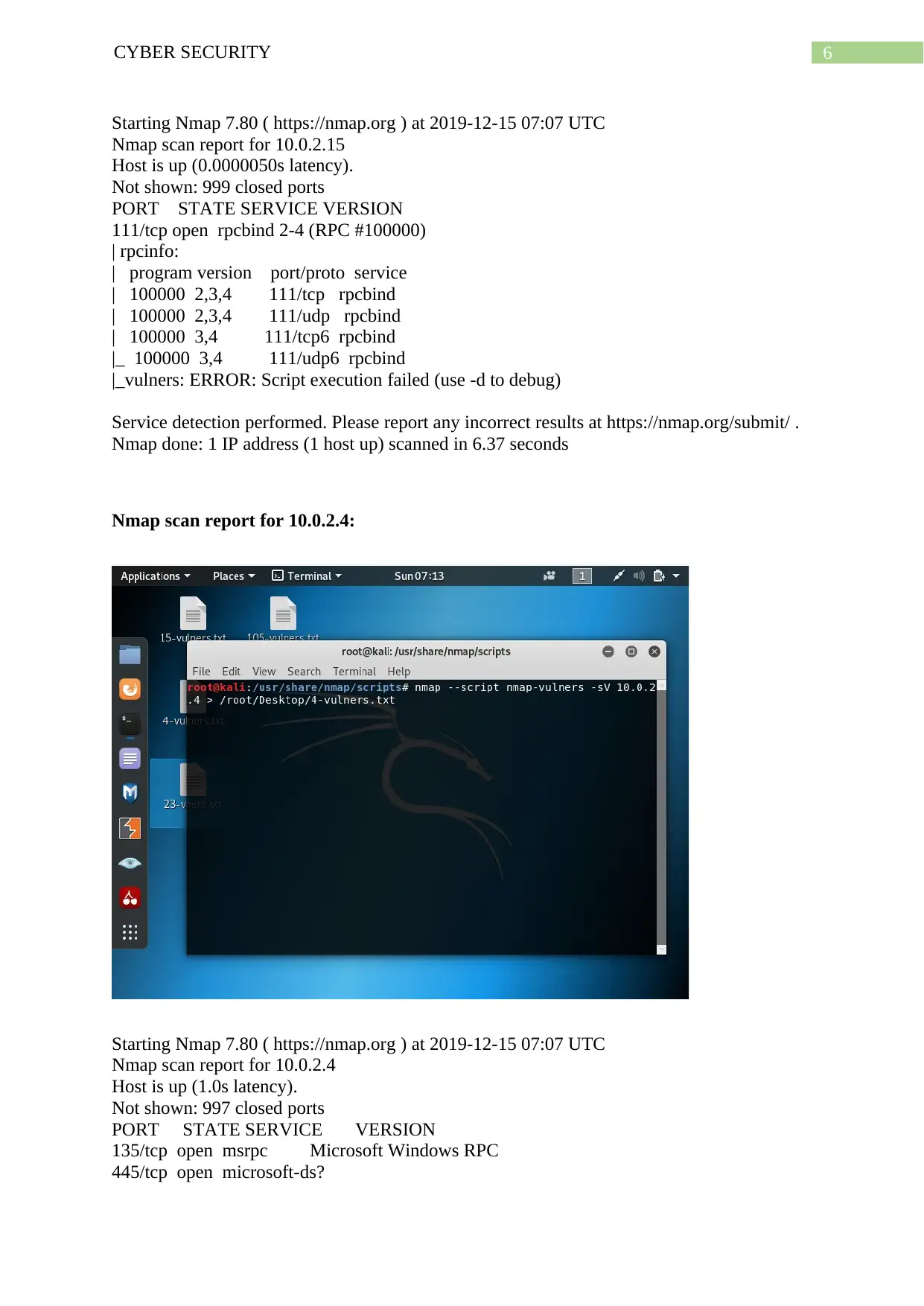
6CYBER SECURITY
Starting Nmap 7.80 ( https://nmap.org ) at 2019-12-15 07:07 UTC
Nmap scan report for 10.0.2.15
Host is up (0.0000050s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
|_ 100000 3,4 111/udp6 rpcbind
|_vulners: ERROR: Script execution failed (use -d to debug)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.37 seconds
Nmap scan report for 10.0.2.4:
Starting Nmap 7.80 ( https://nmap.org ) at 2019-12-15 07:07 UTC
Nmap scan report for 10.0.2.4
Host is up (1.0s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
Starting Nmap 7.80 ( https://nmap.org ) at 2019-12-15 07:07 UTC
Nmap scan report for 10.0.2.15
Host is up (0.0000050s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
|_ 100000 3,4 111/udp6 rpcbind
|_vulners: ERROR: Script execution failed (use -d to debug)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.37 seconds
Nmap scan report for 10.0.2.4:
Starting Nmap 7.80 ( https://nmap.org ) at 2019-12-15 07:07 UTC
Nmap scan report for 10.0.2.4
Host is up (1.0s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
MAC Address: 52:54:00:12:35:04 (QEMU virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.41 seconds
Risk mitigation plan:
The vulnerability is one of the weak most point of a network which could be
exploited by a security related threat. The risks are the impacts and potential consequences of
the vulnerabilities that are unidentified. For mitigating the risks the keys actions that needs to
be taken are as follows:
Understanding the common attacks:
The attacks that come on the network are having varieties. Most of the times the
hacker are unknown to the persons who they are trying to attack. By knowing various
methods that are used for compromising the networks and computers will give the best
prospective for proceeding.
Use of Nmap:
The use of Nmap is depending on the machine that is targeted as there is so much
difference between normal scanning and advance scanning. Some of the advanced techniques
are needed to be used for bypassing the firewall and preventive software or instruction
detection for getting the actual result.
Inventory of the vulnerabilities:
By establishing an entire list of the potential vulnerabilities as well as by taking
special care for the identification of the unknown things that can be harmful for the network.
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
MAC Address: 52:54:00:12:35:04 (QEMU virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.41 seconds
Risk mitigation plan:
The vulnerability is one of the weak most point of a network which could be
exploited by a security related threat. The risks are the impacts and potential consequences of
the vulnerabilities that are unidentified. For mitigating the risks the keys actions that needs to
be taken are as follows:
Understanding the common attacks:
The attacks that come on the network are having varieties. Most of the times the
hacker are unknown to the persons who they are trying to attack. By knowing various
methods that are used for compromising the networks and computers will give the best
prospective for proceeding.
Use of Nmap:
The use of Nmap is depending on the machine that is targeted as there is so much
difference between normal scanning and advance scanning. Some of the advanced techniques
are needed to be used for bypassing the firewall and preventive software or instruction
detection for getting the actual result.
Inventory of the vulnerabilities:
By establishing an entire list of the potential vulnerabilities as well as by taking
special care for the identification of the unknown things that can be harmful for the network.

8CYBER SECURITY
Assessing the risks:
The different type vulnerabilities that are existed on the network can represent
potential costs, money, time as well as assets. The risk assessment is basically a combination
of both of the qualifying and quantifying of the threats and tasks. Each of the libraries will be
needed to determine the own tolerance of it for the risks by depending on the situation. Some
of the examples are given below:
By having the information about patron data that are needed to be compromised are
not acceptable for any of the libraries. The networks would be designed by the owner
self as well as the securities should be implemented for minimizing the risks.
A library always shares the internet connection between the staff networks and public
networks. Increasing the speed of the present network and purchase of a network
monitoring equipment that is complex will be beneficial.
Analysis of the scenario:
The Carpathian corporation needs to increase their network security for that they need
a new firewall. If they want to continue with the own setup of them then they have to face
network vulnerabilities. The staffs need to look at the network vulnerabilities that are existed
on their own network. For mitigating risk a bran =d new firewall setting needs to be created.
Firewall setup:
A firewall basically the combination of rules. Whenever a data packet moves out or
into of the network space that is protected, the contents (such as protocols, target, and origin)
of it are needed to be tested against the rules of the firewall for getting the result of how the
firewall is working.
Installing firewall in kali Linux:
Assessing the risks:
The different type vulnerabilities that are existed on the network can represent
potential costs, money, time as well as assets. The risk assessment is basically a combination
of both of the qualifying and quantifying of the threats and tasks. Each of the libraries will be
needed to determine the own tolerance of it for the risks by depending on the situation. Some
of the examples are given below:
By having the information about patron data that are needed to be compromised are
not acceptable for any of the libraries. The networks would be designed by the owner
self as well as the securities should be implemented for minimizing the risks.
A library always shares the internet connection between the staff networks and public
networks. Increasing the speed of the present network and purchase of a network
monitoring equipment that is complex will be beneficial.
Analysis of the scenario:
The Carpathian corporation needs to increase their network security for that they need
a new firewall. If they want to continue with the own setup of them then they have to face
network vulnerabilities. The staffs need to look at the network vulnerabilities that are existed
on their own network. For mitigating risk a bran =d new firewall setting needs to be created.
Firewall setup:
A firewall basically the combination of rules. Whenever a data packet moves out or
into of the network space that is protected, the contents (such as protocols, target, and origin)
of it are needed to be tested against the rules of the firewall for getting the result of how the
firewall is working.
Installing firewall in kali Linux:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
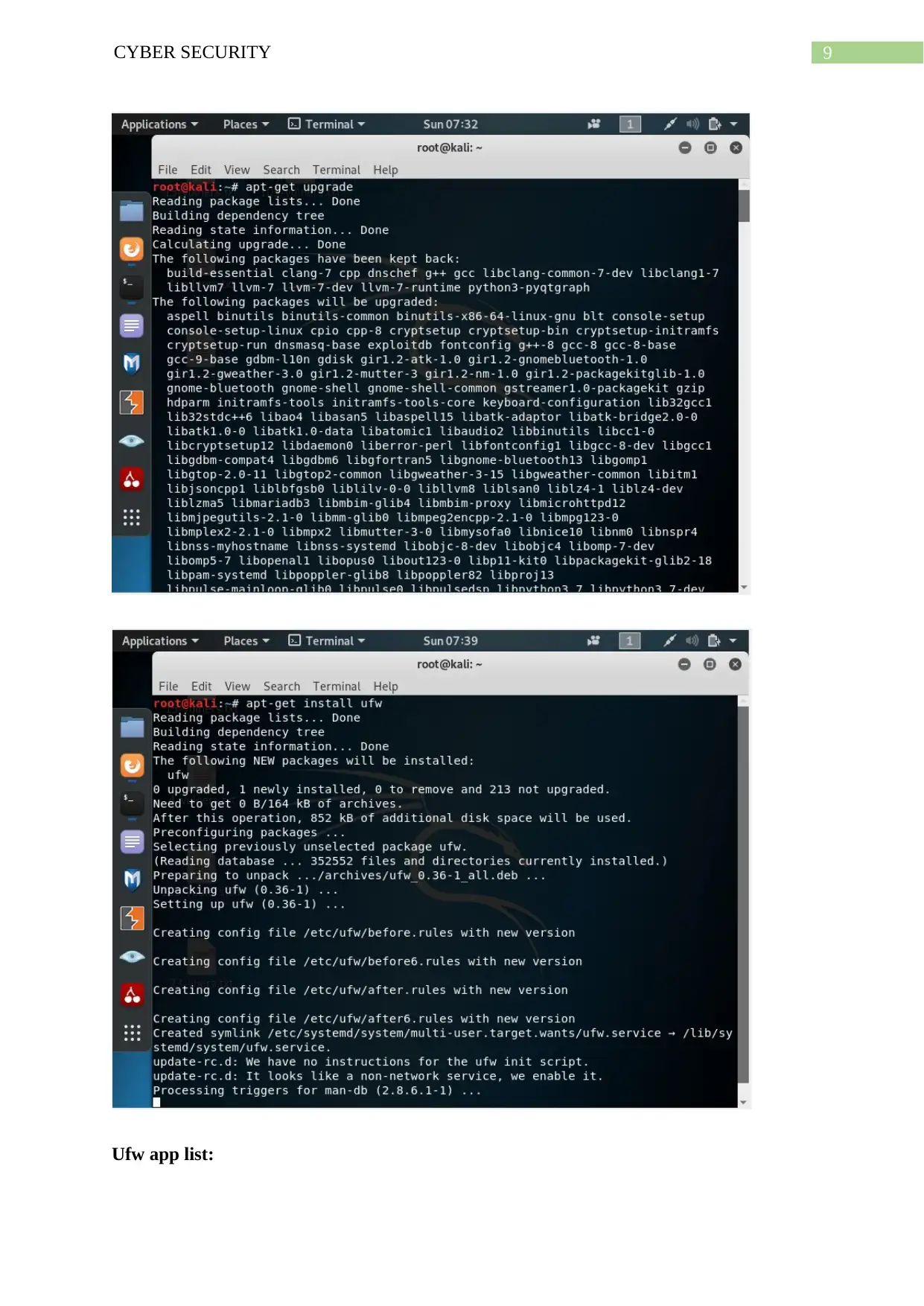
9CYBER SECURITY
Ufw app list:
Ufw app list:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10CYBER SECURITY
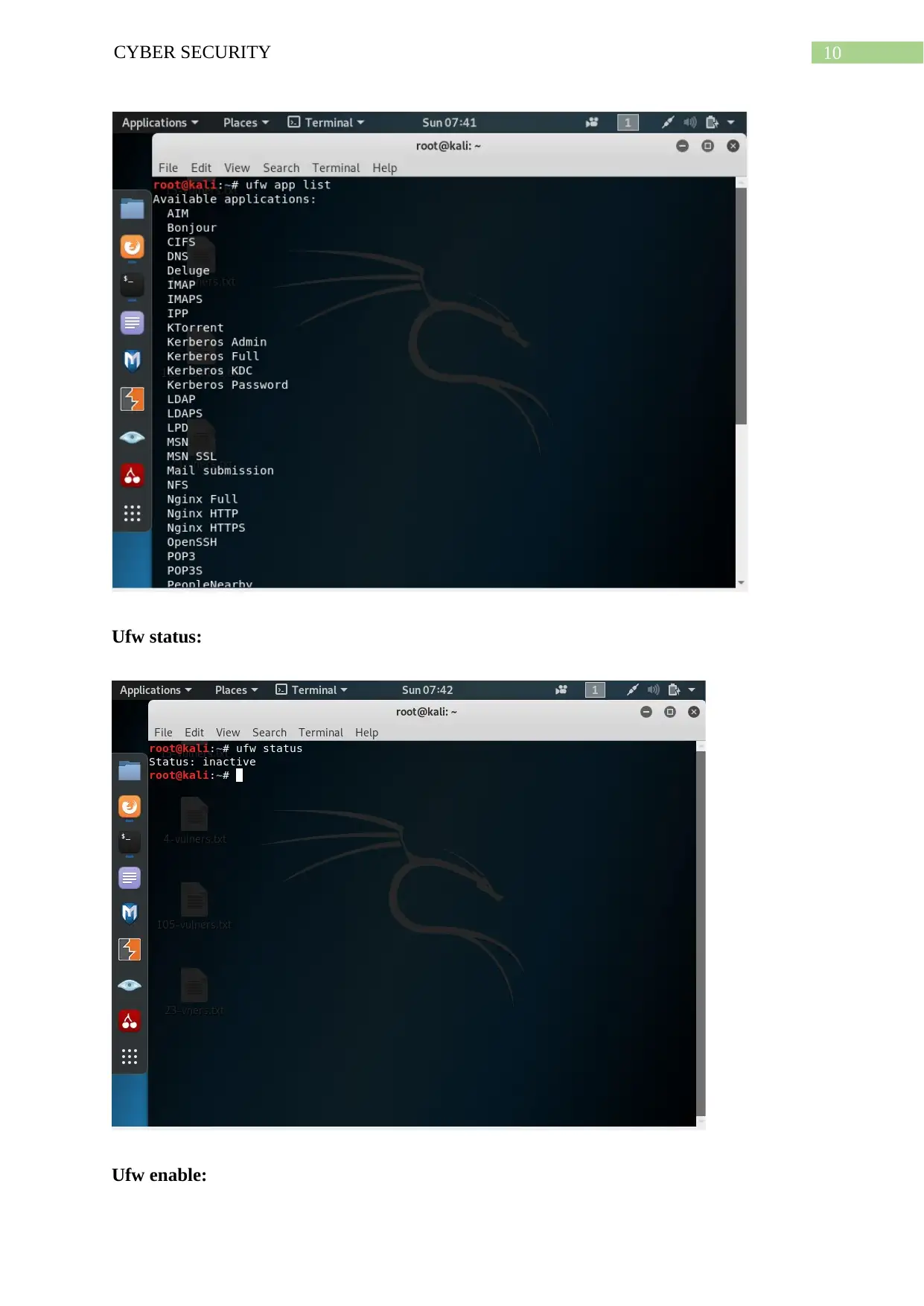
Ufw status:
Ufw enable:
Ufw status:
Ufw enable:
11CYBER SECURITY
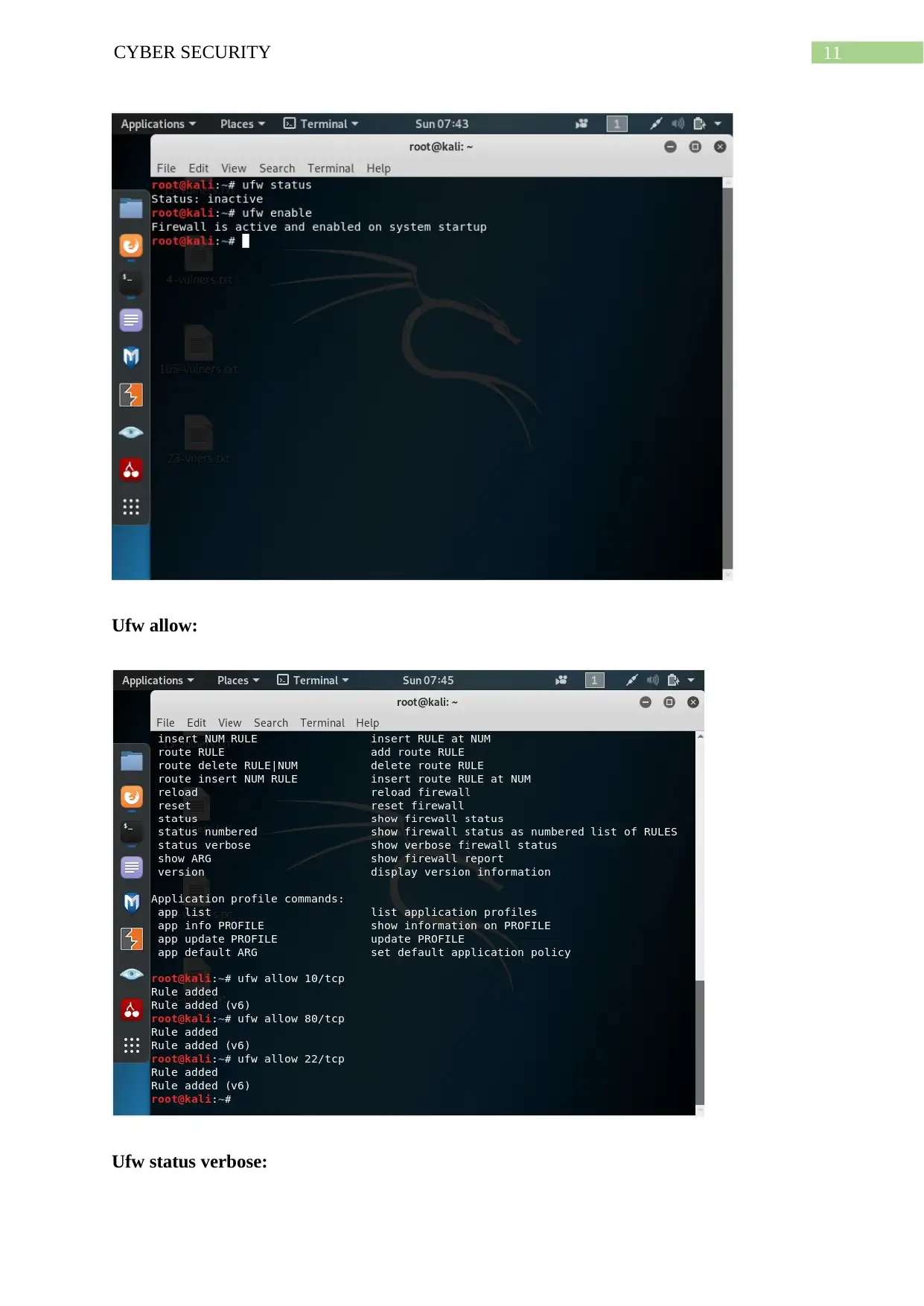
Ufw allow:
Ufw status verbose:
Ufw allow:
Ufw status verbose:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




