COCS71152 - Practical Guide to Securing Kali Linux with IPtables
VerifiedAdded on 2023/06/13
|17
|2477
|200
Practical Assignment
AI Summary
This assignment provides a detailed methodology for securing Kali Linux operating systems using IPtables. It begins by outlining a five-step process for identifying attack types, setting up rules for data packets, validating packet content, defining action policies, and updating IPtables with appropriate rules. The report then demonstrates the practical application of IPtables, including blocking specific websites and implementing rules to prevent XMAS tree attacks, SYN-FLOOD attacks, null packet attacks, and force fragment attacks. Commands and screenshots are provided to illustrate the configuration of IPtables rules and policies, offering a comprehensive guide to enhancing operating system security. The document is available on Desklib, a platform offering a variety of study resources, including past papers and solved assignments, to support students' academic needs.

Running head: OPERATING SYSTEM SECURITY
Operating system security
Name of the Student
Name of the University
Authors note
Operating system security
Name of the Student
Name of the University
Authors note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1OPERATING SYSTEM SECURITY
Executive Summary
With the increasing number of data as well as security breaches it becomes important to
secure the operating systems. For this one of the most common tools are used IPtables. The
following table contributes to the discussion on the Use of IP tables to secure the Kali Linux
systems.
Executive Summary
With the increasing number of data as well as security breaches it becomes important to
secure the operating systems. For this one of the most common tools are used IPtables. The
following table contributes to the discussion on the Use of IP tables to secure the Kali Linux
systems.

2OPERATING SYSTEM SECURITY
Table of Contents
Introduction................................................................................................................................3
Part 1: Methodology for Securing the Kali Linux.....................................................................3
Methodology for Securing the Kali Linux OS...........................................................3
Part 2: Demonstration of the Methodology................................................................................4
IPtable........................................................................................................................4
Use of IPtables to block filter and drop the incoming data packets...........................................6
Conclusion................................................................................................................................15
References................................................................................................................................16
Table of Contents
Introduction................................................................................................................................3
Part 1: Methodology for Securing the Kali Linux.....................................................................3
Methodology for Securing the Kali Linux OS...........................................................3
Part 2: Demonstration of the Methodology................................................................................4
IPtable........................................................................................................................4
Use of IPtables to block filter and drop the incoming data packets...........................................6
Conclusion................................................................................................................................15
References................................................................................................................................16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3OPERATING SYSTEM SECURITY
Introduction
In today’s vulnerable computing environment data packets that are flowing inside
and outside a specific network can be are intercepted using different tools and techniques,
analysed and manipulated to bring down that network. For this specific paper, we are
analysing the use of adding entry to the IPtables and firewall rules to restrict the unwanted
data traffic coming or going outside the system (Jung and Sung 2015). We are using Kali
Linux OS in order to implement this security mechanism.
Following report contributes to the discussion of the utilization of IPtables and
firewall rules to secure an operating system. In addition to that, firewall rules that are
implemented and effectiveness are also provided in different sections of this report.
Part 1: Methodology for Securing the Kali Linux
Methodology for Securing the Kali Linux OS
For Linux operating systems the IPtables is one of the best command-line tools that
can be used firewall utility for this operating system. The IPtables uses policy chains in order
to block or allow traffic to the system (Tekeoglu and Tosun 2016). Every time a network
based connection attempts to set up a connection to the system, IPtables checks for a rule in
its created list to match and try to follow the policies.
For this project we created the following methodology to secure the Linux based
systems so that, the servers using the operating system can check analyse and take action
accordingly for any kind of network based attack to the system. Following are the stages in
this methodology,
Determining the type of the attack
Introduction
In today’s vulnerable computing environment data packets that are flowing inside
and outside a specific network can be are intercepted using different tools and techniques,
analysed and manipulated to bring down that network. For this specific paper, we are
analysing the use of adding entry to the IPtables and firewall rules to restrict the unwanted
data traffic coming or going outside the system (Jung and Sung 2015). We are using Kali
Linux OS in order to implement this security mechanism.
Following report contributes to the discussion of the utilization of IPtables and
firewall rules to secure an operating system. In addition to that, firewall rules that are
implemented and effectiveness are also provided in different sections of this report.
Part 1: Methodology for Securing the Kali Linux
Methodology for Securing the Kali Linux OS
For Linux operating systems the IPtables is one of the best command-line tools that
can be used firewall utility for this operating system. The IPtables uses policy chains in order
to block or allow traffic to the system (Tekeoglu and Tosun 2016). Every time a network
based connection attempts to set up a connection to the system, IPtables checks for a rule in
its created list to match and try to follow the policies.
For this project we created the following methodology to secure the Linux based
systems so that, the servers using the operating system can check analyse and take action
accordingly for any kind of network based attack to the system. Following are the stages in
this methodology,
Determining the type of the attack
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4OPERATING SYSTEM SECURITY
Setting up the rules for data packets
Checking the data packets and its content to check validity.
Defining the action policy if any rule matches for the incoming request data
packets.
Updating IPtables with rules and policies for different types of attacks and its
nature of the attack.
In the following section we have created the rules and policies to prevent the attacks like
XMAS tree attack, SYN-FLOOD attack, null packet attacks and at last force fragment
attacks.
Part 2: Demonstration of the Methodology
IPtable
In case of Linux operating system the server administrator can use IPtable to
populate with chains of security rules. This rules are helpful in the manipulation of the data
packets at several stages of data packet processing lifecycle by the kernel of the system
(Tekeoglu and Tosun 2016). For an ideal scenario to secure a server, it is suggested to
populate rules that will DENY all the incoming data traffic inside a network. After doing this,
explicit rules that acts as exceptions for the IPtables such as for port 80 requests data traffic
can be added to the table (Jung and Sung 2015).
For the IPtable following are the available options to secure the system,
Screenshot 1: man IPtable result.
Setting up the rules for data packets
Checking the data packets and its content to check validity.
Defining the action policy if any rule matches for the incoming request data
packets.
Updating IPtables with rules and policies for different types of attacks and its
nature of the attack.
In the following section we have created the rules and policies to prevent the attacks like
XMAS tree attack, SYN-FLOOD attack, null packet attacks and at last force fragment
attacks.
Part 2: Demonstration of the Methodology
IPtable
In case of Linux operating system the server administrator can use IPtable to
populate with chains of security rules. This rules are helpful in the manipulation of the data
packets at several stages of data packet processing lifecycle by the kernel of the system
(Tekeoglu and Tosun 2016). For an ideal scenario to secure a server, it is suggested to
populate rules that will DENY all the incoming data traffic inside a network. After doing this,
explicit rules that acts as exceptions for the IPtables such as for port 80 requests data traffic
can be added to the table (Jung and Sung 2015).
For the IPtable following are the available options to secure the system,
Screenshot 1: man IPtable result.
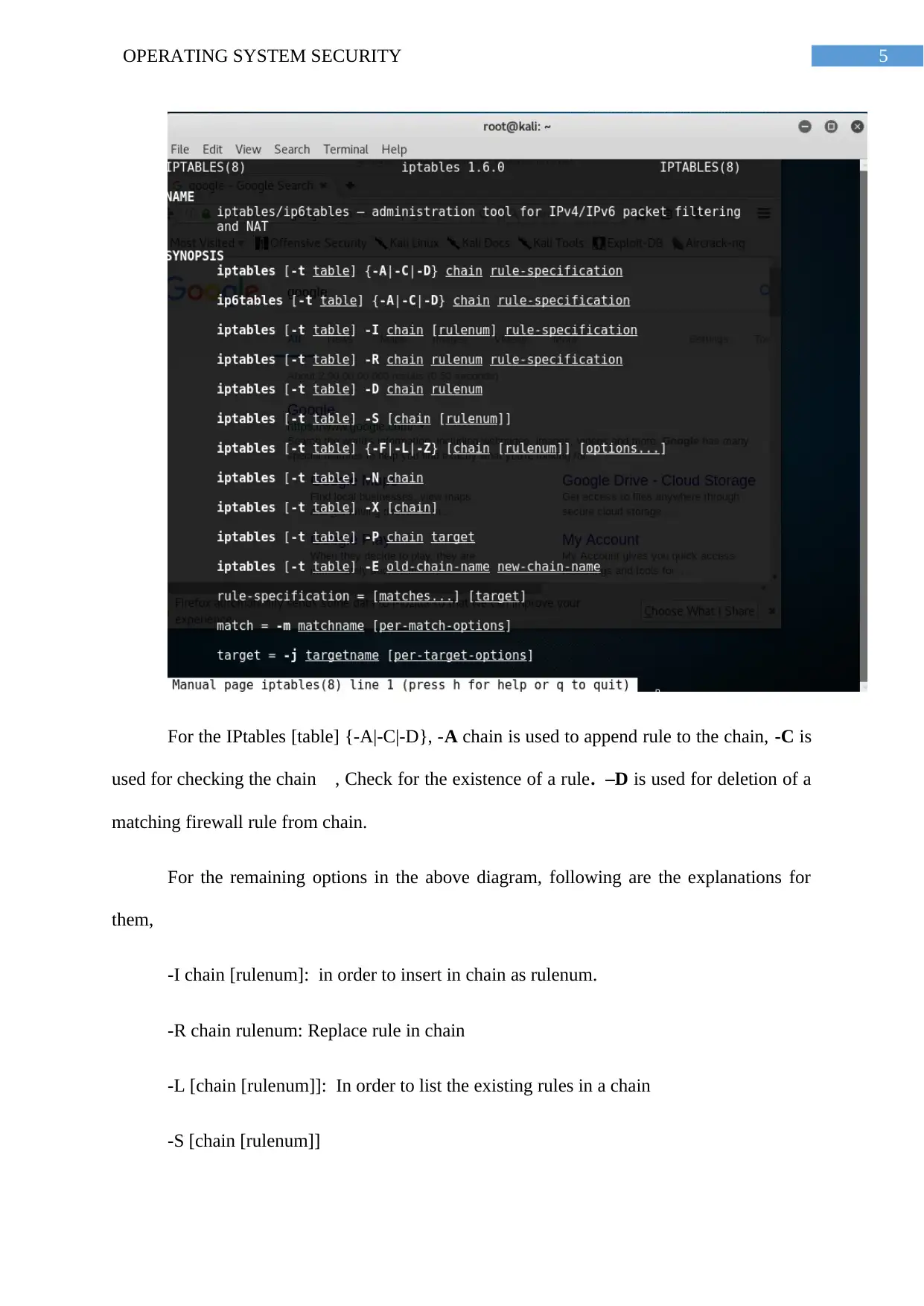
5OPERATING SYSTEM SECURITY
For the IPtables [table] {-A|-C|-D}, -A chain is used to append rule to the chain, -C is
used for checking the chain , Check for the existence of a rule. –D is used for deletion of a
matching firewall rule from chain.
For the remaining options in the above diagram, following are the explanations for
them,
-I chain [rulenum]: in order to insert in chain as rulenum.
-R chain rulenum: Replace rule in chain
-L [chain [rulenum]]: In order to list the existing rules in a chain
-S [chain [rulenum]]
For the IPtables [table] {-A|-C|-D}, -A chain is used to append rule to the chain, -C is
used for checking the chain , Check for the existence of a rule. –D is used for deletion of a
matching firewall rule from chain.
For the remaining options in the above diagram, following are the explanations for
them,
-I chain [rulenum]: in order to insert in chain as rulenum.
-R chain rulenum: Replace rule in chain
-L [chain [rulenum]]: In order to list the existing rules in a chain
-S [chain [rulenum]]
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6OPERATING SYSTEM SECURITY
-L: In order to List all rules in the selected chain
-F: In order to flush the rules in selected chain
-Z: This option is used to Zero the packet and byte counters in all chains.
-N: Useful for creating a new user-defined chain.
-X: useful for deleting an optional user-defined chain.
-P: mainly used for setting the policy for the chain for a given target.
-E, In order to rename an old-chain to a new-chain.
For this specific project, we are using the IPtables to block the websites Facebook and
Twitter. In case real world scenario, this technique can be used for any suspicious website or
IP which may try to get access to the critical data stored on the system.
Use of IPtables to block filter and drop the incoming data packets
Following are the steps that are used for securing the system,
Step 1: If the IPtable tool is not available for Linux system then at first, it can be
retrieved using the following command “sudo apt-get install iptables”
-L: In order to List all rules in the selected chain
-F: In order to flush the rules in selected chain
-Z: This option is used to Zero the packet and byte counters in all chains.
-N: Useful for creating a new user-defined chain.
-X: useful for deleting an optional user-defined chain.
-P: mainly used for setting the policy for the chain for a given target.
-E, In order to rename an old-chain to a new-chain.
For this specific project, we are using the IPtables to block the websites Facebook and
Twitter. In case real world scenario, this technique can be used for any suspicious website or
IP which may try to get access to the critical data stored on the system.
Use of IPtables to block filter and drop the incoming data packets
Following are the steps that are used for securing the system,
Step 1: If the IPtable tool is not available for Linux system then at first, it can be
retrieved using the following command “sudo apt-get install iptables”
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
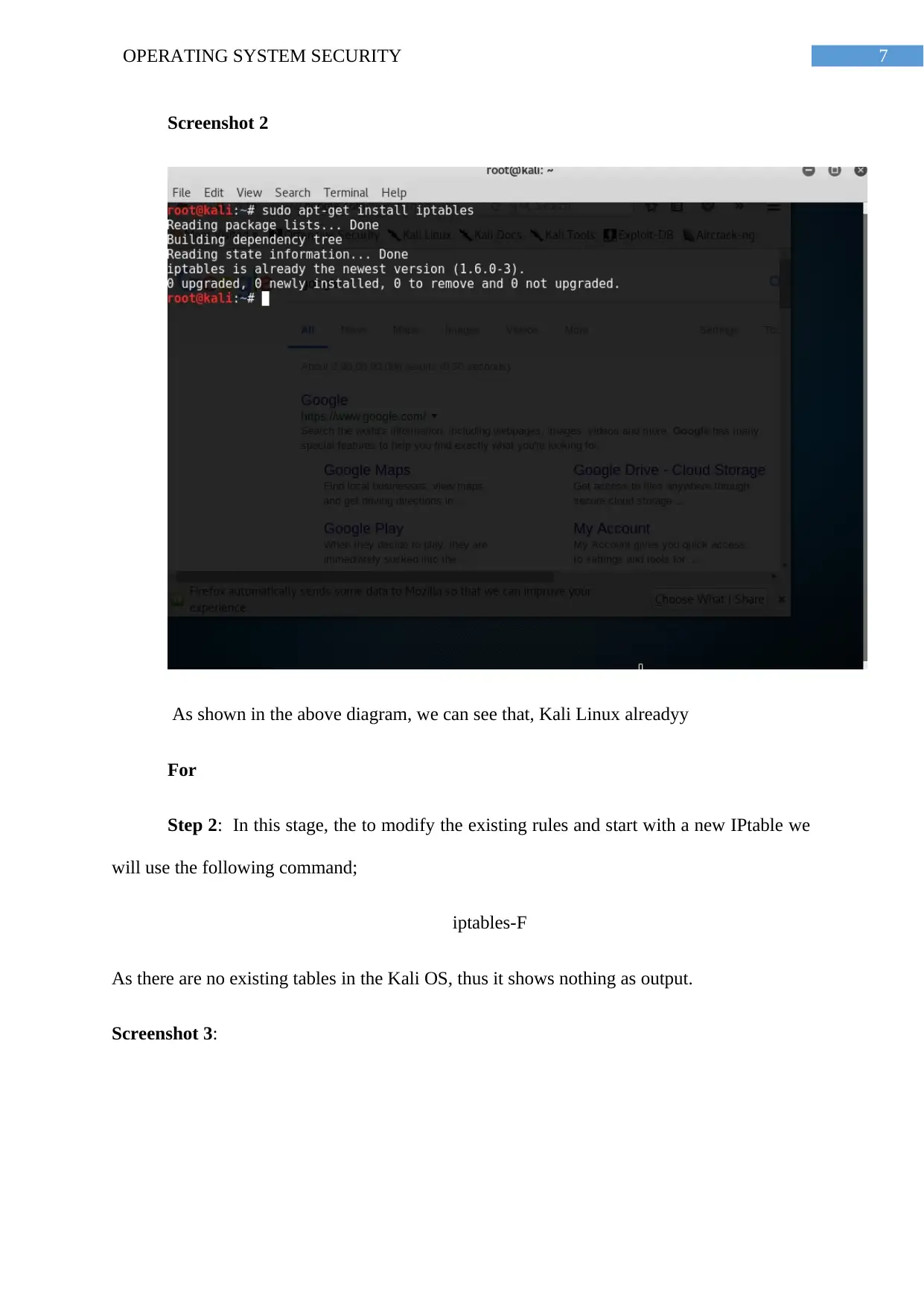
7OPERATING SYSTEM SECURITY
Screenshot 2
As shown in the above diagram, we can see that, Kali Linux alreadyy
For
Step 2: In this stage, the to modify the existing rules and start with a new IPtable we
will use the following command;
iptables-F
As there are no existing tables in the Kali OS, thus it shows nothing as output.
Screenshot 3:
Screenshot 2
As shown in the above diagram, we can see that, Kali Linux alreadyy
For
Step 2: In this stage, the to modify the existing rules and start with a new IPtable we
will use the following command;
iptables-F
As there are no existing tables in the Kali OS, thus it shows nothing as output.
Screenshot 3:
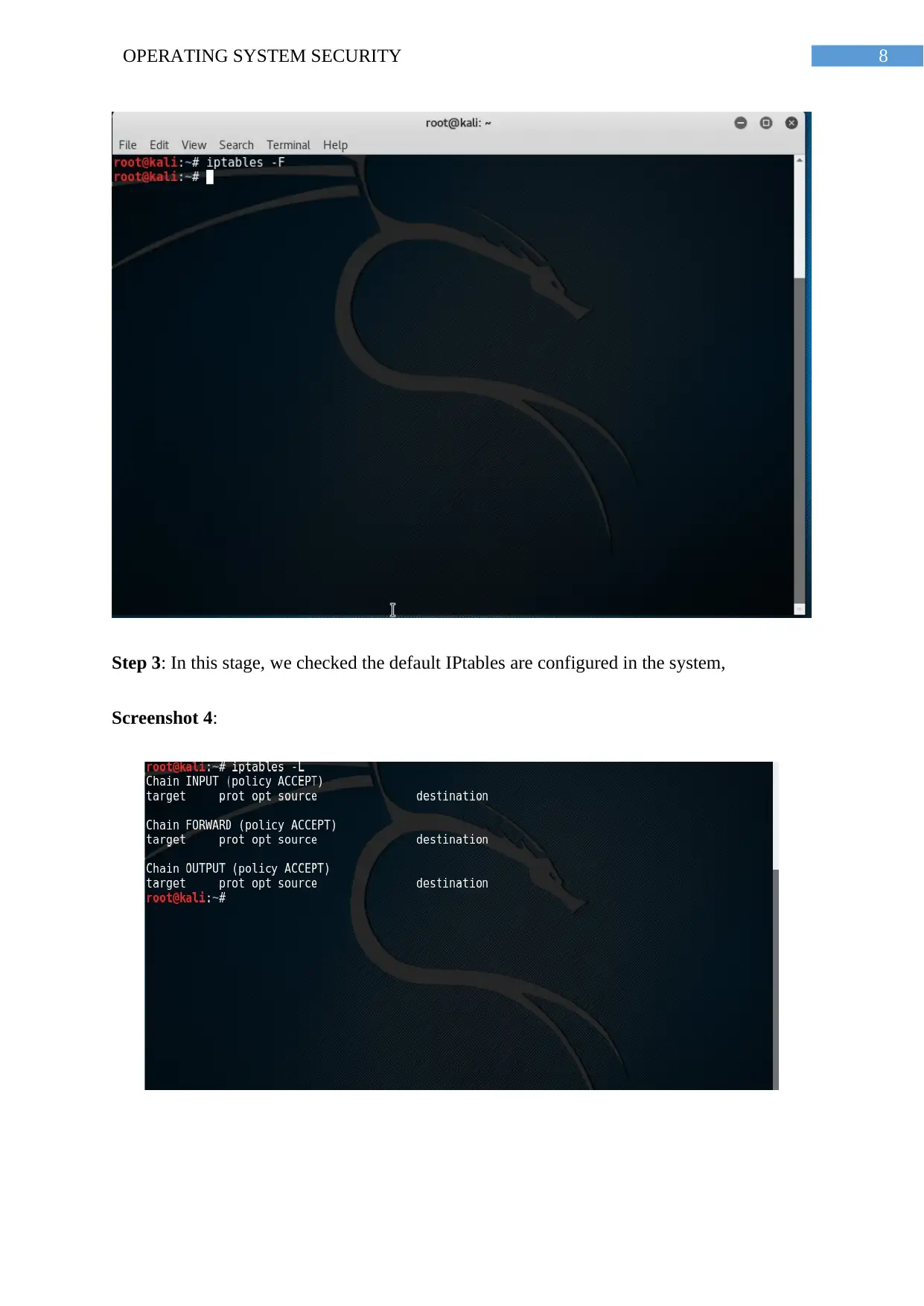
8OPERATING SYSTEM SECURITY
Step 3: In this stage, we checked the default IPtables are configured in the system,
Screenshot 4:
Step 3: In this stage, we checked the default IPtables are configured in the system,
Screenshot 4:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
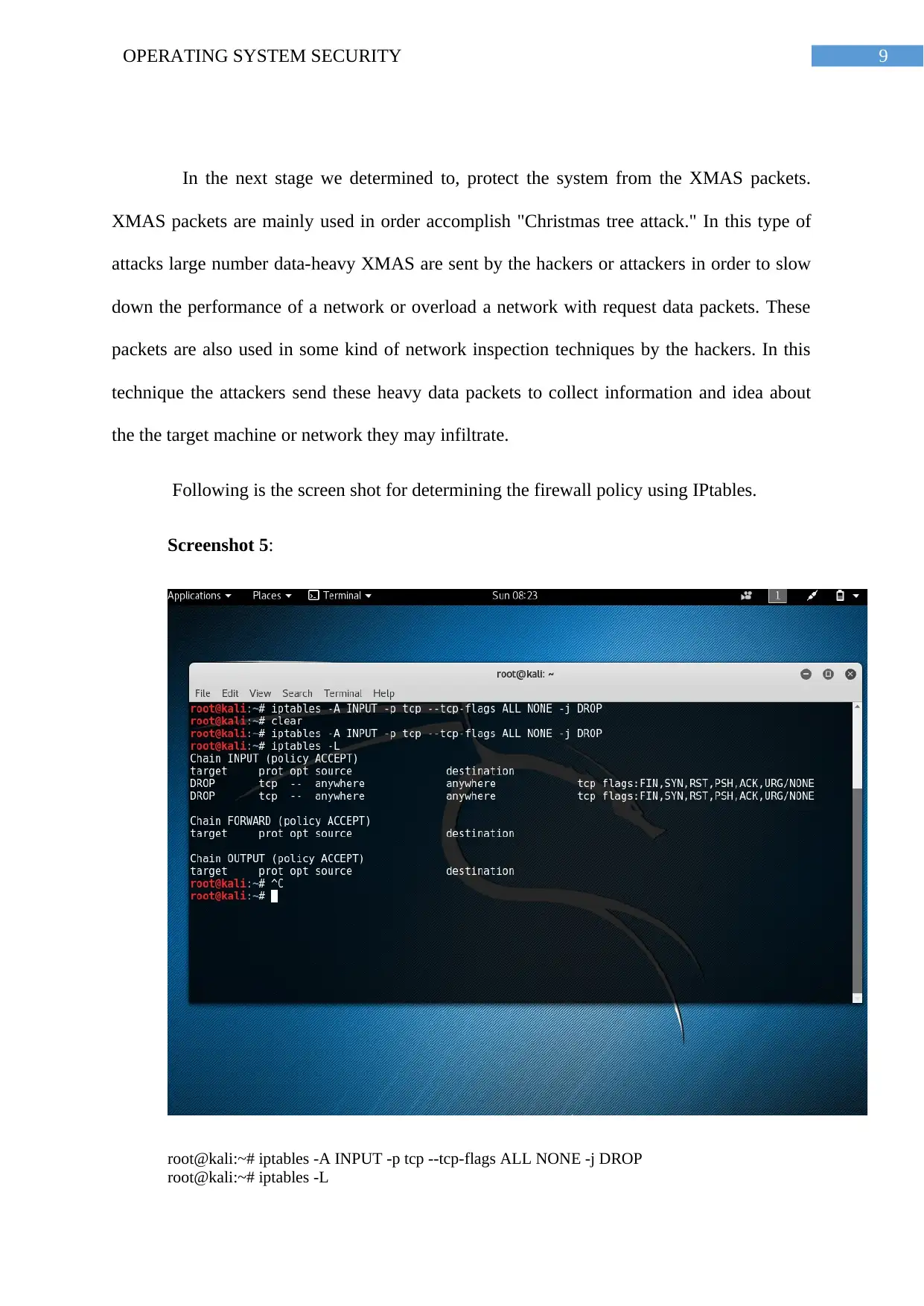
9OPERATING SYSTEM SECURITY
In the next stage we determined to, protect the system from the XMAS packets.
XMAS packets are mainly used in order accomplish "Christmas tree attack." In this type of
attacks large number data-heavy XMAS are sent by the hackers or attackers in order to slow
down the performance of a network or overload a network with request data packets. These
packets are also used in some kind of network inspection techniques by the hackers. In this
technique the attackers send these heavy data packets to collect information and idea about
the the target machine or network they may infiltrate.
Following is the screen shot for determining the firewall policy using IPtables.
Screenshot 5:
root@kali:~# iptables -A INPUT -p tcp --tcp-flags ALL NONE -j DROP
root@kali:~# iptables -L
In the next stage we determined to, protect the system from the XMAS packets.
XMAS packets are mainly used in order accomplish "Christmas tree attack." In this type of
attacks large number data-heavy XMAS are sent by the hackers or attackers in order to slow
down the performance of a network or overload a network with request data packets. These
packets are also used in some kind of network inspection techniques by the hackers. In this
technique the attackers send these heavy data packets to collect information and idea about
the the target machine or network they may infiltrate.
Following is the screen shot for determining the firewall policy using IPtables.
Screenshot 5:
root@kali:~# iptables -A INPUT -p tcp --tcp-flags ALL NONE -j DROP
root@kali:~# iptables -L
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10OPERATING SYSTEM SECURITY
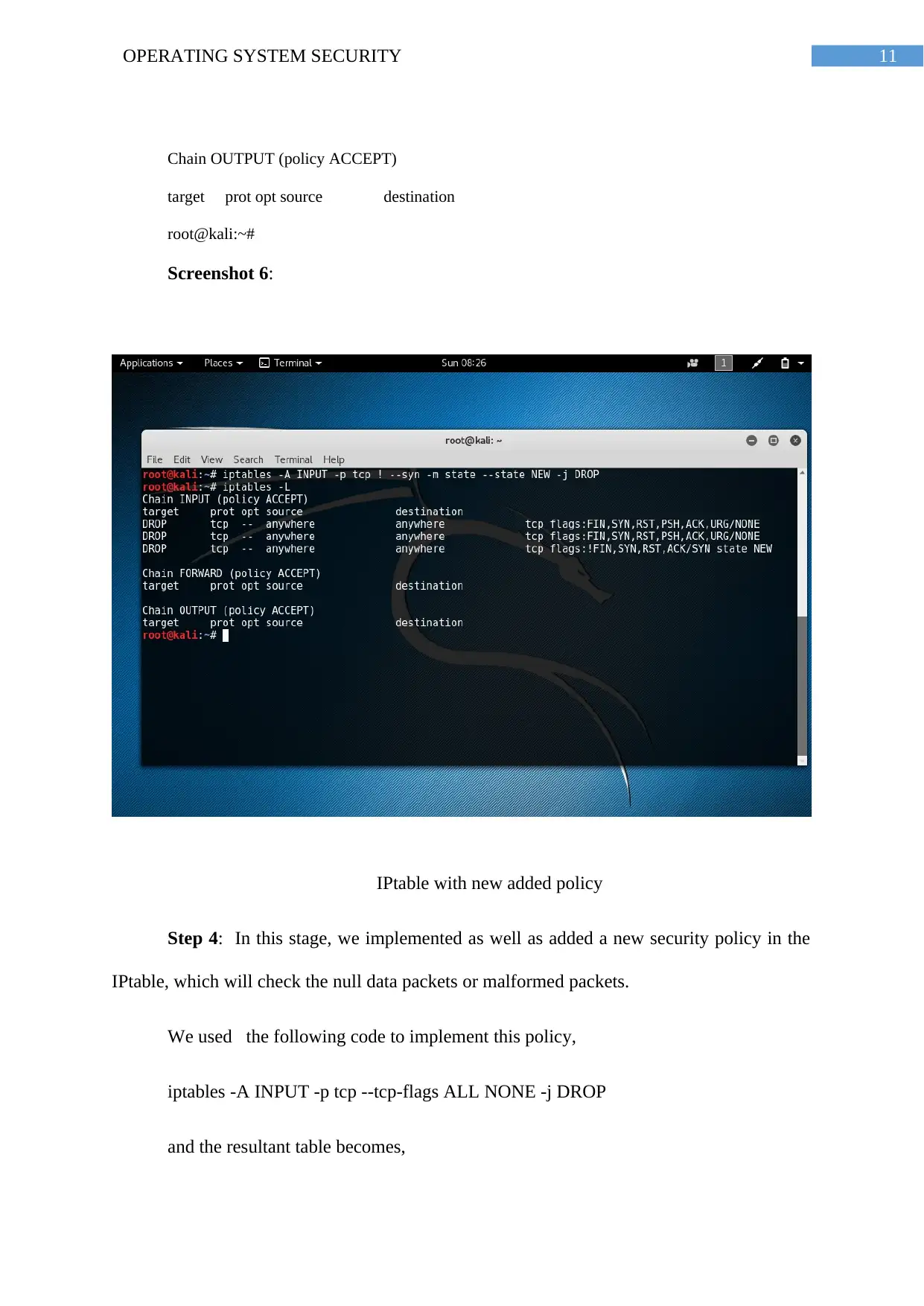
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- anywhere anywhere tcp
flags:FIN,SYN,RST,PSH,ACK,URG/NONE
DROP tcp -- anywhere anywhere tcp
flags:FIN,SYN,RST,PSH,ACK,URG/NONE
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Step 4: In this stage, the code is executed to protect the server or the system from
the SYN-FLOOD attack. After adding this policy following screen is presented using the
IPtables –L. The policy checks the SYN packets.
Following code is used for the adding to check the data packets,
iptables -A INPUT -p tcp ! --syn -m state --state NEW -j DROP
following is the newly added policy in the IPtable
root@kali:~# iptables -A INPUT -p tcp ! --syn -m state --state NEW -j DROP
root@kali:~# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- anywhere anywhere tcp
flags:FIN,SYN,RST,PSH,ACK,URG/NONE
DROP tcp -- anywhere anywhere tcp
flags:FIN,SYN,RST,PSH,ACK,URG/NONE
DROP tcp -- anywhere anywhere tcp flags:!FIN,SYN,RST,ACK/SYN state
NEW
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- anywhere anywhere tcp
flags:FIN,SYN,RST,PSH,ACK,URG/NONE
DROP tcp -- anywhere anywhere tcp
flags:FIN,SYN,RST,PSH,ACK,URG/NONE
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Step 4: In this stage, the code is executed to protect the server or the system from
the SYN-FLOOD attack. After adding this policy following screen is presented using the
IPtables –L. The policy checks the SYN packets.
Following code is used for the adding to check the data packets,
iptables -A INPUT -p tcp ! --syn -m state --state NEW -j DROP
following is the newly added policy in the IPtable
root@kali:~# iptables -A INPUT -p tcp ! --syn -m state --state NEW -j DROP
root@kali:~# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- anywhere anywhere tcp
flags:FIN,SYN,RST,PSH,ACK,URG/NONE
DROP tcp -- anywhere anywhere tcp
flags:FIN,SYN,RST,PSH,ACK,URG/NONE
DROP tcp -- anywhere anywhere tcp flags:!FIN,SYN,RST,ACK/SYN state
NEW
Chain FORWARD (policy ACCEPT)
target prot opt source destination
11OPERATING SYSTEM SECURITY
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
root@kali:~#
Screenshot 6:
IPtable with new added policy
Step 4: In this stage, we implemented as well as added a new security policy in the
IPtable, which will check the null data packets or malformed packets.
We used the following code to implement this policy,
iptables -A INPUT -p tcp --tcp-flags ALL NONE -j DROP
and the resultant table becomes,
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
root@kali:~#
Screenshot 6:
IPtable with new added policy
Step 4: In this stage, we implemented as well as added a new security policy in the
IPtable, which will check the null data packets or malformed packets.
We used the following code to implement this policy,
iptables -A INPUT -p tcp --tcp-flags ALL NONE -j DROP
and the resultant table becomes,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





