Wireless Network Security Analysis
VerifiedAdded on 2020/04/01
|6
|757
|115
AI Summary
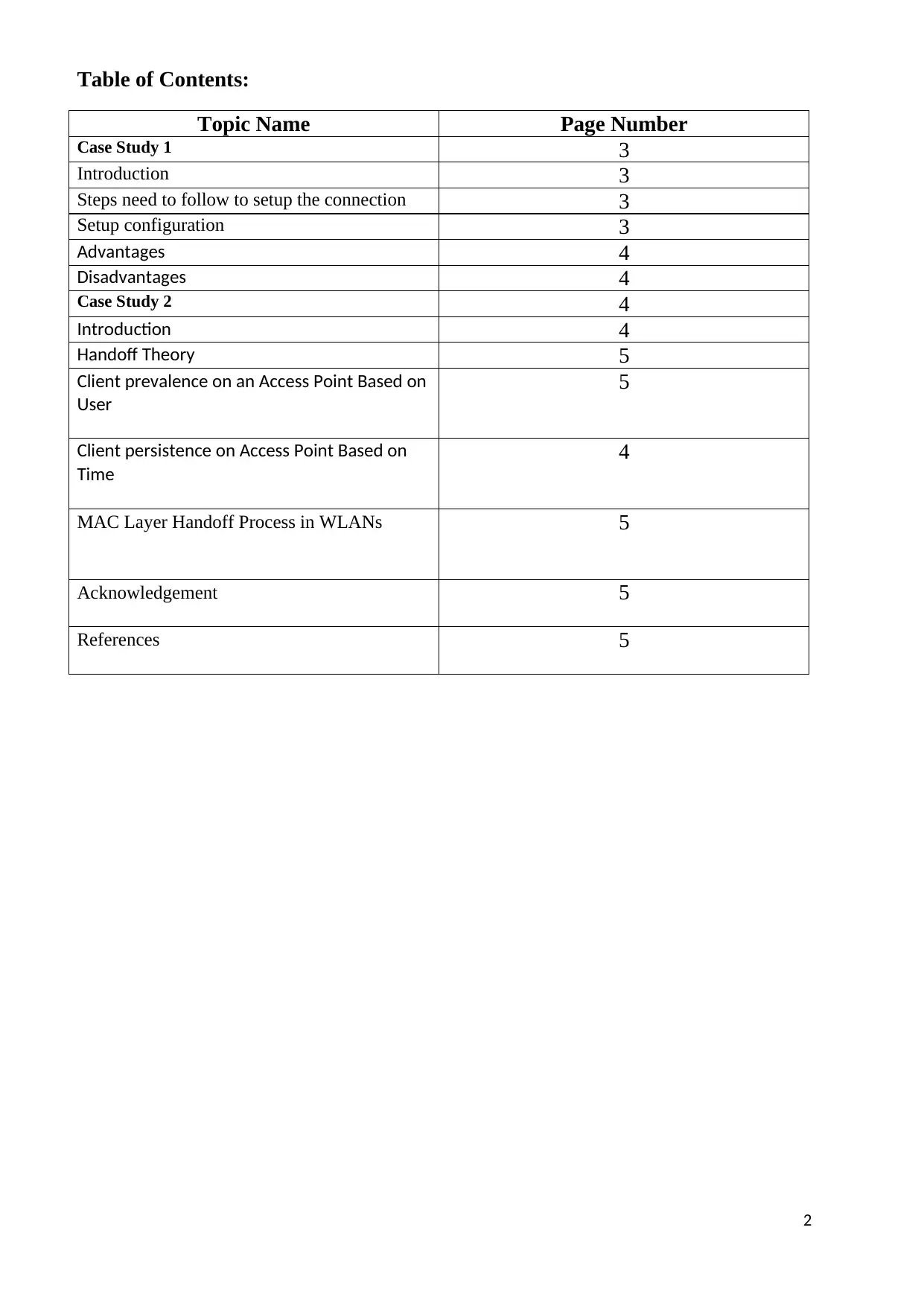
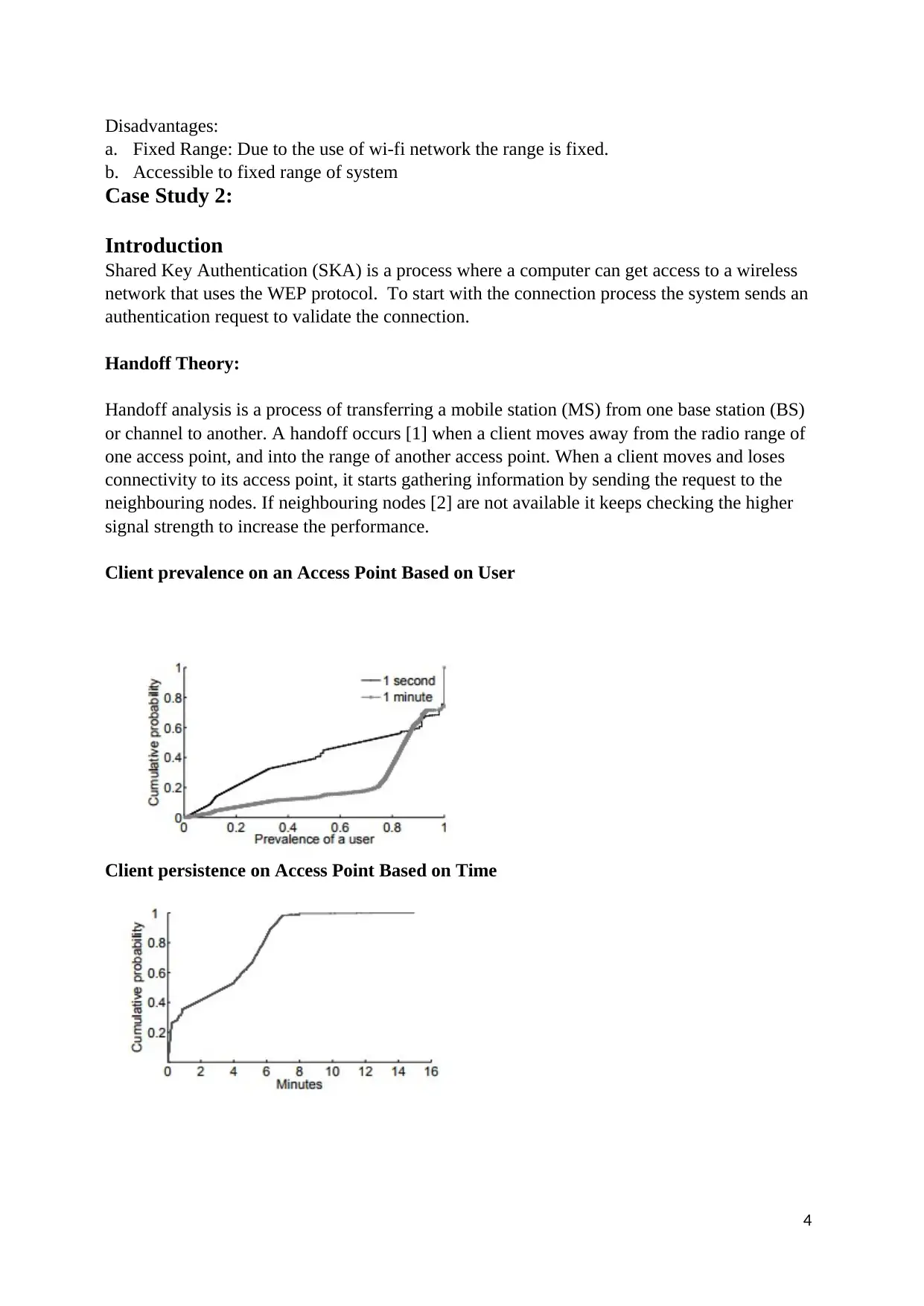
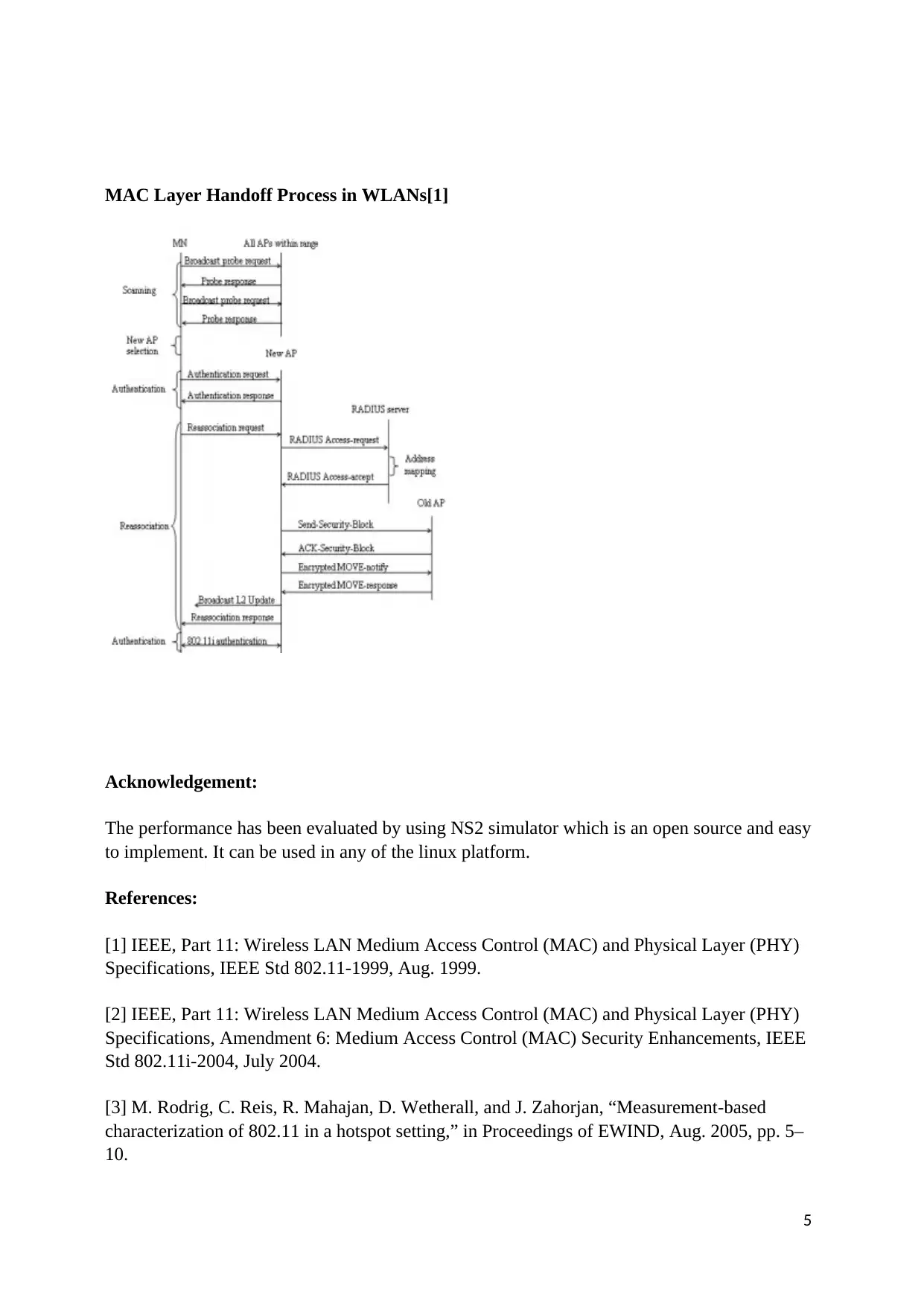
This assignment delves into the realm of wireless network security. It presents two case studies, one focusing on setting up a secure wireless camera system using WPA-2 encryption and static IP addresses, and another exploring the concept of handoff theory in WLANs. The second case study examines client prevalence based on user activity, client persistence over time, the MAC Layer Handoff process, and utilizes the NS2 simulator for performance evaluation.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
1 out of 6









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)