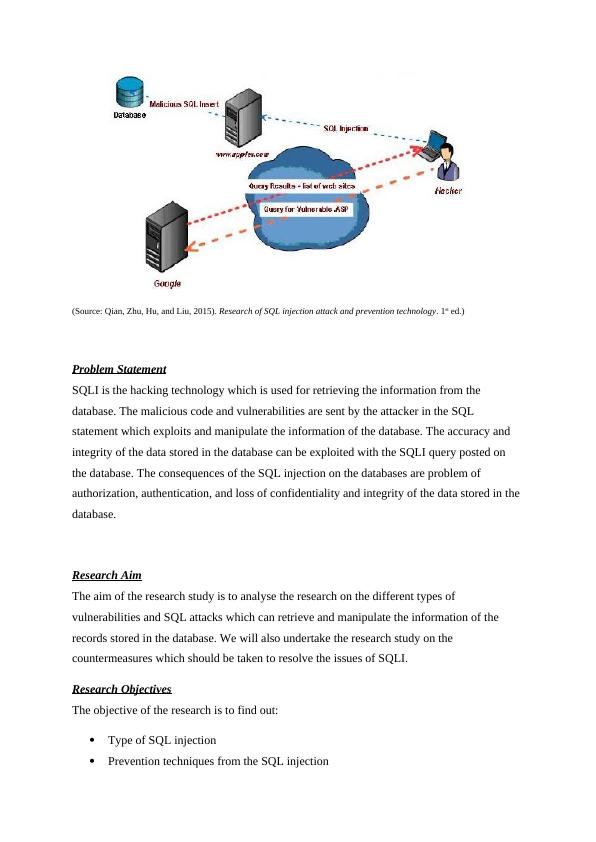
Different Techniques used to deploy SQLi attacks as a way of exploiting the database and the website vulnerabilities
18 Pages5031 Words291 Views
Added on 2023-06-12
About This Document
This research paper analyses the different types of vulnerabilities and SQL attacks which can retrieve and manipulate the information of the records stored in the database. It also covers the countermeasures which should be taken to resolve the issues of SQLI.
Different Techniques used to deploy SQLi attacks as a way of exploiting the database and the website vulnerabilities
Added on 2023-06-12
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Ways of Attacking a Web Application in PHP: SQL Injection, XSS, Session Hijacking, Directory Traversal, and Remote File Inclusion
|9
|1493
|176
Information Security Awareness Assignment PDF
|7
|1466
|95
COIT20262 - Advanced Network Security
|12
|1899
|262
Understanding SQL Injection, Insider Attacks, and Malware Threats for Enhanced Cybersecurity
|7
|2711
|157
Cyber Security: Vulnerabilities, Exploitation, and Security Controls
|10
|2384
|453
Ethical Hacking & Countermeasures Report 2022
|25
|3747
|46