Comprehensive Report: STP Limited IS Upgrade, Security, and Planning
VerifiedAdded on 2020/03/16
|10
|3005
|64
Report
AI Summary
This report, prepared for STP management, evaluates the upgrade of STP Limited's Information System (IS), focusing on ensuring compliance with regulations and maintaining data privacy and confidentiality across its Wollongong headquarters and new locations in Bathurst, Lithgow, and Sydney. The report addresses limitations, assumptions, and the project's scope, including the implementation of a distributed IS with control, client management, and accounting systems accessible via ADSL internet connectivity and WAP for BYOD. It analyzes strategic alignment through SWOT analysis, emphasizing network security considerations, data protection strategies involving people, products, policies, and procedures, and ISP security. Furthermore, the report outlines plans for hardware purchases, acquisition strategies, staff feedback integration, and asset register management, alongside business continuity and risk management plans. The report also covers security policies, training and awareness programs, and provides recommendations to enhance the upgraded IS's effectiveness and security posture.

[Document title]
[Document subtitle]Student Name
Student number | Date
[Document subtitle]Student Name
Student number | Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.............................................................................................................................. 1
Limitations.............................................................................................................................1
Scope of the Report...............................................................................................................1
Assumptions..........................................................................................................................1
Background............................................................................................................................... 1
Scope of the Project.............................................................................................................. 1
Goal of the project................................................................................................................ 1
Strategic Alignment of the Project........................................................................................2
Network Security...................................................................................................................... 2
Securing data.........................................................................................................................2
People, products, policies and procedures............................................................................3
ISP security and privacy considerations.................................................................................3
Other threats to data............................................................................................................ 3
Mobile device security.......................................................................................................... 3
Plan for Hardware Purchases....................................................................................................3
Hardware Acquisition............................................................................................................4
Staff feedback and reviews....................................................................................................4
Strategies of Hardware Purchase..........................................................................................4
Asset Register........................................................................................................................4
Business Continuity...................................................................................................................5
Risk Management..................................................................................................................... 6
Security policy....................................................................................................................... 6
Training and awareness.........................................................................................................7
Conclusion.................................................................................................................................7
Recommendations....................................................................................................................7
References................................................................................................................................ 8
Introduction.............................................................................................................................. 1
Limitations.............................................................................................................................1
Scope of the Report...............................................................................................................1
Assumptions..........................................................................................................................1
Background............................................................................................................................... 1
Scope of the Project.............................................................................................................. 1
Goal of the project................................................................................................................ 1
Strategic Alignment of the Project........................................................................................2
Network Security...................................................................................................................... 2
Securing data.........................................................................................................................2
People, products, policies and procedures............................................................................3
ISP security and privacy considerations.................................................................................3
Other threats to data............................................................................................................ 3
Mobile device security.......................................................................................................... 3
Plan for Hardware Purchases....................................................................................................3
Hardware Acquisition............................................................................................................4
Staff feedback and reviews....................................................................................................4
Strategies of Hardware Purchase..........................................................................................4
Asset Register........................................................................................................................4
Business Continuity...................................................................................................................5
Risk Management..................................................................................................................... 6
Security policy....................................................................................................................... 6
Training and awareness.........................................................................................................7
Conclusion.................................................................................................................................7
Recommendations....................................................................................................................7
References................................................................................................................................ 8

Introduction
As a new manager hired by STP management, the report below will consist of the evaluation
and analysing of the new and the STP IS which is update whose aim will ensure that
everything is complying with all rules and regulations set and the privacy and the
confidential of the information is observed at the STP.
Limitations
The provision of limited report in essence it is not detailed will be a disadvantage to the
staffs at STP as they have technical skills that is limited.
Scope of the Report
Scope of such a report will rotate and revolve around analysing the network of STP that is to
be upgraded serving as the head office at Wollongong, of recent STP purchased a premise at
Bathurst and Lithgow and also another one in Sydney where it did build a state of the art
computer with a manufacture facility.
Assumptions
Some of the assumptions made in the report is that there will be an ISP (Internet Service
Provider) that will supply STP company with ADSL which will be internet connectivity via the
modems and switches.
Background
The project background defines and identify the problems that STP limited company faces
during the process of ensuring the IS to be upgraded is complying with the rules and
regulations for privacy and confidentiality set by STP Limited. The content will consist of
evaluating the project, its scope, the goals of the project and how strategically the alignment
of STP company will look like.
Scope of the Project.
The main aim of the project is to facilitate a well Distributed IS that will have a system for
control, a client management system and a system for accounting. All the mentioned
systems will be accessed in all the locations mentioned as follows, Bathurst, Wollongong,
Lithgow and lastly Sydney. Of the mentioned location every location will have to own its
database that is distributed and each and very staff will have access to these systems
through the provided ADSL internet connectivity via use of modems and the switch of the
overall network which is located at every office in the specified locations. WAP will also be
implemented in the project to facilitate the connections of the staff, hence bringing in the
case of BYOB (Bring Your Own Device) means. The main idea in implementing this network is
to improve the scalable of the network in all the four locations as well as extending the staffs
operations in the current office and also in future.
Goal of the project
Major goals differ in different organizations depending on the main objectives to be
achieved by a certain company. In our case here STP limited company have a desire of
implementing an IS infrastructure whereby the management in managing the rapidly
growing of the organisation in terms of the customers served and the operations of the
business as well. The basic objective of STP is to have their own control system for stock that
As a new manager hired by STP management, the report below will consist of the evaluation
and analysing of the new and the STP IS which is update whose aim will ensure that
everything is complying with all rules and regulations set and the privacy and the
confidential of the information is observed at the STP.
Limitations
The provision of limited report in essence it is not detailed will be a disadvantage to the
staffs at STP as they have technical skills that is limited.
Scope of the Report
Scope of such a report will rotate and revolve around analysing the network of STP that is to
be upgraded serving as the head office at Wollongong, of recent STP purchased a premise at
Bathurst and Lithgow and also another one in Sydney where it did build a state of the art
computer with a manufacture facility.
Assumptions
Some of the assumptions made in the report is that there will be an ISP (Internet Service
Provider) that will supply STP company with ADSL which will be internet connectivity via the
modems and switches.
Background
The project background defines and identify the problems that STP limited company faces
during the process of ensuring the IS to be upgraded is complying with the rules and
regulations for privacy and confidentiality set by STP Limited. The content will consist of
evaluating the project, its scope, the goals of the project and how strategically the alignment
of STP company will look like.
Scope of the Project.
The main aim of the project is to facilitate a well Distributed IS that will have a system for
control, a client management system and a system for accounting. All the mentioned
systems will be accessed in all the locations mentioned as follows, Bathurst, Wollongong,
Lithgow and lastly Sydney. Of the mentioned location every location will have to own its
database that is distributed and each and very staff will have access to these systems
through the provided ADSL internet connectivity via use of modems and the switch of the
overall network which is located at every office in the specified locations. WAP will also be
implemented in the project to facilitate the connections of the staff, hence bringing in the
case of BYOB (Bring Your Own Device) means. The main idea in implementing this network is
to improve the scalable of the network in all the four locations as well as extending the staffs
operations in the current office and also in future.
Goal of the project
Major goals differ in different organizations depending on the main objectives to be
achieved by a certain company. In our case here STP limited company have a desire of
implementing an IS infrastructure whereby the management in managing the rapidly
growing of the organisation in terms of the customers served and the operations of the
business as well. The basic objective of STP is to have their own control system for stock that
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
will enable sharing of even distribute all over the network. The access by the employees
should be enabled to ensure that there is accuracy and stock is reliable and provide exact
details as per the company policies. Another major goal to be implemented in is
management system for its clients that will ensure all staffs serves and manages the
customers’ accounts. STP will also need to implement an online website that will help to
advertise and market all available products for selling.
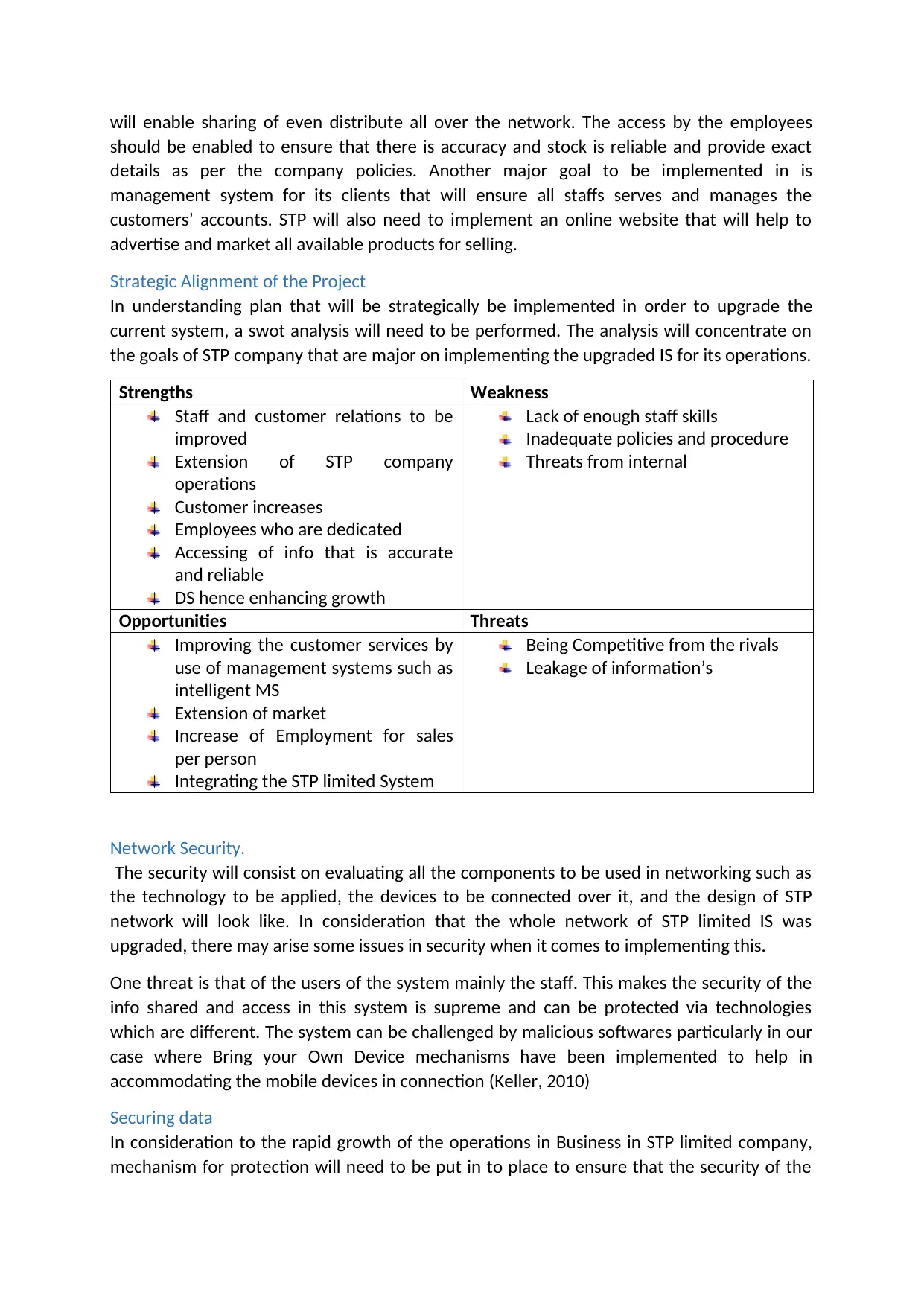
Strategic Alignment of the Project
In understanding plan that will be strategically be implemented in order to upgrade the
current system, a swot analysis will need to be performed. The analysis will concentrate on
the goals of STP company that are major on implementing the upgraded IS for its operations.
Strengths Weakness
Staff and customer relations to be
improved
Extension of STP company
operations
Customer increases
Employees who are dedicated
Accessing of info that is accurate
and reliable
DS hence enhancing growth
Lack of enough staff skills
Inadequate policies and procedure
Threats from internal
Opportunities Threats
Improving the customer services by
use of management systems such as
intelligent MS
Extension of market
Increase of Employment for sales
per person
Integrating the STP limited System
Being Competitive from the rivals
Leakage of information’s
Network Security.
The security will consist on evaluating all the components to be used in networking such as
the technology to be applied, the devices to be connected over it, and the design of STP
network will look like. In consideration that the whole network of STP limited IS was
upgraded, there may arise some issues in security when it comes to implementing this.
One threat is that of the users of the system mainly the staff. This makes the security of the
info shared and access in this system is supreme and can be protected via technologies
which are different. The system can be challenged by malicious softwares particularly in our
case where Bring your Own Device mechanisms have been implemented to help in
accommodating the mobile devices in connection (Keller, 2010)
Securing data
In consideration to the rapid growth of the operations in Business in STP limited company,
mechanism for protection will need to be put in to place to ensure that the security of the
should be enabled to ensure that there is accuracy and stock is reliable and provide exact
details as per the company policies. Another major goal to be implemented in is
management system for its clients that will ensure all staffs serves and manages the
customers’ accounts. STP will also need to implement an online website that will help to
advertise and market all available products for selling.
Strategic Alignment of the Project
In understanding plan that will be strategically be implemented in order to upgrade the
current system, a swot analysis will need to be performed. The analysis will concentrate on
the goals of STP company that are major on implementing the upgraded IS for its operations.
Strengths Weakness
Staff and customer relations to be
improved
Extension of STP company
operations
Customer increases
Employees who are dedicated
Accessing of info that is accurate
and reliable
DS hence enhancing growth
Lack of enough staff skills
Inadequate policies and procedure
Threats from internal
Opportunities Threats
Improving the customer services by
use of management systems such as
intelligent MS
Extension of market
Increase of Employment for sales
per person
Integrating the STP limited System
Being Competitive from the rivals
Leakage of information’s
Network Security.
The security will consist on evaluating all the components to be used in networking such as
the technology to be applied, the devices to be connected over it, and the design of STP
network will look like. In consideration that the whole network of STP limited IS was
upgraded, there may arise some issues in security when it comes to implementing this.
One threat is that of the users of the system mainly the staff. This makes the security of the
info shared and access in this system is supreme and can be protected via technologies
which are different. The system can be challenged by malicious softwares particularly in our
case where Bring your Own Device mechanisms have been implemented to help in
accommodating the mobile devices in connection (Keller, 2010)
Securing data
In consideration to the rapid growth of the operations in Business in STP limited company,
mechanism for protection will need to be put in to place to ensure that the security of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

larger information will be handled by STP limited due to the large numbers of increased
customers and operations of the business. In securing the data, STP should put in place
mechanisms internally that will help in managing employees, the products of STP and mostly
improve on implementing the policies and procedures that are appropriate and hence
defining how the staff will conduct themselves while using the upgraded network.
People, products, policies and procedures
The above 4ps work hand in hand as they relate with each other. Policies and procedures
provide a clear way in which employees at STP Limited will follow while executing their
services in selling of STP product. These rules are very important considering that the
company relies on internet to conduct its service and therefore employees might engage in
other activities that do not benefit the organization but rather put it at risk. Policies and
procedures ensures defines what information is to be accessed, used and by who. It also
outlines some of the rules that staff ought to observe while using the companies network.
The policies also dictate the network design and configuration mechanism thus ensuring that
the information shared across this network is secured.
ISP security and privacy considerations
The versions that is upgraded of the IS will rely on the connection of internet in its
operations. Therefore, this means that the ISP that will provide internet services to STP
Company will have to ensure that their network has been secured and cannot be infiltrated
by attacks such as viruses.
Other threats to data
The other big threat is that the staff lacks the technical skills on how to operate the
proposed Upgraded IS and hence making so risky in operating when the security of STP data
is concerned. This will come up in essence that the staff may interfere with working of the IS
either knowing or even not knowing thus leading to call the measures that will ensure the
security of IS. The measures to be called or put in place include:
Protections of IS components physically
Installation and configuration of firewalls that will help in filtering all actions that are
unwanted
Introducing mechanisms that will detect intrusion
Authorisation and authentication
Use of antiviruses and that are up to date.
Mobile device security
Use of portable devices such as the laptops, tablets and smartphones has been used in
greater numbers at STP Limited. Them being portable make it easy to move them across the
network, but with the security concern they contradict as they come up with threats in
security such as the downloading of malicious softwares, security issues that are physical
and access of sites that aare unsecured which in return might disclose the integrity of the
customers and operations of the business. In securing the data, STP should put in place
mechanisms internally that will help in managing employees, the products of STP and mostly
improve on implementing the policies and procedures that are appropriate and hence
defining how the staff will conduct themselves while using the upgraded network.
People, products, policies and procedures
The above 4ps work hand in hand as they relate with each other. Policies and procedures
provide a clear way in which employees at STP Limited will follow while executing their
services in selling of STP product. These rules are very important considering that the
company relies on internet to conduct its service and therefore employees might engage in
other activities that do not benefit the organization but rather put it at risk. Policies and
procedures ensures defines what information is to be accessed, used and by who. It also
outlines some of the rules that staff ought to observe while using the companies network.
The policies also dictate the network design and configuration mechanism thus ensuring that
the information shared across this network is secured.
ISP security and privacy considerations
The versions that is upgraded of the IS will rely on the connection of internet in its
operations. Therefore, this means that the ISP that will provide internet services to STP
Company will have to ensure that their network has been secured and cannot be infiltrated
by attacks such as viruses.
Other threats to data
The other big threat is that the staff lacks the technical skills on how to operate the
proposed Upgraded IS and hence making so risky in operating when the security of STP data
is concerned. This will come up in essence that the staff may interfere with working of the IS
either knowing or even not knowing thus leading to call the measures that will ensure the
security of IS. The measures to be called or put in place include:
Protections of IS components physically
Installation and configuration of firewalls that will help in filtering all actions that are
unwanted
Introducing mechanisms that will detect intrusion
Authorisation and authentication
Use of antiviruses and that are up to date.
Mobile device security
Use of portable devices such as the laptops, tablets and smartphones has been used in
greater numbers at STP Limited. Them being portable make it easy to move them across the
network, but with the security concern they contradict as they come up with threats in
security such as the downloading of malicious softwares, security issues that are physical
and access of sites that aare unsecured which in return might disclose the integrity of the

Such company(Collett, 2017). Therefore, STP should implement mechanisms for protection
to help in ensuring that the portable devices will not or ever compromise the entire STP
Limited network (Phifer, 2013).
Plan for Hardware Purchases
Hardware’s to be used by STP Company in offering the upgraded IS operations should be of
great significant. The purchase of that specific hardware should consider the following
factors in terms of the goals to achieve.
Performance and STP limited company operations.
Ensuring that it has more merits than from the9ir competitors(P, 2015).
The plan for hardware purchase is very important in essence that it helps in minimizing
delays and ensuring that the STP Operations will continue or there will be business
continuity.
Hardware Acquisition
STP company should have a plan that is very clear in acquiring the H/W due to failure or that
may have been damaged in the process operations when in consideration that the staff lacks
technical skills in operating such hardware’s. In order to enhance the business continuity,
STP company should come up with a plan for emergency on ways of acquiring the
hardware’s that are new especially in case where such situation arise. This will help in
minimizing the delays and ensuring that there is zero loss in the productions stage
Staff feedback and reviews
Staff at STP limited should be considered and made part of h/w plan when purchasing. This
will be through the regular review on how compatible the softwares used are with reference
to the version of the hardware’s. Also STP Limited should seek proper feedbacks on the staff
especially on the performance of hardware systems that are in place. This will allow the
management to realize what hardware components are in need and so forth.
Strategies of Hardware Purchase
Understanding of the requirements of the business where we have to use AR will help in
determining the chances of buying hardware’s of low cost from the suppliers that are of your
choice or the preferred. This will enhance STP Limited to come up with strategies that are
proper in procurement making it compatible with the plan of the business and that the
purchases will not in essence affect the continuation of the operations of the business may it
be due to constraints on finance.
Asset Register
This will be a record meant for all tools available in STP Limited Company(Intelligence, 2017).
This means that STP should have a records which are clear for each particular hardware
device and with reference to its location. This register will help in managing the monitor and
hence managing all the assets of IS that will be implemented at STP Limited. It is also much
significant to know that AR will help in improving the management on how to determ9ne the
hardware that will require replacement for improving the performance and the minimizing
to help in ensuring that the portable devices will not or ever compromise the entire STP
Limited network (Phifer, 2013).
Plan for Hardware Purchases
Hardware’s to be used by STP Company in offering the upgraded IS operations should be of
great significant. The purchase of that specific hardware should consider the following
factors in terms of the goals to achieve.
Performance and STP limited company operations.
Ensuring that it has more merits than from the9ir competitors(P, 2015).
The plan for hardware purchase is very important in essence that it helps in minimizing
delays and ensuring that the STP Operations will continue or there will be business
continuity.
Hardware Acquisition
STP company should have a plan that is very clear in acquiring the H/W due to failure or that
may have been damaged in the process operations when in consideration that the staff lacks
technical skills in operating such hardware’s. In order to enhance the business continuity,
STP company should come up with a plan for emergency on ways of acquiring the
hardware’s that are new especially in case where such situation arise. This will help in
minimizing the delays and ensuring that there is zero loss in the productions stage
Staff feedback and reviews
Staff at STP limited should be considered and made part of h/w plan when purchasing. This
will be through the regular review on how compatible the softwares used are with reference
to the version of the hardware’s. Also STP Limited should seek proper feedbacks on the staff
especially on the performance of hardware systems that are in place. This will allow the
management to realize what hardware components are in need and so forth.
Strategies of Hardware Purchase
Understanding of the requirements of the business where we have to use AR will help in
determining the chances of buying hardware’s of low cost from the suppliers that are of your
choice or the preferred. This will enhance STP Limited to come up with strategies that are
proper in procurement making it compatible with the plan of the business and that the
purchases will not in essence affect the continuation of the operations of the business may it
be due to constraints on finance.
Asset Register
This will be a record meant for all tools available in STP Limited Company(Intelligence, 2017).
This means that STP should have a records which are clear for each particular hardware
device and with reference to its location. This register will help in managing the monitor and
hence managing all the assets of IS that will be implemented at STP Limited. It is also much
significant to know that AR will help in improving the management on how to determ9ne the
hardware that will require replacement for improving the performance and the minimizing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
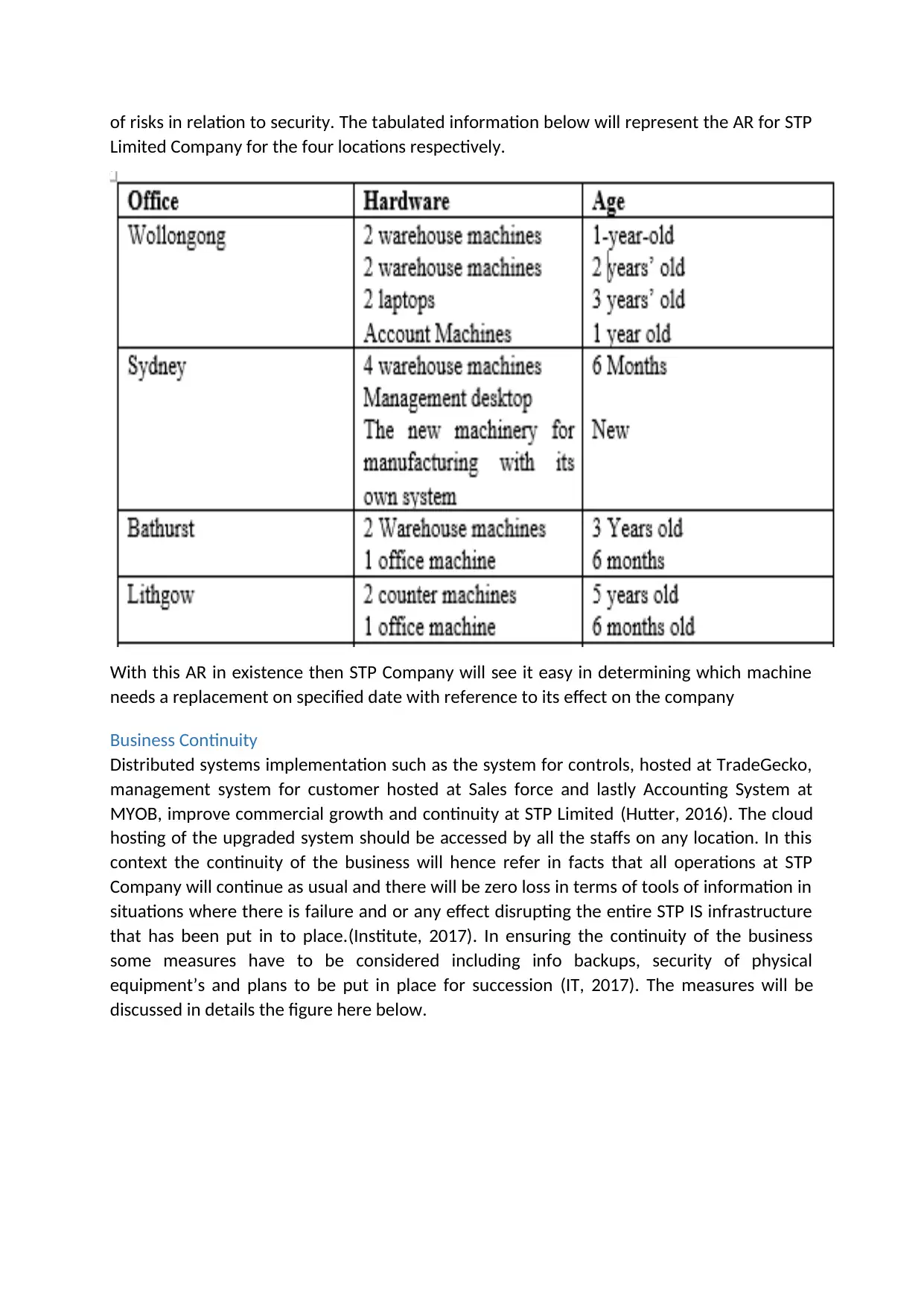
of risks in relation to security. The tabulated information below will represent the AR for STP
Limited Company for the four locations respectively.
With this AR in existence then STP Company will see it easy in determining which machine
needs a replacement on specified date with reference to its effect on the company
Business Continuity
Distributed systems implementation such as the system for controls, hosted at TradeGecko,
management system for customer hosted at Sales force and lastly Accounting System at
MYOB, improve commercial growth and continuity at STP Limited (Hutter, 2016). The cloud
hosting of the upgraded system should be accessed by all the staffs on any location. In this
context the continuity of the business will hence refer in facts that all operations at STP
Company will continue as usual and there will be zero loss in terms of tools of information in
situations where there is failure and or any effect disrupting the entire STP IS infrastructure
that has been put in to place.(Institute, 2017). In ensuring the continuity of the business
some measures have to be considered including info backups, security of physical
equipment’s and plans to be put in place for succession (IT, 2017). The measures will be
discussed in details the figure here below.
Limited Company for the four locations respectively.
With this AR in existence then STP Company will see it easy in determining which machine
needs a replacement on specified date with reference to its effect on the company
Business Continuity
Distributed systems implementation such as the system for controls, hosted at TradeGecko,
management system for customer hosted at Sales force and lastly Accounting System at
MYOB, improve commercial growth and continuity at STP Limited (Hutter, 2016). The cloud
hosting of the upgraded system should be accessed by all the staffs on any location. In this
context the continuity of the business will hence refer in facts that all operations at STP
Company will continue as usual and there will be zero loss in terms of tools of information in
situations where there is failure and or any effect disrupting the entire STP IS infrastructure
that has been put in to place.(Institute, 2017). In ensuring the continuity of the business
some measures have to be considered including info backups, security of physical
equipment’s and plans to be put in place for succession (IT, 2017). The measures will be
discussed in details the figure here below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk Management
The number of issues with reference to risk involved in operations of business at STP limited
has grown and the idea is that there will be an upgraded IS that will be put in place (isaca,
2017). The issues related or clearly said to be risks will rotates around the privacy, optimizing
and the general security of the new IS. These risks that are likely to be faced by STP Limited
are as follows.
Strategic risks
Operations risks
Technical risks
Managerial risks
Financial risks
Compliance risks
The above mentioned risks may come up due to completion, theft cases, cost increases, and
calamities including fire, IS attacks, Staff not available and many others. All these risks and
explanations of the anticipated effects will call for measure management of the risks by STP
Limited Company that will help in avoiding all the effects that might be negative and might
interfere with the smooth moving operation of the company.
The number of issues with reference to risk involved in operations of business at STP limited
has grown and the idea is that there will be an upgraded IS that will be put in place (isaca,
2017). The issues related or clearly said to be risks will rotates around the privacy, optimizing
and the general security of the new IS. These risks that are likely to be faced by STP Limited
are as follows.
Strategic risks
Operations risks
Technical risks
Managerial risks
Financial risks
Compliance risks
The above mentioned risks may come up due to completion, theft cases, cost increases, and
calamities including fire, IS attacks, Staff not available and many others. All these risks and
explanations of the anticipated effects will call for measure management of the risks by STP
Limited Company that will help in avoiding all the effects that might be negative and might
interfere with the smooth moving operation of the company.

Security policy
Proper security policies will have to be put in to place to enable proper protection of its
assets and the procedures in which the staffs are supposed to work upon or even within
themselves especially when rendering their services, STP should ensure that the have proper
security policy. This will ensure that the communication expectation of the company is
proper and according to the objectives stated by STP Limited company. Some of the security
policy to be implemented will be thing like the use of antivirus, data policy, ethics policy,
access management and lastly the wireless communication policy
Training and awareness.
Company have to ensure that its staff are trained well in order for them to be equipped with
the knowledge and have proper skills concerning the updated IS. The training will ensure
that the set standards will be in compliance with the objectives of STP Limited company
while staffs are performing their duties. Also they should also be educated on the awareness
of the threats in security that may be associated with the upgraded IS.
Conclusion
From the above explanation on the report an evaluation that is clear of the information
system upgrade will be performed and an analysis of the network security will be reached
upon. The report has highlighted threats in security that the STP limited company should put
first in ensuring the continuity the business and proper management of processes. Also a
training that is thorough should be offered to the staffs as it will ensure that all staffs will
have a proper understanding of the upgraded information system. STP Limited should also
formulate policies to manage wireless network and BYOD devices in order to ensure that
their network is not compromised by the use of mobile devices.
Recommendations.
The company should perform policies and procedures that will clearly show how the
operations will be done for enhancing proper system security. Lastly STP should have a
proper plan for purchasing hardware tools as it will help in keeping the h/w records in asset
registers.
Proper security policies will have to be put in to place to enable proper protection of its
assets and the procedures in which the staffs are supposed to work upon or even within
themselves especially when rendering their services, STP should ensure that the have proper
security policy. This will ensure that the communication expectation of the company is
proper and according to the objectives stated by STP Limited company. Some of the security
policy to be implemented will be thing like the use of antivirus, data policy, ethics policy,
access management and lastly the wireless communication policy
Training and awareness.
Company have to ensure that its staff are trained well in order for them to be equipped with
the knowledge and have proper skills concerning the updated IS. The training will ensure
that the set standards will be in compliance with the objectives of STP Limited company
while staffs are performing their duties. Also they should also be educated on the awareness
of the threats in security that may be associated with the upgraded IS.
Conclusion
From the above explanation on the report an evaluation that is clear of the information
system upgrade will be performed and an analysis of the network security will be reached
upon. The report has highlighted threats in security that the STP limited company should put
first in ensuring the continuity the business and proper management of processes. Also a
training that is thorough should be offered to the staffs as it will ensure that all staffs will
have a proper understanding of the upgraded information system. STP Limited should also
formulate policies to manage wireless network and BYOD devices in order to ensure that
their network is not compromised by the use of mobile devices.
Recommendations.
The company should perform policies and procedures that will clearly show how the
operations will be done for enhancing proper system security. Lastly STP should have a
proper plan for purchasing hardware tools as it will help in keeping the h/w records in asset
registers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Collett, S., 2017. Five new threats to your mobile security. Information Security, 1 August.pp.
1-7.
Hutter, D., 2016. Physical Security and Why It Is Important, s.l.: GIAC (GSEC) Gold
Certification.
Institute, B. C., 2017. resources. [Online]
Available at: http://www.thebci.org/index.php/resources/what-is-business-continuity
[Accessed 7 October 2017].
Intelligence, L., 2017. Infrastructure Asset Management, UK: Pitney Bowes.
isaca, 2017. knowledge-center. [Online]
Available at: http://www.isaca.org/knowledge-center/risk-it-it-risk-management/pages/
default.aspx
[Accessed 7 October 2017].
IT, R., 2017. News. [Online]
Available at: http://www.riscitsolutions.com/news/archived-news/why-you-should-backup
[Accessed 7 October 2017].
Keller, 2010. Information security threats in small businesses. Information Systems
Management, Volume 22, pp. 1-19.
Phifer, L., 2013. BYOD Security Strategies. Balancing BYOD risks and rewards, pp. 1-32.
P, P., 2015. Industrial Management & Data Systems. s.l.:s.n.
Collett, S., 2017. Five new threats to your mobile security. Information Security, 1 August.pp.
1-7.
Hutter, D., 2016. Physical Security and Why It Is Important, s.l.: GIAC (GSEC) Gold
Certification.
Institute, B. C., 2017. resources. [Online]
Available at: http://www.thebci.org/index.php/resources/what-is-business-continuity
[Accessed 7 October 2017].
Intelligence, L., 2017. Infrastructure Asset Management, UK: Pitney Bowes.
isaca, 2017. knowledge-center. [Online]
Available at: http://www.isaca.org/knowledge-center/risk-it-it-risk-management/pages/
default.aspx
[Accessed 7 October 2017].
IT, R., 2017. News. [Online]
Available at: http://www.riscitsolutions.com/news/archived-news/why-you-should-backup
[Accessed 7 October 2017].
Keller, 2010. Information security threats in small businesses. Information Systems
Management, Volume 22, pp. 1-19.
Phifer, L., 2013. BYOD Security Strategies. Balancing BYOD risks and rewards, pp. 1-32.
P, P., 2015. Industrial Management & Data Systems. s.l.:s.n.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





