The Point of Sales System Assignment PDF
Added on 2021-04-17
12 Pages1220 Words34 Views
Running head: THE POINT OF SALES SYSTEM
The Point of Sales System
Name of the student:
Name of the University:
Author note:
The Point of Sales System
Name of the student:
Name of the University:
Author note:

1
THE POINT OF SALES SYSTEM
Table of Contents
Introduction................................................................................................................................2
Development Commentary........................................................................................................2
Login Page and Added Security.............................................................................................2
The Add Transaction page.....................................................................................................4
Add Items to cart....................................................................................................................5
View Stock status...................................................................................................................6
Use Case Diagram..................................................................................................................8
UML Class Diagram..............................................................................................................9
Sequence Diagram...............................................................................................................10
THE POINT OF SALES SYSTEM
Table of Contents
Introduction................................................................................................................................2
Development Commentary........................................................................................................2
Login Page and Added Security.............................................................................................2
The Add Transaction page.....................................................................................................4
Add Items to cart....................................................................................................................5
View Stock status...................................................................................................................6
Use Case Diagram..................................................................................................................8
UML Class Diagram..............................................................................................................9
Sequence Diagram...............................................................................................................10

2
THE POINT OF SALES SYSTEM
Introduction
The aim of this report is to design and develop an Employee Resource Management
system that provides the base for implementing a Point of Sales system. This is meant to be a
sub-system of the entire ERM software. The Point of Sales system is being designed to fulfill
the needs of a retailer staff who may add new transactions into the system, add new customer
details and view stock quantities of the specified items. This is a system to be used by a
pharmaceutical company; hence, the items are accordingly updated into the database along
with all other necessary details. The software is to be developed using C#, and would be a
Windows-based multi forms application software (Net 2012). It is going to have multiple
forms to serve as the various modules of functions that the system must implement.
Furthermore, MySQL through phpMyAdmin shall be used as the backend database to store
all necessary data.
Development Commentary
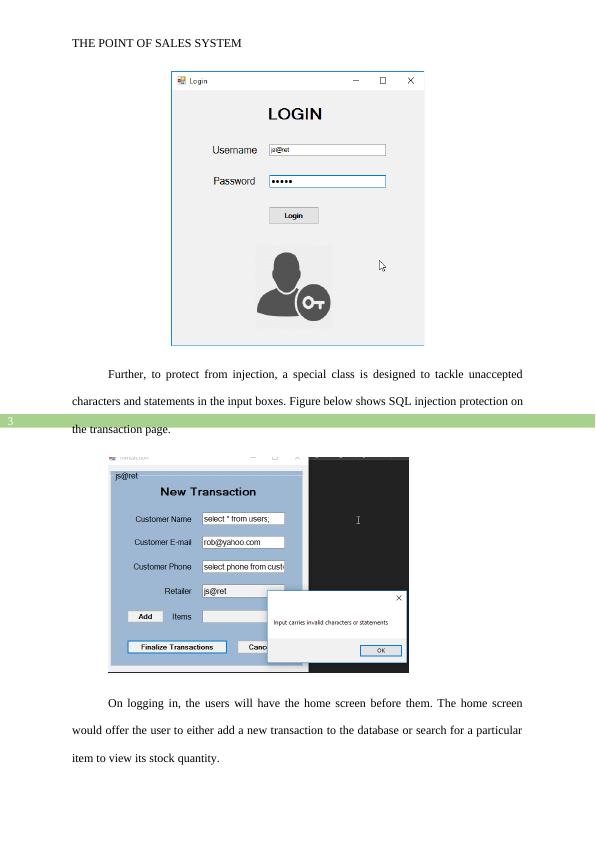
Login Page and Added Security
The software opens up to the user with the login page. It is assumed that only the
Retail Staffs can login for the time being. Accordingly, some dummy user data is fed into the
associated database. The users need to login using their respective user ID and password. To
comply with the security guidelines, the software uses MD5 cryptography methods to encrypt
the user passwords in the database. This averts the chances of the system from being hacked.
Data security is one of the most important factors that must be integrated to any information
system (Stallings et al 2012). MD5 is a strong data encryption method that can encrypt and
decrypt messages of any length. It produces hash values worth 128 bits (Gupta and Kumar
2014).
THE POINT OF SALES SYSTEM
Introduction
The aim of this report is to design and develop an Employee Resource Management
system that provides the base for implementing a Point of Sales system. This is meant to be a
sub-system of the entire ERM software. The Point of Sales system is being designed to fulfill
the needs of a retailer staff who may add new transactions into the system, add new customer
details and view stock quantities of the specified items. This is a system to be used by a
pharmaceutical company; hence, the items are accordingly updated into the database along
with all other necessary details. The software is to be developed using C#, and would be a
Windows-based multi forms application software (Net 2012). It is going to have multiple
forms to serve as the various modules of functions that the system must implement.
Furthermore, MySQL through phpMyAdmin shall be used as the backend database to store
all necessary data.
Development Commentary
Login Page and Added Security
The software opens up to the user with the login page. It is assumed that only the
Retail Staffs can login for the time being. Accordingly, some dummy user data is fed into the
associated database. The users need to login using their respective user ID and password. To
comply with the security guidelines, the software uses MD5 cryptography methods to encrypt
the user passwords in the database. This averts the chances of the system from being hacked.
Data security is one of the most important factors that must be integrated to any information
system (Stallings et al 2012). MD5 is a strong data encryption method that can encrypt and
decrypt messages of any length. It produces hash values worth 128 bits (Gupta and Kumar
2014).

3
THE POINT OF SALES SYSTEM
Further, to protect from injection, a special class is designed to tackle unaccepted
characters and statements in the input boxes. Figure below shows SQL injection protection on
the transaction page.
On logging in, the users will have the home screen before them. The home screen
would offer the user to either add a new transaction to the database or search for a particular
item to view its stock quantity.
THE POINT OF SALES SYSTEM
Further, to protect from injection, a special class is designed to tackle unaccepted
characters and statements in the input boxes. Figure below shows SQL injection protection on
the transaction page.
On logging in, the users will have the home screen before them. The home screen
would offer the user to either add a new transaction to the database or search for a particular
item to view its stock quantity.
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Test Taken in the Website Applicationlg...
|21
|875
|50
System Modellinglg...
|8
|807
|1
First National Bank - User Registration, Login, Account Management and Transactionslg...
|9
|830
|301
Assignment on Oracle Virtual Machine Installationlg...
|16
|1480
|225
Security Measures in Database Principleslg...
|9
|1927
|298
System Analysislg...
|8
|876
|42
