SNMP in Network Management: A Detailed Report
VerifiedAdded on 2023/01/19
|12
|2240
|29
AI Summary
This document provides a detailed report on SNMP in network management. It covers topics such as introduction to SNMP, network management using SNMP, SNMP components, SNMP versions, and SNMP working. It also discusses SNMP commands, assessing target hosts using SNMP, switch MIBs, port identification, operational and non-operational ports, and the VYOS test network. Additionally, it explores SNMP traps and dealing with cyber attacks. Finally, it presents the key points to consider when purchasing a network management system.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

University
Semester
NETWORKING
Student ID
Student Name
Submission Date
1
Semester
NETWORKING
Student ID
Student Name
Submission Date
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Section A...............................................................................................................................................3
1. Introduction to SNMP................................................................................................................3
2. Network Management - SNMP..................................................................................................3
3. SMMP Components...................................................................................................................3
4. SNMP Version...........................................................................................................................4
5. SNMP Working.........................................................................................................................4
Section B...............................................................................................................................................5
1. SNMP commands......................................................................................................................5
2. Assessing Target Hosts Using SNMP........................................................................................6
3. Switch MIBs..............................................................................................................................9
4. Port Identification......................................................................................................................9
5. Operational and Non-Operational Ports.....................................................................................9
6. VYOS Test Network..................................................................................................................9
Section C.............................................................................................................................................10
1. SNMP Traps............................................................................................................................10
2. Cyber Attack............................................................................................................................10
Section D.............................................................................................................................................11
2
Section A...............................................................................................................................................3
1. Introduction to SNMP................................................................................................................3
2. Network Management - SNMP..................................................................................................3
3. SMMP Components...................................................................................................................3
4. SNMP Version...........................................................................................................................4
5. SNMP Working.........................................................................................................................4
Section B...............................................................................................................................................5
1. SNMP commands......................................................................................................................5
2. Assessing Target Hosts Using SNMP........................................................................................6
3. Switch MIBs..............................................................................................................................9
4. Port Identification......................................................................................................................9
5. Operational and Non-Operational Ports.....................................................................................9
6. VYOS Test Network..................................................................................................................9
Section C.............................................................................................................................................10
1. SNMP Traps............................................................................................................................10
2. Cyber Attack............................................................................................................................10
Section D.............................................................................................................................................11
2

Section A
In this section, we are explain the detailed report on SNMP in certain areas of
management and also explain the details of traditional SNMP controlled technologies and
areas covered by the various management systems.
1. Introduction to SNMP
Now a day, the complex network of servers, routers and switches and it can seem like
a daunting task to manage all the devices on network and make sure not only up and running
but also performing optimally. In this situation, the simple network management protocol
can help and it is used to provide users with a simple set of operations which allow these
devices are managed remotely. Basically, the SNMP is a set of operations which are provides
the administrators the ability to change the state of the SNMP based devices. It usually
associated with managing routers and it can be used to manage the many types of devices. It
allows the retrieval of SNMP information can be managed. In network management, it
consists of all the administrative actions taken to keep a network running efficiently.
2. Network Management - SNMP
In network management, the simple network management protocol is allows a device
to report information about its current operational state. It is most popular protocol for
supporting the network device monitoring. It also allows polling of individual designated
device attributes such as number of packets and system name received through the interface.
It is organized into tables, sets and records. While simplest switches and routers are quite
limited provisions for SMNP and provides the extensive support. The significant of SNMP
support which are sometimes referred as managed devices. The SNMP node that replies to
requests for information is called as SNMP agent. It is more simply to be a standalone tool
known as an SNMP browser or MIB browser. While most MIB browsers are used to
understand the graphical user interface and most command line tools of SNMP is snmpget
and snmpwalk command.
3. SMMP Components
SNMP Managers
The SNMP managers are is used to configure the computer to poll the SNMP
agent for information. The managers are send the query required to SNMP agent with
the credentials.
SNMP Agents
3
In this section, we are explain the detailed report on SNMP in certain areas of
management and also explain the details of traditional SNMP controlled technologies and
areas covered by the various management systems.
1. Introduction to SNMP
Now a day, the complex network of servers, routers and switches and it can seem like
a daunting task to manage all the devices on network and make sure not only up and running
but also performing optimally. In this situation, the simple network management protocol
can help and it is used to provide users with a simple set of operations which allow these
devices are managed remotely. Basically, the SNMP is a set of operations which are provides
the administrators the ability to change the state of the SNMP based devices. It usually
associated with managing routers and it can be used to manage the many types of devices. It
allows the retrieval of SNMP information can be managed. In network management, it
consists of all the administrative actions taken to keep a network running efficiently.
2. Network Management - SNMP
In network management, the simple network management protocol is allows a device
to report information about its current operational state. It is most popular protocol for
supporting the network device monitoring. It also allows polling of individual designated
device attributes such as number of packets and system name received through the interface.
It is organized into tables, sets and records. While simplest switches and routers are quite
limited provisions for SMNP and provides the extensive support. The significant of SNMP
support which are sometimes referred as managed devices. The SNMP node that replies to
requests for information is called as SNMP agent. It is more simply to be a standalone tool
known as an SNMP browser or MIB browser. While most MIB browsers are used to
understand the graphical user interface and most command line tools of SNMP is snmpget
and snmpwalk command.
3. SMMP Components
SNMP Managers
The SNMP managers are is used to configure the computer to poll the SNMP
agent for information. The managers are send the query required to SNMP agent with
the credentials.
SNMP Agents
3

The SNMP agents are used to do the bulk of the work in network management
and the agents are responsible for gathering the information about the local system
and storing them in to format which can be queried. And, the updating the database is
called as management information base.
Management information base (MIB)
Basically, the MIB is a pre defined infrastructure and hierarchical structure
which is used to stores the information that can be queried or set. Generally the
SNMP agent computer configures which managers should have access to its
information. The SNMP agents are act as an intermediary to report the information on
devices.
4. SNMP Version
The SNMP has three versions such as
SNMPv1 - The SNMPv1 is collections of RFCs starting with RFC1065. It
considered a temporary network management protocol.
SNMPv2 - The SNMPv2 is expanding the basic information and RFCs
starting with RFC1442. It introduced the improved techniques
for managing tables. It also included the proposed security
mechanism.
SNMPv3 - The SNMPv3 is finally delivered a model for effective security.
The RFCs final version is in RFC3414.
5. SNMP Working
The SNMP performs the multitude of the function and relying on the mixture of pulls
and push communications between the network management and network devices. It can
issue write and read commands such as changing the configuration setting and resetting the
password. The SNMP is used to provide the report based on how much bandwidth, memory
and CPU in use and also the SNMP managers are automatically sending the text or email
message alert for administrator if a predefined threshold is exceeded.
The SNMP is still popular because it consumes the low network resources and it
requires the few processing capabilities. It has the capabilities to monitor the number of
processes are running on the particular device, information about the memory of the various
devices and CPU usages, graph and chart with traffic statistics. It has ability to allow more
the one device on network which to be used as managers. It easily identifies the any unusual
activities and defects by processing the information gathered by the managed device.
4
and the agents are responsible for gathering the information about the local system
and storing them in to format which can be queried. And, the updating the database is
called as management information base.
Management information base (MIB)
Basically, the MIB is a pre defined infrastructure and hierarchical structure
which is used to stores the information that can be queried or set. Generally the
SNMP agent computer configures which managers should have access to its
information. The SNMP agents are act as an intermediary to report the information on
devices.
4. SNMP Version
The SNMP has three versions such as
SNMPv1 - The SNMPv1 is collections of RFCs starting with RFC1065. It
considered a temporary network management protocol.
SNMPv2 - The SNMPv2 is expanding the basic information and RFCs
starting with RFC1442. It introduced the improved techniques
for managing tables. It also included the proposed security
mechanism.
SNMPv3 - The SNMPv3 is finally delivered a model for effective security.
The RFCs final version is in RFC3414.
5. SNMP Working
The SNMP performs the multitude of the function and relying on the mixture of pulls
and push communications between the network management and network devices. It can
issue write and read commands such as changing the configuration setting and resetting the
password. The SNMP is used to provide the report based on how much bandwidth, memory
and CPU in use and also the SNMP managers are automatically sending the text or email
message alert for administrator if a predefined threshold is exceeded.
The SNMP is still popular because it consumes the low network resources and it
requires the few processing capabilities. It has the capabilities to monitor the number of
processes are running on the particular device, information about the memory of the various
devices and CPU usages, graph and chart with traffic statistics. It has ability to allow more
the one device on network which to be used as managers. It easily identifies the any unusual
activities and defects by processing the information gathered by the managed device.
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Section B
In this section, we are analysis the SNMP in detail such as SNMP command, targt
hosts to assess using the SNMP, Identification of ports, identification of operational and non -
operational ports and finally, find out the list of the devices are connected on the VYOS test
network.
1. SNMP commands
In SNMP, the snmpget and snmpwalk commands are most important commands. It
can be easily operated from the command prompt. Both commands are using the SNMPv3
version of SNMP.
snmpget
snmpget command is used to retrieve the information from a network subscriber
through the simple network management protocol and it use the SNMP message type "GET"
which is requests a specific record on the target system.
snmpwalk
This command is not only retrieve the specific data on the targeted SNMP enabled
device, but it also retrieve the subsequent of the data on the target system. It uses the
messages from the “GETNEXT” type.
5
In this section, we are analysis the SNMP in detail such as SNMP command, targt
hosts to assess using the SNMP, Identification of ports, identification of operational and non -
operational ports and finally, find out the list of the devices are connected on the VYOS test
network.
1. SNMP commands
In SNMP, the snmpget and snmpwalk commands are most important commands. It
can be easily operated from the command prompt. Both commands are using the SNMPv3
version of SNMP.
snmpget
snmpget command is used to retrieve the information from a network subscriber
through the simple network management protocol and it use the SNMP message type "GET"
which is requests a specific record on the target system.
snmpwalk
This command is not only retrieve the specific data on the targeted SNMP enabled
device, but it also retrieve the subsequent of the data on the target system. It uses the
messages from the “GETNEXT” type.
5
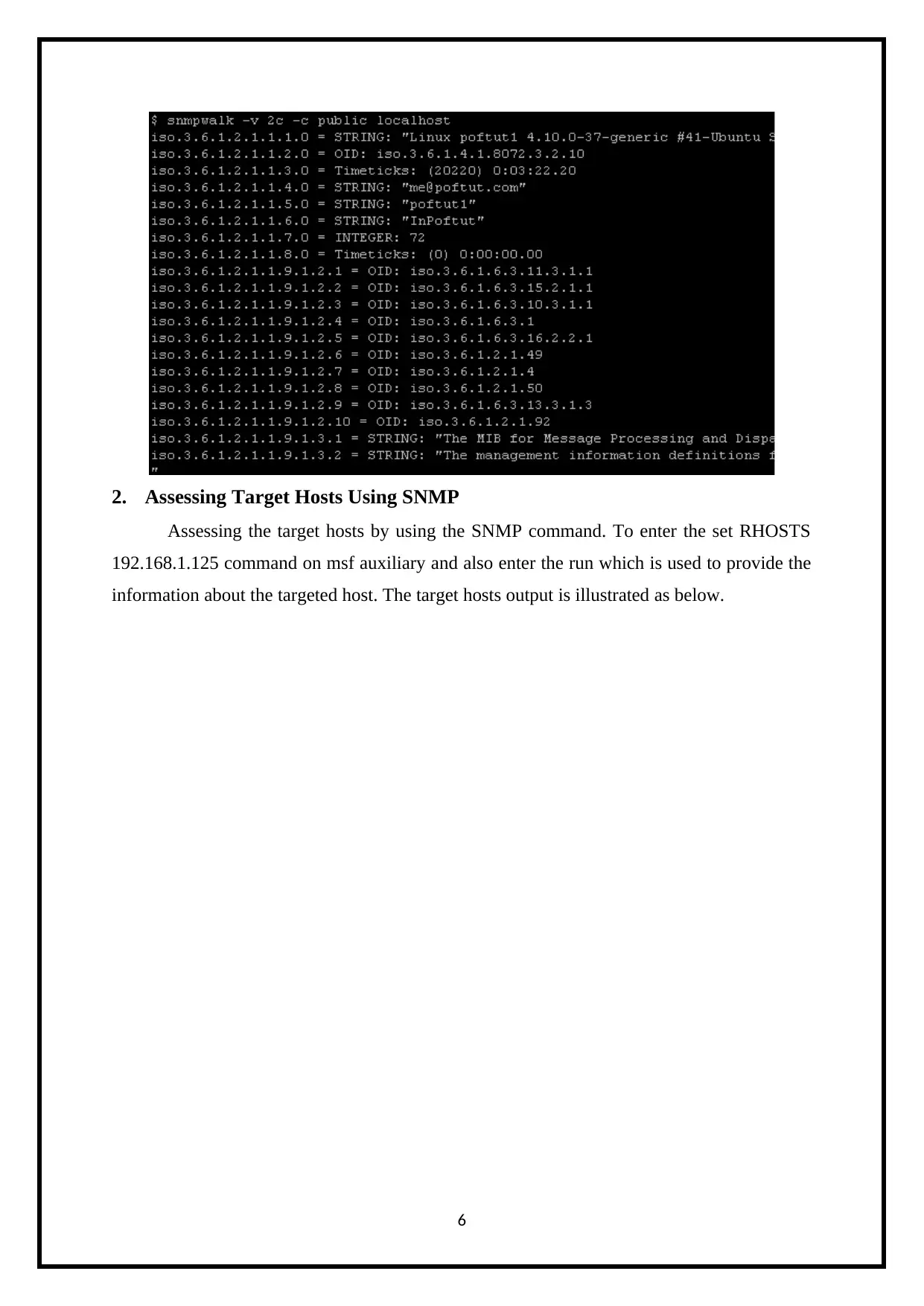
2. Assessing Target Hosts Using SNMP
Assessing the target hosts by using the SNMP command. To enter the set RHOSTS
192.168.1.125 command on msf auxiliary and also enter the run which is used to provide the
information about the targeted host. The target hosts output is illustrated as below.
6
Assessing the target hosts by using the SNMP command. To enter the set RHOSTS
192.168.1.125 command on msf auxiliary and also enter the run which is used to provide the
information about the targeted host. The target hosts output is illustrated as below.
6
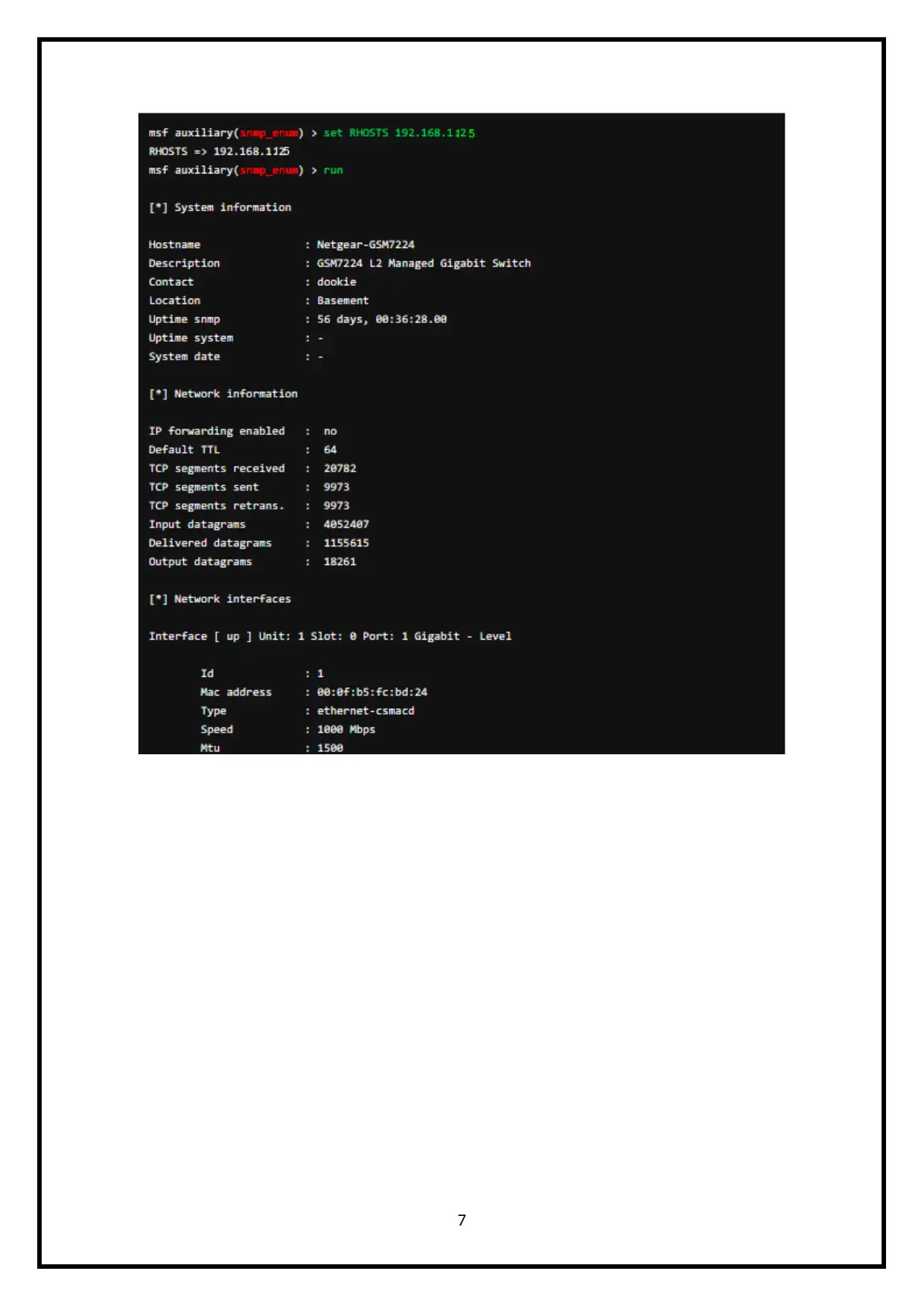
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

a. Number of network interfaces 1
b. Number of datagram’s/packets received 4052407
c. Number of ping messages received by the target host 64
d. Network Devices connected to the switch 1
e. How long has the SNMP agent been running? 56 days, 00:36:28.00
f. How many datagram’s have been sent by the target host? 18261
g. Which ports are currently active 23, 80, 4242, 2222
h. How many segments have been received by the target host? 20782
i. How many SNMP Get-Request PDUs have been accepted
and processed by the host switch?
9973
j. Which ports are not available for traffic? Ports 161, and 514
k. What is the CPU utilization of the router attached to the
main target host?
1000 Mbps
3. Switch MIBs
The parts of the switch MIBs that have used during the assessment are mostly the
ports such as UDP 161 and UDP 162.
8
b. Number of datagram’s/packets received 4052407
c. Number of ping messages received by the target host 64
d. Network Devices connected to the switch 1
e. How long has the SNMP agent been running? 56 days, 00:36:28.00
f. How many datagram’s have been sent by the target host? 18261
g. Which ports are currently active 23, 80, 4242, 2222
h. How many segments have been received by the target host? 20782
i. How many SNMP Get-Request PDUs have been accepted
and processed by the host switch?
9973
j. Which ports are not available for traffic? Ports 161, and 514
k. What is the CPU utilization of the router attached to the
main target host?
1000 Mbps
3. Switch MIBs
The parts of the switch MIBs that have used during the assessment are mostly the
ports such as UDP 161 and UDP 162.
8

The SNMP manager uses the port UDP 161 to poll the agent at the regular
intervals.
And, the port 162 is used by the SNMP traps which are used to send the device and
system information to the manager.
4. Port Identification
To identifying the port that is periodically flapping and intermittently dropping out,
first step to run the netstat -a command to check the port status, after determine the
ports which one is constantly up and down.
In our analysis, Gigabit 0/0 was constantly up and down. So, we taken to trouble
shoot problem is to check if keep alive was enabled which is used to check the any
unusual looping or cabling issues on the identified port.
To check the unusual activity on switch by type the “sh log” command on switch
which is used to analyse the problem on switch ports.
And, the periodic flapping may be occur because user exceed the spanning tree
limits and seven hops are the recommend limit for the spanning tree.
5. Operational and Non-Operational Ports
Generally, the ports are set to be state of operational and non operational.
Operational Ports 2222,4242,80 and 23
Non – Operational Ports 161 and 514
The non operational ports are disconnected ot not allow any traffic to go through
the network. The 161 and 514 ports are set not to allow any traffic and connections
because there is no network connection.
6. VYOS Test Network
To use the below command to identifies the number of devices are connected on the
VYOS test network.
use auxiliary/scanner/snmp/snmp_enumshares
After enter the show options command to view the number of devices are connected
on VYOS test network. It is illustrated as below.
9
intervals.
And, the port 162 is used by the SNMP traps which are used to send the device and
system information to the manager.
4. Port Identification
To identifying the port that is periodically flapping and intermittently dropping out,
first step to run the netstat -a command to check the port status, after determine the
ports which one is constantly up and down.
In our analysis, Gigabit 0/0 was constantly up and down. So, we taken to trouble
shoot problem is to check if keep alive was enabled which is used to check the any
unusual looping or cabling issues on the identified port.
To check the unusual activity on switch by type the “sh log” command on switch
which is used to analyse the problem on switch ports.
And, the periodic flapping may be occur because user exceed the spanning tree
limits and seven hops are the recommend limit for the spanning tree.
5. Operational and Non-Operational Ports
Generally, the ports are set to be state of operational and non operational.
Operational Ports 2222,4242,80 and 23
Non – Operational Ports 161 and 514
The non operational ports are disconnected ot not allow any traffic to go through
the network. The 161 and 514 ports are set not to allow any traffic and connections
because there is no network connection.
6. VYOS Test Network
To use the below command to identifies the number of devices are connected on the
VYOS test network.
use auxiliary/scanner/snmp/snmp_enumshares
After enter the show options command to view the number of devices are connected
on VYOS test network. It is illustrated as below.
9

Section C
In this section, we are remotely investigated and trouble shoots the network problem
scenario. Here, we are assuming the SNMP tool is already established on the network. After,
send the SNMP trap to reporting their CPU utilization and also reporting the suggestion of
the cyber attacks have been identified on targets local email server and web server.
1. SNMP Traps
To detect the issues related to the utilization of the CPU which is addressed by SNMP
trap by using the SNMP command. It is illustrated as below.
It is used to identify the high utilization of CPU which is done on RMON and it is
used to send the SNMP traps to management station. And, the event type of SNMP used to
configure the EEM applet which is used to store the necessary commands in the high_cpu.txt
file.
2. Cyber Attack
If possible cyber attacks are targeting the local email server and web server, to
connect the server from the network which is used to prevent the anymore connections and it
is most effective action to prevent the local email server and web server from the cyber
attacks. After, disconnecting the server to create the efficient post incidence response plan
10
In this section, we are remotely investigated and trouble shoots the network problem
scenario. Here, we are assuming the SNMP tool is already established on the network. After,
send the SNMP trap to reporting their CPU utilization and also reporting the suggestion of
the cyber attacks have been identified on targets local email server and web server.
1. SNMP Traps
To detect the issues related to the utilization of the CPU which is addressed by SNMP
trap by using the SNMP command. It is illustrated as below.
It is used to identify the high utilization of CPU which is done on RMON and it is
used to send the SNMP traps to management station. And, the event type of SNMP used to
configure the EEM applet which is used to store the necessary commands in the high_cpu.txt
file.
2. Cyber Attack
If possible cyber attacks are targeting the local email server and web server, to
connect the server from the network which is used to prevent the anymore connections and it
is most effective action to prevent the local email server and web server from the cyber
attacks. After, disconnecting the server to create the efficient post incidence response plan
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

which is requires the various key components before cyber attack occurs. The effective post
incidence plan includes following actions,
Firstly, identifies the organization critical assets with an anticipation which is
changes unauthorised access made on the potential impact in case of a loss.
Secondly, implement the automated monitoring and enable the logging which
are used to go long way in continuous attach monitoring and detection.
Thirdly, map the threat surface which is including the all the points an attacker
could exploit to get the virtual or physical access to the targeted systems.
And, also create the cyber security team which is used to report the possible cyber
attack information and cyber security teams handling the cyber attack incident. The
organizations are having access to the impact that suspected cyber attack and if cyber attacks
are occurred, implement the disaster recovery plan to restore the normalcy on the
organization.
Section D
In this section, we are considering the network management scenario to produce the
detailed reports and summarize the silent points.
Based on network management scenario, the medium size company currently relied
on third party support for their data network. And, it interested to manage their own network.
So, we are providing the detailed key points considered when purchasing a network
management system. The main objective of the network management system is used to,
Assist in capacity planning
View the network topology
Track the activates of network
Streamline the network trouble shooting
Improve the overall network reliability
The various factors are should be considered the choosing the network management
system such as,
Easy of Deployment
Ease of use
Real time visibility
Automated Base lines
Monitoring Efficiency
11
incidence plan includes following actions,
Firstly, identifies the organization critical assets with an anticipation which is
changes unauthorised access made on the potential impact in case of a loss.
Secondly, implement the automated monitoring and enable the logging which
are used to go long way in continuous attach monitoring and detection.
Thirdly, map the threat surface which is including the all the points an attacker
could exploit to get the virtual or physical access to the targeted systems.
And, also create the cyber security team which is used to report the possible cyber
attack information and cyber security teams handling the cyber attack incident. The
organizations are having access to the impact that suspected cyber attack and if cyber attacks
are occurred, implement the disaster recovery plan to restore the normalcy on the
organization.
Section D
In this section, we are considering the network management scenario to produce the
detailed reports and summarize the silent points.
Based on network management scenario, the medium size company currently relied
on third party support for their data network. And, it interested to manage their own network.
So, we are providing the detailed key points considered when purchasing a network
management system. The main objective of the network management system is used to,
Assist in capacity planning
View the network topology
Track the activates of network
Streamline the network trouble shooting
Improve the overall network reliability
The various factors are should be considered the choosing the network management
system such as,
Easy of Deployment
Ease of use
Real time visibility
Automated Base lines
Monitoring Efficiency
11

Integrated Work flows
Consolidation Tools
OSS Integration
Future Proof Solution
Based on above key feature, suggest that company needs to choose the PRTG network
monitor system which is used to provide the capacity to monitor the all the traffic, device,
system and applications of the company network infrastructure. It offers the reliability of the
network and it supports the various technologies such as SSH, ping, flow technology, SNMP
and WMI. It has the powerful API such as REST, DDL and Python.
12
Consolidation Tools
OSS Integration
Future Proof Solution
Based on above key feature, suggest that company needs to choose the PRTG network
monitor system which is used to provide the capacity to monitor the all the traffic, device,
system and applications of the company network infrastructure. It offers the reliability of the
network and it supports the various technologies such as SSH, ping, flow technology, SNMP
and WMI. It has the powerful API such as REST, DDL and Python.
12
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




