VANET: Current Challenges, Security, and Future Perspectives Analysis
VerifiedAdded on 2019/09/20
|19
|4643
|441
Report
AI Summary
This report provides a comprehensive overview of Vehicular Ad-hoc Networks (VANETs), a subclass of Mobile Ad Hoc Networks (MANETs) and a promising technology for Intelligent Transportation Systems (ITS). It explores the unique mobility patterns and rapidly changing topology of VANETs, highlighting the limitations of applying MANET routing protocols. The report delves into the current challenges, including security attacks such as Denial of Service (DoS), Sybil attacks, Black Hole attacks, and alteration attacks, as well as network management issues. It examines security requirements and identifies key areas for future research, such as addressing security vulnerabilities and improving network performance. The study also discusses the architecture, components, and layered model of VANETs, including Roadside Units (RSUs) and On-Board Units (OBUs), and the various communication protocols used. The report emphasizes the importance of addressing these challenges to facilitate the widespread implementation of VANETs and improve traffic flow, reduce accidents, and enhance road safety. The conclusion summarizes the key findings and emphasizes the need for ongoing research to realize the full potential of VANETs.

VEHICULA AD-HOC NETWORK
Name:
Student Number:
Word count:
Name of the course:
Tutor name:
“VEHICULAR AD-HOC NETWORK:
CURRENT CHALLENGES, AND FUTURE
PERSPECTIVE”
1 | P a g e
Name:
Student Number:
Word count:
Name of the course:
Tutor name:
“VEHICULAR AD-HOC NETWORK:
CURRENT CHALLENGES, AND FUTURE
PERSPECTIVE”
1 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

VEHICULA AD-HOC NETWORK
Abstract
Vehicular Ad-hoc Network (VANET) is considered as the subclass of the mobile ad hoc networks
(MANETs) and this is also considered as the promising approach in case of intelligent
transportation system (ITS). There is the design for the routing protocols in VANETs which is
very important as well as necessary issue to support the new smart technique ITS. There is the key
difference in between VANET as well as MANET which is the special mobility pattern as well as
it is designed based on rapidly changing topology. This technique is also not applied effectively
for occurrence of the routing protocols for MANETs within VANETs. This paper focuses on the
technology used in case of laden those multiple challenges which is needed for sorting out before
it is considered with possible implementation for the large range of scale. This study also assesses
the present challenges as well as the future perspectives that are associated with the vehicular Ad-
Hoc Network or simply VANET. It is also found through this research paper, some challenges are
going to be identified which is primarily depending on security attacks as well as network
management. Finally, there is a brief description on the issues for future research in the field of
VANET followed by a strong conclusion.
Keywords: Vehicular Ad hoc Networks or VANETs; Road side unit, On-board Unit; Black hole;
Wormhole etc.
2 | P a g e
Abstract
Vehicular Ad-hoc Network (VANET) is considered as the subclass of the mobile ad hoc networks
(MANETs) and this is also considered as the promising approach in case of intelligent
transportation system (ITS). There is the design for the routing protocols in VANETs which is
very important as well as necessary issue to support the new smart technique ITS. There is the key
difference in between VANET as well as MANET which is the special mobility pattern as well as
it is designed based on rapidly changing topology. This technique is also not applied effectively
for occurrence of the routing protocols for MANETs within VANETs. This paper focuses on the
technology used in case of laden those multiple challenges which is needed for sorting out before
it is considered with possible implementation for the large range of scale. This study also assesses
the present challenges as well as the future perspectives that are associated with the vehicular Ad-
Hoc Network or simply VANET. It is also found through this research paper, some challenges are
going to be identified which is primarily depending on security attacks as well as network
management. Finally, there is a brief description on the issues for future research in the field of
VANET followed by a strong conclusion.
Keywords: Vehicular Ad hoc Networks or VANETs; Road side unit, On-board Unit; Black hole;
Wormhole etc.
2 | P a g e

VEHICULA AD-HOC NETWORK
TABLE OF CONTENTS
Introduction........................................................................................................................................4
Background of the study....................................................................................................................4
Problem of the study..........................................................................................................................9
Possible security attacks.................................................................................................................9
Challenges in terms of network among vehicles.........................................................................14
Security Requirements.................................................................................................................15
Future research and Prospective......................................................................................................16
Conclusion.......................................................................................................................................17
Reference List..................................................................................................................................18
3 | P a g e
TABLE OF CONTENTS
Introduction........................................................................................................................................4
Background of the study....................................................................................................................4
Problem of the study..........................................................................................................................9
Possible security attacks.................................................................................................................9
Challenges in terms of network among vehicles.........................................................................14
Security Requirements.................................................................................................................15
Future research and Prospective......................................................................................................16
Conclusion.......................................................................................................................................17
Reference List..................................................................................................................................18
3 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

VEHICULA AD-HOC NETWORK
INTRODUCTION
This paper focuses on investigating various aspects that are associated with the vehicular ad-hoc
network for understanding the system to implement among general public. There is a brief
description of the structure or framework of VANET followed by the possible security attacks and
some challenges to regularize this technology among public transportation system. At the last
section there is a brief discussion of future aspects of VANETs in the field of research.
BACKGROUND OF THE STUDY
The Ad hoc network is considered as the distributed, temporary network system. For the formation
of ad hoc network there is a dynamic link consists of nodes is very much required. On the same
time, it does not rely upon the infrastructures with existing network, like gateway, router, or
regular power supply etc. There is the Ad hoc network which is the kind of peer to peer networks
and also there is other node which has functions for data collecting, storing, as well as processing
followed by forwarding. This solution is cost-effective in case of short-range communication for
some particular scenarios, like automation, environment sensing, or hazards preventive. To
improve these cases Vehicle Ad Hoc network has been introduced in recent years (Qiu, Chen, Li,
Qiao, & Fu, 2017).
There are more than 1 billion of active Android users as of June, 2014 and it is growing in
numbers day by day very rapidly. There are more than one million devices is being activated in
each day. For this dramatic growth in numbers, there are portable wireless devices which have a
huge market development in case of smart applications and these changes will interact with the
lifestyles of users and also provides the context-aware interactions. It has been observed that the
mobile games markets have been grown and it has crossed the target range $23 billion in 2016
(Ahmed, Pierre, & Quintero, 2017).
It is also observed that from the last five years, there are automakers who have adopted the
integration platforms with onboard devices as well as personal smartphone. Therefore, the
connection between consumer electronic devices, like smart phones as well as the onboard
vehicles has been reduced. Moreover, for multiple applications, the data makers are going for
VANET applications to target the consumer electronics.
The aim of VANET is to insure safe drive through improvement of the traffic flow as well as it is
expected for decreasing the car accidents with a great numbers. It has been also observed that the
users of VANET would get benefitted from active road safety, infotainment along with traffic
4 | P a g e
INTRODUCTION
This paper focuses on investigating various aspects that are associated with the vehicular ad-hoc
network for understanding the system to implement among general public. There is a brief
description of the structure or framework of VANET followed by the possible security attacks and
some challenges to regularize this technology among public transportation system. At the last
section there is a brief discussion of future aspects of VANETs in the field of research.
BACKGROUND OF THE STUDY
The Ad hoc network is considered as the distributed, temporary network system. For the formation
of ad hoc network there is a dynamic link consists of nodes is very much required. On the same
time, it does not rely upon the infrastructures with existing network, like gateway, router, or
regular power supply etc. There is the Ad hoc network which is the kind of peer to peer networks
and also there is other node which has functions for data collecting, storing, as well as processing
followed by forwarding. This solution is cost-effective in case of short-range communication for
some particular scenarios, like automation, environment sensing, or hazards preventive. To
improve these cases Vehicle Ad Hoc network has been introduced in recent years (Qiu, Chen, Li,
Qiao, & Fu, 2017).
There are more than 1 billion of active Android users as of June, 2014 and it is growing in
numbers day by day very rapidly. There are more than one million devices is being activated in
each day. For this dramatic growth in numbers, there are portable wireless devices which have a
huge market development in case of smart applications and these changes will interact with the
lifestyles of users and also provides the context-aware interactions. It has been observed that the
mobile games markets have been grown and it has crossed the target range $23 billion in 2016
(Ahmed, Pierre, & Quintero, 2017).
It is also observed that from the last five years, there are automakers who have adopted the
integration platforms with onboard devices as well as personal smartphone. Therefore, the
connection between consumer electronic devices, like smart phones as well as the onboard
vehicles has been reduced. Moreover, for multiple applications, the data makers are going for
VANET applications to target the consumer electronics.
The aim of VANET is to insure safe drive through improvement of the traffic flow as well as it is
expected for decreasing the car accidents with a great numbers. It has been also observed that the
users of VANET would get benefitted from active road safety, infotainment along with traffic
4 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
VEHICULA AD-HOC NETWORK
efficiency as well as management, especially in case of speed management and also co-operative
navigation (Hasrouny, Samhat, Bassil, & Laouiti, 2017).
As per the infrastructure concerned, VANET consists of two types of necessary units for the
communication, management as well as registrations. Those are Roadside units (RSUs) or On-
Board units (OBUs). In case of roadside units there are entities, like traffic lights. In case of On-
Board units, the infrastructure management centers are belonging to it, like traffic management
centers (TMCs) as well as the vehicle management centers (Liang, Li, Zhang, Wang, & Bie,
2015).
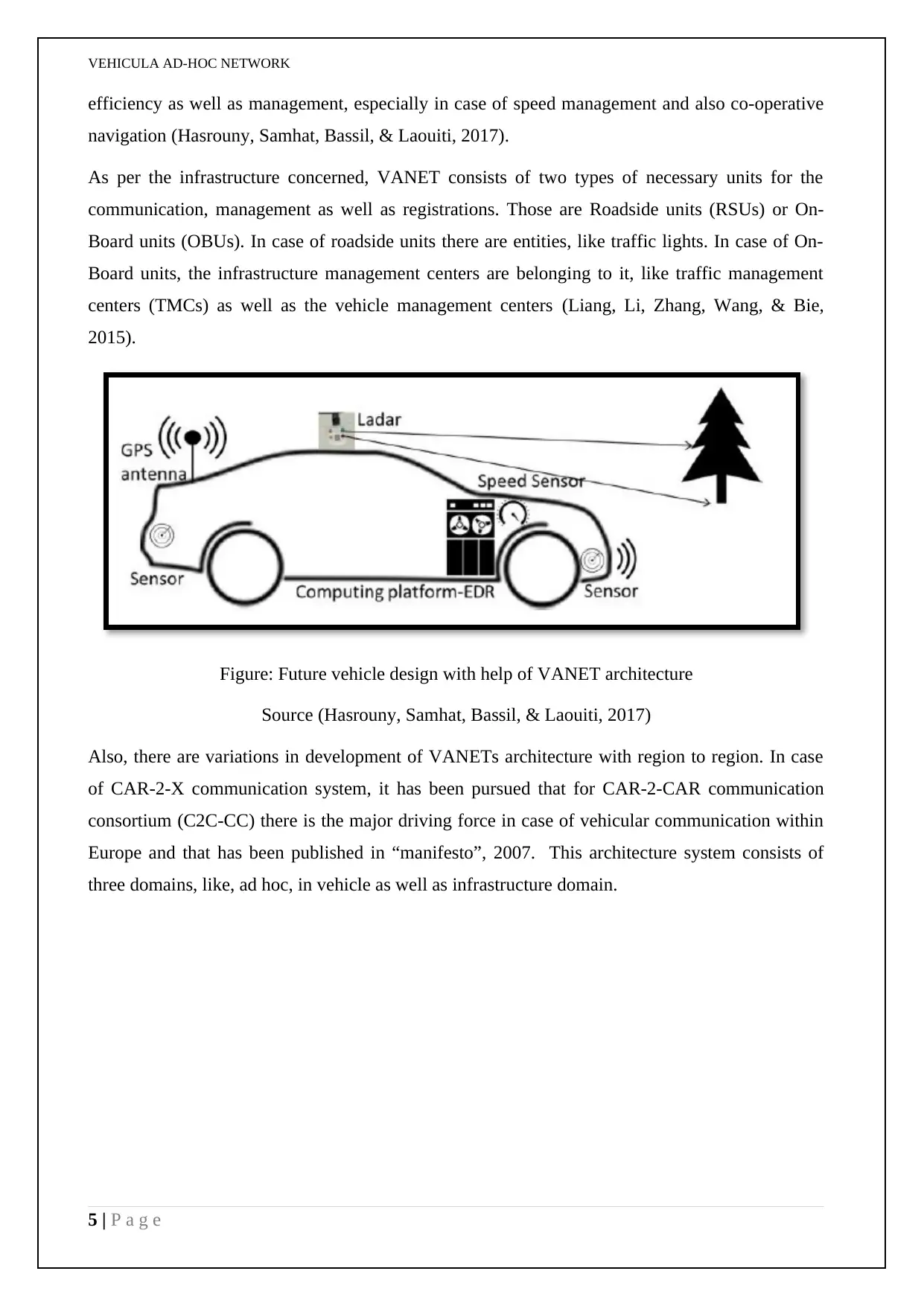
Figure: Future vehicle design with help of VANET architecture
Source (Hasrouny, Samhat, Bassil, & Laouiti, 2017)
Also, there are variations in development of VANETs architecture with region to region. In case
of CAR-2-X communication system, it has been pursued that for CAR-2-CAR communication
consortium (C2C-CC) there is the major driving force in case of vehicular communication within
Europe and that has been published in “manifesto”, 2007. This architecture system consists of
three domains, like, ad hoc, in vehicle as well as infrastructure domain.
5 | P a g e
efficiency as well as management, especially in case of speed management and also co-operative
navigation (Hasrouny, Samhat, Bassil, & Laouiti, 2017).
As per the infrastructure concerned, VANET consists of two types of necessary units for the
communication, management as well as registrations. Those are Roadside units (RSUs) or On-
Board units (OBUs). In case of roadside units there are entities, like traffic lights. In case of On-
Board units, the infrastructure management centers are belonging to it, like traffic management
centers (TMCs) as well as the vehicle management centers (Liang, Li, Zhang, Wang, & Bie,
2015).
Figure: Future vehicle design with help of VANET architecture
Source (Hasrouny, Samhat, Bassil, & Laouiti, 2017)
Also, there are variations in development of VANETs architecture with region to region. In case
of CAR-2-X communication system, it has been pursued that for CAR-2-CAR communication
consortium (C2C-CC) there is the major driving force in case of vehicular communication within
Europe and that has been published in “manifesto”, 2007. This architecture system consists of
three domains, like, ad hoc, in vehicle as well as infrastructure domain.
5 | P a g e
VEHICULA AD-HOC NETWORK
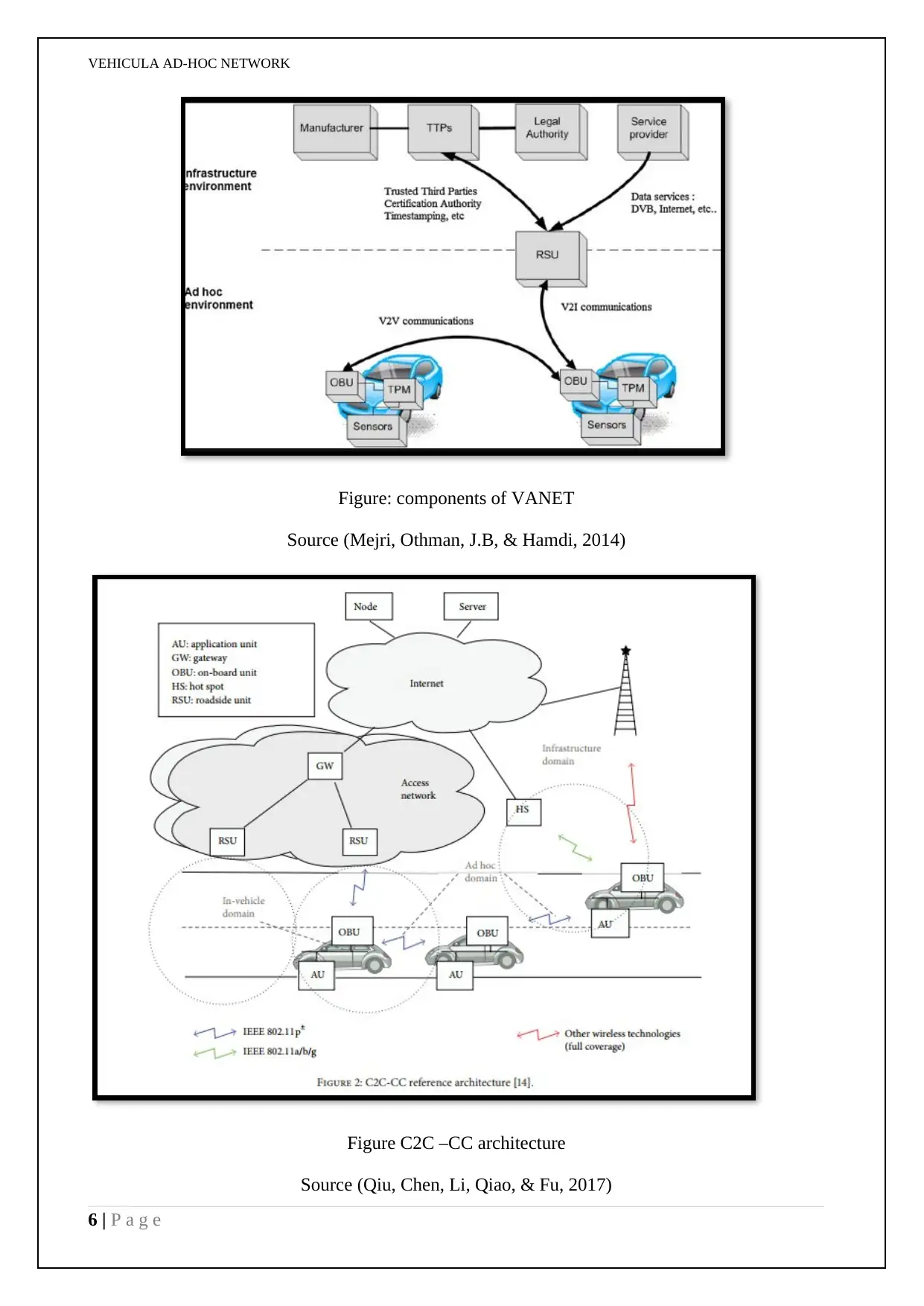
Figure: components of VANET
Source (Mejri, Othman, J.B, & Hamdi, 2014)
Figure C2C –CC architecture
Source (Qiu, Chen, Li, Qiao, & Fu, 2017)
6 | P a g e
Figure: components of VANET
Source (Mejri, Othman, J.B, & Hamdi, 2014)
Figure C2C –CC architecture
Source (Qiu, Chen, Li, Qiao, & Fu, 2017)
6 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

VEHICULA AD-HOC NETWORK
Further, in case of OBU unit as well as one or more application units (AUs) there are connections
between them which are usually wired with sometimes wireless. That ad hoc domain also found to
be composed of vehicles equipment arranged with OBUs as well as RSUs. That OBU is thereafter
has been found in case of mobile node for the ad hoc network. On the other hand, RSU is a static
node. That RSU will connect with Internet through the gateway and that RSUs will communicate
for each other through direct connection or through multihop in many cases. There are also two
types of infrastructure access of domain, like RSUs or hot spots (HSs). When these are not found,
OBUs will continue the communication through cellular radio networks, viz, UMTS, GSM, 4G,
GPRS, and WiMAX etc. (Liang, Li, Zhang, Wang, & Bie, 2015).
In case of Layered architecture model of VANETS, it has been found the application of open
systems interconnection model or OSI and that has been divided into sublayers depending on the
protocols. In US, there is the protocol stack consists of Dedicated Short-Range communication
(DSRC) system which is designed especially for automotive use. This corresponding set of
protocols as well as the standards has been allocated by US FCC with 75 MHz of spectrum in case
of DSRC communication. It has designed to get the communication in between 5.850 GHz to
5.925 GHz. There are also different protocols which are designed for using the various layers
some of them are used under active development.
7 | P a g e
Further, in case of OBU unit as well as one or more application units (AUs) there are connections
between them which are usually wired with sometimes wireless. That ad hoc domain also found to
be composed of vehicles equipment arranged with OBUs as well as RSUs. That OBU is thereafter
has been found in case of mobile node for the ad hoc network. On the other hand, RSU is a static
node. That RSU will connect with Internet through the gateway and that RSUs will communicate
for each other through direct connection or through multihop in many cases. There are also two
types of infrastructure access of domain, like RSUs or hot spots (HSs). When these are not found,
OBUs will continue the communication through cellular radio networks, viz, UMTS, GSM, 4G,
GPRS, and WiMAX etc. (Liang, Li, Zhang, Wang, & Bie, 2015).
In case of Layered architecture model of VANETS, it has been found the application of open
systems interconnection model or OSI and that has been divided into sublayers depending on the
protocols. In US, there is the protocol stack consists of Dedicated Short-Range communication
(DSRC) system which is designed especially for automotive use. This corresponding set of
protocols as well as the standards has been allocated by US FCC with 75 MHz of spectrum in case
of DSRC communication. It has designed to get the communication in between 5.850 GHz to
5.925 GHz. There are also different protocols which are designed for using the various layers
some of them are used under active development.
7 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
VEHICULA AD-HOC NETWORK
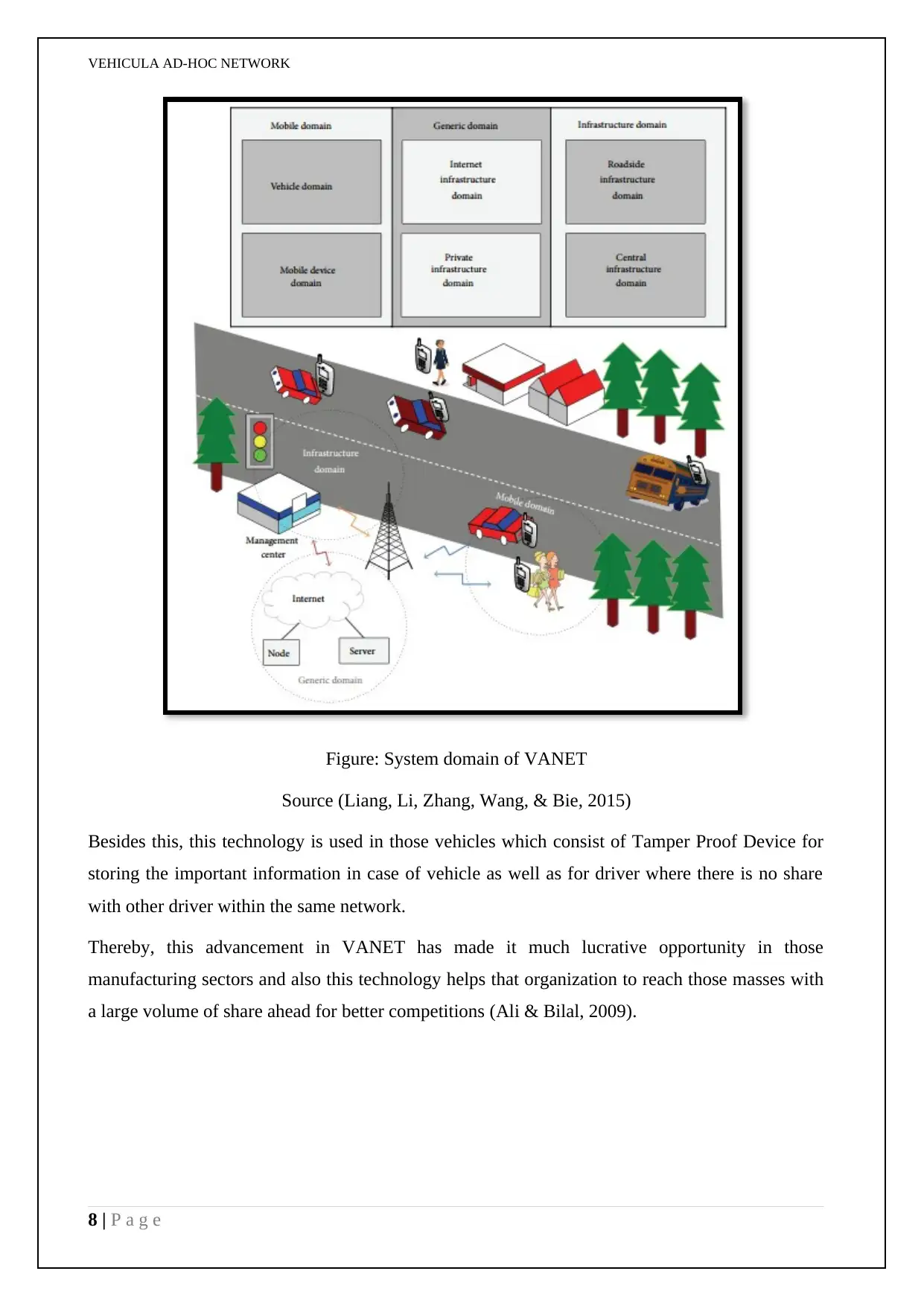
Figure: System domain of VANET
Source (Liang, Li, Zhang, Wang, & Bie, 2015)
Besides this, this technology is used in those vehicles which consist of Tamper Proof Device for
storing the important information in case of vehicle as well as for driver where there is no share
with other driver within the same network.
Thereby, this advancement in VANET has made it much lucrative opportunity in those
manufacturing sectors and also this technology helps that organization to reach those masses with
a large volume of share ahead for better competitions (Ali & Bilal, 2009).
8 | P a g e
Figure: System domain of VANET
Source (Liang, Li, Zhang, Wang, & Bie, 2015)
Besides this, this technology is used in those vehicles which consist of Tamper Proof Device for
storing the important information in case of vehicle as well as for driver where there is no share
with other driver within the same network.
Thereby, this advancement in VANET has made it much lucrative opportunity in those
manufacturing sectors and also this technology helps that organization to reach those masses with
a large volume of share ahead for better competitions (Ali & Bilal, 2009).
8 | P a g e

VEHICULA AD-HOC NETWORK
PROBLEM OF THE STUDY
In this study, it has given on the emphasis on understanding various types of cyber-security
challenges for preventing the system for going live in general public. It has been depended on
three types of scenarios of securities, like security attacks along with network challenges as well
as security requirements in case of VANET.
POSSIBLE SECURITY ATTACKS
To deal with the attacks against VANET, researchers has found some ways and classified them
into different categories as the threat to availability, threat to authenticity as well as the threat to
driver confidentiality and for other miscellaneous purpose. Researchers have classified these
attackers for three classes, like, Active vs. Passive along with Insider vs. Outsider or Malicious vs.
Rational. Moreover, various types of attack have been observed in case of VANET, like,
Application Attack (MA), Network Attack (NA), or Social Attack (SA) as well as Monitoring
Attack (MA) or Timing Attack (TA). There are also malicious classes of attacker, Pranksters or
Selfish Driver has been found simultaneously (Al-Raba'nah & Samara, 2015). Thus, under this
section, some of these attacks have been discussed as follows.
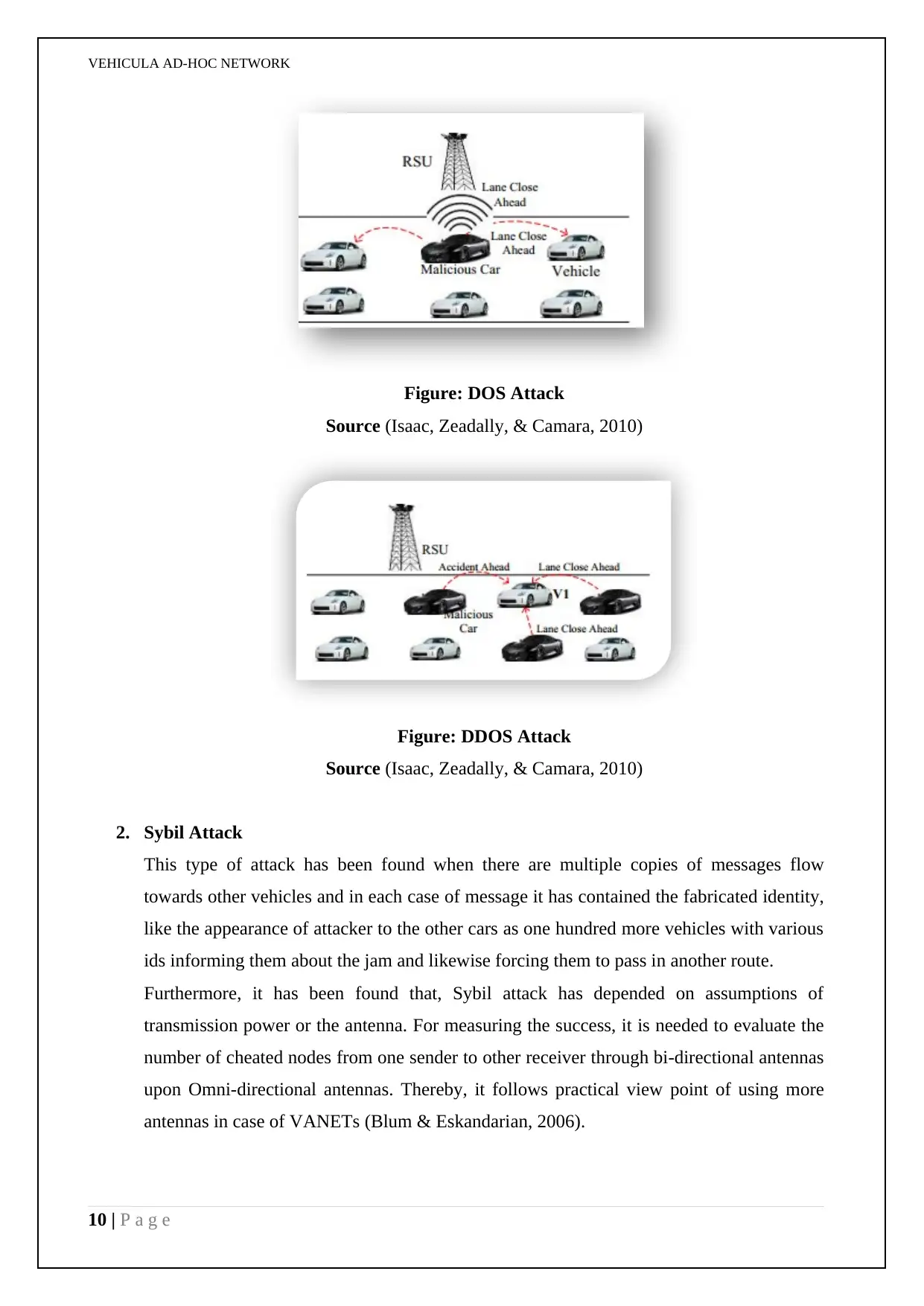
1. Denial of Service Attack
In this case attackers are found to transmit the dummy messages for the purpose of jam the
channel and that in turn will reduce the efficiency as well as the performance in the
network. The Distributed DoS (DDoS) attack is found to be more severe than the DoS and
in this case more number of malicious cars has been attacked through distributed manner
in various locations as well as the time slots. In these types of attacks the network is tried
to breakdown, prevent sending as well as receiving messages within network towards other
vehicles. Here, attacker first jams the communication channel along with makes some
exclusive control over vehicle’s resources. In case of VANET, this kind of attack has been
considered as one of most dangerous attacks where the vehicles could not access through
network or passing any information or messages towards other vehicles (Biswas,
Tatchikou, & Dion, 2006).
9 | P a g e
PROBLEM OF THE STUDY
In this study, it has given on the emphasis on understanding various types of cyber-security
challenges for preventing the system for going live in general public. It has been depended on
three types of scenarios of securities, like security attacks along with network challenges as well
as security requirements in case of VANET.
POSSIBLE SECURITY ATTACKS
To deal with the attacks against VANET, researchers has found some ways and classified them
into different categories as the threat to availability, threat to authenticity as well as the threat to
driver confidentiality and for other miscellaneous purpose. Researchers have classified these
attackers for three classes, like, Active vs. Passive along with Insider vs. Outsider or Malicious vs.
Rational. Moreover, various types of attack have been observed in case of VANET, like,
Application Attack (MA), Network Attack (NA), or Social Attack (SA) as well as Monitoring
Attack (MA) or Timing Attack (TA). There are also malicious classes of attacker, Pranksters or
Selfish Driver has been found simultaneously (Al-Raba'nah & Samara, 2015). Thus, under this
section, some of these attacks have been discussed as follows.
1. Denial of Service Attack
In this case attackers are found to transmit the dummy messages for the purpose of jam the
channel and that in turn will reduce the efficiency as well as the performance in the
network. The Distributed DoS (DDoS) attack is found to be more severe than the DoS and
in this case more number of malicious cars has been attacked through distributed manner
in various locations as well as the time slots. In these types of attacks the network is tried
to breakdown, prevent sending as well as receiving messages within network towards other
vehicles. Here, attacker first jams the communication channel along with makes some
exclusive control over vehicle’s resources. In case of VANET, this kind of attack has been
considered as one of most dangerous attacks where the vehicles could not access through
network or passing any information or messages towards other vehicles (Biswas,
Tatchikou, & Dion, 2006).
9 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
VEHICULA AD-HOC NETWORK
Figure: DOS Attack
Source (Isaac, Zeadally, & Camara, 2010)
Figure: DDOS Attack
Source (Isaac, Zeadally, & Camara, 2010)
2. Sybil Attack
This type of attack has been found when there are multiple copies of messages flow
towards other vehicles and in each case of message it has contained the fabricated identity,
like the appearance of attacker to the other cars as one hundred more vehicles with various
ids informing them about the jam and likewise forcing them to pass in another route.
Furthermore, it has been found that, Sybil attack has depended on assumptions of
transmission power or the antenna. For measuring the success, it is needed to evaluate the
number of cheated nodes from one sender to other receiver through bi-directional antennas
upon Omni-directional antennas. Thereby, it follows practical view point of using more
antennas in case of VANETs (Blum & Eskandarian, 2006).
10 | P a g e
Figure: DOS Attack
Source (Isaac, Zeadally, & Camara, 2010)
Figure: DDOS Attack
Source (Isaac, Zeadally, & Camara, 2010)
2. Sybil Attack
This type of attack has been found when there are multiple copies of messages flow
towards other vehicles and in each case of message it has contained the fabricated identity,
like the appearance of attacker to the other cars as one hundred more vehicles with various
ids informing them about the jam and likewise forcing them to pass in another route.
Furthermore, it has been found that, Sybil attack has depended on assumptions of
transmission power or the antenna. For measuring the success, it is needed to evaluate the
number of cheated nodes from one sender to other receiver through bi-directional antennas
upon Omni-directional antennas. Thereby, it follows practical view point of using more
antennas in case of VANETs (Blum & Eskandarian, 2006).
10 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
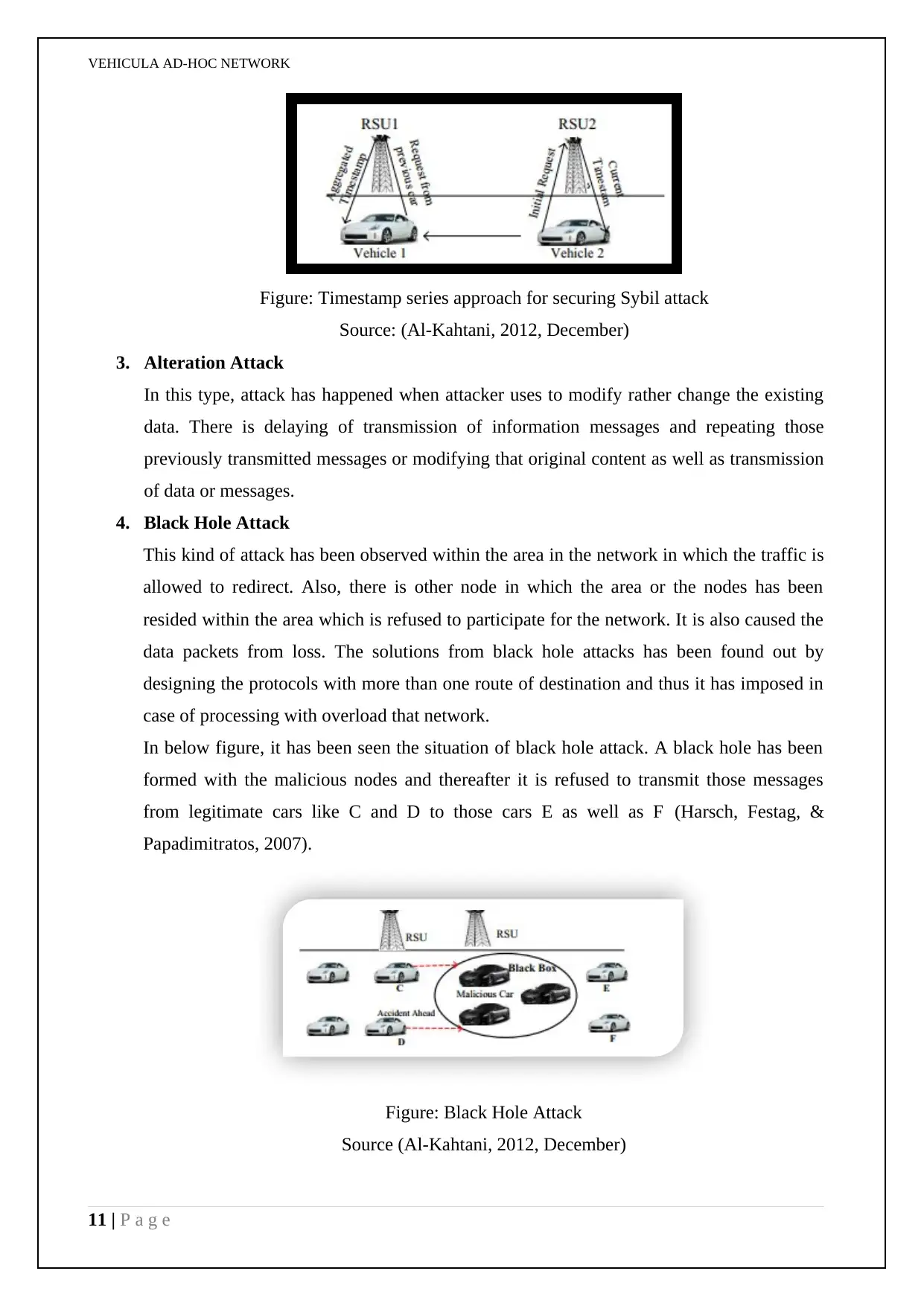
VEHICULA AD-HOC NETWORK
Figure: Timestamp series approach for securing Sybil attack
Source: (Al-Kahtani, 2012, December)
3. Alteration Attack
In this type, attack has happened when attacker uses to modify rather change the existing
data. There is delaying of transmission of information messages and repeating those
previously transmitted messages or modifying that original content as well as transmission
of data or messages.
4. Black Hole Attack
This kind of attack has been observed within the area in the network in which the traffic is
allowed to redirect. Also, there is other node in which the area or the nodes has been
resided within the area which is refused to participate for the network. It is also caused the
data packets from loss. The solutions from black hole attacks has been found out by
designing the protocols with more than one route of destination and thus it has imposed in
case of processing with overload that network.
In below figure, it has been seen the situation of black hole attack. A black hole has been
formed with the malicious nodes and thereafter it is refused to transmit those messages
from legitimate cars like C and D to those cars E as well as F (Harsch, Festag, &
Papadimitratos, 2007).
Figure: Black Hole Attack
Source (Al-Kahtani, 2012, December)
11 | P a g e
Figure: Timestamp series approach for securing Sybil attack
Source: (Al-Kahtani, 2012, December)
3. Alteration Attack
In this type, attack has happened when attacker uses to modify rather change the existing
data. There is delaying of transmission of information messages and repeating those
previously transmitted messages or modifying that original content as well as transmission
of data or messages.
4. Black Hole Attack
This kind of attack has been observed within the area in the network in which the traffic is
allowed to redirect. Also, there is other node in which the area or the nodes has been
resided within the area which is refused to participate for the network. It is also caused the
data packets from loss. The solutions from black hole attacks has been found out by
designing the protocols with more than one route of destination and thus it has imposed in
case of processing with overload that network.
In below figure, it has been seen the situation of black hole attack. A black hole has been
formed with the malicious nodes and thereafter it is refused to transmit those messages
from legitimate cars like C and D to those cars E as well as F (Harsch, Festag, &
Papadimitratos, 2007).
Figure: Black Hole Attack
Source (Al-Kahtani, 2012, December)
11 | P a g e
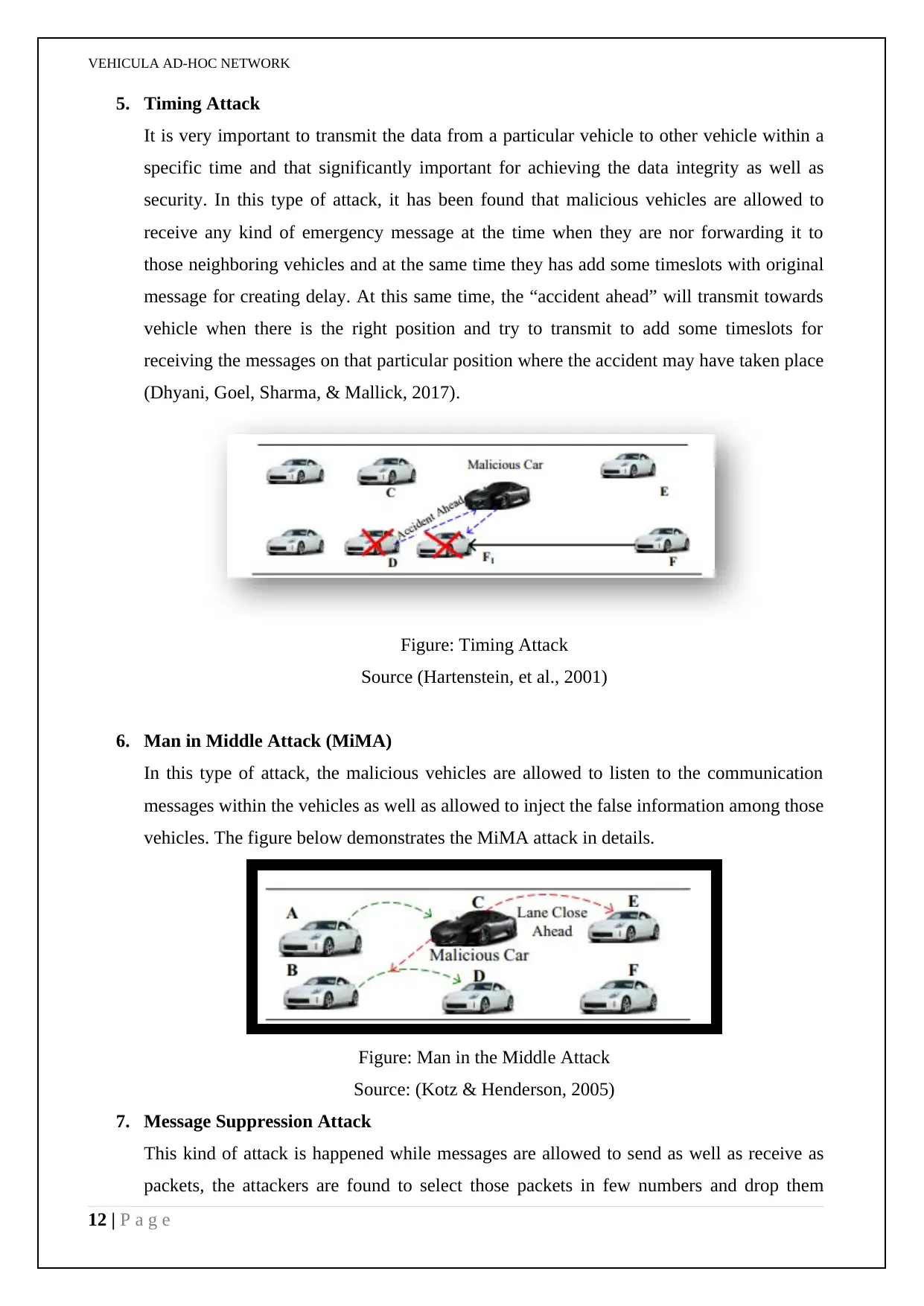
VEHICULA AD-HOC NETWORK
5. Timing Attack
It is very important to transmit the data from a particular vehicle to other vehicle within a
specific time and that significantly important for achieving the data integrity as well as
security. In this type of attack, it has been found that malicious vehicles are allowed to
receive any kind of emergency message at the time when they are nor forwarding it to
those neighboring vehicles and at the same time they has add some timeslots with original
message for creating delay. At this same time, the “accident ahead” will transmit towards
vehicle when there is the right position and try to transmit to add some timeslots for
receiving the messages on that particular position where the accident may have taken place
(Dhyani, Goel, Sharma, & Mallick, 2017).
Figure: Timing Attack
Source (Hartenstein, et al., 2001)
6. Man in Middle Attack (MiMA)
In this type of attack, the malicious vehicles are allowed to listen to the communication
messages within the vehicles as well as allowed to inject the false information among those
vehicles. The figure below demonstrates the MiMA attack in details.
Figure: Man in the Middle Attack
Source: (Kotz & Henderson, 2005)
7. Message Suppression Attack
This kind of attack is happened while messages are allowed to send as well as receive as
packets, the attackers are found to select those packets in few numbers and drop them
12 | P a g e
5. Timing Attack
It is very important to transmit the data from a particular vehicle to other vehicle within a
specific time and that significantly important for achieving the data integrity as well as
security. In this type of attack, it has been found that malicious vehicles are allowed to
receive any kind of emergency message at the time when they are nor forwarding it to
those neighboring vehicles and at the same time they has add some timeslots with original
message for creating delay. At this same time, the “accident ahead” will transmit towards
vehicle when there is the right position and try to transmit to add some timeslots for
receiving the messages on that particular position where the accident may have taken place
(Dhyani, Goel, Sharma, & Mallick, 2017).
Figure: Timing Attack
Source (Hartenstein, et al., 2001)
6. Man in Middle Attack (MiMA)
In this type of attack, the malicious vehicles are allowed to listen to the communication
messages within the vehicles as well as allowed to inject the false information among those
vehicles. The figure below demonstrates the MiMA attack in details.
Figure: Man in the Middle Attack
Source: (Kotz & Henderson, 2005)
7. Message Suppression Attack
This kind of attack is happened while messages are allowed to send as well as receive as
packets, the attackers are found to select those packets in few numbers and drop them
12 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





