IT Security: Vulnerability Testing using NMap Tool
VerifiedAdded on 2023/04/23
|10
|1948
|80
AI Summary
This report discusses vulnerability testing using the NMap tool, which is a powerful tool for penetration testing. It covers the features of the tool, techniques used to exploit vulnerabilities, and evidence of usage of the tool. The report also includes an experimental setup and conclusions.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: IT SECURITY
IT Security
Name of the Student:
Name of the University:
Author Note
IT Security
Name of the Student:
Name of the University:
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
IT SECURITY
Introduction of the tool
The most powerful tool in the world for performing the penetration testing is Kali
Linux. The tool is also a very efficient testing platform that is used by the security personnel
at every organization. The tool is also used for a wide range of specialization, involving the
testing, reverse engineering, vulnerability testing and forensics for the system. This report is
concerned with vulnerability testing using the NMap Tool.
The Kali Linux tool has not only been built for being a collection of simple tools but
also a flexible framework that would be helpful for the professionals involved in penetration
testing and security enthusiast. The amateurs and the students involved in the field of
networking also would be able to customize the tool that would be able to fulfil their specific
needs.
Nmap is one of the tools in Kali Linux which helps the vulnerability tester with the
testing process and the performs all the vulnerability procedures. It is an open source and free
security scanning software that helps in detecting the hosts and the services that are currently
used in the network. This helps in development of a map for a network that is being
concerned for users. The software that would be helpful in probing computer networks
provides a number of features and it includes an operating system detection and host
discovery services. Advance services, vulnerability detection and other features are also
included for this software.
Features of the tool
The features of the Nmap tools involves the following functions:
IT SECURITY
Introduction of the tool
The most powerful tool in the world for performing the penetration testing is Kali
Linux. The tool is also a very efficient testing platform that is used by the security personnel
at every organization. The tool is also used for a wide range of specialization, involving the
testing, reverse engineering, vulnerability testing and forensics for the system. This report is
concerned with vulnerability testing using the NMap Tool.
The Kali Linux tool has not only been built for being a collection of simple tools but
also a flexible framework that would be helpful for the professionals involved in penetration
testing and security enthusiast. The amateurs and the students involved in the field of
networking also would be able to customize the tool that would be able to fulfil their specific
needs.
Nmap is one of the tools in Kali Linux which helps the vulnerability tester with the
testing process and the performs all the vulnerability procedures. It is an open source and free
security scanning software that helps in detecting the hosts and the services that are currently
used in the network. This helps in development of a map for a network that is being
concerned for users. The software that would be helpful in probing computer networks
provides a number of features and it includes an operating system detection and host
discovery services. Advance services, vulnerability detection and other features are also
included for this software.
Features of the tool
The features of the Nmap tools involves the following functions:

2
IT SECURITY
Host discovery – The tool can be used for the identification of the hosts on a network.
They help in listing all the hosts that provides a response to the ICMP and TCP/IP
request and have any particular open ports.
The tool also helps in the identification of the opens ports for the host, which has been
targeted for vulnerability detection.
Port Scanning – The tools helps the security personnel to enumerate the open port on
the target hosts.
Version detection – The names of the applications and the version information can be
fetched by interrogating the network services of the devices, which work remotely
with the help of the Nmap tool.
Security Audits can be performed for any type of networking peripheral with the help
of the Nmap tool. The connections and the hotspots for the connection to the
peripherals in the network.
Network inventory monitoring, network management, network maintenance and
management of the network assets are done with the help of this tool.
The tool very easily identifies the vulnerabilities and the factors, which can be
exploited in the network.
The tool helps to generate the traffic for the host on the network, and helps in
performing the time management response and response analysis.
Operating system detection – The determination of operating system for a network
and also detect the hardware that are being used in the network currently.
Nmap also helps in using the scripting engines provided by Nmap and programming
language named Lua.
IT SECURITY
Host discovery – The tool can be used for the identification of the hosts on a network.
They help in listing all the hosts that provides a response to the ICMP and TCP/IP
request and have any particular open ports.
The tool also helps in the identification of the opens ports for the host, which has been
targeted for vulnerability detection.
Port Scanning – The tools helps the security personnel to enumerate the open port on
the target hosts.
Version detection – The names of the applications and the version information can be
fetched by interrogating the network services of the devices, which work remotely
with the help of the Nmap tool.
Security Audits can be performed for any type of networking peripheral with the help
of the Nmap tool. The connections and the hotspots for the connection to the
peripherals in the network.
Network inventory monitoring, network management, network maintenance and
management of the network assets are done with the help of this tool.
The tool very easily identifies the vulnerabilities and the factors, which can be
exploited in the network.
The tool helps to generate the traffic for the host on the network, and helps in
performing the time management response and response analysis.
Operating system detection – The determination of operating system for a network
and also detect the hardware that are being used in the network currently.
Nmap also helps in using the scripting engines provided by Nmap and programming
language named Lua.

3
IT SECURITY
Techniques used by the tool to exploit vulnerabilities of information
systems
The technique involved in using the Nmap tool for the vulnerabilities detection is
described below:
Step 1: Reconnaissance
This is the first step and in this step firstly information gained is matched and more
information is fetched from the targeted system. Different type of tools are used for gathering
the information. After the information have been obtained, it is broken down into several
steps firstly locating the range of the network, secondly discovering the ports and thirdly
detecting the access points to the system. The identification of the services and the ports and
lastly the network is mapped accordingly. The NSlooup, Whois tools can be used for the
information gathering process.
Step 2: Scanning
The second step involves the scanning process that would detect the systems, which
are online by scanning the network, and evaluation of the IP addresses in the network. There
are a variety of tool, which are available for scanning and gathering the information of the
port. The port address and the IP address can be fetched by performing this method.
Step 3: Gaining Access
The third step involves gaining access to the system from the scanning phase. The
passwords instilled into the system would be cracked by using brute force attacks. This would
provide the access to the password of the directory files. Additional tools such as key loggers
and the spywares can be used.
IT SECURITY
Techniques used by the tool to exploit vulnerabilities of information
systems
The technique involved in using the Nmap tool for the vulnerabilities detection is
described below:
Step 1: Reconnaissance
This is the first step and in this step firstly information gained is matched and more
information is fetched from the targeted system. Different type of tools are used for gathering
the information. After the information have been obtained, it is broken down into several
steps firstly locating the range of the network, secondly discovering the ports and thirdly
detecting the access points to the system. The identification of the services and the ports and
lastly the network is mapped accordingly. The NSlooup, Whois tools can be used for the
information gathering process.
Step 2: Scanning
The second step involves the scanning process that would detect the systems, which
are online by scanning the network, and evaluation of the IP addresses in the network. There
are a variety of tool, which are available for scanning and gathering the information of the
port. The port address and the IP address can be fetched by performing this method.
Step 3: Gaining Access
The third step involves gaining access to the system from the scanning phase. The
passwords instilled into the system would be cracked by using brute force attacks. This would
provide the access to the password of the directory files. Additional tools such as key loggers
and the spywares can be used.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
IT SECURITY
Step 4: Maintaining Access
The fourth step involves maintaining the access to the identified target and hence the
hackers create backdoors so that the access to the system is also maintained and the different
type of programs that are to be installed in the target machine that would be helpful in the
gathering the data which is confidential for the system. This would also help the attacker in
controlling the system largely. For hiding the utilities for the system, the rootkit can be used
and hacker’s main aim is thus accessing the rootkit. The rootkit is installed in the kernel
mode device driver_root_sys, which contains a program along with it known as
DEPLOY.EXE. This is used for running the rootkit files in the system. The program is used
for hiding the files for the list of directory.
Step 5: Clearing the Tracks
The last step involves the track clearing process on a targeted machine by the hacker.
The hacker does this so that the activity of the hacker in the system cannot be tracked. This
might fool the administrator and the hacker can thus access the system for a longer period of
time. The log files are to be deleted from the system and tunnelling protocol or the log file
alteration process is performed.
Experimental setup and evidence of usage of the tool
At first the nmap command is tested on the system
Commands used for checking nmap on the system:
root@kali:~# nmap
Output
IT SECURITY
Step 4: Maintaining Access
The fourth step involves maintaining the access to the identified target and hence the
hackers create backdoors so that the access to the system is also maintained and the different
type of programs that are to be installed in the target machine that would be helpful in the
gathering the data which is confidential for the system. This would also help the attacker in
controlling the system largely. For hiding the utilities for the system, the rootkit can be used
and hacker’s main aim is thus accessing the rootkit. The rootkit is installed in the kernel
mode device driver_root_sys, which contains a program along with it known as
DEPLOY.EXE. This is used for running the rootkit files in the system. The program is used
for hiding the files for the list of directory.
Step 5: Clearing the Tracks
The last step involves the track clearing process on a targeted machine by the hacker.
The hacker does this so that the activity of the hacker in the system cannot be tracked. This
might fool the administrator and the hacker can thus access the system for a longer period of
time. The log files are to be deleted from the system and tunnelling protocol or the log file
alteration process is performed.
Experimental setup and evidence of usage of the tool
At first the nmap command is tested on the system
Commands used for checking nmap on the system:
root@kali:~# nmap
Output

5
IT SECURITY
The output shows that Nmap has been installed successfully into the system and the
different options available with the Nmap tool for scanning the host has been displayed.
There are various options with Nmap available such as os detection done by the command
nmap –A. In addition to this there are other commands which provide various other results.
For scanning targets from a text file the nmap -iL list-of-ips.txt command is used.
Additionally, the for scanning a single port nmap –p is required and for scanning all the ports
of a single host the command namp –p- is used. nmap –sT is used for scaning using the TCP
connections. In addition to this, nmap is used for gather information about all the hosts
which are open in the system. The privilege that has been acquired using yhe Namp scan is
used for the SYN scans. TCP connect scans can be used if the provilegde offered seems in
sufficient. Therefore a TCP connection would be established however the scanning process
would be much slower.
IT SECURITY
The output shows that Nmap has been installed successfully into the system and the
different options available with the Nmap tool for scanning the host has been displayed.
There are various options with Nmap available such as os detection done by the command
nmap –A. In addition to this there are other commands which provide various other results.
For scanning targets from a text file the nmap -iL list-of-ips.txt command is used.
Additionally, the for scanning a single port nmap –p is required and for scanning all the ports
of a single host the command namp –p- is used. nmap –sT is used for scaning using the TCP
connections. In addition to this, nmap is used for gather information about all the hosts
which are open in the system. The privilege that has been acquired using yhe Namp scan is
used for the SYN scans. TCP connect scans can be used if the provilegde offered seems in
sufficient. Therefore a TCP connection would be established however the scanning process
would be much slower.

6
IT SECURITY
Commands used for checking the configurations of the network:
root@kali:~# ifconfig
Output
The ifconfig command is at first used for gathering the information about the subnet
of the network the attack machine is selected. This would help the attacker in gathering the
information about the subnet in which he should look for the desired host for attacking in the
target system. The command helps in minimizing the number of machines the attacker is
required to attack, so that the attack process is accelerated largely. This would also reduce the
time for scanning and provide more time for the brute force trails.
Command used for scanning the active hosts in the system:
root@kali:~# nmap -sP 192.168.255.0/24
IT SECURITY
Commands used for checking the configurations of the network:
root@kali:~# ifconfig
Output
The ifconfig command is at first used for gathering the information about the subnet
of the network the attack machine is selected. This would help the attacker in gathering the
information about the subnet in which he should look for the desired host for attacking in the
target system. The command helps in minimizing the number of machines the attacker is
required to attack, so that the attack process is accelerated largely. This would also reduce the
time for scanning and provide more time for the brute force trails.
Command used for scanning the active hosts in the system:
root@kali:~# nmap -sP 192.168.255.0/24
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT SECURITY
Output
The command helps in identifying the hosts in the network that would be up for
scanning by the tool. The subnet used for the identification of the host in the network is
192.168.255.0/24. The rslut shows that the identified hosts are 192.168.255.2,
192.168.255.132 and 192.168.255.254. Hence one of these hosts are to be targeted.
Command used for scaning the operating system of the targeted host
root@kali:~# root@kali:~# nmap -A 192.168.255.2
Output
IT SECURITY
Output
The command helps in identifying the hosts in the network that would be up for
scanning by the tool. The subnet used for the identification of the host in the network is
192.168.255.0/24. The rslut shows that the identified hosts are 192.168.255.2,
192.168.255.132 and 192.168.255.254. Hence one of these hosts are to be targeted.
Command used for scaning the operating system of the targeted host
root@kali:~# root@kali:~# nmap -A 192.168.255.2
Output
8
IT SECURITY
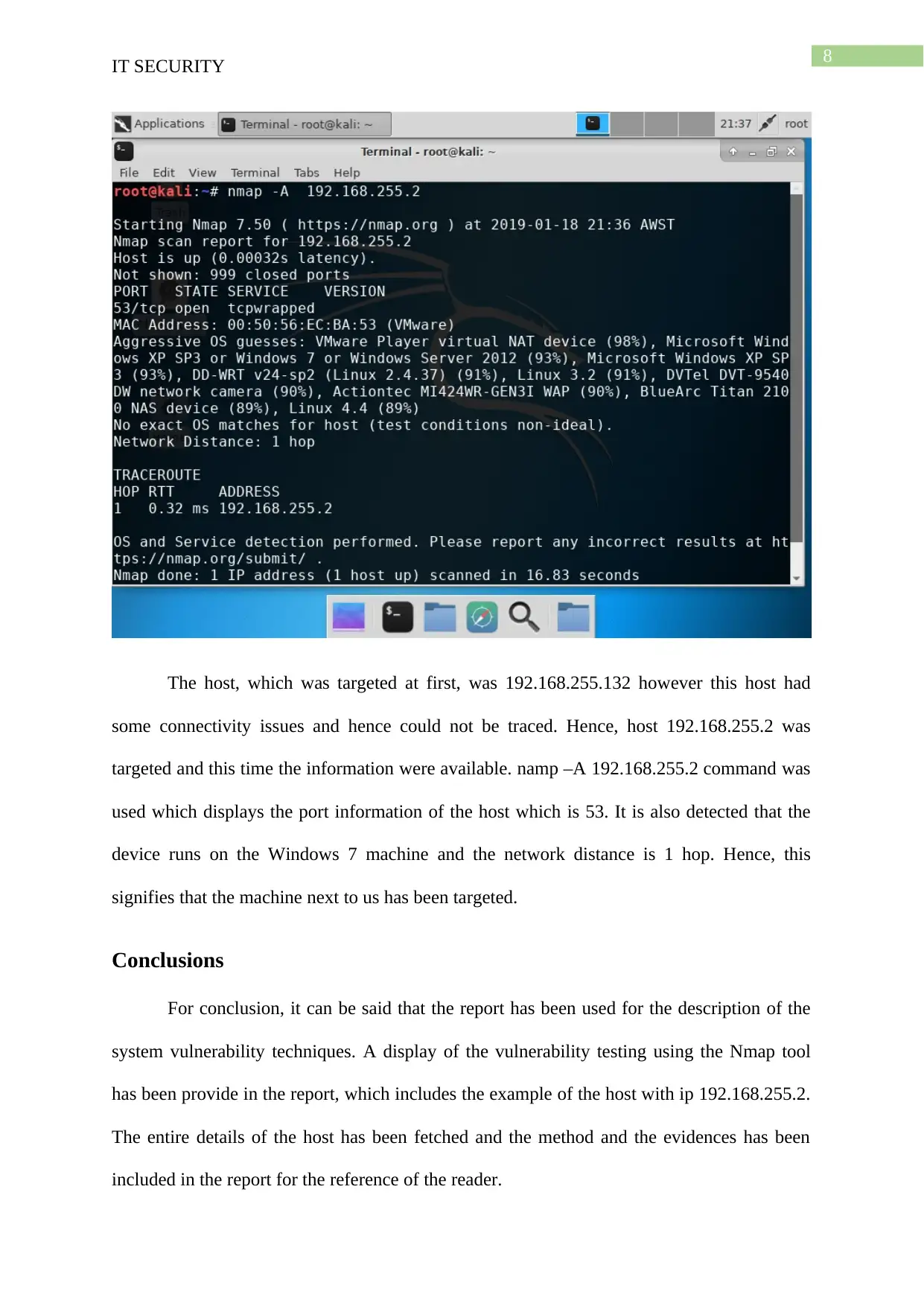
The host, which was targeted at first, was 192.168.255.132 however this host had
some connectivity issues and hence could not be traced. Hence, host 192.168.255.2 was
targeted and this time the information were available. namp –A 192.168.255.2 command was
used which displays the port information of the host which is 53. It is also detected that the
device runs on the Windows 7 machine and the network distance is 1 hop. Hence, this
signifies that the machine next to us has been targeted.
Conclusions
For conclusion, it can be said that the report has been used for the description of the
system vulnerability techniques. A display of the vulnerability testing using the Nmap tool
has been provide in the report, which includes the example of the host with ip 192.168.255.2.
The entire details of the host has been fetched and the method and the evidences has been
included in the report for the reference of the reader.
IT SECURITY
The host, which was targeted at first, was 192.168.255.132 however this host had
some connectivity issues and hence could not be traced. Hence, host 192.168.255.2 was
targeted and this time the information were available. namp –A 192.168.255.2 command was
used which displays the port information of the host which is 53. It is also detected that the
device runs on the Windows 7 machine and the network distance is 1 hop. Hence, this
signifies that the machine next to us has been targeted.
Conclusions
For conclusion, it can be said that the report has been used for the description of the
system vulnerability techniques. A display of the vulnerability testing using the Nmap tool
has been provide in the report, which includes the example of the host with ip 192.168.255.2.
The entire details of the host has been fetched and the method and the evidences has been
included in the report for the reference of the reader.

9
IT SECURITY
Bibliography
[1] Perlman, Radia, Charlie Kaufman, and Mike Speciner. Network security: private
communication in a public world. Pearson Education India, 2016.
[2] Chen, Gaojie, et al. "Physical layer network security in the full-duplex relay system."
IEEE transactions on information forensics and security 10.3 (2015): 574-583.
[3] Yu, Tianlong, et al. "Handling a trillion (unfixable) flaws on a billion devices: Rethinking
network security for the internet-of-things." Proceedings of the 14th ACM Workshop on Hot
Topics in Networks. ACM, 2015.
[4] Lopez, D., et al. Framework for interface to network security functions. No. RFC 8329.
2018.
[5] Zheng, Shiyong, Zhao Li, and Biqing Li. "Campus Network Security Defense Strategy."
2017 International Conference on Mechanical, Electronic, Control and Automation
Engineering (MECAE 2017). Atlantis Press, 2017.
[6] Yang, Nan, et al. "Safeguarding 5G wireless communication networks using physical
layer security." IEEE Communications Magazine 53.4 (2015): 20-27.
[7] Xu, Guangquan, et al. "Network security situation awareness based on semantic ontology
and user-defined rules for Internet of Things." IEEE Access 5 (2017): 21046-21056.
IT SECURITY
Bibliography
[1] Perlman, Radia, Charlie Kaufman, and Mike Speciner. Network security: private
communication in a public world. Pearson Education India, 2016.
[2] Chen, Gaojie, et al. "Physical layer network security in the full-duplex relay system."
IEEE transactions on information forensics and security 10.3 (2015): 574-583.
[3] Yu, Tianlong, et al. "Handling a trillion (unfixable) flaws on a billion devices: Rethinking
network security for the internet-of-things." Proceedings of the 14th ACM Workshop on Hot
Topics in Networks. ACM, 2015.
[4] Lopez, D., et al. Framework for interface to network security functions. No. RFC 8329.
2018.
[5] Zheng, Shiyong, Zhao Li, and Biqing Li. "Campus Network Security Defense Strategy."
2017 International Conference on Mechanical, Electronic, Control and Automation
Engineering (MECAE 2017). Atlantis Press, 2017.
[6] Yang, Nan, et al. "Safeguarding 5G wireless communication networks using physical
layer security." IEEE Communications Magazine 53.4 (2015): 20-27.
[7] Xu, Guangquan, et al. "Network security situation awareness based on semantic ontology
and user-defined rules for Internet of Things." IEEE Access 5 (2017): 21046-21056.
1 out of 10
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)





