Understanding Symmetric and Asymmetric Encryption
VerifiedAdded on 2020/10/09
|5
|884
|175
AI Summary
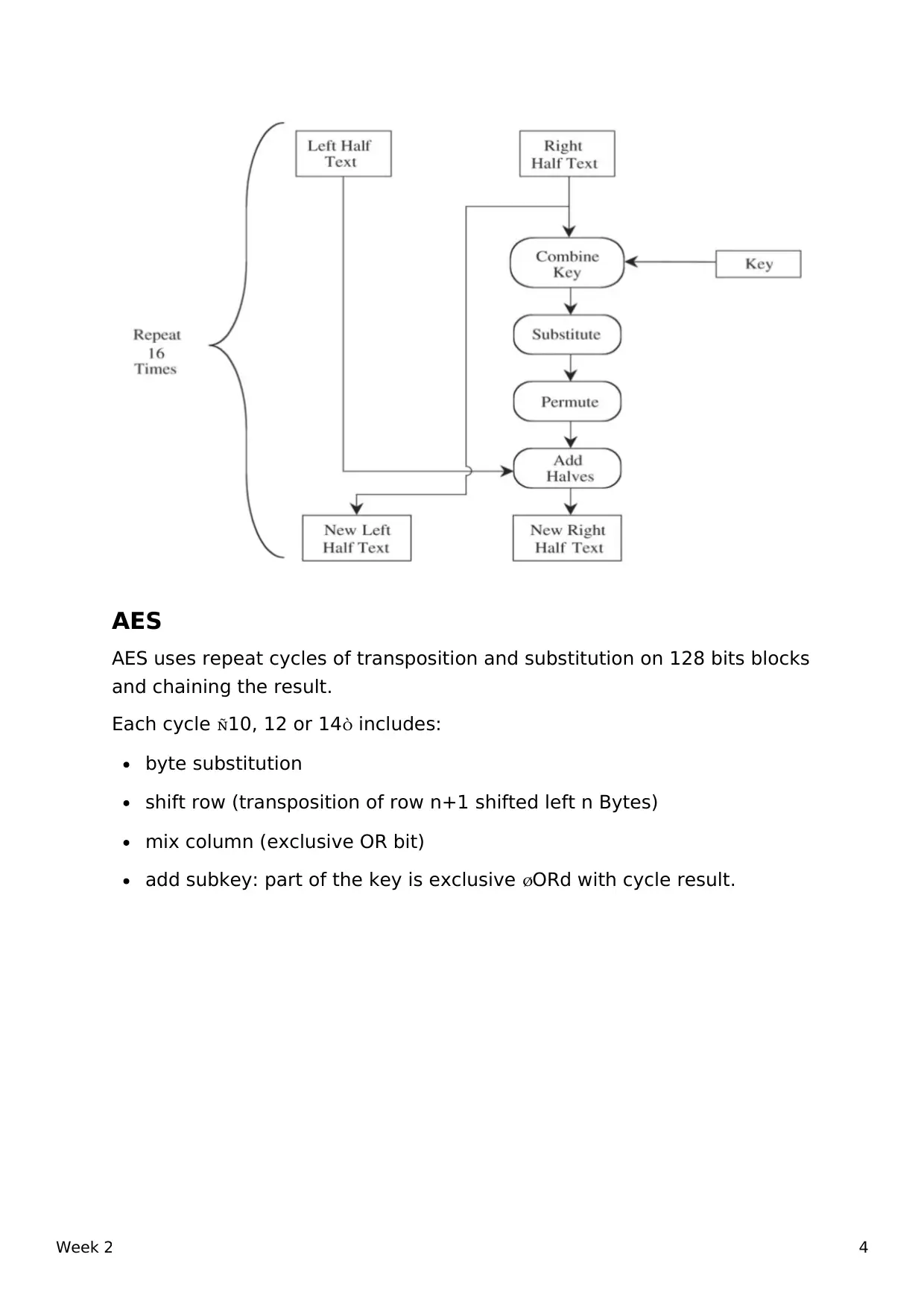
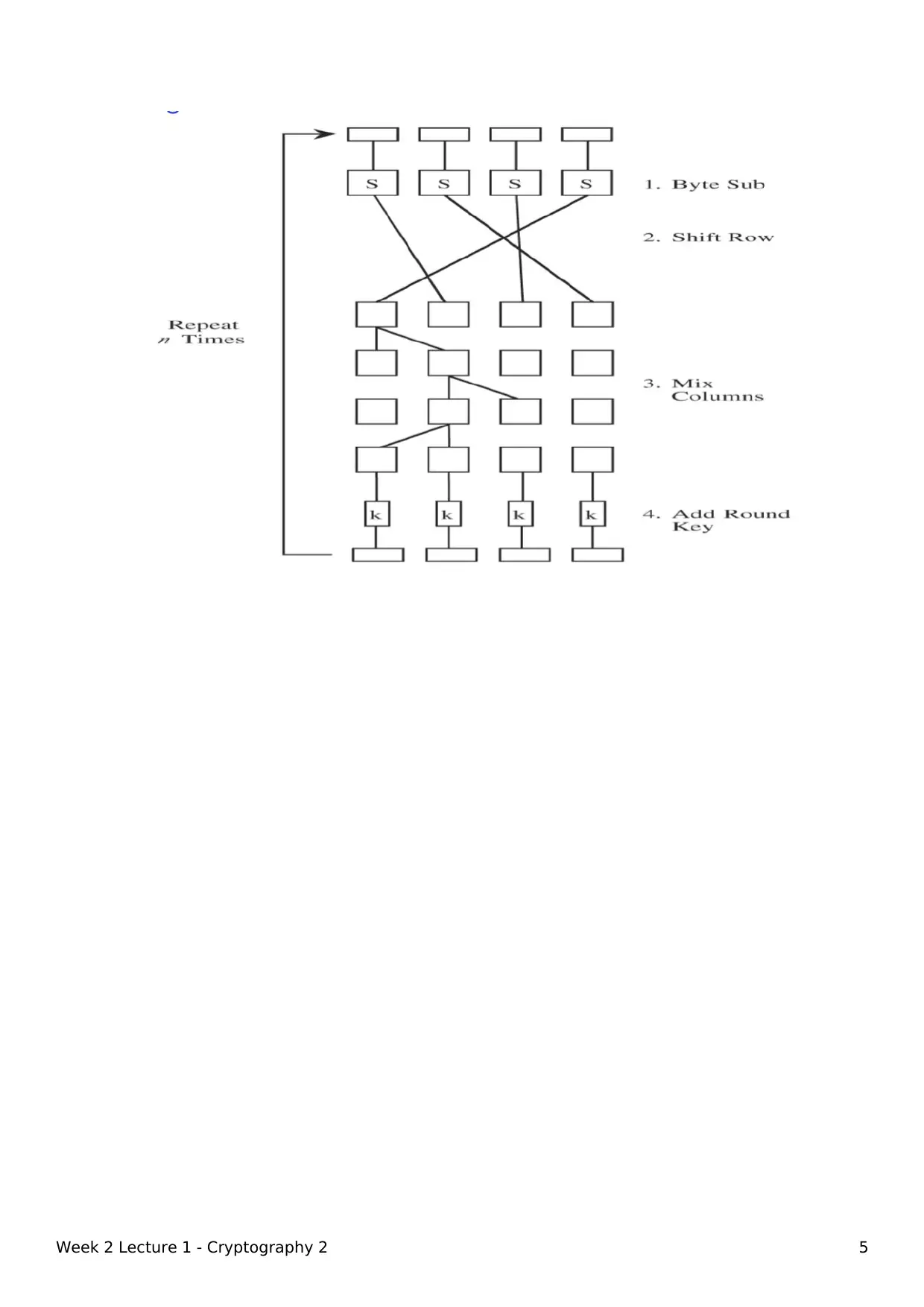
This document covers the concepts of symmetric encryption, asymmetric encryption, Diffie-Hellman Key Exchange, RSA, and commercial-grade encryption algorithms. It explains how symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption uses a public key for encryption and a private key for decryption. The document also discusses the principles of Confusion and Diffusion, and provides an overview of stream ciphers, block ciphers, and specific algorithms like DES and AES.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
1 out of 5









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)