Bell Studio: Report on Organizational Weaknesses, Risks, and Processes
VerifiedAdded on 2023/01/05
|13
|2691
|52
Report
AI Summary
This report provides a comprehensive analysis of Bell Studio's organizational weaknesses, focusing on the payroll, cash disbursement, and purchasing systems. It includes detailed data flow diagrams for the payroll, purchases, and cash disbursement processes, along with system flowcharts for each system. The report identifies key weaknesses within the organization, such as vulnerabilities in unsecured computer terminals and database security, and discusses associated risks, including sniffing attacks, unauthorized access, and potential data breaches. The report concludes with a summary of the findings and recommendations for improving the organization's security and operational efficiency. This report is contributed by a student to be published on the website Desklib. Desklib is a platform which provides all the necessary AI based study tools for students.

Running head: BELL STUDIO
BELL STUDIO
Name of student
Name of university
Author’s note:
BELL STUDIO
Name of student
Name of university
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
BELL STUDIO
Table of Contents
Introduction........................................................................................................2
Discussion..........................................................................................................3
Data flow diagram of payroll system..............................................................3
Data flow diagram of purchases and cash disbursements systems..............4
System flowchart of cash disbursements system..........................................5
System flowchart of payroll system................................................................6
System flowchart of purchases system.........................................................7
Weakness of the organisation........................................................................7
Risks connected with the organisation..........................................................8
Conclusion.........................................................................................................9
Bibliography.....................................................................................................11
BELL STUDIO
Table of Contents
Introduction........................................................................................................2
Discussion..........................................................................................................3
Data flow diagram of payroll system..............................................................3
Data flow diagram of purchases and cash disbursements systems..............4
System flowchart of cash disbursements system..........................................5
System flowchart of payroll system................................................................6
System flowchart of purchases system.........................................................7
Weakness of the organisation........................................................................7
Risks connected with the organisation..........................................................8
Conclusion.........................................................................................................9
Bibliography.....................................................................................................11

2
BELL STUDIO
Introduction
In the recent times, the organisation Bell studio has been facing several
problems in the business that are required to be analysed and corrected. This report
provides the clear discussion of the Bell studio organisation and provide the detailed
analysis of the organisation. The risks that are associated with the weaknesses of
the organisation are detailed in this report along with the detailed analysis of the
weaknesses of the organisation. The detailed diagram of the data flow among the
purchase and cash disbursement system is provided in this report. A detailed
diagram of the data flow in the payroll system is detailed in this report. The system
flowchart of the payroll system, cash disbursement system and the purchase system
is provided in this report. Lastly, this report concludes with the appropriate
conclusion for the report.
BELL STUDIO
Introduction
In the recent times, the organisation Bell studio has been facing several
problems in the business that are required to be analysed and corrected. This report
provides the clear discussion of the Bell studio organisation and provide the detailed
analysis of the organisation. The risks that are associated with the weaknesses of
the organisation are detailed in this report along with the detailed analysis of the
weaknesses of the organisation. The detailed diagram of the data flow among the
purchase and cash disbursement system is provided in this report. A detailed
diagram of the data flow in the payroll system is detailed in this report. The system
flowchart of the payroll system, cash disbursement system and the purchase system
is provided in this report. Lastly, this report concludes with the appropriate
conclusion for the report.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
BELL STUDIO
Discussion
Data flow diagram of payroll system
The initiation of the flow of the data in the payroll system starts when the
employees provide the details of the working hours to the supervisors. The extensive
review of the time cards is done by the supervisors for the correction of any kind
issue in the time cards and if there is no issue in the time cards, then the time cards
BELL STUDIO
Discussion
Data flow diagram of payroll system
The initiation of the flow of the data in the payroll system starts when the
employees provide the details of the working hours to the supervisors. The extensive
review of the time cards is done by the supervisors for the correction of any kind
issue in the time cards and if there is no issue in the time cards, then the time cards
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
BELL STUDIO
are submitted to the payroll department. With the utilisation of the computer terminal
that has been connected in the central payroll system that has been located in the
department of the data processing, the payroll clerk then inputs the information of the
time card data in the database of the organisation. the time cards are filed in the
payroll department and then provides the employees pay cheques to the various
supervisors for the distribution within the employees. The payroll clerk then performs
the sending of the one copy of the payroll register to the accounts payable
department and also files one more along with the time cards in payroll department.
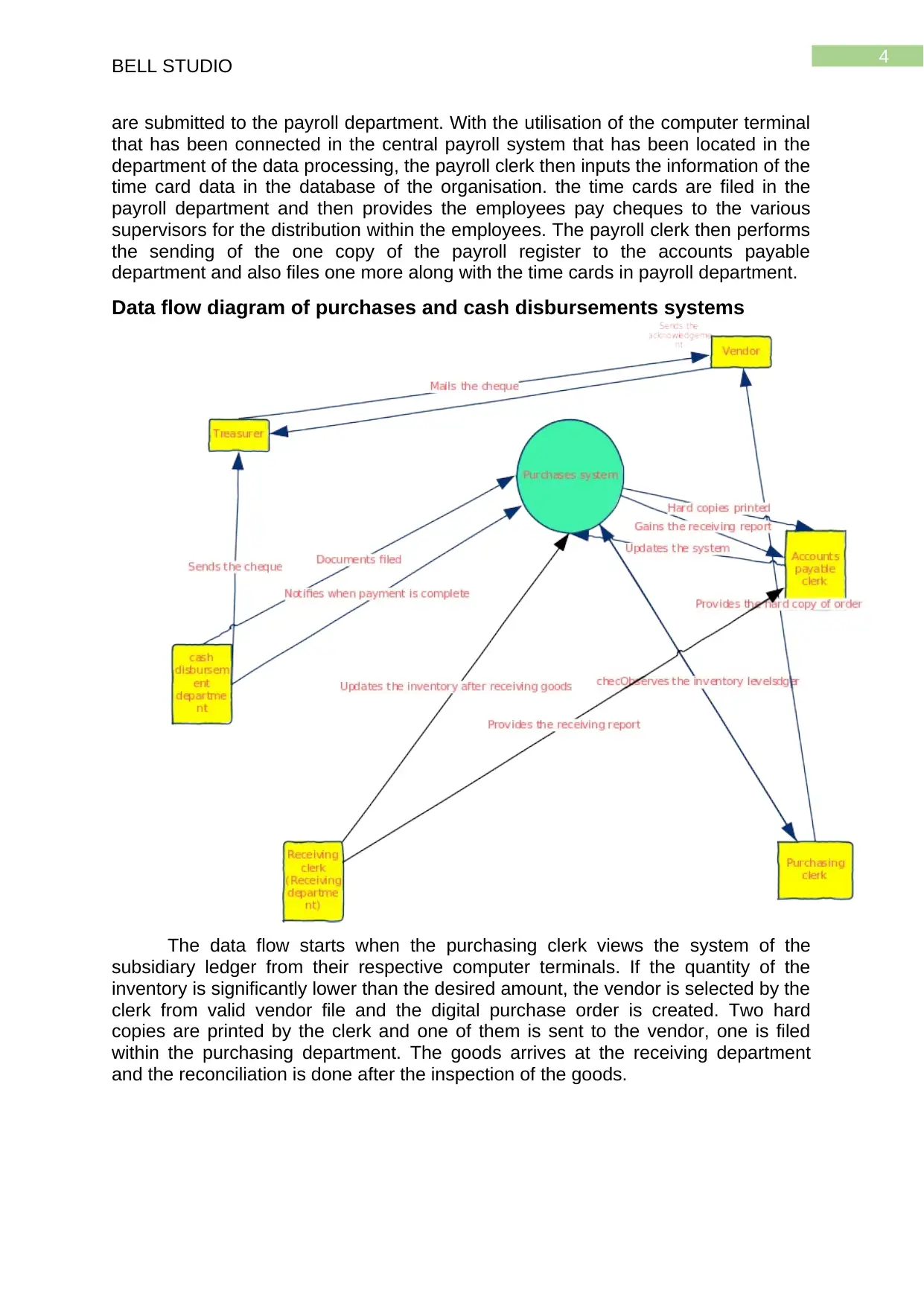
Data flow diagram of purchases and cash disbursements systems
The data flow starts when the purchasing clerk views the system of the
subsidiary ledger from their respective computer terminals. If the quantity of the
inventory is significantly lower than the desired amount, the vendor is selected by the
clerk from valid vendor file and the digital purchase order is created. Two hard
copies are printed by the clerk and one of them is sent to the vendor, one is filed
within the purchasing department. The goods arrives at the receiving department
and the reconciliation is done after the inspection of the goods.
BELL STUDIO
are submitted to the payroll department. With the utilisation of the computer terminal
that has been connected in the central payroll system that has been located in the
department of the data processing, the payroll clerk then inputs the information of the
time card data in the database of the organisation. the time cards are filed in the
payroll department and then provides the employees pay cheques to the various
supervisors for the distribution within the employees. The payroll clerk then performs
the sending of the one copy of the payroll register to the accounts payable
department and also files one more along with the time cards in payroll department.
Data flow diagram of purchases and cash disbursements systems
The data flow starts when the purchasing clerk views the system of the
subsidiary ledger from their respective computer terminals. If the quantity of the
inventory is significantly lower than the desired amount, the vendor is selected by the
clerk from valid vendor file and the digital purchase order is created. Two hard
copies are printed by the clerk and one of them is sent to the vendor, one is filed
within the purchasing department. The goods arrives at the receiving department
and the reconciliation is done after the inspection of the goods.
5
BELL STUDIO
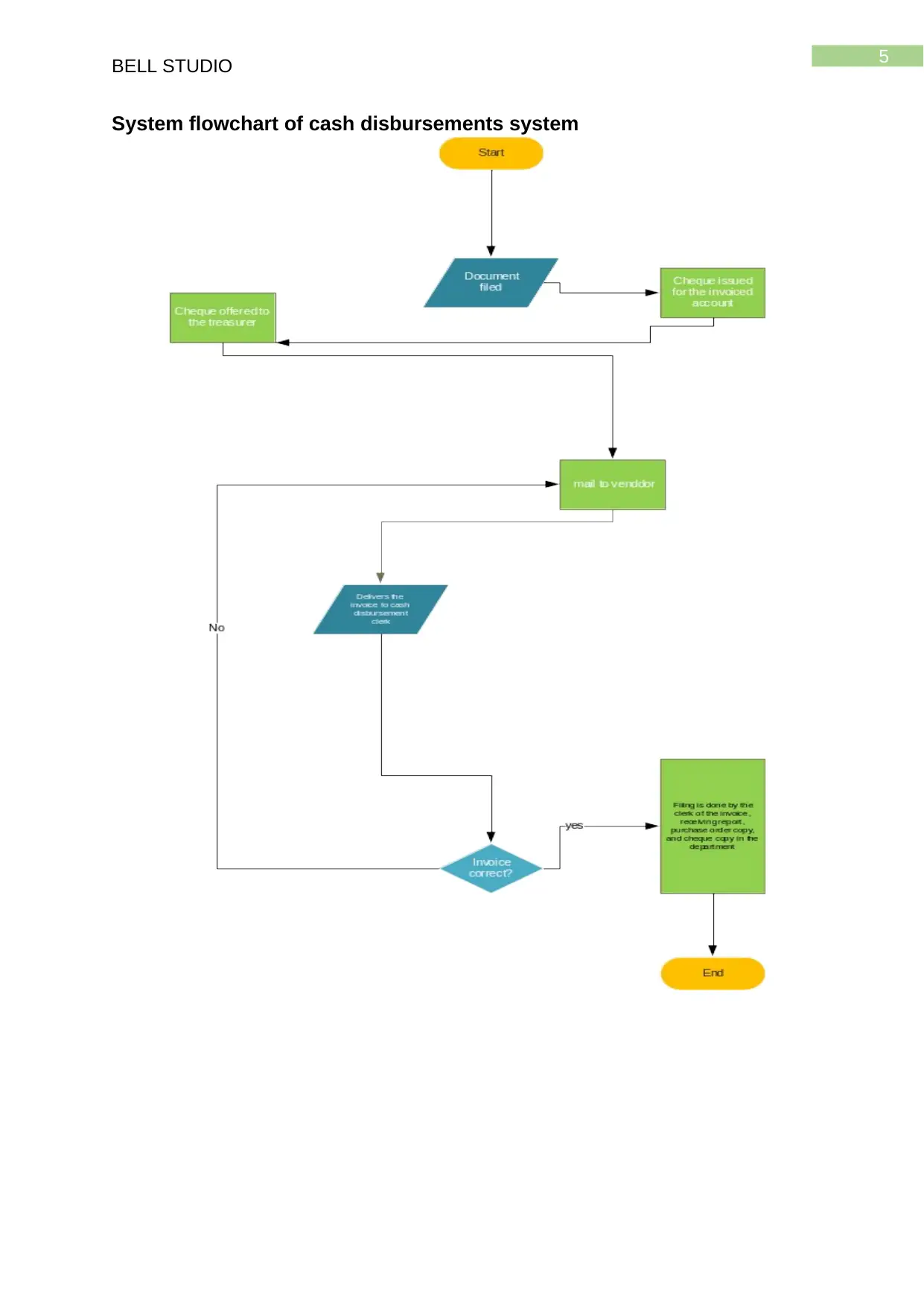
System flowchart of cash disbursements system
BELL STUDIO
System flowchart of cash disbursements system
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
BELL STUDIO
System flowchart of payroll system
BELL STUDIO
System flowchart of payroll system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
BELL STUDIO
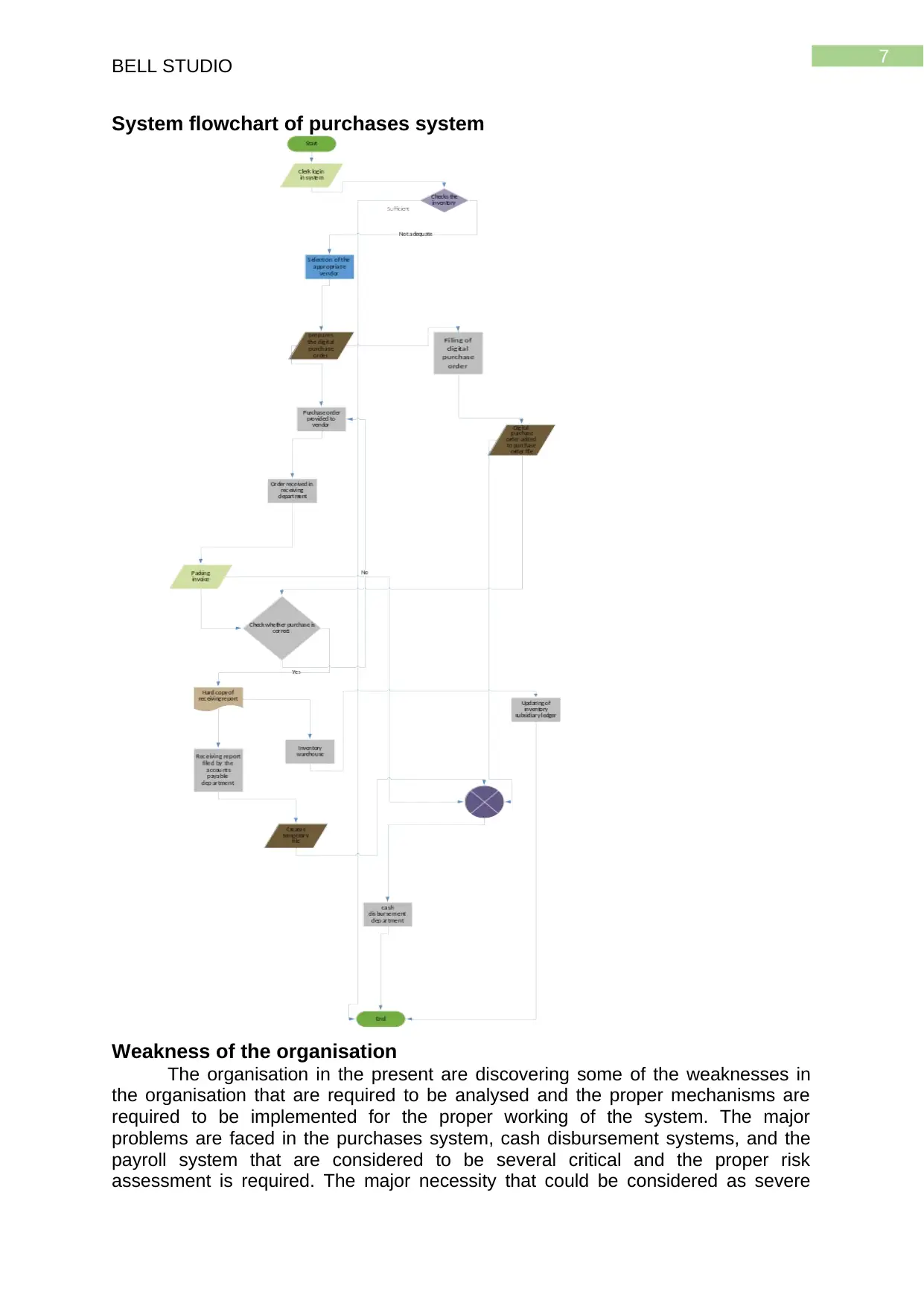
System flowchart of purchases system
Weakness of the organisation
The organisation in the present are discovering some of the weaknesses in
the organisation that are required to be analysed and the proper mechanisms are
required to be implemented for the proper working of the system. The major
problems are faced in the purchases system, cash disbursement systems, and the
payroll system that are considered to be several critical and the proper risk
assessment is required. The major necessity that could be considered as severe
BELL STUDIO
System flowchart of purchases system
Weakness of the organisation
The organisation in the present are discovering some of the weaknesses in
the organisation that are required to be analysed and the proper mechanisms are
required to be implemented for the proper working of the system. The major
problems are faced in the purchases system, cash disbursement systems, and the
payroll system that are considered to be several critical and the proper risk
assessment is required. The major necessity that could be considered as severe

8
BELL STUDIO
along with the complexity of the system of the purchasing along with the cash
disbursement has unfortunately denoted to several modifications that are executed
within the system and it could lead to the numerous disruptions that are majorly
operational by the depending on the methods by which the major system is
developed and the deployment of the system has been done. Some of the particular
systems of the company that could be considered as not working with the help of the
modern technology and majority of these system are falling behind on the various
patches that could be considered as critical for the additional expansion of the
updates residing inside the system might be subjected to the risk of the security or
even organisational risk. It could be observed that there is a significant weakness in
the system of the organisation that could lead to the increased vulnerability within the
various systems of the organisation. it could increase the threat of any kind of the
external attacks that could damage the proper working of the organisation. The
weaknesses could be considered as the loopholes in the system that might provide
the attackers with the opportunity of the executing the various kinds of attacks on the
system. This organisation conducts their business and manages the data of the
organisation in the unsecured computer terminals that could be the gateway for the
exploitation by the attackers. There might be situations when the attackers launch
the attacks on the system of the organisation are steal the confidential data of the
organisation as there is a unsecured system. Any hacker could discover the
vulnerability easily by the utilisation of the severe methods and launch the attack.
The network of the organisation does not includes the proper defence mechanisms
that are essential in the securing of the network of the organisation. The additional
danger might be observed as it has emerged because of the deployment of the
modern technology of the preventive measures.
Several kinds of resources are being consistently utilised by the company and
it include the financial sector, professional sector as well as the management of the
company. The data of all these sectors are required to be extensively protected and
secured for the prevention of any kind of attack by the outsider on the network for
gaining illegal entrance in the organisational network. The data of the various
departments of the organisation is managed in the databases that are implemented
in the network of the organisation. It could be considered that there are several
weaknesses in the databases. Some of the common weaknesses in the databases
are the lack of the proper and strict authentication protocols that prevents any
outsider by the detection of the authentication credentials of the user. The lack of the
robust firewall in the network of the organisation could create the issue of the attacks
on the network of the organisation with ease for the attackers. Another weakness of
the company that could be exploited by the illegal users is the lack of the proper
organisational culture among the various departments of the organisation. The
coordination among the various groups of the organisation could be exploited any
competitors and create the situation of the bad environment. These are major
weaknesses of the organisation that could be exploited by the malicious users with
the possessing of accurate tools and the techniques.
Risks connected with the organisation
The risks that could be considered as severely connected with the
weaknesses of the organisation are:
Sniffing attacks: majority of the hackers have been attempting the launching
of the attacks in the network of the organisation and the most common attack that
BELL STUDIO
along with the complexity of the system of the purchasing along with the cash
disbursement has unfortunately denoted to several modifications that are executed
within the system and it could lead to the numerous disruptions that are majorly
operational by the depending on the methods by which the major system is
developed and the deployment of the system has been done. Some of the particular
systems of the company that could be considered as not working with the help of the
modern technology and majority of these system are falling behind on the various
patches that could be considered as critical for the additional expansion of the
updates residing inside the system might be subjected to the risk of the security or
even organisational risk. It could be observed that there is a significant weakness in
the system of the organisation that could lead to the increased vulnerability within the
various systems of the organisation. it could increase the threat of any kind of the
external attacks that could damage the proper working of the organisation. The
weaknesses could be considered as the loopholes in the system that might provide
the attackers with the opportunity of the executing the various kinds of attacks on the
system. This organisation conducts their business and manages the data of the
organisation in the unsecured computer terminals that could be the gateway for the
exploitation by the attackers. There might be situations when the attackers launch
the attacks on the system of the organisation are steal the confidential data of the
organisation as there is a unsecured system. Any hacker could discover the
vulnerability easily by the utilisation of the severe methods and launch the attack.
The network of the organisation does not includes the proper defence mechanisms
that are essential in the securing of the network of the organisation. The additional
danger might be observed as it has emerged because of the deployment of the
modern technology of the preventive measures.
Several kinds of resources are being consistently utilised by the company and
it include the financial sector, professional sector as well as the management of the
company. The data of all these sectors are required to be extensively protected and
secured for the prevention of any kind of attack by the outsider on the network for
gaining illegal entrance in the organisational network. The data of the various
departments of the organisation is managed in the databases that are implemented
in the network of the organisation. It could be considered that there are several
weaknesses in the databases. Some of the common weaknesses in the databases
are the lack of the proper and strict authentication protocols that prevents any
outsider by the detection of the authentication credentials of the user. The lack of the
robust firewall in the network of the organisation could create the issue of the attacks
on the network of the organisation with ease for the attackers. Another weakness of
the company that could be exploited by the illegal users is the lack of the proper
organisational culture among the various departments of the organisation. The
coordination among the various groups of the organisation could be exploited any
competitors and create the situation of the bad environment. These are major
weaknesses of the organisation that could be exploited by the malicious users with
the possessing of accurate tools and the techniques.
Risks connected with the organisation
The risks that could be considered as severely connected with the
weaknesses of the organisation are:
Sniffing attacks: majority of the hackers have been attempting the launching
of the attacks in the network of the organisation and the most common attack that
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
BELL STUDIO
could be executed on the network of the organisation is the sniffing attack. These
attacks are not targeted towards the destruction of the working of the organisation
rather these kinds of the attacks are utilised for the gaining insight regarding the
weaknesses of the organisation. Redirecting of the spoofing could be considered
actually redirection of some type of the link of the web to an address that could be
significantly different from any other one that is used in the actual website. The
hackers could gain the access in the system of the organisation using the network
that has been implemented in the organisation or using the web platform and
discover any gateway that provides the complete access to the data of the
organisation. there has been the recent discovery regarding the sniffer program that
the execution of the this kind of program is significantly costly for the organisation.
Any sniffer individual majorly intends to allow hackers to steal majority of the
information that are significantly proprietary from any specific place within the
network and it includes the email discussion, business reports that are stored in the
confidential location and the documents whose exposure might lead to the significant
loss for the business. The hackers could possibly utilise the Trojan virus for the
execution of the severe attacks on the network of the organisation and obtain the
secure data easily. It has been discovered that the Trojan horses mostly comprises
of the opportunity of the key logging that could be referred as the keystroke recorder
for the major capturing of the input from the keyboard from a computer. The
computers of the organisation could be extensively exploited by the insider or the
employees of the organisation for launching the severe attacks on the organisation.
The information of the organisation that has been stored in the system could
severely face the specific issue and would be majorly involved in the stealing of the
confidential information.
Unauthorised access: This is the common kind of the attack that has to be
analysed with the extra caution and implement the proper working protocols for the
securing of the confidential information. In this organisation, all the departmental
employees are provided with the access to the system with the proper credentials.
The credentials could be compromised and stolen by any outsider who could
execute the launching of the attacks on the network of the organisation. The threat of
the viruses in the organisation could be severe as these computer programs could
be exploited by the outsiders and damage the working of the organisation.
Conclusion
Therefore, it can be concluded that the organisation is facing several
weaknesses in the network of the organisation that are required to be rectified and
the proper security protocols are required. The initiation of the flow of the data in the
payroll system starts when the employees provide the details of the working hours to
the supervisors. The extensive review of the time cards is done by the supervisors
for the correction of any kind issue in the time cards and if there is no issue in the
time cards, then the time cards are submitted to the payroll department. The data
flow starts when the purchasing clerk views the system of the subsidiary ledger from
their respective computer terminals. If the quantity of the inventory is significantly
lower than the desired amount, the vendor is selected by the clerk from valid vendor
file and the digital purchase order is created. Two hard copies are printed by the
clerk and one of them is sent to the vendor, one is filed within the purchasing
department. Several kinds of resources are being consistently utilised by the
company and it include the financial sector, professional sector as well as the
BELL STUDIO
could be executed on the network of the organisation is the sniffing attack. These
attacks are not targeted towards the destruction of the working of the organisation
rather these kinds of the attacks are utilised for the gaining insight regarding the
weaknesses of the organisation. Redirecting of the spoofing could be considered
actually redirection of some type of the link of the web to an address that could be
significantly different from any other one that is used in the actual website. The
hackers could gain the access in the system of the organisation using the network
that has been implemented in the organisation or using the web platform and
discover any gateway that provides the complete access to the data of the
organisation. there has been the recent discovery regarding the sniffer program that
the execution of the this kind of program is significantly costly for the organisation.
Any sniffer individual majorly intends to allow hackers to steal majority of the
information that are significantly proprietary from any specific place within the
network and it includes the email discussion, business reports that are stored in the
confidential location and the documents whose exposure might lead to the significant
loss for the business. The hackers could possibly utilise the Trojan virus for the
execution of the severe attacks on the network of the organisation and obtain the
secure data easily. It has been discovered that the Trojan horses mostly comprises
of the opportunity of the key logging that could be referred as the keystroke recorder
for the major capturing of the input from the keyboard from a computer. The
computers of the organisation could be extensively exploited by the insider or the
employees of the organisation for launching the severe attacks on the organisation.
The information of the organisation that has been stored in the system could
severely face the specific issue and would be majorly involved in the stealing of the
confidential information.
Unauthorised access: This is the common kind of the attack that has to be
analysed with the extra caution and implement the proper working protocols for the
securing of the confidential information. In this organisation, all the departmental
employees are provided with the access to the system with the proper credentials.
The credentials could be compromised and stolen by any outsider who could
execute the launching of the attacks on the network of the organisation. The threat of
the viruses in the organisation could be severe as these computer programs could
be exploited by the outsiders and damage the working of the organisation.
Conclusion
Therefore, it can be concluded that the organisation is facing several
weaknesses in the network of the organisation that are required to be rectified and
the proper security protocols are required. The initiation of the flow of the data in the
payroll system starts when the employees provide the details of the working hours to
the supervisors. The extensive review of the time cards is done by the supervisors
for the correction of any kind issue in the time cards and if there is no issue in the
time cards, then the time cards are submitted to the payroll department. The data
flow starts when the purchasing clerk views the system of the subsidiary ledger from
their respective computer terminals. If the quantity of the inventory is significantly
lower than the desired amount, the vendor is selected by the clerk from valid vendor
file and the digital purchase order is created. Two hard copies are printed by the
clerk and one of them is sent to the vendor, one is filed within the purchasing
department. Several kinds of resources are being consistently utilised by the
company and it include the financial sector, professional sector as well as the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
BELL STUDIO
management of the company. The data of all these sectors are required to be
extensively protected and secured for the prevention of any kind of attack by the
outsider on the network for gaining illegal entrance in the organisational network.
The data of the various departments of the organisation is managed in the
databases that are implemented in the network of the organisation. The hackers
could gain the access in the system of the organisation using the network that has
been implemented in the organisation or using the web platform and discover any
gateway that provides the complete access to the data of the organisation. there has
been the recent discovery regarding the sniffer program that the execution of the this
kind of program is significantly costly for the organisation. In this organisation, all the
departmental employees are provided with the access to the system with the proper
credentials. The credentials could be compromised and stolen by any outsider who
could execute the launching of the attacks on the network of the organisation.
BELL STUDIO
management of the company. The data of all these sectors are required to be
extensively protected and secured for the prevention of any kind of attack by the
outsider on the network for gaining illegal entrance in the organisational network.
The data of the various departments of the organisation is managed in the
databases that are implemented in the network of the organisation. The hackers
could gain the access in the system of the organisation using the network that has
been implemented in the organisation or using the web platform and discover any
gateway that provides the complete access to the data of the organisation. there has
been the recent discovery regarding the sniffer program that the execution of the this
kind of program is significantly costly for the organisation. In this organisation, all the
departmental employees are provided with the access to the system with the proper
credentials. The credentials could be compromised and stolen by any outsider who
could execute the launching of the attacks on the network of the organisation.

11
BELL STUDIO
Bibliography
AbdAllah, E.G., Hassanein, H.S. and Zulkernine, M., 2015. A survey of security
attacks in information-centric networking. IEEE Communications Surveys &
Tutorials, 17(3), pp.1441-1454.
Atymtayeva, L., Kozhakhmet, K. and Bortsova, G., 2014. Building a knowledge base
for expert system in information security. In Soft computing in artificial
intelligence (pp. 57-76). Springer, Cham.
B. Kim, E., 2014. Recommendations for information security awareness training for
college students. Information Management & Computer Security, 22(1), pp.115-126.
Elnajjar, A.E.A. and Naser, S.S.A., 2017. DES-Tutor: An Intelligent Tutoring System
for Teaching DES Information Security Algorithm.
Gupta, B., Agrawal, D.P. and Yamaguchi, S. eds., 2016. Handbook of research on
modern cryptographic solutions for computer and cyber security. IGI global.
Huang, C.D., Behara, R.S. and Goo, J., 2014. Optimal information security
investment in a Healthcare Information Exchange: An economic analysis. Decision
Support Systems, 61, pp.1-11.
Lavenex, S., 2017. Revival: The Europeanisation of Refugee Policies (2001):
Between Human Rights and Internal Security. Routledge.
Lebek, B., Uffen, J., Neumann, M., Hohler, B. and H. Breitner, M., 2014. Information
security awareness and behavior: a theory-based literature review. Management
Research Review, 37(12), pp.1049-1092.
Mahdi, A.O., Alhabbash, M.I. and Naser, S.S.A., 2016. An intelligent tutoring system
for teaching advanced topics in information security.
Montesdioca, G.P.Z. and Maçada, A.C.G., 2015. Measuring user satisfaction with
information security practices. Computers & Security, 48, pp.267-280.
Narain Singh, A., Gupta, M.P. and Ojha, A., 2014. Identifying factors of
“organizational information security management”. Journal of Enterprise Information
Management, 27(5), pp.644-667.
Posey, C., Roberts, T.L., Lowry, P.B. and Hightower, R.T., 2014. Bridging the divide:
A qualitative comparison of information security thought patterns between
information security professionals and ordinary organizational insiders. Information &
management, 51(5), pp.551-567.
Shameli-Sendi, A., Aghababaei-Barzegar, R. and Cheriet, M., 2016. Taxonomy of
information security risk assessment (ISRA). Computers & Security, 57, pp.14-30.
Stojmenovic, I., Wen, S., Huang, X. and Luan, H., 2016. An overview of fog
computing and its security issues. Concurrency and Computation: Practice and
Experience, 28(10), pp.2991-3005.
Webb, J., Ahmad, A., Maynard, S.B. and Shanks, G., 2014. A situation awareness
model for information security risk management. Computers & security, 44, pp.1-15.
BELL STUDIO
Bibliography
AbdAllah, E.G., Hassanein, H.S. and Zulkernine, M., 2015. A survey of security
attacks in information-centric networking. IEEE Communications Surveys &
Tutorials, 17(3), pp.1441-1454.
Atymtayeva, L., Kozhakhmet, K. and Bortsova, G., 2014. Building a knowledge base
for expert system in information security. In Soft computing in artificial
intelligence (pp. 57-76). Springer, Cham.
B. Kim, E., 2014. Recommendations for information security awareness training for
college students. Information Management & Computer Security, 22(1), pp.115-126.
Elnajjar, A.E.A. and Naser, S.S.A., 2017. DES-Tutor: An Intelligent Tutoring System
for Teaching DES Information Security Algorithm.
Gupta, B., Agrawal, D.P. and Yamaguchi, S. eds., 2016. Handbook of research on
modern cryptographic solutions for computer and cyber security. IGI global.
Huang, C.D., Behara, R.S. and Goo, J., 2014. Optimal information security
investment in a Healthcare Information Exchange: An economic analysis. Decision
Support Systems, 61, pp.1-11.
Lavenex, S., 2017. Revival: The Europeanisation of Refugee Policies (2001):
Between Human Rights and Internal Security. Routledge.
Lebek, B., Uffen, J., Neumann, M., Hohler, B. and H. Breitner, M., 2014. Information
security awareness and behavior: a theory-based literature review. Management
Research Review, 37(12), pp.1049-1092.
Mahdi, A.O., Alhabbash, M.I. and Naser, S.S.A., 2016. An intelligent tutoring system
for teaching advanced topics in information security.
Montesdioca, G.P.Z. and Maçada, A.C.G., 2015. Measuring user satisfaction with
information security practices. Computers & Security, 48, pp.267-280.
Narain Singh, A., Gupta, M.P. and Ojha, A., 2014. Identifying factors of
“organizational information security management”. Journal of Enterprise Information
Management, 27(5), pp.644-667.
Posey, C., Roberts, T.L., Lowry, P.B. and Hightower, R.T., 2014. Bridging the divide:
A qualitative comparison of information security thought patterns between
information security professionals and ordinary organizational insiders. Information &
management, 51(5), pp.551-567.
Shameli-Sendi, A., Aghababaei-Barzegar, R. and Cheriet, M., 2016. Taxonomy of
information security risk assessment (ISRA). Computers & Security, 57, pp.14-30.
Stojmenovic, I., Wen, S., Huang, X. and Luan, H., 2016. An overview of fog
computing and its security issues. Concurrency and Computation: Practice and
Experience, 28(10), pp.2991-3005.
Webb, J., Ahmad, A., Maynard, S.B. and Shanks, G., 2014. A situation awareness
model for information security risk management. Computers & security, 44, pp.1-15.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





