Cloud-based Secure Log Management System for Disaster Response
VerifiedAdded on 2019/09/22
|19
|5462
|148
Report
AI Summary
The assignment discusses the role of log management in disaster management systems. It emphasizes the importance of using a mixed methodology approach, combining both secondary and primary research methods with qualitative analysis, to gain a deeper understanding of syslog functions. The researcher acknowledges the ethical considerations involved in human subjects' participation and ensures that their dignity, privacy, and respect are maintained during data collection. The references provided are relevant studies on log management, disaster management, and research methodology.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT
AND DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Highly Secured Cloud Based Syslog Disaster Management and Disaster Recovery Site with
Encrypted Log
Name of the Student
Name of the University
Author note
AND DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Highly Secured Cloud Based Syslog Disaster Management and Disaster Recovery Site with
Encrypted Log
Name of the Student
Name of the University
Author note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Executive summary
The aim of the paper is to explore into the highly secured cloud based syslog disaster
management system and also disaster recovery site using encrypted log. Syslog is a function that
helps the servers to send messages on critical events that is being taking place in an area. It is a
centrally located server and messages from this server is transmitted to other locations. There are
various log management process that the business has to follow while using it to save messages.
Moreover, cloud based system gives a better opportunity to secure the data and save it from
getting misused. The study will explore into this system and the ways it benefits the disaster
management companies while handling critical situation. For the purpose a secondary and
primary research tool is adopted and used so that the entire information on the system is known.
For primary method as survey will be conducted with the help of questionnaire and will be filled
by the disaster management companies. This will help the research to get an accurate outcome of
the survey.
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Executive summary
The aim of the paper is to explore into the highly secured cloud based syslog disaster
management system and also disaster recovery site using encrypted log. Syslog is a function that
helps the servers to send messages on critical events that is being taking place in an area. It is a
centrally located server and messages from this server is transmitted to other locations. There are
various log management process that the business has to follow while using it to save messages.
Moreover, cloud based system gives a better opportunity to secure the data and save it from
getting misused. The study will explore into this system and the ways it benefits the disaster
management companies while handling critical situation. For the purpose a secondary and
primary research tool is adopted and used so that the entire information on the system is known.
For primary method as survey will be conducted with the help of questionnaire and will be filled
by the disaster management companies. This will help the research to get an accurate outcome of
the survey.

2
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Table of Contents
Introduction......................................................................................................................................2
Background......................................................................................................................................3
Aim and Objectives.....................................................................................................................4
Literature Review............................................................................................................................4
Technologies and Resources............................................................................................................9
Method and Work Plan..................................................................................................................10
Research approach.....................................................................................................................10
Research philosophy..................................................................................................................10
Data collection method..............................................................................................................11
Sampling method and size.........................................................................................................12
Data Analysis method................................................................................................................12
Gantt chart.....................................................................................................................................12
Discussion......................................................................................................................................13
Conclusion.....................................................................................................................................14
References......................................................................................................................................16
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Table of Contents
Introduction......................................................................................................................................2
Background......................................................................................................................................3
Aim and Objectives.....................................................................................................................4
Literature Review............................................................................................................................4
Technologies and Resources............................................................................................................9
Method and Work Plan..................................................................................................................10
Research approach.....................................................................................................................10
Research philosophy..................................................................................................................10
Data collection method..............................................................................................................11
Sampling method and size.........................................................................................................12
Data Analysis method................................................................................................................12
Gantt chart.....................................................................................................................................12
Discussion......................................................................................................................................13
Conclusion.....................................................................................................................................14
References......................................................................................................................................16

3
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Introduction
Disaster management is a process by which the lives and property of people in the
economy is saved and managed from vulnerable natural and man-made disasters. The rate of
natural disaster has been increasing over the years and this had made it important for the disaster
management companies to take a step to protect the loss that take place. Even with the progress
in scientific and material solutions, the impact of disaster management has not decreased to that
extent. Thus, disaster management forms an integral part of the policy framework of the
economy to save the poor and underprivileged people from the negative impact of such disaster
(O'Brien et al. 2006). Disaster impacts property and huge loss to the organization as well that
exists in and around the property. According to Song et al. (2013) disaster management is a
prevention process that involves engaging in such an activity that would help in reducing the
impacts of disasters. Even though all disasters cannot be prevented, its impact can be reduced to
an extent that there is no harm to life and property. Technology is improving in conducting
disaster management work. The technology is helping the disaster management person to carry
out a good deal of control and prevent the harmful impact. However, it is seen that while
implementing the control process.
Disaster has been a common phenomenon in the Indian economy as about 59 percent of
the landmass of India is prone to earthquake, 40 millions are prone to floods and other areas are
prone to various other types of disaster that hits the country from time to time with different
intensities. This has caused great loss to the private, community and public property and thus the
issue has been concerned on the global issue. The annual loss of India due to various disaster that
take place every year is estimated to be $9.8 billion. Among these loss most of the loss has come
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Introduction
Disaster management is a process by which the lives and property of people in the
economy is saved and managed from vulnerable natural and man-made disasters. The rate of
natural disaster has been increasing over the years and this had made it important for the disaster
management companies to take a step to protect the loss that take place. Even with the progress
in scientific and material solutions, the impact of disaster management has not decreased to that
extent. Thus, disaster management forms an integral part of the policy framework of the
economy to save the poor and underprivileged people from the negative impact of such disaster
(O'Brien et al. 2006). Disaster impacts property and huge loss to the organization as well that
exists in and around the property. According to Song et al. (2013) disaster management is a
prevention process that involves engaging in such an activity that would help in reducing the
impacts of disasters. Even though all disasters cannot be prevented, its impact can be reduced to
an extent that there is no harm to life and property. Technology is improving in conducting
disaster management work. The technology is helping the disaster management person to carry
out a good deal of control and prevent the harmful impact. However, it is seen that while
implementing the control process.
Disaster has been a common phenomenon in the Indian economy as about 59 percent of
the landmass of India is prone to earthquake, 40 millions are prone to floods and other areas are
prone to various other types of disaster that hits the country from time to time with different
intensities. This has caused great loss to the private, community and public property and thus the
issue has been concerned on the global issue. The annual loss of India due to various disaster that
take place every year is estimated to be $9.8 billion. Among these loss most of the loss has come
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
from floods (Thakur 2015). Thus, this gave a wakeup call and has made adequate investment in
the reduction of risk from disaster loss. Various steps has been taken to control the disasters and
to control the impact various types of timely data is needed and secured so that it can be used to
estimate the threat from any disaster.
The paper plans to conduct a research into the use of highly secured cloud based syslog
disaster management and disaster recovery site with encrypted log. The report discusses the
meaning and concept of syslog in disaster management work in which encrypted log will be used
in disaster recovery site. Further, it proposes method to analyze the role syslog offers to secure
the data while conducting disaster management step and disaster site recovery.
Background
Disaster management system is not an easy process as it requires a lot of information and
analysis to estimate and understand the urgency of the event and the threat a place has from it.
Further, the data is also required while deciding the disaster recovery site also to understand the
risk a place has. It helps in taking the decision about what kind of disaster recovery site an
organization needs and careful planning needs to be done to reduce the risk (Song et al. 2013).
However, all this is not possible without proper data management techniques. One such data
management technique and benefit is offered by the syslog disaster management. Syslog is a
system log that allows the network devices to send messages to a centrally located server. The
information from this server can then be used to help identify critical events and alert the area
about the disaster. This is the recent system that is allowing the disaster management team to
secure the area prior to the disaster (Kolhe and Shaikh 2018). The system is protected by
encryption so that there is no kind of data breach in case of critical incidents. This shows the
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
from floods (Thakur 2015). Thus, this gave a wakeup call and has made adequate investment in
the reduction of risk from disaster loss. Various steps has been taken to control the disasters and
to control the impact various types of timely data is needed and secured so that it can be used to
estimate the threat from any disaster.
The paper plans to conduct a research into the use of highly secured cloud based syslog
disaster management and disaster recovery site with encrypted log. The report discusses the
meaning and concept of syslog in disaster management work in which encrypted log will be used
in disaster recovery site. Further, it proposes method to analyze the role syslog offers to secure
the data while conducting disaster management step and disaster site recovery.
Background
Disaster management system is not an easy process as it requires a lot of information and
analysis to estimate and understand the urgency of the event and the threat a place has from it.
Further, the data is also required while deciding the disaster recovery site also to understand the
risk a place has. It helps in taking the decision about what kind of disaster recovery site an
organization needs and careful planning needs to be done to reduce the risk (Song et al. 2013).
However, all this is not possible without proper data management techniques. One such data
management technique and benefit is offered by the syslog disaster management. Syslog is a
system log that allows the network devices to send messages to a centrally located server. The
information from this server can then be used to help identify critical events and alert the area
about the disaster. This is the recent system that is allowing the disaster management team to
secure the area prior to the disaster (Kolhe and Shaikh 2018). The system is protected by
encryption so that there is no kind of data breach in case of critical incidents. This shows the

5
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
importance that syslog system has formed in case of disaster management and this makes it
important for the researcher to conduct a research in this technology of disaster management
process. The syslog system server has an important role to play to secure the data and use it at
the time of emergency. This research will help in knowing and identifying the critical events,
logs, alerts and alarms that is given by the network devices (Kelsey, Callas and Clemm 2010). In
addition to this the attachment of cloud system has helped in accessing the data from the network
form anywhere in the world. Thus, the rationale of the paper lies in the analyzing the role that
syslog plays in disaster management and disaster recovery site.
Aim and Objectives
The aim of paper is to understand the role that syslog system of data management plays
in disaster management and disaster recovery site with the help of encrypted log data. Further,
the analysis will be done on the highly secured cloud based syslog rather than the in house data
management. The paper will directly aim of this system on the basis of disaster management and
not for any other purpose or management areas. The objective of the paper are as follows:
To analyze the concept of syslog system
To analyze the importance of high secured cloud based syslog system in which data is
found in encrypted format
To analyze the availability of the sensitive syslog data in the areas of investigation or
audit
To investigate into the role of highly secure cloud based syslog data in the disaster
management work
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
importance that syslog system has formed in case of disaster management and this makes it
important for the researcher to conduct a research in this technology of disaster management
process. The syslog system server has an important role to play to secure the data and use it at
the time of emergency. This research will help in knowing and identifying the critical events,
logs, alerts and alarms that is given by the network devices (Kelsey, Callas and Clemm 2010). In
addition to this the attachment of cloud system has helped in accessing the data from the network
form anywhere in the world. Thus, the rationale of the paper lies in the analyzing the role that
syslog plays in disaster management and disaster recovery site.
Aim and Objectives
The aim of paper is to understand the role that syslog system of data management plays
in disaster management and disaster recovery site with the help of encrypted log data. Further,
the analysis will be done on the highly secured cloud based syslog rather than the in house data
management. The paper will directly aim of this system on the basis of disaster management and
not for any other purpose or management areas. The objective of the paper are as follows:
To analyze the concept of syslog system
To analyze the importance of high secured cloud based syslog system in which data is
found in encrypted format
To analyze the availability of the sensitive syslog data in the areas of investigation or
audit
To investigate into the role of highly secure cloud based syslog data in the disaster
management work

6
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Literature Review
According to Kelsey, Callas and Clemm (2010) syslog is a computing tool that is used for
message logging in which it allows all network devices to send messages to the logging server.
This logging servers are also known as syslog server and are centrally located. The process of
syslog is supported by a number of devices or products that helps to collect logs or records based
on a particular event. Syslog allows the separation of three system that circulates the logs from
one place to another such as the software or device that collects the logs or generates it, the
network that stores or transfers the logs or messages and the software that helps in analyzing
those logs. These three processes are managed by syslog in its own way. The log generated in
syslog is assigned with a code and a security level to help secure the logs from any kind of
alterations. It is a common function that is used by the system designer for system management
and security auditing and analysis. There are various types of standards designed as well in a
syslog system that is assigned to the security level depending on the event that is occurring.
Different types of designed standards are emergency, alert, critical, error, warning and others.
These security levels are assigned depending on the situation and the level of severity that
situation might assert (Kelsey, Callas and Clemm 2010). The server using the syslog displays all
types of severity occurring in that system ranging from most severe to least severe level. This the
role that system plays in acquiring the log and transferring it to the situation for usage in a most
secured way. Linus based web server and windows based servers uses various software to push
the syslog message to the syslog server. Okmianski (2009) has pointed out that log is a record of
all types of information on events or activities that is being taking place on a system, network of
an organization. Logs are the most important information to be considered while solving a
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Literature Review
According to Kelsey, Callas and Clemm (2010) syslog is a computing tool that is used for
message logging in which it allows all network devices to send messages to the logging server.
This logging servers are also known as syslog server and are centrally located. The process of
syslog is supported by a number of devices or products that helps to collect logs or records based
on a particular event. Syslog allows the separation of three system that circulates the logs from
one place to another such as the software or device that collects the logs or generates it, the
network that stores or transfers the logs or messages and the software that helps in analyzing
those logs. These three processes are managed by syslog in its own way. The log generated in
syslog is assigned with a code and a security level to help secure the logs from any kind of
alterations. It is a common function that is used by the system designer for system management
and security auditing and analysis. There are various types of standards designed as well in a
syslog system that is assigned to the security level depending on the event that is occurring.
Different types of designed standards are emergency, alert, critical, error, warning and others.
These security levels are assigned depending on the situation and the level of severity that
situation might assert (Kelsey, Callas and Clemm 2010). The server using the syslog displays all
types of severity occurring in that system ranging from most severe to least severe level. This the
role that system plays in acquiring the log and transferring it to the situation for usage in a most
secured way. Linus based web server and windows based servers uses various software to push
the syslog message to the syslog server. Okmianski (2009) has pointed out that log is a record of
all types of information on events or activities that is being taking place on a system, network of
an organization. Logs are the most important information to be considered while solving a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
problem in an emergency situation as it offers all possible information on that event. They are a
crucial requirement for identifying a security incidents, fraud activities and policy.
Song et al. (2013) has pointed out that the function of a syslog helps in making the work
of the network admin easier than before as they do not have to log into each devices while
investigating about their network infrastructure. There are various network devices that helps in
sending syslog messages and also confirms that the message has been sent successfully. These
devices usually uses TCP port 1468 to send those messages in a secured form. According to
Church et al. (2012) syslog messages are the most helpful one while identifying analyzing
information about a critical event, alerts, logs or alarms. The system helps in addressing those
critical events in time by sending useful message or logs about it. A syslog servers are placed
under the same premises in a large scale data center to be used in an emergency situation. In
some cases the servers are also placed in different geographical locations. This is done so that in
case of a critical situation the logs saved by the server are used as a main fact for investigating
into the events. Thus, this is the importance that syslog holds in a critical incidents and there
should always some efforts made to protect the syslog server so that a conclusion can be reached
after a critical incident has occurred.
Thottan and Ji (2004) has described that syslog server also allows various types of
management benefits as well as syslog messages helps an organization to change from a reactive
state to a proactive state. This means that the organization should use syslog messages for
predicting critical events rather than using it to know the facts of the events after it has been
caused.
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
problem in an emergency situation as it offers all possible information on that event. They are a
crucial requirement for identifying a security incidents, fraud activities and policy.
Song et al. (2013) has pointed out that the function of a syslog helps in making the work
of the network admin easier than before as they do not have to log into each devices while
investigating about their network infrastructure. There are various network devices that helps in
sending syslog messages and also confirms that the message has been sent successfully. These
devices usually uses TCP port 1468 to send those messages in a secured form. According to
Church et al. (2012) syslog messages are the most helpful one while identifying analyzing
information about a critical event, alerts, logs or alarms. The system helps in addressing those
critical events in time by sending useful message or logs about it. A syslog servers are placed
under the same premises in a large scale data center to be used in an emergency situation. In
some cases the servers are also placed in different geographical locations. This is done so that in
case of a critical situation the logs saved by the server are used as a main fact for investigating
into the events. Thus, this is the importance that syslog holds in a critical incidents and there
should always some efforts made to protect the syslog server so that a conclusion can be reached
after a critical incident has occurred.
Thottan and Ji (2004) has described that syslog server also allows various types of
management benefits as well as syslog messages helps an organization to change from a reactive
state to a proactive state. This means that the organization should use syslog messages for
predicting critical events rather than using it to know the facts of the events after it has been
caused.

8
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Another important factor to be judged in the syslog system using cloud is to learn log
management system in cloud system. According to Lehner, Sattler and Sattler (2013) cloud is
one of the best and secured storage device of the logs and help in having access from anywhere
easily. Cloud offers three service models such as software as a service, platform as a service and
infrastructure as a service. Log management in cloud is a crucial decision to be taken by the
organization or the group using it for a purpose. Kolhe and Shaikh (2018) has stated that before
deciding on the models of log management that one wants to choose, it is necessary to first
identify the reason as to why the log needs to be collected. There are a set of reason on the basis
of which the type of log management system (internally or in cloud) can be decided. The first
step in deciding the log management system is to identify the goals that the project wants to
achieve over the course of it. This will help them decide whether they need an internal log
management or in cloud. The need of log differs from business to business such as the need of IT
organization would be to use log for solving their issues, while the security based business would
interested in event management and use log in there. Other than this, the other critical factor to
log management is to find resources that will handle and manage the log and the system (Lee et
al. 2011). The third factor is to try the service before purchasing it. This means that it is crucial to
try the type of log management system before deciding on to the type of system to be adopted.
According to Ray et al. (2013) selecting a log management system for the usage is very
much like building the partnership and then taking the service. However, as log management is
critical it is necessary to understand various factors that has to be considered while taking cloud
service provider. The factors that has to be considered are:
SaaS availability
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Another important factor to be judged in the syslog system using cloud is to learn log
management system in cloud system. According to Lehner, Sattler and Sattler (2013) cloud is
one of the best and secured storage device of the logs and help in having access from anywhere
easily. Cloud offers three service models such as software as a service, platform as a service and
infrastructure as a service. Log management in cloud is a crucial decision to be taken by the
organization or the group using it for a purpose. Kolhe and Shaikh (2018) has stated that before
deciding on the models of log management that one wants to choose, it is necessary to first
identify the reason as to why the log needs to be collected. There are a set of reason on the basis
of which the type of log management system (internally or in cloud) can be decided. The first
step in deciding the log management system is to identify the goals that the project wants to
achieve over the course of it. This will help them decide whether they need an internal log
management or in cloud. The need of log differs from business to business such as the need of IT
organization would be to use log for solving their issues, while the security based business would
interested in event management and use log in there. Other than this, the other critical factor to
log management is to find resources that will handle and manage the log and the system (Lee et
al. 2011). The third factor is to try the service before purchasing it. This means that it is crucial to
try the type of log management system before deciding on to the type of system to be adopted.
According to Ray et al. (2013) selecting a log management system for the usage is very
much like building the partnership and then taking the service. However, as log management is
critical it is necessary to understand various factors that has to be considered while taking cloud
service provider. The factors that has to be considered are:
SaaS availability

9
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Time within which the log data will be shown in the system
The delivery time of the alert to the client
Maintenance of compliance regularly
Upgrading the processing system with new attack vectors when a new attack is identified
Support the upgrade to software and hardware system
Other than this there are other considerations as well such as is the log management system
safe, the way it can be transported, the frequency in which the data is getting transferred and
others. All these has to be known before judging whether cloud service is useful in log
management system. Angin et al. (2010) on the other hand has stated that in case the cloud
provider is helping in sending alert for an emergency or critical events, it is necessary to
determine the way it is determining the event.
Waichal and Meshram (2013) has pointed out that log management under cloud has an
advantage that it allows to develop encrypted protocols that helps in maintaining the
confidentiality of the logs. There are various protocols that cloud system offers in log
management such as upload-tag generation, upload-log data, retrieve log data and delete logs. In
the upload tag generation it is necessary that the uploaded log record is secured with an index
key and it is set in such a way that it is not easy for the logging client to suggest the value while
monitoring the data. Further, upload logs data allows the user to send the message for the
uploaded log data and in return the logging monitor sends the log data to the cloud which can
then be retrieved for future use. The third protocol is on retrieve log data that allows to download
the log data from the cloud. The last protocol is delete logs which allows the requester to send a
message to the cloud and delete the data (Angin et al. 2010). Thus, these are the protocols that
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Time within which the log data will be shown in the system
The delivery time of the alert to the client
Maintenance of compliance regularly
Upgrading the processing system with new attack vectors when a new attack is identified
Support the upgrade to software and hardware system
Other than this there are other considerations as well such as is the log management system
safe, the way it can be transported, the frequency in which the data is getting transferred and
others. All these has to be known before judging whether cloud service is useful in log
management system. Angin et al. (2010) on the other hand has stated that in case the cloud
provider is helping in sending alert for an emergency or critical events, it is necessary to
determine the way it is determining the event.
Waichal and Meshram (2013) has pointed out that log management under cloud has an
advantage that it allows to develop encrypted protocols that helps in maintaining the
confidentiality of the logs. There are various protocols that cloud system offers in log
management such as upload-tag generation, upload-log data, retrieve log data and delete logs. In
the upload tag generation it is necessary that the uploaded log record is secured with an index
key and it is set in such a way that it is not easy for the logging client to suggest the value while
monitoring the data. Further, upload logs data allows the user to send the message for the
uploaded log data and in return the logging monitor sends the log data to the cloud which can
then be retrieved for future use. The third protocol is on retrieve log data that allows to download
the log data from the cloud. The last protocol is delete logs which allows the requester to send a
message to the cloud and delete the data (Angin et al. 2010). Thus, these are the protocols that
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
can be used in log management when it is done in cloud. Cloud log management system not only
offers benefit of retrieving the data from anywhere, they also help in offering security benefit to
the logs.
These roles of log management is crucial in a disaster management sites as the enterprise that
runs such management of both natural and man-made disasters needs to adhere to recovery
policies. Thus, in this case logs offer the management with information to recover from such
disaster such as solution, data, events and also alarm to a secondary site. Moreover, for this
purpose a centralized event management is needed so that it can help in filtering the most
security data from the other type of data. Thus, this makes it important to use the syslog function
as it allows to manage events as well as the logs centrally. Thus, the centralized syslog
management system using cloud is the best option while managing logs that is needed to manage
any disaster events.
Technologies and Resources
This section will study the resources and the techniques that the researcher will use to
reach out to the evidence for the research and complete investigation. Resources forms an
integral part of the research because with lack of proper resources the researcher will not be able
to reach out to the accurate outcome of the result. In case of inadequate resources the role of
highly secured syslog function in disaster management and disaster recovery with the use of
cloud will not be clear. The paper intends to use two types of resources for the research purpose
such as primary and secondary resources (Pakes and Schankerman 1984). Further, for these two
resources there will be further sub-resources that would be required. The first technique will be
to conduct secondary data collection, which will use electronic device such as ProQuest, Google
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
can be used in log management when it is done in cloud. Cloud log management system not only
offers benefit of retrieving the data from anywhere, they also help in offering security benefit to
the logs.
These roles of log management is crucial in a disaster management sites as the enterprise that
runs such management of both natural and man-made disasters needs to adhere to recovery
policies. Thus, in this case logs offer the management with information to recover from such
disaster such as solution, data, events and also alarm to a secondary site. Moreover, for this
purpose a centralized event management is needed so that it can help in filtering the most
security data from the other type of data. Thus, this makes it important to use the syslog function
as it allows to manage events as well as the logs centrally. Thus, the centralized syslog
management system using cloud is the best option while managing logs that is needed to manage
any disaster events.
Technologies and Resources
This section will study the resources and the techniques that the researcher will use to
reach out to the evidence for the research and complete investigation. Resources forms an
integral part of the research because with lack of proper resources the researcher will not be able
to reach out to the accurate outcome of the result. In case of inadequate resources the role of
highly secured syslog function in disaster management and disaster recovery with the use of
cloud will not be clear. The paper intends to use two types of resources for the research purpose
such as primary and secondary resources (Pakes and Schankerman 1984). Further, for these two
resources there will be further sub-resources that would be required. The first technique will be
to conduct secondary data collection, which will use electronic device such as ProQuest, Google

11
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Scholar and many other resources to study articles and past researches on the topic. Only the
trusted and the reliable search engine will be selected so that they offer accurate information
about syslog and cloud management system. These are the resources that will be used to conduct
secondary research. Further, for collecting primary research the selected resources will be five
disaster management companies that use this system of log management to protect their data and
utilize it to prevent or analyzing any critical events. Thus, for the purpose the companies will be
approached using a questionnaire for the survey (Amaratunga et al. 2002). The questionnaire in
this area and the managers of the companies, acts like a resource as it will help in continuing
with the work. Other than this the internet connection that will help in collecting both primary
and secondary data also acts like an important resource. This is because in case of absence of
internet connection none of the files can be opened nor the questionnaire can be mailed to the
companies. The most important resource above all this is time as it is the most crucial thing for
conducting the overall research appropriately and with minimum errors.
Method and Work Plan
The work plan offers a systematic view of the entire research process so that the
researcher can move forward the entire research in a proper manner and reduce potential errors.
The methodology of the research helps in designing the research approach, research philosophy,
and data collection method and research analysis (Prasad et al. 2012). All these together allows
the researcher to understand the way they can reach to the accurate outcome of the research.
Research approach
Research approach allows the user to know the ways in which it can approach the process
of the research that could help him get the best possible outcome. Research approach is a
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Scholar and many other resources to study articles and past researches on the topic. Only the
trusted and the reliable search engine will be selected so that they offer accurate information
about syslog and cloud management system. These are the resources that will be used to conduct
secondary research. Further, for collecting primary research the selected resources will be five
disaster management companies that use this system of log management to protect their data and
utilize it to prevent or analyzing any critical events. Thus, for the purpose the companies will be
approached using a questionnaire for the survey (Amaratunga et al. 2002). The questionnaire in
this area and the managers of the companies, acts like a resource as it will help in continuing
with the work. Other than this the internet connection that will help in collecting both primary
and secondary data also acts like an important resource. This is because in case of absence of
internet connection none of the files can be opened nor the questionnaire can be mailed to the
companies. The most important resource above all this is time as it is the most crucial thing for
conducting the overall research appropriately and with minimum errors.
Method and Work Plan
The work plan offers a systematic view of the entire research process so that the
researcher can move forward the entire research in a proper manner and reduce potential errors.
The methodology of the research helps in designing the research approach, research philosophy,
and data collection method and research analysis (Prasad et al. 2012). All these together allows
the researcher to understand the way they can reach to the accurate outcome of the research.
Research approach
Research approach allows the user to know the ways in which it can approach the process
of the research that could help him get the best possible outcome. Research approach is a

12
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
systematic tool that decides the attitude that the researcher use for conducting the investigation.
There are two types of research approach method such as inductive method and deductive
method of research approach. The inductive approach is adopted when the researcher intends to
collect data from a new source and a new information is formed out of it. On the other hand,
deductive approach allows the research to deduce the information from sources in which the
information is already available and known (Holt 2009). There is no new information formed out
of a deductive approach. The researcher will use both deductive and inductive approach for
investigating into the use of highly secured syslog function in disaster management.
Research philosophy
Research philosophy helps in stating the logic on which the research is being conducted
and the ways in which it should be done. There are various types of research philosophy such as
realism, positivism, interpretivism and others. Each of it helps in defining a new logic to the
research area in which the investigation will take place. The paper will use both positivism and
interpretivism philosophy. This is because the paper will use both secondary and primary data
for the research. While collecting secondary data, the positivism philosophy is accurate because
it depends on the philosophy that reality is known and it can be used with the help of observation
and without interfering into it much. On the other hand, interpretivism philosophy is used while
collecting primary data. This is because interpretivism philosophy contends that by interfering
into the reality the exact meaning is understood (Pakes and Schankerman 1984). Thus, both the
philosophy will be used in the paper for conducting primary and secondary research each.
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
systematic tool that decides the attitude that the researcher use for conducting the investigation.
There are two types of research approach method such as inductive method and deductive
method of research approach. The inductive approach is adopted when the researcher intends to
collect data from a new source and a new information is formed out of it. On the other hand,
deductive approach allows the research to deduce the information from sources in which the
information is already available and known (Holt 2009). There is no new information formed out
of a deductive approach. The researcher will use both deductive and inductive approach for
investigating into the use of highly secured syslog function in disaster management.
Research philosophy
Research philosophy helps in stating the logic on which the research is being conducted
and the ways in which it should be done. There are various types of research philosophy such as
realism, positivism, interpretivism and others. Each of it helps in defining a new logic to the
research area in which the investigation will take place. The paper will use both positivism and
interpretivism philosophy. This is because the paper will use both secondary and primary data
for the research. While collecting secondary data, the positivism philosophy is accurate because
it depends on the philosophy that reality is known and it can be used with the help of observation
and without interfering into it much. On the other hand, interpretivism philosophy is used while
collecting primary data. This is because interpretivism philosophy contends that by interfering
into the reality the exact meaning is understood (Pakes and Schankerman 1984). Thus, both the
philosophy will be used in the paper for conducting primary and secondary research each.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Data collection method
This is the major and the most important area of the research and helps in knowing the
way in which the researcher will collect data about the investigation. There are two types of data
collection method such as primary data collection and secondary data collection method. Primary
data collection method allow collecting data directly from the source so that it is accurate and
reliable (Kumar and Phrommathed 2005). On the other hand, Kothari (2004) points out that
secondary data collection method collect data from already existing sources or data from
internet. Secondary data is collected from reliable sources such as Google Scholar, Podcasts and
others. For the paper the researcher will use a mixed method for collecting data using both
secondary and primary data collection method (Amaratunga et al. 2002). This will allow the
researcher to get a detailed analysis of the data available and use it in the data. For the secondary
research method the researcher will search few keywords in internet to get appropriate
information such as “Syslog”, “Disaster management”, “Log management”, “cloud system” and
others. the primary method will be done by conducting a survey with five disaster management
company that use this syslog system to maintain data used for critical events. The survey will be
filled by 10 managers which will consists of 2 managers from each company and the result
obtained will be surveyed whether high security syslog system helps in disaster management
system. the survey will consists of a questionnaire consisting of 10 questions that will help in
generating an outcome.
Sampling method and size
A sample will be chosen for the research in such a way that it could represent the entire
population of disaster management companies. The sampling will be done with the help of non-
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Data collection method
This is the major and the most important area of the research and helps in knowing the
way in which the researcher will collect data about the investigation. There are two types of data
collection method such as primary data collection and secondary data collection method. Primary
data collection method allow collecting data directly from the source so that it is accurate and
reliable (Kumar and Phrommathed 2005). On the other hand, Kothari (2004) points out that
secondary data collection method collect data from already existing sources or data from
internet. Secondary data is collected from reliable sources such as Google Scholar, Podcasts and
others. For the paper the researcher will use a mixed method for collecting data using both
secondary and primary data collection method (Amaratunga et al. 2002). This will allow the
researcher to get a detailed analysis of the data available and use it in the data. For the secondary
research method the researcher will search few keywords in internet to get appropriate
information such as “Syslog”, “Disaster management”, “Log management”, “cloud system” and
others. the primary method will be done by conducting a survey with five disaster management
company that use this syslog system to maintain data used for critical events. The survey will be
filled by 10 managers which will consists of 2 managers from each company and the result
obtained will be surveyed whether high security syslog system helps in disaster management
system. the survey will consists of a questionnaire consisting of 10 questions that will help in
generating an outcome.
Sampling method and size
A sample will be chosen for the research in such a way that it could represent the entire
population of disaster management companies. The sampling will be done with the help of non-
14
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
probabilistic sampling because it will focus on collecting data from disaster management
companies that use the syslog system and not the entire group of disaster management entity.
The sample selected for the survey will be five disaster management companies using the syslog
system to manage their logs while critical events and 10 managers will participate in the survey
from the selected companies.
Data Analysis method
There are two types of data analysis method such as qualitative method and quantitative
method of data analysis. The data analysis method helps in analyzing the data in the best possible
way so that the desired outcome is achieved (Newman and Benz 1998). The paper will use
qualitative method of data analysis in which the data will be analyzed in a descriptive way so
that it is easily understood by the reader and the collected data is analyzed in a detailed way.
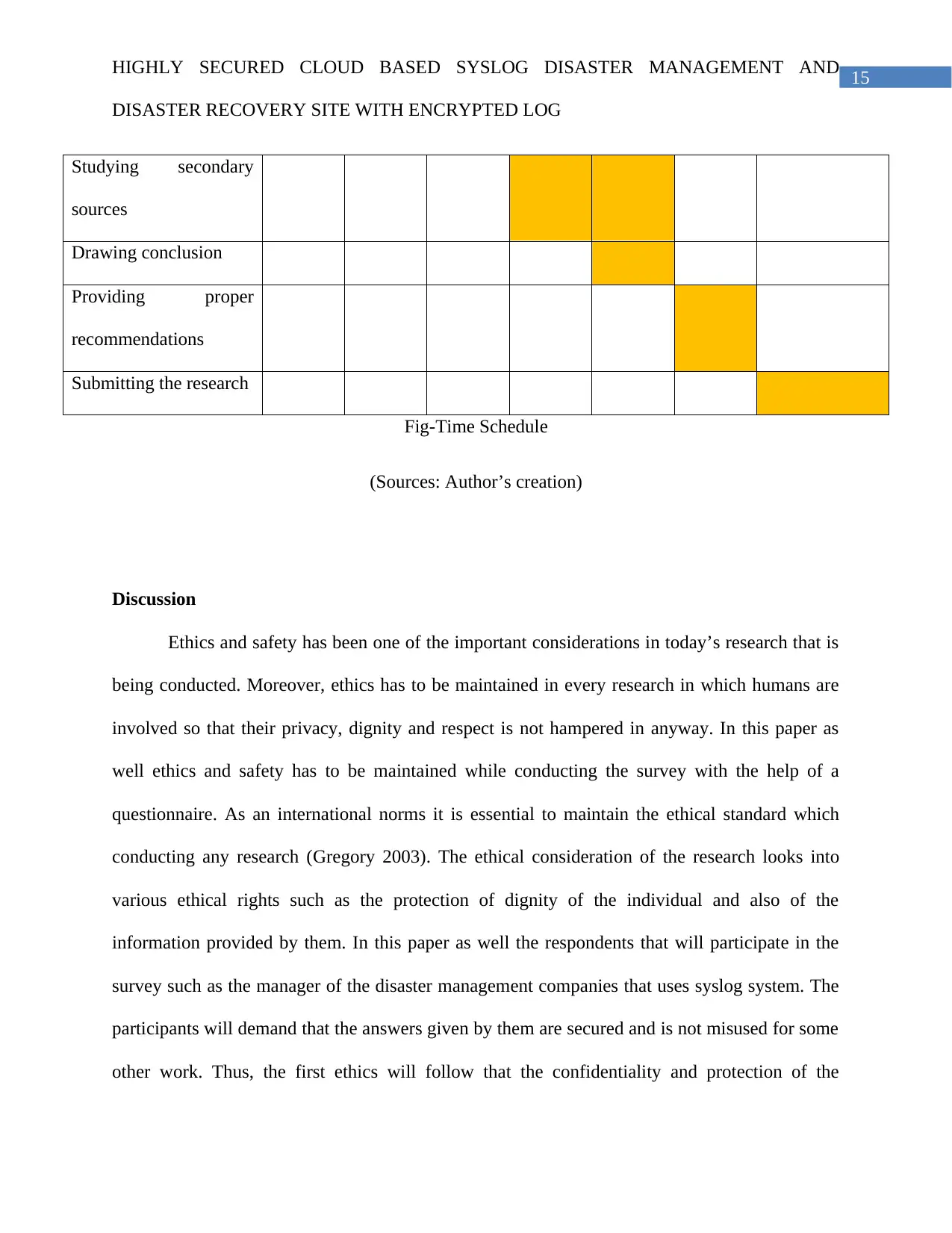
Gantt chart
Activities Week 1 Week 3 Week 6 Week
10
Week
15
Week
18
Week 22
Selecting the research
topic
Literature Review
Selection of research
methods
Collecting primary data
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
probabilistic sampling because it will focus on collecting data from disaster management
companies that use the syslog system and not the entire group of disaster management entity.
The sample selected for the survey will be five disaster management companies using the syslog
system to manage their logs while critical events and 10 managers will participate in the survey
from the selected companies.
Data Analysis method
There are two types of data analysis method such as qualitative method and quantitative
method of data analysis. The data analysis method helps in analyzing the data in the best possible
way so that the desired outcome is achieved (Newman and Benz 1998). The paper will use
qualitative method of data analysis in which the data will be analyzed in a descriptive way so
that it is easily understood by the reader and the collected data is analyzed in a detailed way.
Gantt chart
Activities Week 1 Week 3 Week 6 Week
10
Week
15
Week
18
Week 22
Selecting the research
topic
Literature Review
Selection of research
methods
Collecting primary data
15
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Studying secondary
sources
Drawing conclusion
Providing proper
recommendations
Submitting the research
Fig-Time Schedule
(Sources: Author’s creation)
Discussion
Ethics and safety has been one of the important considerations in today’s research that is
being conducted. Moreover, ethics has to be maintained in every research in which humans are
involved so that their privacy, dignity and respect is not hampered in anyway. In this paper as
well ethics and safety has to be maintained while conducting the survey with the help of a
questionnaire. As an international norms it is essential to maintain the ethical standard which
conducting any research (Gregory 2003). The ethical consideration of the research looks into
various ethical rights such as the protection of dignity of the individual and also of the
information provided by them. In this paper as well the respondents that will participate in the
survey such as the manager of the disaster management companies that uses syslog system. The
participants will demand that the answers given by them are secured and is not misused for some
other work. Thus, the first ethics will follow that the confidentiality and protection of the
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Studying secondary
sources
Drawing conclusion
Providing proper
recommendations
Submitting the research
Fig-Time Schedule
(Sources: Author’s creation)
Discussion
Ethics and safety has been one of the important considerations in today’s research that is
being conducted. Moreover, ethics has to be maintained in every research in which humans are
involved so that their privacy, dignity and respect is not hampered in anyway. In this paper as
well ethics and safety has to be maintained while conducting the survey with the help of a
questionnaire. As an international norms it is essential to maintain the ethical standard which
conducting any research (Gregory 2003). The ethical consideration of the research looks into
various ethical rights such as the protection of dignity of the individual and also of the
information provided by them. In this paper as well the respondents that will participate in the
survey such as the manager of the disaster management companies that uses syslog system. The
participants will demand that the answers given by them are secured and is not misused for some
other work. Thus, the first ethics will follow that the confidentiality and protection of the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
answers will be maintained. Further, while making the questionnaire it will be kept in mind that
none of the question harms the dignity of the participants and does not ask for any personal
information (Gregory 2003). Moreover, while using the information from the questionnaire
anonymity will be maintained so that there is no privacy issue faced by the participants as well as
the researcher.
Conclusion
From the above analysis it can be concluded that the entire research will help in learning
about the highly secured syslog system in disaster management and disaster recovery site using
cloud system. the system of log management using cloud has been studied and showed that is
important way to manage logs in a centralized server sand sent it to any local server when and
emergency or critical events take place. Various protocols are also added by cloud system of log
management that allows encryption of data sand secure it from any kind of risk. Many other area
has been studied about log management and its role in disaster management system. The
research is a useful one and will be conducted using both secondary and primary research
method and qualitative analysis method so that a detailed understanding and information about
the syslog function can be known. Thus, the researcher will follow a mixed methodology to
research into the topic deeply. As humans will be involved in the primary data collection
process, ethics are also considered and are maintained in a better way so that their respect dignity
and privacy is not hampered in anyway while using the survey for the work.
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
answers will be maintained. Further, while making the questionnaire it will be kept in mind that
none of the question harms the dignity of the participants and does not ask for any personal
information (Gregory 2003). Moreover, while using the information from the questionnaire
anonymity will be maintained so that there is no privacy issue faced by the participants as well as
the researcher.
Conclusion
From the above analysis it can be concluded that the entire research will help in learning
about the highly secured syslog system in disaster management and disaster recovery site using
cloud system. the system of log management using cloud has been studied and showed that is
important way to manage logs in a centralized server sand sent it to any local server when and
emergency or critical events take place. Various protocols are also added by cloud system of log
management that allows encryption of data sand secure it from any kind of risk. Many other area
has been studied about log management and its role in disaster management system. The
research is a useful one and will be conducted using both secondary and primary research
method and qualitative analysis method so that a detailed understanding and information about
the syslog function can be known. Thus, the researcher will follow a mixed methodology to
research into the topic deeply. As humans will be involved in the primary data collection
process, ethics are also considered and are maintained in a better way so that their respect dignity
and privacy is not hampered in anyway while using the survey for the work.

17
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
References
Amaratunga, D., Baldry, D., Sarshar, M. and Newton, R., 2002. Quantitative and qualitative
research in the built environment: application of “mixed” research approach. Work study, 51(1),
pp.17-31.
Angin, P., Bhargava, B., Ranchal, R., Singh, N., Linderman, M., Othmane, L.B. and Lilien, L.,
2010, October. An entity-centric approach for privacy and identity management in cloud
computing. In Reliable Distributed Systems, 2010 29th IEEE Symposium on (pp. 177-183).
IEEE.
Church, C., Golovinsky, E. and Govshteyn, M., Alert Logic Inc, 2012. Systems and methods for
correlating log messages into actionable security incidents and managing human responses.
U.S. Patent 8,156,553.
Gregory, I., 2003. Ethics in research. A&C Black.
Holt, J., 2009. Quantitative research: An overview. British Journal of Cardiac Nursing, 4(5),
pp.234-236.
Kelsey, J., Callas, J. and Clemm, A., 2010. Signed syslog messages (No. RFC 5848).
Kolhe, H.N. and Shaikh, I.R., Design of Secure Log Management Over Cloud.
Kothari, C.R., 2004. Research methodology: Methods and techniques. New Age International.
Kumar, S. and Phrommathed, P., 2005. Research methodology (pp. 43-50). Springer US.
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
References
Amaratunga, D., Baldry, D., Sarshar, M. and Newton, R., 2002. Quantitative and qualitative
research in the built environment: application of “mixed” research approach. Work study, 51(1),
pp.17-31.
Angin, P., Bhargava, B., Ranchal, R., Singh, N., Linderman, M., Othmane, L.B. and Lilien, L.,
2010, October. An entity-centric approach for privacy and identity management in cloud
computing. In Reliable Distributed Systems, 2010 29th IEEE Symposium on (pp. 177-183).
IEEE.
Church, C., Golovinsky, E. and Govshteyn, M., Alert Logic Inc, 2012. Systems and methods for
correlating log messages into actionable security incidents and managing human responses.
U.S. Patent 8,156,553.
Gregory, I., 2003. Ethics in research. A&C Black.
Holt, J., 2009. Quantitative research: An overview. British Journal of Cardiac Nursing, 4(5),
pp.234-236.
Kelsey, J., Callas, J. and Clemm, A., 2010. Signed syslog messages (No. RFC 5848).
Kolhe, H.N. and Shaikh, I.R., Design of Secure Log Management Over Cloud.
Kothari, C.R., 2004. Research methodology: Methods and techniques. New Age International.
Kumar, S. and Phrommathed, P., 2005. Research methodology (pp. 43-50). Springer US.

18
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Lee, J.H., Park, M.W., Eom, J.H. and Chung, T.M., 2011, February. Multi-level intrusion
detection system and log management in cloud computing. In Advanced Communication
Technology (ICACT), 2011 13th International Conference on (pp. 552-555). IEEE.
Lehner, W., Sattler, K.U. and Sattler, K.U., 2013. Web-scale data management for the
cloud (Vol. 5). Berlin: Springer.
Newman, I. and Benz, C.R., 1998. Qualitative-quantitative research methodology: Exploring the
interactive continuum. SIU Press.
O'Brien, G., O'Keefe, P., Rose, J. and Wisner, B., 2006. Climate change and disaster
management. Disasters, 30(1), pp.64-80.
Okmianski, A., 2009. Transmission of syslog Messages over UDP (No. RFC 5426).
Pakes, A. and Schankerman, M., 1984. The rate of obsolescence of patents, research gestation
lags, and the private rate of return to research resources. In R&D, patents, and productivity (pp.
73-88). University of Chicago Press.
Prasad, M.R., Sharath, V., Nagendra, G., Reddy, K.D. and Sridhar, V., 2012. Research Method
to Optimizse Logger for Telecom Application Running on Embedded System. International
Journal of Engineering Research and Development, 1(6), pp.01-09.
Ray, I., Belyaev, K., Strizhov, M., Mulamba, D. and Rajaram, M., 2013. Secure logging as a
service—delegating log management to the cloud. IEEE systems journal, 7(2), pp.323-334.
Resnik, D.B., 2011. What is ethics in research & why is it important. National Institute of
Environmental Health Sciences, pp.1-10.
HIGHLY SECURED CLOUD BASED SYSLOG DISASTER MANAGEMENT AND
DISASTER RECOVERY SITE WITH ENCRYPTED LOG
Lee, J.H., Park, M.W., Eom, J.H. and Chung, T.M., 2011, February. Multi-level intrusion
detection system and log management in cloud computing. In Advanced Communication
Technology (ICACT), 2011 13th International Conference on (pp. 552-555). IEEE.
Lehner, W., Sattler, K.U. and Sattler, K.U., 2013. Web-scale data management for the
cloud (Vol. 5). Berlin: Springer.
Newman, I. and Benz, C.R., 1998. Qualitative-quantitative research methodology: Exploring the
interactive continuum. SIU Press.
O'Brien, G., O'Keefe, P., Rose, J. and Wisner, B., 2006. Climate change and disaster
management. Disasters, 30(1), pp.64-80.
Okmianski, A., 2009. Transmission of syslog Messages over UDP (No. RFC 5426).
Pakes, A. and Schankerman, M., 1984. The rate of obsolescence of patents, research gestation
lags, and the private rate of return to research resources. In R&D, patents, and productivity (pp.
73-88). University of Chicago Press.
Prasad, M.R., Sharath, V., Nagendra, G., Reddy, K.D. and Sridhar, V., 2012. Research Method
to Optimizse Logger for Telecom Application Running on Embedded System. International
Journal of Engineering Research and Development, 1(6), pp.01-09.
Ray, I., Belyaev, K., Strizhov, M., Mulamba, D. and Rajaram, M., 2013. Secure logging as a
service—delegating log management to the cloud. IEEE systems journal, 7(2), pp.323-334.
Resnik, D.B., 2011. What is ethics in research & why is it important. National Institute of
Environmental Health Sciences, pp.1-10.
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





