ICT and Networking | Report
VerifiedAdded on 2022/08/19
|17
|1770
|12
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: ICT AND NETWORKING
ICT and Networking
Name of the Student
Name of the University
Author Note
ICT and Networking
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1ICT AND NETWORKING
Executive Summary
Information Communications Technology or ICT plays an important role in enabling
communications within an organization. This report proposes a network design for a
company that has branches in three different cities in Australia. The proposed network
ensures that the hosts from different departments of a LAN network can communicate with
each other as also communicate with other branches and the Internet. After validating this the
report is to present the IP addressing scheme and then talk about network devices. Then the
report ends with concluding notes.
Executive Summary
Information Communications Technology or ICT plays an important role in enabling
communications within an organization. This report proposes a network design for a
company that has branches in three different cities in Australia. The proposed network
ensures that the hosts from different departments of a LAN network can communicate with
each other as also communicate with other branches and the Internet. After validating this the
report is to present the IP addressing scheme and then talk about network devices. Then the
report ends with concluding notes.

2ICT AND NETWORKING
Table of Contents
Introduction................................................................................................................................3
Requirements..............................................................................................................................3
Network Design.........................................................................................................................4
Logical Diagram.....................................................................................................................4
Justification............................................................................................................................4
Connectivity...........................................................................................................................6
IP Addressing.........................................................................................................................7
Subnet Table...........................................................................................................................7
IP Address Allocation............................................................................................................8
Networking Hardware................................................................................................................9
Routers...................................................................................................................................9
Layer 3 (L3) Switches..........................................................................................................10
Layer 2 (L2) Switches..........................................................................................................11
Wireless Access Points........................................................................................................11
Conclusion................................................................................................................................13
Bibliography.............................................................................................................................14
Table of Contents
Introduction................................................................................................................................3
Requirements..............................................................................................................................3
Network Design.........................................................................................................................4
Logical Diagram.....................................................................................................................4
Justification............................................................................................................................4
Connectivity...........................................................................................................................6
IP Addressing.........................................................................................................................7
Subnet Table...........................................................................................................................7
IP Address Allocation............................................................................................................8
Networking Hardware................................................................................................................9
Routers...................................................................................................................................9
Layer 3 (L3) Switches..........................................................................................................10
Layer 2 (L2) Switches..........................................................................................................11
Wireless Access Points........................................................................................................11
Conclusion................................................................................................................................13
Bibliography.............................................................................................................................14

3ICT AND NETWORKING
Introduction
The following report tries to show the importance of Information Communications
Technology or ICT when it comes to communications within organizations (Habibullah,
Rondeau and Georges 2018). This report begins by listing the different network requirements
and then elaborates the proposed network with a logical network diagram drawn in Cisco
Packet Tracer. Then the report explains how the network ensures connectivity among the
hosts and with the Internet. After that the different subnets get listed along with their
respective network addresses, broadcasts, mask and IP ranges. Following that the IP
addressing scheme is explained. Next the different networking hardware devices are
discussed and the wireless connectivity is shown. After this the report ends with concluding
notes.
Requirements
The company XYZ needs to build a network interconnect between its branches in Sydney,
Melbourne and Adelaide.
The company must purchase appropriate major network and mask to be able to allocate
adequate range of IP addresses for the respective subnets.
The branch at Sydney is to use Subnet A and operate 63 hosts including 60 PCs and 2 servers
namely Windows and Fax servers.
The Melbourne branch needs to use Subnet B and provide connections to 53 hosts including
50 PCs and 2 servers namely DNS and Database servers.
The Adelaide is to provide IP address made available from Subnet C to 43 hosts including 40
PCs and 2 servers namely Linux and Applications servers.
Introduction
The following report tries to show the importance of Information Communications
Technology or ICT when it comes to communications within organizations (Habibullah,
Rondeau and Georges 2018). This report begins by listing the different network requirements
and then elaborates the proposed network with a logical network diagram drawn in Cisco
Packet Tracer. Then the report explains how the network ensures connectivity among the
hosts and with the Internet. After that the different subnets get listed along with their
respective network addresses, broadcasts, mask and IP ranges. Following that the IP
addressing scheme is explained. Next the different networking hardware devices are
discussed and the wireless connectivity is shown. After this the report ends with concluding
notes.
Requirements
The company XYZ needs to build a network interconnect between its branches in Sydney,
Melbourne and Adelaide.
The company must purchase appropriate major network and mask to be able to allocate
adequate range of IP addresses for the respective subnets.
The branch at Sydney is to use Subnet A and operate 63 hosts including 60 PCs and 2 servers
namely Windows and Fax servers.
The Melbourne branch needs to use Subnet B and provide connections to 53 hosts including
50 PCs and 2 servers namely DNS and Database servers.
The Adelaide is to provide IP address made available from Subnet C to 43 hosts including 40
PCs and 2 servers namely Linux and Applications servers.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4ICT AND NETWORKING
The network must also be able to provide wireless network connectivity for supported
devices.
Network Design
Logical Diagram
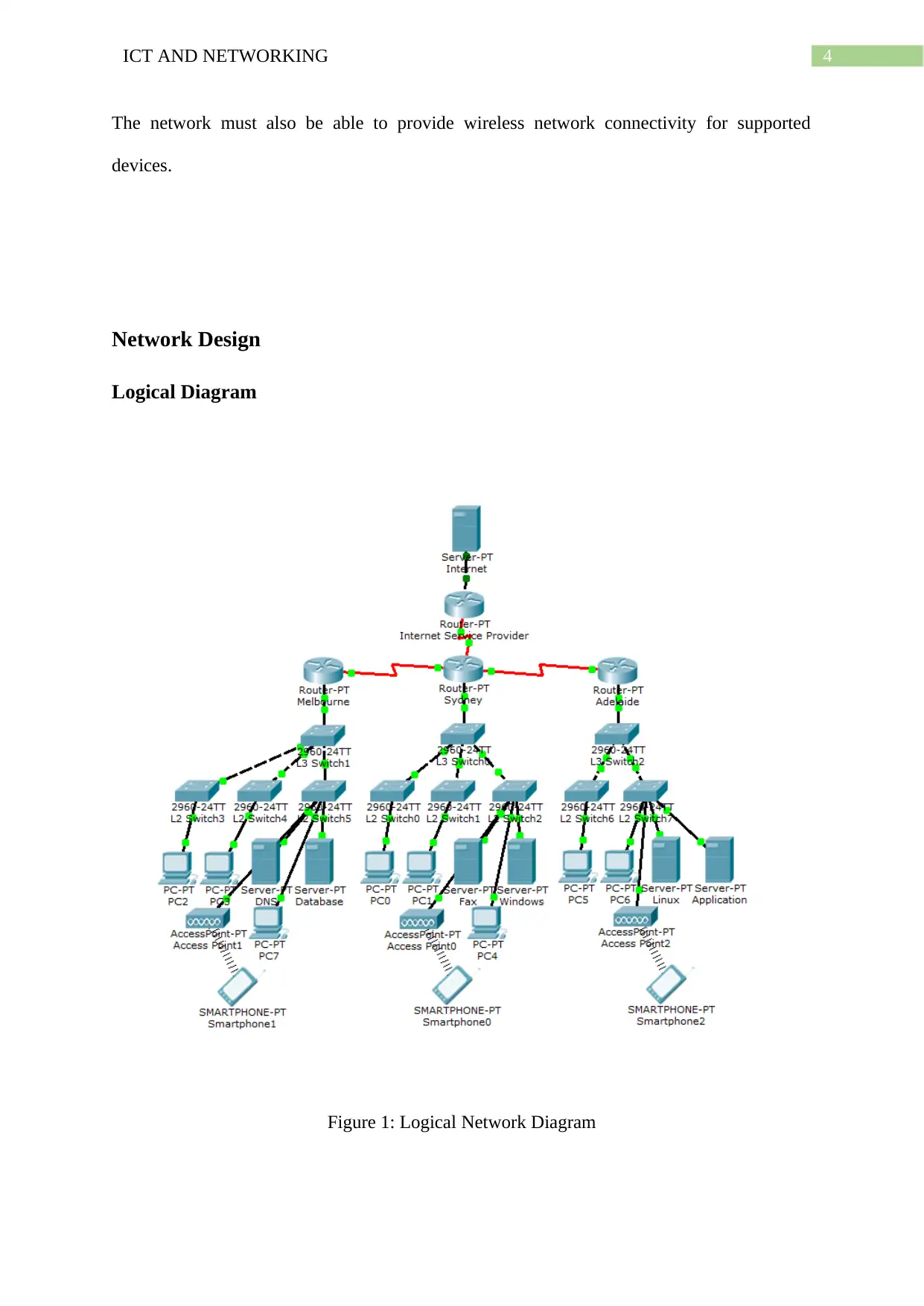
Figure 1: Logical Network Diagram
The network must also be able to provide wireless network connectivity for supported
devices.
Network Design
Logical Diagram
Figure 1: Logical Network Diagram

5ICT AND NETWORKING
Justification
The above diagram shows the logical network diagram of the network interconnect of
the company XYZ. Here, the connection to internet is provided to the company network by
the ISP router. Each of the of the individual LAN network of the sites – Sydney, Melbourne
and Adelaide are formed by following a top down approach using a three-layered hierarchical
network architecture where the layer 3 switch distributes the network connection to the host
devices through adequate number of layer 2 switches. The hosts include the PCs and two
servers installed in all the three locations. These hosts acquire their IP configuration
automatically through DHCP from one of the servers present in the respective site. These are
the Windows server for Sydney LAN, DNS server for Melbourne LAN and Linux server for
the Adelaide LAN. IP addressing of these servers is done manually and the DHCP
configuration is shown below.
Justification
The above diagram shows the logical network diagram of the network interconnect of
the company XYZ. Here, the connection to internet is provided to the company network by
the ISP router. Each of the of the individual LAN network of the sites – Sydney, Melbourne
and Adelaide are formed by following a top down approach using a three-layered hierarchical
network architecture where the layer 3 switch distributes the network connection to the host
devices through adequate number of layer 2 switches. The hosts include the PCs and two
servers installed in all the three locations. These hosts acquire their IP configuration
automatically through DHCP from one of the servers present in the respective site. These are
the Windows server for Sydney LAN, DNS server for Melbourne LAN and Linux server for
the Adelaide LAN. IP addressing of these servers is done manually and the DHCP
configuration is shown below.
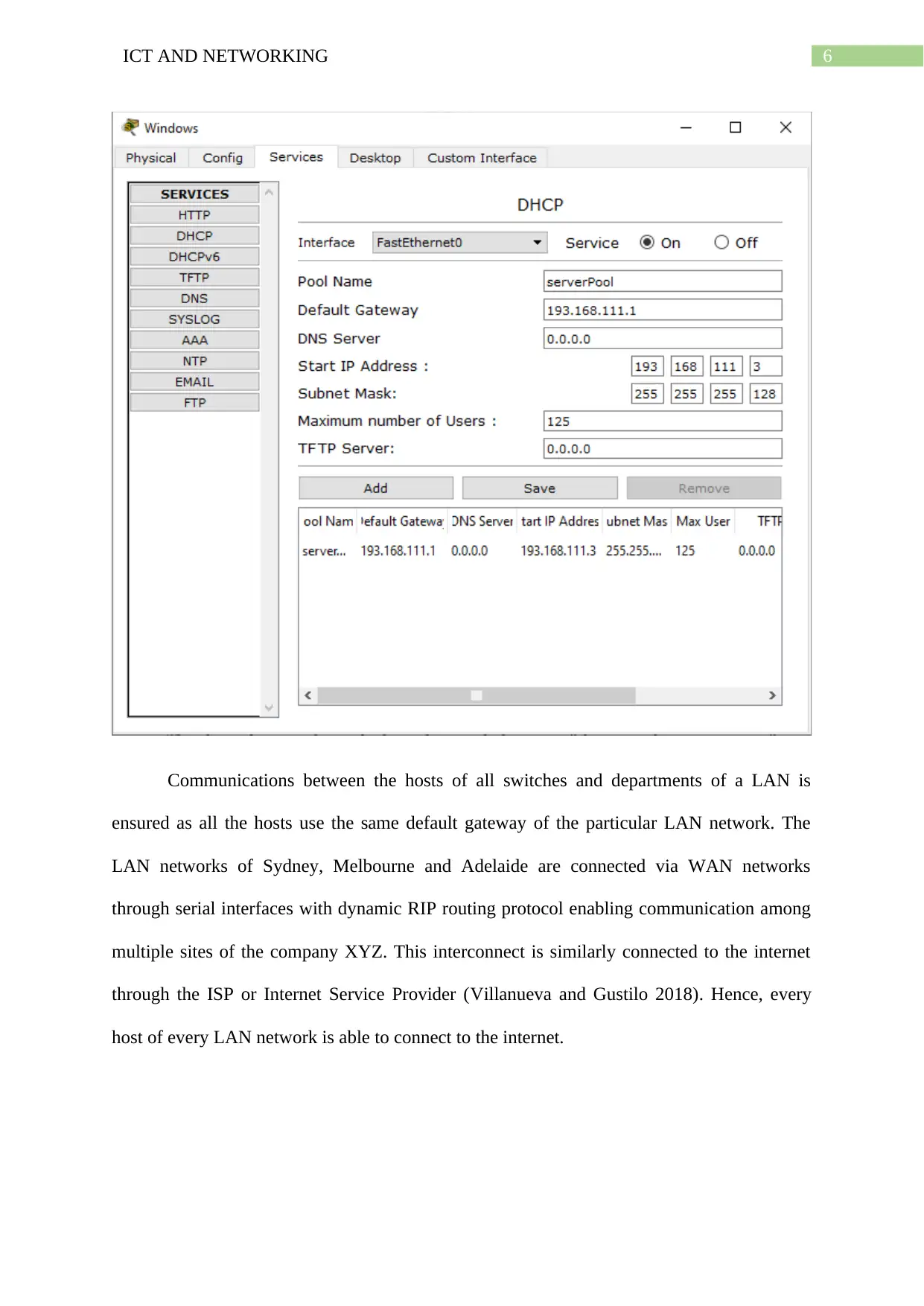
6ICT AND NETWORKING
Communications between the hosts of all switches and departments of a LAN is
ensured as all the hosts use the same default gateway of the particular LAN network. The
LAN networks of Sydney, Melbourne and Adelaide are connected via WAN networks
through serial interfaces with dynamic RIP routing protocol enabling communication among
multiple sites of the company XYZ. This interconnect is similarly connected to the internet
through the ISP or Internet Service Provider (Villanueva and Gustilo 2018). Hence, every
host of every LAN network is able to connect to the internet.
Communications between the hosts of all switches and departments of a LAN is
ensured as all the hosts use the same default gateway of the particular LAN network. The
LAN networks of Sydney, Melbourne and Adelaide are connected via WAN networks
through serial interfaces with dynamic RIP routing protocol enabling communication among
multiple sites of the company XYZ. This interconnect is similarly connected to the internet
through the ISP or Internet Service Provider (Villanueva and Gustilo 2018). Hence, every
host of every LAN network is able to connect to the internet.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7ICT AND NETWORKING
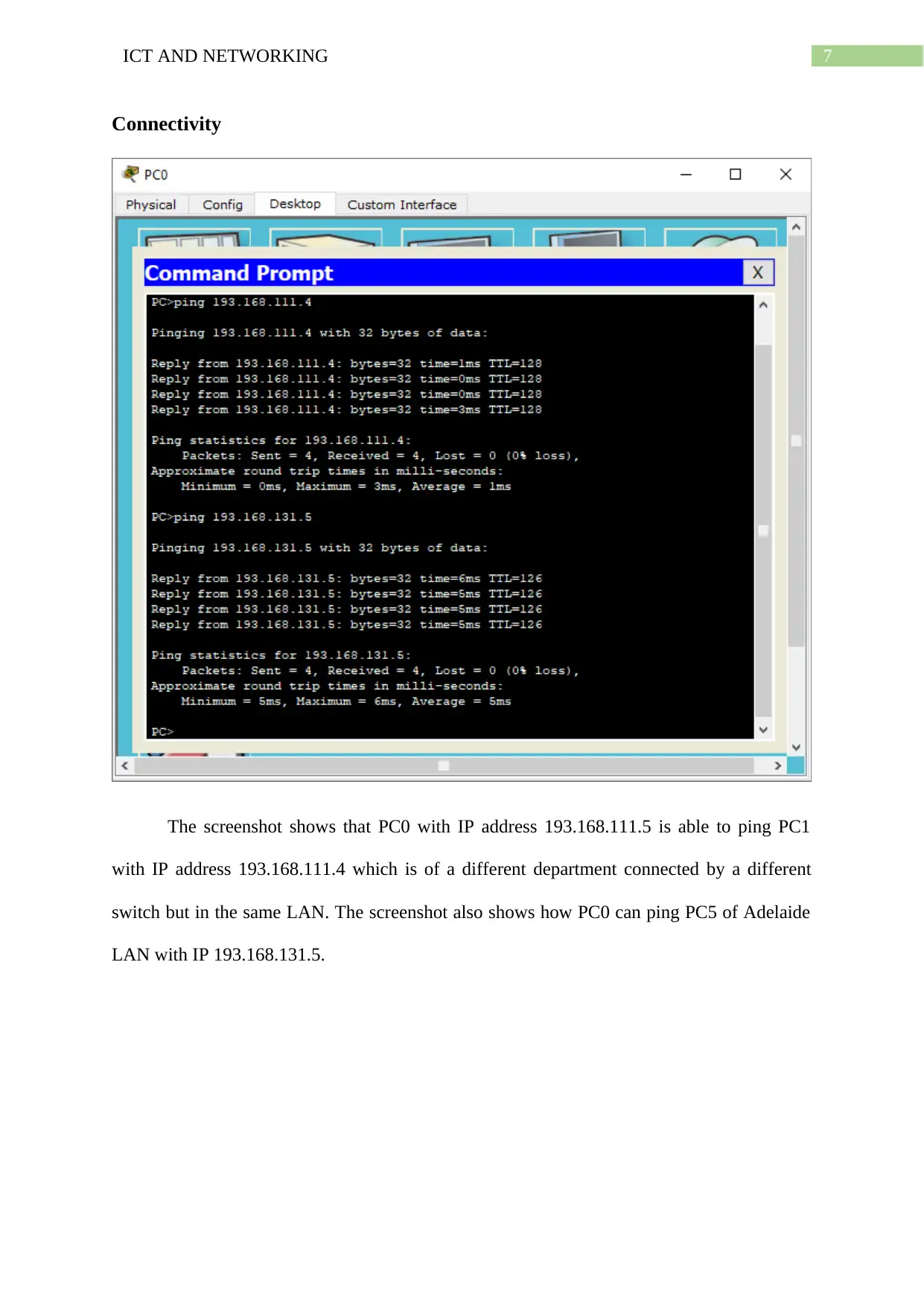
Connectivity
The screenshot shows that PC0 with IP address 193.168.111.5 is able to ping PC1
with IP address 193.168.111.4 which is of a different department connected by a different
switch but in the same LAN. The screenshot also shows how PC0 can ping PC5 of Adelaide
LAN with IP 193.168.131.5.
Connectivity
The screenshot shows that PC0 with IP address 193.168.111.5 is able to ping PC1
with IP address 193.168.111.4 which is of a different department connected by a different
switch but in the same LAN. The screenshot also shows how PC0 can ping PC5 of Adelaide
LAN with IP 193.168.131.5.
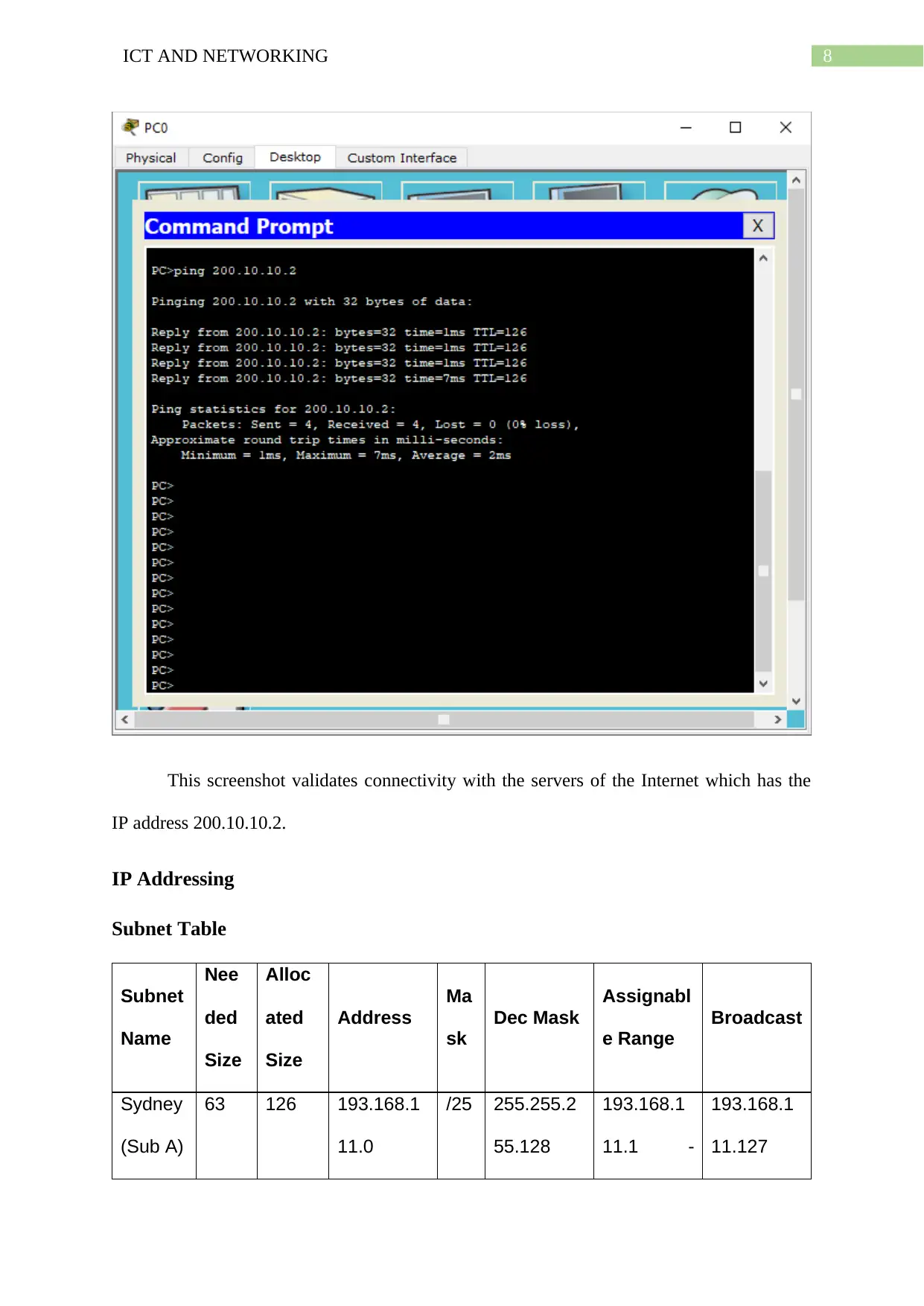
8ICT AND NETWORKING
This screenshot validates connectivity with the servers of the Internet which has the
IP address 200.10.10.2.
IP Addressing
Subnet Table
Subnet
Name
Nee
ded
Size
Alloc
ated
Size
Address
Ma
sk
Dec Mask
Assignabl
e Range
Broadcast
Sydney
(Sub A)
63 126 193.168.1
11.0
/25 255.255.2
55.128
193.168.1
11.1 -
193.168.1
11.127
This screenshot validates connectivity with the servers of the Internet which has the
IP address 200.10.10.2.
IP Addressing
Subnet Table
Subnet
Name
Nee
ded
Size
Alloc
ated
Size
Address
Ma
sk
Dec Mask
Assignabl
e Range
Broadcast
Sydney
(Sub A)
63 126 193.168.1
11.0
/25 255.255.2
55.128
193.168.1
11.1 -
193.168.1
11.127
9ICT AND NETWORKING
193.168.1
11.126
Melbou
rne
(Sub B)
53 62
193.168.1
21.128
/26
255.255.2
55.192
193.168.1
21.129 -
193.168.1
21.190
193.168.1
21.191
Adelaid
e (Sub
C)
43 62
193.168.1
31.192
/26
255.255.2
55.192
193.168.1
31.193 -
193.168.1
31.254
193.168.1
31.255
Interco
nnect
Sub D
4 6
193.168.1
01.0
/29
255.255.2
55.248
193.168.1
01.1 -
193.168.1
01.6
193.168.1
01.7
IP Address Allocation
To build the network interconnect, the company XYZ is assumed to make use of the
major network 193.168.100.0. To do this the subnet with CIDR mask /23 has been purchased
from the ISP (Shirmarz and Sabaei 2016). The network interconnect of the company thus
uses 52% of the available address space from the major network and uses 64% of the sub-
netted IP addresses allocated. The translated IP addresses 193.168.101.1 and 193.168.101.5
in the serial interfaces S0/3 and S0/6 of the Sydney router are used to connect the routers of
Melbourne and Adelaide LAN networks respectively. Therefore the routers of the Melbourne
and Adelaide are found to obtain the network of the company through serial interfaces S0/2
with the IP addresses 193.168.101.2 and 193.168.101.6 respectively. The subnets with
193.168.1
11.126
Melbou
rne
(Sub B)
53 62
193.168.1
21.128
/26
255.255.2
55.192
193.168.1
21.129 -
193.168.1
21.190
193.168.1
21.191
Adelaid
e (Sub
C)
43 62
193.168.1
31.192
/26
255.255.2
55.192
193.168.1
31.193 -
193.168.1
31.254
193.168.1
31.255
Interco
nnect
Sub D
4 6
193.168.1
01.0
/29
255.255.2
55.248
193.168.1
01.1 -
193.168.1
01.6
193.168.1
01.7
IP Address Allocation
To build the network interconnect, the company XYZ is assumed to make use of the
major network 193.168.100.0. To do this the subnet with CIDR mask /23 has been purchased
from the ISP (Shirmarz and Sabaei 2016). The network interconnect of the company thus
uses 52% of the available address space from the major network and uses 64% of the sub-
netted IP addresses allocated. The translated IP addresses 193.168.101.1 and 193.168.101.5
in the serial interfaces S0/3 and S0/6 of the Sydney router are used to connect the routers of
Melbourne and Adelaide LAN networks respectively. Therefore the routers of the Melbourne
and Adelaide are found to obtain the network of the company through serial interfaces S0/2
with the IP addresses 193.168.101.2 and 193.168.101.6 respectively. The subnets with
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10ICT AND NETWORKING
network addresses 193.168.111.0, 193.168.121.0 and 193.168.131.0 are used in the private
LAN networks of Sydney, Melbourne and Adelaide respectively.
Networking Hardware
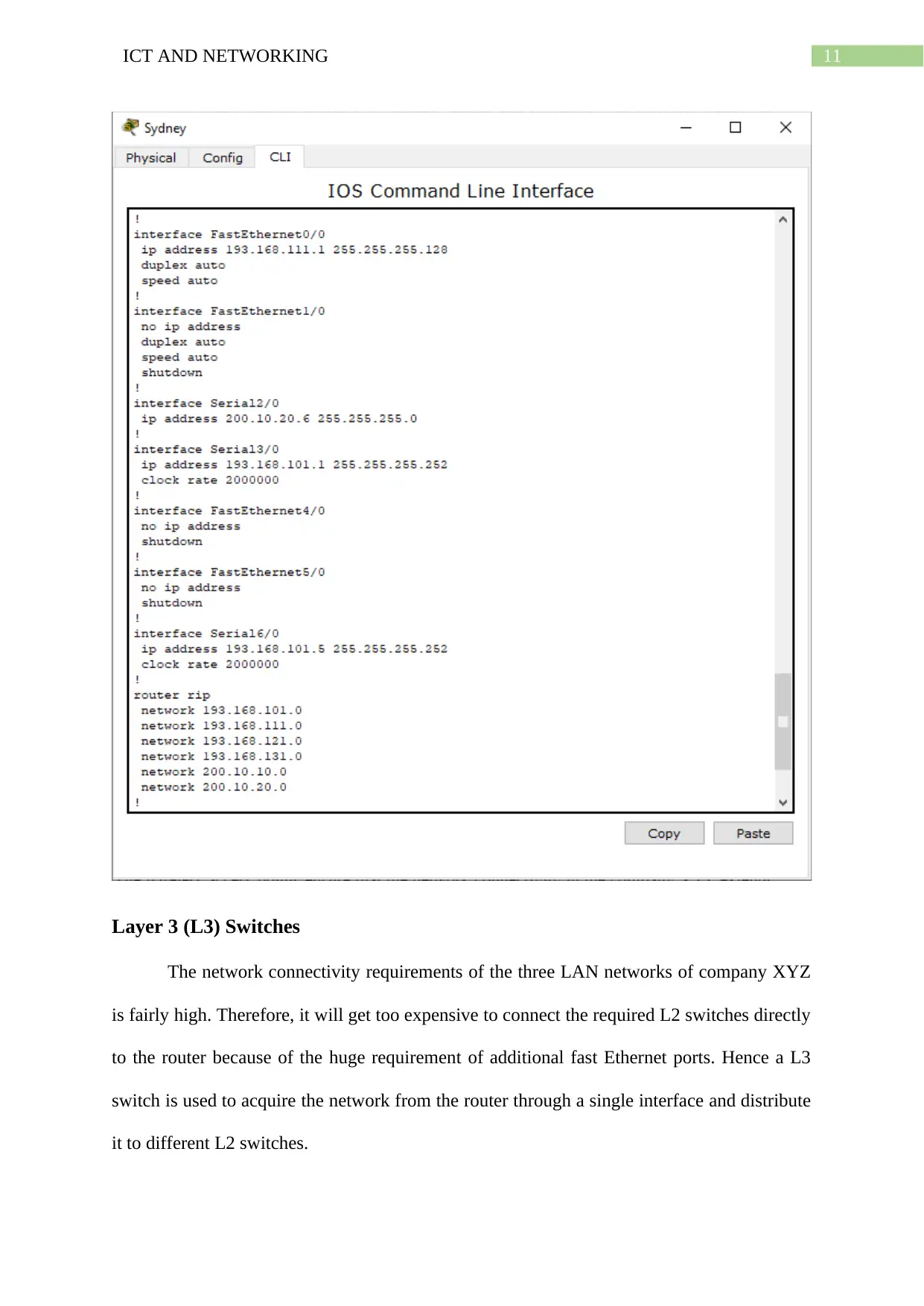
Routers
The routers are the primary networking device that is enabling the effective routing of
the network from each network segment to another. The ISP router, the Sydney router, the
Melbourne router and the Adelaide router are connected over a WAN network through serial
interfaces by using the RIP dynamic routing protocol. The company routers then go on to
connect the host devices of their respective LAN networks through the fast Ethernet
interfaces. The configuration of the Sydney router is given in the next screenshot.
network addresses 193.168.111.0, 193.168.121.0 and 193.168.131.0 are used in the private
LAN networks of Sydney, Melbourne and Adelaide respectively.
Networking Hardware
Routers
The routers are the primary networking device that is enabling the effective routing of
the network from each network segment to another. The ISP router, the Sydney router, the
Melbourne router and the Adelaide router are connected over a WAN network through serial
interfaces by using the RIP dynamic routing protocol. The company routers then go on to
connect the host devices of their respective LAN networks through the fast Ethernet
interfaces. The configuration of the Sydney router is given in the next screenshot.
11ICT AND NETWORKING
Layer 3 (L3) Switches
The network connectivity requirements of the three LAN networks of company XYZ
is fairly high. Therefore, it will get too expensive to connect the required L2 switches directly
to the router because of the huge requirement of additional fast Ethernet ports. Hence a L3
switch is used to acquire the network from the router through a single interface and distribute
it to different L2 switches.
Layer 3 (L3) Switches
The network connectivity requirements of the three LAN networks of company XYZ
is fairly high. Therefore, it will get too expensive to connect the required L2 switches directly
to the router because of the huge requirement of additional fast Ethernet ports. Hence a L3
switch is used to acquire the network from the router through a single interface and distribute
it to different L2 switches.

12ICT AND NETWORKING
Layer 2 (L2) Switches
The L2 switches are used to directly connect the host devices. The L2 switches used
in the network can support a maximum of 24 Ethernet ports. Therefore, the networks of the
branches at Sydney, Melbourne will both be requiring 3 L2 switches to connect 63 and 53
host devices respectively while the network of the Adelaide branch will require 2 L2 switches
to connect its 43 hosts.
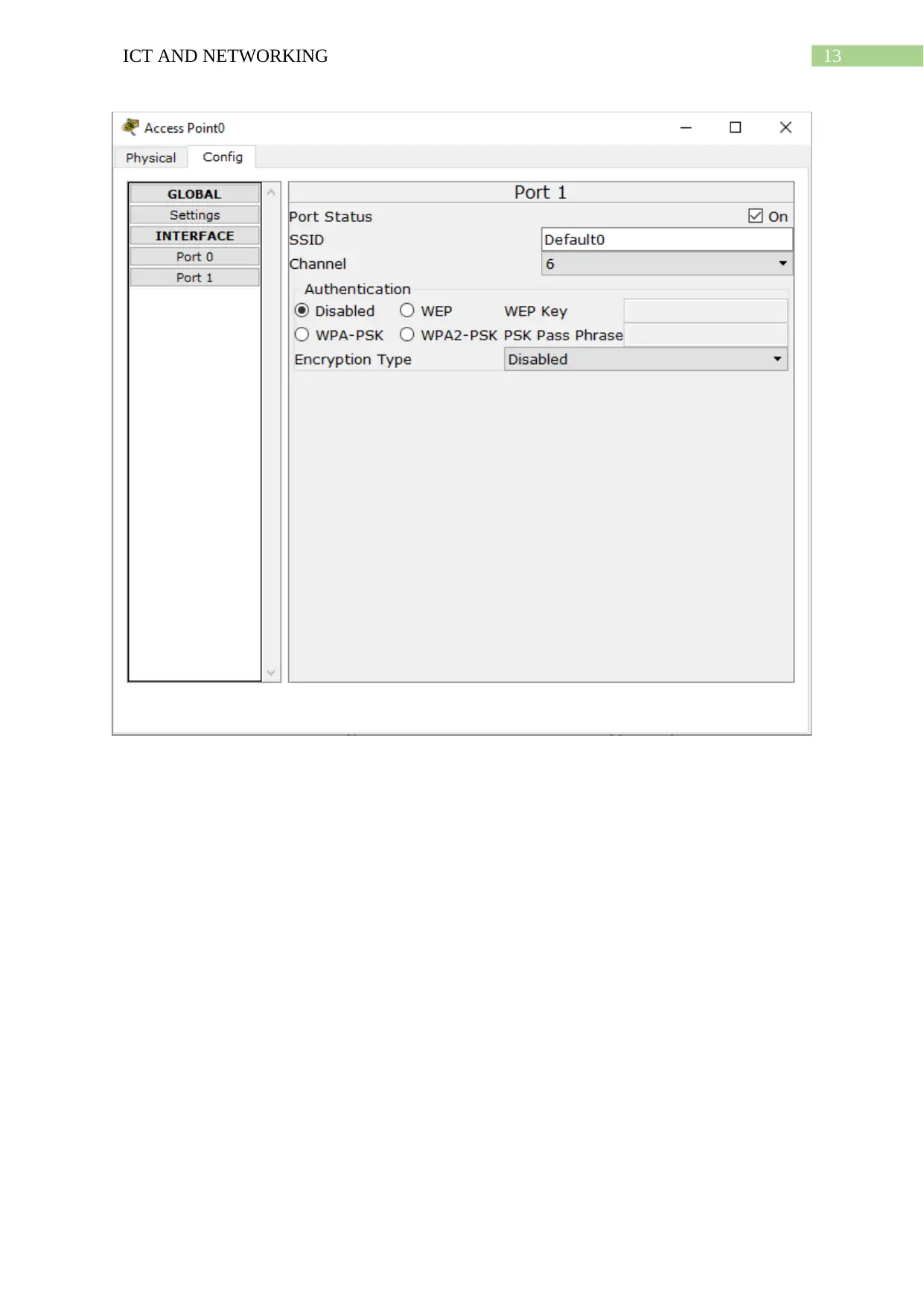
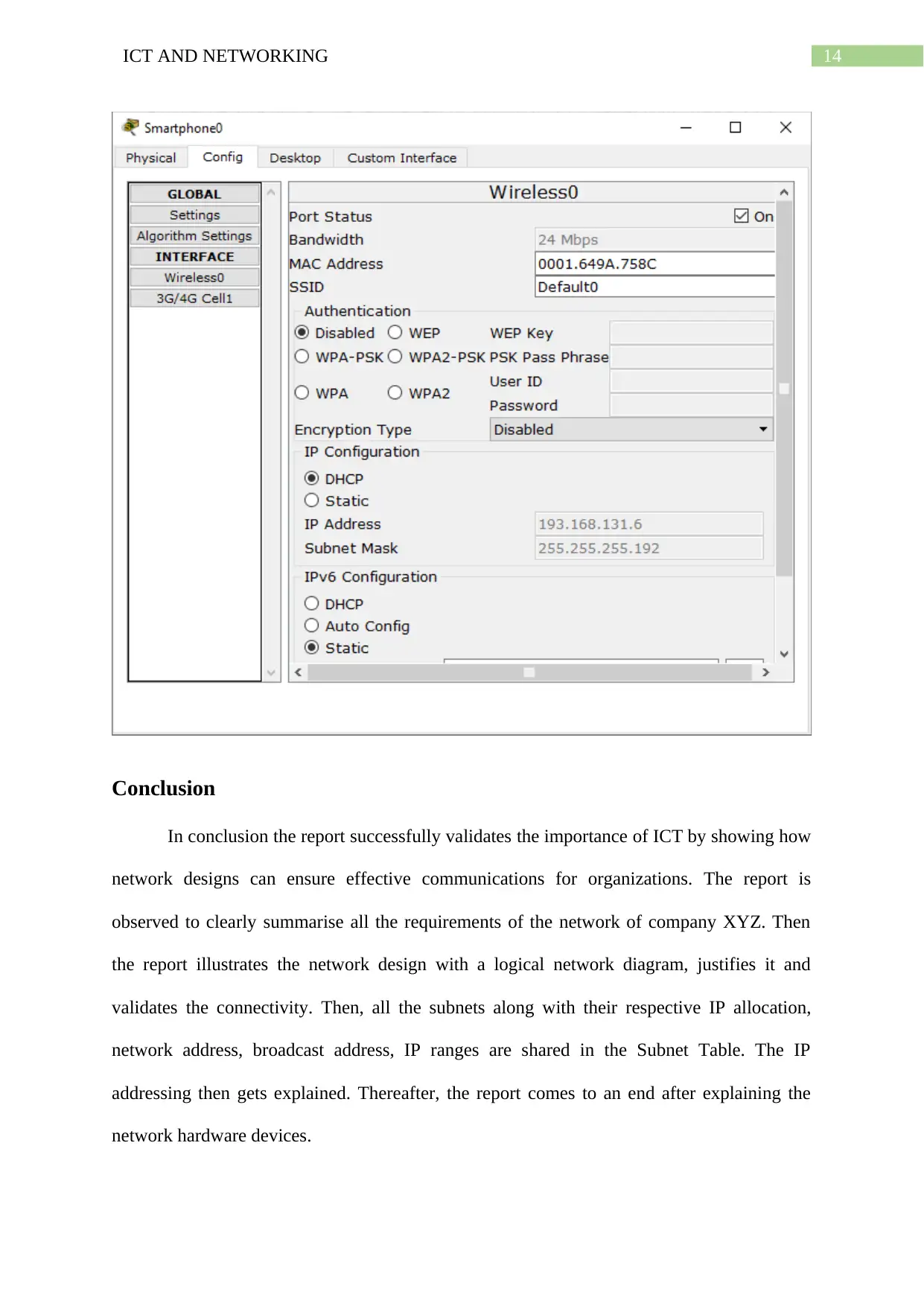
Wireless Access Points
The wireless access points ensure that the network connectivity in the company XYZ
extends from the fixed networking devices and hosts to devices that support or prefer wireless
connections like laptops or smart phones (VanSickle, Abegaz and Payne 2019). The network
diagram shows how the access points of each LAN network are providing connections to the
smartphones in the specific branch. The access points connect to the specific smartphones by
having matching the SSID names.
Layer 2 (L2) Switches
The L2 switches are used to directly connect the host devices. The L2 switches used
in the network can support a maximum of 24 Ethernet ports. Therefore, the networks of the
branches at Sydney, Melbourne will both be requiring 3 L2 switches to connect 63 and 53
host devices respectively while the network of the Adelaide branch will require 2 L2 switches
to connect its 43 hosts.
Wireless Access Points
The wireless access points ensure that the network connectivity in the company XYZ
extends from the fixed networking devices and hosts to devices that support or prefer wireless
connections like laptops or smart phones (VanSickle, Abegaz and Payne 2019). The network
diagram shows how the access points of each LAN network are providing connections to the
smartphones in the specific branch. The access points connect to the specific smartphones by
having matching the SSID names.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13ICT AND NETWORKING
14ICT AND NETWORKING
Conclusion
In conclusion the report successfully validates the importance of ICT by showing how
network designs can ensure effective communications for organizations. The report is
observed to clearly summarise all the requirements of the network of company XYZ. Then
the report illustrates the network design with a logical network diagram, justifies it and
validates the connectivity. Then, all the subnets along with their respective IP allocation,
network address, broadcast address, IP ranges are shared in the Subnet Table. The IP
addressing then gets explained. Thereafter, the report comes to an end after explaining the
network hardware devices.
Conclusion
In conclusion the report successfully validates the importance of ICT by showing how
network designs can ensure effective communications for organizations. The report is
observed to clearly summarise all the requirements of the network of company XYZ. Then
the report illustrates the network design with a logical network diagram, justifies it and
validates the connectivity. Then, all the subnets along with their respective IP allocation,
network address, broadcast address, IP ranges are shared in the Subnet Table. The IP
addressing then gets explained. Thereafter, the report comes to an end after explaining the
network hardware devices.

15ICT AND NETWORKING
Bibliography
Fondo-Ferreiro, P., Rodríguez-Pérez, M., Fernández-Veiga, M. and Herrería-Alonso, S.,
2018. Matching SDN and legacy networking hardware for energy efficiency and bounded
delay. Sensors, 18(11), p.3915.
Habibullah, K.M., Rondeau, E. and Georges, J.P., 2018. Reducing energy consumption of
network infrastructure using spectral approach. In Technology for Smart Futures (pp. 235-
250). Springer, Cham.
Huitao, W., Ruopeng, Y. and Xiaofei, Z., 2019, April. Research on IP Address Allocation of
Tactical Communication Network. In Journal of Physics: Conference Series (Vol. 1187, No.
4, p. 042105). IOP Publishing.
Rosewell, J., Kear, K., Jones, A., Smith, A., Donelan, H., Mikroyannidis, A., Peasgood, A.,
Sanders, C., Third, A., Wermelinger, M. and Moss, N., 2018. Open Networking Lab: online
practical learning of computer networking.
Shirmarz, A. and Sabaei, M., 2016. Evaluation and Comparison of binary trie base IP Lookup
Algorithms with real Edge Router IP prefix Dataset. Evaluation, 7(6).
Toor, A.S. and Jain, A.K., 2017. A survey on wireless network simulators. Bulletin of
Electrical Engineering and Informatics, 6(1), pp.62-69.
VanSickle, R., Abegaz, T. and Payne, B., 2019. Effectiveness of Tools in Identifying Rogue
Access Points on a Wireless Network.
Villanueva, L. and Gustilo, R.C., 2018. Artificial neural network based antenna sensitivity
assignments for chaotic Internet Service Provider network architecture. International Journal
of Engineering and Technology (UAE), 7(2), pp.14-17.
Bibliography
Fondo-Ferreiro, P., Rodríguez-Pérez, M., Fernández-Veiga, M. and Herrería-Alonso, S.,
2018. Matching SDN and legacy networking hardware for energy efficiency and bounded
delay. Sensors, 18(11), p.3915.
Habibullah, K.M., Rondeau, E. and Georges, J.P., 2018. Reducing energy consumption of
network infrastructure using spectral approach. In Technology for Smart Futures (pp. 235-
250). Springer, Cham.
Huitao, W., Ruopeng, Y. and Xiaofei, Z., 2019, April. Research on IP Address Allocation of
Tactical Communication Network. In Journal of Physics: Conference Series (Vol. 1187, No.
4, p. 042105). IOP Publishing.
Rosewell, J., Kear, K., Jones, A., Smith, A., Donelan, H., Mikroyannidis, A., Peasgood, A.,
Sanders, C., Third, A., Wermelinger, M. and Moss, N., 2018. Open Networking Lab: online
practical learning of computer networking.
Shirmarz, A. and Sabaei, M., 2016. Evaluation and Comparison of binary trie base IP Lookup
Algorithms with real Edge Router IP prefix Dataset. Evaluation, 7(6).
Toor, A.S. and Jain, A.K., 2017. A survey on wireless network simulators. Bulletin of
Electrical Engineering and Informatics, 6(1), pp.62-69.
VanSickle, R., Abegaz, T. and Payne, B., 2019. Effectiveness of Tools in Identifying Rogue
Access Points on a Wireless Network.
Villanueva, L. and Gustilo, R.C., 2018. Artificial neural network based antenna sensitivity
assignments for chaotic Internet Service Provider network architecture. International Journal
of Engineering and Technology (UAE), 7(2), pp.14-17.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16ICT AND NETWORKING
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





