Contribute to Copyright, Ethics & Privacy
VerifiedAdded on 2020/03/23
|24
|5679
|453
AI Summary
This assignment focuses on the 'Code of Conduct' for students at a specific educational institution (NIT). It outlines expectations for student behaviour in various contexts, including academic integrity, classroom conduct, computer lab usage, and addressing potential misconduct. Students are expected to demonstrate understanding of these guidelines and their importance in maintaining a respectful and ethical learning environment.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
Assessment 2: Privacy and ethics in an IT environment
Unit and Assessment Details
Assessment Title Protect Intellectual Property, Contribute to Copyright Policy and
Protect Rights of Stakeholders
Unit/Cluster Code ICTICT418
Unit/Cluster Title Contribute to copyright, ethics and privacy in an ICT environment
Course Code Title
ICT50415 Diploma of Information Technology Networking
ICT40415 Certificate 4 in Information Technology Networking
ICT50115 Diploma of Information Technology
Assessor Name Vidhu Bhardwaj
Assessment Date/Due Date As per LMS
Assessment Instructions for Students
1. This assessment involves completing seven (7) tasks.
2. If you require any clarification or support to complete this assessment, ask your assessor.
3. For a satisfactory result in this assessment, you must successfully complete ALL tasks to a
satisfactory standard.
4. Your assessor will assess you individually for each assessment task in this assessment.
Plagiarism, collusion and cheating are strictly prohibited [see NIT Student Handbook Section
13.10].
5. Support is available for students with special needs or learning difficulties. If you require any
support or modified equipment to complete this assessment, please ask your assessor.
6. Make sure you check grammar and spellings in your assessment before submission.
7. You must submit all completed assessment work to your assessor by the assessment due date.
8. You must keep a copy of all submitted work.
9. Please use the following naming convention when saving and submitting your assessments:
Required Resources and Tools
The following resources and tools are required to complete this assessment and will be made
available to you at the time of assessment:
1. Computer Lab (Computers, Word processing software, Internet access)
2. Access to relevant policies and legislation
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 1 of 24
privacy in an ICT environment
Assessment 2: Privacy and ethics in an IT environment
Unit and Assessment Details
Assessment Title Protect Intellectual Property, Contribute to Copyright Policy and
Protect Rights of Stakeholders
Unit/Cluster Code ICTICT418
Unit/Cluster Title Contribute to copyright, ethics and privacy in an ICT environment
Course Code Title
ICT50415 Diploma of Information Technology Networking
ICT40415 Certificate 4 in Information Technology Networking
ICT50115 Diploma of Information Technology
Assessor Name Vidhu Bhardwaj
Assessment Date/Due Date As per LMS
Assessment Instructions for Students
1. This assessment involves completing seven (7) tasks.
2. If you require any clarification or support to complete this assessment, ask your assessor.
3. For a satisfactory result in this assessment, you must successfully complete ALL tasks to a
satisfactory standard.
4. Your assessor will assess you individually for each assessment task in this assessment.
Plagiarism, collusion and cheating are strictly prohibited [see NIT Student Handbook Section
13.10].
5. Support is available for students with special needs or learning difficulties. If you require any
support or modified equipment to complete this assessment, please ask your assessor.
6. Make sure you check grammar and spellings in your assessment before submission.
7. You must submit all completed assessment work to your assessor by the assessment due date.
8. You must keep a copy of all submitted work.
9. Please use the following naming convention when saving and submitting your assessments:
Required Resources and Tools
The following resources and tools are required to complete this assessment and will be made
available to you at the time of assessment:
1. Computer Lab (Computers, Word processing software, Internet access)
2. Access to relevant policies and legislation
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 1 of 24
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
Scenario
You are an IT consultantworking for ABC IT Companyand your manager (Trainer) has assigned
you a task of reviewing ABC IT Company’s Privacy Policy. The policy reassures its clients that the
data they collect from them will be used responsibly, and that the behaviour of their company,
employees and sub-contractors will comply with the Australian Privacy Act of 1988.
ABC IT Companyhas its Privacy Policy on its website. A copy of the policy is included below
(Refer to Appendix 1).You are required to review this policy and report on its compliance with
privacy legislation.
Task 1
Submit a report (minimum of 500 words) to your manager that critiques the Privacy Policy of IT
Consultants.
You should address the following questions in your report and add any further information you may
think is appropriate to complete Task 1.
1. Does ABC IT Company have a legal responsibility to have a Corporate Privacy Policy?
2. Map each paragraph of the ABC IT Company Policy statement to 1 or more of the 10
National Privacy Principles (NPPs).
3. Does this policy comply with the "10 Steps to Protecting Other People's Personal
Information" as outlined by the Office of the Privacy Commissioner? Explain why or why
not.
4. What alterations or additions would you make to this policy?
5. Does this privacy policy address relevant system security concerns in relation to maintaining
the integrity, confidentiality, and availability of information?
6. What suggestions do you have for ways that new work practices, resulting from the policy
update, could be implemented?
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 2 of 24
privacy in an ICT environment
Scenario
You are an IT consultantworking for ABC IT Companyand your manager (Trainer) has assigned
you a task of reviewing ABC IT Company’s Privacy Policy. The policy reassures its clients that the
data they collect from them will be used responsibly, and that the behaviour of their company,
employees and sub-contractors will comply with the Australian Privacy Act of 1988.
ABC IT Companyhas its Privacy Policy on its website. A copy of the policy is included below
(Refer to Appendix 1).You are required to review this policy and report on its compliance with
privacy legislation.
Task 1
Submit a report (minimum of 500 words) to your manager that critiques the Privacy Policy of IT
Consultants.
You should address the following questions in your report and add any further information you may
think is appropriate to complete Task 1.
1. Does ABC IT Company have a legal responsibility to have a Corporate Privacy Policy?
2. Map each paragraph of the ABC IT Company Policy statement to 1 or more of the 10
National Privacy Principles (NPPs).
3. Does this policy comply with the "10 Steps to Protecting Other People's Personal
Information" as outlined by the Office of the Privacy Commissioner? Explain why or why
not.
4. What alterations or additions would you make to this policy?
5. Does this privacy policy address relevant system security concerns in relation to maintaining
the integrity, confidentiality, and availability of information?
6. What suggestions do you have for ways that new work practices, resulting from the policy
update, could be implemented?
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 2 of 24

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
Introduction:
ABC is a highly committed Privacy Policy that protects the privacy while interacting with the clients,
services and products. The following report provides responses to various queries criticizing the privacy
policies of the IT consultants.
1. Legal responsibility of ABC:
The ABC definitely possesses legal responsibilities to possess the Corporate Privacy Policies. To
deliver the services to the users, ABC has been transparent regarding how and why they gather
data of the users. In many situations, as the user never wants them to use their information, they
are provided with the scopes to state so.
2. Mapping every paragraph of the ABC IT Company Policy statement to 1 or
more of the 10 NPPs:
The policy statements have been in alignment with the National Privacy Principles (NPPs). The
policy has been explaining the following:
How and why they have been collecting and using the extra information while visiting the
shop of ABC.
The type of data ABC has been collecting about the users, how they have been collecting
that and how to use that
The way they could disclose the data
The way they could access the data they have been holding about them
The time they could use the data for contacting them
The use of cookies of ABC to gather data and how they could delete or manage those
cookies
Extra steps for protecting the young people
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 3 of 24
privacy in an ICT environment
Introduction:
ABC is a highly committed Privacy Policy that protects the privacy while interacting with the clients,
services and products. The following report provides responses to various queries criticizing the privacy
policies of the IT consultants.
1. Legal responsibility of ABC:
The ABC definitely possesses legal responsibilities to possess the Corporate Privacy Policies. To
deliver the services to the users, ABC has been transparent regarding how and why they gather
data of the users. In many situations, as the user never wants them to use their information, they
are provided with the scopes to state so.
2. Mapping every paragraph of the ABC IT Company Policy statement to 1 or
more of the 10 NPPs:
The policy statements have been in alignment with the National Privacy Principles (NPPs). The
policy has been explaining the following:
How and why they have been collecting and using the extra information while visiting the
shop of ABC.
The type of data ABC has been collecting about the users, how they have been collecting
that and how to use that
The way they could disclose the data
The way they could access the data they have been holding about them
The time they could use the data for contacting them
The use of cookies of ABC to gather data and how they could delete or manage those
cookies
Extra steps for protecting the young people
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 3 of 24

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
3. Complying with the "10 Steps to Protecting Other People's Personal
Information":
The policies has been complying with the steps as their aim has been deliver the users the media
experiences that has been informing, entertaining and educating. At few cases they have been
using data provided to ABC from the users about themselves in customizing the experiences.
4. The additions or alterations needed to this policy:
The policy has been only applicable to ABC. This has never been applicable to other organizations or
companies. This has been including the digital services having links to the services or contents of ABC.
The third party services having links to the ABC services or documents have been governing the usage of
the personal data submitted to them. This has been also including the collection through the cookies as the
users use or visits them. They have never been accepting any liability or responsibility for the practices of
privacy of the digital services of the third party.
5. The relevant concerns of system security addressed by the privacy policy:
The policy has been applicable to the ABC shops. This is the multichannel retailer storing throughout
Australia and including the online shopping.
6. Suggestions for the ways of practices of new work:
The information provided by the users should include the personal data that is needed. This must
also include the personal data which has been optional. Lastly permissions must be made while
asked about the agreement of any specific activity.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 4 of 24
privacy in an ICT environment
3. Complying with the "10 Steps to Protecting Other People's Personal
Information":
The policies has been complying with the steps as their aim has been deliver the users the media
experiences that has been informing, entertaining and educating. At few cases they have been
using data provided to ABC from the users about themselves in customizing the experiences.
4. The additions or alterations needed to this policy:
The policy has been only applicable to ABC. This has never been applicable to other organizations or
companies. This has been including the digital services having links to the services or contents of ABC.
The third party services having links to the ABC services or documents have been governing the usage of
the personal data submitted to them. This has been also including the collection through the cookies as the
users use or visits them. They have never been accepting any liability or responsibility for the practices of
privacy of the digital services of the third party.
5. The relevant concerns of system security addressed by the privacy policy:
The policy has been applicable to the ABC shops. This is the multichannel retailer storing throughout
Australia and including the online shopping.
6. Suggestions for the ways of practices of new work:
The information provided by the users should include the personal data that is needed. This must
also include the personal data which has been optional. Lastly permissions must be made while
asked about the agreement of any specific activity.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 4 of 24
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
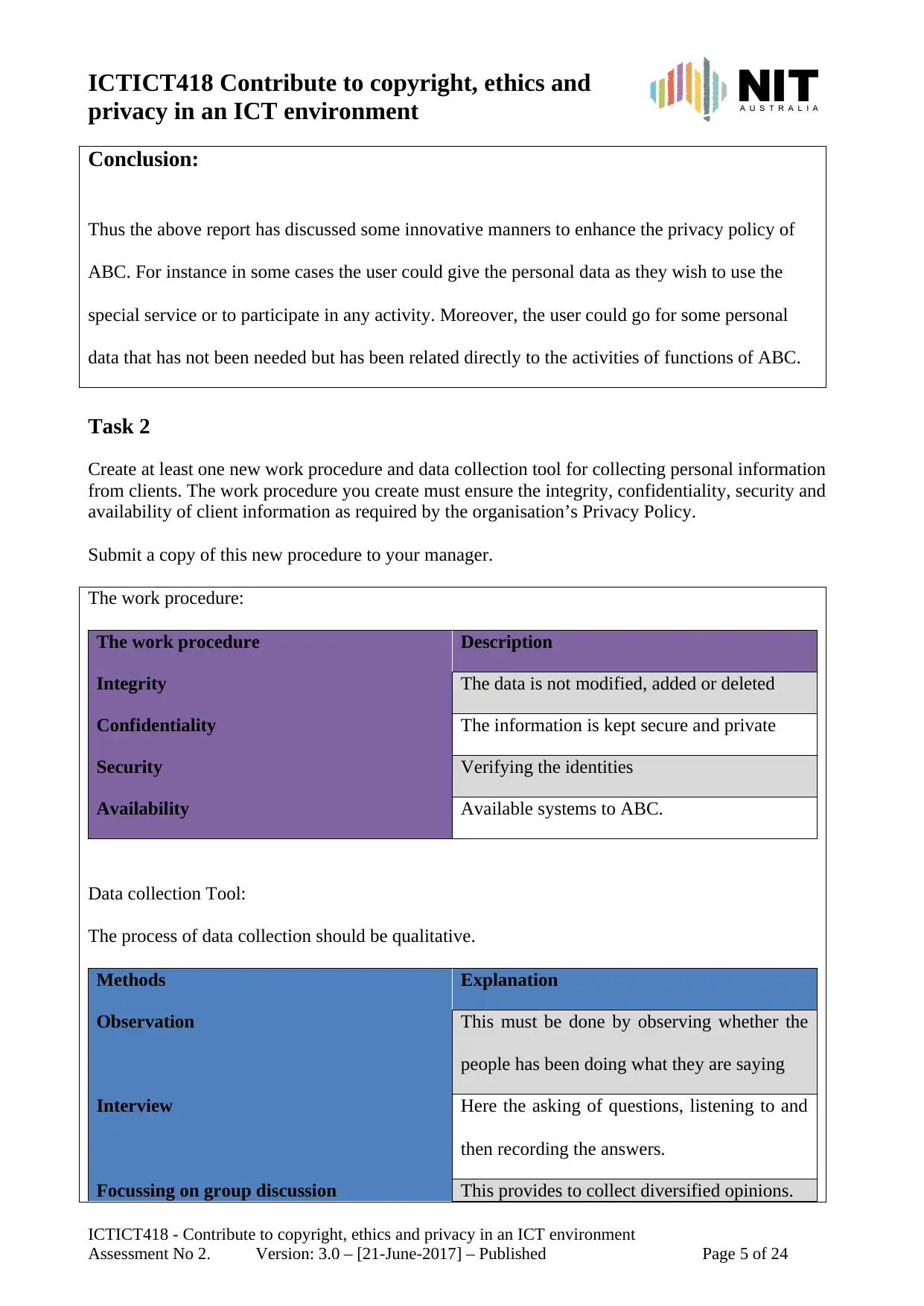
Conclusion:
Thus the above report has discussed some innovative manners to enhance the privacy policy of
ABC. For instance in some cases the user could give the personal data as they wish to use the
special service or to participate in any activity. Moreover, the user could go for some personal
data that has not been needed but has been related directly to the activities of functions of ABC.
Task 2
Create at least one new work procedure and data collection tool for collecting personal information
from clients. The work procedure you create must ensure the integrity, confidentiality, security and
availability of client information as required by the organisation’s Privacy Policy.
Submit a copy of this new procedure to your manager.
The work procedure:
The work procedure Description
Integrity The data is not modified, added or deleted
Confidentiality The information is kept secure and private
Security Verifying the identities
Availability Available systems to ABC.
Data collection Tool:
The process of data collection should be qualitative.
Methods Explanation
Observation This must be done by observing whether the
people has been doing what they are saying
Interview Here the asking of questions, listening to and
then recording the answers.
Focussing on group discussion This provides to collect diversified opinions.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 5 of 24
privacy in an ICT environment
Conclusion:
Thus the above report has discussed some innovative manners to enhance the privacy policy of
ABC. For instance in some cases the user could give the personal data as they wish to use the
special service or to participate in any activity. Moreover, the user could go for some personal
data that has not been needed but has been related directly to the activities of functions of ABC.
Task 2
Create at least one new work procedure and data collection tool for collecting personal information
from clients. The work procedure you create must ensure the integrity, confidentiality, security and
availability of client information as required by the organisation’s Privacy Policy.
Submit a copy of this new procedure to your manager.
The work procedure:
The work procedure Description
Integrity The data is not modified, added or deleted
Confidentiality The information is kept secure and private
Security Verifying the identities
Availability Available systems to ABC.
Data collection Tool:
The process of data collection should be qualitative.
Methods Explanation
Observation This must be done by observing whether the
people has been doing what they are saying
Interview Here the asking of questions, listening to and
then recording the answers.
Focussing on group discussion This provides to collect diversified opinions.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 5 of 24

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
The other methods This includes the life history, ranking and the
rapid assessment procedure.
Task 3
Implement the new work procedure that you created in Task 2 as a trial to collect personal
information from at least three clients.
Create and submit a report (minimum 300 words) to your manager outlining the results of your trial.
You should address any information integrity, confidentiality, system security and availability
issues identified in the work practices identified during your trial. You may also include any other
relevant information you feel is appropriate to complete this task.
The following study addresses the information integrity, availability issues, system securities and
confidentialities recognized in the working practices recognized in the trials.
As per as the integrity is concerned some of the data must include the checksums. The
cryptographic checksums could be also considered to verify the integrity. The redundancies or
backups should be available for restoring the data affected to the proper state. The safeguarding
of the data confidentiality could include the specialized training for the privacy of those
documents. These trainings could include the security risks threatening the information.
Moreover the aspects of the training can include the strong passwords or the best practices related
to password and data about the social-engineering methods. This is to prevent them from bending
the rules of data-handling with proper intentions and the disastrous results. Moreover the users
could take precautions for minimizing the number of spaces where the data could appear and the
amount of time actually transmitted for completing the needed transaction. Additional measures
could be considered for the case of highly sensitive documents. This might also include the
precautions like storing only in the disconnected storage devices, air applied computers for the
huge sensitive data in the format of hard copy only. For the availability a copy of backup could
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 6 of 24
privacy in an ICT environment
The other methods This includes the life history, ranking and the
rapid assessment procedure.
Task 3
Implement the new work procedure that you created in Task 2 as a trial to collect personal
information from at least three clients.
Create and submit a report (minimum 300 words) to your manager outlining the results of your trial.
You should address any information integrity, confidentiality, system security and availability
issues identified in the work practices identified during your trial. You may also include any other
relevant information you feel is appropriate to complete this task.
The following study addresses the information integrity, availability issues, system securities and
confidentialities recognized in the working practices recognized in the trials.
As per as the integrity is concerned some of the data must include the checksums. The
cryptographic checksums could be also considered to verify the integrity. The redundancies or
backups should be available for restoring the data affected to the proper state. The safeguarding
of the data confidentiality could include the specialized training for the privacy of those
documents. These trainings could include the security risks threatening the information.
Moreover the aspects of the training can include the strong passwords or the best practices related
to password and data about the social-engineering methods. This is to prevent them from bending
the rules of data-handling with proper intentions and the disastrous results. Moreover the users
could take precautions for minimizing the number of spaces where the data could appear and the
amount of time actually transmitted for completing the needed transaction. Additional measures
could be considered for the case of highly sensitive documents. This might also include the
precautions like storing only in the disconnected storage devices, air applied computers for the
huge sensitive data in the format of hard copy only. For the availability a copy of backup could
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 6 of 24

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
be stored in the location that is isolated geographically. Moreover regarding the system security
the softwares like proxy servers and firewalls could protect against the unreachable data and the
downtime because of some malicious actions like network intrusions and DoS Attacks.
Besides all these, the data encryption is the general process to ensure the confidentiality. The
other options could be the security tokens, biometric verification and the soft tokens. Moreover,
the users could take preventions for minimizing the number of places where the data has been
appearing and the time it could be transmitted actually to finish the needed transaction.
Scenario
Sandra, your manager (Trainer) at Solutions One had the following to say about ethics, standards
and legislation:
Great work! Mr Fields was impressed with how you addressed all his concerns. Let’s see
what else we can do to help Solutions1 employees maintain ethical conduct.
Firstly, the team would like to know more about legislation and industry standards. Can
you identify all the legislation and industry standards that apply to our area of work, and
explain how each fits in with what we do?
This recent experience has highlighted the need for a grievance procedure so that staff
and clients can feel confident to raise confidential or sensitive matters with management.
Finally, we need to have a code of conduct in place within the organisation — this will be a useful
tool to get everyone up to speed on the professional standards we must all adhere to
Sandra has allocated the following tasks to you:
Task 4
Locate a relevant industry code of ethics and deliver a short 5 minutes’ presentation to the team
(your class) that discusses one or more of the practices listed in the code. Your presentation must
provide two examples of situations in which the ethical practice would apply.
The presentation slides are provided below:
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 7 of 24
privacy in an ICT environment
be stored in the location that is isolated geographically. Moreover regarding the system security
the softwares like proxy servers and firewalls could protect against the unreachable data and the
downtime because of some malicious actions like network intrusions and DoS Attacks.
Besides all these, the data encryption is the general process to ensure the confidentiality. The
other options could be the security tokens, biometric verification and the soft tokens. Moreover,
the users could take preventions for minimizing the number of places where the data has been
appearing and the time it could be transmitted actually to finish the needed transaction.
Scenario
Sandra, your manager (Trainer) at Solutions One had the following to say about ethics, standards
and legislation:
Great work! Mr Fields was impressed with how you addressed all his concerns. Let’s see
what else we can do to help Solutions1 employees maintain ethical conduct.
Firstly, the team would like to know more about legislation and industry standards. Can
you identify all the legislation and industry standards that apply to our area of work, and
explain how each fits in with what we do?
This recent experience has highlighted the need for a grievance procedure so that staff
and clients can feel confident to raise confidential or sensitive matters with management.
Finally, we need to have a code of conduct in place within the organisation — this will be a useful
tool to get everyone up to speed on the professional standards we must all adhere to
Sandra has allocated the following tasks to you:
Task 4
Locate a relevant industry code of ethics and deliver a short 5 minutes’ presentation to the team
(your class) that discusses one or more of the practices listed in the code. Your presentation must
provide two examples of situations in which the ethical practice would apply.
The presentation slides are provided below:
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 7 of 24
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 8 of 24
privacy in an ICT environment
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 8 of 24

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 9 of 24
privacy in an ICT environment
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 9 of 24
ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 10 of 24
privacy in an ICT environment
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 10 of 24
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
Task 5
a. Develop a new ethical work procedure to implement one principle or a value from any relevant
industry code of ethics or code of professional conduct followed within the IT industry. Present
and explain this procedure to your manager (Trainer) and team (your class) to obtain feedback
on the procedure ensuring application of the code.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 11 of 24
privacy in an ICT environment
Task 5
a. Develop a new ethical work procedure to implement one principle or a value from any relevant
industry code of ethics or code of professional conduct followed within the IT industry. Present
and explain this procedure to your manager (Trainer) and team (your class) to obtain feedback
on the procedure ensuring application of the code.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 11 of 24
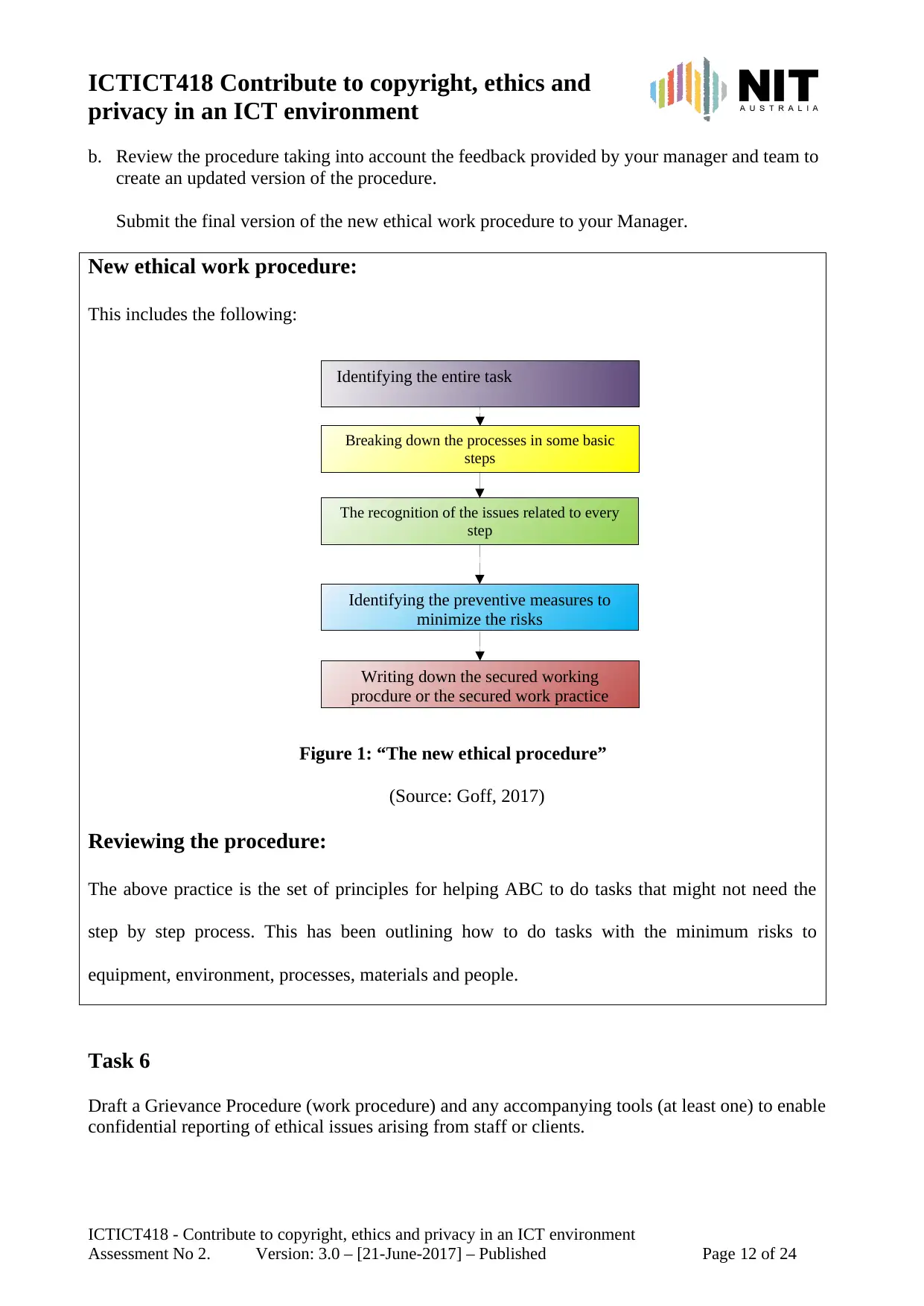
Identifying the entire task
Breaking down the processes in some basic
steps
The recognition of the issues related to every
step
Identifying the preventive measures to
minimize the risks
Writing down the secured working
procdure or the secured work practice
ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
b. Review the procedure taking into account the feedback provided by your manager and team to
create an updated version of the procedure.
Submit the final version of the new ethical work procedure to your Manager.
New ethical work procedure:
This includes the following:
Figure 1: “The new ethical procedure”
(Source: Goff, 2017)
Reviewing the procedure:
The above practice is the set of principles for helping ABC to do tasks that might not need the
step by step process. This has been outlining how to do tasks with the minimum risks to
equipment, environment, processes, materials and people.
Task 6
Draft a Grievance Procedure (work procedure) and any accompanying tools (at least one) to enable
confidential reporting of ethical issues arising from staff or clients.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 12 of 24
Breaking down the processes in some basic
steps
The recognition of the issues related to every
step
Identifying the preventive measures to
minimize the risks
Writing down the secured working
procdure or the secured work practice
ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
b. Review the procedure taking into account the feedback provided by your manager and team to
create an updated version of the procedure.
Submit the final version of the new ethical work procedure to your Manager.
New ethical work procedure:
This includes the following:
Figure 1: “The new ethical procedure”
(Source: Goff, 2017)
Reviewing the procedure:
The above practice is the set of principles for helping ABC to do tasks that might not need the
step by step process. This has been outlining how to do tasks with the minimum risks to
equipment, environment, processes, materials and people.
Task 6
Draft a Grievance Procedure (work procedure) and any accompanying tools (at least one) to enable
confidential reporting of ethical issues arising from staff or clients.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 12 of 24
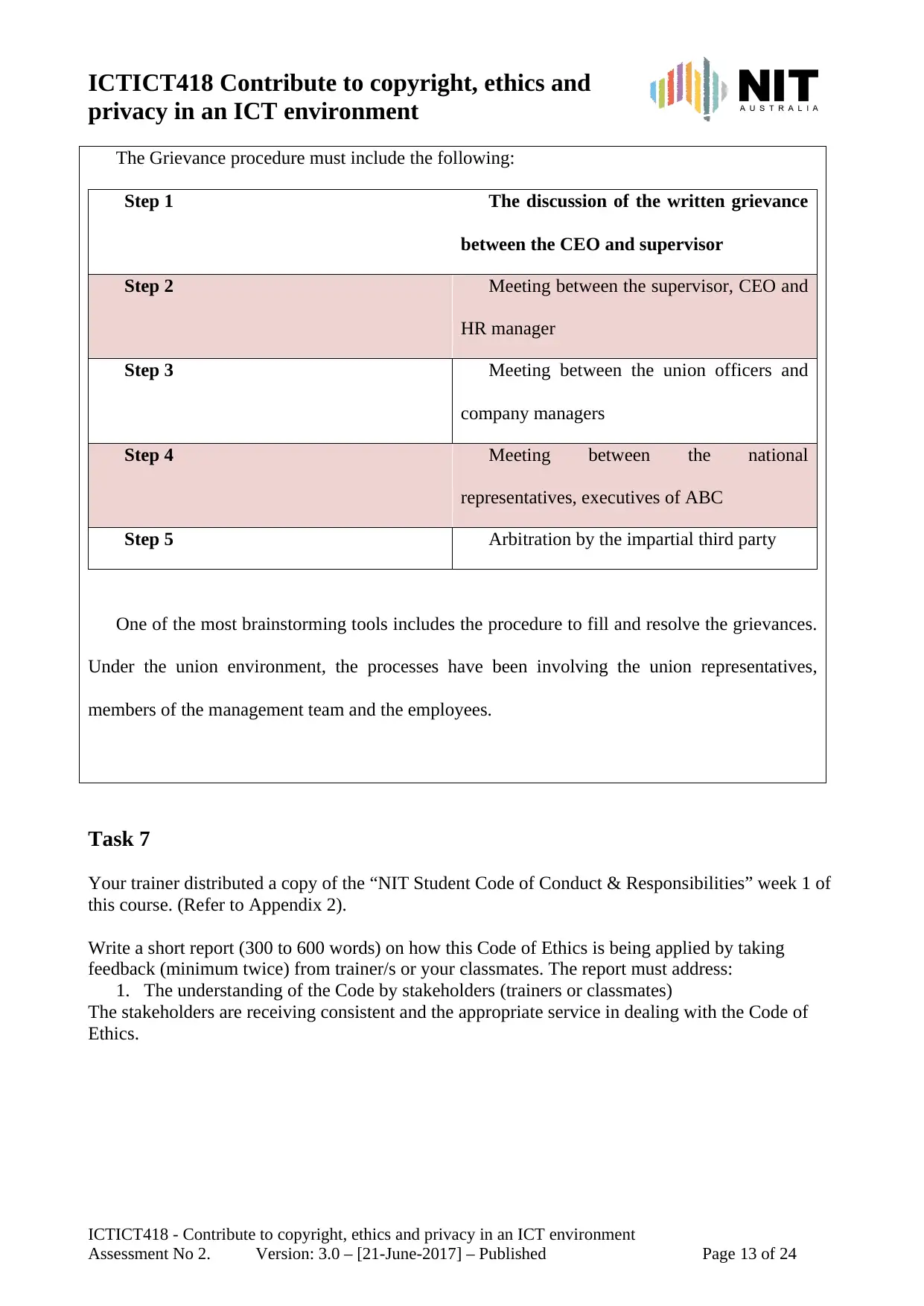
ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
The Grievance procedure must include the following:
Step 1 The discussion of the written grievance
between the CEO and supervisor
Step 2 Meeting between the supervisor, CEO and
HR manager
Step 3 Meeting between the union officers and
company managers
Step 4 Meeting between the national
representatives, executives of ABC
Step 5 Arbitration by the impartial third party
One of the most brainstorming tools includes the procedure to fill and resolve the grievances.
Under the union environment, the processes have been involving the union representatives,
members of the management team and the employees.
Task 7
Your trainer distributed a copy of the “NIT Student Code of Conduct & Responsibilities” week 1 of
this course. (Refer to Appendix 2).
Write a short report (300 to 600 words) on how this Code of Ethics is being applied by taking
feedback (minimum twice) from trainer/s or your classmates. The report must address:
1. The understanding of the Code by stakeholders (trainers or classmates)
The stakeholders are receiving consistent and the appropriate service in dealing with the Code of
Ethics.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 13 of 24
privacy in an ICT environment
The Grievance procedure must include the following:
Step 1 The discussion of the written grievance
between the CEO and supervisor
Step 2 Meeting between the supervisor, CEO and
HR manager
Step 3 Meeting between the union officers and
company managers
Step 4 Meeting between the national
representatives, executives of ABC
Step 5 Arbitration by the impartial third party
One of the most brainstorming tools includes the procedure to fill and resolve the grievances.
Under the union environment, the processes have been involving the union representatives,
members of the management team and the employees.
Task 7
Your trainer distributed a copy of the “NIT Student Code of Conduct & Responsibilities” week 1 of
this course. (Refer to Appendix 2).
Write a short report (300 to 600 words) on how this Code of Ethics is being applied by taking
feedback (minimum twice) from trainer/s or your classmates. The report must address:
1. The understanding of the Code by stakeholders (trainers or classmates)
The stakeholders are receiving consistent and the appropriate service in dealing with the Code of
Ethics.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 13 of 24
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
Like most other things the strategy should begin with the people. These are described below.
Firstly, the stakeholders are needed to be identified. ABC could assume that the project goal
in mind and this is the first step for better collaboration in the process of approval.
Secondly, it must be identifies what has been at stake. All the stakeholders are included in the
project for various reasons. The roles are to be used and the advantages are been encouraged.
For instance as the user if working with the graphic designer, he must be included. This is
because the designer could be impacted by the decisions created in the conversations.
Thirdly, the languages of the stakeholders are needed to be identified. Making communication
with the stakeholders has been linked to their motivations. For instance, for the decision-
makers, all the projects are the investment as they have been responsible typically to allocate
the project resources.
Next, ABC has been setting specific expectations. As the stakeholders are known, what they
have been demanding and in what way they must be communicated, the user has been
articulating their expectations better for their inclusion. For instance, the SME or Subject
Matter Experts have known rightly when they require delivering the knowledge for the
project and also in what form and how the feedback must be delivered. The feedback is able
to double the time slot allotted for the project. Hence they have been as specific they could on
the way in which the feedback has been incorporated and evaluated.
Lastly the value of their input could be shown. One of the causes that the stakeholders could
be disappointed if they feel neglected. Thus helping the stakeholders to fetch how the input
was included or rejected has been vital. This has been making them the active part of the
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 14 of 24
privacy in an ICT environment
Like most other things the strategy should begin with the people. These are described below.
Firstly, the stakeholders are needed to be identified. ABC could assume that the project goal
in mind and this is the first step for better collaboration in the process of approval.
Secondly, it must be identifies what has been at stake. All the stakeholders are included in the
project for various reasons. The roles are to be used and the advantages are been encouraged.
For instance as the user if working with the graphic designer, he must be included. This is
because the designer could be impacted by the decisions created in the conversations.
Thirdly, the languages of the stakeholders are needed to be identified. Making communication
with the stakeholders has been linked to their motivations. For instance, for the decision-
makers, all the projects are the investment as they have been responsible typically to allocate
the project resources.
Next, ABC has been setting specific expectations. As the stakeholders are known, what they
have been demanding and in what way they must be communicated, the user has been
articulating their expectations better for their inclusion. For instance, the SME or Subject
Matter Experts have known rightly when they require delivering the knowledge for the
project and also in what form and how the feedback must be delivered. The feedback is able
to double the time slot allotted for the project. Hence they have been as specific they could on
the way in which the feedback has been incorporated and evaluated.
Lastly the value of their input could be shown. One of the causes that the stakeholders could
be disappointed if they feel neglected. Thus helping the stakeholders to fetch how the input
was included or rejected has been vital. This has been making them the active part of the
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 14 of 24

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
process of decision making. This is done without letting them make those decisions.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 15 of 24
privacy in an ICT environment
process of decision making. This is done without letting them make those decisions.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 15 of 24

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
Bibliography:
ABC Privacy Policy | About the ABC. (2017). About.abc.net.au. Retrieved 18 September 2017,
from http://about.abc.net.au/abc-privacy-policy/
Abdallah, A., & Shen, X. (2017). Lightweight security and privacy preserving scheme for smart
grid customer-side networks. IEEE Transactions on Smart Grid, 8(3), 1064-1074.
Amoore, L. (2014). Security and the claim to privacy. International Political Sociology, 8(1),
108-112.
Bohli, J. M., Gruschka, N., Jensen, M., Iacono, L. L., & Marnau, N. (2013). Security and
privacy-enhancing multicloud architectures. IEEE Transactions on Dependable and
Secure Computing, 10(4), 212-224.
Davies, N., Friday, A., Clinch, S., Sas, C., Langheinrich, M., Ward, G., & Schmidt, A. (2015).
Security and privacy implications of pervasive memory augmentation. IEEE Pervasive
Computing, 14(1), 44-53.
Goff, D. (2017). Implementing an Ethics Program in the Workplace. Info.knowledgeleader.com.
Retrieved 18 September 2017, from
http://info.knowledgeleader.com/bid/165219/implementing-an-ethics-program-in-the-
workplace
Kegel, R. H., & Wieringa, R. (2015, June). Behavior Change Support Systems for Privacy and
Security. In BCSS@ PERSUASIVE (pp. 51-55).
Manshaei, M. H., Zhu, Q., Alpcan, T., Bacşar, T., & Hubaux, J. P. (2013). Game theory meets
network security and privacy. ACM Computing Surveys (CSUR), 45(3), 25.
Razzaque, M. A., Salehi, A., & Cheraghi, S. M. (2013). Security and privacy in vehicular ad-
hoc networks: survey and the road ahead. Wireless Networks and Security, 107-132.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 16 of 24
privacy in an ICT environment
Bibliography:
ABC Privacy Policy | About the ABC. (2017). About.abc.net.au. Retrieved 18 September 2017,
from http://about.abc.net.au/abc-privacy-policy/
Abdallah, A., & Shen, X. (2017). Lightweight security and privacy preserving scheme for smart
grid customer-side networks. IEEE Transactions on Smart Grid, 8(3), 1064-1074.
Amoore, L. (2014). Security and the claim to privacy. International Political Sociology, 8(1),
108-112.
Bohli, J. M., Gruschka, N., Jensen, M., Iacono, L. L., & Marnau, N. (2013). Security and
privacy-enhancing multicloud architectures. IEEE Transactions on Dependable and
Secure Computing, 10(4), 212-224.
Davies, N., Friday, A., Clinch, S., Sas, C., Langheinrich, M., Ward, G., & Schmidt, A. (2015).
Security and privacy implications of pervasive memory augmentation. IEEE Pervasive
Computing, 14(1), 44-53.
Goff, D. (2017). Implementing an Ethics Program in the Workplace. Info.knowledgeleader.com.
Retrieved 18 September 2017, from
http://info.knowledgeleader.com/bid/165219/implementing-an-ethics-program-in-the-
workplace
Kegel, R. H., & Wieringa, R. (2015, June). Behavior Change Support Systems for Privacy and
Security. In BCSS@ PERSUASIVE (pp. 51-55).
Manshaei, M. H., Zhu, Q., Alpcan, T., Bacşar, T., & Hubaux, J. P. (2013). Game theory meets
network security and privacy. ACM Computing Surveys (CSUR), 45(3), 25.
Razzaque, M. A., Salehi, A., & Cheraghi, S. M. (2013). Security and privacy in vehicular ad-
hoc networks: survey and the road ahead. Wireless Networks and Security, 107-132.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 16 of 24
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
Roman, R., Zhou, J., & Lopez, J. (2013). On the features and challenges of security and privacy
in distributed internet of things. Computer Networks, 57(10), 2266-2279.
Sadeghi, A. R., Wachsmann, C., & Waidner, M. (2015, June). Security and privacy challenges
in industrial internet of things. In Design Automation Conference (DAC), 2015 52nd
ACM/EDAC/IEEE (pp. 1-6). IEEE.
Skarmeta, A. F., Hernandez-Ramos, J. L., & Moreno, M. V. (2014, March). A decentralized
approach for security and privacy challenges in the internet of things. In Internet of
Things (WF-IoT), 2014 IEEE World Forum on (pp. 67-72). IEEE.
Wei, L., Zhu, H., Cao, Z., Dong, X., Jia, W., Chen, Y., & Vasilakos, A. V. (2014). Security and
privacy for storage and computation in cloud computing. Information Sciences, 258,
371-386.
Winkler, T., & Rinner, B. (2014). Security and privacy protection in visual sensor networks: A
survey. ACM Computing Surveys (CSUR), 47(1), 2.
Yang, K., Zhang, K., Ren, J., & Shen, X. (2015). Security and privacy in mobile crowdsourcing
networks: challenges and opportunities. IEEE Communications Magazine, 53(8), 75-81.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 17 of 24
privacy in an ICT environment
Roman, R., Zhou, J., & Lopez, J. (2013). On the features and challenges of security and privacy
in distributed internet of things. Computer Networks, 57(10), 2266-2279.
Sadeghi, A. R., Wachsmann, C., & Waidner, M. (2015, June). Security and privacy challenges
in industrial internet of things. In Design Automation Conference (DAC), 2015 52nd
ACM/EDAC/IEEE (pp. 1-6). IEEE.
Skarmeta, A. F., Hernandez-Ramos, J. L., & Moreno, M. V. (2014, March). A decentralized
approach for security and privacy challenges in the internet of things. In Internet of
Things (WF-IoT), 2014 IEEE World Forum on (pp. 67-72). IEEE.
Wei, L., Zhu, H., Cao, Z., Dong, X., Jia, W., Chen, Y., & Vasilakos, A. V. (2014). Security and
privacy for storage and computation in cloud computing. Information Sciences, 258,
371-386.
Winkler, T., & Rinner, B. (2014). Security and privacy protection in visual sensor networks: A
survey. ACM Computing Surveys (CSUR), 47(1), 2.
Yang, K., Zhang, K., Ren, J., & Shen, X. (2015). Security and privacy in mobile crowdsourcing
networks: challenges and opportunities. IEEE Communications Magazine, 53(8), 75-81.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 17 of 24

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
Appendix 1 - ABC IT Company Privacy Policy
ABC IT Company respects the privacy of our Clients, Contractors, Employees and Suppliers. As
such we have taken appropriate steps to comply with the Australian Privacy Act of 1988. The
following policy outlines our commitment to adhering to this Act.
What Data Do We Collect?
ABC IT Company only collects data that is relevant to our business dealings. This includes
resumes, contact names, business addresses, email and Internet addresses, telephone and fax
numbers.
ABC IT Company does collect and store the financial records of our dealings with Clients, Sub
Contractors and Suppliers.
ABC IT Company does collect financial information relating to credit references with regards to
our Clients and Sub Contractors.
We do not collect personal or sensitive data regarding any Employee or owner of any Sub
Contractor or Client, unless this is specifically related to a work practice.
ABC IT Company collects and stores sensitive and personal information regarding employees.
This includes addresses, telephone numbers, next of kin, employment references, financial details
and police histories.
When Do We Destroy The Data We Collect?
ABC IT Company keeps records for a period of one full year in “active service”. Any paper based
records are stored in locked filing cabinets at our Melbourne Office
ABC IT Company archives all legally required records after a period of one year. These are stored
at our Melbourne Office for a period of not less than 7 years.
ABC IT Company destroys all non-legally required records after a period of one year by the
means of a shredding machine on our premises.
How Do We Store The Data We Collect?
ABC IT Company stores all data related to Clients or Sub Contractors and employees in an
electronic database. Backup hard copies of this data are kept in a locked filing cabinet at our
Melbourne Office.
How Do We Protect The Information We Store?
ABC IT Company electronic data is protected by a Watchguard Firebox firewall. This firewall is
designed to prevent intrusion from unauthorised parties accessing information stored on the ABC
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 18 of 24
privacy in an ICT environment
Appendix 1 - ABC IT Company Privacy Policy
ABC IT Company respects the privacy of our Clients, Contractors, Employees and Suppliers. As
such we have taken appropriate steps to comply with the Australian Privacy Act of 1988. The
following policy outlines our commitment to adhering to this Act.
What Data Do We Collect?
ABC IT Company only collects data that is relevant to our business dealings. This includes
resumes, contact names, business addresses, email and Internet addresses, telephone and fax
numbers.
ABC IT Company does collect and store the financial records of our dealings with Clients, Sub
Contractors and Suppliers.
ABC IT Company does collect financial information relating to credit references with regards to
our Clients and Sub Contractors.
We do not collect personal or sensitive data regarding any Employee or owner of any Sub
Contractor or Client, unless this is specifically related to a work practice.
ABC IT Company collects and stores sensitive and personal information regarding employees.
This includes addresses, telephone numbers, next of kin, employment references, financial details
and police histories.
When Do We Destroy The Data We Collect?
ABC IT Company keeps records for a period of one full year in “active service”. Any paper based
records are stored in locked filing cabinets at our Melbourne Office
ABC IT Company archives all legally required records after a period of one year. These are stored
at our Melbourne Office for a period of not less than 7 years.
ABC IT Company destroys all non-legally required records after a period of one year by the
means of a shredding machine on our premises.
How Do We Store The Data We Collect?
ABC IT Company stores all data related to Clients or Sub Contractors and employees in an
electronic database. Backup hard copies of this data are kept in a locked filing cabinet at our
Melbourne Office.
How Do We Protect The Information We Store?
ABC IT Company electronic data is protected by a Watchguard Firebox firewall. This firewall is
designed to prevent intrusion from unauthorised parties accessing information stored on the ABC
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 18 of 24

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
IT Company network via the Internet.
ABC IT Company virus protection is regularly updated to protect against the loss or corruption of
data to a virus, and to prevent the installation of any virus that may provide unauthorised parties
with a “back door” into our computer systems.
All authorised personnel require a password and a log on to access ABC IT Company’ network.
This applies to both Internet access and onsite computer terminal access.
Logons for the ABC IT Company network can only be authorised via the ABC IT Company
Systems Administrator. Only ABC IT Company permanent staff may apply for a log on to this
network.
Security levels are set for each log on, so that non-essential staff cannot view details that are not
relevant to their position.
ABC IT Company has a strict confidentiality agreement in place with all staff and Sub
Contractors. All Staff and subcontractors are aware of the principals of the Privacy Act of 1988
and have a copy of this corporate Privacy Policy included in the Corporate Procedures Manual.
ABC IT Company staff or sub contactors may not export any information regarding our Clients
for non-business purposes. This includes downloads to floppy disks, photocopies, original hard
copies, email (including attachments) or uploads to the World Wide Web. The only exception to
this is if the information is required to complete a current job for a Client.
ABC IT Company staff or Sub Contractors may not give out any information regarding our
Clients via the telephone to non-authorised parties, unless directly related to a current business
activity for a Client.
ABC IT Company store all hard copy or paper data in locked filing cabinets at our Melbourne
Office.
ABC IT Company has an extensive security system in place at Level 3, 607 Bourke St,
Melbourne, Victoria to further ensure the security of both electronic and hard copy information.
Who Do We Disclose Information To?
ABC IT Company only disclose the business relevant information collected by us to our Suppliers
and Sub Contractors when requested for legitimate business purposes
We do not under any circumstances pass on information relating to our Clients to third parties for
non-direct business related reasons.
ABC IT Company reserves the right to pass on relevant details of current Clients to prospective
Clients for purposes of site references, where the existing Client has specifically authorised ABC
IT Company to use this information for this purpose.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 19 of 24
privacy in an ICT environment
IT Company network via the Internet.
ABC IT Company virus protection is regularly updated to protect against the loss or corruption of
data to a virus, and to prevent the installation of any virus that may provide unauthorised parties
with a “back door” into our computer systems.
All authorised personnel require a password and a log on to access ABC IT Company’ network.
This applies to both Internet access and onsite computer terminal access.
Logons for the ABC IT Company network can only be authorised via the ABC IT Company
Systems Administrator. Only ABC IT Company permanent staff may apply for a log on to this
network.
Security levels are set for each log on, so that non-essential staff cannot view details that are not
relevant to their position.
ABC IT Company has a strict confidentiality agreement in place with all staff and Sub
Contractors. All Staff and subcontractors are aware of the principals of the Privacy Act of 1988
and have a copy of this corporate Privacy Policy included in the Corporate Procedures Manual.
ABC IT Company staff or sub contactors may not export any information regarding our Clients
for non-business purposes. This includes downloads to floppy disks, photocopies, original hard
copies, email (including attachments) or uploads to the World Wide Web. The only exception to
this is if the information is required to complete a current job for a Client.
ABC IT Company staff or Sub Contractors may not give out any information regarding our
Clients via the telephone to non-authorised parties, unless directly related to a current business
activity for a Client.
ABC IT Company store all hard copy or paper data in locked filing cabinets at our Melbourne
Office.
ABC IT Company has an extensive security system in place at Level 3, 607 Bourke St,
Melbourne, Victoria to further ensure the security of both electronic and hard copy information.
Who Do We Disclose Information To?
ABC IT Company only disclose the business relevant information collected by us to our Suppliers
and Sub Contractors when requested for legitimate business purposes
We do not under any circumstances pass on information relating to our Clients to third parties for
non-direct business related reasons.
ABC IT Company reserves the right to pass on relevant details of current Clients to prospective
Clients for purposes of site references, where the existing Client has specifically authorised ABC
IT Company to use this information for this purpose.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 19 of 24
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
What ABC IT Company Must Do
ABC IT Company must abide by this Corporate Privacy Policy.
ABC IT Company must abide by the Privacy Act of 1988.
As a company, ABC IT Company must ensure that the information we store is accurate and up to
date. If information is found to be incorrect, we must rectify this within a reasonable period of
time.
We must only store information that is relevant to our business dealings with the Client, Sub
Contractor, Supplier or Employee.
We must adequately protect the privacy of our Clients, employees, Suppliers and Sub Contractors.
This includes appropriate IT infrastructure, internal security measures and training for our staff.
We must disclose to any Client, sub contactor, Employee or Supplier the information that we hold
about them.
ABC IT Company must make this Policy available to anyone who asks for it.
We must disclose to whom we supply information, and specify what information has been
provided to third parties. This must be approved by the Client, Employee, Sub Contractor or
Supplier to whom the information applies.
We must undertake to train all staff to ensure that this Privacy Policy is understood and
implemented in an appropriate and accurate manner. This must take place during induction
training and is the responsibility of the Department Manager to implement and the responsibility
of the Human Resources Manager to ensure occurs.
The Responsibilities of ABC IT Company Employees
You must abide by this Corporate Privacy Policy.
You must abide by the Privacy Act of 1988.
You must not pass on information of any kind to unauthorised parties about any Employee, Client,
Sub Contractor or Supplier of ABC IT Company without the organisations or person’s specific
approval.
You must not store or collect personal data about any Employee, Clients, Sub Contractor or
Supplier of ABC IT Company.
If you wish to have personal information regarding yourself disclosed to a particular business or
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 20 of 24
privacy in an ICT environment
What ABC IT Company Must Do
ABC IT Company must abide by this Corporate Privacy Policy.
ABC IT Company must abide by the Privacy Act of 1988.
As a company, ABC IT Company must ensure that the information we store is accurate and up to
date. If information is found to be incorrect, we must rectify this within a reasonable period of
time.
We must only store information that is relevant to our business dealings with the Client, Sub
Contractor, Supplier or Employee.
We must adequately protect the privacy of our Clients, employees, Suppliers and Sub Contractors.
This includes appropriate IT infrastructure, internal security measures and training for our staff.
We must disclose to any Client, sub contactor, Employee or Supplier the information that we hold
about them.
ABC IT Company must make this Policy available to anyone who asks for it.
We must disclose to whom we supply information, and specify what information has been
provided to third parties. This must be approved by the Client, Employee, Sub Contractor or
Supplier to whom the information applies.
We must undertake to train all staff to ensure that this Privacy Policy is understood and
implemented in an appropriate and accurate manner. This must take place during induction
training and is the responsibility of the Department Manager to implement and the responsibility
of the Human Resources Manager to ensure occurs.
The Responsibilities of ABC IT Company Employees
You must abide by this Corporate Privacy Policy.
You must abide by the Privacy Act of 1988.
You must not pass on information of any kind to unauthorised parties about any Employee, Client,
Sub Contractor or Supplier of ABC IT Company without the organisations or person’s specific
approval.
You must not store or collect personal data about any Employee, Clients, Sub Contractor or
Supplier of ABC IT Company.
If you wish to have personal information regarding yourself disclosed to a particular business or
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 20 of 24

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
person you should approach your HR Officer
You must not remove documents or information in any format from ABC IT Company premises
unless it is specifically related to a business activity of ABC IT Company.
Dealing with Complaints
If any Client, Employee, Sub Contractor or Supplier wishes to make a complaint regarding the
information we hold about them, or our Privacy Policy, please address them to the Human
Resources Department.
Sub-Contractors
All Sub Contractors conducting work on ABC IT Company behalf must sign a confidentiality
agreement prior to carrying out work for the company.
All Sub Contactors must read and understand our Privacy Policy prior to beginning work on ABC
IT Company behalf.
All Sub Contractors are bound to abide by ABC IT Company Privacy Policy whist carrying out
work on ABC IT Company behalf.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 21 of 24
privacy in an ICT environment
person you should approach your HR Officer
You must not remove documents or information in any format from ABC IT Company premises
unless it is specifically related to a business activity of ABC IT Company.
Dealing with Complaints
If any Client, Employee, Sub Contractor or Supplier wishes to make a complaint regarding the
information we hold about them, or our Privacy Policy, please address them to the Human
Resources Department.
Sub-Contractors
All Sub Contractors conducting work on ABC IT Company behalf must sign a confidentiality
agreement prior to carrying out work for the company.
All Sub Contactors must read and understand our Privacy Policy prior to beginning work on ABC
IT Company behalf.
All Sub Contractors are bound to abide by ABC IT Company Privacy Policy whist carrying out
work on ABC IT Company behalf.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 21 of 24

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
Appendix 2 - NIT Student Code of Conduct & Responsibilities
NIT’s Student Code of Conduct sets out standards of acceptable behaviour required of all students.
This code of conduct is intended to safeguard the reputation and integrity of NIT while also creating
a safe and productive study environment for students and staff.
The code of conduct covers both academic standards of conduct and general standards of conduct
required at NIT. Some of the standards covered in this section are outlined in more detail later in
this handbook.
1.1. Integrity in academic work
Students are expected to:
Conduct themselves honestly and in compliance with published NIT polices
Submit academic work that is free of plagiarism or collusion
Be familiar with the programs and resources available to assist them in conducting their
studies and researching appropriately, including resources to help students avoid
plagiarism
Actively participate in the learning process
Attend scheduled course activities and submit assessment tasks on time, unless
unforeseen or exceptional circumstances arise
Comply with the proper use of copyright materials
Ensure that academic activities are conducted safely and do not place others at risk of
harm.
Avoid behaviours which in any way impair the reasonable freedom of other persons to
pursue their studies, work or research or to participate
1.2. Equity and Respect
Students are expected to:
Treat NIT staff, other students, and visitors with courtesy, tolerance and respect.
Respect the rights of others to be treated equitably, free of all forms of unlawful
discrimination and harassment, including sexual harassment.
Respect the rights of others to express views and opinions and not engage in behaviour
that may be reasonably considered to be obscene, dangerous or offensive to others
Avoid engaging in behaviour that is unlawful, discriminatory, harassing, or bullying.
Avoid engaging in behaviour that is perceived to be threatening or intimidating or causes
any person to fear for their personal safety or well-being
Respect that NIT is a multicultural environment and wear modest attire at all times
whilst attending NIT
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 22 of 24
privacy in an ICT environment
Appendix 2 - NIT Student Code of Conduct & Responsibilities
NIT’s Student Code of Conduct sets out standards of acceptable behaviour required of all students.
This code of conduct is intended to safeguard the reputation and integrity of NIT while also creating
a safe and productive study environment for students and staff.
The code of conduct covers both academic standards of conduct and general standards of conduct
required at NIT. Some of the standards covered in this section are outlined in more detail later in
this handbook.
1.1. Integrity in academic work
Students are expected to:
Conduct themselves honestly and in compliance with published NIT polices
Submit academic work that is free of plagiarism or collusion
Be familiar with the programs and resources available to assist them in conducting their
studies and researching appropriately, including resources to help students avoid
plagiarism
Actively participate in the learning process
Attend scheduled course activities and submit assessment tasks on time, unless
unforeseen or exceptional circumstances arise
Comply with the proper use of copyright materials
Ensure that academic activities are conducted safely and do not place others at risk of
harm.
Avoid behaviours which in any way impair the reasonable freedom of other persons to
pursue their studies, work or research or to participate
1.2. Equity and Respect
Students are expected to:
Treat NIT staff, other students, and visitors with courtesy, tolerance and respect.
Respect the rights of others to be treated equitably, free of all forms of unlawful
discrimination and harassment, including sexual harassment.
Respect the rights of others to express views and opinions and not engage in behaviour
that may be reasonably considered to be obscene, dangerous or offensive to others
Avoid engaging in behaviour that is unlawful, discriminatory, harassing, or bullying.
Avoid engaging in behaviour that is perceived to be threatening or intimidating or causes
any person to fear for their personal safety or well-being
Respect that NIT is a multicultural environment and wear modest attire at all times
whilst attending NIT
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 22 of 24
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
1.3. Using NIT’s Premises and Resources
Students are expected to:
Use and care for NIT resources, such as building, equipment, library, information and
communication technology resources, in a lawful and ethical manner, mindful of the
need for resources to be shared by all members of NIT community
Ensure their actions or inactions as a student do not harm, or bring into disrepute, the
reputation or good standing of NIT
Refrain from littering at campus or in public areas
Leave washrooms and other facilities in a clean and tidy condition
Avoid behaviour that is detrimental to NIT property, such as damage or abuse
Students must not:
o Use, possess or supply any prohibited drug, substance or weapon on campus
o Engage in gambling on any NIT campus sites
o Engage in dishonest behaviour on any NIT sites
1.4. Classroom Conduct
Students are expected to:
Demonstrate respect for staff and students while in a NIT classrooms or at NIT learning
sites
Turn off mobile phones or put mobile phones on silent mode during class times and
assessments
Speak in English language at all times
Refrain from eating and drinking in classrooms
Undertake all required preparation for classes, such as readings
Not participate in any learning activity, such as tutorials or laboratory classes, while
under the influence of alcohol or other drugs
Wear the appropriate uniform and Personal Protective Equipment (PPE)when required.
Attend all classes regularly and punctually except when prevented by illness or other
compassionate or compelling circumstances. In the case of illness, a medical certificate
must be supplied.
1.5. Using Computer Labs
The following rules apply when using the NIT’s computer labs:
No food or drink items are allowed in the NIT computer labs.
No mobile telephones are allowed to be used when in the NIT’s computer labs.
Students must respect other students’ learning and remain quiet in the lab.
Students must not share computer access/log in information with other students
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 23 of 24
privacy in an ICT environment
1.3. Using NIT’s Premises and Resources
Students are expected to:
Use and care for NIT resources, such as building, equipment, library, information and
communication technology resources, in a lawful and ethical manner, mindful of the
need for resources to be shared by all members of NIT community
Ensure their actions or inactions as a student do not harm, or bring into disrepute, the
reputation or good standing of NIT
Refrain from littering at campus or in public areas
Leave washrooms and other facilities in a clean and tidy condition
Avoid behaviour that is detrimental to NIT property, such as damage or abuse
Students must not:
o Use, possess or supply any prohibited drug, substance or weapon on campus
o Engage in gambling on any NIT campus sites
o Engage in dishonest behaviour on any NIT sites
1.4. Classroom Conduct
Students are expected to:
Demonstrate respect for staff and students while in a NIT classrooms or at NIT learning
sites
Turn off mobile phones or put mobile phones on silent mode during class times and
assessments
Speak in English language at all times
Refrain from eating and drinking in classrooms
Undertake all required preparation for classes, such as readings
Not participate in any learning activity, such as tutorials or laboratory classes, while
under the influence of alcohol or other drugs
Wear the appropriate uniform and Personal Protective Equipment (PPE)when required.
Attend all classes regularly and punctually except when prevented by illness or other
compassionate or compelling circumstances. In the case of illness, a medical certificate
must be supplied.
1.5. Using Computer Labs
The following rules apply when using the NIT’s computer labs:
No food or drink items are allowed in the NIT computer labs.
No mobile telephones are allowed to be used when in the NIT’s computer labs.
Students must respect other students’ learning and remain quiet in the lab.
Students must not share computer access/log in information with other students
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 23 of 24

ICTICT418 Contribute to copyright, ethics and
privacy in an ICT environment
Students must not use other student’s access/log in information
Students must not view inappropriate websites or download any unauthorized
programs/materials when using the NIT computer labs.
1.6. Investigation of Misconduct
Any breaches of the guidelines outlined in the code of conduct may be considered misconduct.
Where there are reasonable grounds to believe that academic or general misconduct has occurred,
NIT will investigate the alleged misconduct based on NIT’s Complaints and Appeals policy.
1.7. Consequences of Misconduct
In determining a penalty for misconduct, NIT will take into account:
The nature and severity of the misconduct
Any demonstrated extenuating circumstances
The student’s prior records at NIT
Penalties for misconduct may include but are not limited to:
Provision of a written warning
Requiring the student to resubmit the offending work (academic misconduct)
Awarding a “Not Yet Satisfactory” grade for the work submitted or “Not Yet
Competent” for the entire unit in which the misconduct occurred (academic misconduct)
Deferring, suspending or cancelling the student’s enrolment
Referring the matter to police or DIBP
Students may appeal the outcome of any case of misconduct under the terms of NIT’s Complaints
and Appeals policy.
End of assessment.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 24 of 24
privacy in an ICT environment
Students must not use other student’s access/log in information
Students must not view inappropriate websites or download any unauthorized
programs/materials when using the NIT computer labs.
1.6. Investigation of Misconduct
Any breaches of the guidelines outlined in the code of conduct may be considered misconduct.
Where there are reasonable grounds to believe that academic or general misconduct has occurred,
NIT will investigate the alleged misconduct based on NIT’s Complaints and Appeals policy.
1.7. Consequences of Misconduct
In determining a penalty for misconduct, NIT will take into account:
The nature and severity of the misconduct
Any demonstrated extenuating circumstances
The student’s prior records at NIT
Penalties for misconduct may include but are not limited to:
Provision of a written warning
Requiring the student to resubmit the offending work (academic misconduct)
Awarding a “Not Yet Satisfactory” grade for the work submitted or “Not Yet
Competent” for the entire unit in which the misconduct occurred (academic misconduct)
Deferring, suspending or cancelling the student’s enrolment
Referring the matter to police or DIBP
Students may appeal the outcome of any case of misconduct under the terms of NIT’s Complaints
and Appeals policy.
End of assessment.
ICTICT418 - Contribute to copyright, ethics and privacy in an ICT environment
Assessment No 2. Version: 3.0 – [21-June-2017] – Published Page 24 of 24
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





