Research Paper on IoT: Security Threats and Research Methodology
VerifiedAdded on 2022/12/09
|13
|3029
|492
Report
AI Summary
This research paper delves into the multifaceted world of the Internet of Things (IoT), exploring its foundational concepts, security vulnerabilities, and research methodologies. The paper begins with an introduction to IoT, highlighting its significance in modern communication technology and the critical issue of security. It identifies key problem statements, including network security, configuration complexities, and the challenges of mitigating cyber-attacks. The research outlines specific objectives, such as enhancing ICT skills, demonstrating IoT principles, identifying privacy issues, and emphasizing IoT's future role. A comprehensive literature review synthesizes findings from fifteen articles, analyzing research techniques, variables, and outcomes. The methodology section details a mixed-methods approach, incorporating both quantitative and qualitative designs. It specifies research strategies, data collection techniques (primary and secondary), and data analysis methods. The paper also discusses questionnaire types, including multiple-choice questions and Likert-type scales, providing examples to illustrate their application. Furthermore, it covers key aspects of research ethics and concludes with a detailed list of references, offering a thorough examination of IoT's security landscape and research practices.

RESEARCH PAPER 0
Internet of Things
Internet of Things
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESEARCH PAPER 1
Table of Contents
Question 1...................................................................................................................................................2
Introduction and background..................................................................................................................2
Problem statements................................................................................................................................2
Objectives of the research.......................................................................................................................2
Contribution of the findings....................................................................................................................3
Question 2...................................................................................................................................................3
Literature review.....................................................................................................................................3
Question 3...................................................................................................................................................5
Research methodology............................................................................................................................5
Research design.......................................................................................................................................7
Research strategy....................................................................................................................................7
Data collection technique........................................................................................................................7
Data analysis............................................................................................................................................7
Question 4...................................................................................................................................................8
Types of questionnaire............................................................................................................................8
Multiple choice questions....................................................................................................................8
Likert-type scales.................................................................................................................................8
Examples of questions.............................................................................................................................9
Question 5...................................................................................................................................................9
Key aspects of research ethics.................................................................................................................9
References.................................................................................................................................................11
Table of Contents
Question 1...................................................................................................................................................2
Introduction and background..................................................................................................................2
Problem statements................................................................................................................................2
Objectives of the research.......................................................................................................................2
Contribution of the findings....................................................................................................................3
Question 2...................................................................................................................................................3
Literature review.....................................................................................................................................3
Question 3...................................................................................................................................................5
Research methodology............................................................................................................................5
Research design.......................................................................................................................................7
Research strategy....................................................................................................................................7
Data collection technique........................................................................................................................7
Data analysis............................................................................................................................................7
Question 4...................................................................................................................................................8
Types of questionnaire............................................................................................................................8
Multiple choice questions....................................................................................................................8
Likert-type scales.................................................................................................................................8
Examples of questions.............................................................................................................................9
Question 5...................................................................................................................................................9
Key aspects of research ethics.................................................................................................................9
References.................................................................................................................................................11

RESEARCH PAPER 2
Question 1
Introduction and background
IoT is defined as an ecosystem of linked physical objects which are accessible with
the help of internet connections. It is an advanced version of information and
communication technology that has the potential to connect two or more computing
devices with physical things. The thing in this technology may be an individual with a heart
monitor that is connected to computer devices by using sensors and networks. It is
examined that it is a very important technology from the perspective of communication
because it has the capability to send or receive data over a long distance. The major
problem linked with this information and communication technology is security due to
which many companies are suffering from the data breach and hacking issues. The major
focus of this research is to evaluate the working process of IoT and describe security issues
and threats linked with IoT enabled networks.
Problem statements
There are the following problems statements included in this research:
Security is the biggest issue in the IoT technology that impacts on the performance
of networks
Proper configuration of networks is another problem that faced by the consumers
while implementing IoT systems
The overall performance of IoT depends on the proper communication and it is very
complex to reduce cyber-attacks and threats from IoT networks.
All these problem statements help the author for conducting research in which security
of data is a common problem occurred in the IoT networks which will be analyzed in this
investigation.
Objectives of the research
There are numerous goals of this investigation which are described below:
To enhance skills in the area of ICT
Question 1
Introduction and background
IoT is defined as an ecosystem of linked physical objects which are accessible with
the help of internet connections. It is an advanced version of information and
communication technology that has the potential to connect two or more computing
devices with physical things. The thing in this technology may be an individual with a heart
monitor that is connected to computer devices by using sensors and networks. It is
examined that it is a very important technology from the perspective of communication
because it has the capability to send or receive data over a long distance. The major
problem linked with this information and communication technology is security due to
which many companies are suffering from the data breach and hacking issues. The major
focus of this research is to evaluate the working process of IoT and describe security issues
and threats linked with IoT enabled networks.
Problem statements
There are the following problems statements included in this research:
Security is the biggest issue in the IoT technology that impacts on the performance
of networks
Proper configuration of networks is another problem that faced by the consumers
while implementing IoT systems
The overall performance of IoT depends on the proper communication and it is very
complex to reduce cyber-attacks and threats from IoT networks.
All these problem statements help the author for conducting research in which security
of data is a common problem occurred in the IoT networks which will be analyzed in this
investigation.
Objectives of the research
There are numerous goals of this investigation which are described below:
To enhance skills in the area of ICT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RESEARCH PAPER 3
To demonstrate the key idea behind IoT technology
To identify the privacy issues linked with IoT
To highlight the importance of IoT in the future generation
Contribution of the findings
This research will play a major contribution in the area of research because it is
completely based on the ICT where the author will describe the concept of IoT along with
the security threats. Moreover, the findings of this research will help the readers for
understanding the importance of IoT in future and privacy threats related to the IoT and
companies can easily monitor the performance of IoT enabled devices by reducing the rate
of security issues. In the area of ICT IoT play a crucial character because of their ability to
improve the performance of the developer's networks and reduce communication gaps by
delivering wireless networks and sensors.
Question 2
Literature review
Alrawais, Alhothaily, Hu, & Cheng, (2017) argued that the IoT is a modern ICT
technology which is growing very fast and many business communities are using this
technology because of their ability to reduce the work load and improve overall
performance. From this paper, it has found that the authors used qualitative and secondary
techniques along with the content analysis that helped to reduce drawbacks of the research
and improve the effectiveness of the investigation (Balte, Kashid, & Patil, 2015).
It is highlighted that the author selected wireless networks, sensors, computing
devices and so on as depended variables and internet connection as an independent
variable. The findings of this Frustaci, Pace, Aloi, & Fortino, (2017) show that by using IoT
devices the companies can enhance their performance but security is a common issue that
can impact on their overall productivity.
According to Bekara, (2014) IoT refers to the internet of things that have the
potential to connect computing plans with bodily things using internet connectivity. In this
paper, the author used theoretical based techniques including qualitative research,
To demonstrate the key idea behind IoT technology
To identify the privacy issues linked with IoT
To highlight the importance of IoT in the future generation
Contribution of the findings
This research will play a major contribution in the area of research because it is
completely based on the ICT where the author will describe the concept of IoT along with
the security threats. Moreover, the findings of this research will help the readers for
understanding the importance of IoT in future and privacy threats related to the IoT and
companies can easily monitor the performance of IoT enabled devices by reducing the rate
of security issues. In the area of ICT IoT play a crucial character because of their ability to
improve the performance of the developer's networks and reduce communication gaps by
delivering wireless networks and sensors.
Question 2
Literature review
Alrawais, Alhothaily, Hu, & Cheng, (2017) argued that the IoT is a modern ICT
technology which is growing very fast and many business communities are using this
technology because of their ability to reduce the work load and improve overall
performance. From this paper, it has found that the authors used qualitative and secondary
techniques along with the content analysis that helped to reduce drawbacks of the research
and improve the effectiveness of the investigation (Balte, Kashid, & Patil, 2015).
It is highlighted that the author selected wireless networks, sensors, computing
devices and so on as depended variables and internet connection as an independent
variable. The findings of this Frustaci, Pace, Aloi, & Fortino, (2017) show that by using IoT
devices the companies can enhance their performance but security is a common issue that
can impact on their overall productivity.
According to Bekara, (2014) IoT refers to the internet of things that have the
potential to connect computing plans with bodily things using internet connectivity. In this
paper, the author used theoretical based techniques including qualitative research,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESEARCH PAPER 4
secondary technique and so on. Moreover, the author also included a survey to evaluate the
opinions of other consumers and improve the performance of the investigation. There are
major two dependent variables used by the authors, for example, computing networks,
sensors but a common independent variable included by the author was internet
connectivity (Hossain, Fotouhi, & Hasan, (2015).
The outcomes of this paper highlighted that lack of privacy is a major problem
associated with the IoT that directly impact on the performance of computer networks. A
recent study published by Mahmoud, Yousuf, Aloul, & Zualkernan, (2015) observed that
DDOS and unauthorized networks both are very common threats occurred in the system
while using IoT enabled systems. In this research, the authors adopted numerous
methodologies and techniques while conducting the investigation such as research
strategy, theoretical based approach, mixed research technique, and statistical analysis
method.
It is argued that in this paper the dependent variables are things, consumers, and
servers and so on but independent variables are physical devices, communication system
and internet (Zhao, & Ge, 2013). Therefore, it has found that the authors provided complete
information and also highlighted numerous security issues linked with IoT. Matharu,
Upadhyay, & Chaudhary, (2014) proposed a research study and included the architecture
of IoT servers to understand their key aspects. Moreover, the authors also explained
numerous techniques and methods which involve, wireless systems, sensors, and other
devices used for configuring IoT technologies.
The author argued that IoT technology depends on the internet and sensors that
helped for effectively performing wireless communication between two or more devices.
Moreover, human things are independent variables that can be connected with computer
based networks by using IoT enabled devices. Razzaq, Gill, Qureshi, & Ullah, (2017)
identified that there are two risks elements which can enhance cyber-crimes in IoT for
example misconfiguration of servers and utilization of authentication networks. From this
paper, it has found that the author conducted a literature survey and identified that more
secondary technique and so on. Moreover, the author also included a survey to evaluate the
opinions of other consumers and improve the performance of the investigation. There are
major two dependent variables used by the authors, for example, computing networks,
sensors but a common independent variable included by the author was internet
connectivity (Hossain, Fotouhi, & Hasan, (2015).
The outcomes of this paper highlighted that lack of privacy is a major problem
associated with the IoT that directly impact on the performance of computer networks. A
recent study published by Mahmoud, Yousuf, Aloul, & Zualkernan, (2015) observed that
DDOS and unauthorized networks both are very common threats occurred in the system
while using IoT enabled systems. In this research, the authors adopted numerous
methodologies and techniques while conducting the investigation such as research
strategy, theoretical based approach, mixed research technique, and statistical analysis
method.
It is argued that in this paper the dependent variables are things, consumers, and
servers and so on but independent variables are physical devices, communication system
and internet (Zhao, & Ge, 2013). Therefore, it has found that the authors provided complete
information and also highlighted numerous security issues linked with IoT. Matharu,
Upadhyay, & Chaudhary, (2014) proposed a research study and included the architecture
of IoT servers to understand their key aspects. Moreover, the authors also explained
numerous techniques and methods which involve, wireless systems, sensors, and other
devices used for configuring IoT technologies.
The author argued that IoT technology depends on the internet and sensors that
helped for effectively performing wireless communication between two or more devices.
Moreover, human things are independent variables that can be connected with computer
based networks by using IoT enabled devices. Razzaq, Gill, Qureshi, & Ullah, (2017)
identified that there are two risks elements which can enhance cyber-crimes in IoT for
example misconfiguration of servers and utilization of authentication networks. From this
paper, it has found that the author conducted a literature survey and identified that more

RESEARCH PAPER 5
than 56% communities are utilizing the IoT technology and also suffer from the data
breach and cyber-attacks (Vashi, Ram, Modi, Verma, & Prakash, 2017).
Riahi, Challal, Natalizio, Chtourou, & Bouabdallah, (2013) examined that IoT has the
capability to reduce the communication gaps and improve the effectiveness of the system
but in terms of security it is not much appropriate due to which users may lose their
private data. In which the researchers used qualitative design along with the secondary
data gathering techniques and also highlighted that devices are dependent variable and
sensors or networks are independent. As stated by Yang, Wu, Yin, Li, & Zhao, (2017) the
term IoT is an effective ICT technology which can be used in the companies for reducing
errors and problems that impact on the performance of the networks. But the major issue
associated with this technology is that it increases the rate of cyber-crimes and DOS is a
common attack which occurs in this technology.
Yoon, Park, & Yoo, (2015) also highlighted that there are two security attacks
occurred in the area of IoT which involves DDOS attack and malware attack in which the
hackers send unwanted signals by using internet connections. Moreover, it has found that
the authors used both quantitative and qualitative techniques in order to reduce
drawbacks and improve the effectiveness of the research. Zhang, et al., (2014) provided
their views on IoT and included numerous techniques such as inductive approach, mixed
method, data gathering technique and data analysis methods. In this paper, the author
included techniques, variables used by Yoon, Park, & Yoo, (2015). Moreover, it is observed
that in this research internet was an independent variable and wireless sensors,
communication system and controlling networks were dependent variables (Zhou, Cao,
Dong, & Vasilakos, 2017).
Question 3
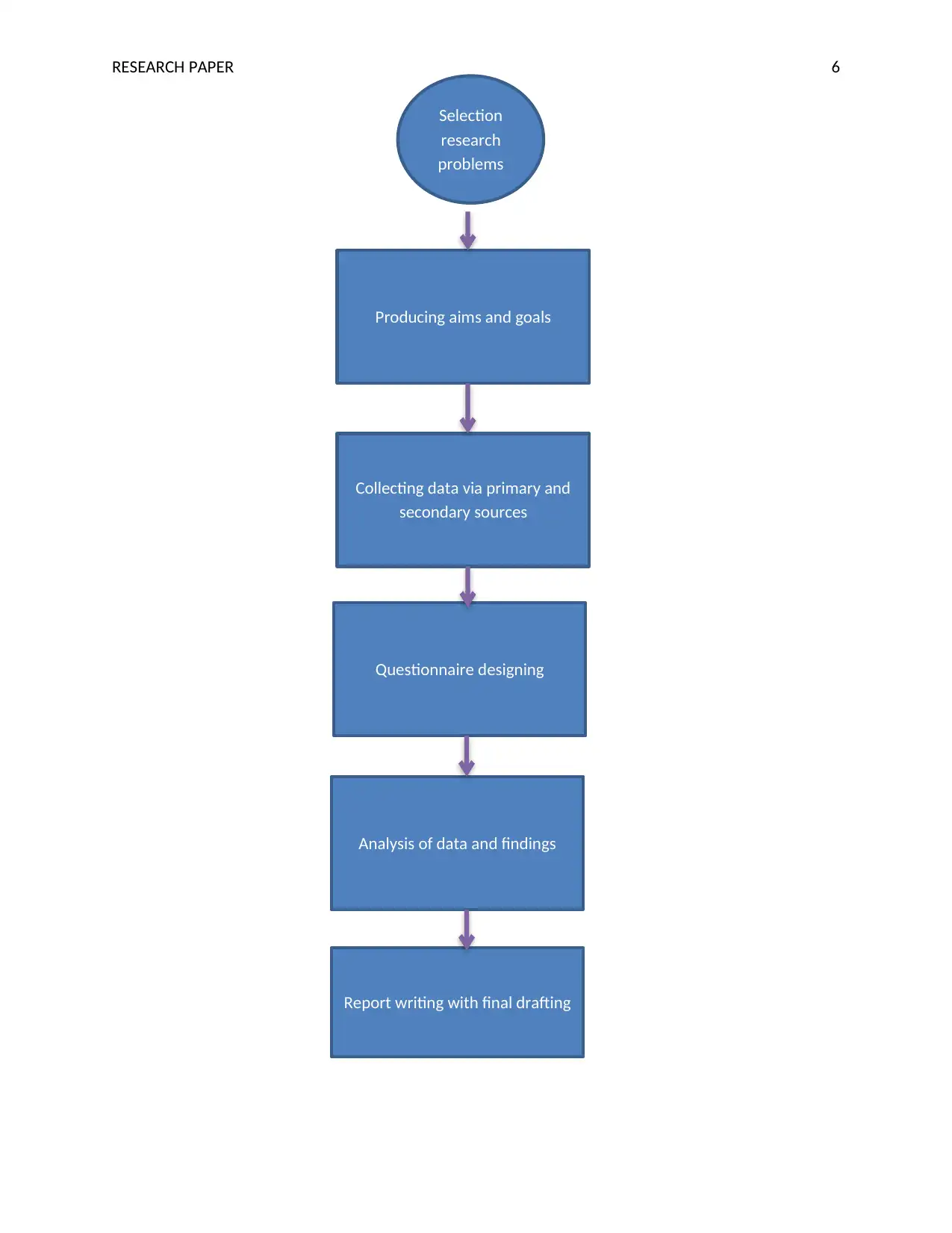
Research methodology
Flow chart for conducting the research
than 56% communities are utilizing the IoT technology and also suffer from the data
breach and cyber-attacks (Vashi, Ram, Modi, Verma, & Prakash, 2017).
Riahi, Challal, Natalizio, Chtourou, & Bouabdallah, (2013) examined that IoT has the
capability to reduce the communication gaps and improve the effectiveness of the system
but in terms of security it is not much appropriate due to which users may lose their
private data. In which the researchers used qualitative design along with the secondary
data gathering techniques and also highlighted that devices are dependent variable and
sensors or networks are independent. As stated by Yang, Wu, Yin, Li, & Zhao, (2017) the
term IoT is an effective ICT technology which can be used in the companies for reducing
errors and problems that impact on the performance of the networks. But the major issue
associated with this technology is that it increases the rate of cyber-crimes and DOS is a
common attack which occurs in this technology.
Yoon, Park, & Yoo, (2015) also highlighted that there are two security attacks
occurred in the area of IoT which involves DDOS attack and malware attack in which the
hackers send unwanted signals by using internet connections. Moreover, it has found that
the authors used both quantitative and qualitative techniques in order to reduce
drawbacks and improve the effectiveness of the research. Zhang, et al., (2014) provided
their views on IoT and included numerous techniques such as inductive approach, mixed
method, data gathering technique and data analysis methods. In this paper, the author
included techniques, variables used by Yoon, Park, & Yoo, (2015). Moreover, it is observed
that in this research internet was an independent variable and wireless sensors,
communication system and controlling networks were dependent variables (Zhou, Cao,
Dong, & Vasilakos, 2017).
Question 3
Research methodology
Flow chart for conducting the research
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
RESEARCH PAPER 6
Selection
research
problems
Producing aims and goals
Collecting data via primary and
secondary sources
Questionnaire designing
Analysis of data and findings
Report writing with final drafting
Selection
research
problems
Producing aims and goals
Collecting data via primary and
secondary sources
Questionnaire designing
Analysis of data and findings
Report writing with final drafting
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESEARCH PAPER 7
Research design
In this investigation, a mixed design will be adopted which involve both quantitative
and qualitative designs. Mainly, quantitative design focus on the numerical data and
qualitative design allow the author for obtaining theoretical information related to the IoT.
Therefore, such kinds of designs will help the author for developing an effective hypothesis
and reduce problems occurred in the research.
Research strategy
It is a common technique which is mainly used in the research because of their
capability to develop a reliable structure of the research. In this research the author will
involve numerous strategies such as literature review, survey through a questionnaire,
collecting data from other resources and so on. The literature review will help the author
for analyzing the opinions and results of other writers and survey will provide fresh and
new information about the research topic.
Data collection technique
In this investigation primary and secondary methodologies will be adopted where
the primary approach focus on the numerical data and secondary technique focus on the
theoretical facts obtained from the previous studies. It is argued that the primary data will
be obtained from survey using questionnaire and theoretical data will be obtained from the
literature survey.
Data analysis
For analyzing the collected data the author will adopt statistical analysis technique
along with the SPSS tool because of their potential to provide the effective results and
findings of the research. SPPS tool will help for including the collected data in a form of
chart, or graph.
Research design
In this investigation, a mixed design will be adopted which involve both quantitative
and qualitative designs. Mainly, quantitative design focus on the numerical data and
qualitative design allow the author for obtaining theoretical information related to the IoT.
Therefore, such kinds of designs will help the author for developing an effective hypothesis
and reduce problems occurred in the research.
Research strategy
It is a common technique which is mainly used in the research because of their
capability to develop a reliable structure of the research. In this research the author will
involve numerous strategies such as literature review, survey through a questionnaire,
collecting data from other resources and so on. The literature review will help the author
for analyzing the opinions and results of other writers and survey will provide fresh and
new information about the research topic.
Data collection technique
In this investigation primary and secondary methodologies will be adopted where
the primary approach focus on the numerical data and secondary technique focus on the
theoretical facts obtained from the previous studies. It is argued that the primary data will
be obtained from survey using questionnaire and theoretical data will be obtained from the
literature survey.
Data analysis
For analyzing the collected data the author will adopt statistical analysis technique
along with the SPSS tool because of their potential to provide the effective results and
findings of the research. SPPS tool will help for including the collected data in a form of
chart, or graph.

RESEARCH PAPER 8
Question 4
Types of questionnaire
Multiple choice questions
It is a very common type of questionnaire which will be used in this research that
has the capability to analyze and evaluate the findings and help the authors for obtaining
reliable facts from participants. It is observed that multiple-choice questions are effective
that provide a way to compile the facts and results related to the research topic and in this
investigation, the researchers will be used such kind of questionnaire while conducting the
research.
Advantages
The major advantage of the multiple-choice question is that it is very simple to
design and implement that reduce complexity from the system. a recent study argued that
multiple-choice question enables the investigators for analyzing and compiling the findings
related to the research topic.
Disadvantages
It is identified that this type of questionnaire is not able to collect the answer related
to the subjective questions because of this it cannot resolve the problem of “why”.
Moreover, it collects only objective types of questions which can reduce the quality of the
research and authors can suffer from the issues and research concerns.
Likert-type scales
It is defined as a psychometric scale which is mainly used in the investigation which
employs questionnaires and it has the potential to scale responses in the area of research.
Therefore, the researchers will be used such kinds of questionnaires while conducting the
research and employs collected responses as per the requirement.
Advantages
Question 4
Types of questionnaire
Multiple choice questions
It is a very common type of questionnaire which will be used in this research that
has the capability to analyze and evaluate the findings and help the authors for obtaining
reliable facts from participants. It is observed that multiple-choice questions are effective
that provide a way to compile the facts and results related to the research topic and in this
investigation, the researchers will be used such kind of questionnaire while conducting the
research.
Advantages
The major advantage of the multiple-choice question is that it is very simple to
design and implement that reduce complexity from the system. a recent study argued that
multiple-choice question enables the investigators for analyzing and compiling the findings
related to the research topic.
Disadvantages
It is identified that this type of questionnaire is not able to collect the answer related
to the subjective questions because of this it cannot resolve the problem of “why”.
Moreover, it collects only objective types of questions which can reduce the quality of the
research and authors can suffer from the issues and research concerns.
Likert-type scales
It is defined as a psychometric scale which is mainly used in the investigation which
employs questionnaires and it has the potential to scale responses in the area of research.
Therefore, the researchers will be used such kinds of questionnaires while conducting the
research and employs collected responses as per the requirement.
Advantages
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RESEARCH PAPER 9
It is determined that the Likert scale is more flexible as compared to the other
questionnaires that have the capability to enhance the effectiveness of the research.
However, such kind of questionnaire is very easy to conduct and also provide a platform to
employs questions in an effective way.
Disadvantages
It is argued that the key drawback of this questionnaire is that it required
development work before conducting the survey which can produce complexity in the
research.
Examples of questions
Question 1: What is the main reason that increases security issues in IoT?
A) Lack of privacy
B) Use of unauthorized networks
C) Misconfiguration of networks
D) Less secure networks
Question 2: Do you agree that the security of data is a common issue associated with IoT?
A) Strongly agree
B) Agree
C) Strongly disagree
D) Disagree
Question 5
Key aspects of research ethics
Use of privacy acts and legislation
Providing credit to the other experts
Use own words while producing a research report
Collect data from reliable resources
Do not use unauthentic references
It is determined that the Likert scale is more flexible as compared to the other
questionnaires that have the capability to enhance the effectiveness of the research.
However, such kind of questionnaire is very easy to conduct and also provide a platform to
employs questions in an effective way.
Disadvantages
It is argued that the key drawback of this questionnaire is that it required
development work before conducting the survey which can produce complexity in the
research.
Examples of questions
Question 1: What is the main reason that increases security issues in IoT?
A) Lack of privacy
B) Use of unauthorized networks
C) Misconfiguration of networks
D) Less secure networks
Question 2: Do you agree that the security of data is a common issue associated with IoT?
A) Strongly agree
B) Agree
C) Strongly disagree
D) Disagree
Question 5
Key aspects of research ethics
Use of privacy acts and legislation
Providing credit to the other experts
Use own words while producing a research report
Collect data from reliable resources
Do not use unauthentic references
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESEARCH PAPER 10
All these are five key aspects that should be included while conducting the research that
can help the authors to reduce ethical issues. Moreover, in order to reduce ethical concerns,
the author will adopt privacy acts and legislation and also use only authentic sources for
obtaining reliable information. In order to improve the effectiveness of the research, the
author should use their own words and also provide credit to the other researchers by
including an in-text citation in each paragraph.
All these are five key aspects that should be included while conducting the research that
can help the authors to reduce ethical issues. Moreover, in order to reduce ethical concerns,
the author will adopt privacy acts and legislation and also use only authentic sources for
obtaining reliable information. In order to improve the effectiveness of the research, the
author should use their own words and also provide credit to the other researchers by
including an in-text citation in each paragraph.

RESEARCH PAPER 11
References
Alrawais, A., Alhothaily, A., Hu, C., & Cheng, X. (2017). Fog computing for the internet of
things: Security and privacy issues. IEEE Internet Computing, 21(2), 34-42.
Balte, A., Kashid, A., & Patil, B. (2015). Security issues in the Internet of things (IoT): A
survey. International Journal of Advanced Research in Computer Science and Software
Engineering, 5(4).
Bekara, C. (2014). Security issues and challenges for the IoT-based smart grid. Procedia
Computer Science, 34, 532-537.
Frustaci, M., Pace, P., Aloi, G., & Fortino, G. (2017). Evaluating critical security issues of the
IoT world: Present and future challenges. IEEE Internet of Things Journal, 5(4),
2483-2495.
Hossain, M. M., Fotouhi, M., & Hasan, R. (2015). Towards an analysis of security issues,
challenges, and open problems in the internet of things. In 2015 IEEE World
Congress on Services, 12(5), 21-28.
Mahmoud, R., Yousuf, T., Aloul, F., & Zualkernan, I. (2015). Internet of things (IoT) security:
Current status, challenges and prospective measures. In 2015 10th International
Conference for Internet Technology and Secured Transactions (ICITST), 12(8), 336-
341.
Matharu, G. S., Upadhyay, P., & Chaudhary, L. (2014). The internet of things: Challenges &
security issues. In 2014 International Conference on Emerging Technologies (ICET),
7(5), 54-59.
Razzaq, M. A., Gill, S. H., Qureshi, M. A., & Ullah, S. (2017). Security issues in the Internet of
Things (IoT): A comprehensive study. International Journal of Advanced Computer
Science and Applications, 8(6), 383.
References
Alrawais, A., Alhothaily, A., Hu, C., & Cheng, X. (2017). Fog computing for the internet of
things: Security and privacy issues. IEEE Internet Computing, 21(2), 34-42.
Balte, A., Kashid, A., & Patil, B. (2015). Security issues in the Internet of things (IoT): A
survey. International Journal of Advanced Research in Computer Science and Software
Engineering, 5(4).
Bekara, C. (2014). Security issues and challenges for the IoT-based smart grid. Procedia
Computer Science, 34, 532-537.
Frustaci, M., Pace, P., Aloi, G., & Fortino, G. (2017). Evaluating critical security issues of the
IoT world: Present and future challenges. IEEE Internet of Things Journal, 5(4),
2483-2495.
Hossain, M. M., Fotouhi, M., & Hasan, R. (2015). Towards an analysis of security issues,
challenges, and open problems in the internet of things. In 2015 IEEE World
Congress on Services, 12(5), 21-28.
Mahmoud, R., Yousuf, T., Aloul, F., & Zualkernan, I. (2015). Internet of things (IoT) security:
Current status, challenges and prospective measures. In 2015 10th International
Conference for Internet Technology and Secured Transactions (ICITST), 12(8), 336-
341.
Matharu, G. S., Upadhyay, P., & Chaudhary, L. (2014). The internet of things: Challenges &
security issues. In 2014 International Conference on Emerging Technologies (ICET),
7(5), 54-59.
Razzaq, M. A., Gill, S. H., Qureshi, M. A., & Ullah, S. (2017). Security issues in the Internet of
Things (IoT): A comprehensive study. International Journal of Advanced Computer
Science and Applications, 8(6), 383.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





