Configuring Active Directory Domain for Thinktank Company
VerifiedAdded on 2023/04/04
|27
|2688
|176
AI Summary
This report focuses on identifying and proposing the needed servers and their roles for Thinktank company and also provides the configuration instructions for setting up an Active Directory Domain.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

System Management
Student Name
Course
Institution
Date
Student Name
Course
Institution
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Introduction................................................................................................................................3
Requirement Analysis................................................................................................................3
Identification of Server Roles & Technologies..........................................................................5
Security Policy...........................................................................................................................5
Network Configuration Process, Screenshots, and Commands.................................................6
Active Directory Domain Structure.........................................................................................23
Summary..................................................................................................................................24
Conclusion................................................................................................................................24
References................................................................................................................................26
Introduction................................................................................................................................3
Requirement Analysis................................................................................................................3
Identification of Server Roles & Technologies..........................................................................5
Security Policy...........................................................................................................................5
Network Configuration Process, Screenshots, and Commands.................................................6
Active Directory Domain Structure.........................................................................................23
Summary..................................................................................................................................24
Conclusion................................................................................................................................24
References................................................................................................................................26

Introduction
If the business is growing, it is important to understand the need to have a reliable and quality
IT infrastructure as it is crucial in ensuring business efficiency [1]. IT network infrastructure
is one of the most essential solutions that a business can implement. A computer network
basically refers an interconnection of computer components for the purpose of
communication and sharing of resources such as printers, data, files, and applications. There
are different computer network topologies and the choice that a company makes should be
able to reflect on the requirements [2]. One way of configuring a network is setting it up to go
through a server. However, when setting up a network it is crucial to have an experience
consultant to guide you through the process and recommending the most reliable and quality
network components such as servers, routers, switches, firewalls, among other components.
Additionally, it is important for any company to realize that technology is evolving at a fast
rate and should adopt a solution that is able to meet future changes and requirements because
of the dynamic nature of technology involve [3]. There are several advantages associated
with computer networks including helping the business to grow as it improves business
operations and overall efficiency. Also, it enhances cost-effectiveness because it facilitates
sharing of resources such as printers, applications, data, and files [4]. This is because the
company will not need to buy equipment for every employee rather, they will be able to share
what is available.
This report will focus on identifying and proposing the needed servers and their roles for
Thinktank company and also provide the configuration instructions. Configurations will be
done on windows server 2012RT that has been installed on the client computer to
demonstrate the configuration process. Every step and process that will be done will be
documented in this report.
Requirement Analysis
The requirements have been mentioned in the case scenario regarding Thinktank company
which is a small and medium sized company (SME) based in Sydney. The company has
grown overtime and the company now have 50 computers from previous 10 computers.
Additionally, the company is quickly growing and is planning to open up new pilot branches
in Melbourne that will be directly connected to the Sydney office which serves as the Head
If the business is growing, it is important to understand the need to have a reliable and quality
IT infrastructure as it is crucial in ensuring business efficiency [1]. IT network infrastructure
is one of the most essential solutions that a business can implement. A computer network
basically refers an interconnection of computer components for the purpose of
communication and sharing of resources such as printers, data, files, and applications. There
are different computer network topologies and the choice that a company makes should be
able to reflect on the requirements [2]. One way of configuring a network is setting it up to go
through a server. However, when setting up a network it is crucial to have an experience
consultant to guide you through the process and recommending the most reliable and quality
network components such as servers, routers, switches, firewalls, among other components.
Additionally, it is important for any company to realize that technology is evolving at a fast
rate and should adopt a solution that is able to meet future changes and requirements because
of the dynamic nature of technology involve [3]. There are several advantages associated
with computer networks including helping the business to grow as it improves business
operations and overall efficiency. Also, it enhances cost-effectiveness because it facilitates
sharing of resources such as printers, applications, data, and files [4]. This is because the
company will not need to buy equipment for every employee rather, they will be able to share
what is available.
This report will focus on identifying and proposing the needed servers and their roles for
Thinktank company and also provide the configuration instructions. Configurations will be
done on windows server 2012RT that has been installed on the client computer to
demonstrate the configuration process. Every step and process that will be done will be
documented in this report.
Requirement Analysis
The requirements have been mentioned in the case scenario regarding Thinktank company
which is a small and medium sized company (SME) based in Sydney. The company has
grown overtime and the company now have 50 computers from previous 10 computers.
Additionally, the company is quickly growing and is planning to open up new pilot branches
in Melbourne that will be directly connected to the Sydney office which serves as the Head

Quarters (HQ). The company will hire the same number of employees in Melbourne office.
Additionally, the company will need to acquire new computer equipment such as printers and
workstations. The company also anticipates to have centralized data collection, authorization,
and authentication for easy monitoring, troubleshooting, and management. One of the key
aspects that the company requires is to ensure that the finance department in the two offices
have separate folders on the network that can be specifically accessed by the individual
departments. Also, the sales departments will have their independent folders just like the
finance department. However, even with this limitation, the managers should be able to
access the whole data folder.
The current setup at Thinktank is that, data is stored centrally in two workstations which are
basically workgroup computers which is share amongst 28 employees from the various
departments within the company. IP addresses are manually assigned to users which has led
to numerous challenges in record maintenance and has led to the IT staff assigning similar IP
addresses to different users causing disruption in network functions because of duplications.
Additionally, the users at Thinktank are having a big challenge in remembering the IP
address for the central servers holding the data because they are required to memorize it. As a
result, the company has requested that they will have to have names instead of IP addresses
for the servers which will be accessible over the internet. Moreover, every user will be given
specific space within the network to store their files which can only be access by them. As
such, the company needs to have a new network infrastructure because the current one does
not support the new requirements. The company also seeks to improve availability within the
network by implementing fault tolerance strategies. Finally, the company also requires a
security policy solution for maintaining the security of the network resources based in best
practices within the industry.
In order to meet the requirements, XYZ company, which is the company that Thinktank has
hired to provide the solution will provide a prototype simulation that will address the
requirements identified above [5]. The domain name that has been used for the prototype is
thinktank.com and the network will be represented as an active directory domain tree which
contain root domain. The network will have two domain controllers for the purpose of
redundancy, print server for managing print jobs on the share printer, Dynamic Host Control
Protocol (DHCP) server for allocating IP addresses automatically, and web server for hosting
Additionally, the company will need to acquire new computer equipment such as printers and
workstations. The company also anticipates to have centralized data collection, authorization,
and authentication for easy monitoring, troubleshooting, and management. One of the key
aspects that the company requires is to ensure that the finance department in the two offices
have separate folders on the network that can be specifically accessed by the individual
departments. Also, the sales departments will have their independent folders just like the
finance department. However, even with this limitation, the managers should be able to
access the whole data folder.
The current setup at Thinktank is that, data is stored centrally in two workstations which are
basically workgroup computers which is share amongst 28 employees from the various
departments within the company. IP addresses are manually assigned to users which has led
to numerous challenges in record maintenance and has led to the IT staff assigning similar IP
addresses to different users causing disruption in network functions because of duplications.
Additionally, the users at Thinktank are having a big challenge in remembering the IP
address for the central servers holding the data because they are required to memorize it. As a
result, the company has requested that they will have to have names instead of IP addresses
for the servers which will be accessible over the internet. Moreover, every user will be given
specific space within the network to store their files which can only be access by them. As
such, the company needs to have a new network infrastructure because the current one does
not support the new requirements. The company also seeks to improve availability within the
network by implementing fault tolerance strategies. Finally, the company also requires a
security policy solution for maintaining the security of the network resources based in best
practices within the industry.
In order to meet the requirements, XYZ company, which is the company that Thinktank has
hired to provide the solution will provide a prototype simulation that will address the
requirements identified above [5]. The domain name that has been used for the prototype is
thinktank.com and the network will be represented as an active directory domain tree which
contain root domain. The network will have two domain controllers for the purpose of
redundancy, print server for managing print jobs on the share printer, Dynamic Host Control
Protocol (DHCP) server for allocating IP addresses automatically, and web server for hosting
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

the company website [6]. Additionally, the company requires to have a file server for storing
all the files which can only be accessed by authorized users.
Identification of Server Roles & Technologies
Servers play a very significant role when implementing an IT infrastructure solution. This is
because the provide the most crucial functions that are needed by the business enterprise.
Moreover, servers play several functions and roles that form part of the enterprise network.
There are several types of servers that can be used in a network or a data center [7]. However,
for the case of Thinktank company, the following servers are required in order to fulfill the
requirements identified in the previous section: Print servers, DHCP servers, File server, and
Web servers.
Print server: this server is responsible for managing shared printers on the network. Print
server is connected on the network with client computer that send print jobs to the shared
printer. The server is responsible for forwarding print jobs to the printer when the printer is
available and has the capability to prioritize urgent jobs [6]. The print server can also make
decisions for the client to use the printer that is closer.
DHCP server: Currently users are allocated IP addresses manually and this has posed serious
challenges to the IT staff because of constant interruption and disruption of network services.
As such, there is need to have a server that will assign IP addresses automatically [8]. DHCP
server will be used for this function because it provides fast, dynamic, and central
management of IP address distribution within the network.
File Server: file server will be responsible for assigning a pace for share disk access.
Thinktank requires a file server to manage access to one of the critical resources, data [6].
Also, the file server to regulate access to the files and shared databases to ensure that only
authorized users are allowed to access the files within the network.
Web server: this server is used to host the company website. Secondly, it will be sued to
secure and store website data, offer access to web database, process end user requests,
controlling traffic to the server, and allow the user create dynamic web pages.
Security Policy
all the files which can only be accessed by authorized users.
Identification of Server Roles & Technologies
Servers play a very significant role when implementing an IT infrastructure solution. This is
because the provide the most crucial functions that are needed by the business enterprise.
Moreover, servers play several functions and roles that form part of the enterprise network.
There are several types of servers that can be used in a network or a data center [7]. However,
for the case of Thinktank company, the following servers are required in order to fulfill the
requirements identified in the previous section: Print servers, DHCP servers, File server, and
Web servers.
Print server: this server is responsible for managing shared printers on the network. Print
server is connected on the network with client computer that send print jobs to the shared
printer. The server is responsible for forwarding print jobs to the printer when the printer is
available and has the capability to prioritize urgent jobs [6]. The print server can also make
decisions for the client to use the printer that is closer.
DHCP server: Currently users are allocated IP addresses manually and this has posed serious
challenges to the IT staff because of constant interruption and disruption of network services.
As such, there is need to have a server that will assign IP addresses automatically [8]. DHCP
server will be used for this function because it provides fast, dynamic, and central
management of IP address distribution within the network.
File Server: file server will be responsible for assigning a pace for share disk access.
Thinktank requires a file server to manage access to one of the critical resources, data [6].
Also, the file server to regulate access to the files and shared databases to ensure that only
authorized users are allowed to access the files within the network.
Web server: this server is used to host the company website. Secondly, it will be sued to
secure and store website data, offer access to web database, process end user requests,
controlling traffic to the server, and allow the user create dynamic web pages.
Security Policy

Security policy is a very crucial element for any network infrastructure for protecting the
network resources which are susceptible to compromise or subvert. Security threats can be
external or internal but, nevertheless, there is need to have the best security policy in place. In
order to have one of the best industry standard policy, it is important to first define and
describe the policies that will be implemented [9]. The security policies will govern how
Thinktank network infrastructure will be configured and implemented to rationalize
employee’s behavior and actions when using or accessing the network resources. For
Thinktank Company, the security policy will cover the following aspects: device security,
internet access policy, port communication policy, WLAN policy, remote connection policy,
firewall rules policy, intrusion policy, secure communication policy, and DMZ policy. All
these policies are necessary to enforce security on the various network resources and at
different levels.
Network security policies are aimed at ensuring the safety of all the network resources from
exploitation and threats. It is necessary for Thinktank to consider the equipment on the
network and how they should communicate and share resources securely including data and
media transmission over the network [10]. The security policy is designed to regulate and
ensure compliance to the company need to have a safe digital operating environment.
Additionally, security policy will server in preventing the network infrastructure from code
injections, executables, software bugs, and malware infections.
Network Configuration Process, Screenshots, and Commands
There are several preconditions that are required to be fulfilled before configuring the domain
network. First, the network will be configured on Windows server 2016 running on virtual
machine. Oracle VirtualBox will also come in handy when configuring the network.
Additionally, the virtual infrastructure should be able to meet the company requirements. The
server will be running on 30GB HDD, 4GB RAM, and 4 vCPUs [11].
First, we are going to create a new virtual machine on Oracle VirtualBox.
network resources which are susceptible to compromise or subvert. Security threats can be
external or internal but, nevertheless, there is need to have the best security policy in place. In
order to have one of the best industry standard policy, it is important to first define and
describe the policies that will be implemented [9]. The security policies will govern how
Thinktank network infrastructure will be configured and implemented to rationalize
employee’s behavior and actions when using or accessing the network resources. For
Thinktank Company, the security policy will cover the following aspects: device security,
internet access policy, port communication policy, WLAN policy, remote connection policy,
firewall rules policy, intrusion policy, secure communication policy, and DMZ policy. All
these policies are necessary to enforce security on the various network resources and at
different levels.
Network security policies are aimed at ensuring the safety of all the network resources from
exploitation and threats. It is necessary for Thinktank to consider the equipment on the
network and how they should communicate and share resources securely including data and
media transmission over the network [10]. The security policy is designed to regulate and
ensure compliance to the company need to have a safe digital operating environment.
Additionally, security policy will server in preventing the network infrastructure from code
injections, executables, software bugs, and malware infections.
Network Configuration Process, Screenshots, and Commands
There are several preconditions that are required to be fulfilled before configuring the domain
network. First, the network will be configured on Windows server 2016 running on virtual
machine. Oracle VirtualBox will also come in handy when configuring the network.
Additionally, the virtual infrastructure should be able to meet the company requirements. The
server will be running on 30GB HDD, 4GB RAM, and 4 vCPUs [11].
First, we are going to create a new virtual machine on Oracle VirtualBox.
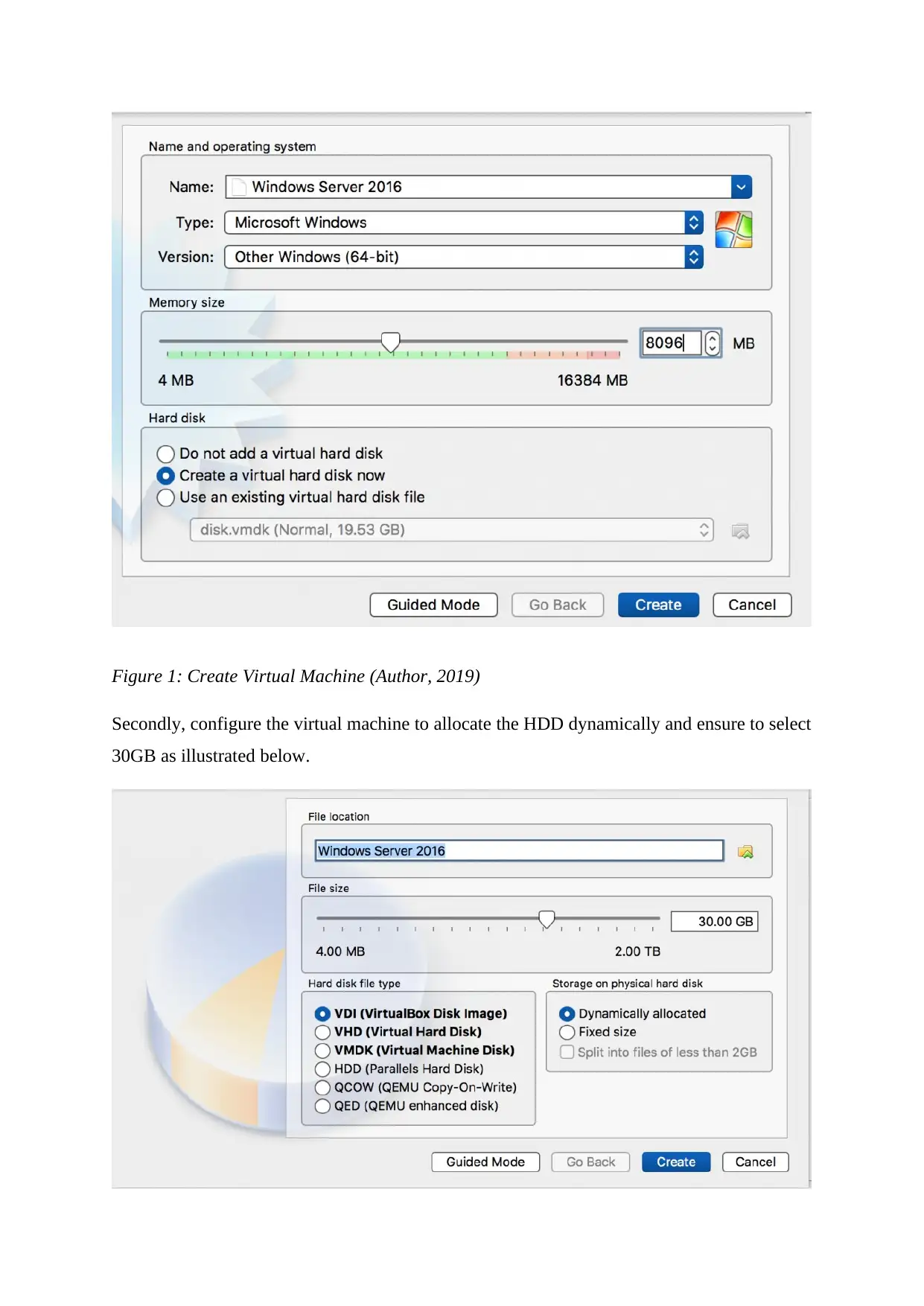
Figure 1: Create Virtual Machine (Author, 2019)
Secondly, configure the virtual machine to allocate the HDD dynamically and ensure to select
30GB as illustrated below.
Secondly, configure the virtual machine to allocate the HDD dynamically and ensure to select
30GB as illustrated below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
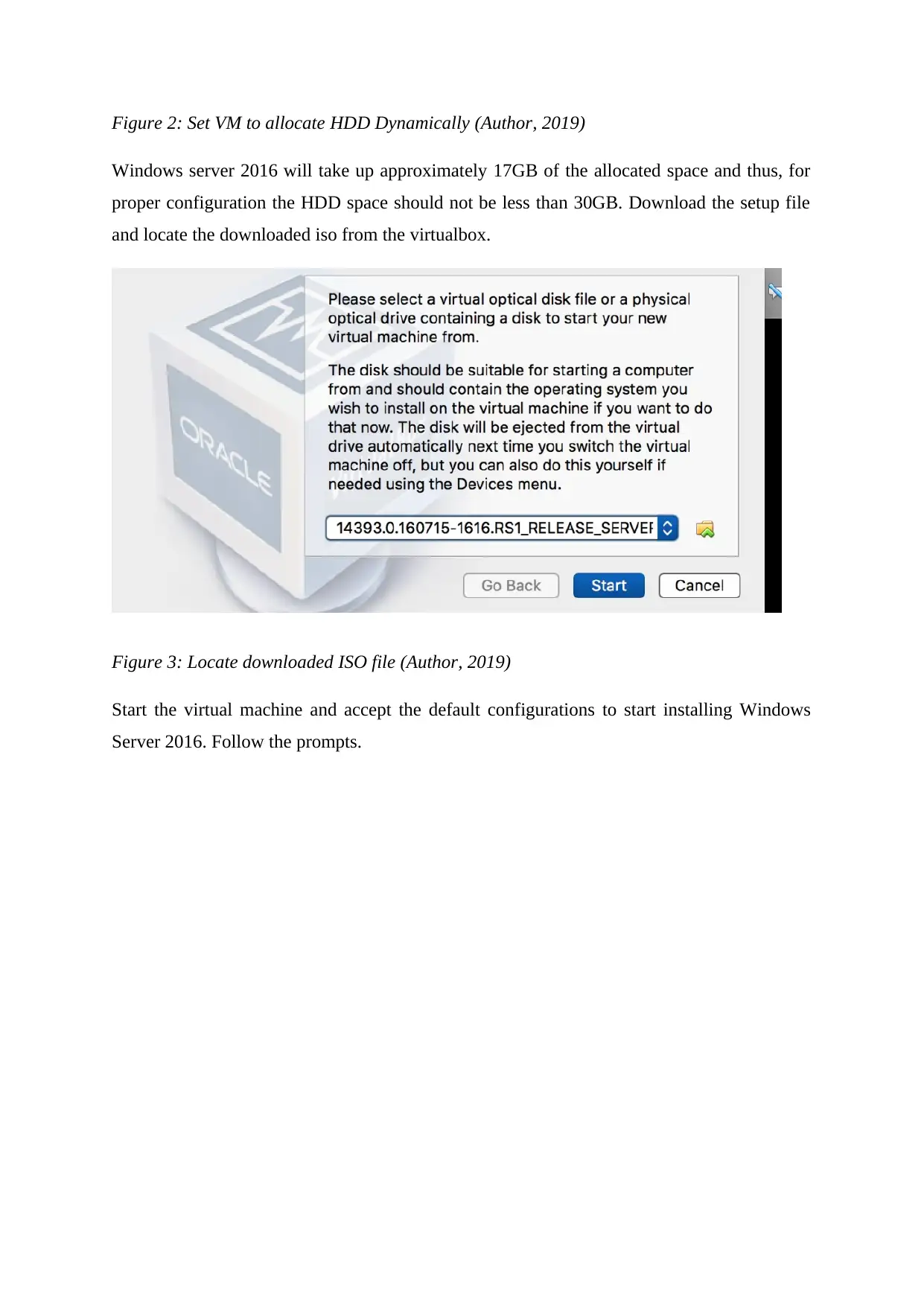
Figure 2: Set VM to allocate HDD Dynamically (Author, 2019)
Windows server 2016 will take up approximately 17GB of the allocated space and thus, for
proper configuration the HDD space should not be less than 30GB. Download the setup file
and locate the downloaded iso from the virtualbox.
Figure 3: Locate downloaded ISO file (Author, 2019)
Start the virtual machine and accept the default configurations to start installing Windows
Server 2016. Follow the prompts.
Windows server 2016 will take up approximately 17GB of the allocated space and thus, for
proper configuration the HDD space should not be less than 30GB. Download the setup file
and locate the downloaded iso from the virtualbox.
Figure 3: Locate downloaded ISO file (Author, 2019)
Start the virtual machine and accept the default configurations to start installing Windows
Server 2016. Follow the prompts.
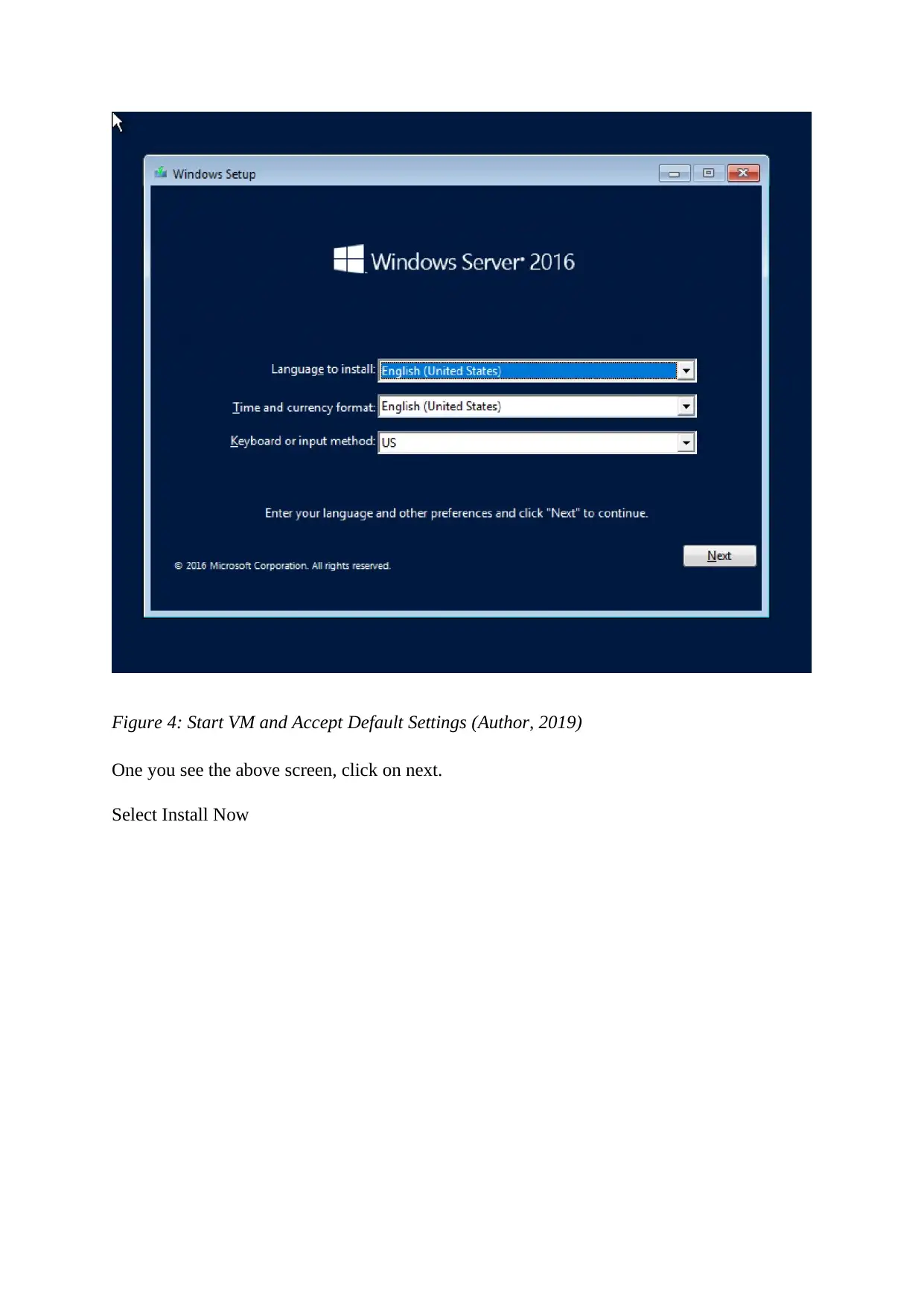
Figure 4: Start VM and Accept Default Settings (Author, 2019)
One you see the above screen, click on next.
Select Install Now
One you see the above screen, click on next.
Select Install Now
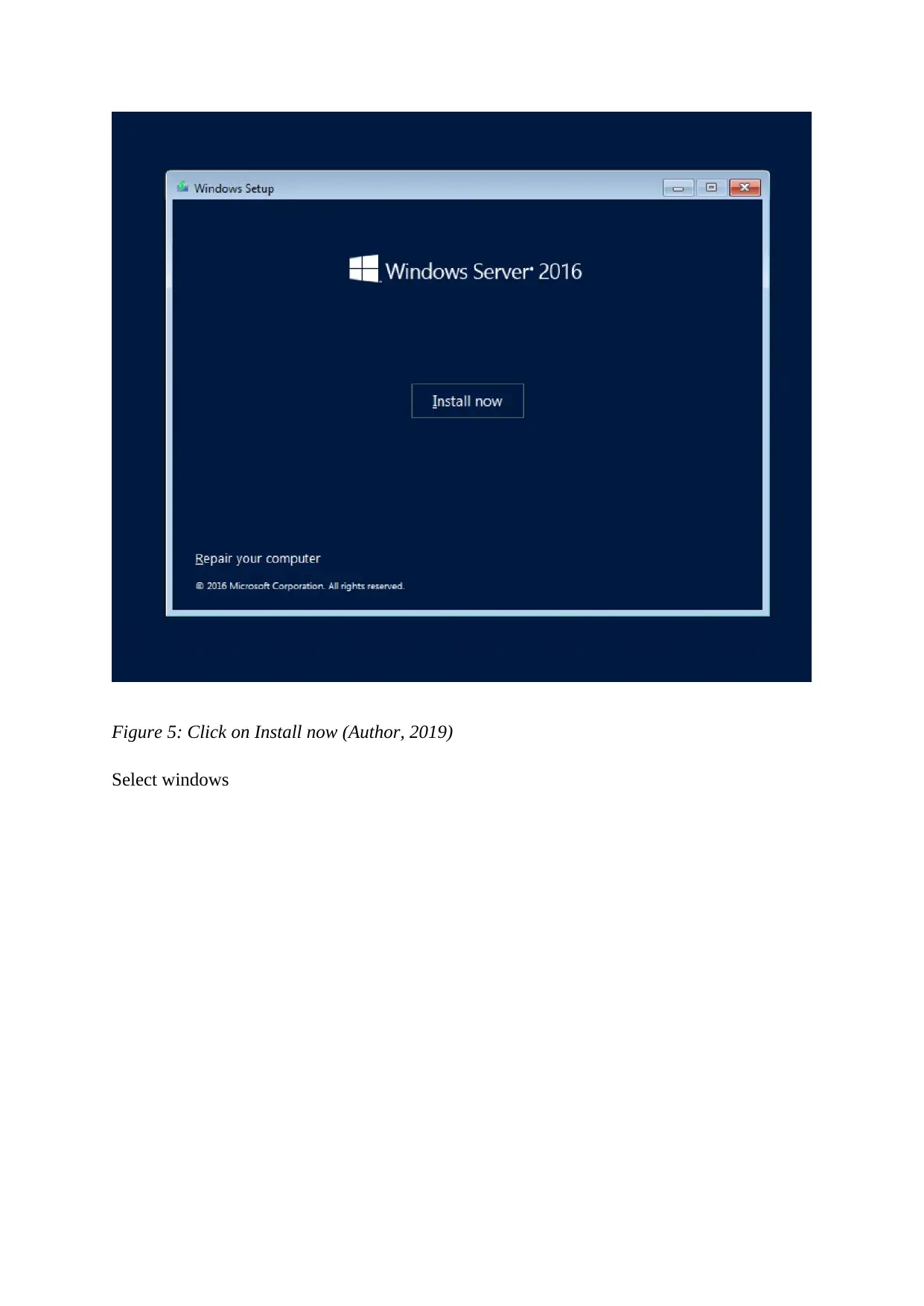
Figure 5: Click on Install now (Author, 2019)
Select windows
Select windows
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Figure 6: Select windows server 2016 evaluation desktop experience (Author, 2019)
Accept the license terms and click on next.
In the next screen select custom install and create drive from the unallocated space and click
next.
Accept the license terms and click on next.
In the next screen select custom install and create drive from the unallocated space and click
next.
Figure 7: Select custom install (Author, 2019)
Wait for the installation process to finish and the server will be ready to be configured as
active directory.
Wait for the installation process to finish and the server will be ready to be configured as
active directory.
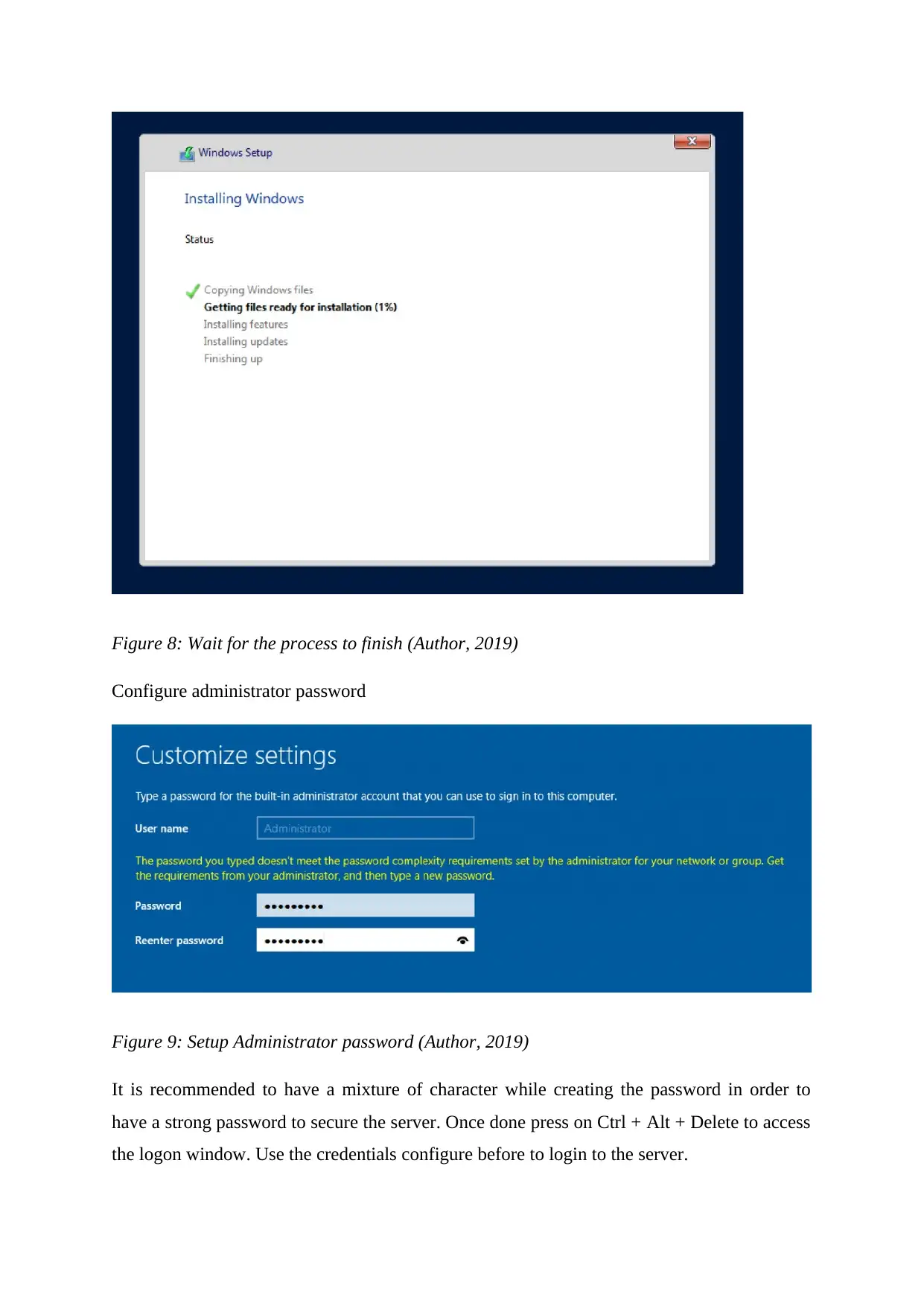
Figure 8: Wait for the process to finish (Author, 2019)
Configure administrator password
Figure 9: Setup Administrator password (Author, 2019)
It is recommended to have a mixture of character while creating the password in order to
have a strong password to secure the server. Once done press on Ctrl + Alt + Delete to access
the logon window. Use the credentials configure before to login to the server.
Configure administrator password
Figure 9: Setup Administrator password (Author, 2019)
It is recommended to have a mixture of character while creating the password in order to
have a strong password to secure the server. Once done press on Ctrl + Alt + Delete to access
the logon window. Use the credentials configure before to login to the server.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Once the server is ready, we can now configure the active directory. From the dashboard
available on the server manager, select Add roles and features.
Figure 10: Click on Add Roles and Features (Author, 2019)
Choose Role-based or feature-based installation and select next.
available on the server manager, select Add roles and features.
Figure 10: Click on Add Roles and Features (Author, 2019)
Choose Role-based or feature-based installation and select next.
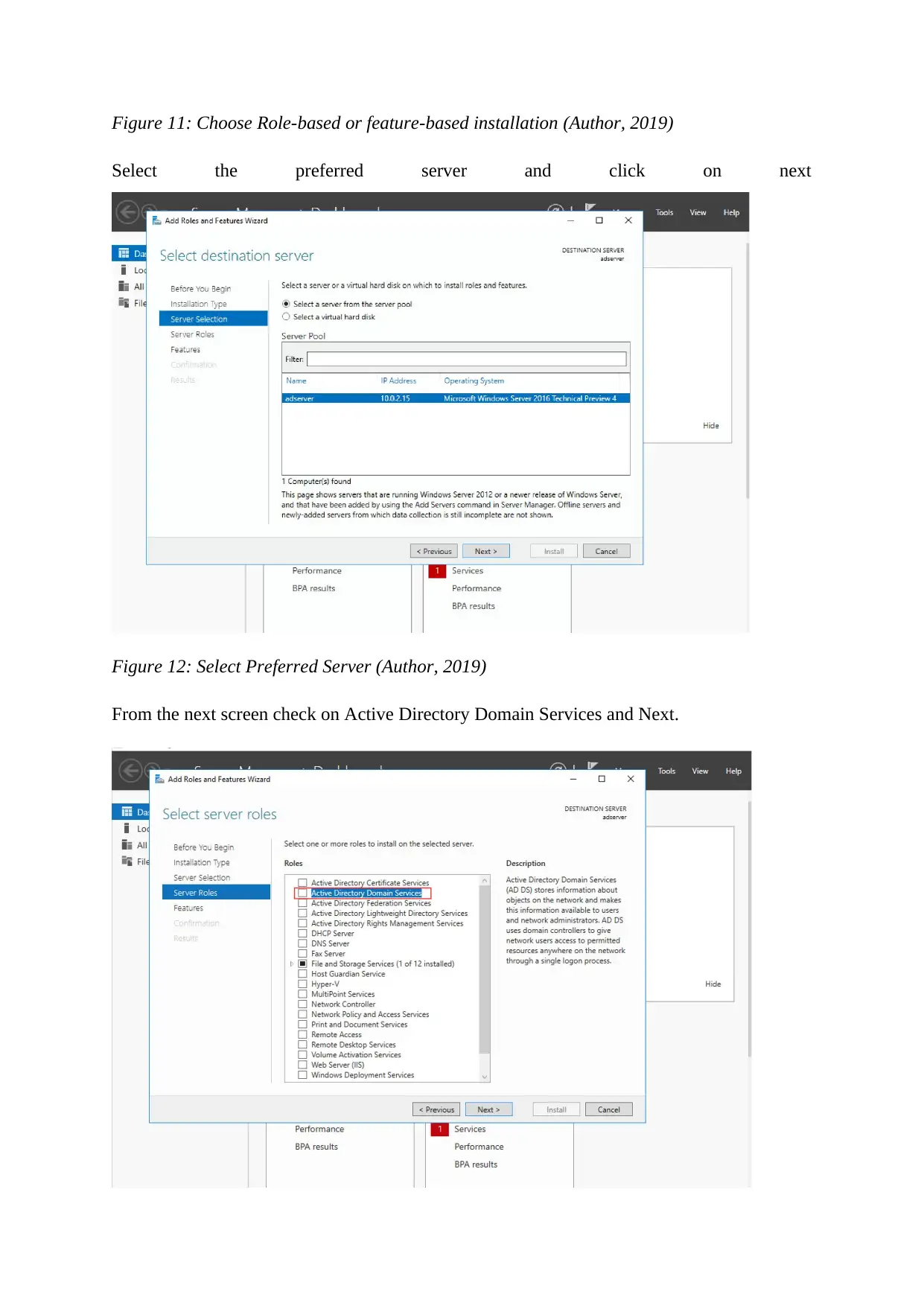
Figure 11: Choose Role-based or feature-based installation (Author, 2019)
Select the preferred server and click on next
Figure 12: Select Preferred Server (Author, 2019)
From the next screen check on Active Directory Domain Services and Next.
Select the preferred server and click on next
Figure 12: Select Preferred Server (Author, 2019)
From the next screen check on Active Directory Domain Services and Next.
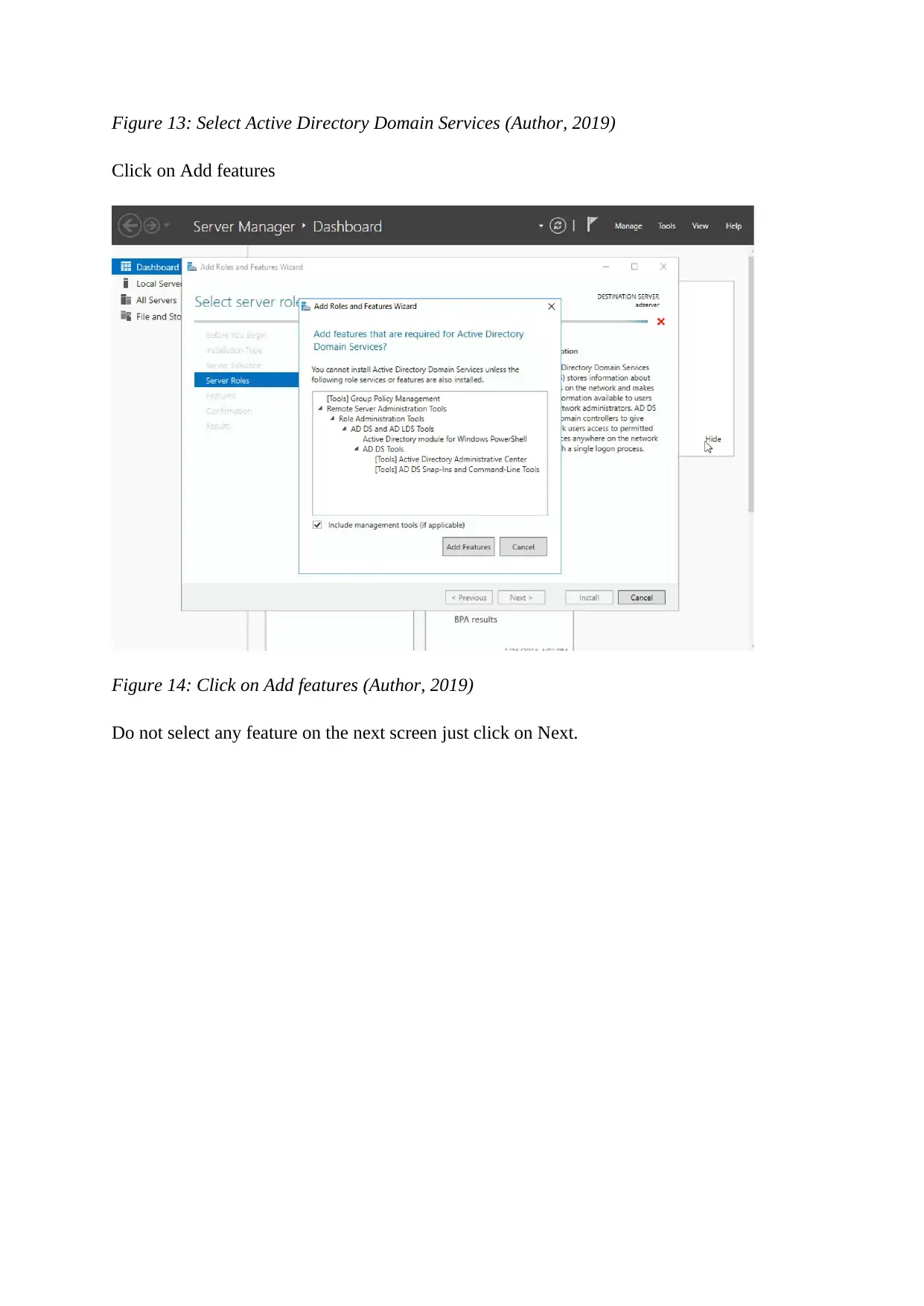
Figure 13: Select Active Directory Domain Services (Author, 2019)
Click on Add features
Figure 14: Click on Add features (Author, 2019)
Do not select any feature on the next screen just click on Next.
Click on Add features
Figure 14: Click on Add features (Author, 2019)
Do not select any feature on the next screen just click on Next.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
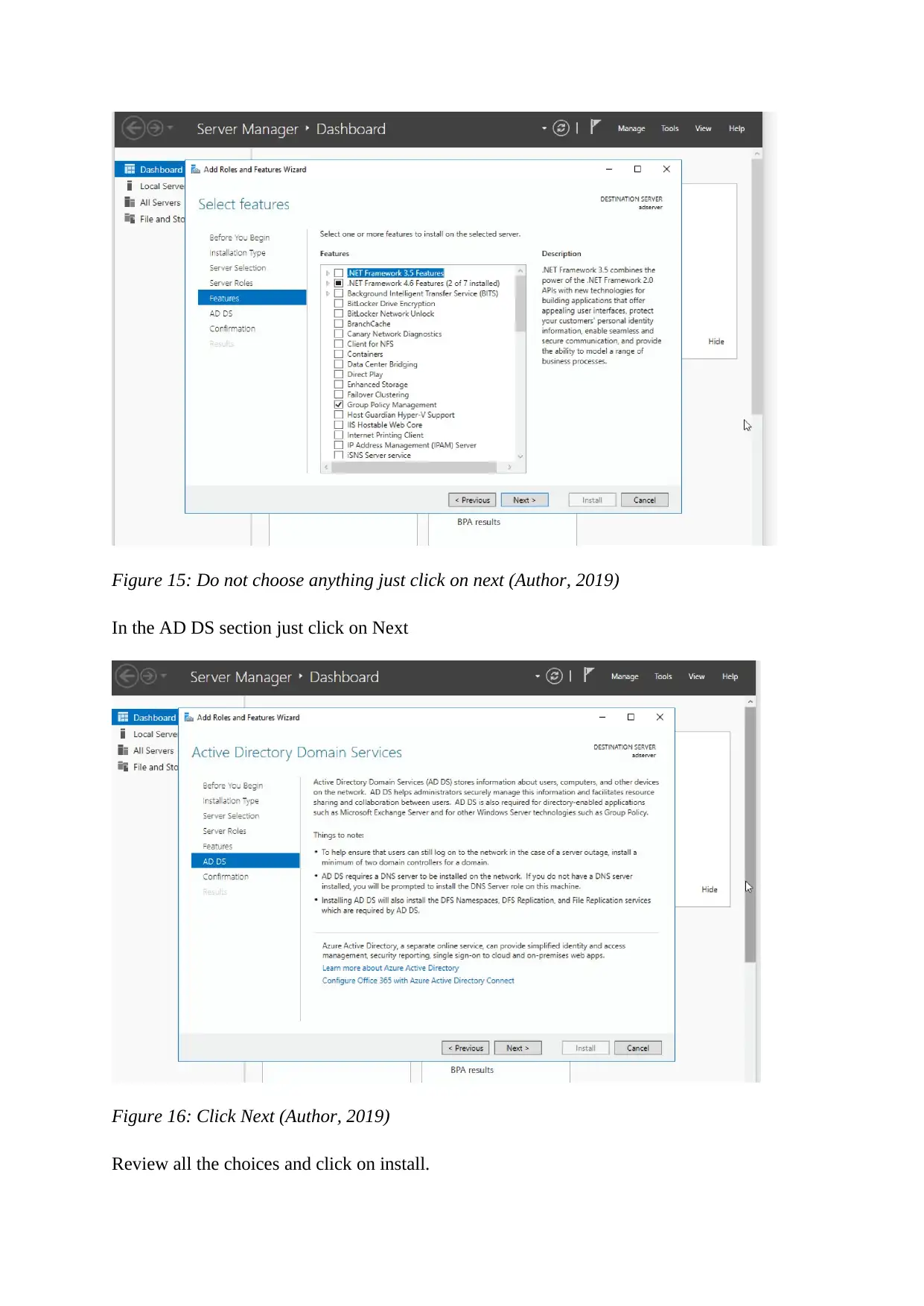
Figure 15: Do not choose anything just click on next (Author, 2019)
In the AD DS section just click on Next
Figure 16: Click Next (Author, 2019)
Review all the choices and click on install.
In the AD DS section just click on Next
Figure 16: Click Next (Author, 2019)
Review all the choices and click on install.
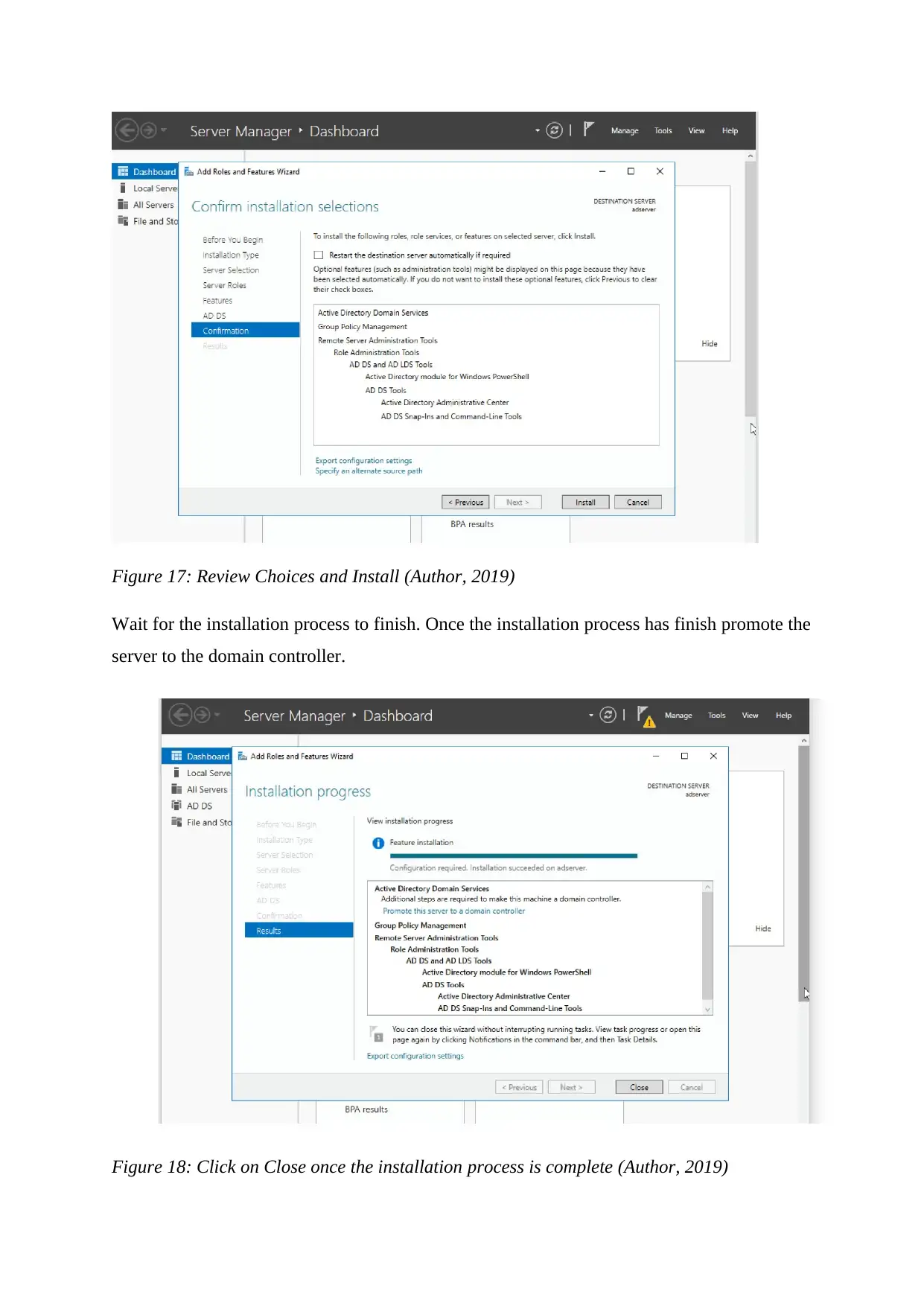
Figure 17: Review Choices and Install (Author, 2019)
Wait for the installation process to finish. Once the installation process has finish promote the
server to the domain controller.
Figure 18: Click on Close once the installation process is complete (Author, 2019)
Wait for the installation process to finish. Once the installation process has finish promote the
server to the domain controller.
Figure 18: Click on Close once the installation process is complete (Author, 2019)
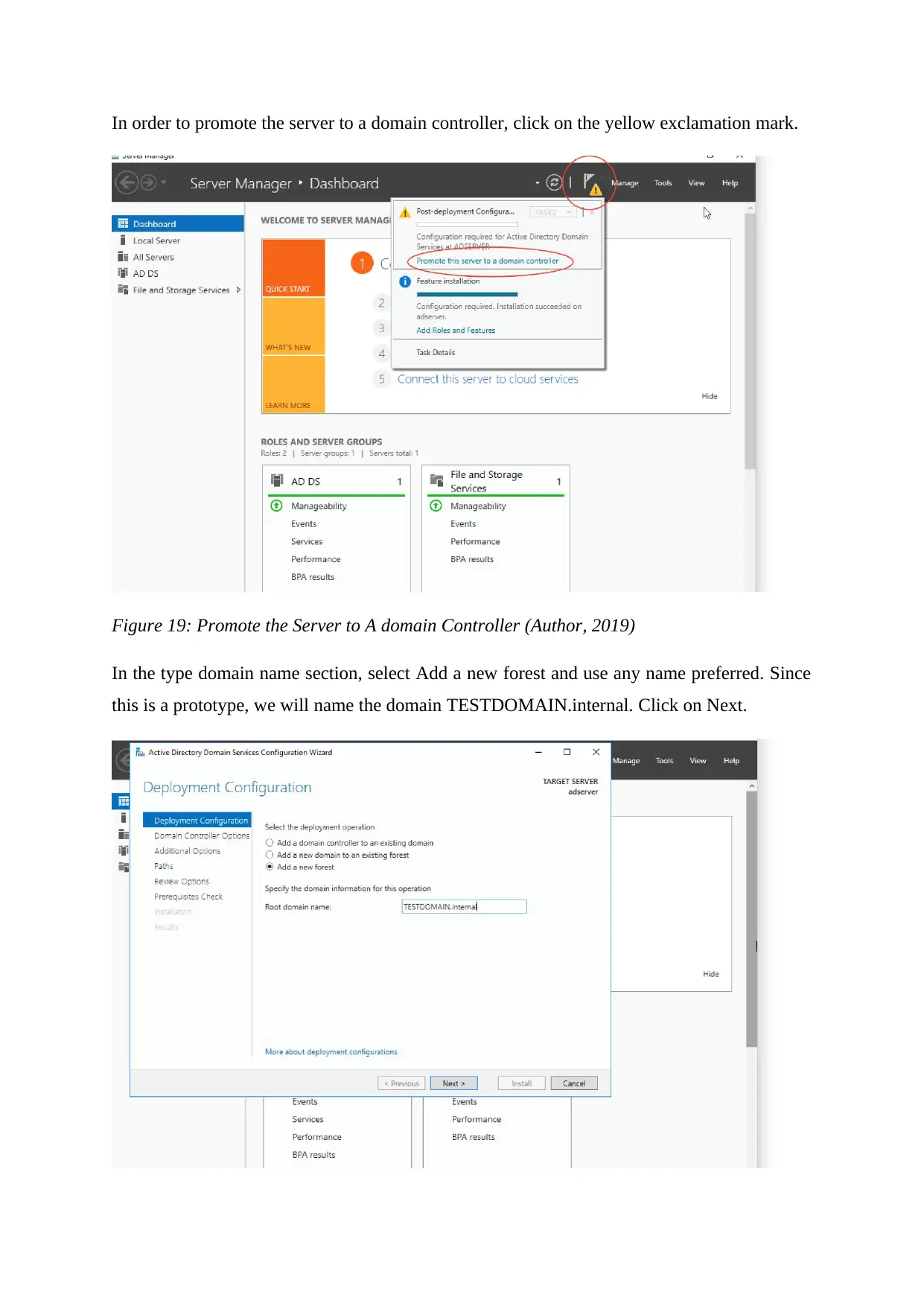
In order to promote the server to a domain controller, click on the yellow exclamation mark.
Figure 19: Promote the Server to A domain Controller (Author, 2019)
In the type domain name section, select Add a new forest and use any name preferred. Since
this is a prototype, we will name the domain TESTDOMAIN.internal. Click on Next.
Figure 19: Promote the Server to A domain Controller (Author, 2019)
In the type domain name section, select Add a new forest and use any name preferred. Since
this is a prototype, we will name the domain TESTDOMAIN.internal. Click on Next.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
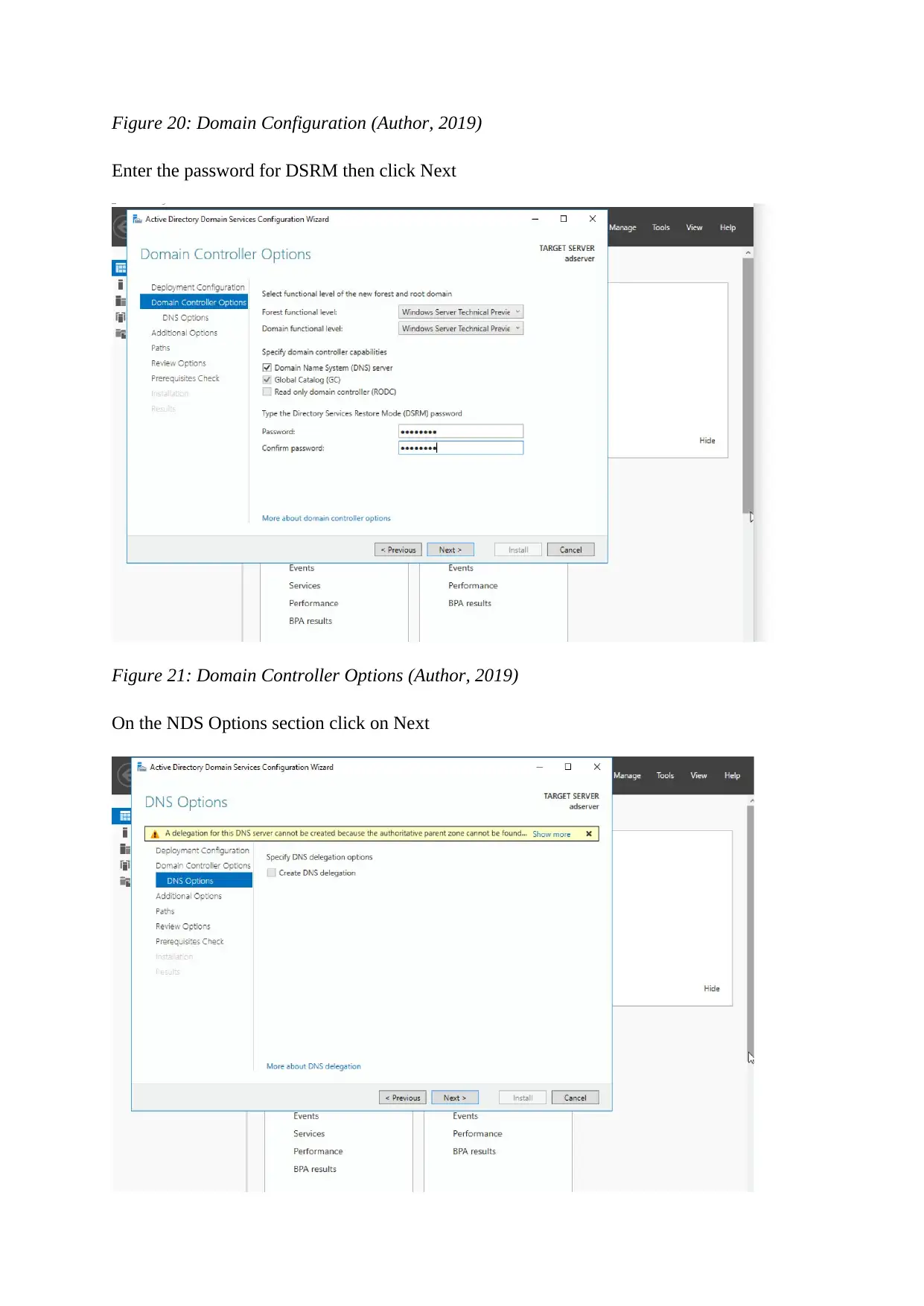
Figure 20: Domain Configuration (Author, 2019)
Enter the password for DSRM then click Next
Figure 21: Domain Controller Options (Author, 2019)
On the NDS Options section click on Next
Enter the password for DSRM then click Next
Figure 21: Domain Controller Options (Author, 2019)
On the NDS Options section click on Next
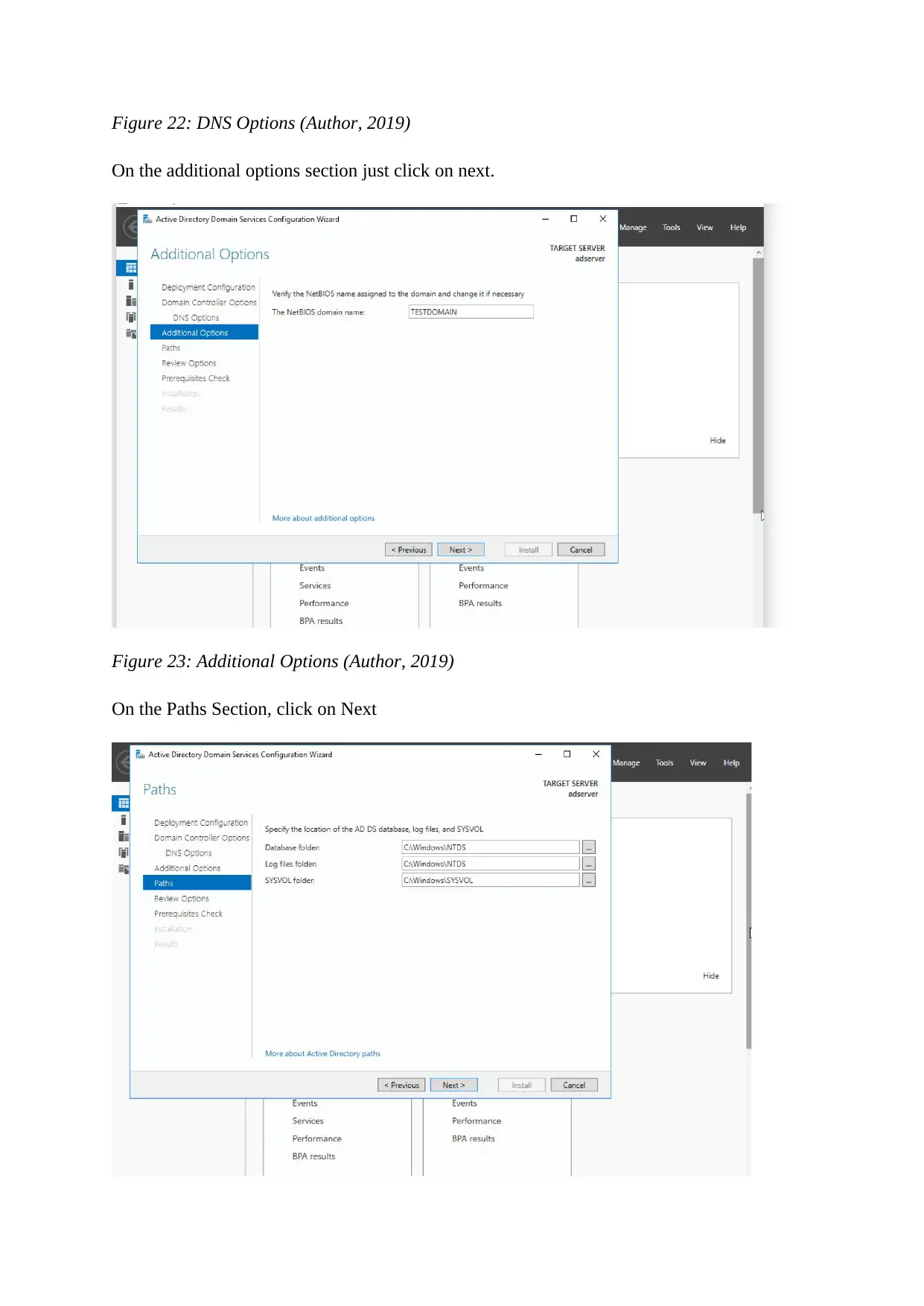
Figure 22: DNS Options (Author, 2019)
On the additional options section just click on next.
Figure 23: Additional Options (Author, 2019)
On the Paths Section, click on Next
On the additional options section just click on next.
Figure 23: Additional Options (Author, 2019)
On the Paths Section, click on Next
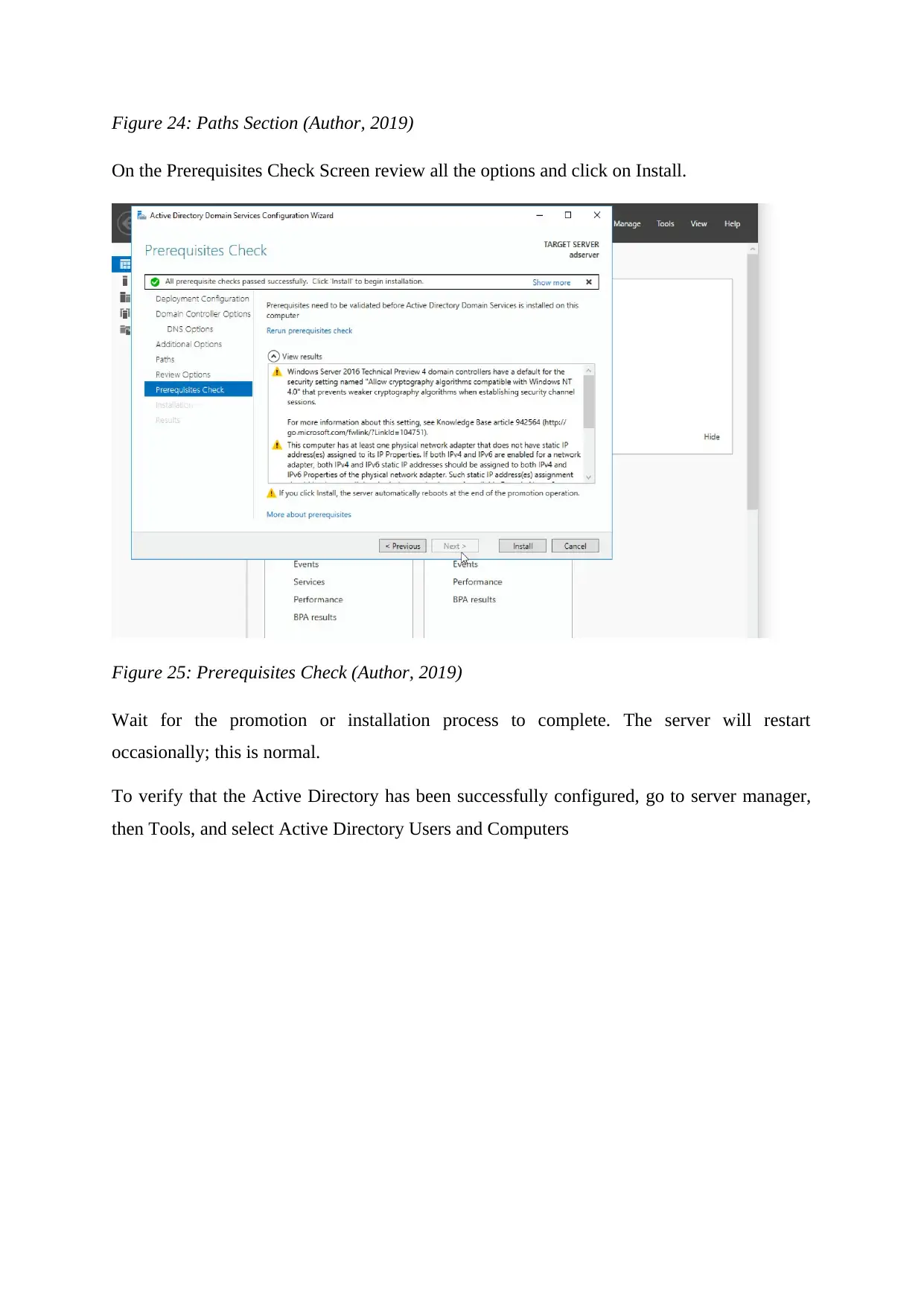
Figure 24: Paths Section (Author, 2019)
On the Prerequisites Check Screen review all the options and click on Install.
Figure 25: Prerequisites Check (Author, 2019)
Wait for the promotion or installation process to complete. The server will restart
occasionally; this is normal.
To verify that the Active Directory has been successfully configured, go to server manager,
then Tools, and select Active Directory Users and Computers
On the Prerequisites Check Screen review all the options and click on Install.
Figure 25: Prerequisites Check (Author, 2019)
Wait for the promotion or installation process to complete. The server will restart
occasionally; this is normal.
To verify that the Active Directory has been successfully configured, go to server manager,
then Tools, and select Active Directory Users and Computers
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
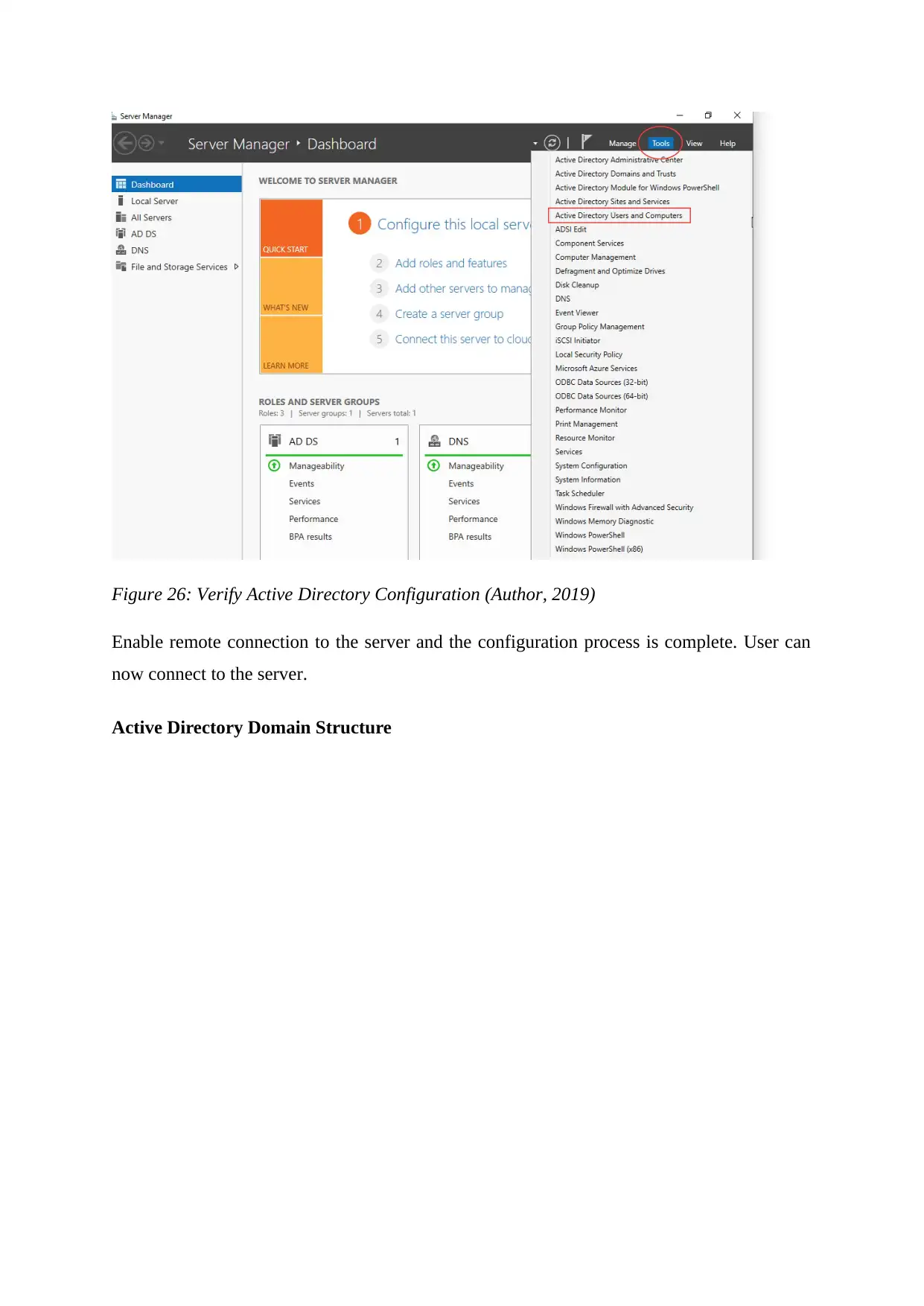
Figure 26: Verify Active Directory Configuration (Author, 2019)
Enable remote connection to the server and the configuration process is complete. User can
now connect to the server.
Active Directory Domain Structure
Enable remote connection to the server and the configuration process is complete. User can
now connect to the server.
Active Directory Domain Structure
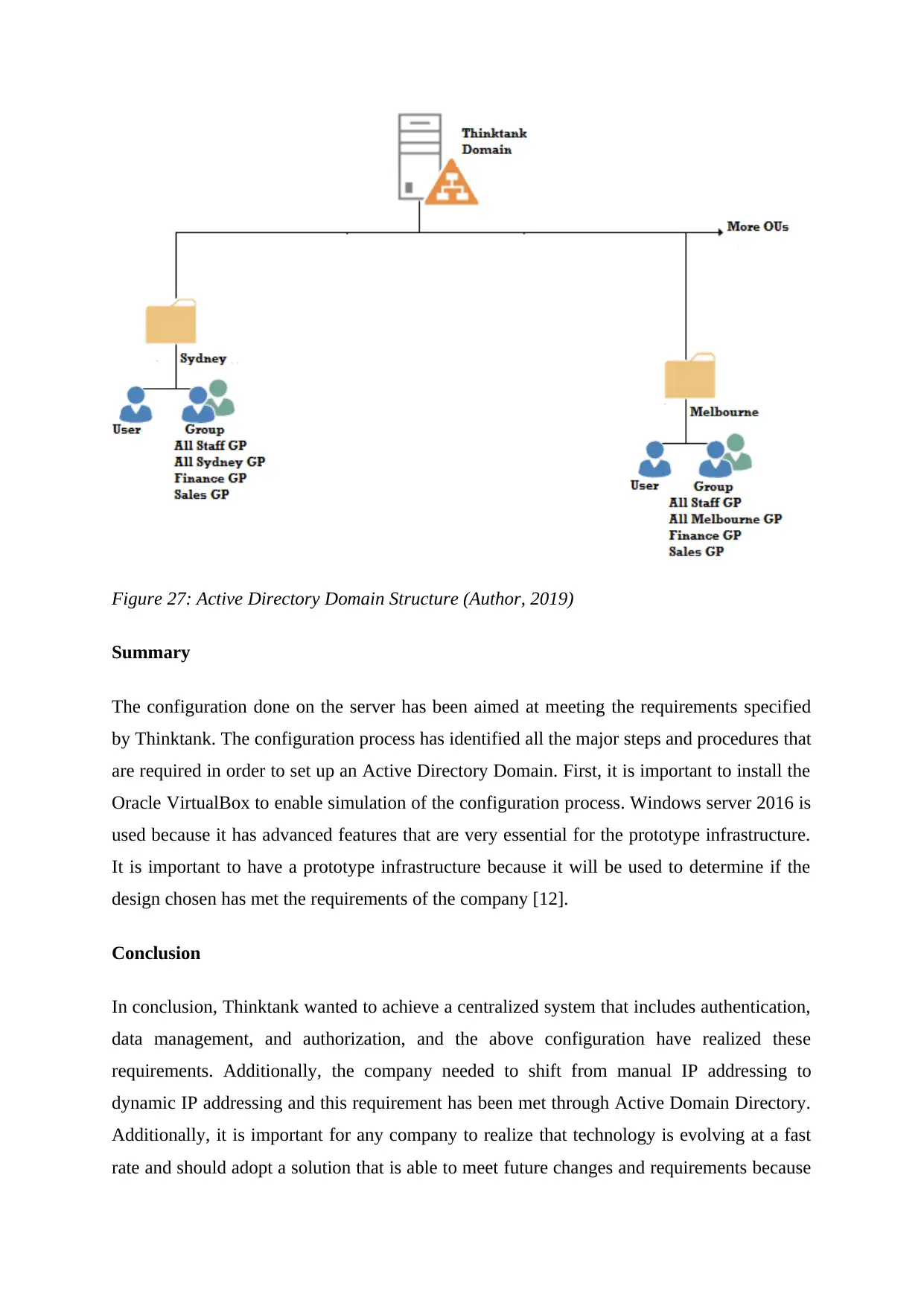
Figure 27: Active Directory Domain Structure (Author, 2019)
Summary
The configuration done on the server has been aimed at meeting the requirements specified
by Thinktank. The configuration process has identified all the major steps and procedures that
are required in order to set up an Active Directory Domain. First, it is important to install the
Oracle VirtualBox to enable simulation of the configuration process. Windows server 2016 is
used because it has advanced features that are very essential for the prototype infrastructure.
It is important to have a prototype infrastructure because it will be used to determine if the
design chosen has met the requirements of the company [12].
Conclusion
In conclusion, Thinktank wanted to achieve a centralized system that includes authentication,
data management, and authorization, and the above configuration have realized these
requirements. Additionally, the company needed to shift from manual IP addressing to
dynamic IP addressing and this requirement has been met through Active Domain Directory.
Additionally, it is important for any company to realize that technology is evolving at a fast
rate and should adopt a solution that is able to meet future changes and requirements because
Summary
The configuration done on the server has been aimed at meeting the requirements specified
by Thinktank. The configuration process has identified all the major steps and procedures that
are required in order to set up an Active Directory Domain. First, it is important to install the
Oracle VirtualBox to enable simulation of the configuration process. Windows server 2016 is
used because it has advanced features that are very essential for the prototype infrastructure.
It is important to have a prototype infrastructure because it will be used to determine if the
design chosen has met the requirements of the company [12].
Conclusion
In conclusion, Thinktank wanted to achieve a centralized system that includes authentication,
data management, and authorization, and the above configuration have realized these
requirements. Additionally, the company needed to shift from manual IP addressing to
dynamic IP addressing and this requirement has been met through Active Domain Directory.
Additionally, it is important for any company to realize that technology is evolving at a fast
rate and should adopt a solution that is able to meet future changes and requirements because

of the dynamic nature of technology involve. There are several advantages associated with
computer networks including helping the business to grow as it improves business operations
and overall efficiency. Also, it enhances cost-effectiveness because it facilitates sharing of
resources such as printers, applications, data, and files. This is because the company will not
need to buy equipment for every employee rather, they will be able to share what is available.
computer networks including helping the business to grow as it improves business operations
and overall efficiency. Also, it enhances cost-effectiveness because it facilitates sharing of
resources such as printers, applications, data, and files. This is because the company will not
need to buy equipment for every employee rather, they will be able to share what is available.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
[1] T. Inspired, "The Main Benefits of Computer Networking in 2017", Inspired Techs, 2019.
[Online]. Available: https://www.inspiredtechs.com.au/computer-networking/.
[Accessed: 23- May- 2019].
[2] J. Perez, "Importance of Computer Networking", Techwalla, 2019. [Online]. Available:
https://www.techwalla.com/articles/importance-of-computer-networking. [Accessed: 23-
May- 2019].
[3] A. Minocha, "Generating domain specific sentiment lexicons using the Web
Directory", Advanced Computing: An International Journal, vol. 3, no. 5, pp. 45-51,
2012. Available: 10.5121/acij.2012.3505.
[4] Z. ZHANG, J. LIU and H. WANG, "Performance analysis and optimization of network
server based on queuing network", Journal of Computer Applications, vol. 30, no. 12,
pp. 3148-3150, 2011. Available: 10.3724/sp.j.1087.2010.03148.
[5] R. Mohan, "Network Analysis and Application Control Software based on Client-Server
Architecture", International Journal of Computer Applications, vol. 68, no. 12, pp. 34-
39, 2013. Available: 10.5120/11634-7111.
[6] T. Techdonut.co.uk, "Network servers overview", Techdonut.co.uk, 2010. [Online].
Available: https://www.techdonut.co.uk/computer-hardware/network-servers/network-
servers-overview. [Accessed: 23- May- 2019].
[7] P. Bajpai, "Advantages of Using a Server", Iitk.ac.in, 2019. [Online]. Available:
https://www.iitk.ac.in/ccnew/index.php/8-servers/102-advantages-of-using-a-server.
[Accessed: 23- May- 2019].
[8] T. Fisher, "What Is DHCP? (Dynamic Host Configuration Protocol)", Lifewire, 2019.
[Online]. Available: https://www.lifewire.com/what-is-dhcp-2625848. [Accessed: 23-
May- 2019].
[9] J. Carter and K. Rajamani, "Designing Energy-Efficient Servers and Data
Centers", Computer, vol. 43, no. 7, pp. 76-78, 2010. Available: 10.1109/mc.2010.198.
[10] L. Hunter and R. Allen, Active directory cookbook. Sebastopol, CA: O'Reilly, 2013.
[1] T. Inspired, "The Main Benefits of Computer Networking in 2017", Inspired Techs, 2019.
[Online]. Available: https://www.inspiredtechs.com.au/computer-networking/.
[Accessed: 23- May- 2019].
[2] J. Perez, "Importance of Computer Networking", Techwalla, 2019. [Online]. Available:
https://www.techwalla.com/articles/importance-of-computer-networking. [Accessed: 23-
May- 2019].
[3] A. Minocha, "Generating domain specific sentiment lexicons using the Web
Directory", Advanced Computing: An International Journal, vol. 3, no. 5, pp. 45-51,
2012. Available: 10.5121/acij.2012.3505.
[4] Z. ZHANG, J. LIU and H. WANG, "Performance analysis and optimization of network
server based on queuing network", Journal of Computer Applications, vol. 30, no. 12,
pp. 3148-3150, 2011. Available: 10.3724/sp.j.1087.2010.03148.
[5] R. Mohan, "Network Analysis and Application Control Software based on Client-Server
Architecture", International Journal of Computer Applications, vol. 68, no. 12, pp. 34-
39, 2013. Available: 10.5120/11634-7111.
[6] T. Techdonut.co.uk, "Network servers overview", Techdonut.co.uk, 2010. [Online].
Available: https://www.techdonut.co.uk/computer-hardware/network-servers/network-
servers-overview. [Accessed: 23- May- 2019].
[7] P. Bajpai, "Advantages of Using a Server", Iitk.ac.in, 2019. [Online]. Available:
https://www.iitk.ac.in/ccnew/index.php/8-servers/102-advantages-of-using-a-server.
[Accessed: 23- May- 2019].
[8] T. Fisher, "What Is DHCP? (Dynamic Host Configuration Protocol)", Lifewire, 2019.
[Online]. Available: https://www.lifewire.com/what-is-dhcp-2625848. [Accessed: 23-
May- 2019].
[9] J. Carter and K. Rajamani, "Designing Energy-Efficient Servers and Data
Centers", Computer, vol. 43, no. 7, pp. 76-78, 2010. Available: 10.1109/mc.2010.198.
[10] L. Hunter and R. Allen, Active directory cookbook. Sebastopol, CA: O'Reilly, 2013.

[11] B. Desmond, Active directory. Farnham: O'Reilly, 2013.
[12] Y. Guangli, "The Design and Implementation of Ducational Resource Management in
Colleges and Universities with Active Directory", Energy Procedia, vol. 11, pp. 418-
423, 2011. Available: 10.1016/j.egypro.2011.10.262.
[12] Y. Guangli, "The Design and Implementation of Ducational Resource Management in
Colleges and Universities with Active Directory", Energy Procedia, vol. 11, pp. 418-
423, 2011. Available: 10.1016/j.egypro.2011.10.262.
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





