Network Infrastructure Design for Thinktank
VerifiedAdded on 2023/03/20
|23
|2963
|87
AI Summary
This report focuses on analyzing the requirements of Thinktank, identifying the different servers required and the roles they play in the network, and providing configuration information that has been taken in setting up the network.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

System Management
Student Name
Course
Institution
Date
Student Name
Course
Institution
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Introduction
Computer networks has become one of the primary needs of any business. A network refers
to an interconnection of many devices including servers, routers, switches, laptops, desktops,
smartphones, among other network components for the purpose of sharing critical resources
and effective communication [1]. Having this in mind, it is important that when designing a
network, it is necessary to carry out and analysis of the situation before coming up with a list
of requirements and objectives [2]. This report focuses on analyzing the requirements of
Thinktank, identifying the different servers required and the roles they play in the network,
and providing configuration information that has been taken in setting up the network.
Case Problem
Thinktank is a small enterprise company that is based in Sydney. The company has grown
over the years and now it has 50 computers from the initial 10 computers. The company also
plans to expand and open up a new branch in Melbourne that will be directly connected to the
head quarters (HQ) in Sydney. More employees will be hired to fill the positions in
Melbourne and will have similar number of employees as those in the HQ. The company
needs to buy new computing equipment for the new branch. The company also hopes to
achieve centralize data management location, authorization, and authentication. Additionally,
the company wants to have separate folders for both offices which can only be specifically
accessed by individual branches. Moreover, the sales departments in both offices will have
separate folders to carry out their respective tasks. Managers in both offices will have access
to the entire data folder.
The current setup within Thinktank is that the data is store on two computers which are
basically workgroup computers; the data is accessible to 28 employees from various
departments: 3 managers, 20 employees from the sales department, and 5 in Finance. The IT
department is also facing a big challenge because IP addresses are assigned manually and
some computers may be assigned similar IP addresses and this often end up disrupting
network services because of duplication issues.
This has made it challenging and difficult for the company to manage and share resources
and communication. This is because the current network infrastructure has been poorly
designed, does not support scalability, or additional of more devices. The company is
Computer networks has become one of the primary needs of any business. A network refers
to an interconnection of many devices including servers, routers, switches, laptops, desktops,
smartphones, among other network components for the purpose of sharing critical resources
and effective communication [1]. Having this in mind, it is important that when designing a
network, it is necessary to carry out and analysis of the situation before coming up with a list
of requirements and objectives [2]. This report focuses on analyzing the requirements of
Thinktank, identifying the different servers required and the roles they play in the network,
and providing configuration information that has been taken in setting up the network.
Case Problem
Thinktank is a small enterprise company that is based in Sydney. The company has grown
over the years and now it has 50 computers from the initial 10 computers. The company also
plans to expand and open up a new branch in Melbourne that will be directly connected to the
head quarters (HQ) in Sydney. More employees will be hired to fill the positions in
Melbourne and will have similar number of employees as those in the HQ. The company
needs to buy new computing equipment for the new branch. The company also hopes to
achieve centralize data management location, authorization, and authentication. Additionally,
the company wants to have separate folders for both offices which can only be specifically
accessed by individual branches. Moreover, the sales departments in both offices will have
separate folders to carry out their respective tasks. Managers in both offices will have access
to the entire data folder.
The current setup within Thinktank is that the data is store on two computers which are
basically workgroup computers; the data is accessible to 28 employees from various
departments: 3 managers, 20 employees from the sales department, and 5 in Finance. The IT
department is also facing a big challenge because IP addresses are assigned manually and
some computers may be assigned similar IP addresses and this often end up disrupting
network services because of duplication issues.
This has made it challenging and difficult for the company to manage and share resources
and communication. This is because the current network infrastructure has been poorly
designed, does not support scalability, or additional of more devices. The company is

growing at a fast rate and need to have a new network infrastructure. As a result, the
company wants to restructure its IT infrastructure to enable central management of resources,
effective communication, and the data center which be located in the headquarters. The new
design will make sure that Thinktank is able to meet the different business goals by
improving communication and business processes.
Other issues currently being experienced by the company is the fact that users need to
remember the IP addresses of the computer holding the data in order to access it.
Remembering IP addresses is very difficult. Also, the company wishes to achieve fault
tolerance.
Requirement Analysis
There are several factors that need to be addressed when setting up the new network
infrastructure. This is important in addressing the network management and administration
challenges in today’s network environment [3]. First, it is important to plan for your network.
This involves understanding the need and the services that the network will provided
including monitoring and management functions. Understanding the reality of the Thinktank
network situation will enable easy planning and implementation [4].
The network should also have the capabilities to avoid outages and offer high availability.
This will be achieved by predicting the growth of the within the company so as to prepare for
any possible rapid configurations and growth to enable integration of reporting and capacity
tools to help in planning for the future needs [5]. Additionally, strategies and guidelines to
implement whenever an outage occurs as a result of unexpected network configuration issues
and growth are necessary.
Scalability: the network should be able to support easy expansion of the network by adding
more devices and users on the network without affecting the normal network operations. This
is an important objective because of the growth that the company is experiencing and thus,
there is need to have a scalable network [6]. Additionally, the company wants to expand its
services to other cities such as Sydney and Perth and wants to ensure that the network should
be able to accommodate the needs of the expected branches without having to setup a new
data center.
Centralized Management: another objective that the company expects is to have all the
monitoring and management of the network critical resources such as servers be done from
company wants to restructure its IT infrastructure to enable central management of resources,
effective communication, and the data center which be located in the headquarters. The new
design will make sure that Thinktank is able to meet the different business goals by
improving communication and business processes.
Other issues currently being experienced by the company is the fact that users need to
remember the IP addresses of the computer holding the data in order to access it.
Remembering IP addresses is very difficult. Also, the company wishes to achieve fault
tolerance.
Requirement Analysis
There are several factors that need to be addressed when setting up the new network
infrastructure. This is important in addressing the network management and administration
challenges in today’s network environment [3]. First, it is important to plan for your network.
This involves understanding the need and the services that the network will provided
including monitoring and management functions. Understanding the reality of the Thinktank
network situation will enable easy planning and implementation [4].
The network should also have the capabilities to avoid outages and offer high availability.
This will be achieved by predicting the growth of the within the company so as to prepare for
any possible rapid configurations and growth to enable integration of reporting and capacity
tools to help in planning for the future needs [5]. Additionally, strategies and guidelines to
implement whenever an outage occurs as a result of unexpected network configuration issues
and growth are necessary.
Scalability: the network should be able to support easy expansion of the network by adding
more devices and users on the network without affecting the normal network operations. This
is an important objective because of the growth that the company is experiencing and thus,
there is need to have a scalable network [6]. Additionally, the company wants to expand its
services to other cities such as Sydney and Perth and wants to ensure that the network should
be able to accommodate the needs of the expected branches without having to setup a new
data center.
Centralized Management: another objective that the company expects is to have all the
monitoring and management of the network critical resources such as servers be done from

one central location, the data center. As such, the design should have the capability to support
easy management, monitoring, and troubleshooting [7].
Security: Network security is a very important aspect to any company. Thinktank expects that
the new network infrastructure should be able ensure the security of the network critical
resources such as data and have strategies for mitigating risks and disaster recovery
techniques [8]. There is need to implement network security measures to protect the integrity
and usability of the company data and network. It includes software and hardware
technologies. Having effective network security mechanisms allows better management of
access to network resources [9]. There are several security mechanisms that needs to be
implemented in the network; they are discussed below.
First, access control will be implemented in the network to control access to the company
network resources. This will prevent any potential attackers who may have intentions of
intentions to access the network resources without authorization. Secondly, antimalware and
antivirus programs to prevent spyware, ransomware, Trojans, worms, and viruses from
spreading on the network [10]. Firewalls, intrusion detection and prevention systems, and
data security systems will be installed on the network. All these measures are necessary to
ensure that Thinktank technologies have secured their critical network resources from any
internal or external threats [11].
Identification of Server Roles & Technologies
Often, servers are dedicated network components with superior processing speeds and
performance that carries out only the functions assigned to them [7]. In order to achieve the
objectives of Thinktank, a number of servers are required while setting up the data center
including DHCP server, web server, file server, and print server. All these servers have
specific roles which are discussed below.
DHCP Server: it stands for Dynamic Host Control Protocol. This server is required for to
address the challenge that the company is facing of assigning IP addresses manually. DHCP
server generates and assigns IP addresses automatically to all the network component to
ensure that no IP is duplicated [9]. DHCP is necessary based on the current setup because it
sends the needed network parameters automatically to enable the clients to communicate and
share files properly on the network.
easy management, monitoring, and troubleshooting [7].
Security: Network security is a very important aspect to any company. Thinktank expects that
the new network infrastructure should be able ensure the security of the network critical
resources such as data and have strategies for mitigating risks and disaster recovery
techniques [8]. There is need to implement network security measures to protect the integrity
and usability of the company data and network. It includes software and hardware
technologies. Having effective network security mechanisms allows better management of
access to network resources [9]. There are several security mechanisms that needs to be
implemented in the network; they are discussed below.
First, access control will be implemented in the network to control access to the company
network resources. This will prevent any potential attackers who may have intentions of
intentions to access the network resources without authorization. Secondly, antimalware and
antivirus programs to prevent spyware, ransomware, Trojans, worms, and viruses from
spreading on the network [10]. Firewalls, intrusion detection and prevention systems, and
data security systems will be installed on the network. All these measures are necessary to
ensure that Thinktank technologies have secured their critical network resources from any
internal or external threats [11].
Identification of Server Roles & Technologies
Often, servers are dedicated network components with superior processing speeds and
performance that carries out only the functions assigned to them [7]. In order to achieve the
objectives of Thinktank, a number of servers are required while setting up the data center
including DHCP server, web server, file server, and print server. All these servers have
specific roles which are discussed below.
DHCP Server: it stands for Dynamic Host Control Protocol. This server is required for to
address the challenge that the company is facing of assigning IP addresses manually. DHCP
server generates and assigns IP addresses automatically to all the network component to
ensure that no IP is duplicated [9]. DHCP is necessary based on the current setup because it
sends the needed network parameters automatically to enable the clients to communicate and
share files properly on the network.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Web Server: the company aims to host the website on their own server. As a result, a web
server is needed to deliver services and contents to the end users over the internet. A web
server is basically a physical server with a software that us required to enable HTTP
communication.
Print Server: this server is responsible for managing print jobs on the network. This is
because the printer alone cannot be able to handle the huge amount of print request from the
different employees. As such, there is need to have a dedicated server that will be able to
manage and prioritize print request.
File server: this is a dedicated server that is the primary role of offering shared disk access
such as share files that can be accessed by authorized users over the network. It is primarily
designed to facilitate storage and retrieval of files over the network.
Other servers that may be implemented but not necessary for the company include:
Proxy server: this server is required to filter to enable sharing of connections, improving
network performance, and filtering traffic and is placed between web browser and another
server on the web (external server).
Mail server: mail servers plays a crucial role in managing email communication amongst the
employees and to the customers. It stores and moves emails over the company network
though LAN and over the internet.
Database server: dedicated server is needed to manage and control permissions to the data
stored in the database. It also has defined security principles on how to access the data
thorough access control policies.
Application server: an application server is required to host applications and related services
needed by Thinktank employees. It delivers high-end business and consumer applications
which are necessary to be used simultaneously and multiple connected remote or local users.
Network Configuration Process
While setting up the network the following requirements need to be considered: the company
domain is thinktank.com, and the network will be created as an active directory domain
which has a root domain. The network should ensure centralized user authentication. DHCP
server is needed to deliver services and contents to the end users over the internet. A web
server is basically a physical server with a software that us required to enable HTTP
communication.
Print Server: this server is responsible for managing print jobs on the network. This is
because the printer alone cannot be able to handle the huge amount of print request from the
different employees. As such, there is need to have a dedicated server that will be able to
manage and prioritize print request.
File server: this is a dedicated server that is the primary role of offering shared disk access
such as share files that can be accessed by authorized users over the network. It is primarily
designed to facilitate storage and retrieval of files over the network.
Other servers that may be implemented but not necessary for the company include:
Proxy server: this server is required to filter to enable sharing of connections, improving
network performance, and filtering traffic and is placed between web browser and another
server on the web (external server).
Mail server: mail servers plays a crucial role in managing email communication amongst the
employees and to the customers. It stores and moves emails over the company network
though LAN and over the internet.
Database server: dedicated server is needed to manage and control permissions to the data
stored in the database. It also has defined security principles on how to access the data
thorough access control policies.
Application server: an application server is required to host applications and related services
needed by Thinktank employees. It delivers high-end business and consumer applications
which are necessary to be used simultaneously and multiple connected remote or local users.
Network Configuration Process
While setting up the network the following requirements need to be considered: the company
domain is thinktank.com, and the network will be created as an active directory domain
which has a root domain. The network should ensure centralized user authentication. DHCP
will be used to assign IP addresses automatically to the clients. The following are necessary
for configuring the network:
Domain name system (DNS) is essential for Active Directory to operate as DNS is used to
establish the services that are available on the domain and what is provided by who [11].
Lightweight Directory Access Control (LDAP) is required to keep track of network activities.
Kerberos will be used to handle single sign on because it facilitates use of one password and
username to access multiple computers.
To build the network we will need Windows Server and Oracle VirualBox Tool. The
specifications are 30GB HDD storage, 2GB RAM, and 2 vCPU. We will create a Host-Only
network for Thinktank.
Configuration Screenshots
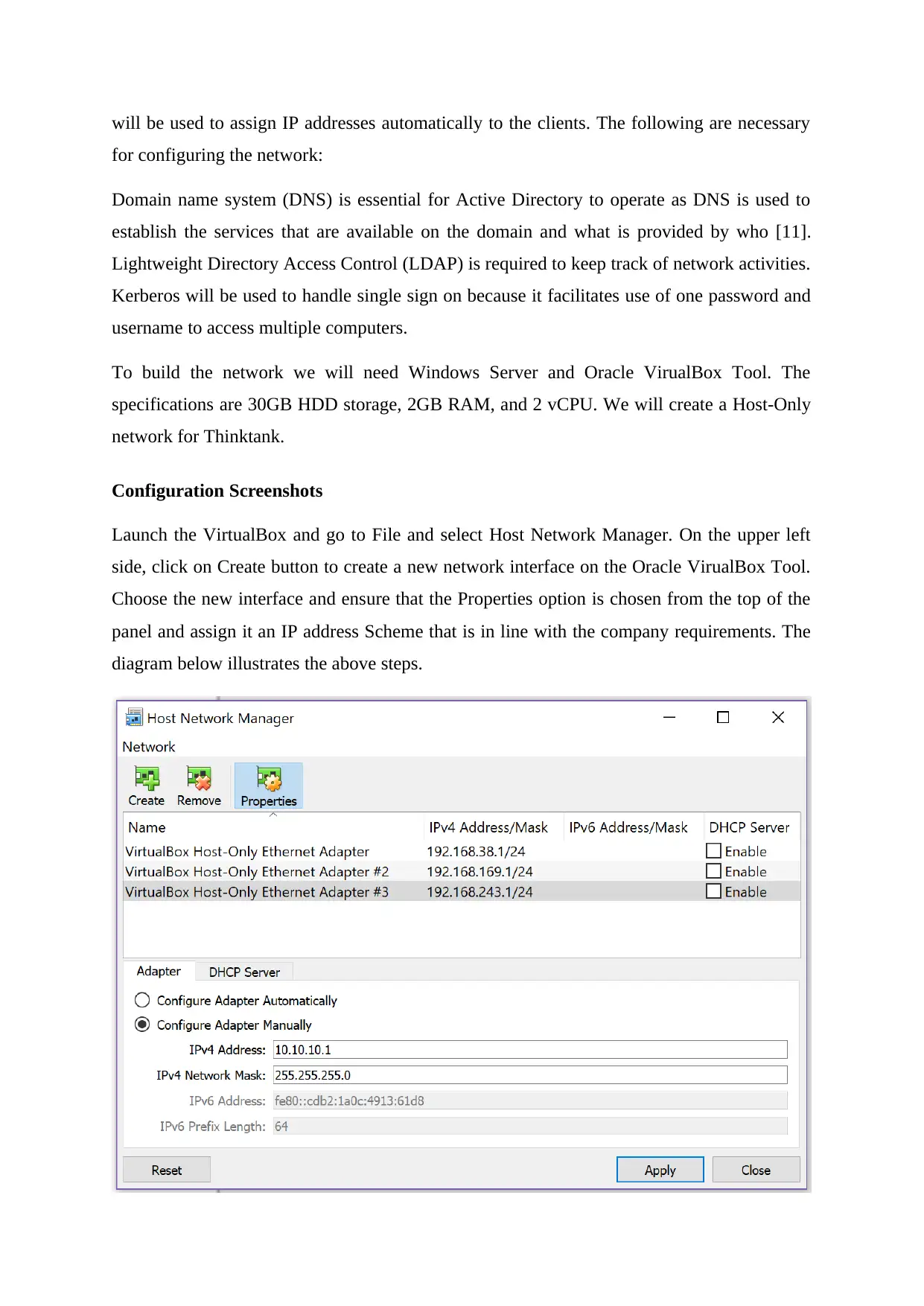
Launch the VirtualBox and go to File and select Host Network Manager. On the upper left
side, click on Create button to create a new network interface on the Oracle VirualBox Tool.
Choose the new interface and ensure that the Properties option is chosen from the top of the
panel and assign it an IP address Scheme that is in line with the company requirements. The
diagram below illustrates the above steps.
for configuring the network:
Domain name system (DNS) is essential for Active Directory to operate as DNS is used to
establish the services that are available on the domain and what is provided by who [11].
Lightweight Directory Access Control (LDAP) is required to keep track of network activities.
Kerberos will be used to handle single sign on because it facilitates use of one password and
username to access multiple computers.
To build the network we will need Windows Server and Oracle VirualBox Tool. The
specifications are 30GB HDD storage, 2GB RAM, and 2 vCPU. We will create a Host-Only
network for Thinktank.
Configuration Screenshots
Launch the VirtualBox and go to File and select Host Network Manager. On the upper left
side, click on Create button to create a new network interface on the Oracle VirualBox Tool.
Choose the new interface and ensure that the Properties option is chosen from the top of the
panel and assign it an IP address Scheme that is in line with the company requirements. The
diagram below illustrates the above steps.
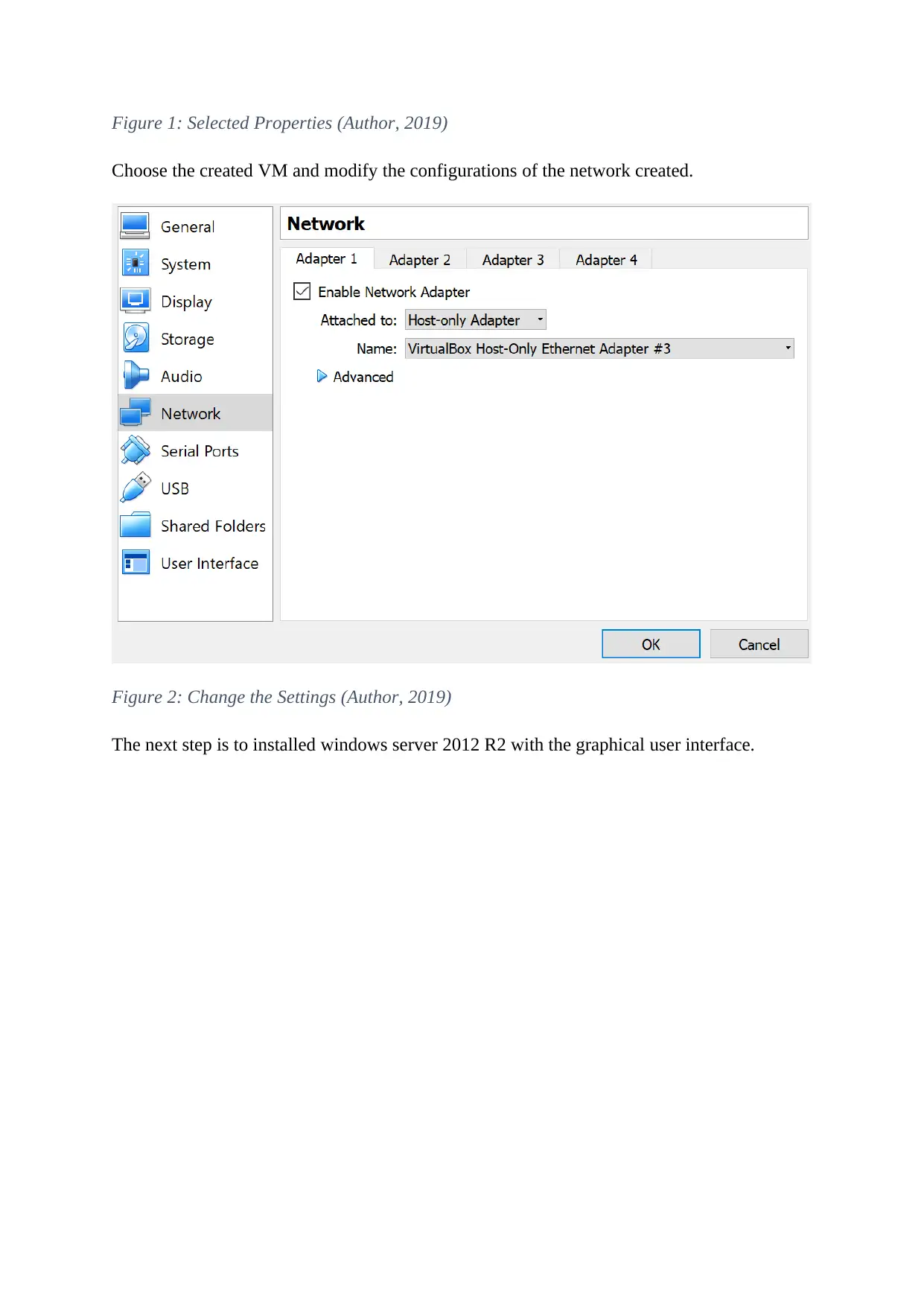
Figure 1: Selected Properties (Author, 2019)
Choose the created VM and modify the configurations of the network created.
Figure 2: Change the Settings (Author, 2019)
The next step is to installed windows server 2012 R2 with the graphical user interface.
Choose the created VM and modify the configurations of the network created.
Figure 2: Change the Settings (Author, 2019)
The next step is to installed windows server 2012 R2 with the graphical user interface.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
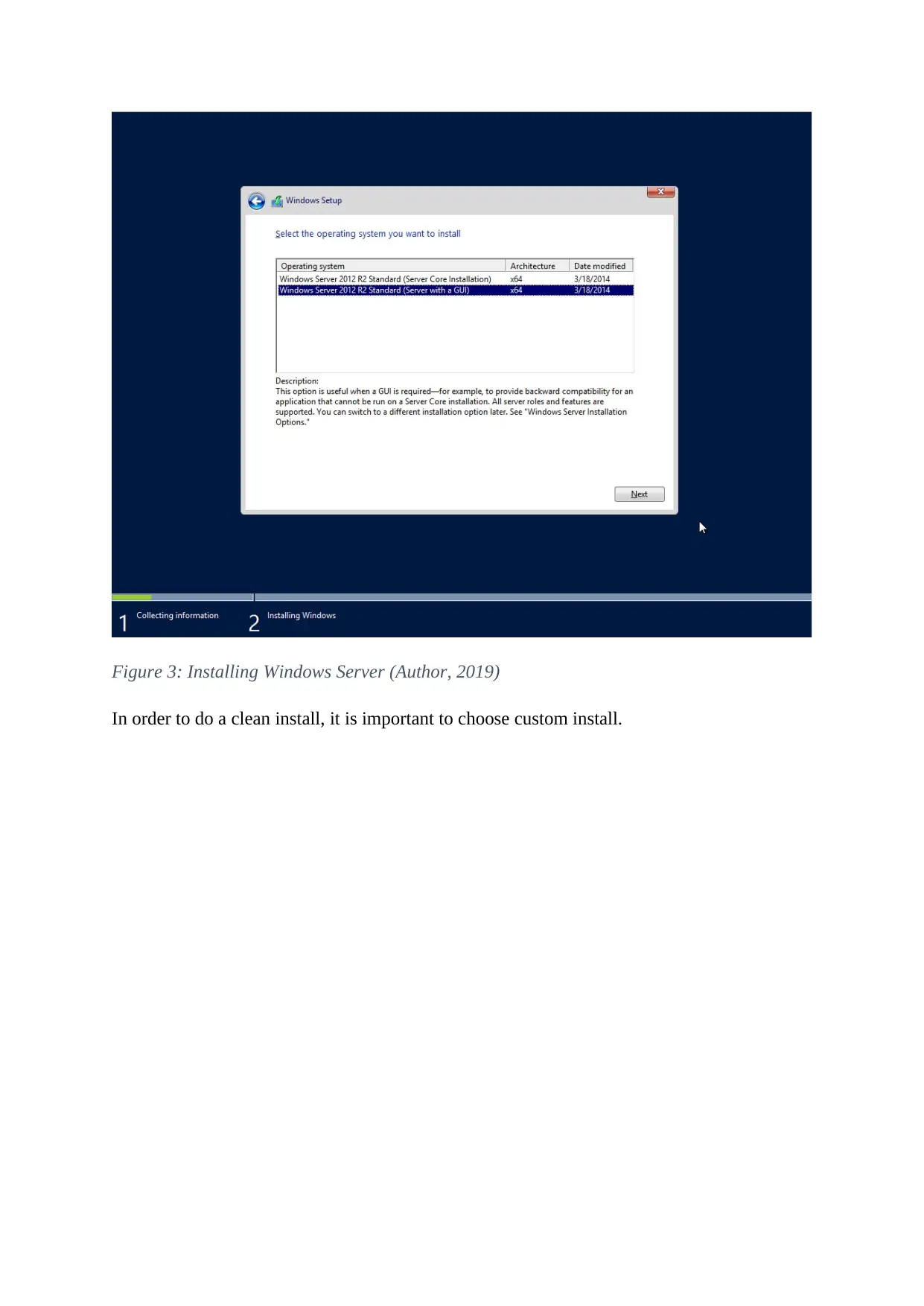
Figure 3: Installing Windows Server (Author, 2019)
In order to do a clean install, it is important to choose custom install.
In order to do a clean install, it is important to choose custom install.
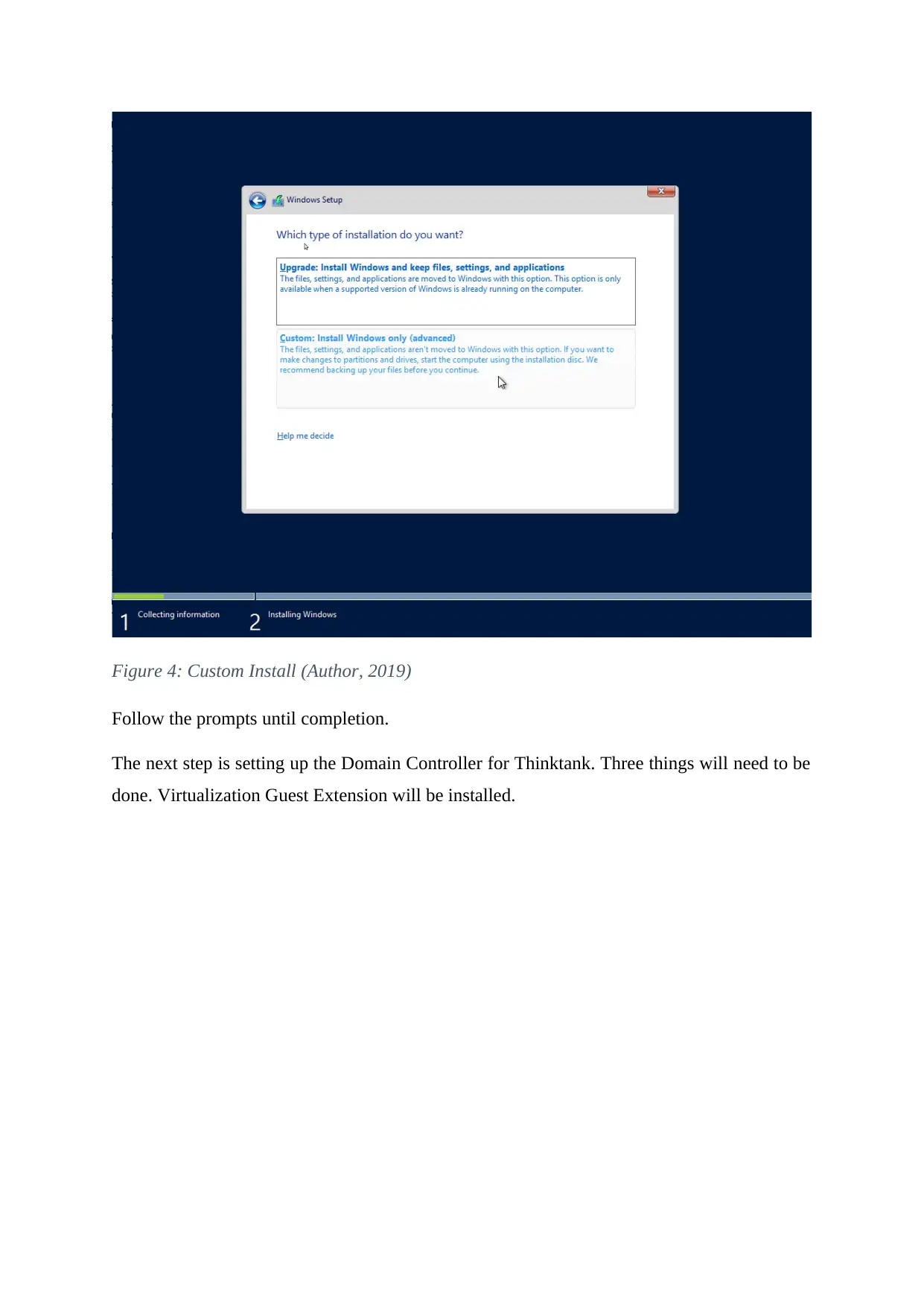
Figure 4: Custom Install (Author, 2019)
Follow the prompts until completion.
The next step is setting up the Domain Controller for Thinktank. Three things will need to be
done. Virtualization Guest Extension will be installed.
Follow the prompts until completion.
The next step is setting up the Domain Controller for Thinktank. Three things will need to be
done. Virtualization Guest Extension will be installed.
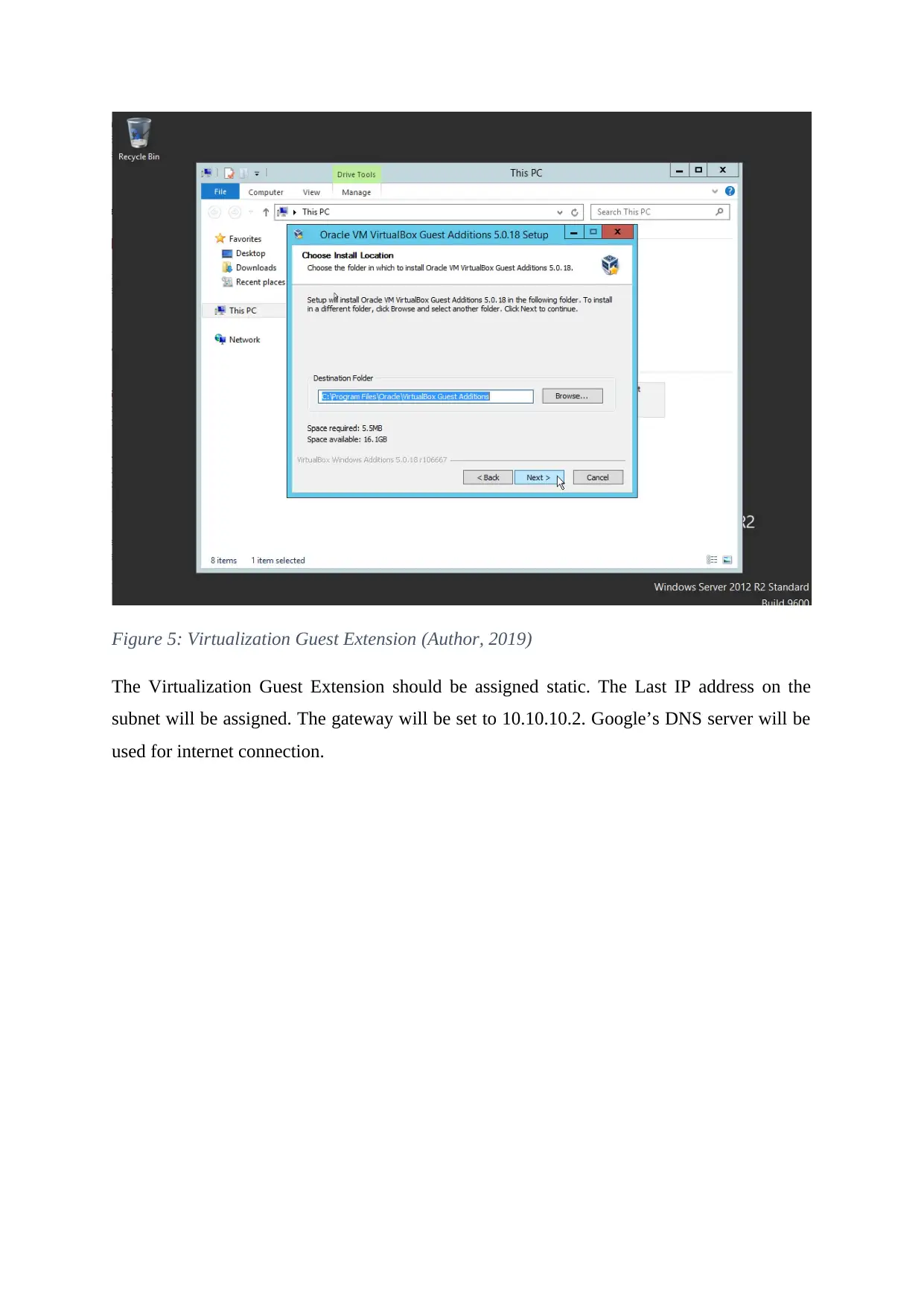
Figure 5: Virtualization Guest Extension (Author, 2019)
The Virtualization Guest Extension should be assigned static. The Last IP address on the
subnet will be assigned. The gateway will be set to 10.10.10.2. Google’s DNS server will be
used for internet connection.
The Virtualization Guest Extension should be assigned static. The Last IP address on the
subnet will be assigned. The gateway will be set to 10.10.10.2. Google’s DNS server will be
used for internet connection.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
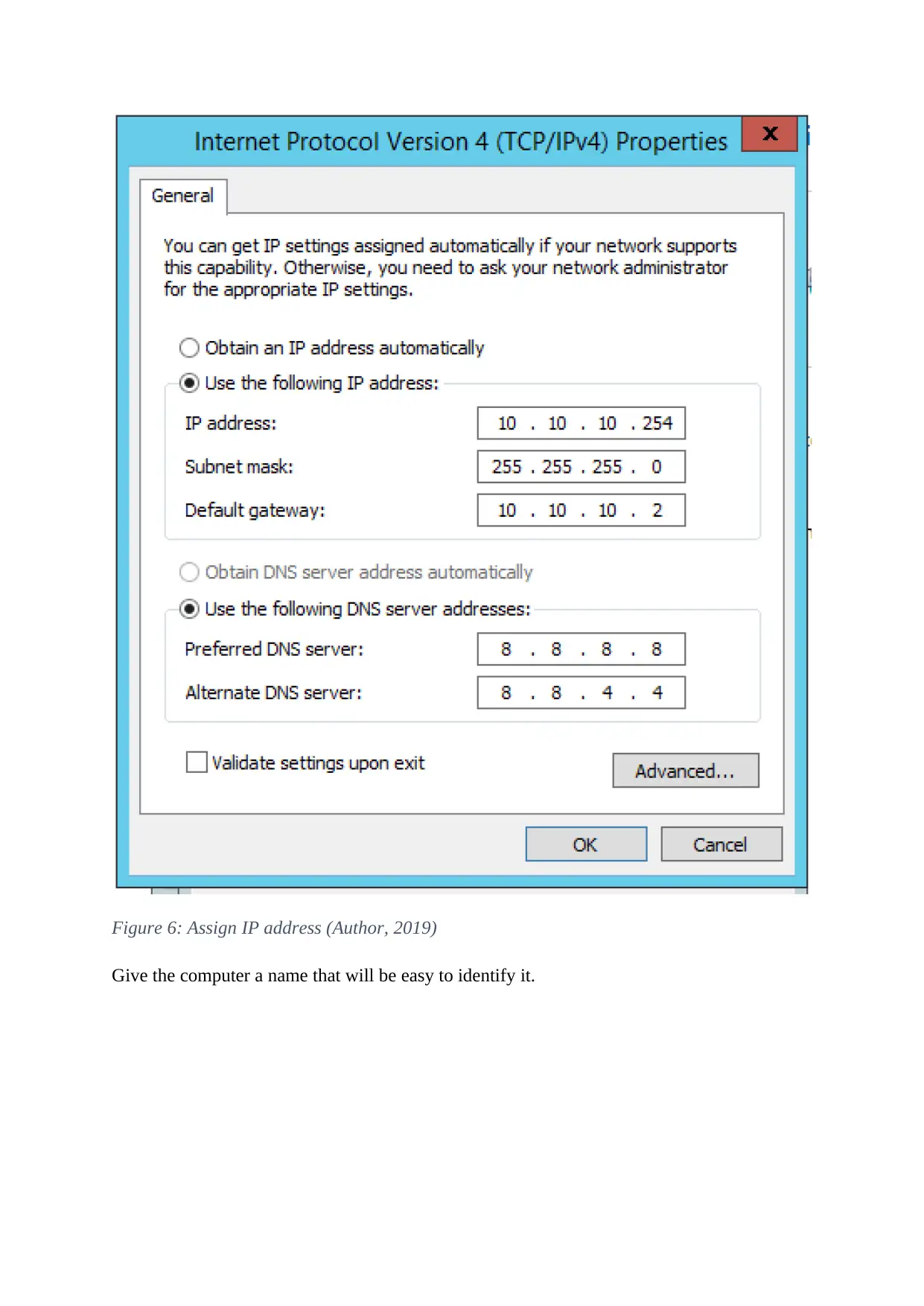
Figure 6: Assign IP address (Author, 2019)
Give the computer a name that will be easy to identify it.
Give the computer a name that will be easy to identify it.
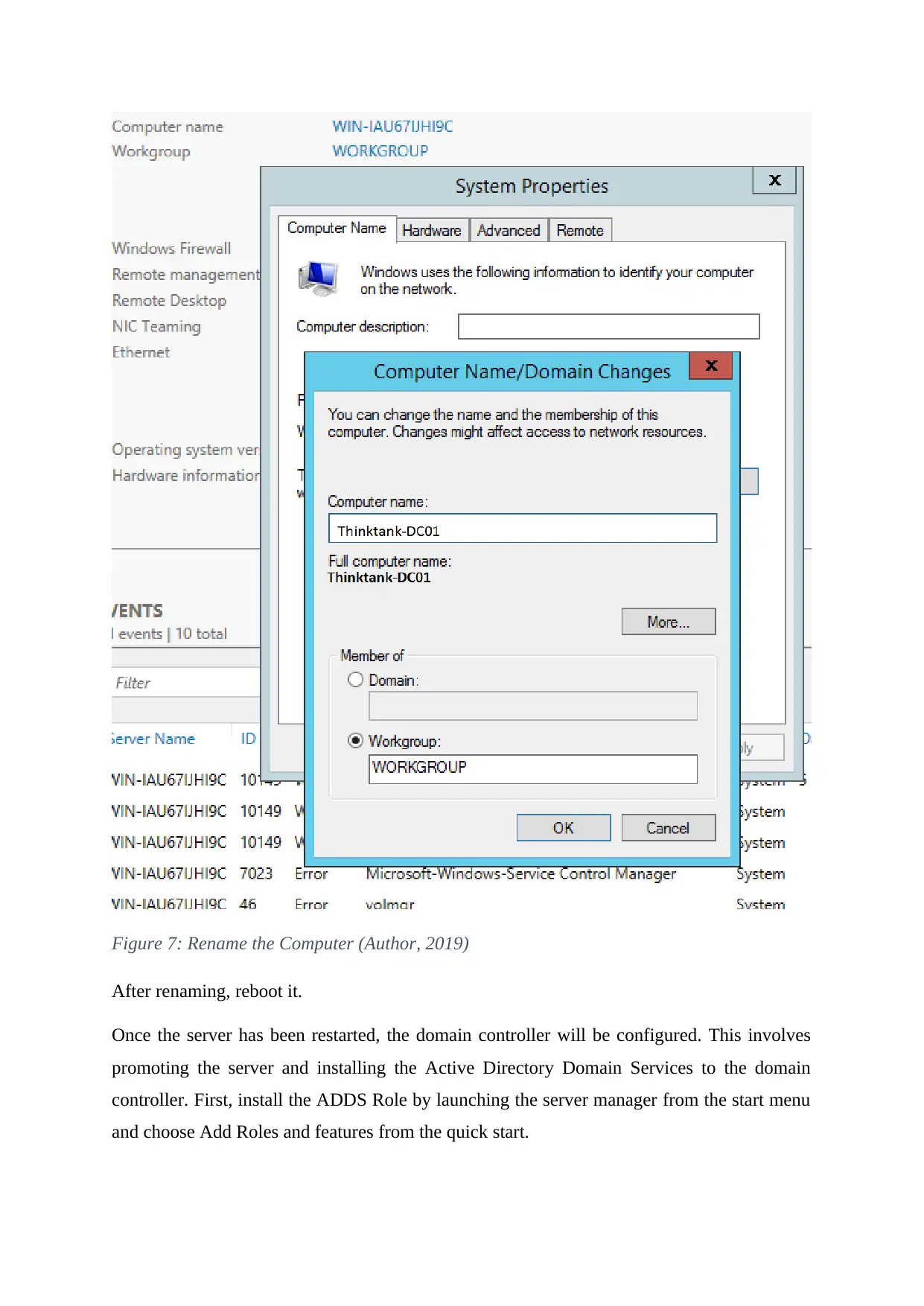
Figure 7: Rename the Computer (Author, 2019)
After renaming, reboot it.
Once the server has been restarted, the domain controller will be configured. This involves
promoting the server and installing the Active Directory Domain Services to the domain
controller. First, install the ADDS Role by launching the server manager from the start menu
and choose Add Roles and features from the quick start.
After renaming, reboot it.
Once the server has been restarted, the domain controller will be configured. This involves
promoting the server and installing the Active Directory Domain Services to the domain
controller. First, install the ADDS Role by launching the server manager from the start menu
and choose Add Roles and features from the quick start.
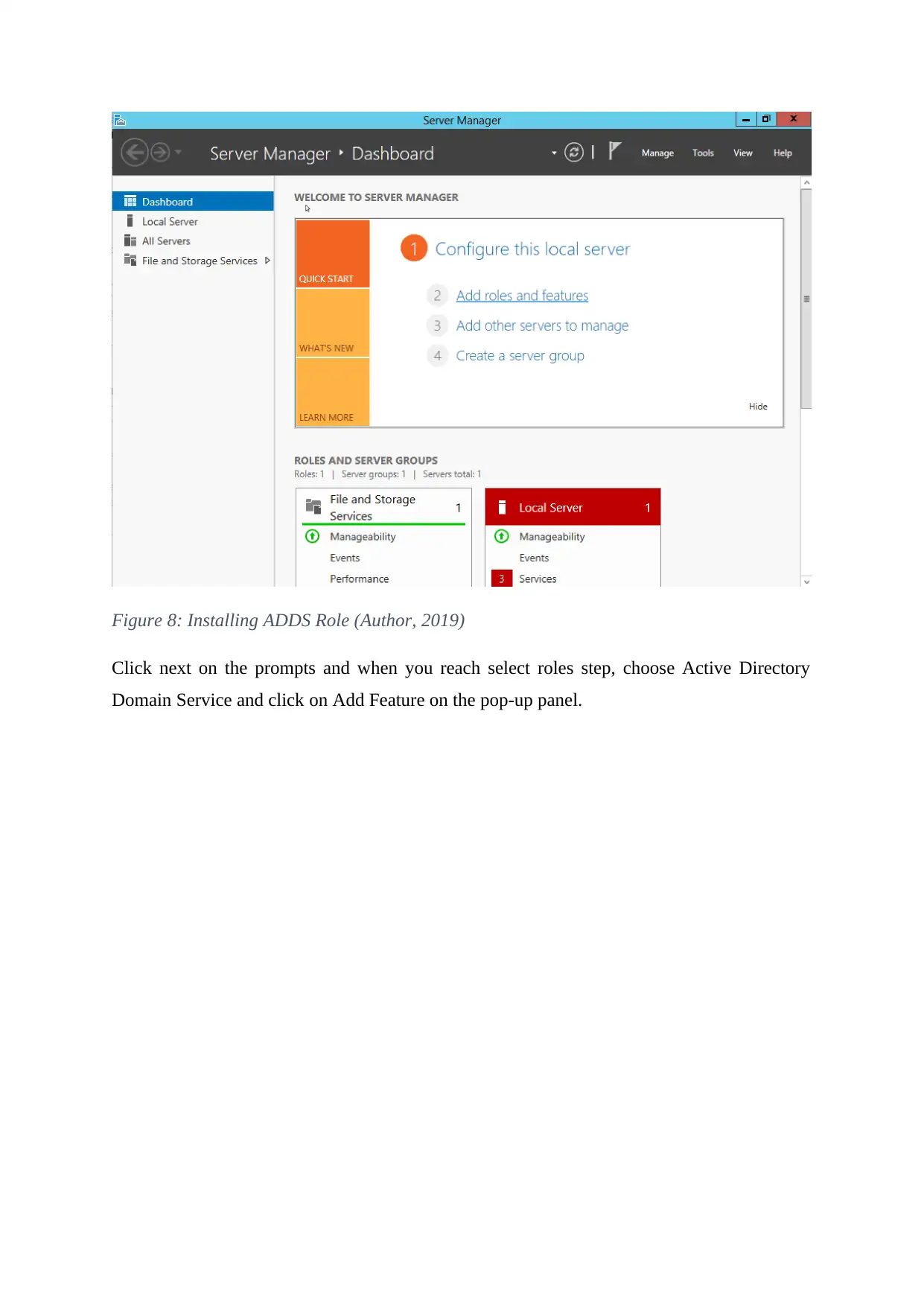
Figure 8: Installing ADDS Role (Author, 2019)
Click next on the prompts and when you reach select roles step, choose Active Directory
Domain Service and click on Add Feature on the pop-up panel.
Click next on the prompts and when you reach select roles step, choose Active Directory
Domain Service and click on Add Feature on the pop-up panel.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
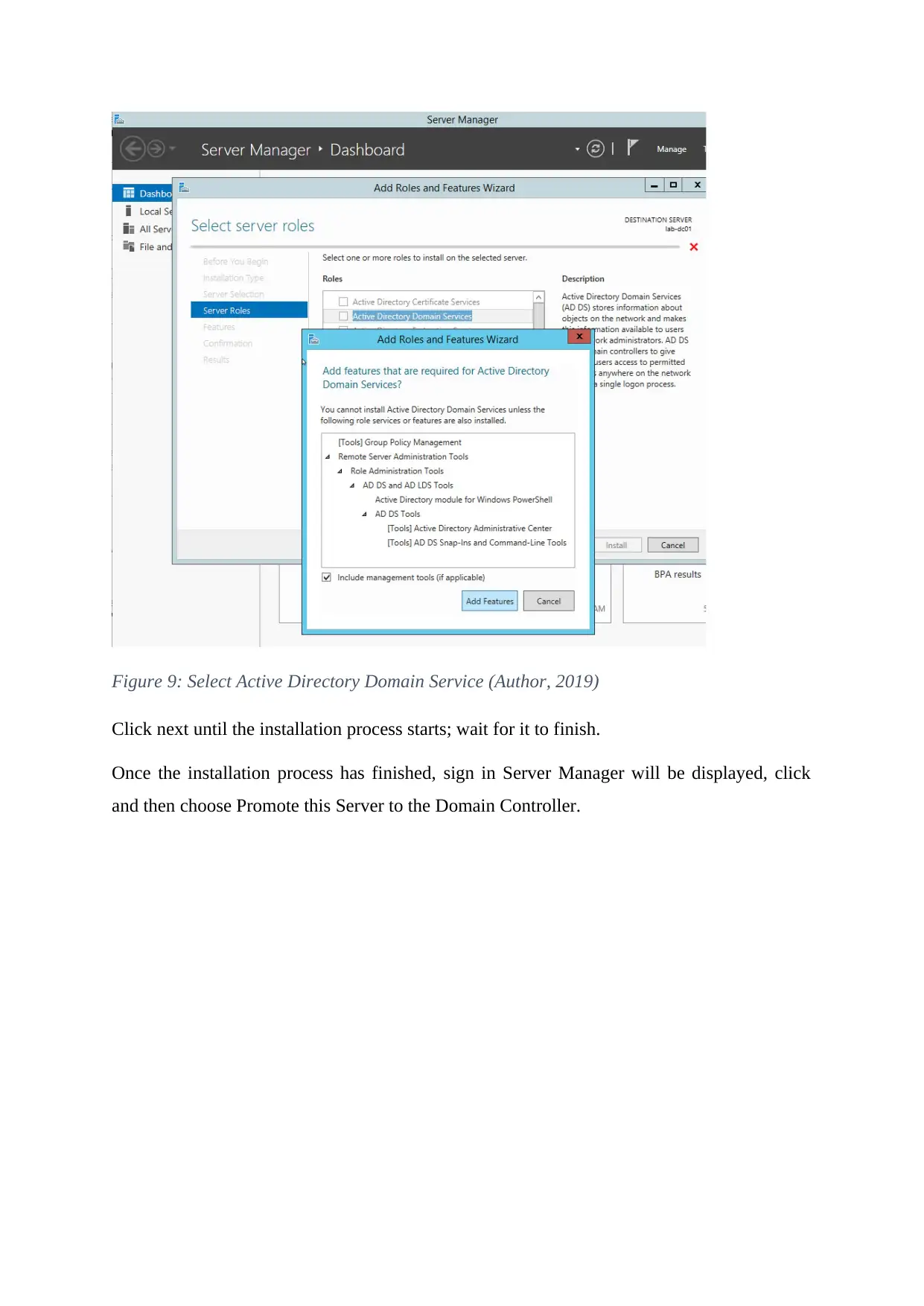
Figure 9: Select Active Directory Domain Service (Author, 2019)
Click next until the installation process starts; wait for it to finish.
Once the installation process has finished, sign in Server Manager will be displayed, click
and then choose Promote this Server to the Domain Controller.
Click next until the installation process starts; wait for it to finish.
Once the installation process has finished, sign in Server Manager will be displayed, click
and then choose Promote this Server to the Domain Controller.
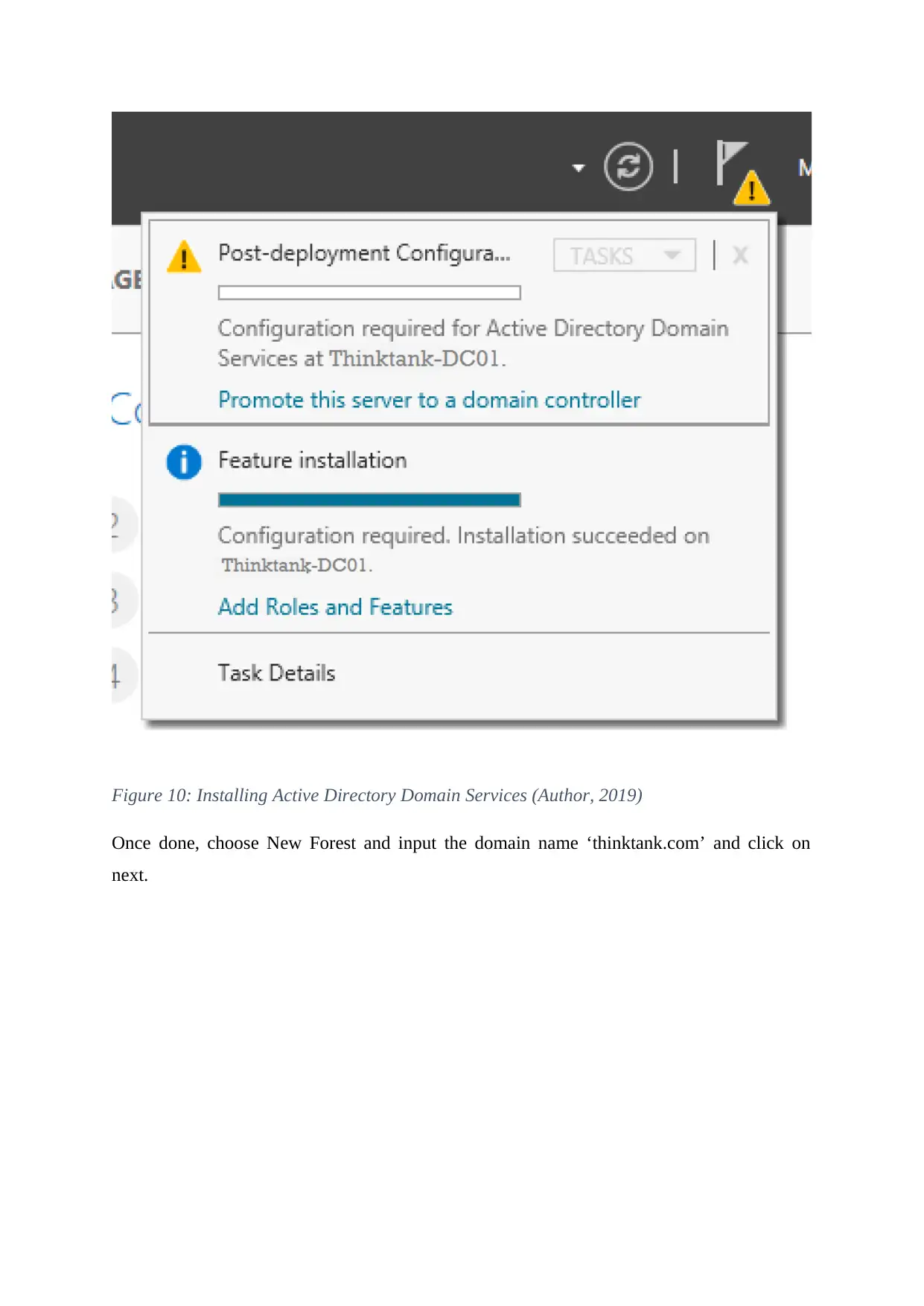
Figure 10: Installing Active Directory Domain Services (Author, 2019)
Once done, choose New Forest and input the domain name ‘thinktank.com’ and click on
next.
Once done, choose New Forest and input the domain name ‘thinktank.com’ and click on
next.
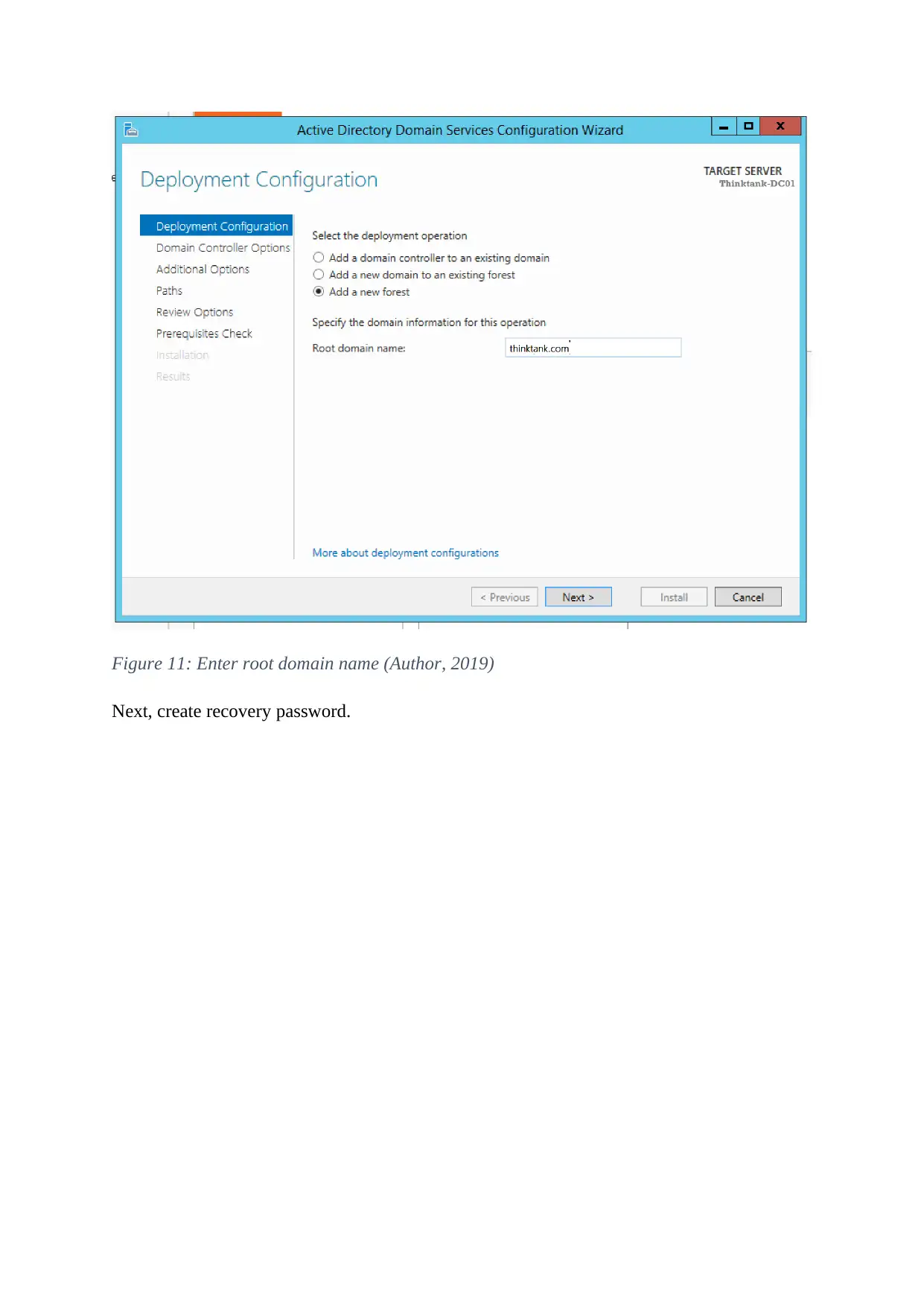
Figure 11: Enter root domain name (Author, 2019)
Next, create recovery password.
Next, create recovery password.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
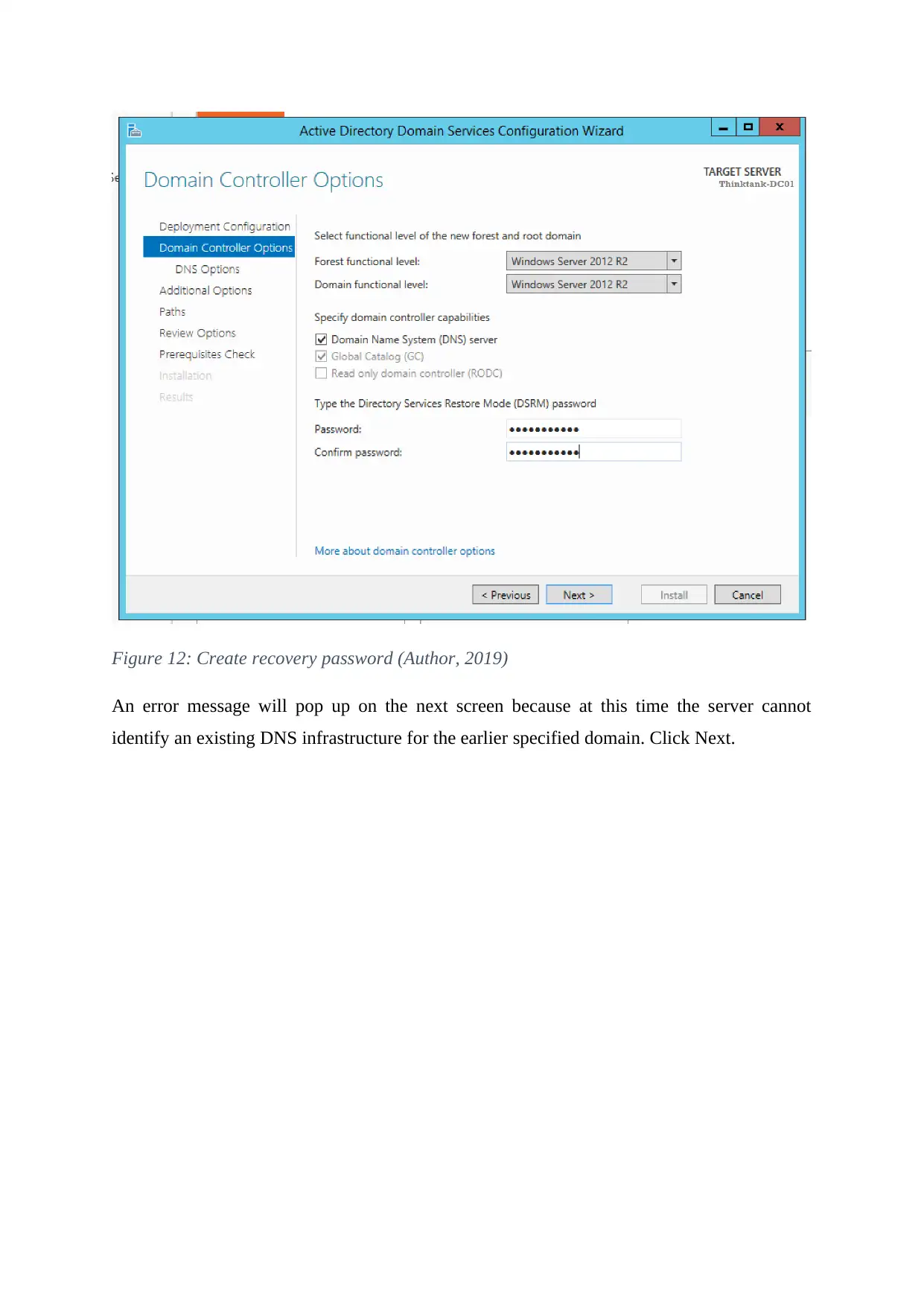
Figure 12: Create recovery password (Author, 2019)
An error message will pop up on the next screen because at this time the server cannot
identify an existing DNS infrastructure for the earlier specified domain. Click Next.
An error message will pop up on the next screen because at this time the server cannot
identify an existing DNS infrastructure for the earlier specified domain. Click Next.
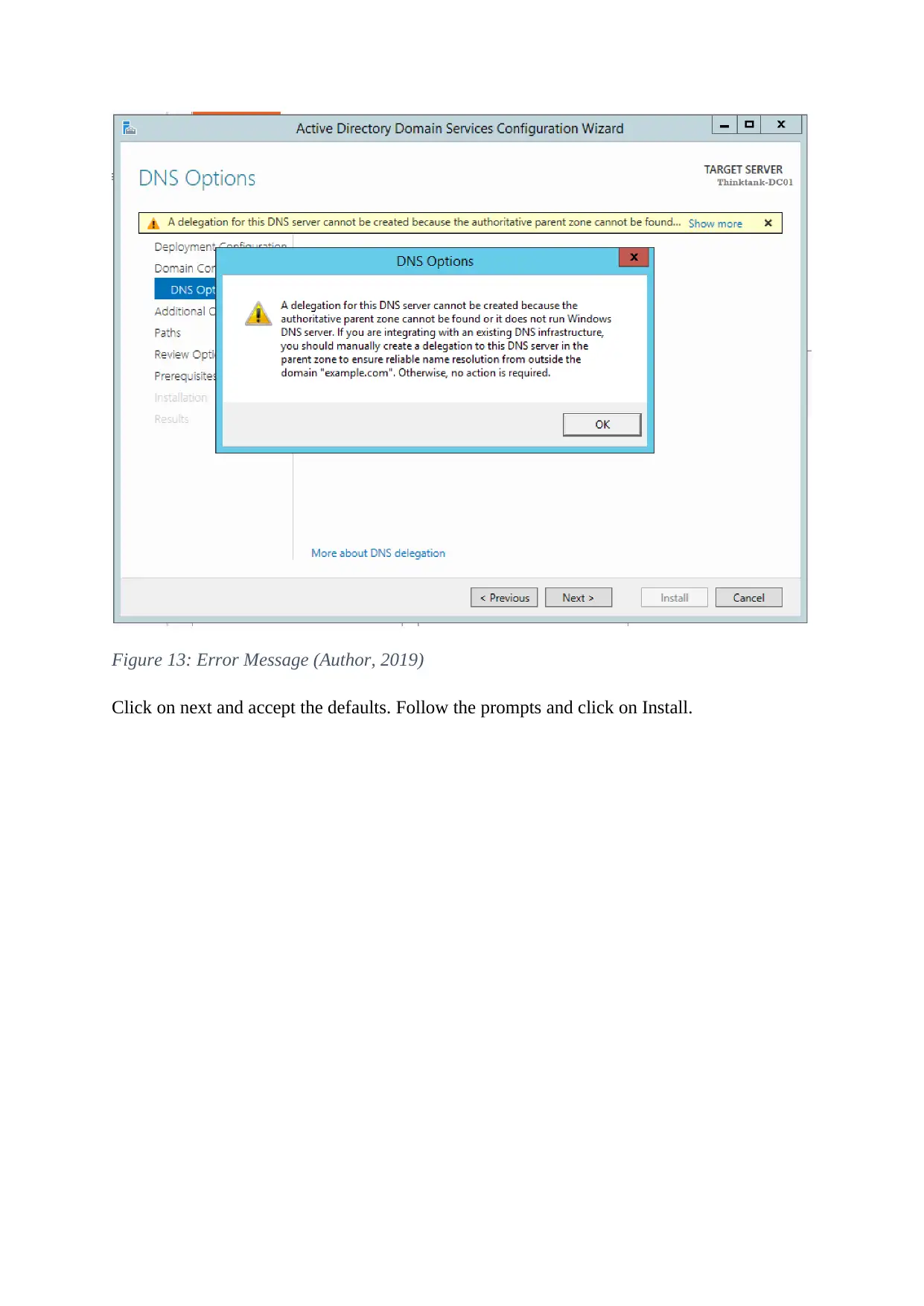
Figure 13: Error Message (Author, 2019)
Click on next and accept the defaults. Follow the prompts and click on Install.
Click on next and accept the defaults. Follow the prompts and click on Install.
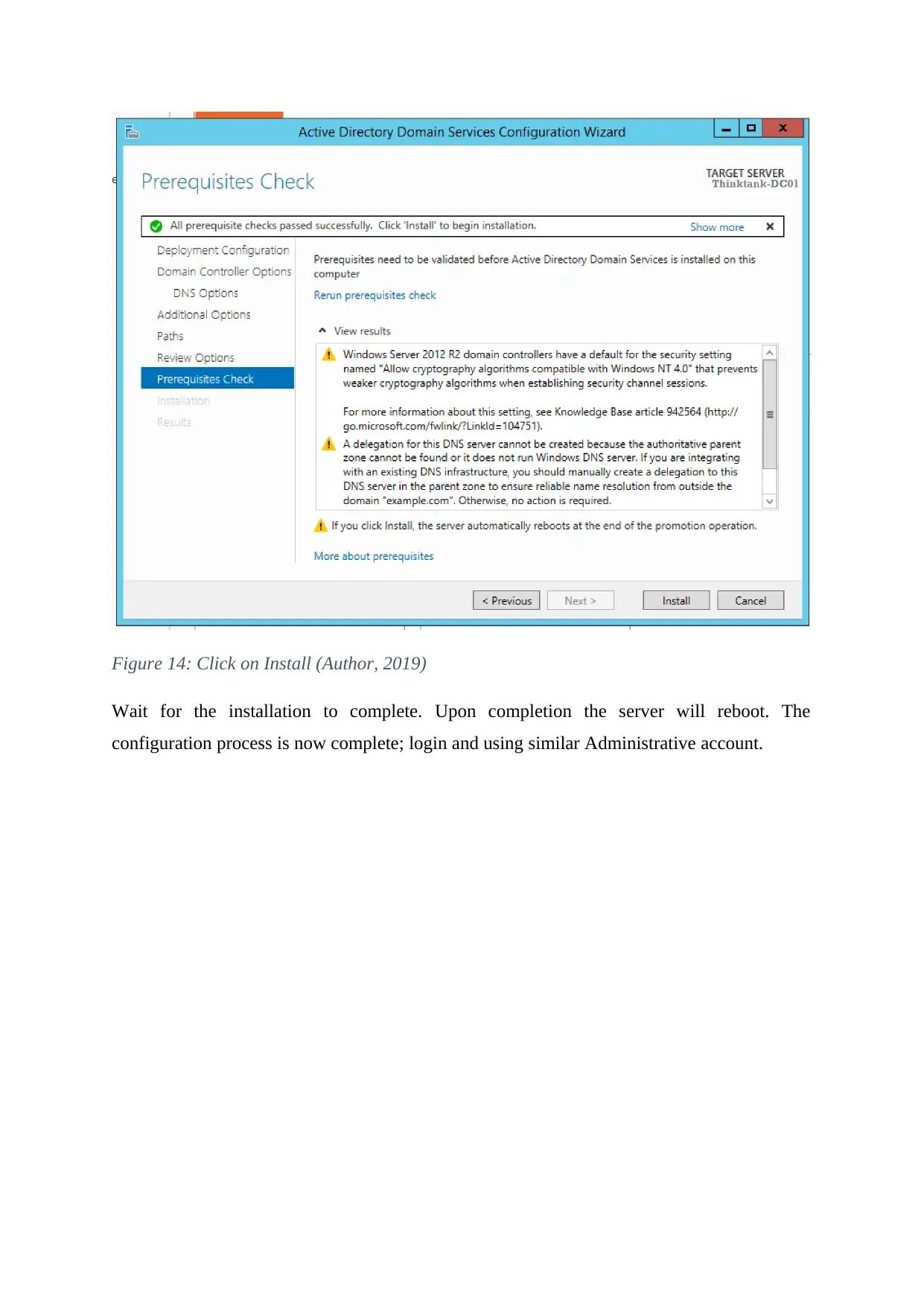
Figure 14: Click on Install (Author, 2019)
Wait for the installation to complete. Upon completion the server will reboot. The
configuration process is now complete; login and using similar Administrative account.
Wait for the installation to complete. Upon completion the server will reboot. The
configuration process is now complete; login and using similar Administrative account.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Figure 15: Login and Start using the services. (Author, 2019)
Active Directory Domain Structure
Active Directory Domain Structure
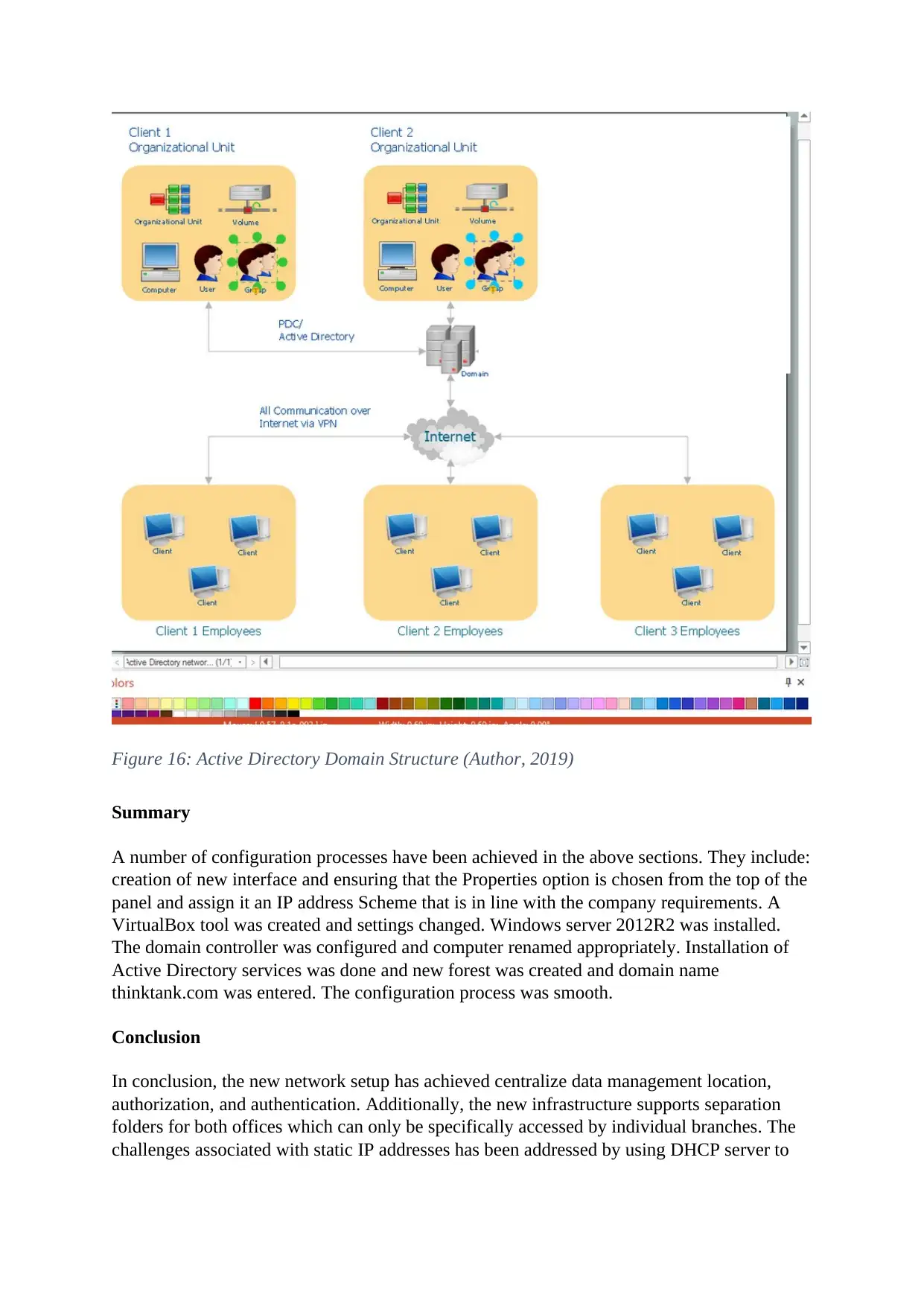
Figure 16: Active Directory Domain Structure (Author, 2019)
Summary
A number of configuration processes have been achieved in the above sections. They include:
creation of new interface and ensuring that the Properties option is chosen from the top of the
panel and assign it an IP address Scheme that is in line with the company requirements. A
VirtualBox tool was created and settings changed. Windows server 2012R2 was installed.
The domain controller was configured and computer renamed appropriately. Installation of
Active Directory services was done and new forest was created and domain name
thinktank.com was entered. The configuration process was smooth.
Conclusion
In conclusion, the new network setup has achieved centralize data management location,
authorization, and authentication. Additionally, the new infrastructure supports separation
folders for both offices which can only be specifically accessed by individual branches. The
challenges associated with static IP addresses has been addressed by using DHCP server to
Summary
A number of configuration processes have been achieved in the above sections. They include:
creation of new interface and ensuring that the Properties option is chosen from the top of the
panel and assign it an IP address Scheme that is in line with the company requirements. A
VirtualBox tool was created and settings changed. Windows server 2012R2 was installed.
The domain controller was configured and computer renamed appropriately. Installation of
Active Directory services was done and new forest was created and domain name
thinktank.com was entered. The configuration process was smooth.
Conclusion
In conclusion, the new network setup has achieved centralize data management location,
authorization, and authentication. Additionally, the new infrastructure supports separation
folders for both offices which can only be specifically accessed by individual branches. The
challenges associated with static IP addresses has been addressed by using DHCP server to

dynamically assign the IP addresses. The network has achieved most of the company
requirements.
requirements.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

References
[1] D. Fisher, Professional Networking For Dummies. New York, NY: John Wiley & Sons,
2011.
[2] M. Ciampa, Security+ guide to network security fundamentals. Boston, MA.: Course
Technology/ Cengage Learning, 2011.
[3] M. Schiffman, Building open source network security tools. New York: Wiley Pub., 2013.
[4] M. Mahmoud, N. Larrieu and A. Pirovano, Risk propagation assessment for network
security. London: ISTE, 2013.
[5] W. Stanek, Active directory. Redmond, Wash.: Microsoft Press, 2011.
[6] M. Femminella, F. Giacinti and G. Reali, "Optimal deployment of open source
application servers providing multimedia services", IEEE Network, vol. 28, no. 5, pp.
54-63, 2014. Available: 10.1109/mnet.2014.6915440.
[7] U. Ghosh and R. Datta, "IDSDDIP: a secure distributed dynamic IP configuration scheme
for mobile ad hoc networks", International Journal of Network Management, vol. 23, no.
6, pp. 424-446, 2013. Available: 10.1002/nem.1849.
[8] F. Andrus, "Beyond scan and block: an adaptive approach to network access
control", Network Security, vol. 2011, no. 11, pp. 5-9, 2011. Available: 10.1016/s1353-
4858(11)70117-9.
[9] I. Infoblox, "What is a DHCP Server? | Learn What They Are & How They Work |
Infoblox", Infoblox, 2018. [Online]. Available: https://www.infoblox.com/glossary/dhcp-
server/. [Accessed: 17- May- 2019].
[10] A. Minocha, "Generating domain using the Web Directory", Advanced Computing: An
International Journal, vol. 3, no. 5, pp. 45-51, 2012. Available: 10.5121/acij.2012.3505.
[11] B. Desmond, Active directory. Farnham: O'Reilly, 2013.
[12] M. Minasi, Mastering Windows Server 2012 R2. Indianapolis: Sybex, 2014.
[1] D. Fisher, Professional Networking For Dummies. New York, NY: John Wiley & Sons,
2011.
[2] M. Ciampa, Security+ guide to network security fundamentals. Boston, MA.: Course
Technology/ Cengage Learning, 2011.
[3] M. Schiffman, Building open source network security tools. New York: Wiley Pub., 2013.
[4] M. Mahmoud, N. Larrieu and A. Pirovano, Risk propagation assessment for network
security. London: ISTE, 2013.
[5] W. Stanek, Active directory. Redmond, Wash.: Microsoft Press, 2011.
[6] M. Femminella, F. Giacinti and G. Reali, "Optimal deployment of open source
application servers providing multimedia services", IEEE Network, vol. 28, no. 5, pp.
54-63, 2014. Available: 10.1109/mnet.2014.6915440.
[7] U. Ghosh and R. Datta, "IDSDDIP: a secure distributed dynamic IP configuration scheme
for mobile ad hoc networks", International Journal of Network Management, vol. 23, no.
6, pp. 424-446, 2013. Available: 10.1002/nem.1849.
[8] F. Andrus, "Beyond scan and block: an adaptive approach to network access
control", Network Security, vol. 2011, no. 11, pp. 5-9, 2011. Available: 10.1016/s1353-
4858(11)70117-9.
[9] I. Infoblox, "What is a DHCP Server? | Learn What They Are & How They Work |
Infoblox", Infoblox, 2018. [Online]. Available: https://www.infoblox.com/glossary/dhcp-
server/. [Accessed: 17- May- 2019].
[10] A. Minocha, "Generating domain using the Web Directory", Advanced Computing: An
International Journal, vol. 3, no. 5, pp. 45-51, 2012. Available: 10.5121/acij.2012.3505.
[11] B. Desmond, Active directory. Farnham: O'Reilly, 2013.
[12] M. Minasi, Mastering Windows Server 2012 R2. Indianapolis: Sybex, 2014.
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





